Patents
Literature
104results about How to "Fix technical issues with less security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
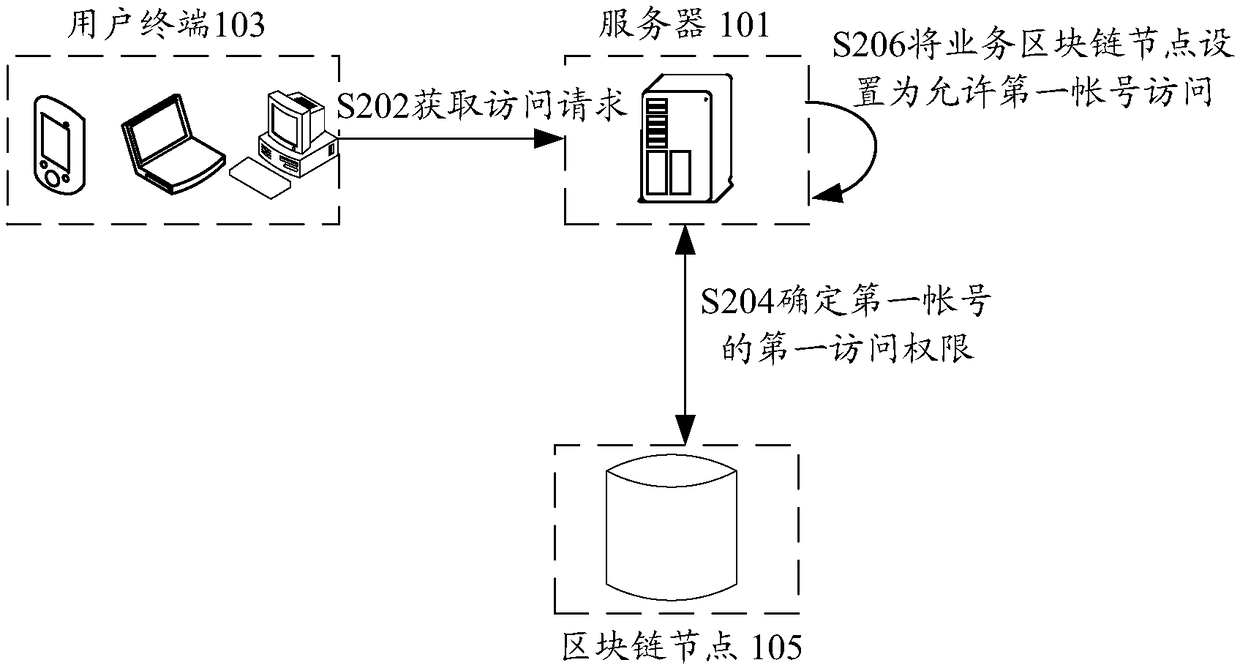
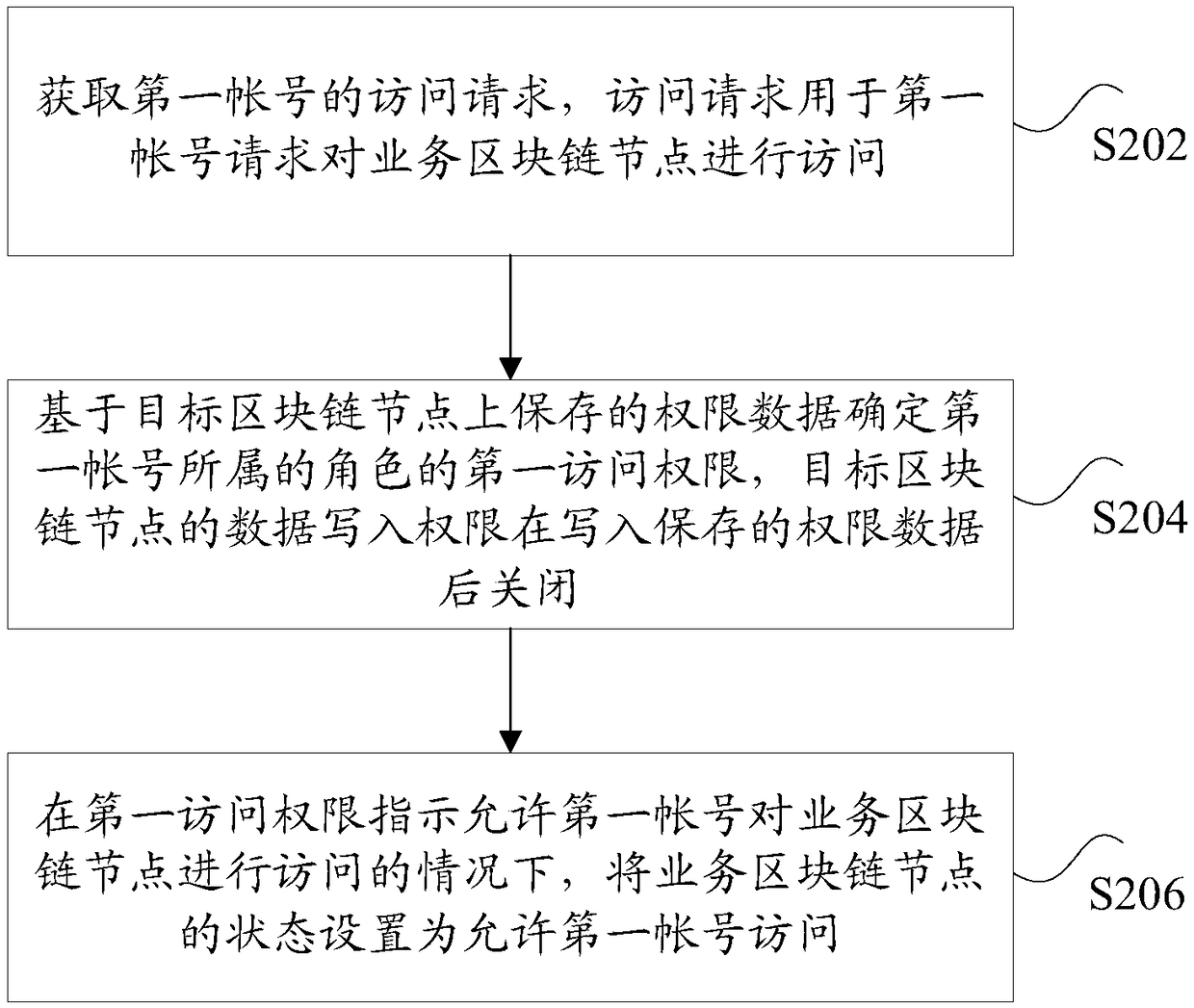
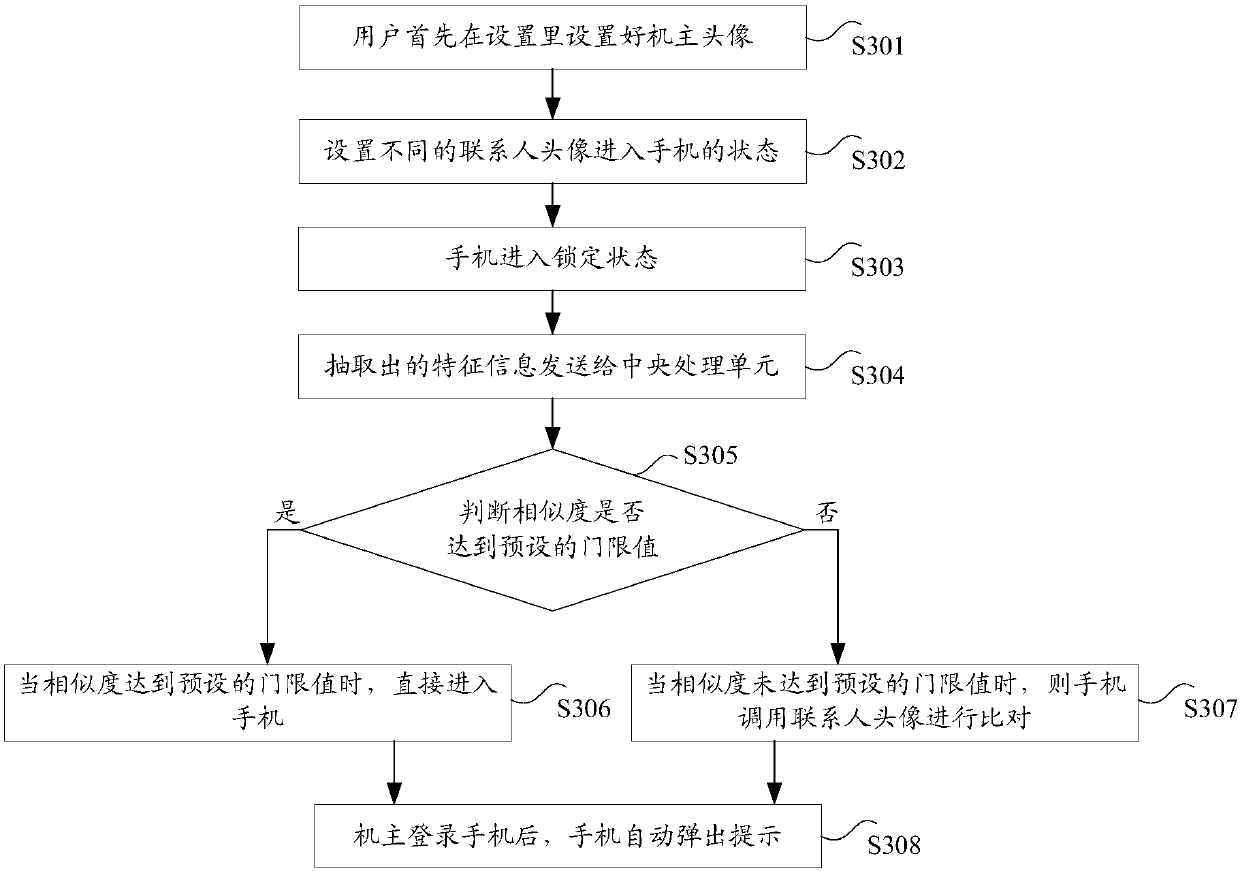
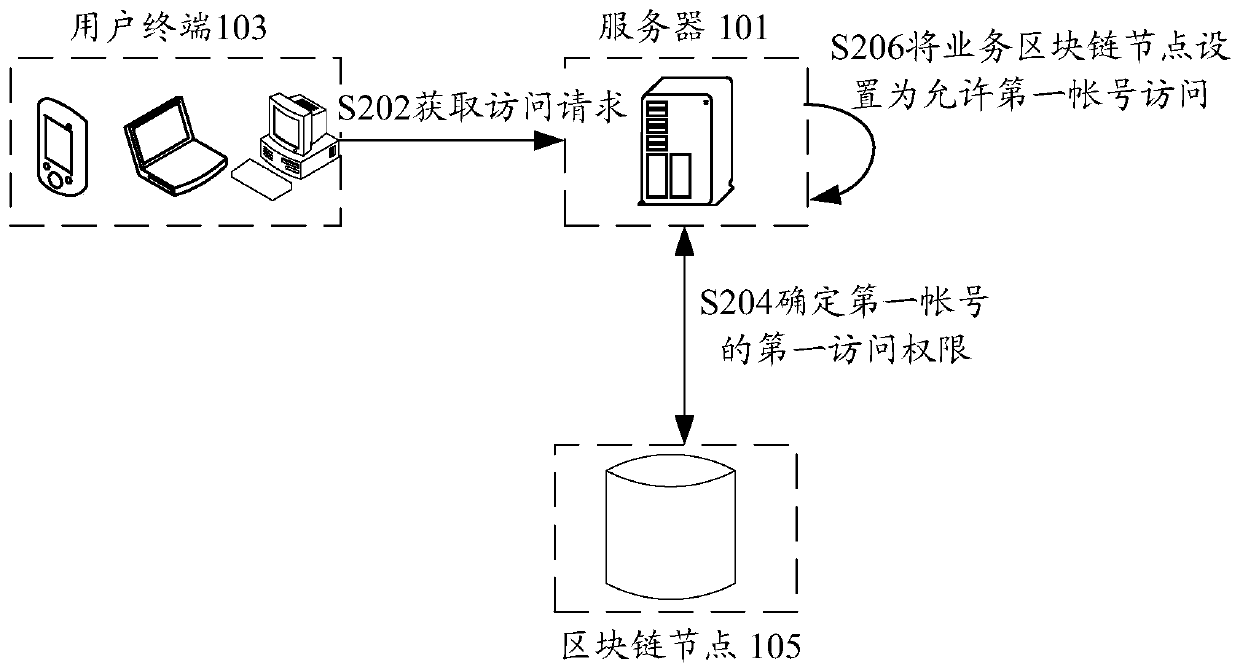
Blockchain access authentication method and device, storage medium and electronic device
ActiveCN108632268AGuaranteed to be tamper-proofGuaranteed traceabilityDatabase distribution/replicationTransmissionAuthenticationBlockchain
