Information hiding method and system based on elliptic curve cryptography
An elliptic curve and information hiding technology, which is applied in the field of information hiding based on elliptic curve cryptography, can solve the problems of single type of encryption technology, small key space, and no information hiding method based on elliptic curve cryptography. The effect of low cost, encrypted security, and complex algorithm structure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
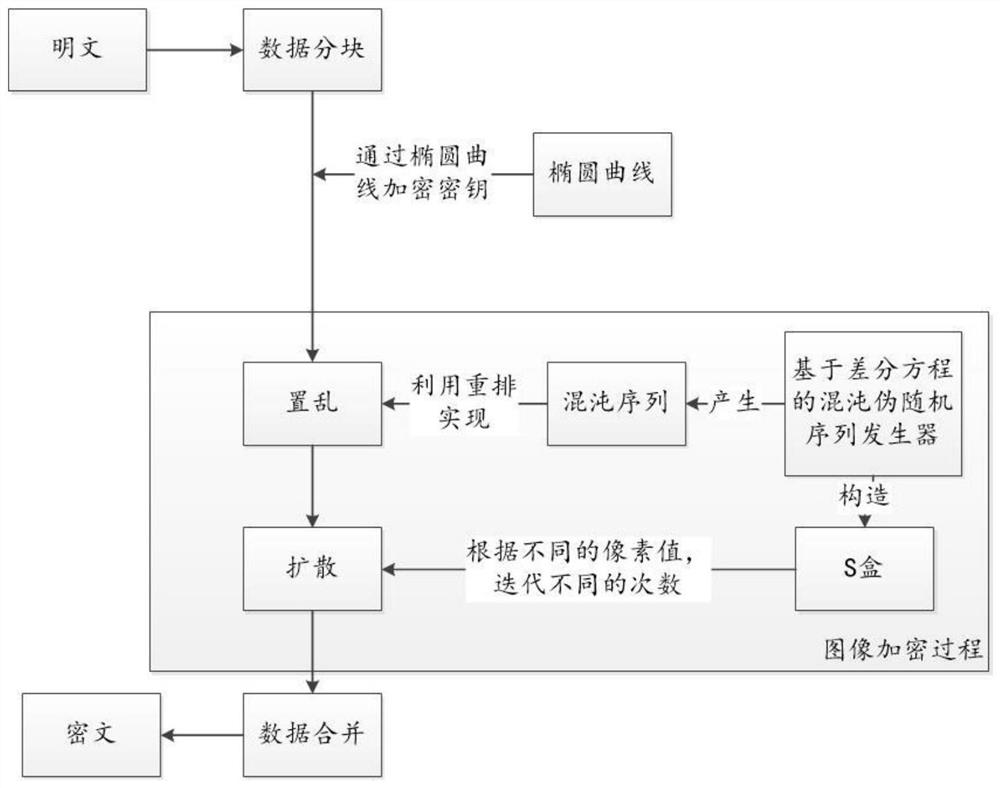
[0049] In this example, see figure 1 , an information hiding method based on elliptic curve cryptography, the steps are as follows:
[0050]a. Use the cryptographic system based on the elliptic curve on the finite field to generate the secret key as follows:
[0051] Choose one defined in the prime field F p Elliptic curves on:
[0052] E:y 2 ≡x 3 +ax+b(mod p)
[0053] The basic elliptic curve that constitutes the MVECC encryption system;
[0054] b. Select the base point α, the private key K of the communication parties A and B A and K B ;
[0055] Calculate P A =K A ·α,P B =K B α,P A and P B are the public keys of A and B respectively, and then calculate the encryption key (c 1 ,c 2 )=K B ·P A =K A ·P B ;
[0056] c. Take the initial secret key as ν; then take in is rounded down;
[0057] ν' 01 = c 1 ·ν 01 mod p
[0058] ν' 02 = c 2 ·ν 02 mod p
[0059] The ciphertext is ((c 1 ,c 2 ),ν′ 01 ,ν′ 02 ),thereby is the encrypted secret key...
Embodiment 2
[0066] This embodiment is basically the same as Embodiment 1, especially in that:
[0067] In this example, see Figure 1-Figure 2 , an information hiding method based on elliptic curve cryptography, characterized in that the steps are as follows:
[0068] a. Use the cryptographic system based on the elliptic curve on the finite field to generate the secret key as follows:
[0069] Choose one defined in the prime field F p Elliptic curves on:
[0070] E:y 2 ≡x 3 +ax+b(mod p)
[0071] The prime number p is 100003; the coefficient a is 1; the coefficient b=6; the basic elliptic curve constituting the MVECC encryption system;
[0072] b. Select the base point α, the private key K of the communication parties A and B A and K B ;
[0073] Calculate P A =K A ·α,P B =K B α,P A and P B are the public keys of A and B respectively, and then calculate the encryption key (c 1 ,c 2 )=K B ·P A =K A ·P B ; In this embodiment, select α=(2,4), the private key K of the comm...
Embodiment 3
[0090] This embodiment is basically the same as Embodiment 1, especially in that:
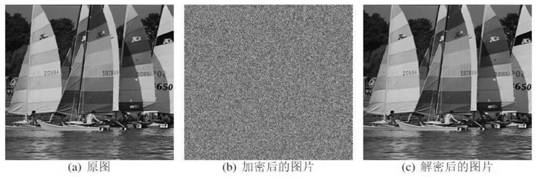
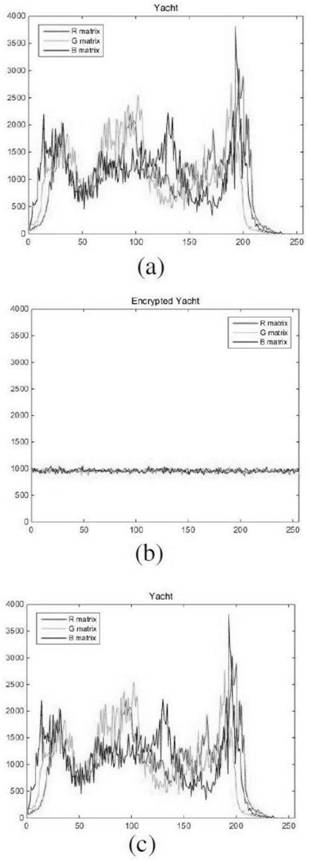
[0091] In this example, see Figure 1-Figure 2 , an information hiding system based on elliptic curve cryptography, implements the information hiding method based on elliptic curve cryptography described in the above embodiment, scrambles pixel values of plaintext pictures, and encrypts pixel values.
[0092]To sum up, the above embodiments are based on the information hiding technology of elliptic curve cryptography, using the elliptic curve based on the finite field as the substrate, after the key is scrambled, the fractional order chaotic map is used to generate the chaotic sequence. Use the randomness of the chaotic sequence to scramble the plaintext image, and then use the chaotic sequence and the pixel value to perform XOR operation to encrypt the picture pixels, so as to achieve the effect of scrambling and diffusion. The above embodiments combine elliptic curve public key cryptograph...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com