Encryption/decryption method
An encryption and decryption technology to be encrypted, which is applied in the field of encryption and decryption, can solve the problems that the encryption and decryption method cannot meet people's needs, the algorithm encryption security is not enough, the security and reliability are insufficient, and the encryption and decryption method is simple and the encryption is safe. , the effect of convenient operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
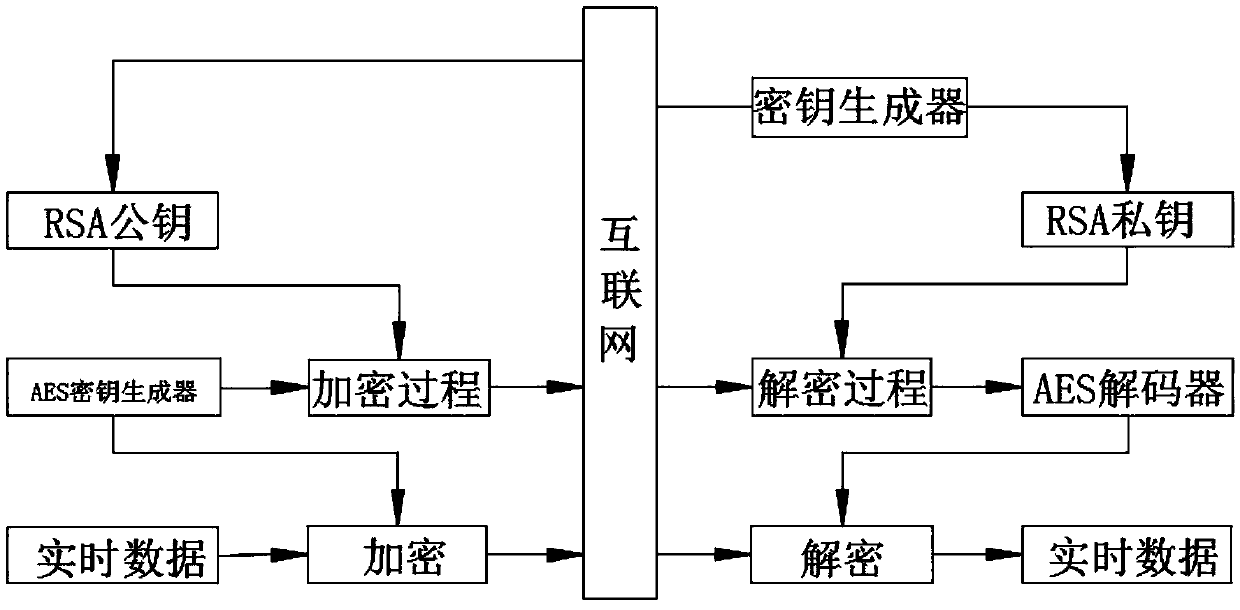
[0023] (1), select the plaintext to be encrypted, read the plaintext data through the processor, and the processor reads the binary digital data in the plaintext;
[0024] (2), use the AES algorithm to encrypt the plaintext data obtained in step (1), and the plaintext to be encrypted is encrypted by the AES key generator. The AES password is an iterative, symmetric key block password, and it can use 256-bit encryption key, and use 128-bit block encryption and decryption data to obtain encrypted plaintext and AES password, add at least one set of interference data in front and rear of the plaintext data, after decryption, remove the interference data added in front and rear of the sequence;
[0025] (3), use the RSA algorithm to encrypt the AES password obtained through step (2), and use SSL to send the connection request at the same time, after being encrypted by the RSA algorithm, the public key and the private key are obtained;
[0026] (4), after authentication, accept the ...