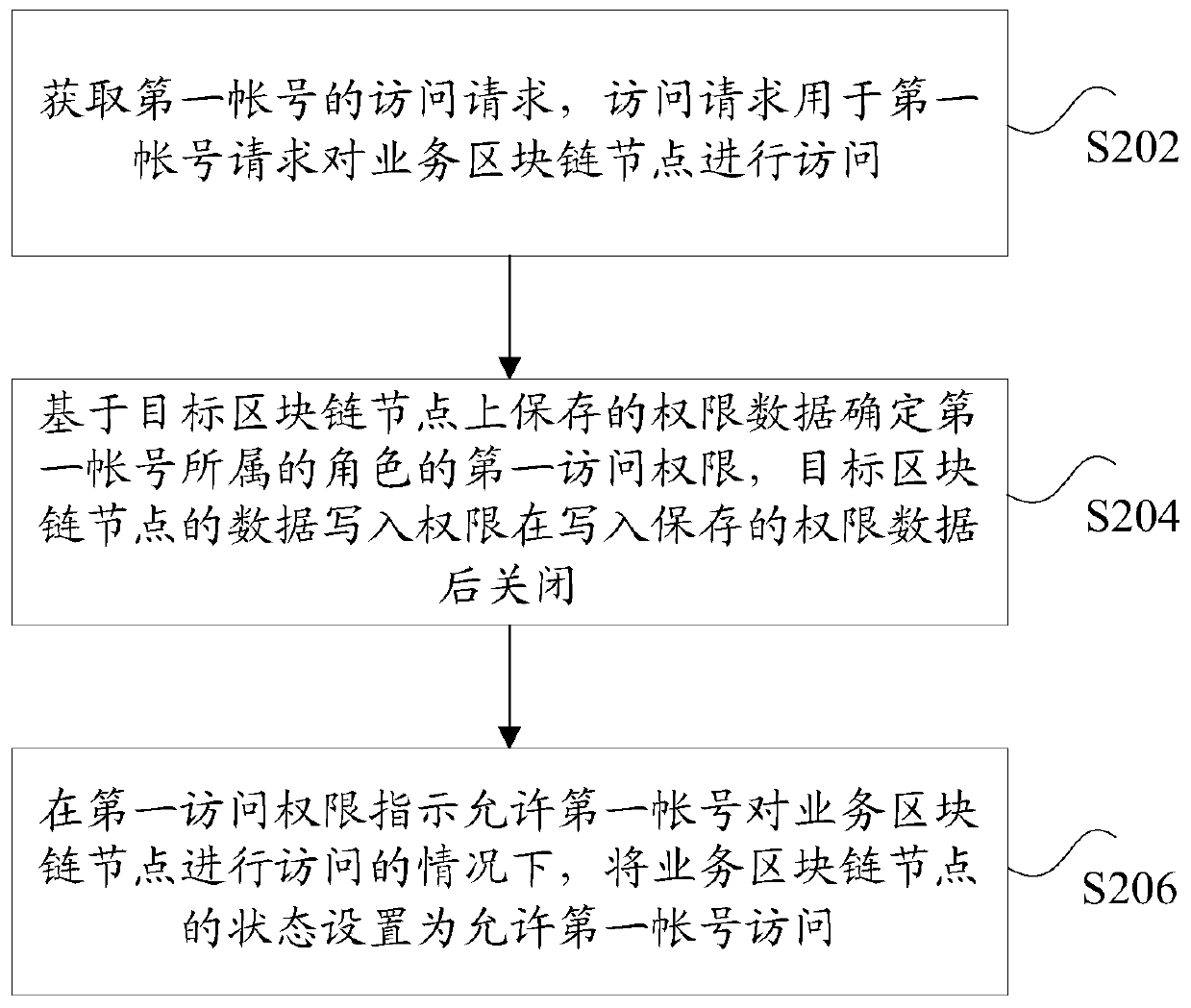
The invention discloses a blockchain access authentication method and device, a storage medium and an electronic device, wherein the method comprises the following steps: obtaining an access request of a first account, wherein the access request is used for the first account to request to access a service blockchain node; responding to the access request, and determining a first access