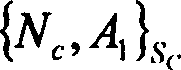Patents
Literature
92results about How to "Enable secure access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
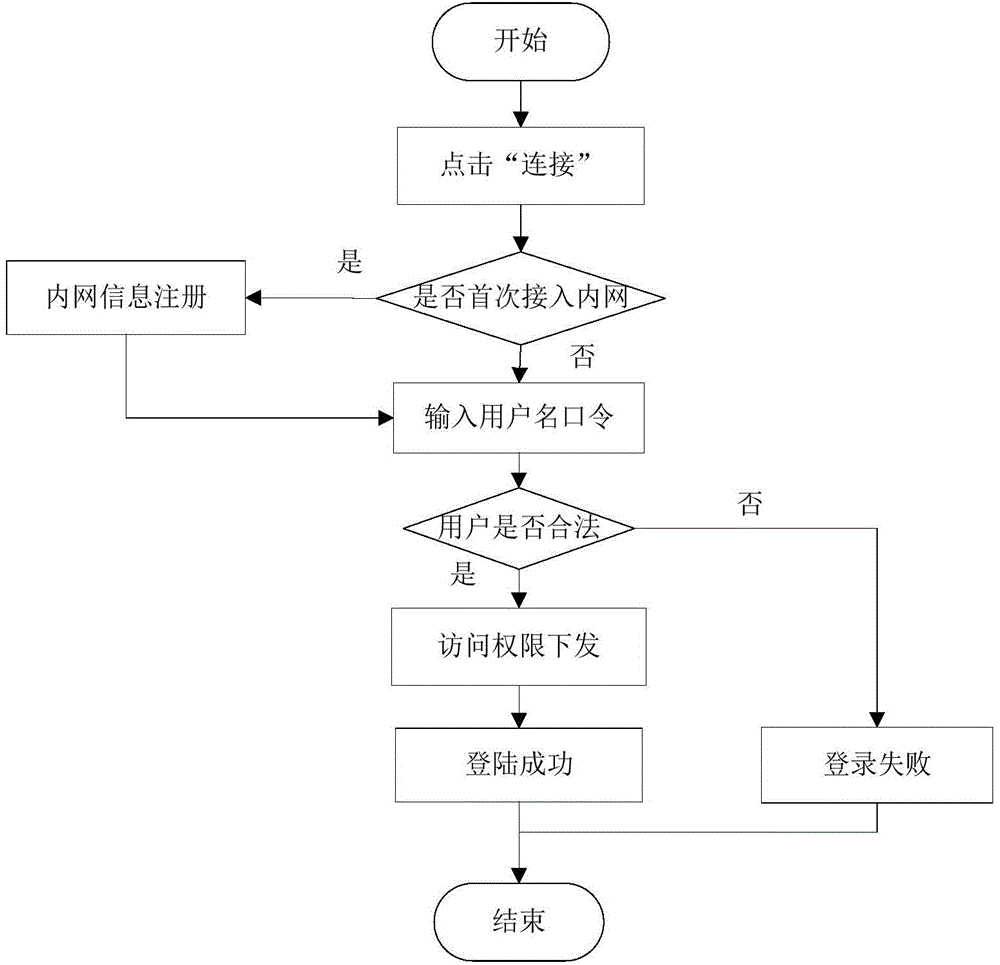
Network authentication and key allocation method across secure domains
InactiveCN1805341AOvercoming the shortcomings of decentralized authenticationEnsure safetyKey distribution for secure communicationUser identity/authority verificationApplication serverWeb authentication
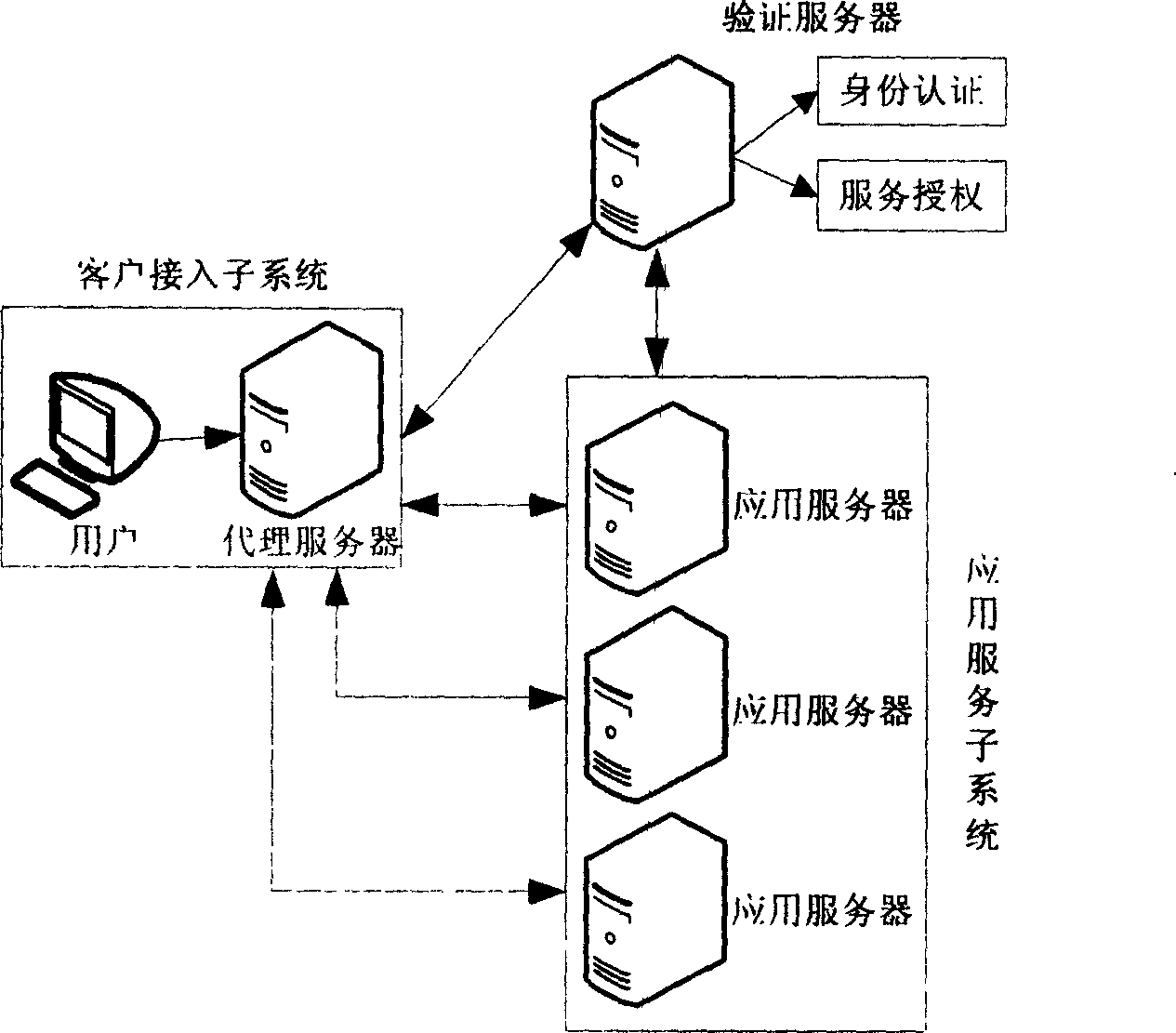
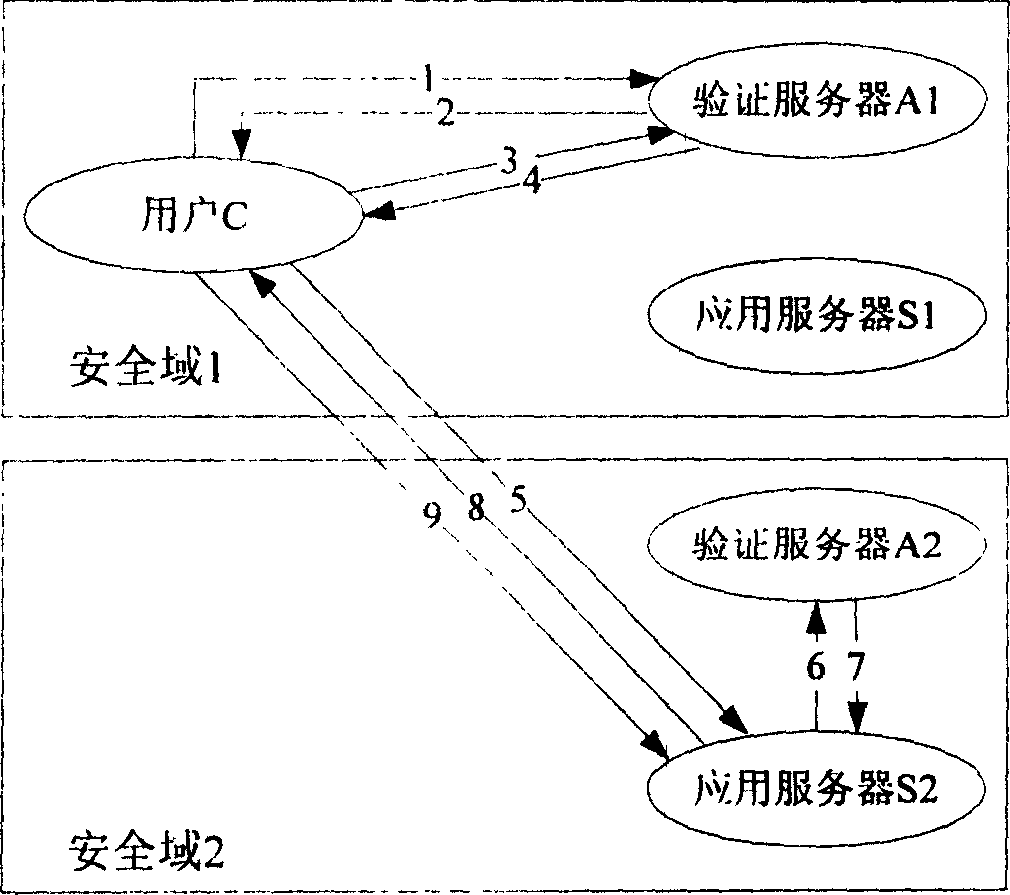
The invention relates to a network authentication and key distribution method. based on the single point log-in, connecting one authentication server and several application servers into each safety field; distributing the authentication and keys according to the demand of application server when the user accesses into different safety fields. First, user processes the identification authentication in said safety field to attain a server card communicating with the application server in another safety field; then the user at the accessed safety field validates the card to attain the service connecting with the application server; at last, the user processes the identification authentication on said application server. The inventive system comprises a client access subsystem, an application service subsystem and a validate server which can complete the user identification authentication and the service authorization. The invention has simple process, with high safety and effect.
Owner:XIDIAN UNIV
Method, apparatus, system, storage medium, and electronic device for securely accessing block chain
ActiveCN108235806AEnable secure accessReduce complexityUser identity/authority verificationThird partyChain network
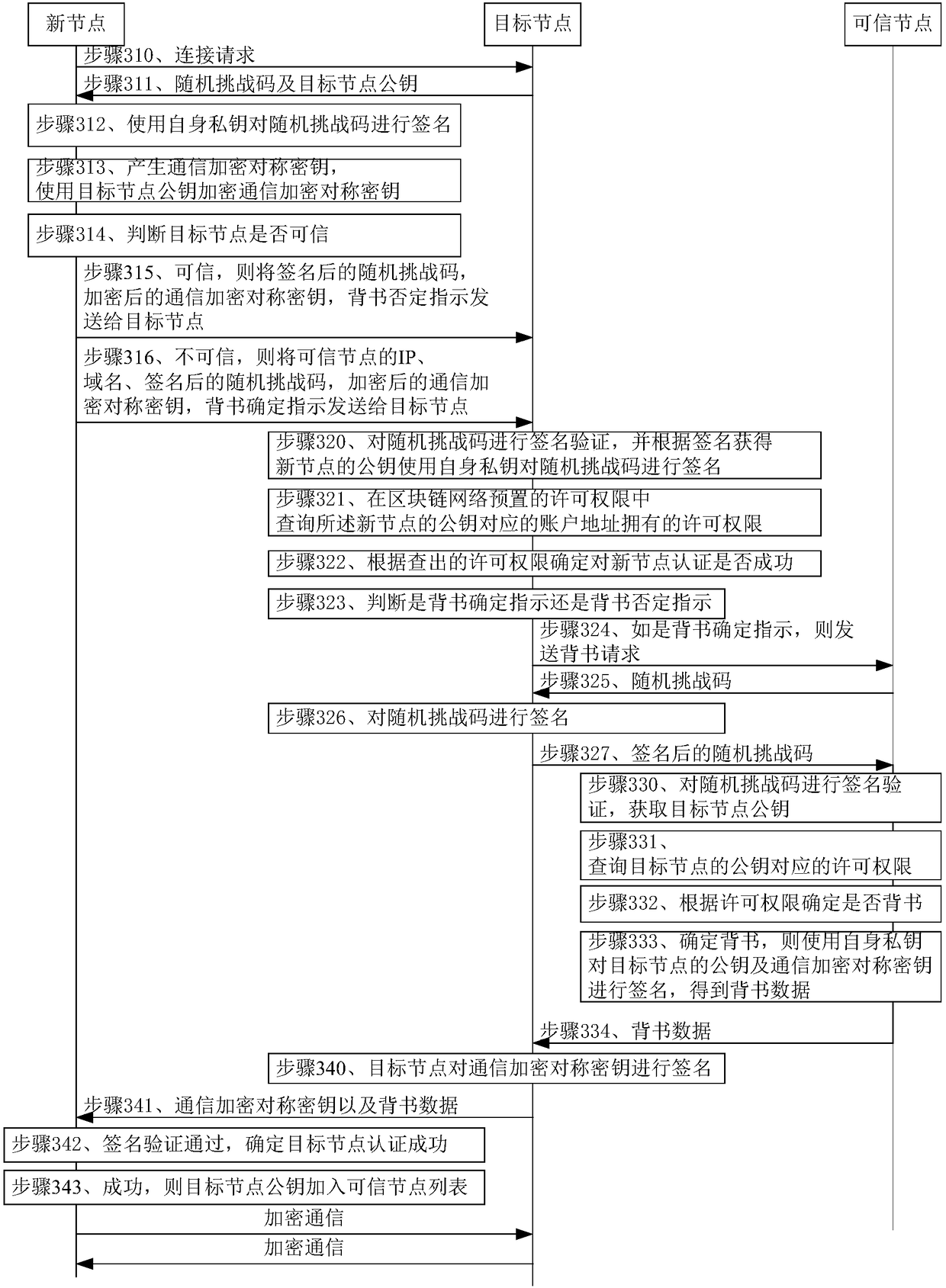
The present disclosure proposes a method, an apparatus, a system, a storage medium, and an electronic device for securely accessing a block chain. The method comprises: preparing a new node accessingthe blockchain network to obtain endorsement data obtained by the trusted node preset in the block chain network using the private key to sign the target node public key, and performing signature verification on the endorsement data, if the signature After the verification is passed, it is determined that the identity authentication of the target node is successful, and the target node queries thepermission right of the new node's public key corresponding to the account address in the permission preset by the block chain network, and determines the new permission according to the checked permission. Whether the identity authentication of the node is successful. Therefore, the two-way authentication of the new node and the target node of the present disclosure directly utilizes the publicand private keys of the node of the block chain network node, and does not require a centralized third party to participate in the digital certificate, thereby avoiding the high complexity brought bythe digital certificate issuance. Secure access between nodes in the block chain network.
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
Secure access control system and method for network terminal nodes
InactiveCN104796261AReal-time monitoring of identity informationReal-time monitoring of the access verification processUser identity/authority verificationNetwork terminationPrivate network
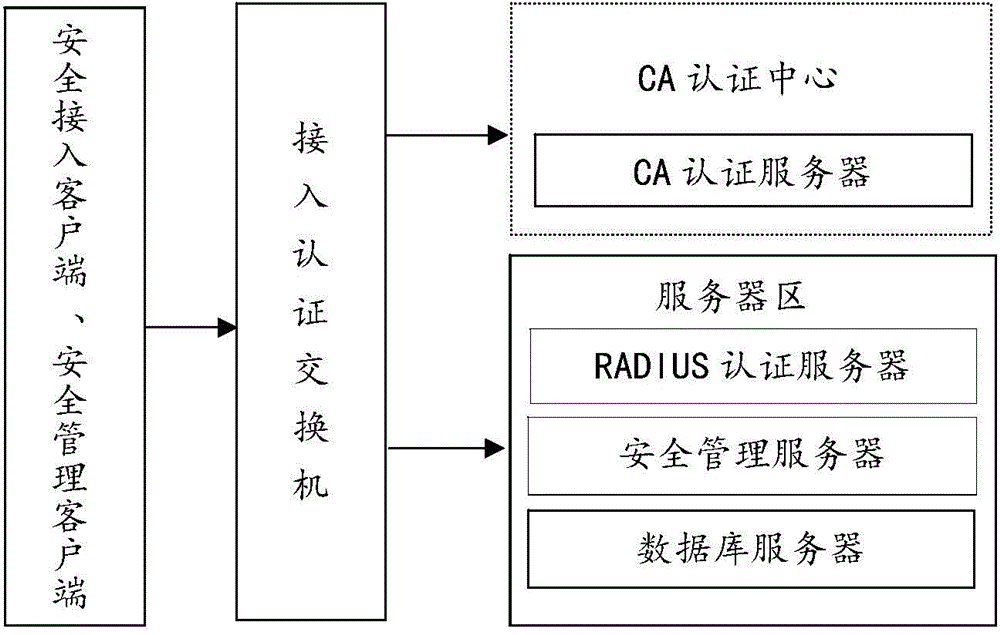
The invention discloses a secure access control system and method for network terminal nodes. A C / S (client / server) architecture is provided between a secure access client and a CA (certificate authority) authentication server, and another C / S architecture is provided between the secure access client and an RADIUS (remote authentication dial-in user service) authentication server; the two C / S architectures are used for user identity authentication and terminal access authentication, respectively. A B / S (browser / server) architecture is provided between a security management client and a security management server and is used mainly for registering and checking user information, setting network access group permissions and controlling and monitoring secure access in real time. The secure access control system and method has the advantages that the access terminals can be subjected to trusted identity authentication, trusted access authentication, terminal proxy authentication, network access permission control and network access state real-time monitoring; a trusted terminal access control system based on identity authentication is achieved and is stable and reliable and is high in authentication efficiency, violations such as NAT (network address translation) and proxy services can be detected and warned accurately, network states of terminal users are monitored and controlled through a web management interface, and the needs of private networks for safety management can be fully met.