Embodiment 2
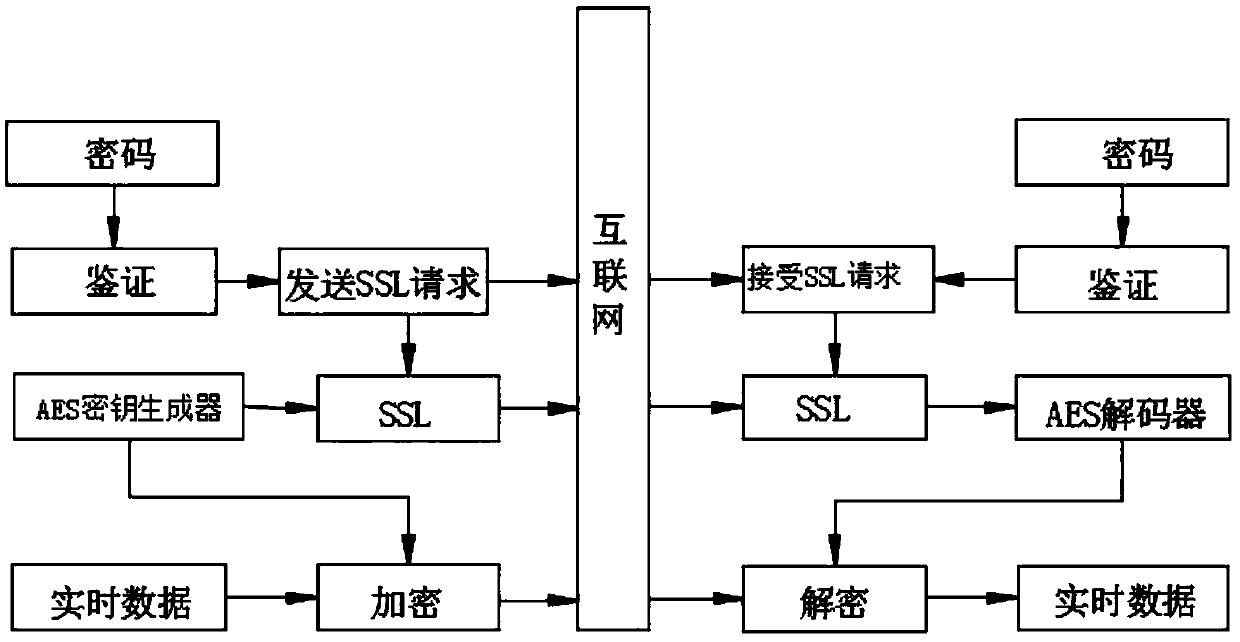
[0036] (1), select the plaintext to be encrypted, read the plaintext data through the processor, and the processor reads the binary digital data in the plaintext;
[0037] (2), use the AES algorithm to encrypt the plaintext data obtained in step (1), and the plaintext to be encrypted is encrypted by the AES key generator. The AES password is an iterative, symmetric key block password, and it can use 256-bit encryption key, and use 128-bit block encryption and decryption data to obtain encrypted plaintext and AES password, add at least one set of interference data in front and rear of the plaintext data, after decryption, remove the interference data added in front and rear of the sequence;
[0038] (3), use the RSA algorithm to encrypt the AES password obtained through step (2), and use SSL to send the connection request at the same time, after being encrypted by the RSA algorithm, the public key and the private key are obtained;
[0039] (4), after authentication, accept the ...
Embodiment 3
[0047] (1), select the plaintext to be encrypted, read the plaintext data through the processor, and the processor reads the binary digital data in the plaintext;
[0048] (2), use the AES algorithm to encrypt the plaintext data obtained in step (1), and the plaintext to be encrypted is encrypted by the AES key generator. The AES password is an iterative, symmetric key block password, and it can use 256-bit encryption key, and use 128-bit block encryption and decryption data, the delay of AES algorithm is 227 / ms, get the encrypted plaintext and AES password, add at least one set of interference data in front and rear of the plaintext data, after decryption, the sequence of Removal of interference data added in the front and rear;
[0049] (3) Use the RSA algorithm to encrypt the AES password obtained in step (2), and use SSL to send the connection request at the same time. After being encrypted by the RSA algorithm, the public key and the private key are obtained. The delay of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com