Micro-isolation protection system adopting zero-trust architecture and protection method thereof
A protection system and architecture technology, applied in transmission systems, electrical components, etc., can solve problems such as springboard attacks, difficulty in controlling east-west traffic, difficulty in realizing north-south traffic access control and business application resource access control, etc., to achieve resistance The effect of stopping infringement and simplifying network isolation management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
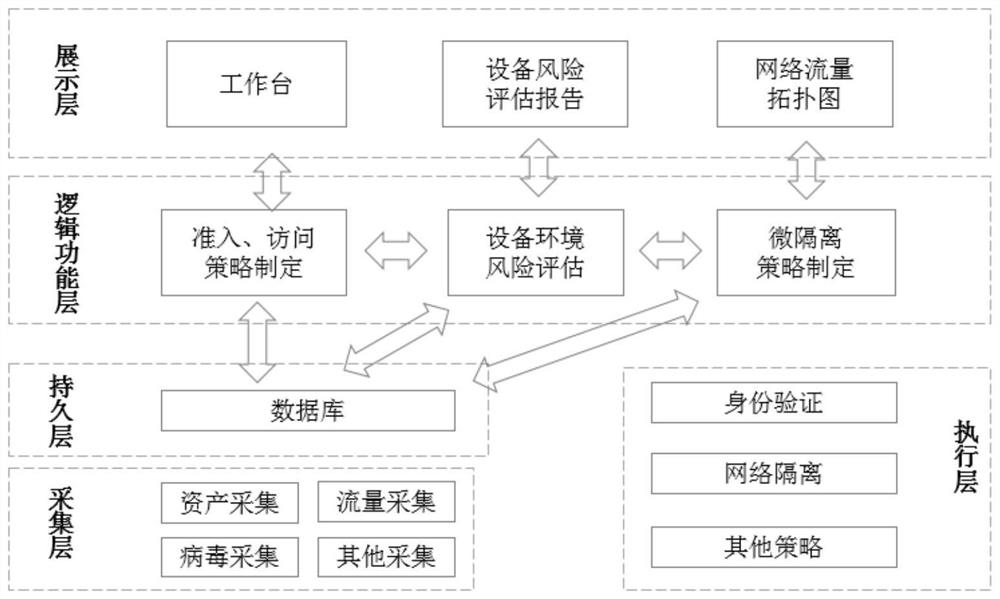
[0066] like figure 1 As shown, a micro-isolation protection system adopting a zero-trust architecture includes a logical architecture and a physical architecture, wherein the logical architecture includes an execution layer, an acquisition layer, a persistence layer, a logical function layer, and a presentation layer; the physical architecture includes a policy control Center, Security Gateway and Agent plug-ins;
[0067] The execution layer is used to execute the security policy specified by the policy control center; the collection layer is used to collect the assets of network access devices; the persistence layer is used to format and store asset information, and provide a data basis for the policy control center; The logical function layer is used for network credit access, formulation and maintenance of access policies, equipment environment risk assessment and micro-isolation policy formulation and maintenance; the display layer is used for exporting equipment risk asse...
Embodiment 2
[0072] Based on the system structure in Embodiment 1 above, this embodiment provides a micro-isolation protection method using a zero-trust architecture, the micro-isolation protection method is applied to the micro-isolation protection system, and the micro-isolation protection method using a zero-trust architecture The micro-isolation protection methods are as follows:
[0073] Real-time monitoring of east-west traffic, north-south traffic, and security status of network access devices during network operation, and real-time association of any network in need of self-adaptive control of east-west traffic, security access of north-south traffic, and security status of network access devices When there is one or more items, use the corresponding strategy to achieve micro-isolation protection.
[0074] In the above method, the conditions for adaptive control of east-west traffic are: the east-west traffic used to provide hosts or services exceeds the set threshold;
[0075] Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com