authority of a role belonging to the first account based on the permission data saved on the target blockchain node, wherein the data writing permission of the target blockchain node is closed after the saved permission data are written; in the case that the first access permission indicates that the first account is allowed to access the service blockchain node, the status of the business blockchain node isset to allow the first account to access. The blockchain access authentication method and device in the present invention solve the technical problem that the security of the permission data in the related art is low.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
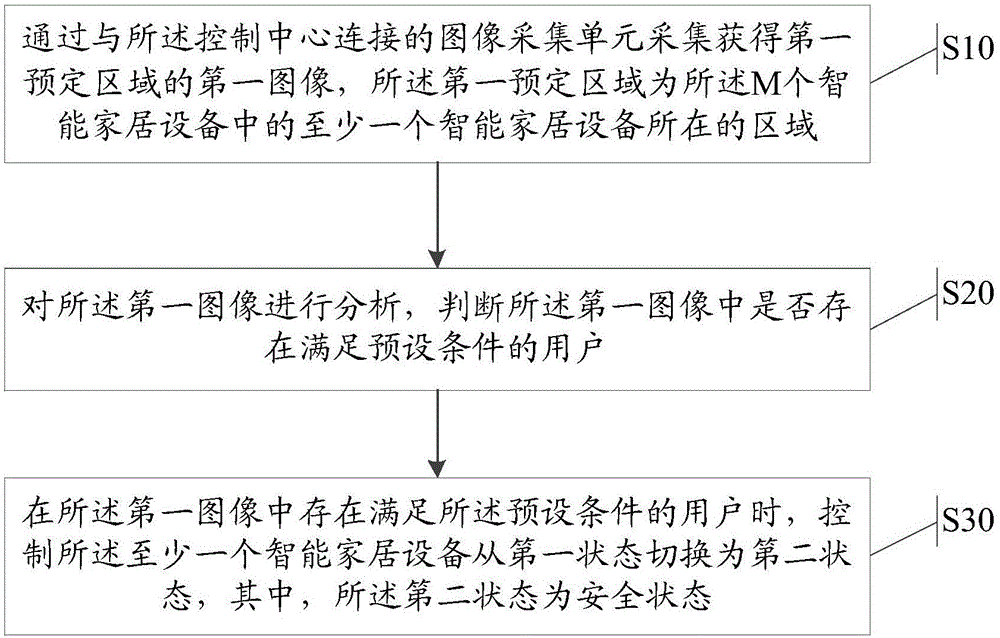
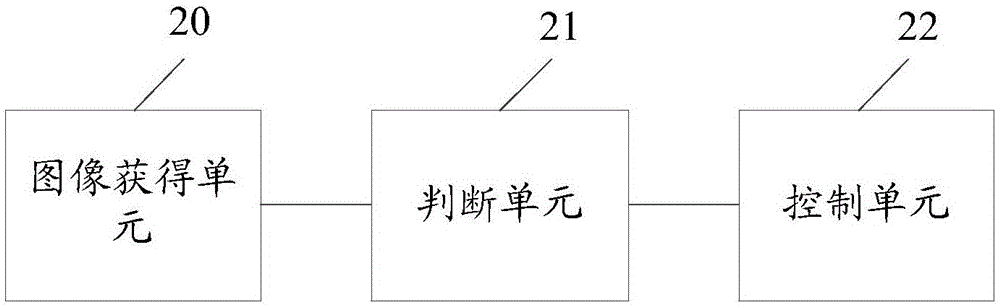
Intelligent household control method and control center
ActiveCN105137778AFix technical issues with less securityImprove securityComputer controlProgramme total factory controlControl engineeringHuman–computer interaction
