Contract text protection method based on RSA encryption sha-256 digital signature
A sha-256 and digital signature technology, applied in digital data protection, electronic digital data processing, instruments, etc., can solve the problems of small SHA1 hash value and high possibility of collision, and achieve more secure data encryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be further described below in conjunction with specific examples.
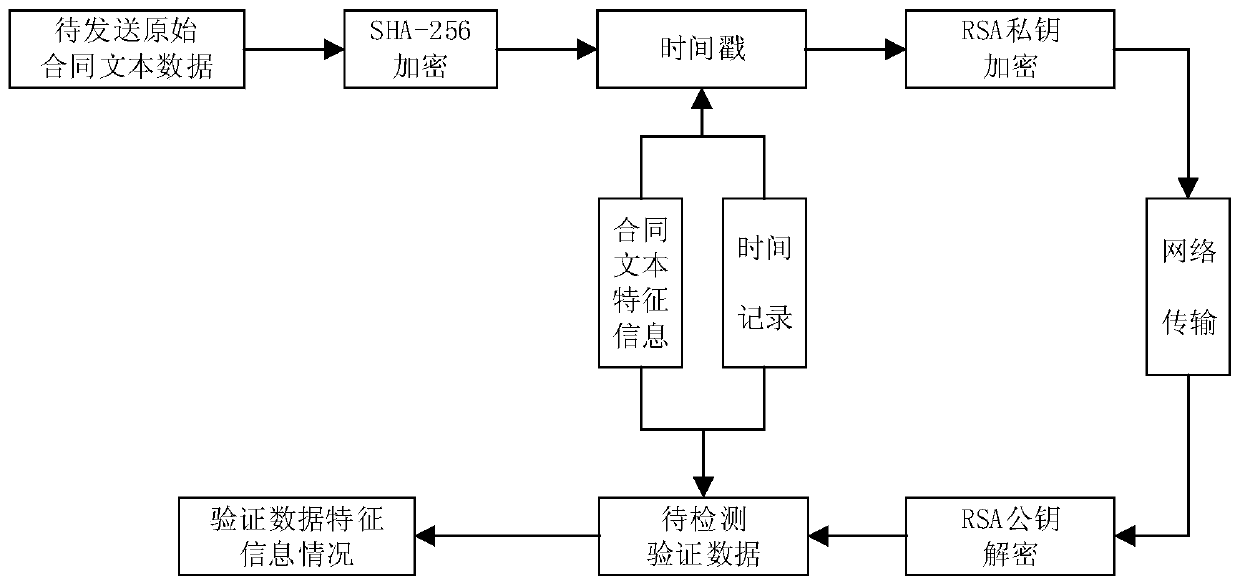
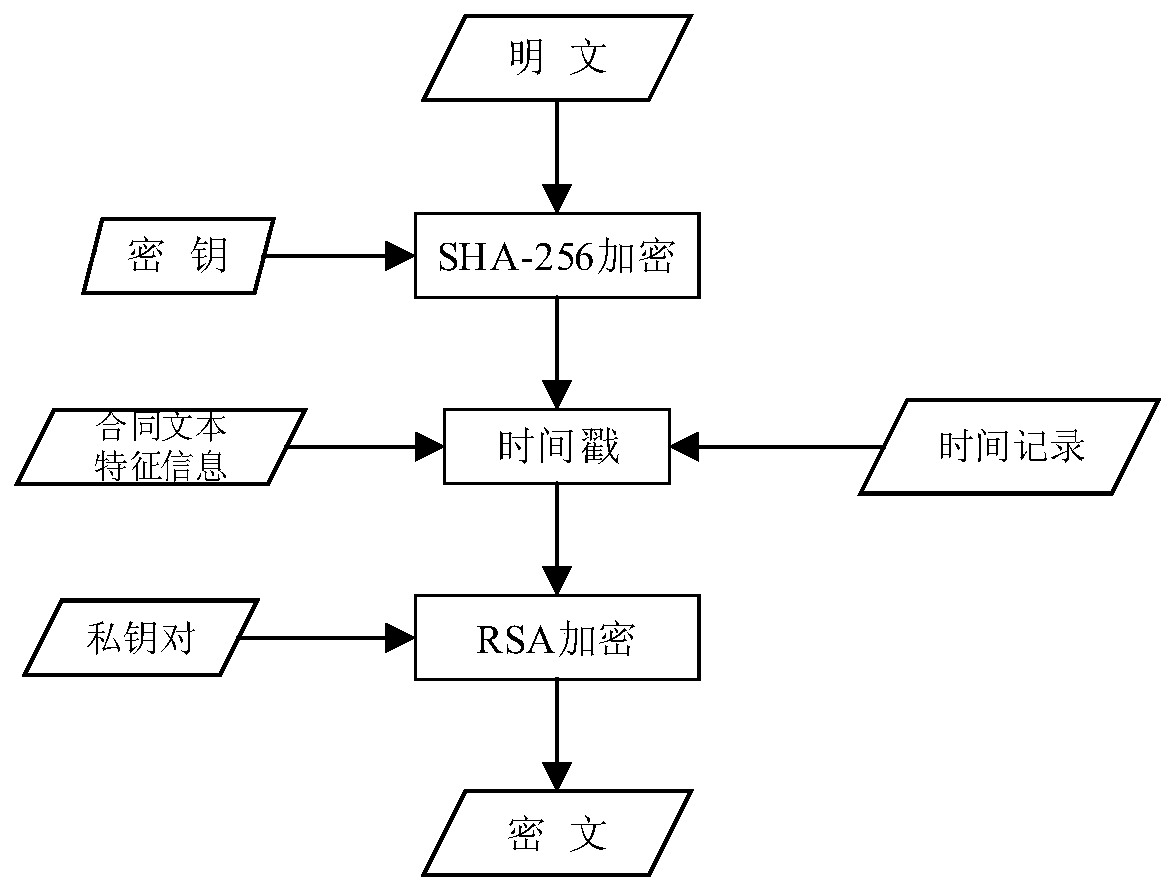
[0032] refer to Figure 1 to Figure 4 , a contract text protection method based on RSA encrypted sha-256 digital signature, comprising the following steps:
[0033] 1) Obtain the original data of the contract text to be sent;