Owner:CHANGAN UNIV
System and method for self-organized network
InactiveCN101364910ASelf-organizingEnable secure accessNetwork topologiesNetworks interconnectionHome Node BData information
Owner:ZTE CORP
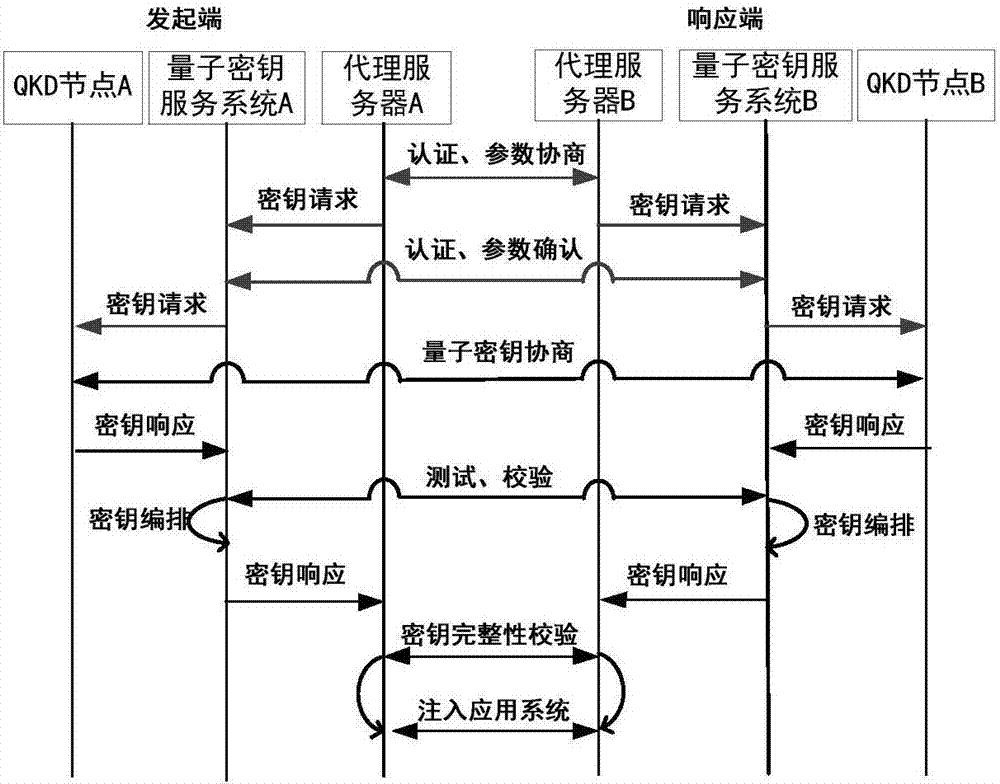
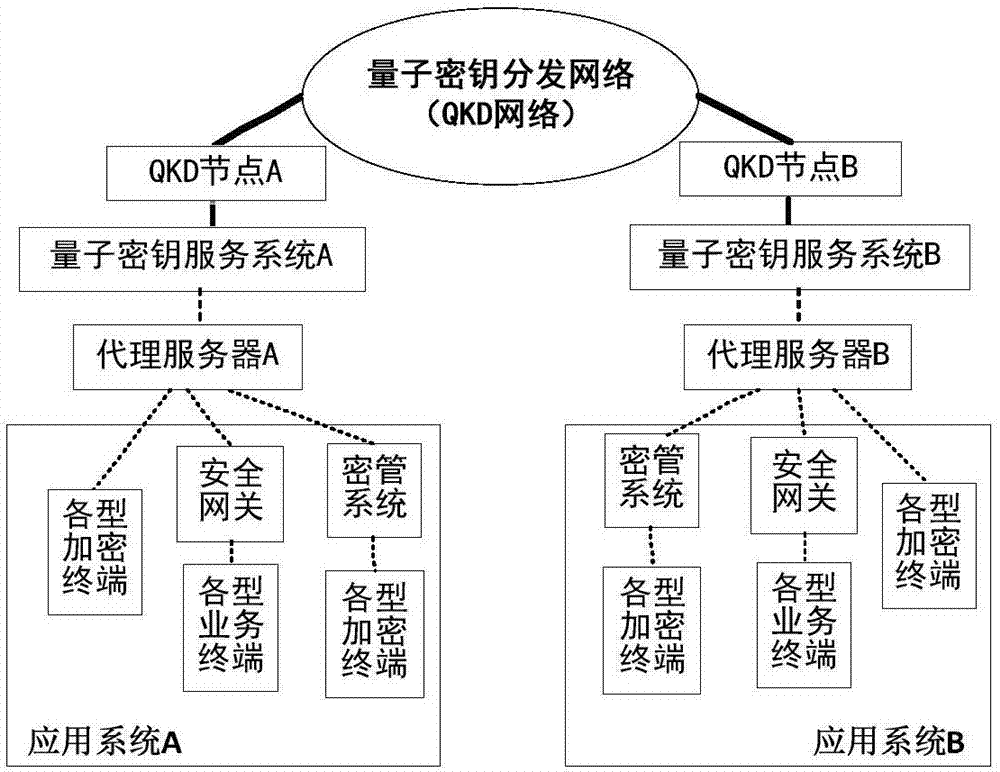
Safe and high-efficient quantum key service method
ActiveCN107453868AIncrease flexibilityQuick dockingKey distribution for secure communicationService modeQuantum
The invention discloses a safe and high-efficient quantum key service method. The method aims at solving flexibility, safety and efficiency problems of a cross-domain service of a quantum key from a QKD network to a traditional secret communication network. A special interface is adopted to realize real-time access and adaption of the quantum key; cross-domain isolation is adopted to realize physical safety of quantum key processing; and a centralized layout and distributed encryption ferry is adopted to realize a safe and high-efficiency service of the quantum key. In the invention, through deploying a quantum key service system on a QKD node, based on the traditional secret communication network, a safe and high-efficiency quantum key service is provided for a user in an area range; and simultaneously the safety, flexibility and efficiency problems of the quantum key service are solved. Based on high safety, convenient application access and a flexible service mode, a good application prospect is possessed in fields of party, government, industrial control, finance, military and the like.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
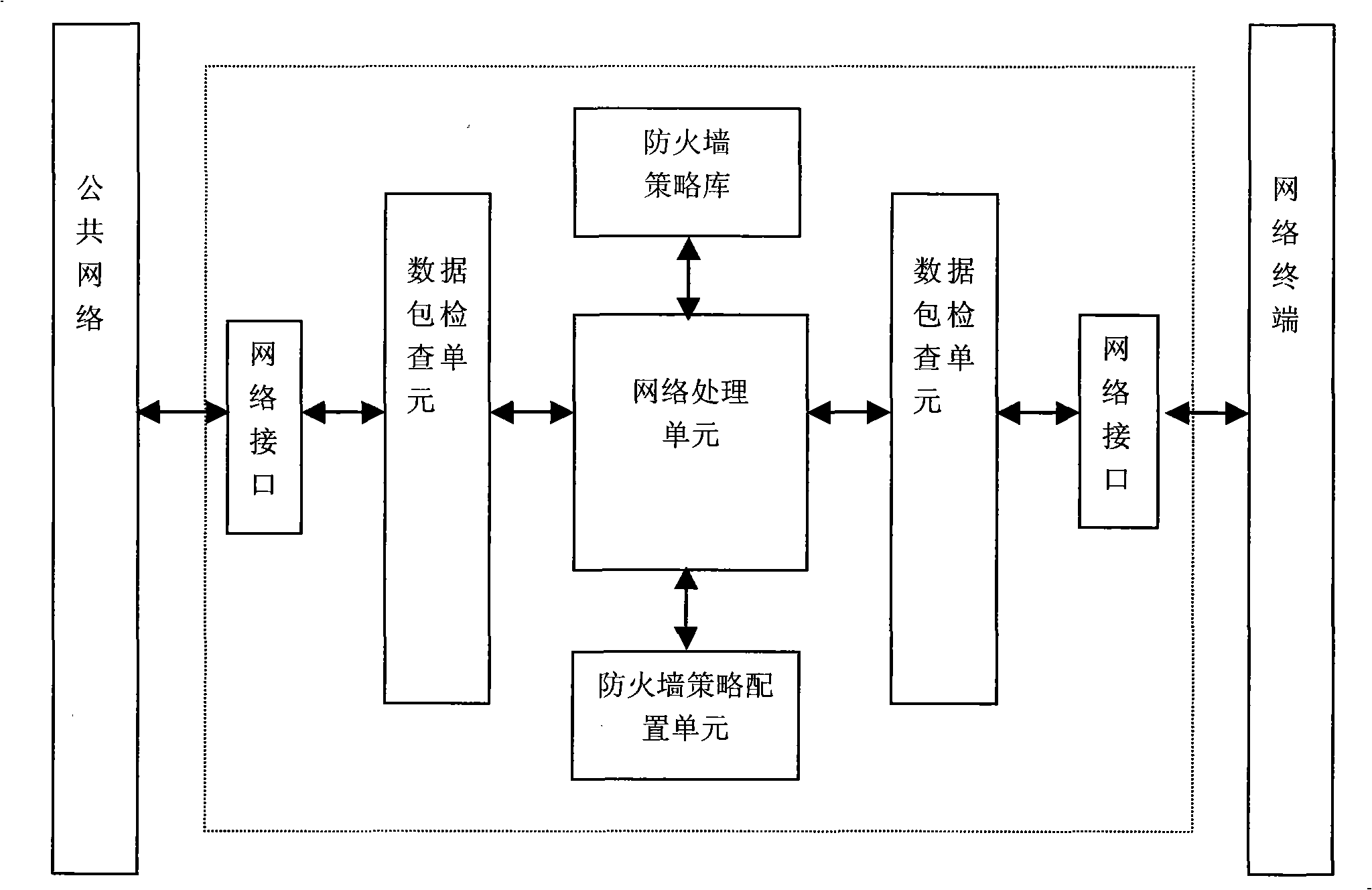
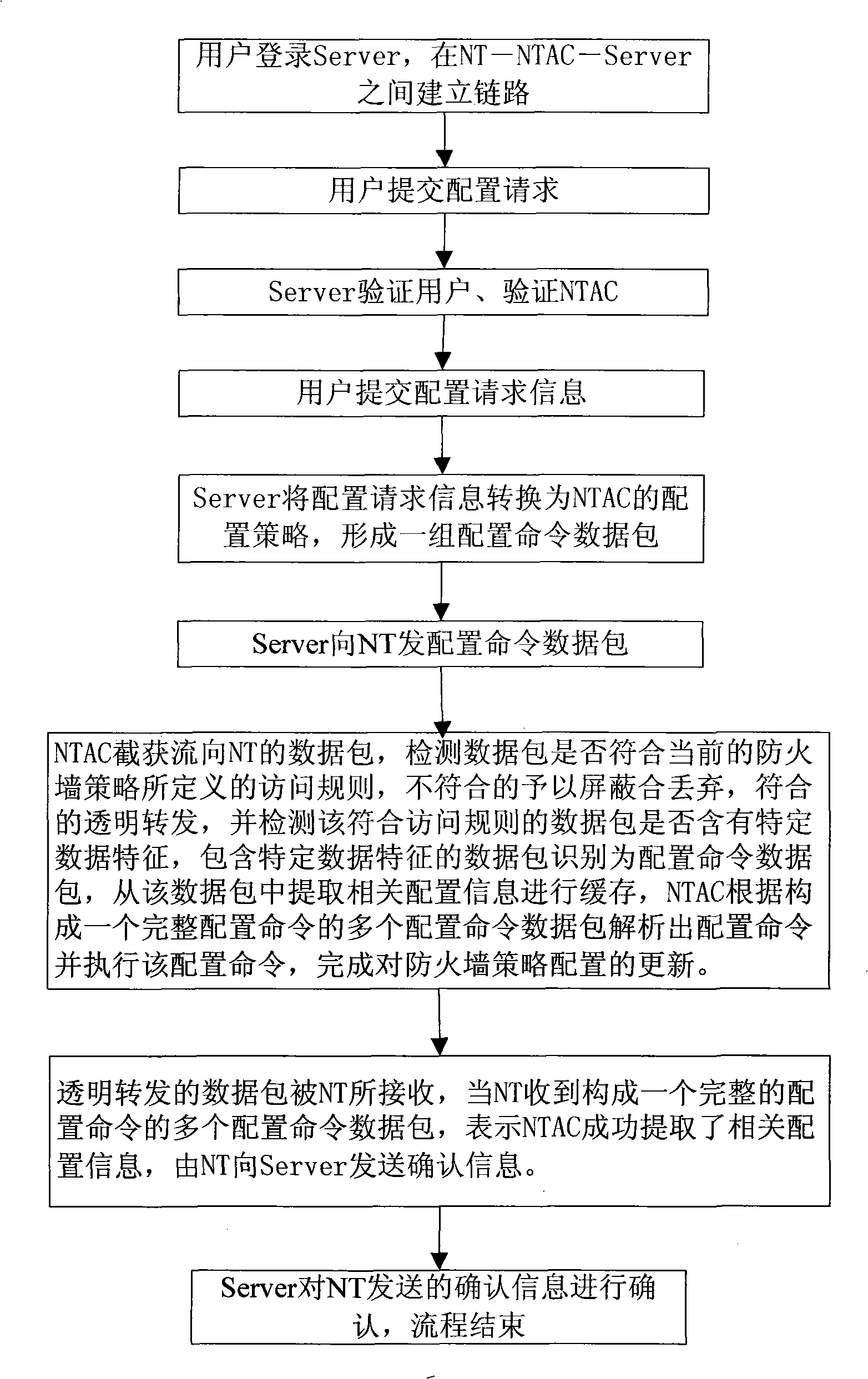
Method and system for implementing safety access public network of network terminal as well as special network access controller thereof
ActiveCN101355415ASecure AccessEasy to useNetwork connectionsSecuring communicationNetwork terminationNetwork packet
The invention discloses a method for realizing that a network terminal can safely access a public network. The method comprises the following steps: a network access controller is connected in series between the network terminal and the public network; when a firewall strategy database is required to be configured, a user on a network terminal submits configuration request information; the network access control server generates a group of corresponding configuration command data packet which is transmitted to the network terminal according to the configuration request information; the group of configuration command data packet is captured by the network access control server which is connected in series on the link so as to analyze and execute the corresponding configuration command and complete the update to the configuration of firewall policy; and the user on the network terminal access the public network under the security protection of the firewall policy configured by the network access control server. The invention also discloses a system for realizing that the network terminal can safely access the public network and the network access control server. The method, the system and the network access control server not only can ensure that the network terminal can safely access the public network, but also can be convenient for a user to use.
Owner:苏州凌犀物联网技术有限公司
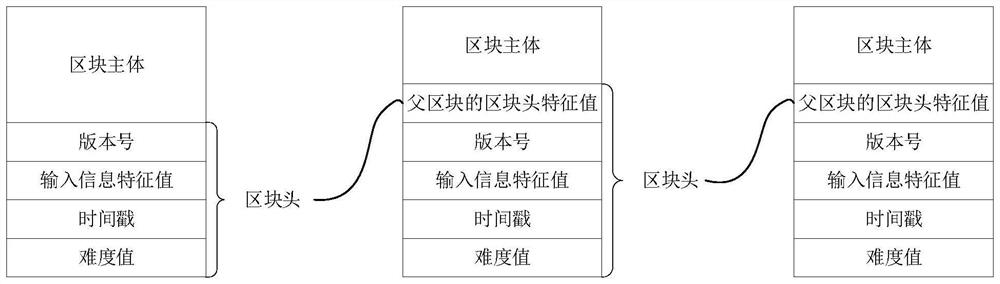
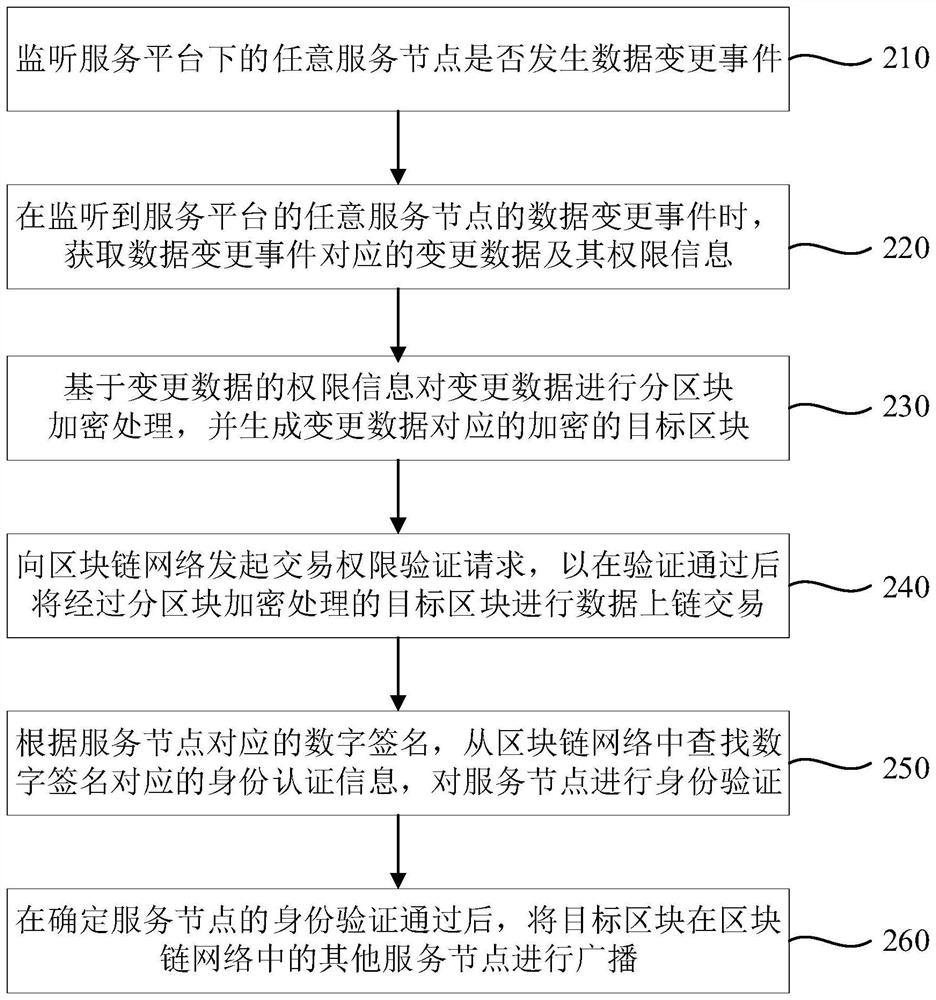
Platform data management method and device based on block chain and storage medium
PendingCN112581126AGuaranteed data sharingImprove securityEncryption apparatus with shift registers/memoriesUser identity/authority verificationIndependent dataChain network
The embodiment of the invention provides a platform data management method and device based on a block chain and a storage medium, and relates to the technical field of block chains. The method comprises the steps of obtaining change data corresponding to a data change event when the data change event of any service node under a service platform is monitored; wherein the service platform comprisesa plurality of service nodes which are constructed based on a block chain technology and are deployed in the same block chain network; encrypting the change data based on the authority information ofthe change data, and generating a target block corresponding to the change data; and after determining that the identity verification of the service node is passed, broadcasting the target block in other service nodes in the blockchain network. According to the technical scheme, data sharing of a plurality of original independent data systems is achieved, the service nodes corresponding to the data systems are deployed in the same block chain network, data sharing is guaranteed, meanwhile, information safety is effectively improved, and cross-department efficient and safe utilization of service data is achieved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Terminal and method for improving system safety
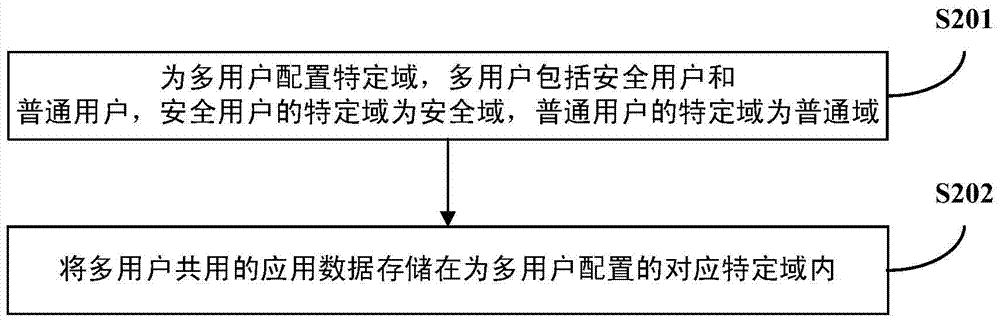
InactiveCN103886270AEnable secure accessImprove securityInternal/peripheral component protectionSecurity solutionComputer terminal
The invention discloses a terminal and a method for improving system safety. The terminal comprises a configuration module and a storage module, wherein the configuration module is used for configuring specific domains to a plurality of users, the users comprise the safe users and the common users, the specific domain of each safe user is a safe domain, and the specific domain of each common user is a common domain; the storage module is used for storing application data commonly used by the users in the specific domains corresponding to the users. By means of the technical scheme, the terminal and the method for improving the system safety solve the problem that an existing safe system cannot relate to multi-user safety solution schemes. By combining a multi-user mechanism and a Seandroid mechanism, a safety solution scheme is provided for the system, application can process the data in the specific domains of the users, and therefore the effect of improving the system safety is achieved, and the single terminal can have safe access to the data in the specific domains.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Wireless body area network security access method
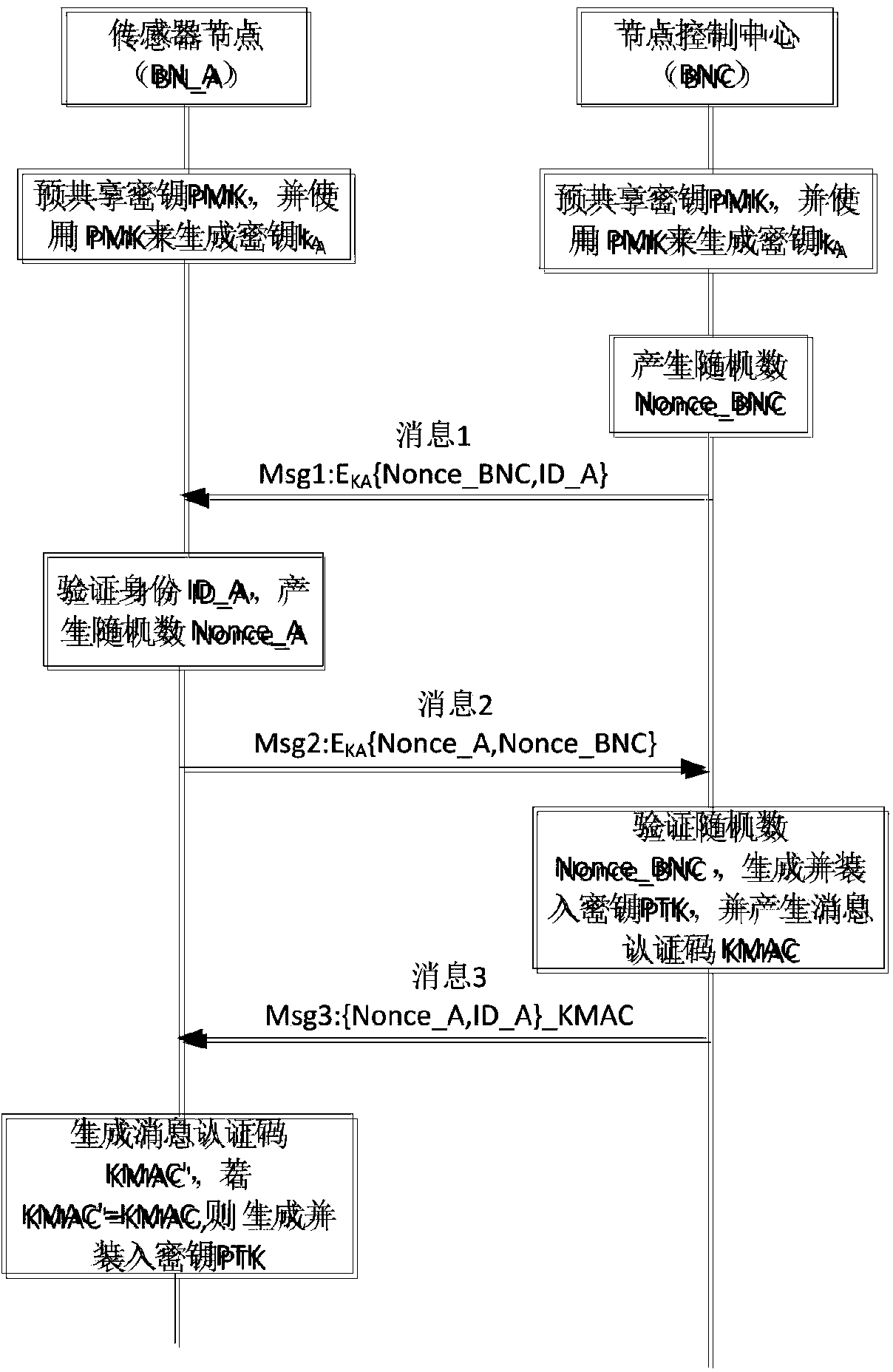
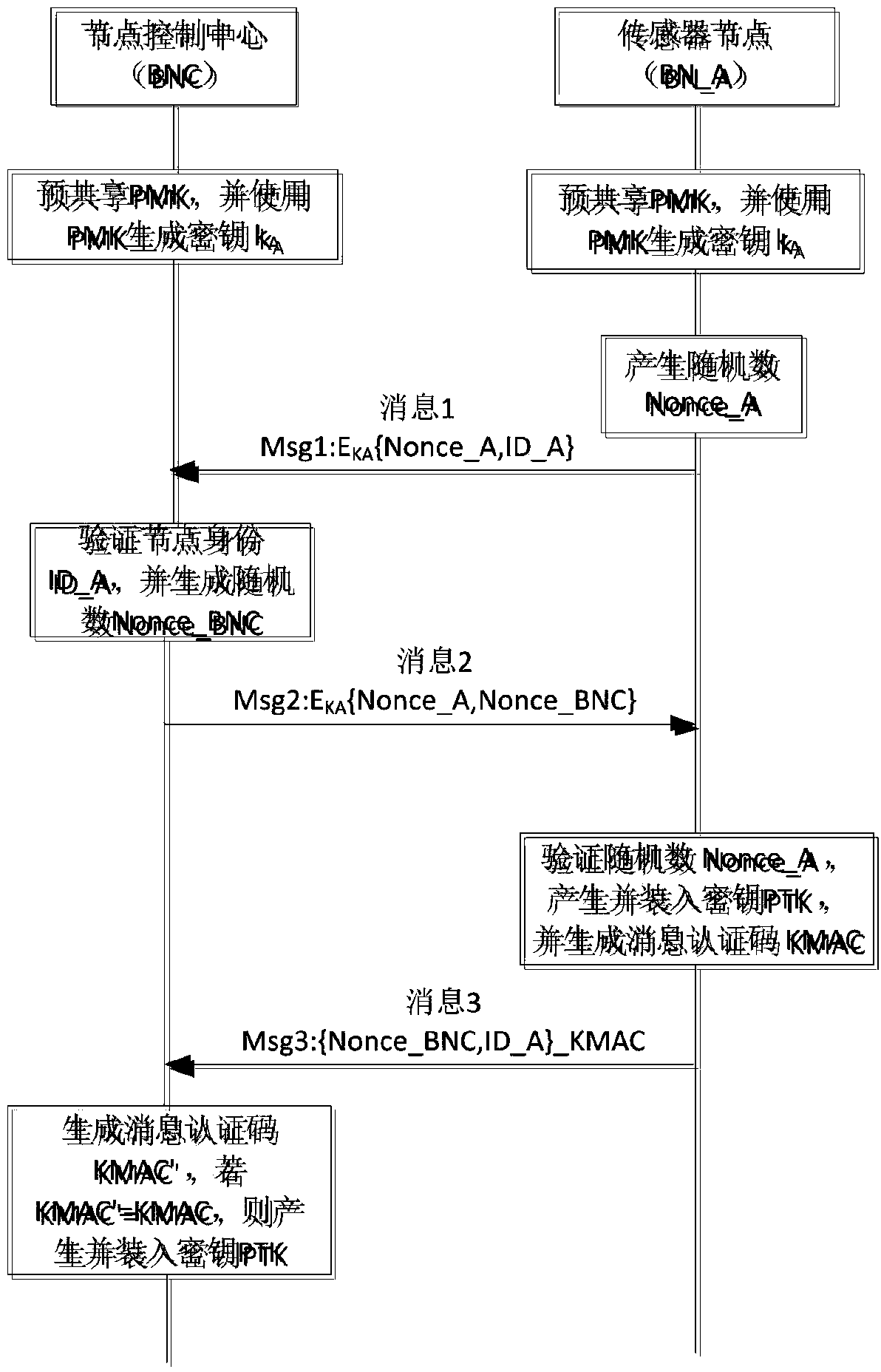
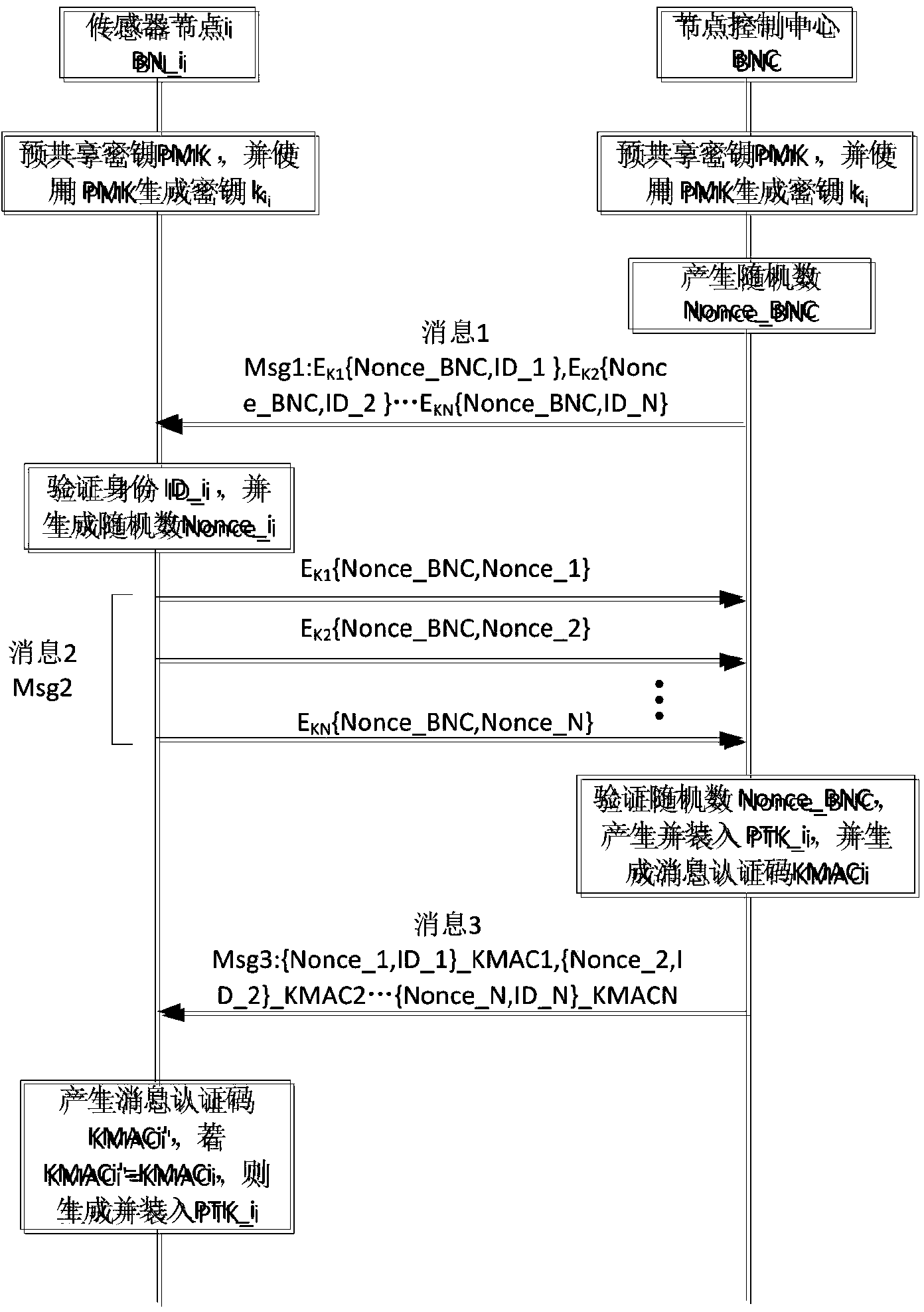
ActiveCN104301888AEnable secure accessReduce communication delayShort range communication serviceSecurity arrangementHand shakesAccess method
The invention discloses a wireless body area network security access method. Two interaction modes, namely, the unicast mode and the multicast mode, are set; two launching modes are set, and in other words, a network coordinator launches hand shaking and sensor nodes launch hand shaking; thus, when a certain part is injured and the blood pressure suddenly rises or in other words, the measurement indexes of a certain or some sensor nodes exceed the corresponding index limitations, the corresponding sensor nodes actively launch the hand shaking process, the situations of patients are rapidly fed back to medical staff, and patients are helped in time. According to the method, dynamic negotiation of a user conversation key is achieved through enhanced four-step hand shaking, hand shaking information is reduced, all the information is encrypted, the unicast access mode and the multicast access mode are set, and the remote access problem is solved through a multi-hop method. The method has the advantages that the access efficiency of a large number of sensing nodes is high, security is high, and the energy consumption is low, and the method can be used for the access of the sensing nodes in a wireless body area network and the dynamic negotiation of the user conversation key.
