Safe access method and system for ECU in vehicle and storage medium
A technology of safe access and number of visits, which is applied in the field of vehicle information security, can solve problems such as hidden security loopholes, and achieve the effect of ensuring integrity, access mechanism security, and solving hidden security loopholes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
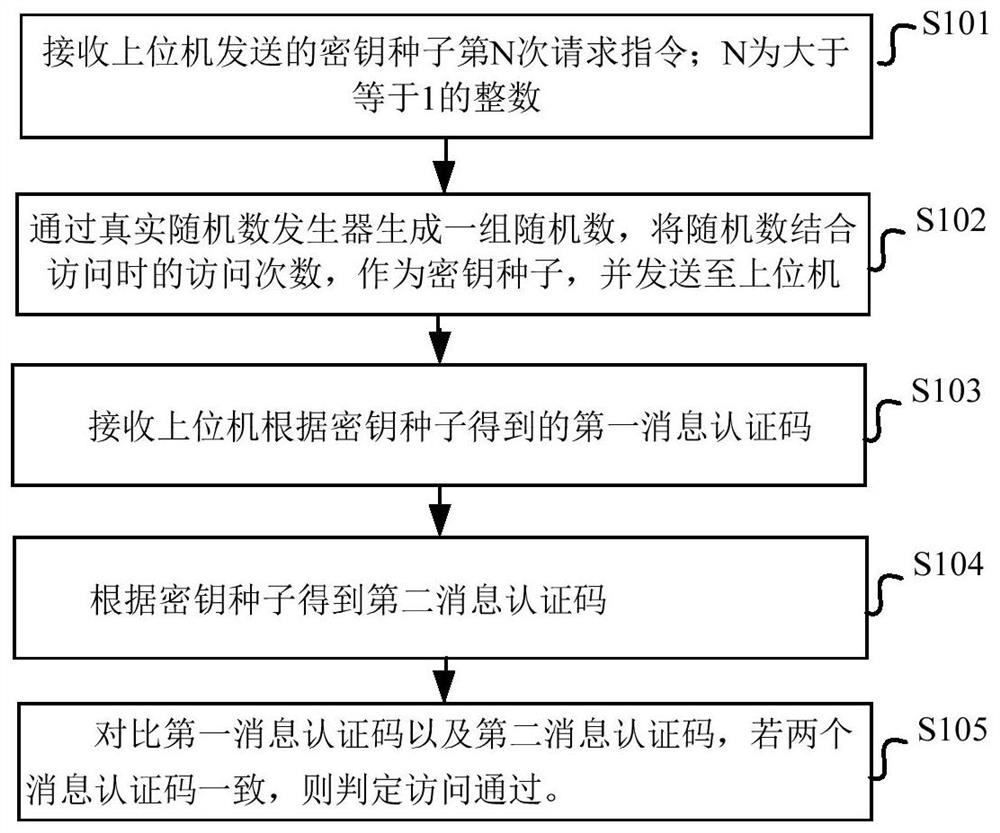
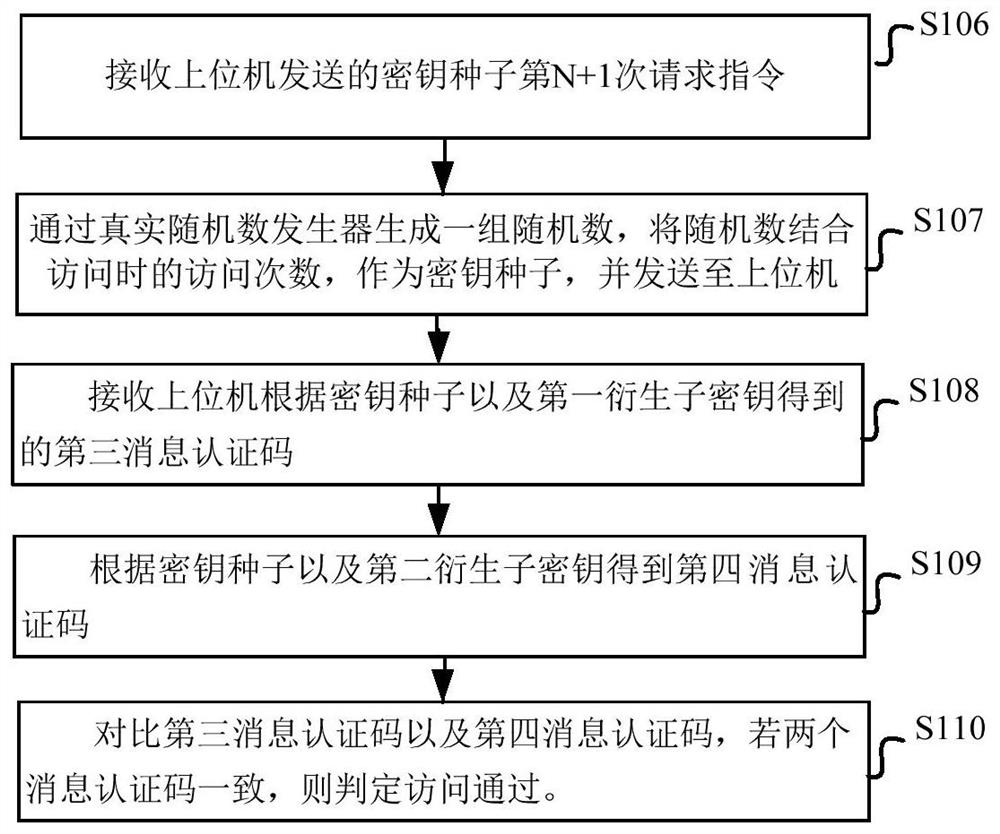
[0058] figure 1 A schematic diagram of steps of a method for securely accessing an in-vehicle ECU according to an embodiment of the present application is shown in .
[0059] like figure 1 As shown, the secure access method for the ECU in the vehicle according to the embodiment of the present application specifically includes the following steps:
[0060] S101: Receive the Nth request instruction of the key seed sent by the host computer; N is an integer greater than or equal to 1.
[0061] S102: Generate a set of random numbers by a real random number generator, combine the random numbers with the number of visits during visits as a key seed, and send it to the host computer.
[0062] S103: Receive the first message authentication code obtained by the host computer according to the key seed.
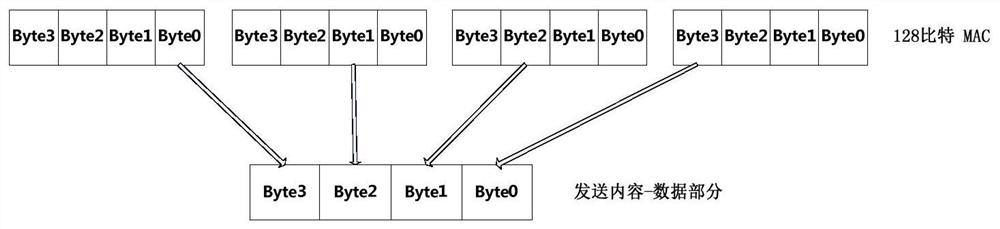
[0063] Specifically, the upper computer message authentication code module extracts the corresponding first key in the upper computer key array according to the key seed, and obtains...
Embodiment 2
[0110] This embodiment provides a security access system for in-vehicle ECU. For details not disclosed in the security access system for in-vehicle ECU in this embodiment, please refer to the security access system for in-vehicle ECU in other embodiments. The specific implementation content of the security access method.