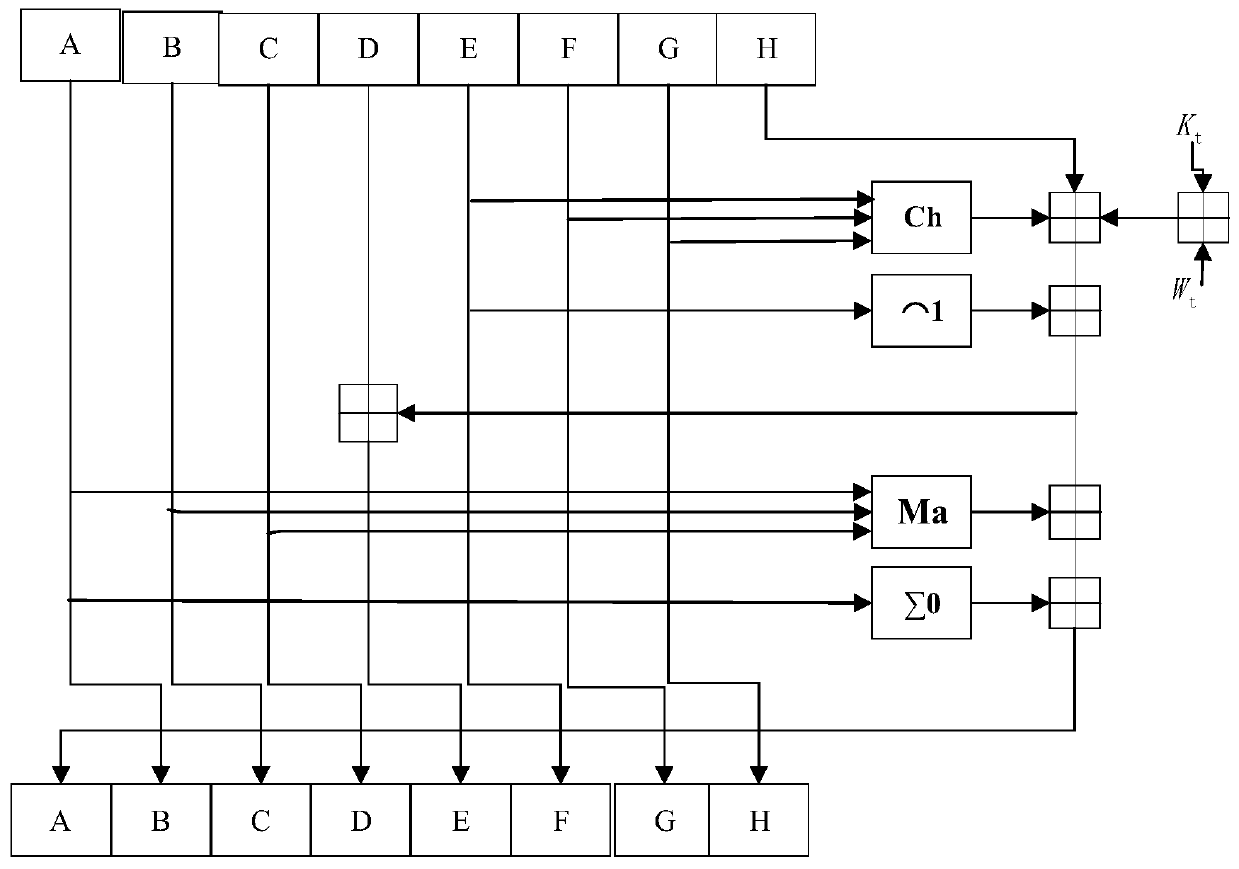
[0034] 2) Encrypt the contract text to be sent for the first time, that is, use the sha-256 algorithm to encrypt the original contract text data to generate a signature file;
[0035] 3) Add a time stamp to the signature file that has been encrypted for the first time, and encrypt it again with the sender's own RSA private key to generate a digital signature;
[0036] 4) The generated digital signature is stored in the data header for network transmission;
[0037] 5) Use the sender's RSA public key to decrypt, and the receiver obtains the data and performs user identity authentication combined with the timestamp, and gets the sha-256 digital signatu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com