Owner:XIDIAN UNIV
Access control method, device, medium and electronic device
InactiveCN109472159AEnable secure accessImprove securityDigital data protectionAccess control matrixEmbedded system
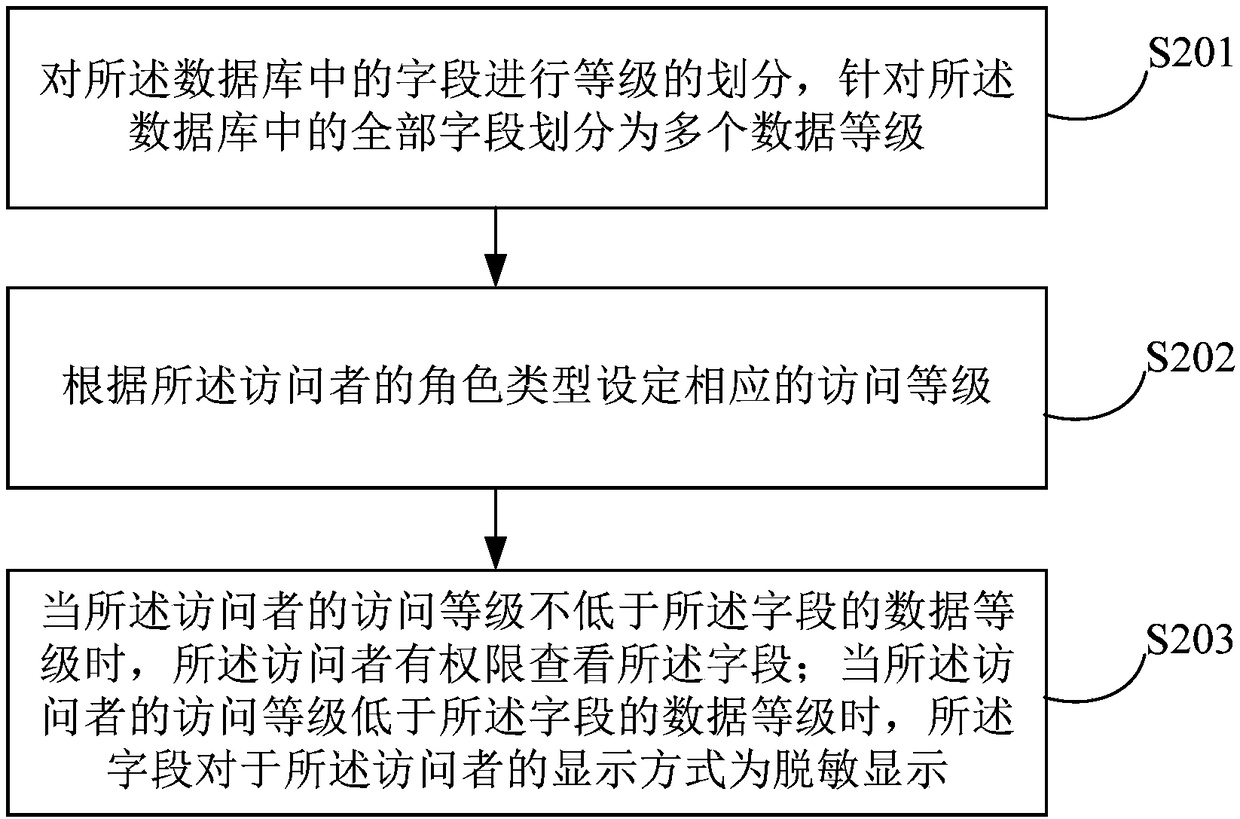
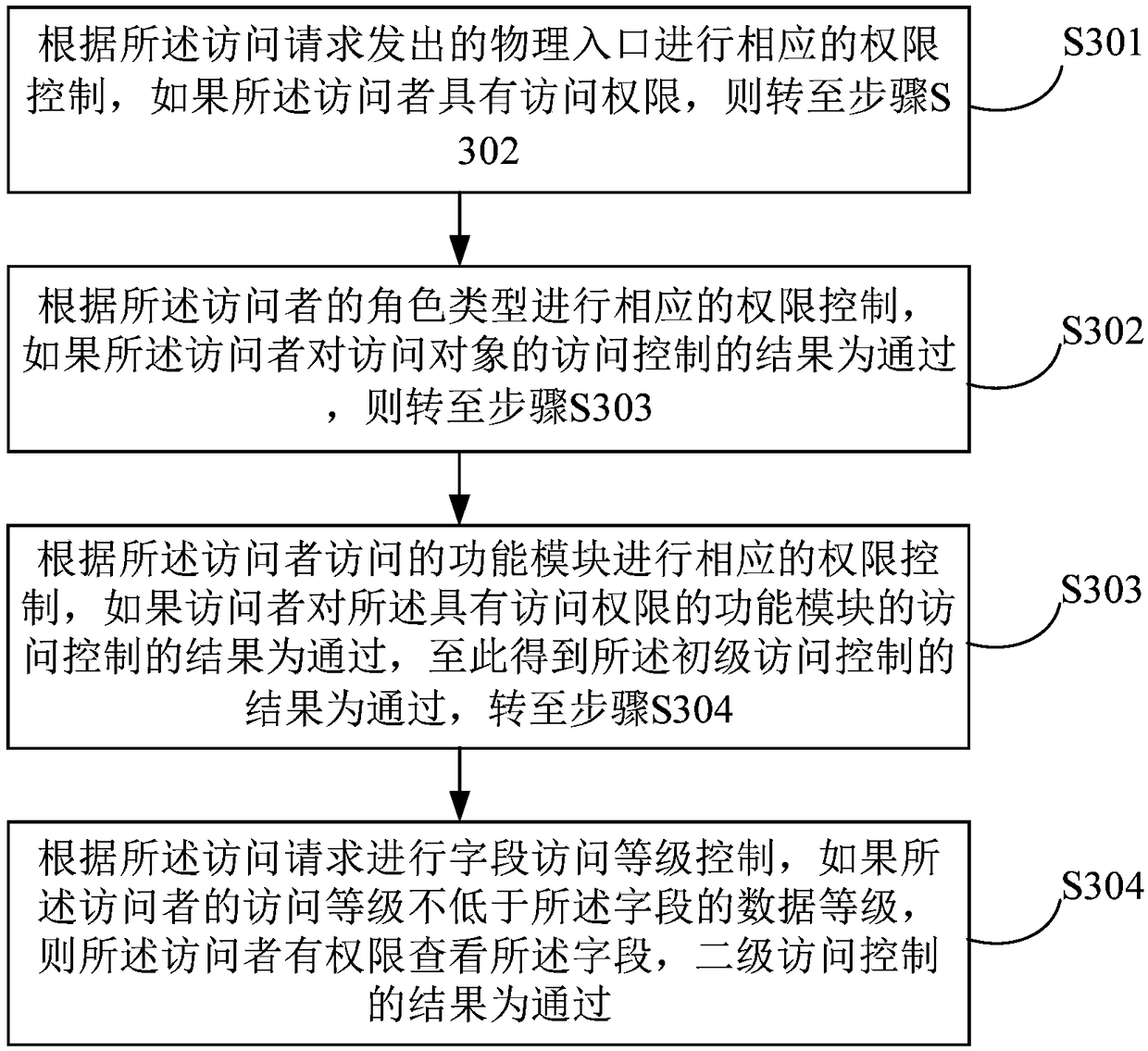
The embodiment of that invention relate to the field of information technology, Provided are an access control method, apparatus, computer-readable medium, and electronic device. The access control method includes receiving an access request from a visitor, obtaining a physical entry issued by the access request, at least one of a role type of the visitor, and a functional module accessed by the visitor. According to the physical entry sent out by the access request, the role type of the accessor and at least one of the functional modules accessed by the accessor to carry out corresponding right control to complete primary access control; If the result of the primary access control is passed, field access level control is performed according to the access request to complete the secondaryaccess control; Wherein the function module is obtained by classifying the requested database according to preset rules. The embodiment of the invention realizes the safe access to the database and improves the safety by controlling the access authority layer by layer.
Owner:TAIKANG LIFE INSURANCE CO LTD
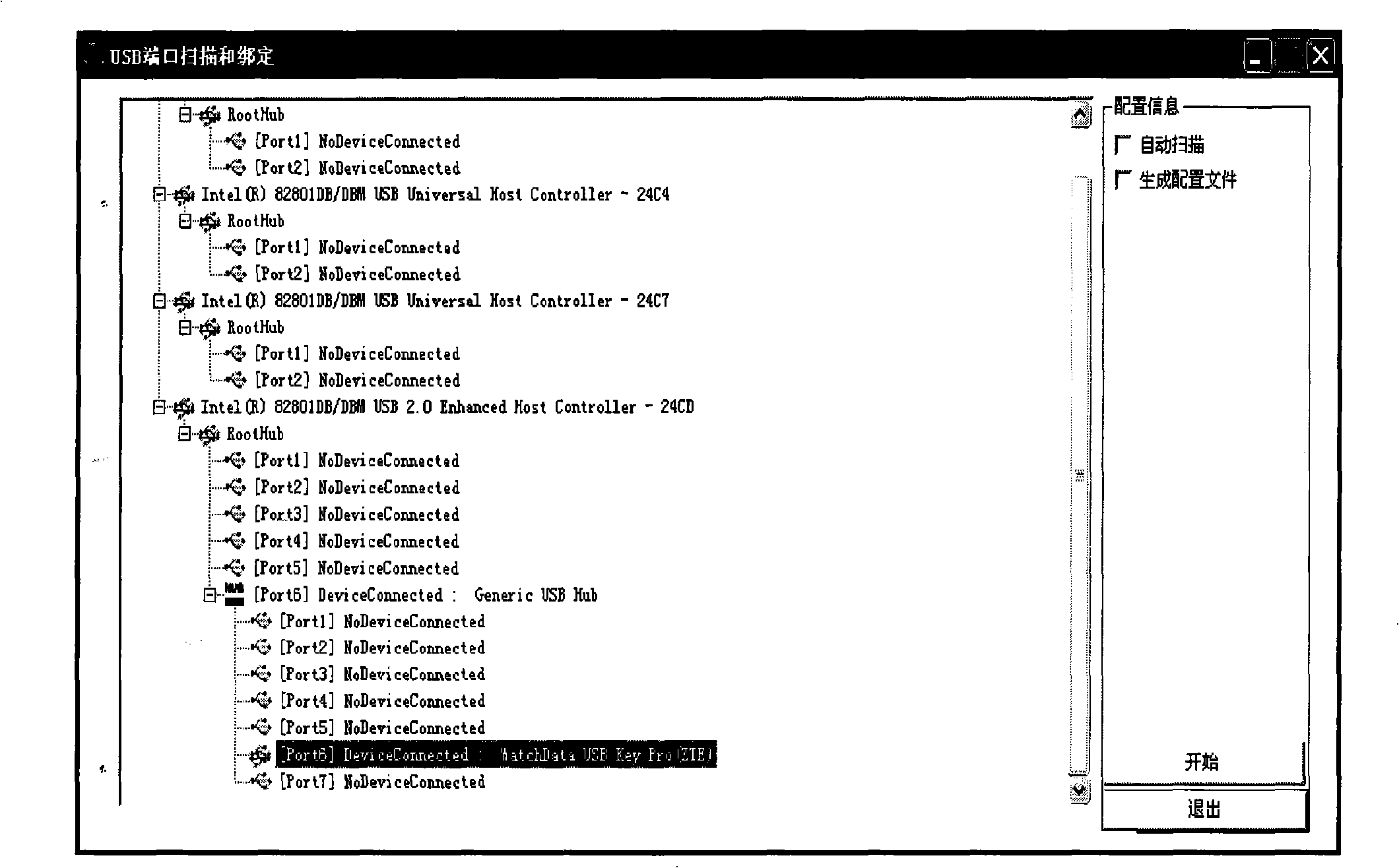
Method and apparatus for opening appoint terminal port USB equipment
InactiveCN101281474AAvoid writing messy issuesEnable secure accessProgram loading/initiatingUSBDevice name
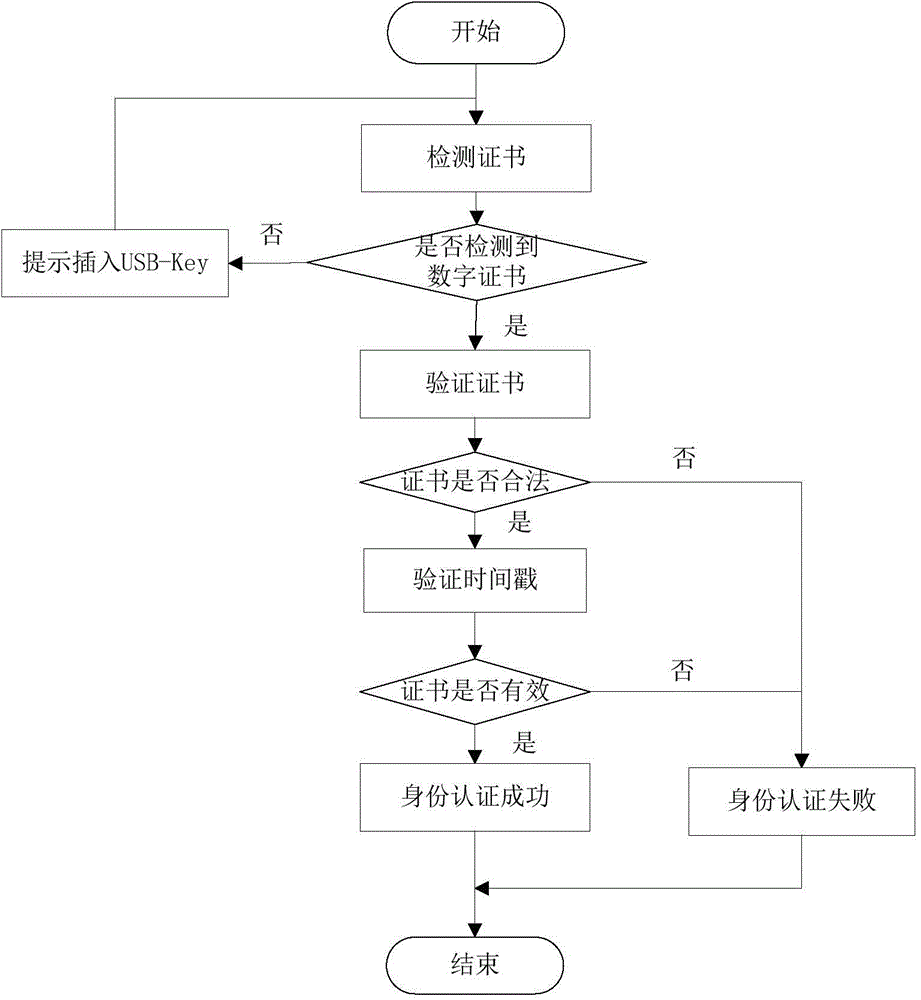
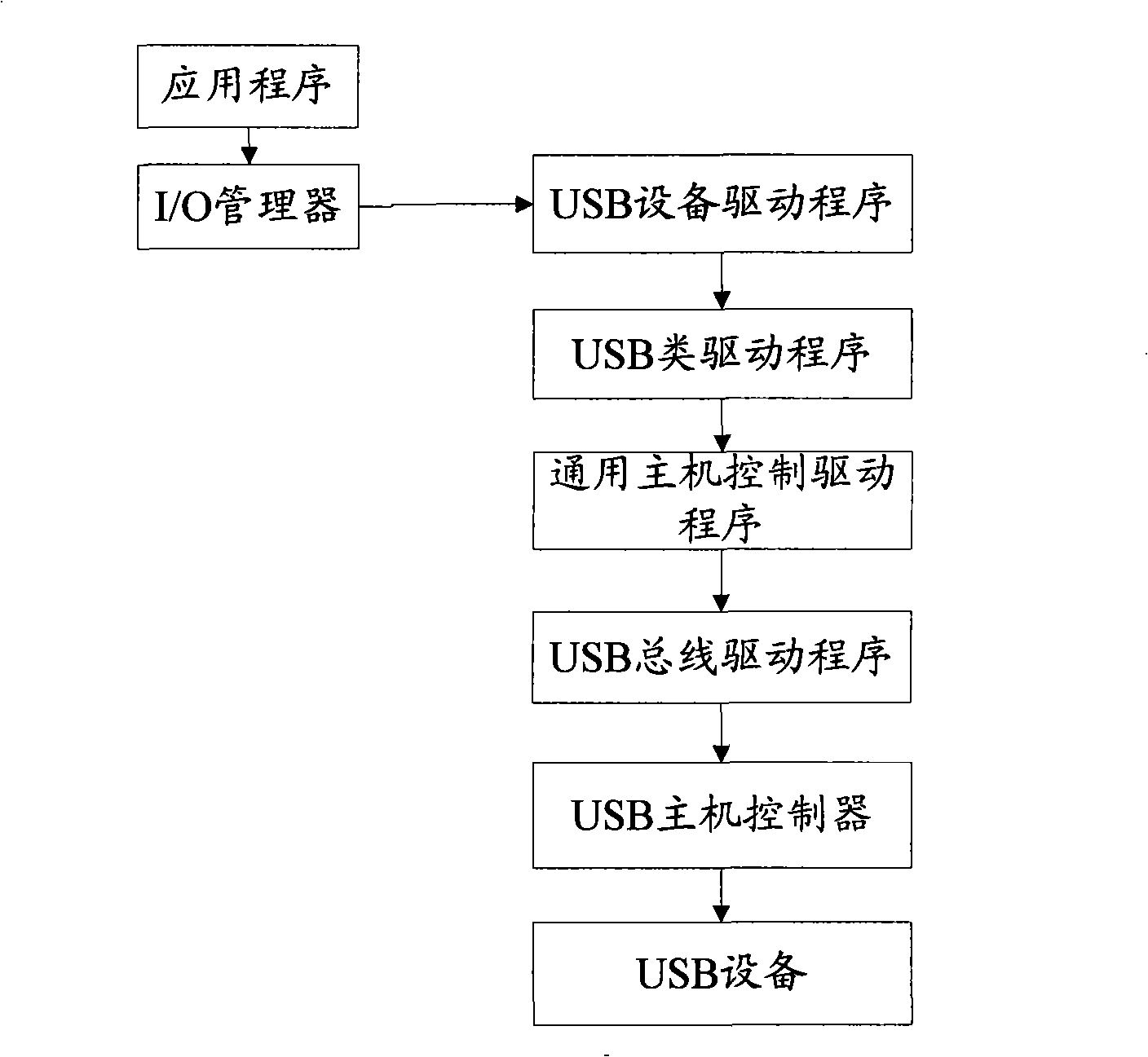
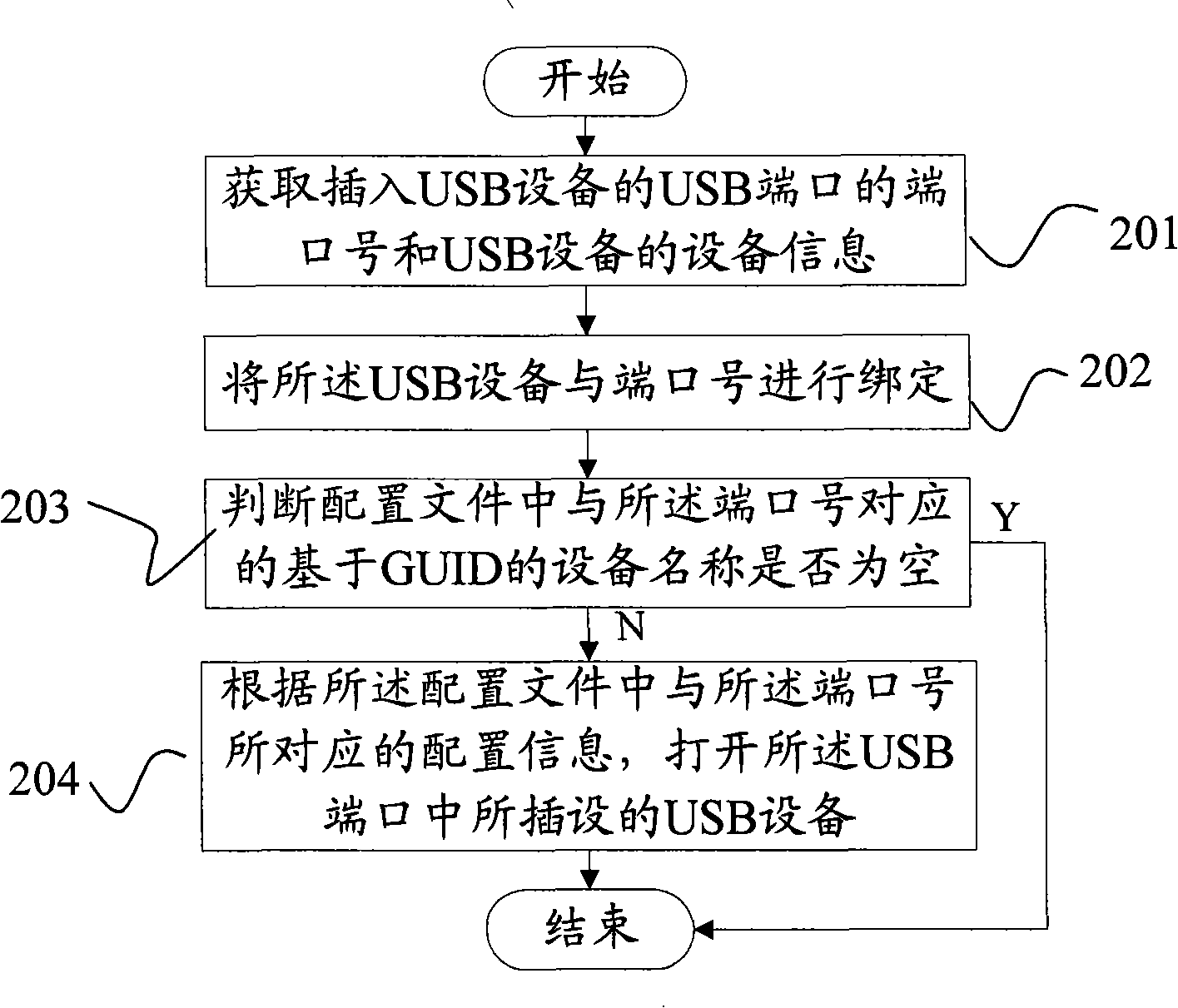
The invention discloses a method and an apparatus for opening a USB device corresponding to an appointed port, solves the problem of unfixed port number in the prior art, belonging to the technical field of USB device. The method for opening a USB device corresponding to an appointed port comprises: obtaining the port number of a USB device inserted into a USB port; judging whether a GUID-based device name corresponding to the port number in a configuration file is empty or not; and opening the inserted USB device according to the configuration information corresponding to the port number in the configuration file if the device name is not empty. The apparatus for a USB device corresponding to an appointed port includes a USB port unit, a scanning unit, a judging unit and an opening unit. According to the method and the apparatus for opening a USB device corresponding to an appointed port, a USB port and a USB device can be bound, the USB device corresponding to a USB port can be read and written, thus realizing the security access of the USB device corresponding the specific port.