[0111] Figure 5 A schematic structural diagram of a secure access system for an ECU in a vehicle according to an embodiment of the present application is shown in .
[0112] like Figure 5 As shown, the secure access system for the ECU in the vehicle according to the embodiment of the present application specifically includes a host computer access instruction module 10, an ECU hardware encryption module 20, a host computer message authentication code module 30, an ECU message authentication code module 40, and an ECU access Judgment module 50 .
[0113] specific,
[0114] Host computer access command module 10: for sending key seed request command.
...
Embodiment 3
[0139]This embodiment provides a security access device for an in-vehicle ECU. For details not disclosed in the security access device for an in-vehicle ECU in this embodiment, please refer to the security access device for an in-vehicle ECU in other embodiments. The specific implementation content of the security access method or system.
[0140] Image 6 A schematic structural diagram of a security access device 400 for an in-vehicle ECU according to an embodiment of the present application is shown in .
[0141] like Image 6 As shown, a security access device 400 for an ECU in a vehicle includes:
[0142] Memory 402: for storing executable instructions; and
[0143] Processor 401: used to connect with memory 402 to execute executable instructions so as to complete the motion vector prediction method.
[0144] Those skilled in the art can understand that the Image 6 It is only an example of the security access device 400 for the ECU in the vehicle, and does not consti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com