Owner:BEIJING WATCH DATA SYST
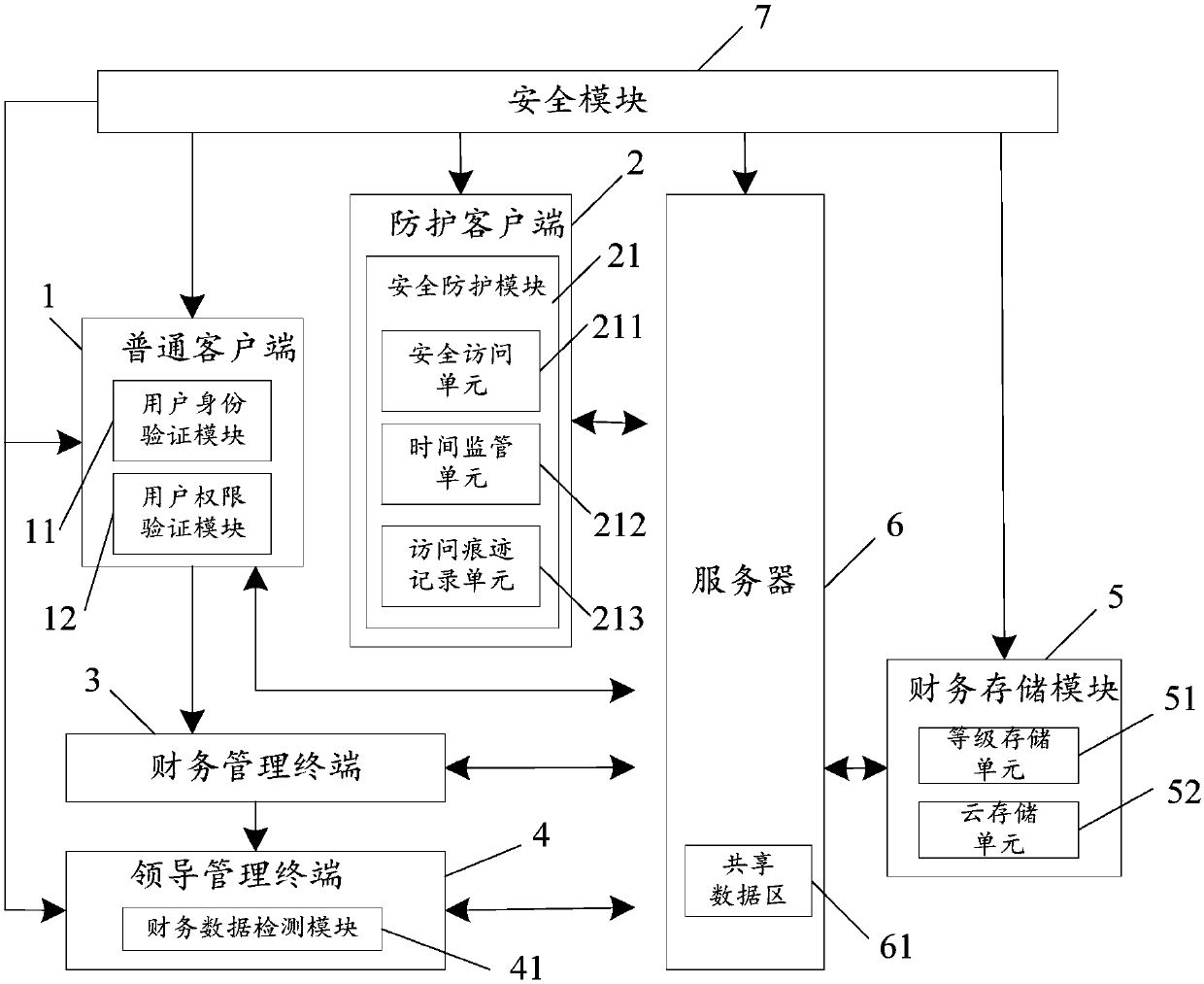
Enterprise finance management system with security protection
ActiveCN107770191ARealize security protectionEnable secure accessFinanceDigital data protectionComputer terminalUser authentication
The invention discloses an enterprise finance management system with security protection, and relates to the field of finance management. The system comprises multiple ordinary clients, a protection client, a finance management terminal, a leader management terminal, a finance storage module, a server and a security module. According to the enterprise finance management system, the security protection is performed on each of the terminals via the security module; the identity verification is performed on users of the ordinary clients via a user identity verification module and a user authorityverification module to implement security access to ordinary finance data; the security access is performed comprehensively on aspects such as a user identity, an access browse and an access historical trace of the protection client via a security access unit, a time supervision unit and an access trace recording unit; and well-organized security management of the finance data is implemented by setting a security level on the finance data, correspondingly storing to each level of storage units and selecting different work modes according to a level of an access authority; and thus the comprehensive security protection of the enterprise finance management system is implemented.
Owner:HEILONGJIANG UNIV OF TECH
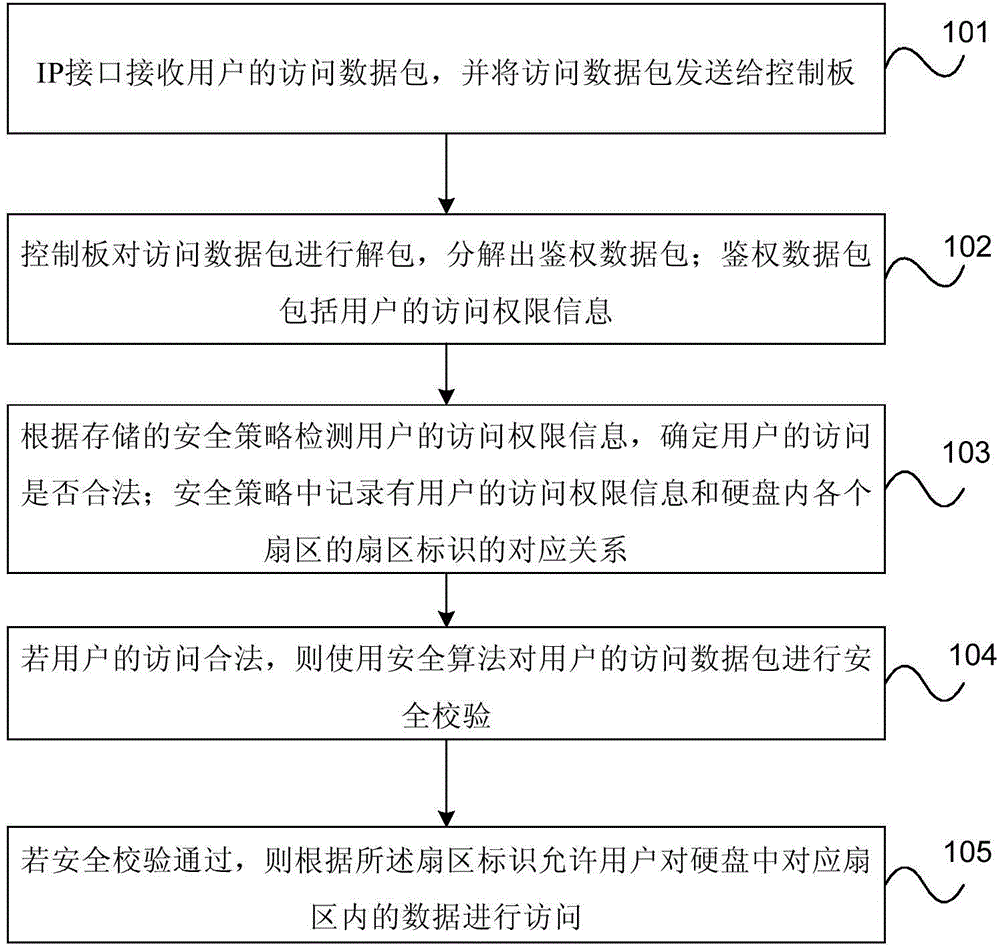
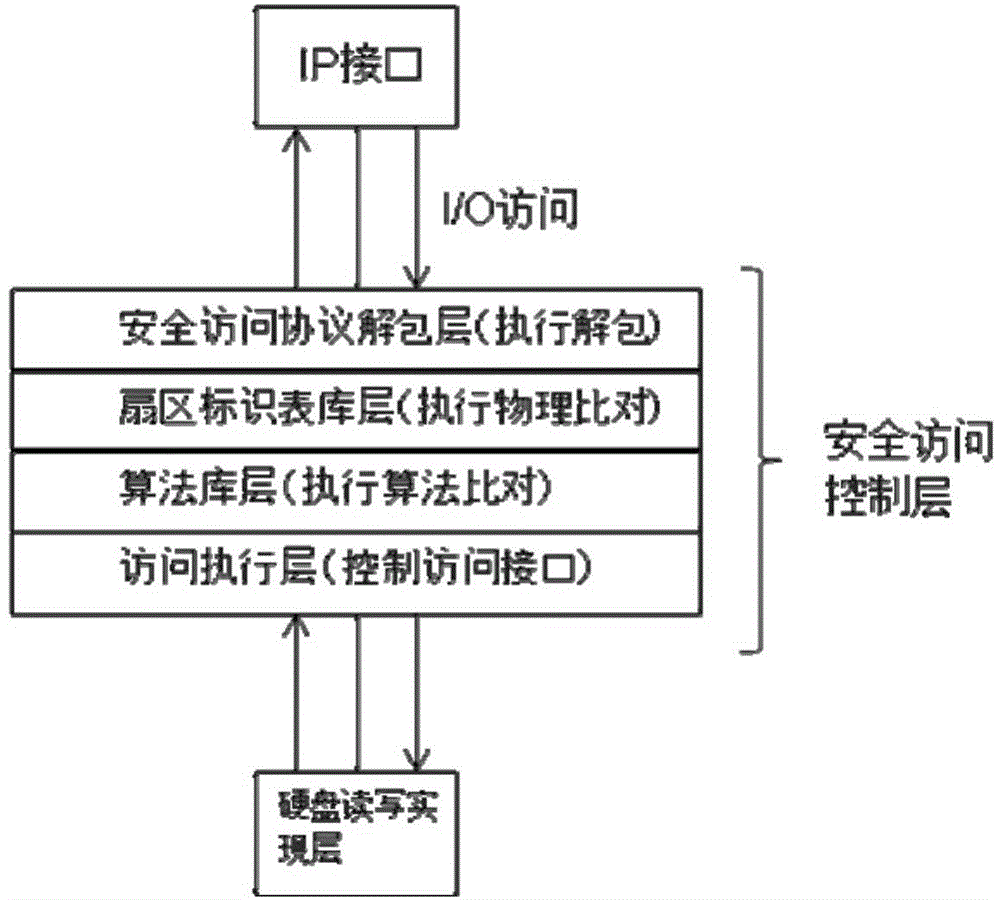
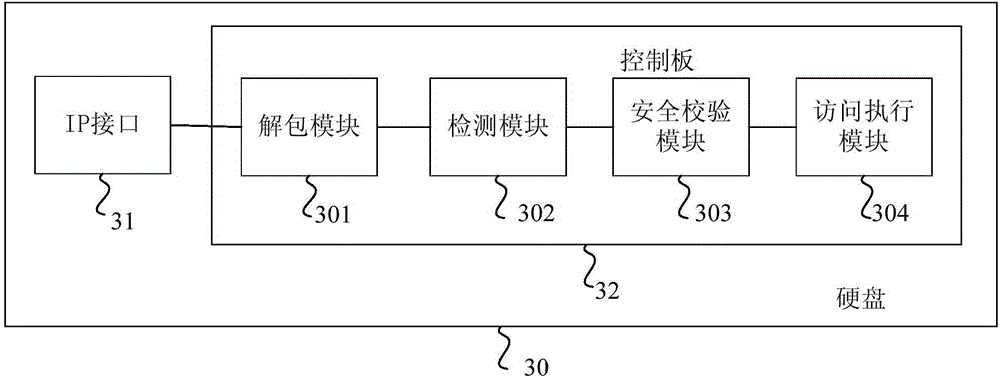
Hard-disk safety-access control method and hard disk
ActiveCN104063641AEnable secure accessAvoid security issuesMemory architecture accessing/allocationUnauthorized memory use protectionNetwork packetSecurity policy
The embodiment of the invention provides a hard-disk safety-access control method and a hard disk. According to the hard-disk safety-access control method, the hard disk comprises an IP (Internet Protocol) interface and a control panel, and the hard-disk safety-access control method comprises the following steps of receiving an access data packet of a user by the IP interface, and sending the access data packet to the control panel; unpacking the access data packet by the control panel to resolve an authentication data packet, wherein the authentication data packet comprises the access authority information of the user; detecting the access authority information of the user according to a stored safety strategy, and determining whether the access of the user is legal or not, wherein the corresponding relation of the access authority information of the user and the sector mark of each sector in the hard disk is recorded in the safety strategy; if the access of the user is legal, then carrying out safety verification on the access data packet of the user by using a safety algorithm; if the access data packet of the user passes the safety verification, then allowing the user to access the data in the corresponding sector in the hard disk according to the sector mark. The access safety for the hard disk is improved by the embodiment of the invention.
Owner:HUAWEI TECH CO LTD
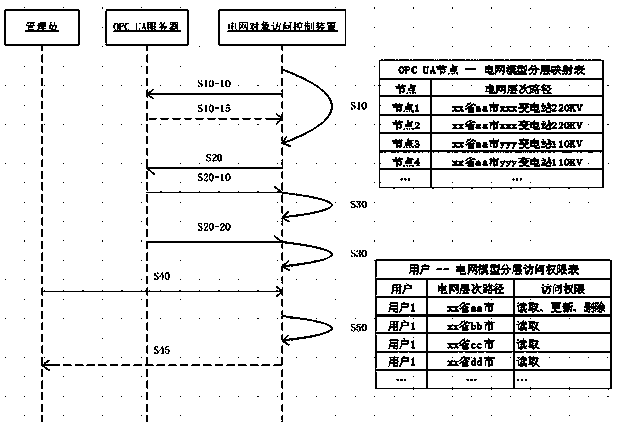
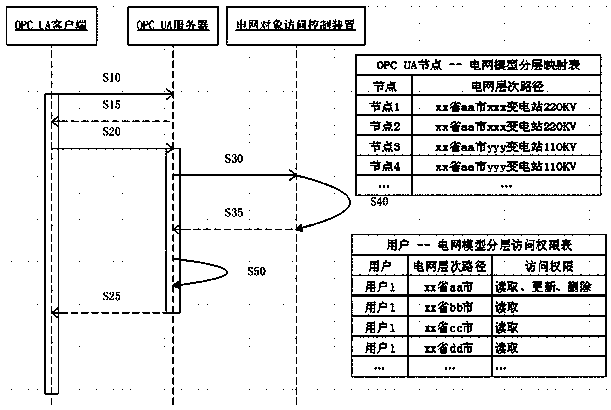
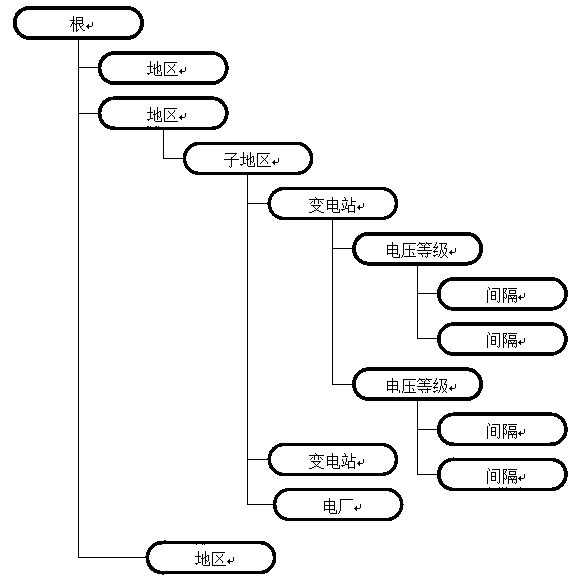
Power grid object access control device capable of realizing safety configuration and access of power grid model data
ActiveCN104168268AOperational data access is fine-grainedFlexible and efficient security management and controlCircuit arrangementsTransmissionPower stationMeasurement device
The invention aims at providing a power grid object access control device capable of realizing safety configuration and access of power grid model data. The device is characterized by including a layered division and security permission configuration module of the power grid model data and an access security control module; the layered division and security permission configuration module realizes layered division and security permission configuration of the power grid model data; and the access security control module realizes access security control of a power grid model. Through hierarchical organization of the power grid model according to region, sub regions, power stations and voltage levels, classification of other power grid objects such as devices, terminals and measurement devices and the like into corresponding hierarchies according to incidence relations, and combination of access permissions of system access users for the data and the hierarchical result, the device realizes access security control which is appropriate in granularity and enables security access of operation data of the whole power grid to be corresponding to a management system which is currently in effect.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
Encryption and authentication protection method and system of secondary development embedded type application program
ActiveCN102831357AImprove securityEnable secure accessUser identity/authority verificationComputer security arrangementsComputer moduleApplication software
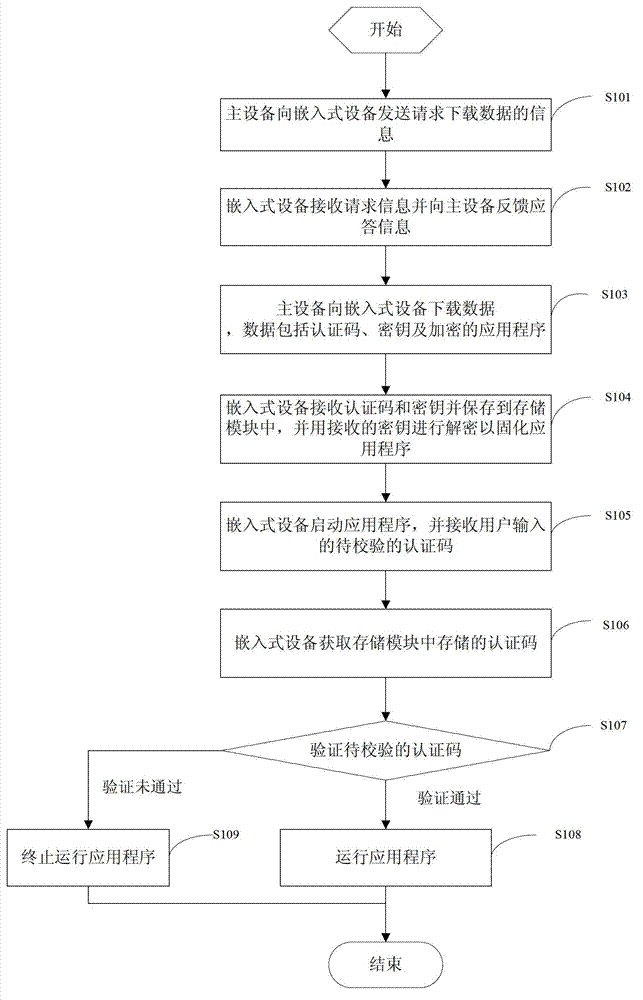
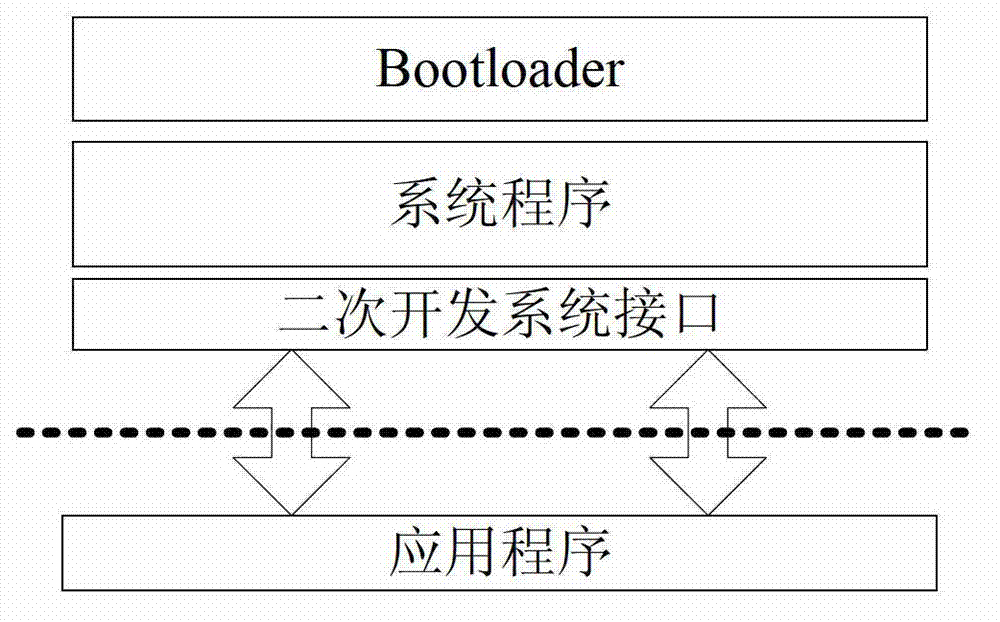
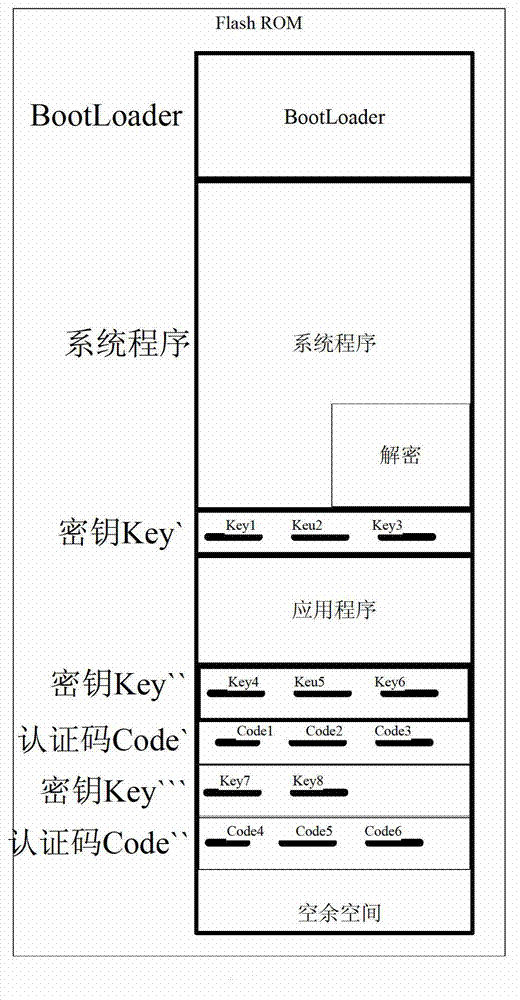
The invention provides an encryption and authentication protection method and system of a secondary development embedded type application program. The encryption and authentication protection method comprises the steps that: primary equipment requests for information of downloading data to the embedded equipment; embedded equipment receives the request information and feeds back response information to the embedded equipment; the primary equipment downloads data from the embedded equipment, wherein the data comprises an authentication code, a key and an encrypted application program; the embedded equipment receives and stores the requested data to a storage module and decrypt by using the received key to solidify the application program; the embedded equipment starts up the application program and receives a to-be-verified authentication code input by the user; the embedded equipment obtains the authentication code stored in the storage module and verifies the to-be-verified authentication code; and if the verification passes, the embedded equipment runs the application program, otherwise, ends running the application program. According to the invention, safety of the secondary development software of the embedded equipment can be improved without adding extra hardware.
Owner:深圳市君安宏图技术有限公司
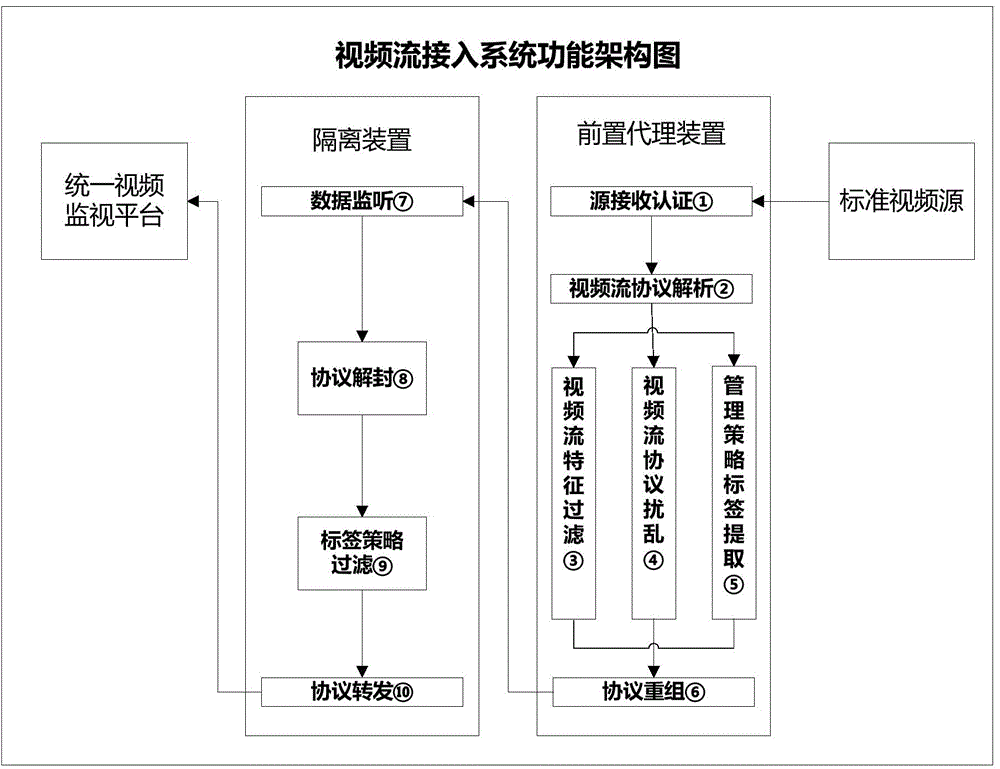
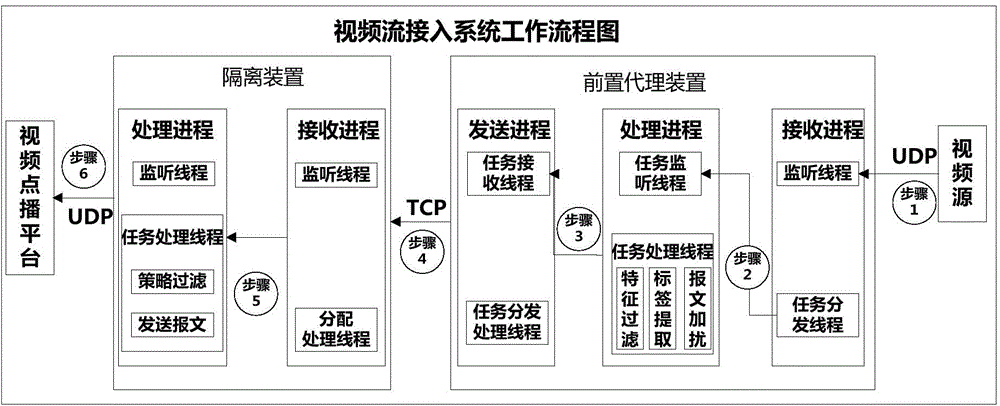
Video security access system based on agency and isolation and method of video security access system
InactiveCN104378657AImprove security levelTo achieve the purpose of data scramblingSelective content distributionComputer hardwareMetadata
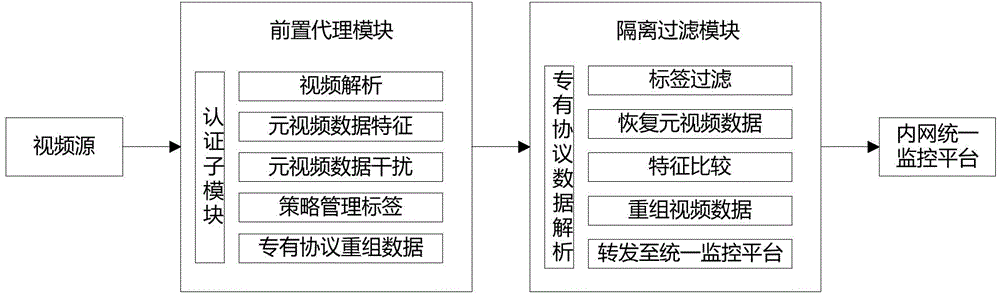
The invention relates to a video security access system based on agency and isolation and a method of the video security access system. The video security access system comprises a front agency module, a special communication protocol and an isolation filtering module, wherein a video source safely has access to an internal network unified monitoring platform through the front agency module, the special communication protocol and the isolation filtering module. The method includes the steps that firstly, the front agency module authenticates the video source which has access to the internal network unified monitoring platform; secondly, video data have access to the front agency module, and the video protocol is analyzed; thirdly, characteristic filtering, scrambling and strategy labor adding are conducted on the video data; fourthly, the video data are recombined through the special communication protocol and sent to the isolation filtering module; fifthly, the isolation filtering module receives the video data, packaged through the special protocol, sent by the front agency module; sixthly, the isolation filtering module analyzes labels and conducts filtering; seventhly, video metadata are recovered; eighthly, the video format packaging is conducted on the video metadata, and the video metadata are sent to the internal network unified monitoring platform.
Owner:STATE GRID CORP OF CHINA +2
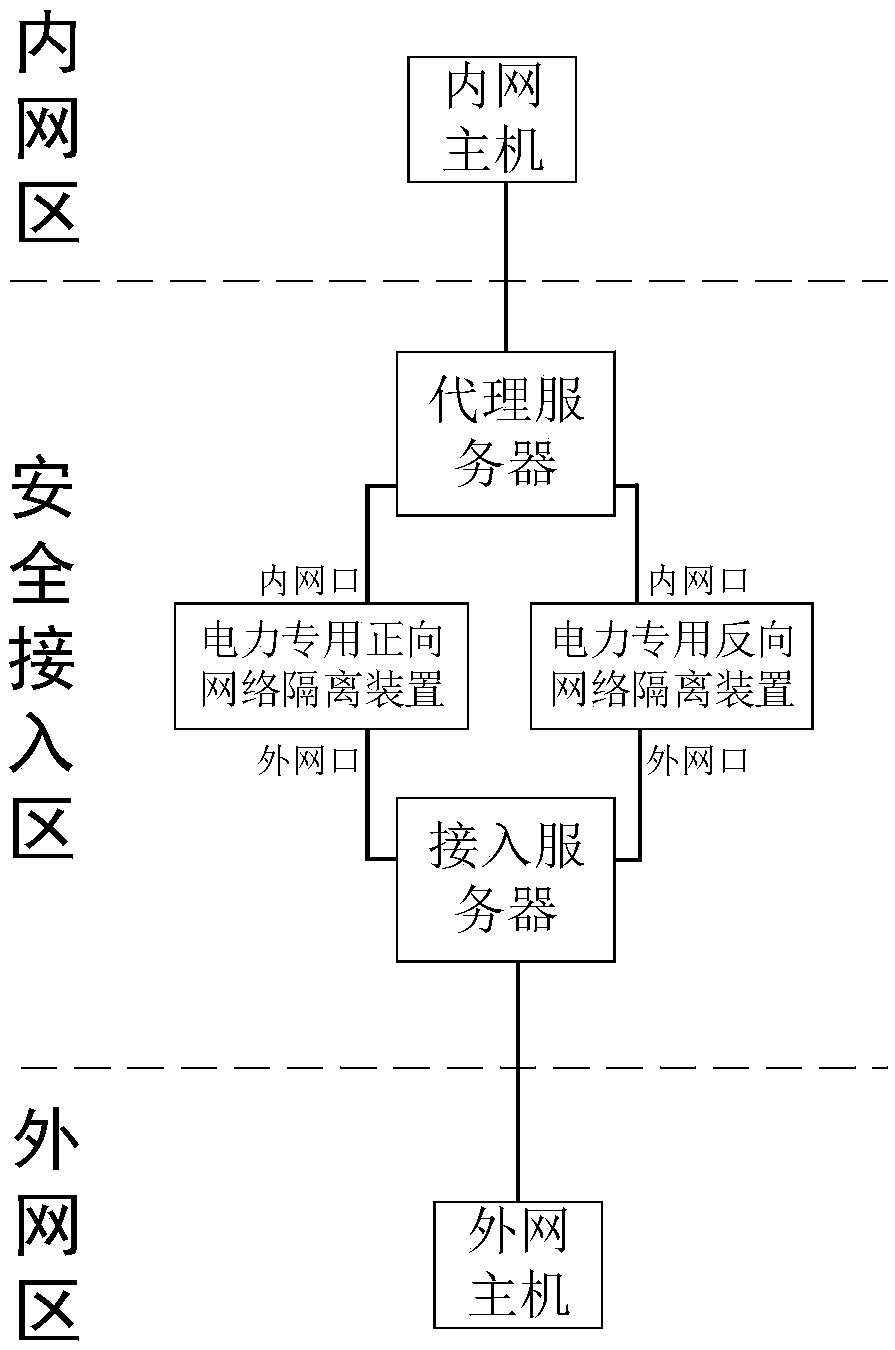
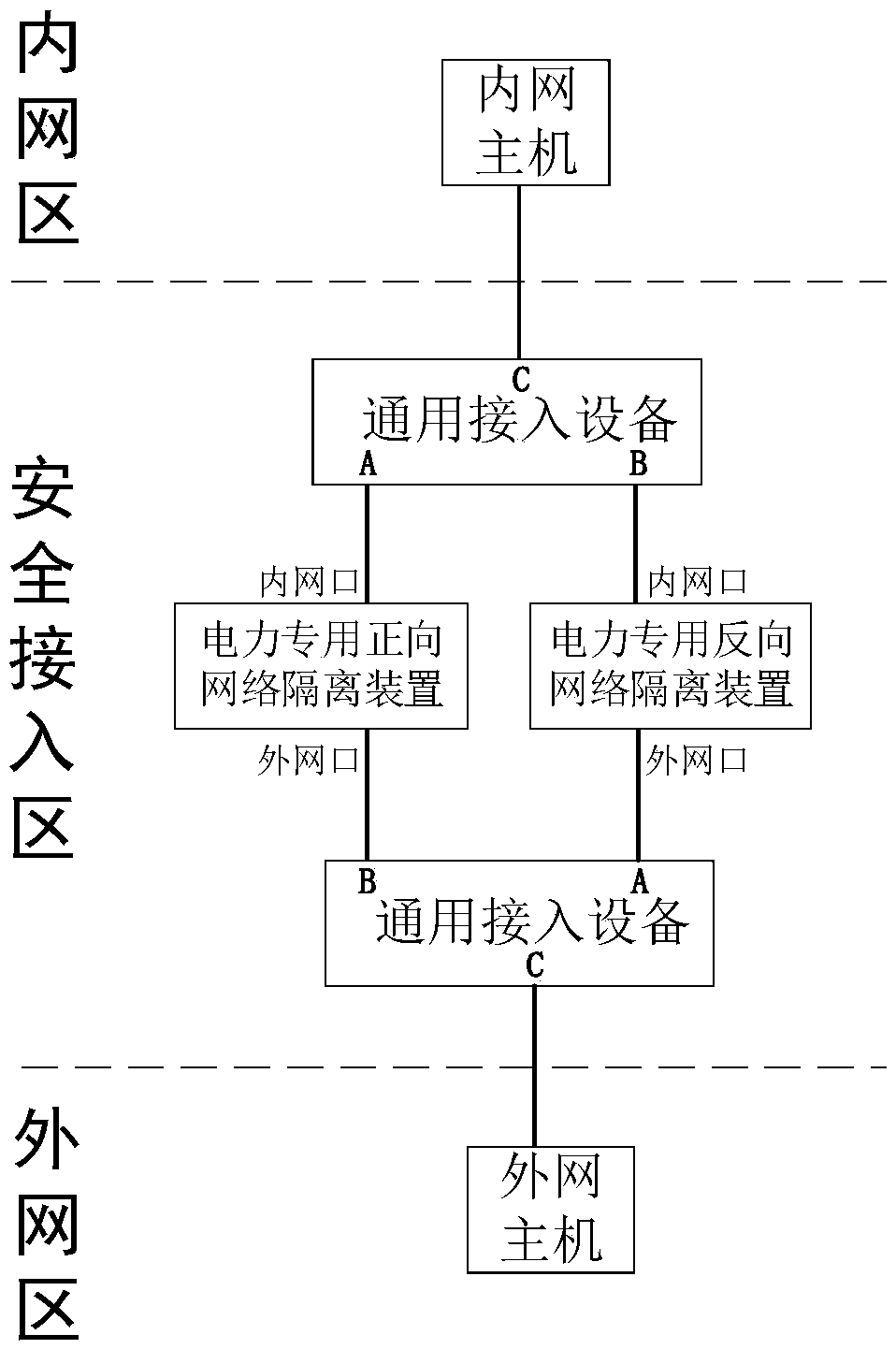
Universal network safe access area system applicable to electric power private network and message processing method
InactiveCN108810011ASimple designSimplify operation and maintenance workNetworks interconnectionAccess methodPrivate network
The present invention discloses a universal network safe access area system applicable to an electric power private network and a message processing method. The safe access area system includes two identical universal access devices, a forward network isolating device for electric power and a reverse network isolating device for electric power. The universal access devices are used as message agents of an internal network area host and an external network area host to convert an original message into a message that can pass through the forward network isolating device for electric power and the reverse network isolating device for electric power, thus realizing non-inductive access to the internal network area host and the external network area host. The forward / reverse network isolating devices for electric power are used as physical isolation and protocol conversion. The present invention has the advantages that the system structure is simple, the original access method is not affected, the access difficulty is reduced, the universal access devices are free of configuration, the risk of network failure is lowered, and it is convenient to operate and maintain, thus providing protection for safe access of the internal network area when longitudinal connection of an internal network area and an external network area is required.
Owner:NR ELECTRIC CO LTD +1
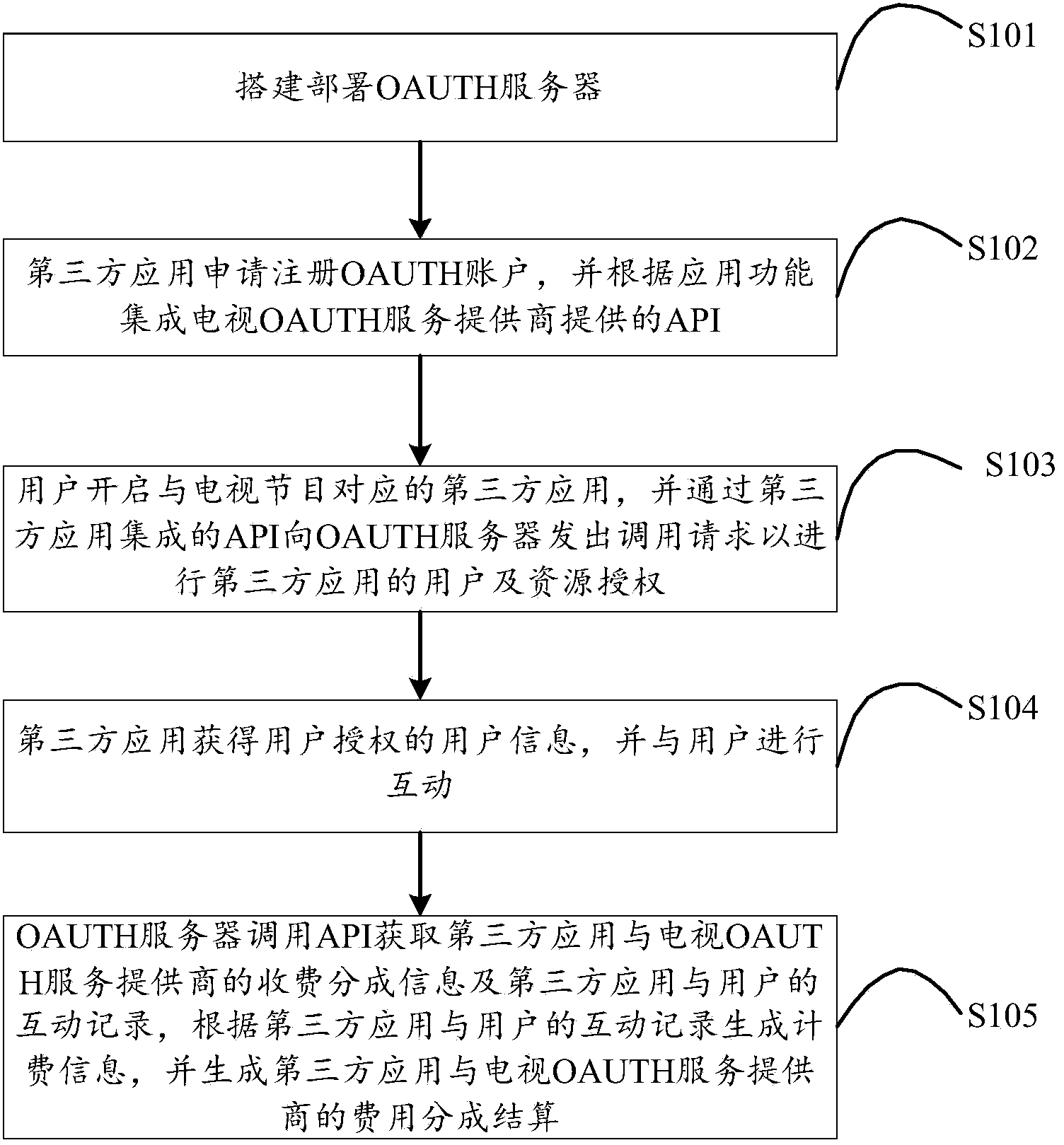
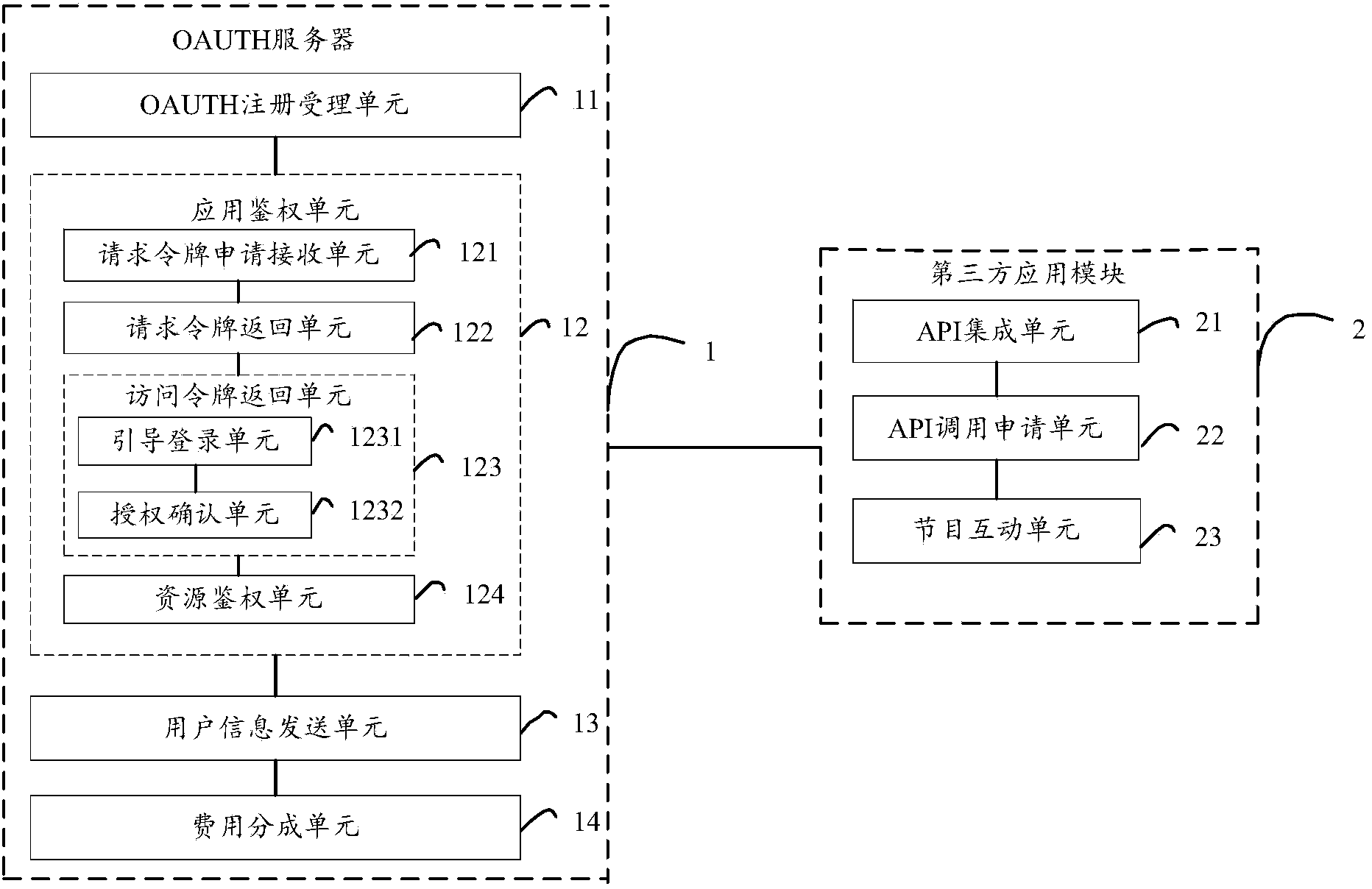
Value-added service integration method and system for network television user
InactiveCN103441857AAchieve integrationEnable secure accessUser identity/authority verificationDigital data authenticationSoftware engineeringTelevision equipment
The invention is suitable for multimedia application field and provides a value-added service integration method for a network television user. The method comprises the following steps of: setting up and deploying an OAUTH (Open the Authentication) server; applying for registering an OAUTH account by a third-party application, and integrating an API (Application Program Interface) provided by a television OAUTH service provider according to the application function; opening the third-party application corresponding to television programs by a user, issuing a calling request to the OAUTH server by the API integrated by the third-party application to carry out user and resource authorization to the third-party application; and obtaining the user information authorized by the user and carrying out interaction with the user by the third-party application. According to the method, the integration of the third-party application and the television value added service is realized, the API calling inside television equipment is opened, and on the premise that the television provides the base core function API, the third-party application can be self-integrated and the peripheral service can be expanded. The safety access to the television resources is effectively realized through the operation authorization realized by an OAUTH protocol, and the rapidity and the safety for API calling and the resource access are ensured.
Owner:TCL CORPORATION
Method and equipment for implementing safety access
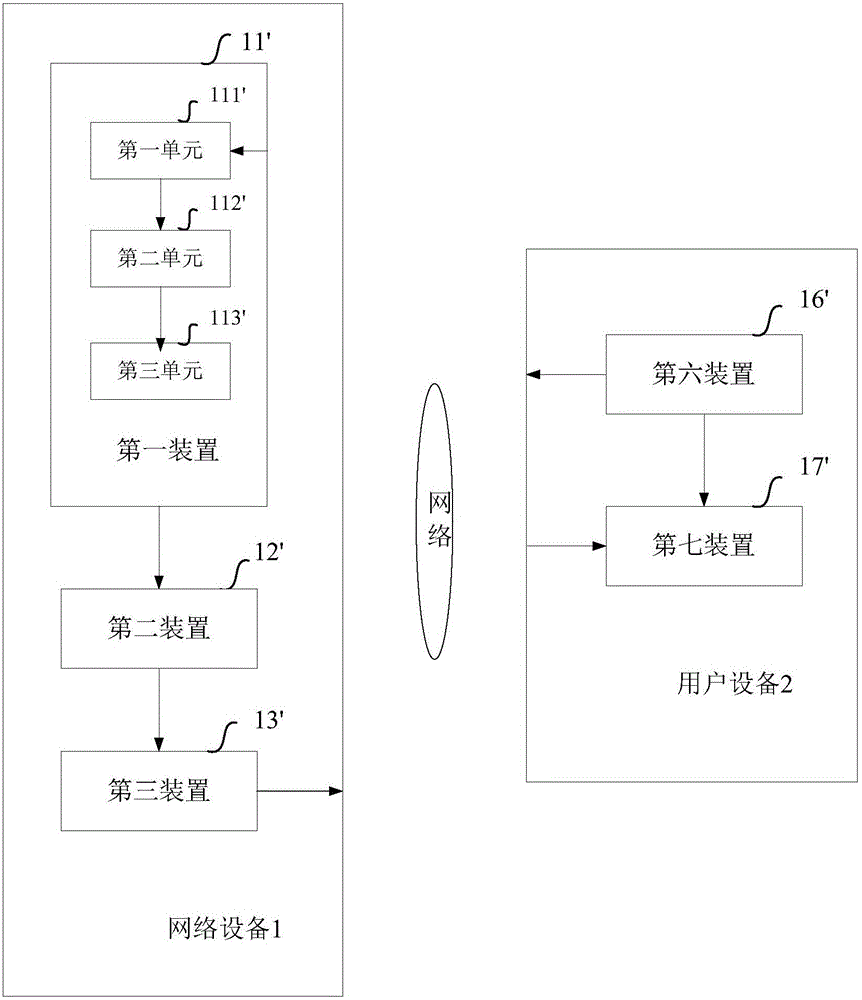
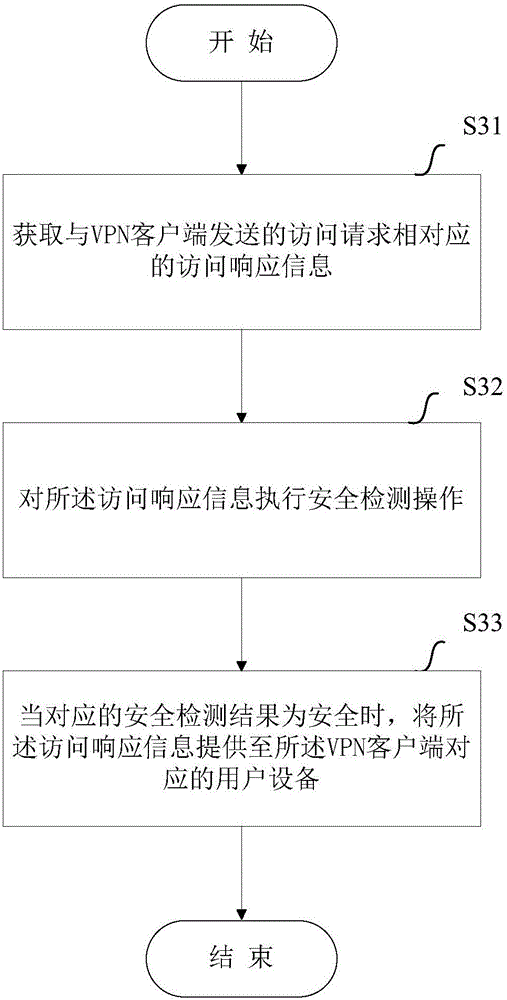
ActiveCN106101075AReduce security risksAvoid constraintsData switching networksPrivate networkClient-side
The application aims to provide a method and equipment for implementing safety access. The method comprises the steps of: acquiring access response information corresponding to an access request sent by a VPN (Virtual Private Network) client; executing a safety detection operation on the access response information; and when a corresponding safety detection result is that the access response information is safe, providing the access response information to user equipment corresponding to the VPN client. Compared with the prior art, according to the method and equipment provided by the application, the acquired access response information corresponding to the access request sent by the VPN client of the user equipment is subjected to the safety detection operation by network equipment, and the access response information, of which the safety detection result is that the access response information is safe, is sent to the user equipment, thereby avoiding direct acquisition of the user equipment on network transmission data which is not subjected to safety detection, effectively implementing interception on access response information with the safety problem and preventing the potential safety hazard brought to the user equipment by the access response information.
Owner:SHANGHAI LIANSHANG NETWORK TECHNOLOGY CO LTD
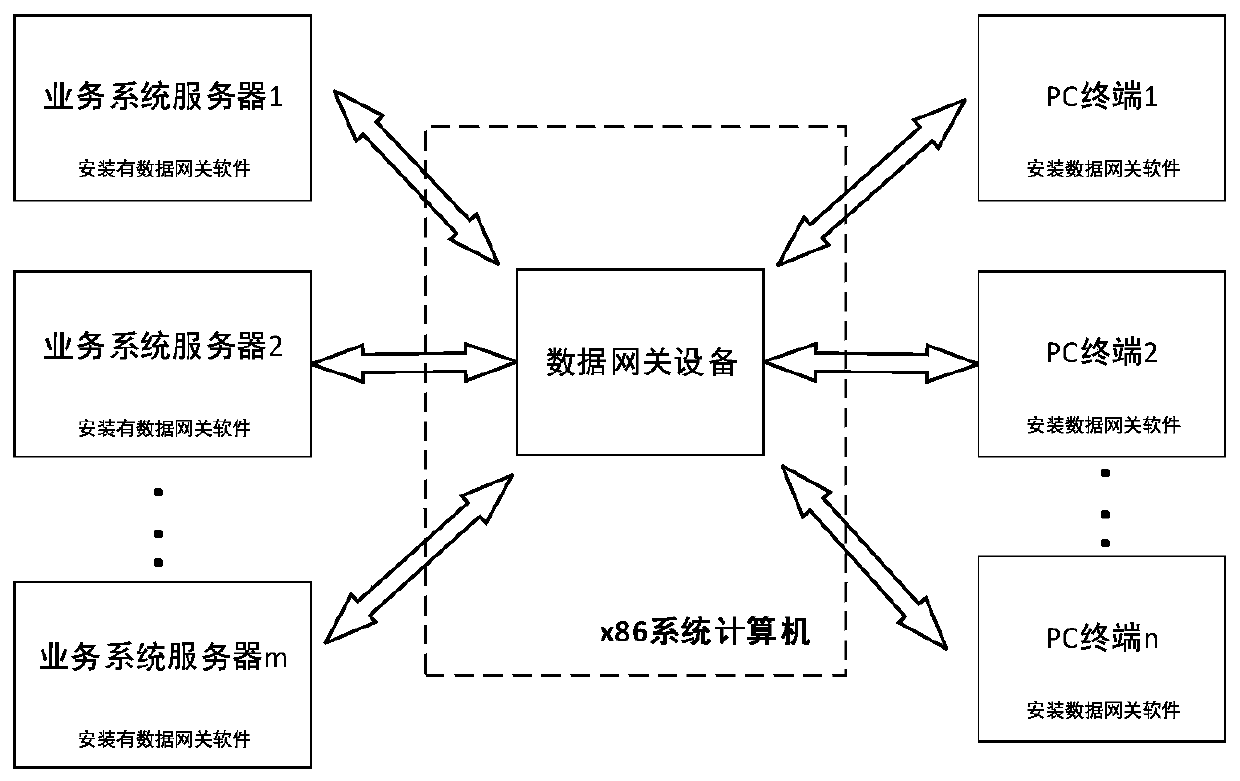
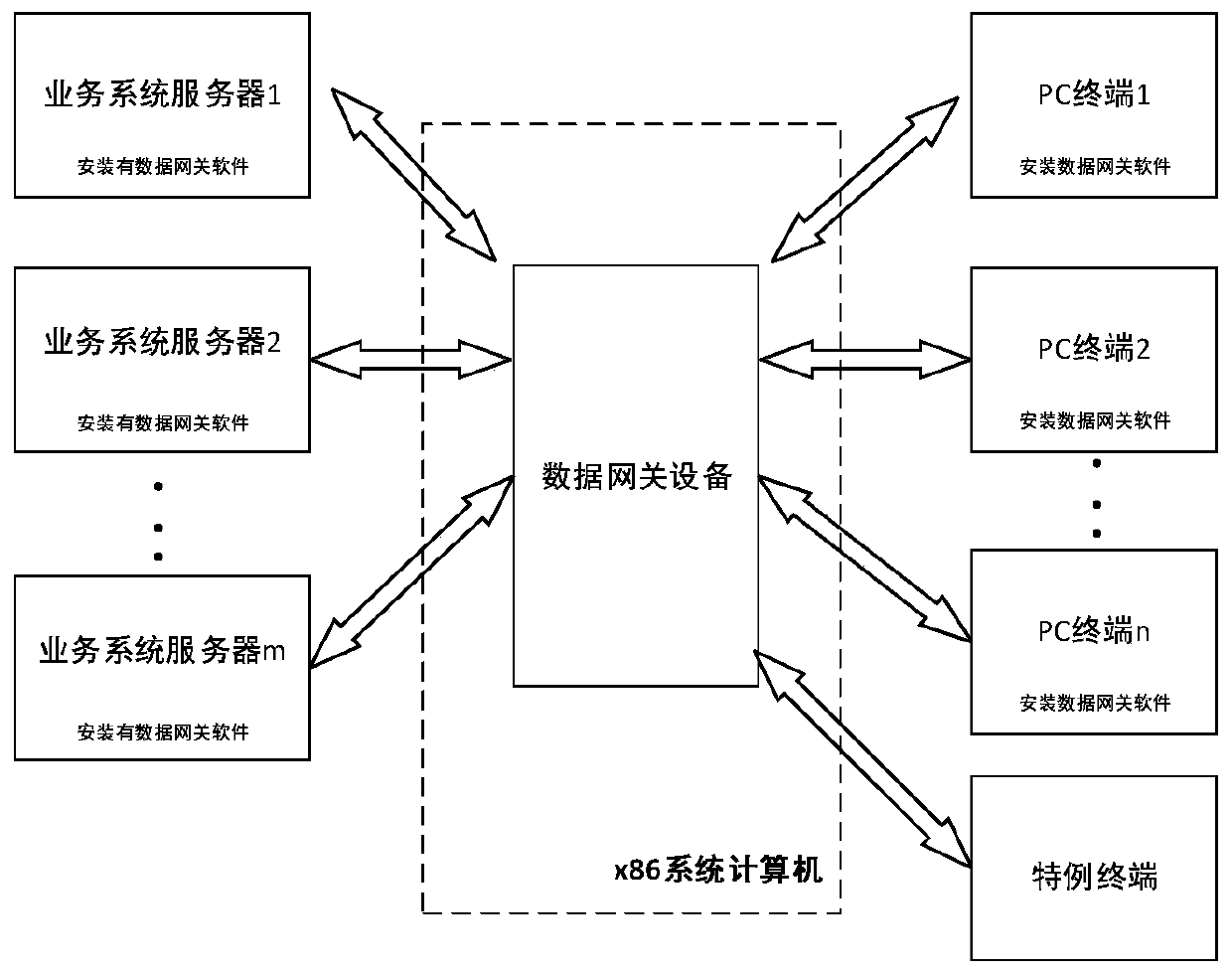
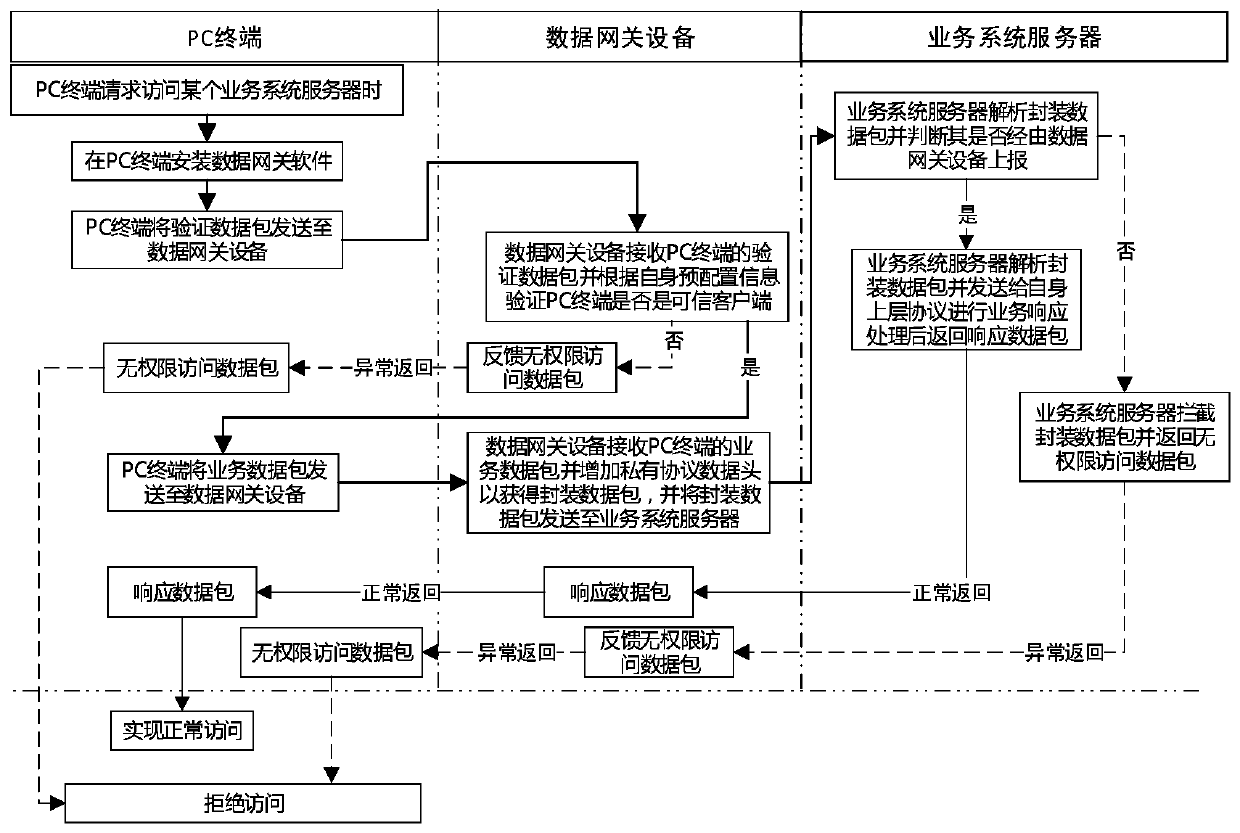
Data security transmission system and method based on data gateway
The invention relates to a data security transmission system based on a data gateway. The system comprises a plurality of PC terminals and a plurality of service system servers, wherein the PC terminals and the service system servers perform bidirectional data transmission through data gateway equipment. Data gateway software is installed in each service system server. Before a PC terminal accesses the service system server, data gateway software needs to be installed in the PC terminal; the data gateway equipment performs trust judgment on the PC terminal, adds a private protocol data head toa service data packet received from the PC terminal and transmits the service data packet to a service system server when the service data packet is confirmed to be a trusted terminal; the service system server analyzes and judges whether the data packet is reported by the data gateway equipment or not, and if not, the service system server intercepts the data packet and returns an unauthorized access data packet; and if yes, the service system server analyzes the data packet, performs service response processing and then returns a response data packet, so that the method is safe and efficient. The invention also relates to a data security transmission method based on the data gateway.
Owner:北京泰立鑫科技有限公司
Method for managing network elements by network management system
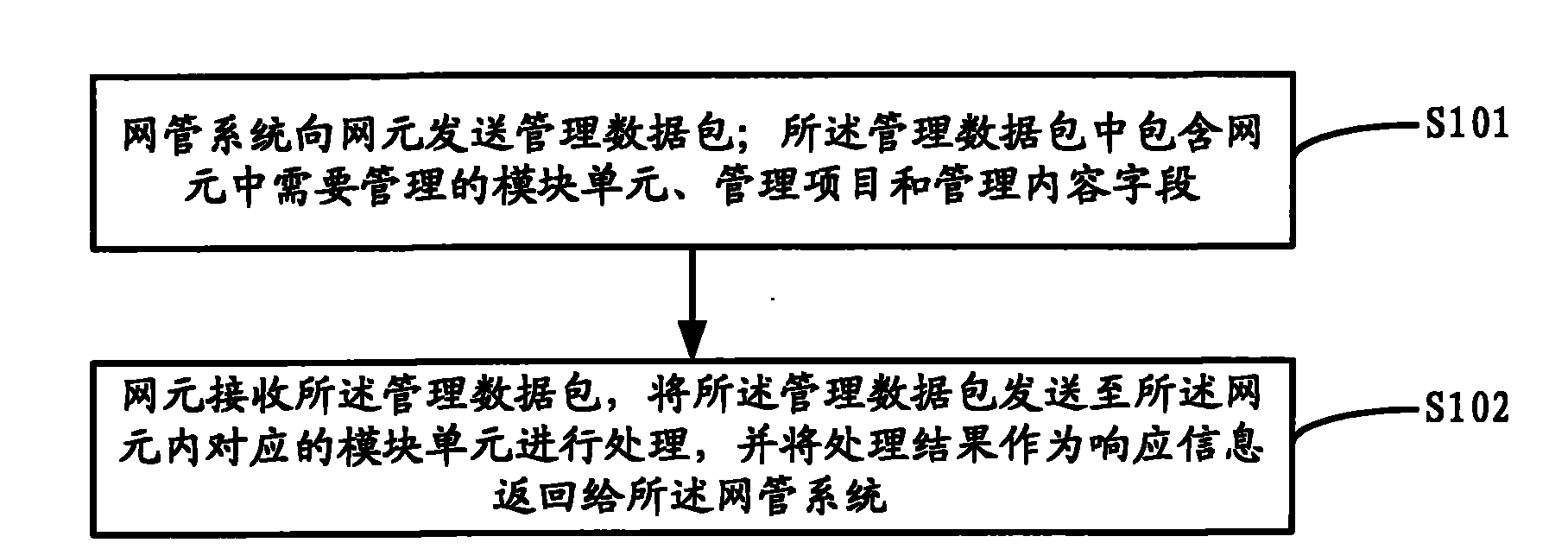
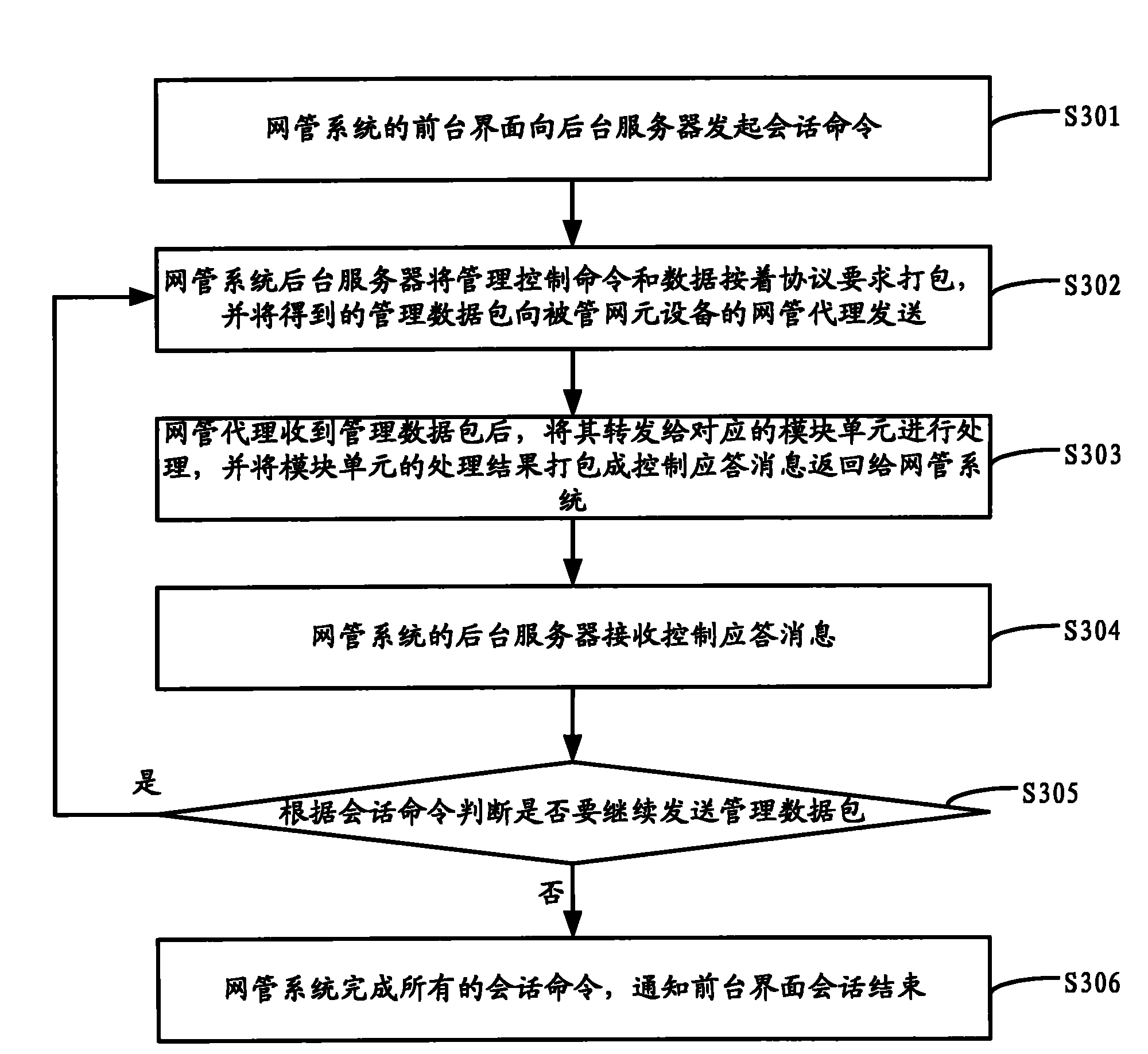
InactiveCN102014004AImprove operational efficiencyEnable secure accessData switching networksNetwork elementReal-time computing
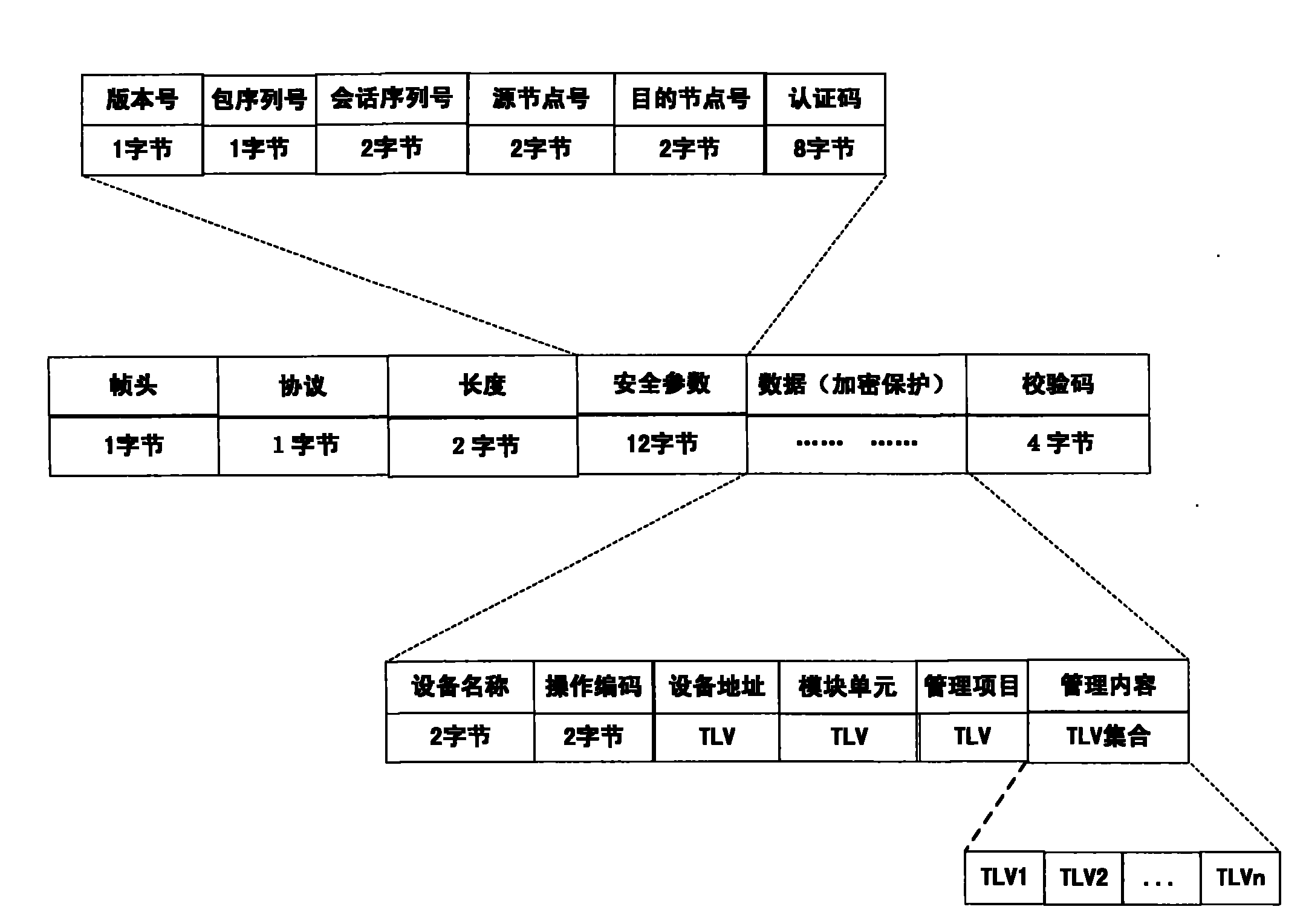
The invention discloses a method for managing network elements by a network management system. The method comprises the following steps: the network management system sends a management data packet to the network elements, wherein, the management data packet contains module units, management items and management content fields which need to be managed in the network elements; and the network elements receive and send the management data packet to the corresponding module units in the network elements for processing, and take the processing results as response information to return to the network management system. By adopting the method, the data packet format defined by an SNMP (simple network management protocol) is extended; and by adding information of the network elements such as the module units, the management items, the management content and the like to the data fields, when the network management system allocates the network elements, a plurality of interactive processes between the network management system and the managed network element equipment are effectively simplified, the communication traffic between the network management system and the managed network element equipment is reduced, and the operating efficiency for network management is improved when the network management system carries out network element configuration.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Network terminal audio internal and external intercommunication system and method
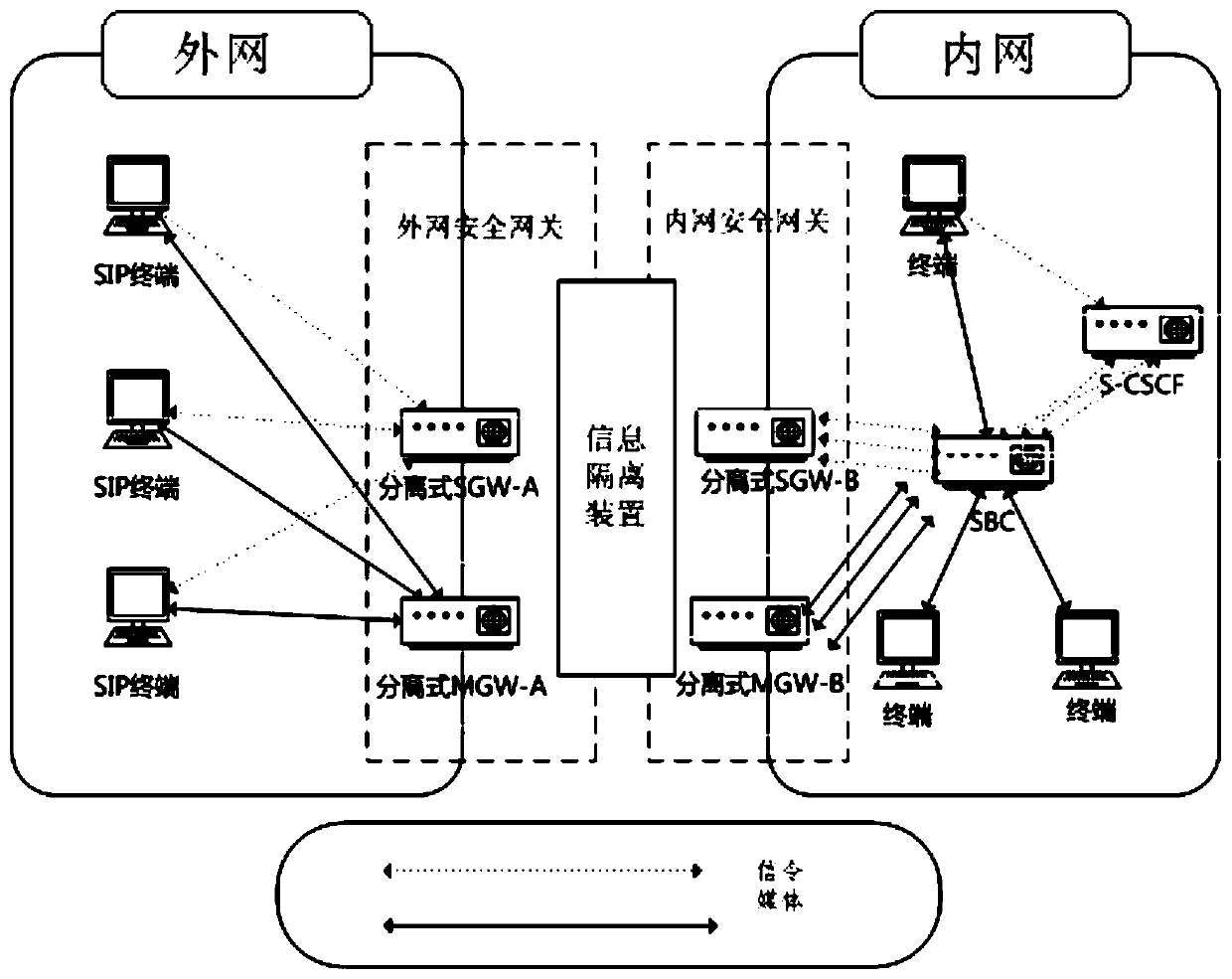
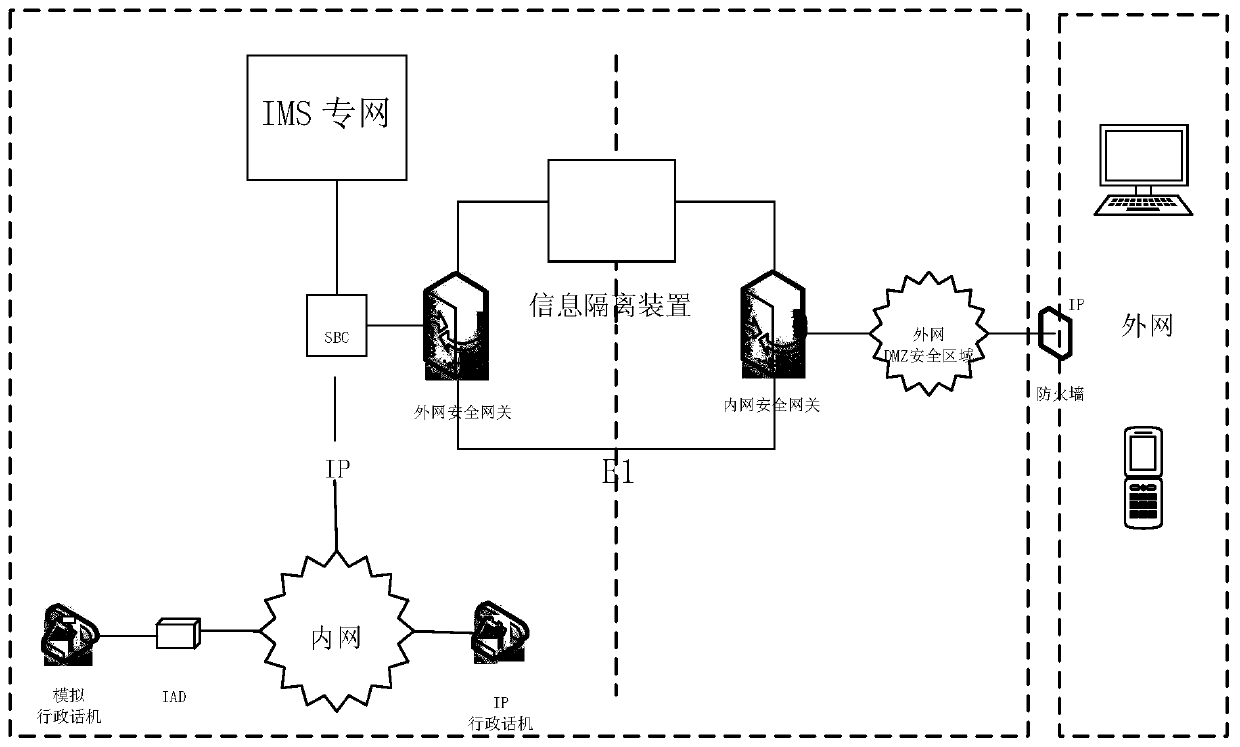
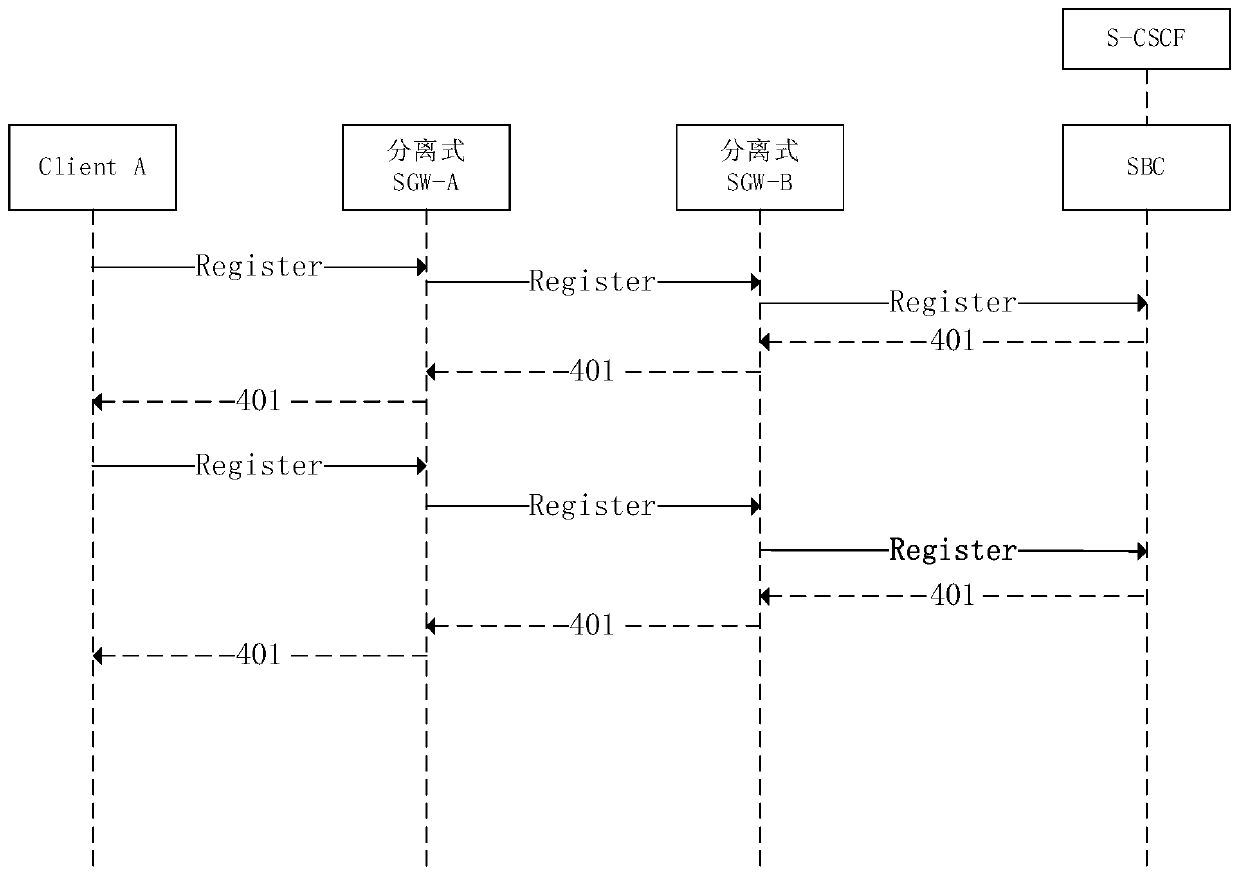
The invention discloses a network terminal audio internal and external network intercommunication system and method. The network terminal audio internal and external network intercommunication systemcomprises an internal and external security gateway, wherein the internal and external network security gateway is composed of an internal and external network separated signaling gateway SGW and an internal and external network separated media gateway MGW; the SGW is divided into an external network signaling gateway SGW-A and an internal network signaling gateway SGW-B; the MGWs are respectivelydeployed in an external network and an internal network; the SGW-A and the SGW-B cooperate to realize SIP signaling interaction; the MGWs are divided into an external network media gateway MGW-A andan MGW-B internal network media gateway which are respectively deployed in the external network and the internal network; and the MGW-A and the MGW-B realize real-time media stream intercommunicationthrough an E1 board card. According to the network terminal audio internal and external network intercommunication system, the external security gateway and the internal security gateway are deployedin the information intranet and the information extranet, and the innovative application of the information security isolation device is matched, so that the security access of the existing network signaling stream and media stream of the mobile internet terminal society is realized.
Owner:NARI INFORMATION & COMM TECH +1
Access request processing method, container cloud platform, electronic equipment and storage medium
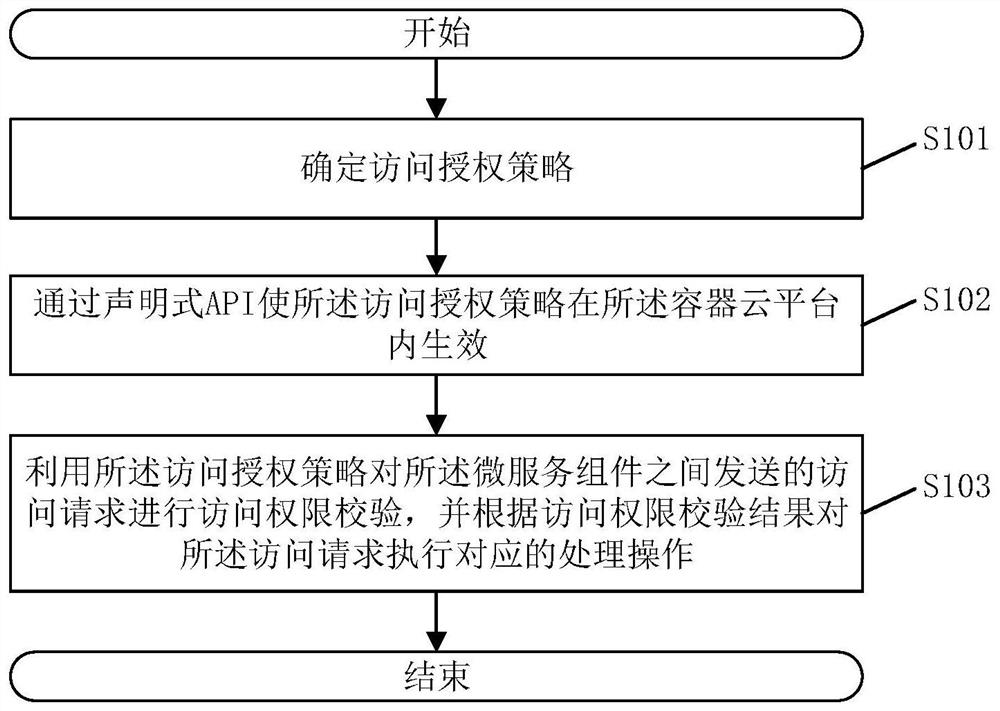
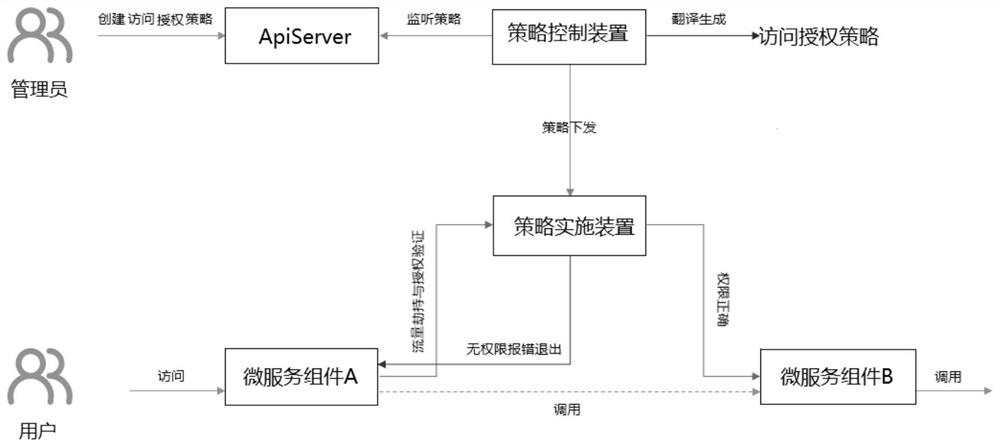
PendingCN113672901AImprove securityEnable secure accessDigital data protectionDigital data authenticationEngineeringService component
The invention discloses an access request processing method, which is applied to a container cloud platform and comprises the following steps: determining an access authorization strategy, wherein the access authorization strategy is a code for configuring access authority between micro-service components, and the micro-service components run on the container cloud platform; enabling the access authorization strategy to take effect in the container cloud platform through a declarative API; and performing access permission verification on an access request sent between the micro-service components by using the access authorization strategy, and executing a corresponding processing operation on the access request according to an access permission verification result. According to the invention, non-invasive micro-service secure access can be realized, and the security of the container cloud platform is improved. The invention further discloses a container cloud platform, electronic equipment and a storage medium, which have the above beneficial effects.
Owner:济南浪潮数据技术有限公司
Information security access architecture, method and system
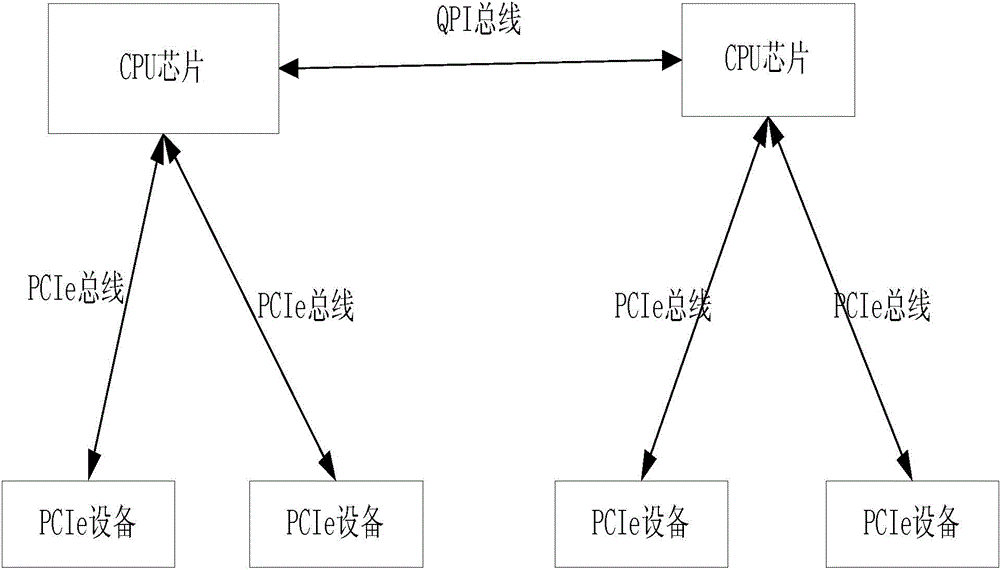
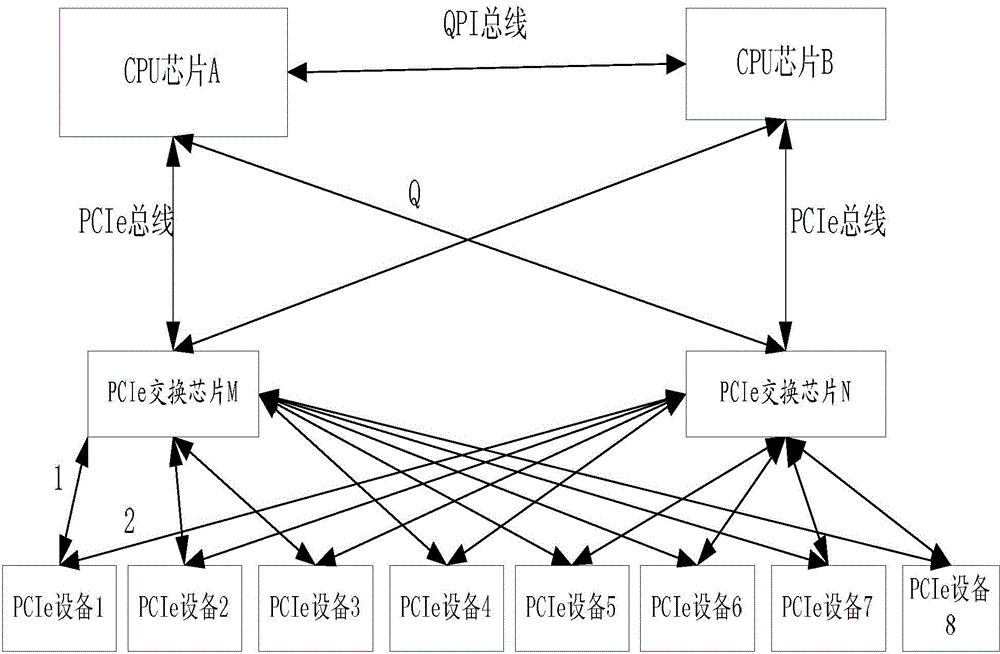
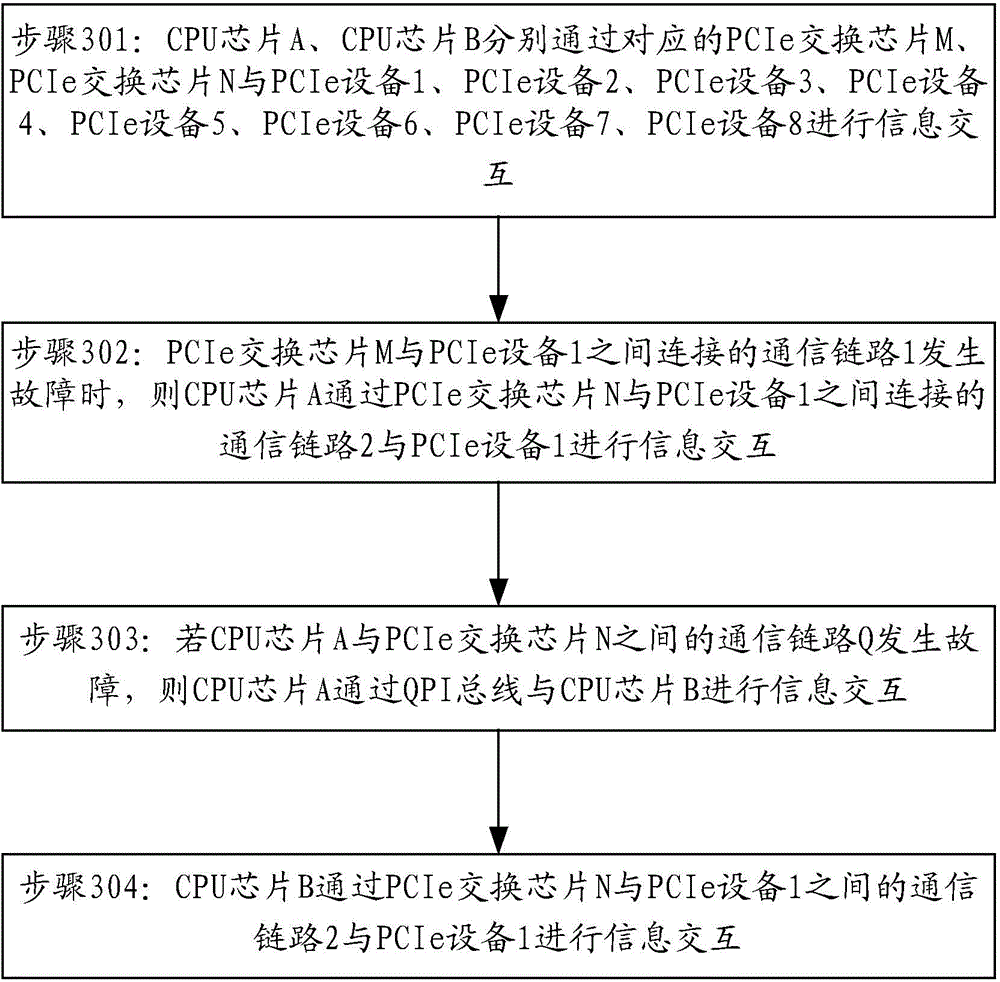
InactiveCN104407999AEnable secure accessAvoid the problem of not being able to access the corresponding PCIe deviceMultiple digital computer combinationsElectric digital data processingTelecommunications linkInterconnection
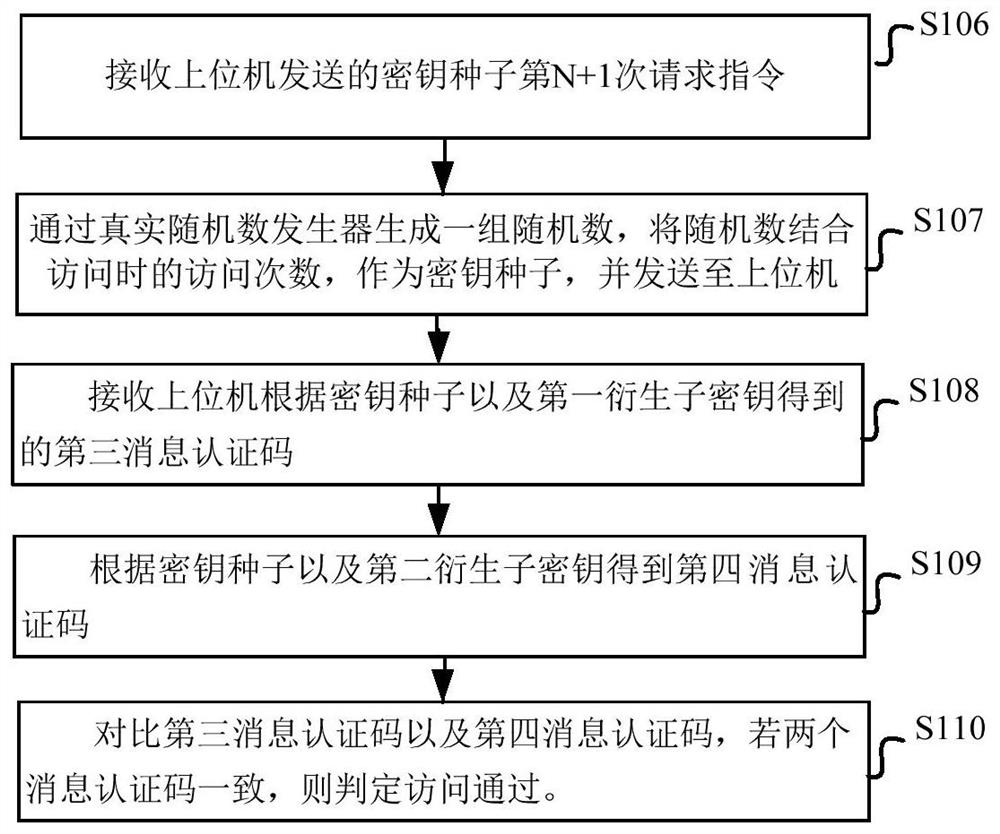
The invention provides an information security access architecture, method and system. The architecture comprises a CPU (central processing unit) chip, a plurality of PCIe (peripheral component interface express) exchanging chips and PCIe equipment; the CPU chip is respectively interconnected with the PCIe exchanging chips through a peripheral component express interconnection bus, i.e. a PCIe bus; the PCIe exchanging chips are interconnected with the PCIe equipment. By adopting the information security access architecture, method and system, the problem that the corresponding PCIe equipment cannot be accessed due to the failure of a communication link can be avoided, and the information security access is realized.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Method and device for achieving remote access
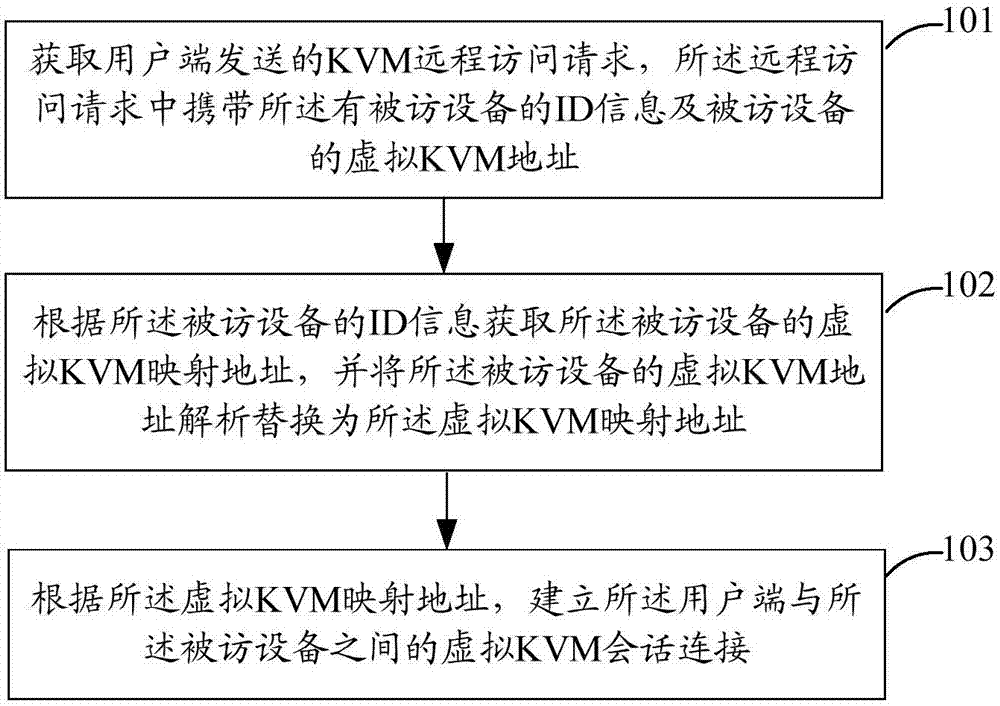
ActiveCN107342972AEnable remote accessEnable secure accessTransmissionDisplay deviceVirtual keyboard
The invention discloses a method for achieving remote access. The method comprises the steps that a virtual keyboard, a display and a mouse (KVM) remote access request sent by a user side is acquired, wherein the remote access request carries ID information and a virtual KVM address of accessed equipment; a virtual KVM mapping address of the accessed equipment is acquired according to the ID information of the accessed equipment; the virtual KVM address of the accessed equipment is replaced with the virtual KVM mapping address; and a virtual KVM session connection between the user side and the accessed equipment is established according to the virtual KVM mapping address. The invention further discloses a device for achieving remote access.
Owner:LIAONING MOBILE COMM
A multi-host network architecture and gateway device
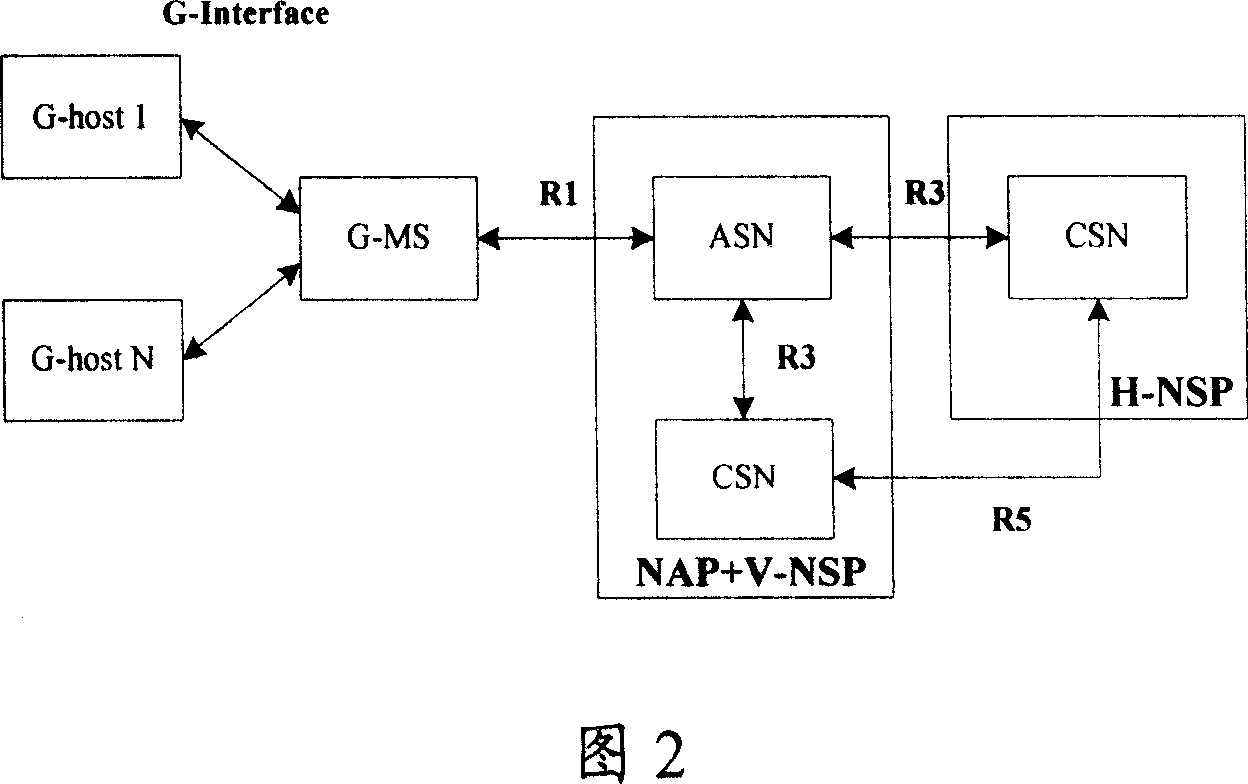
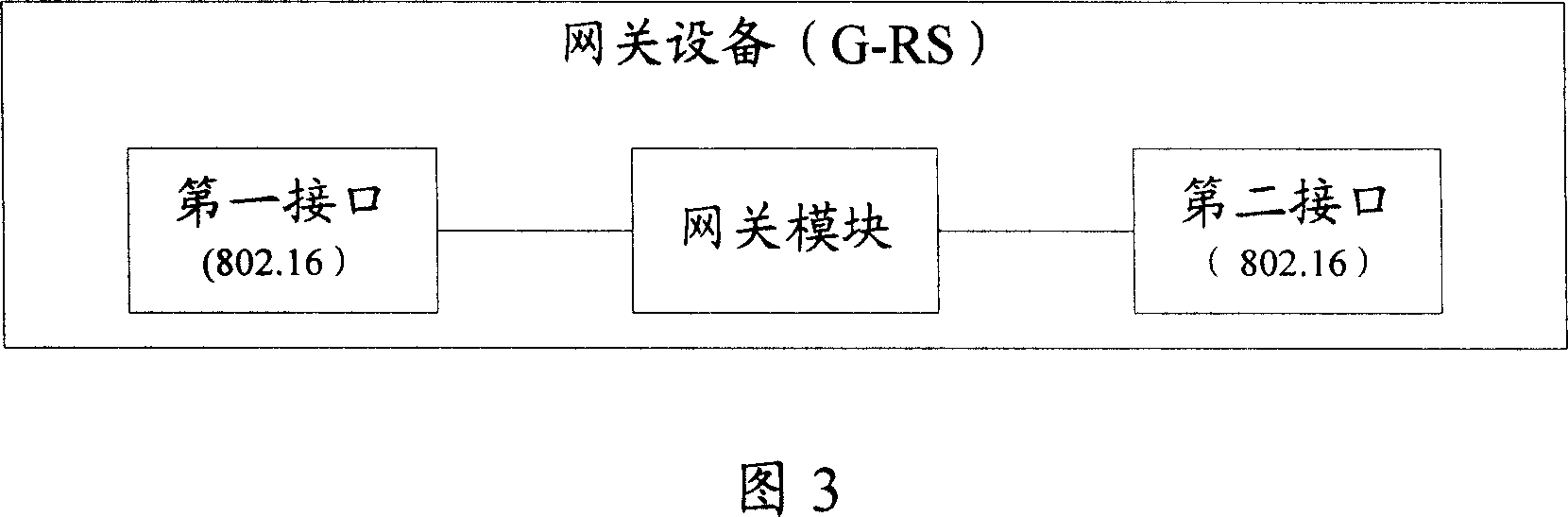
InactiveCN101056233AEnable secure accessWith transfer functionAssess restrictionData switching by path configurationNetwork architectureWiMAX
The invention discloses multiple host network architecture and gateway device, which is used to solve the problem that the existing WiMAX network architecture generates too high ASN and G-MS resource consumption and can not support the host devices based on the 802.16 radio transmission protocol. The multi-host network architecture of the invention includes: at least two host devices, and internetworking access server ASN and connection service network CSN; the described network also includes gateway device, which is connected with all host devices via the first interface and connected with the ASN via the second interface.
Owner:HUAWEI TECH CO LTD
Device for providing, editing, and playing video content and method for same
InactiveCN105531737AQuick feedbackPurchase fulfillmentData processing applicationsElectronic editing digitised analogue information signalsComputer graphics (images)Data file
The present invention relates to a platform for providing video content, a device for editing and playing video content, and a method for same, the platform not only allowing a user to directly produce and edit a video and generate content but also providing an application program, which is capable of playing the video content, and allowing the sale or purchase of the video content on the basis of social networking services, and the method and device storing editing information on video content as a separate data file, when editing and playing the video content, without affecting the stream of the original video content and accordingly controlling the playing of the original video content file.
Owner:伟播 +1
Micro-isolation protection system adopting zero-trust architecture and protection method thereof
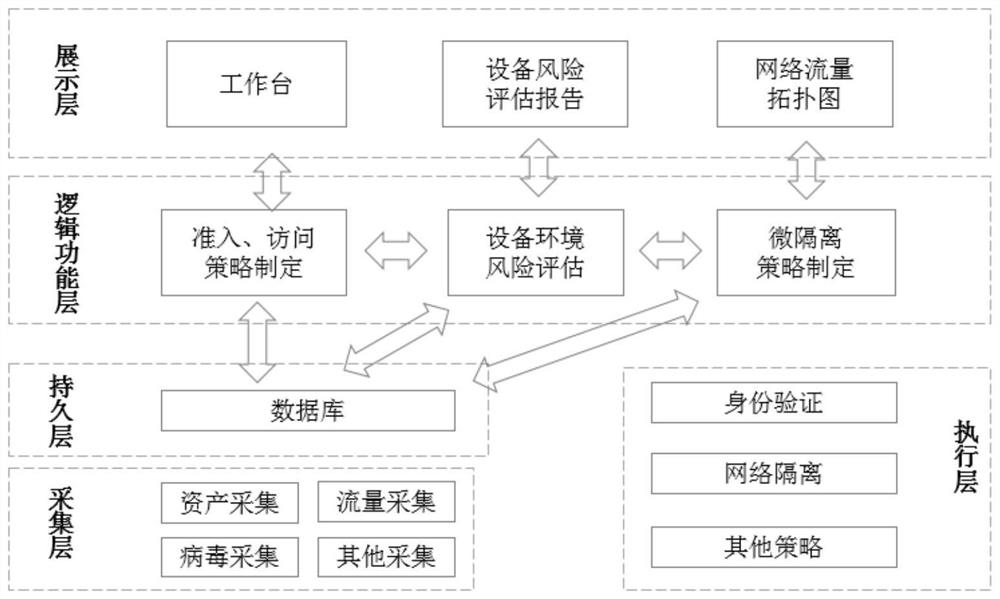
ActiveCN113783871AEnable secure accessSimplify quarantine managementTransmissionComputer networkAdaptive management
The invention discloses a micro-isolation protection system and method adopting a zero-trust architecture, the system comprises a logic architecture and a physical architecture, the logic architecture comprises an execution layer, an collection layer, a persistence layer, a logic function layer and a display layer; the physical architecture comprises a strategy control center, a safety gateway and an Agent plug-in; according to the invention, based on full understanding of the cloud computing environment, under the idea of zero-trust safety, multiple safety technologies such as network micro-isolation, safety gateways and system environment perception are integrated, and the effects of south-north traffic safety admission, east-west traffic (adaptive management and control, and real-time network strategy association of the safety state of access equipment) are finally realized.
Owner:云南电网有限责任公司信息中心
WiFi access method and device
ActiveCN106714158AImprove securityEnable secure accessSecurity arrangementPoint registrationAccess method
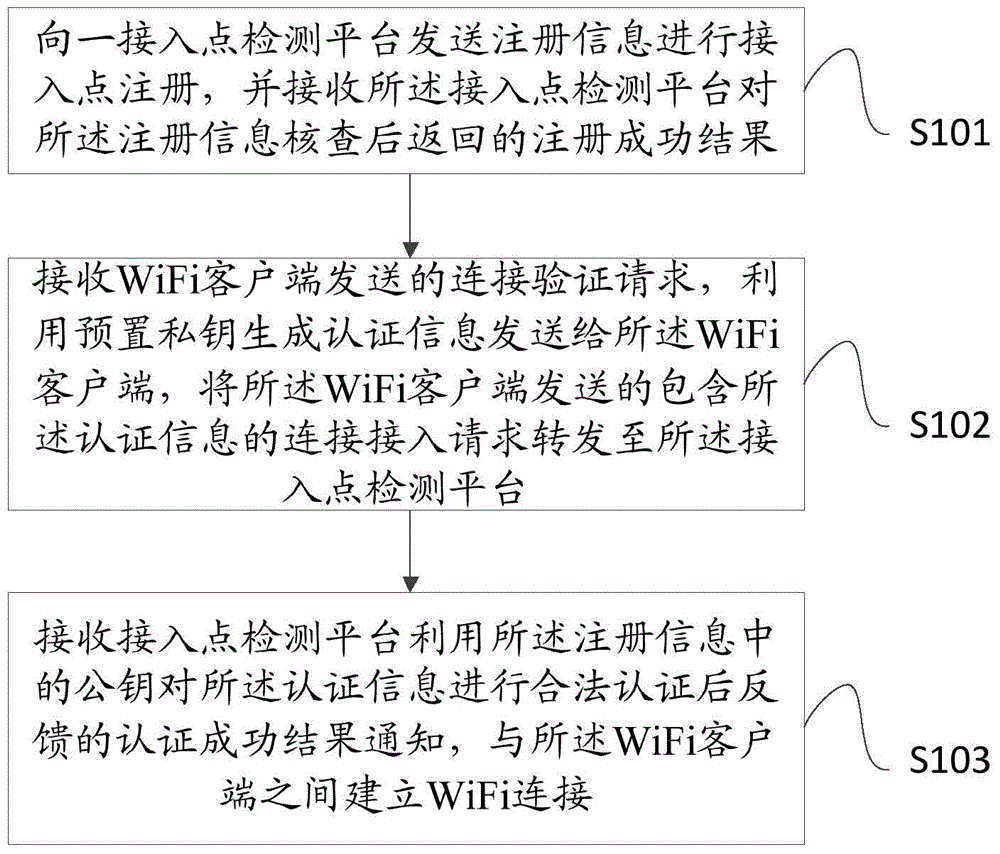
The present invention provides a WiFi access method and device. The WiFi access method comprises a step of sending registration information to an access point detection platform to carry out access point registration, and receiving a registration success result which is returned after the access point detection platform verifies the registration information, wherein the registration information comprises access authentication related information and a public key, a step of receiving a connection verification request sent by a WiFi client, and generating authentication information by using a preset private key and sending the authentication information to the WiFi client, and forwarding a connection access request comprising the authentication information sent by the WiFi client to the access point detection platform, a step of receiving an authentication success result notification fed by the access point detection platform after the access point detection platform carries out legal authentication on the authentication information by using the public key in the registration information, and establishing a WiFi connection with the WiFi client. Through the embodiment of the invention, the security of the WiFi verification is improved, the data information is prevented from being tampered maliciously, the access to a fishing WiFi access point is prevented, and the secure access of WiFi is realized.
Owner:CHINA MOBILE COMM GRP CO LTD
Safe access method and system for ECU in vehicle and storage medium
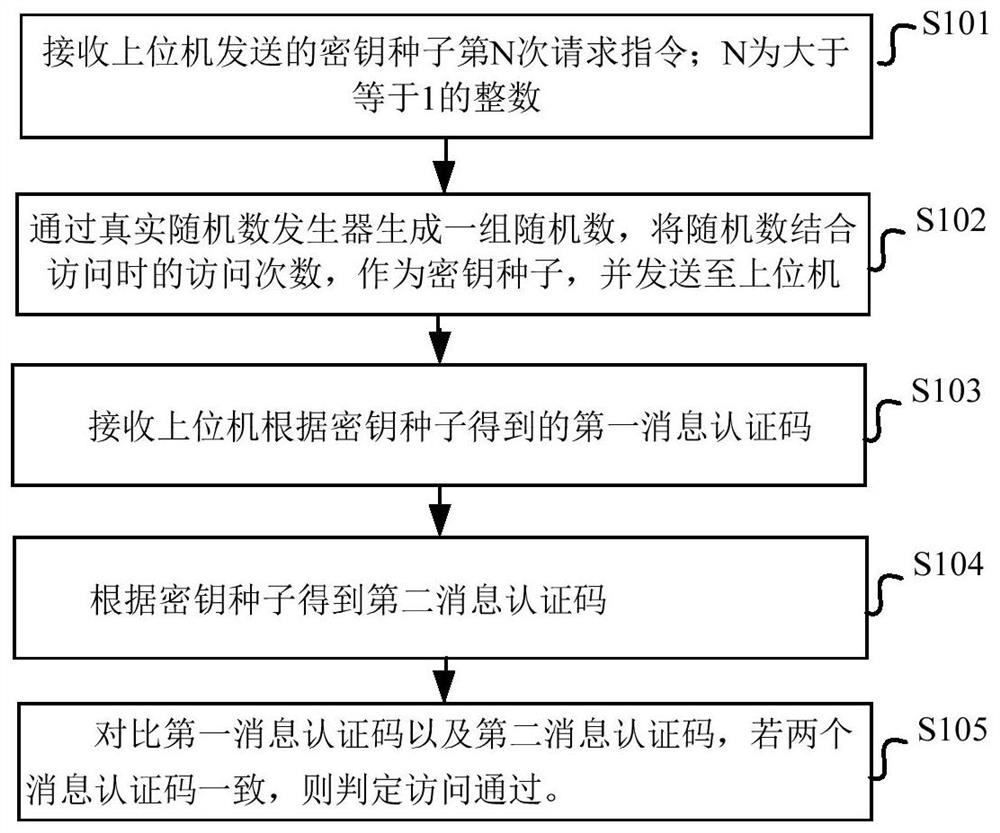
ActiveCN112487408AEnable secure accessResolving Source UncertaintyDigital data protectionDigital data authenticationAccess methodIn vehicle
The invention provides a safety access method and system for an in-vehicle ECU and a storage medium. The safety access method comprises the steps of receiving an Nth request instruction, sent by an upper computer, of a key seed; generating a group of random numbers through a real random number generator, taking the random numbers as key seeds in combination with the access times during access, andsending the key seeds to an upper computer; receiving a first message authentication code obtained by the upper computer according to the key seed; obtaining a second message authentication code according to the key seed; and comparing the first message authentication code with the second message authentication code, and if the two message authentication codes are consistent, judging that the access is passed. The upper computer and the ECU are respectively based on the real random number, the number of times of access is combined with the real random number to serve as a key seed, and then authentication comparison is carried out on the obtained two message authentication codes, so that an access mechanism is safer, and the integrity, timeliness and authenticity of a communication accessmechanism of the ECU and other equipment are guaranteed. The problem that potential safety loopholes exist in an existing ECU safety access strategy is solved.
Owner:WEICHAI POWER CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com