The invention provides an intelligent household control method and a control center. The method is applied to the control center. The control center is connected with M intelligent household devices. The method comprises steps: an image acquisition unit connected with the control center acquires and obtains a first image of a first predetermined region, wherein the first predetermined region is a region in which at least one intelligent household device in the M intelligent household devices is; the first image is analyzed, and whether a user meeting a preset condition exists in the first image is judged; and when a user meeting a preset condition exists in the first image, the at least one intelligent household device is controlled to be switched from a second state to a first state, wherein the second state is a safe state.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
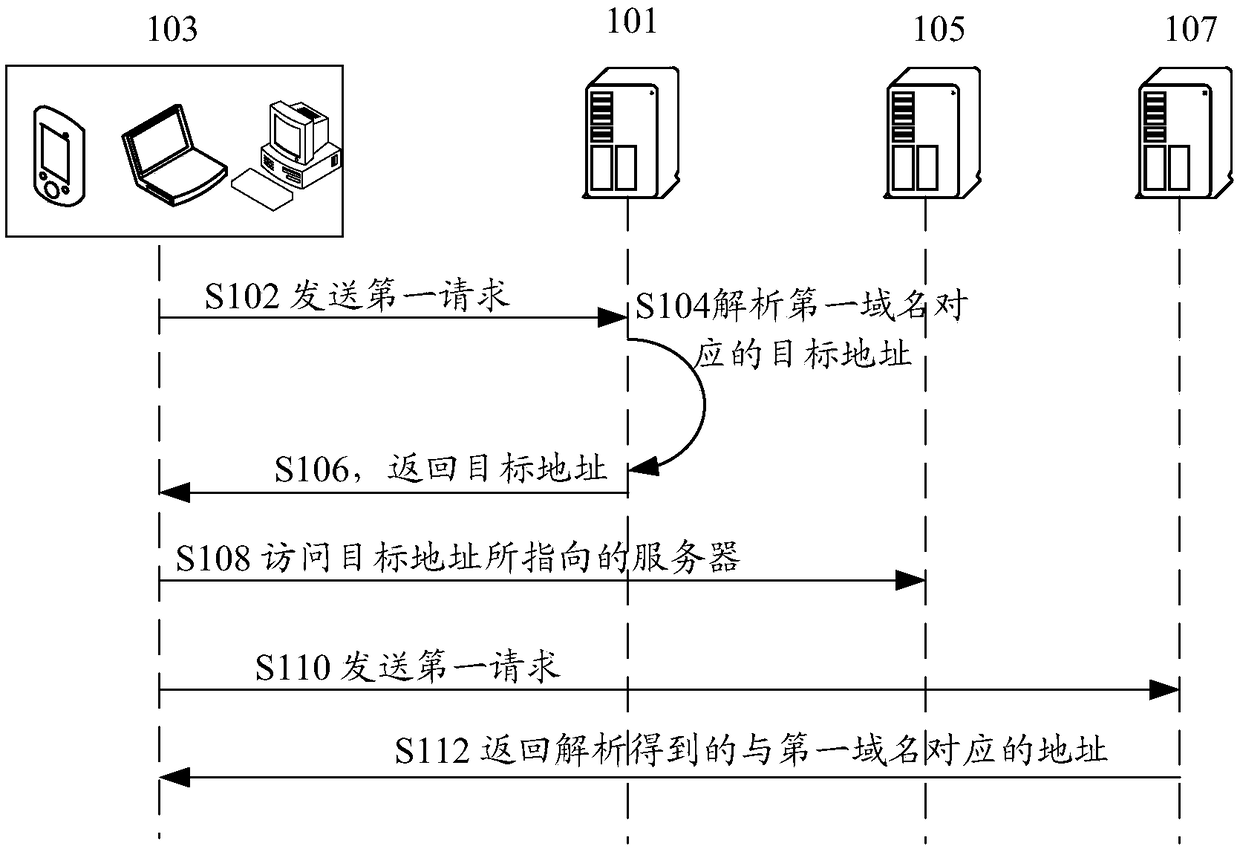
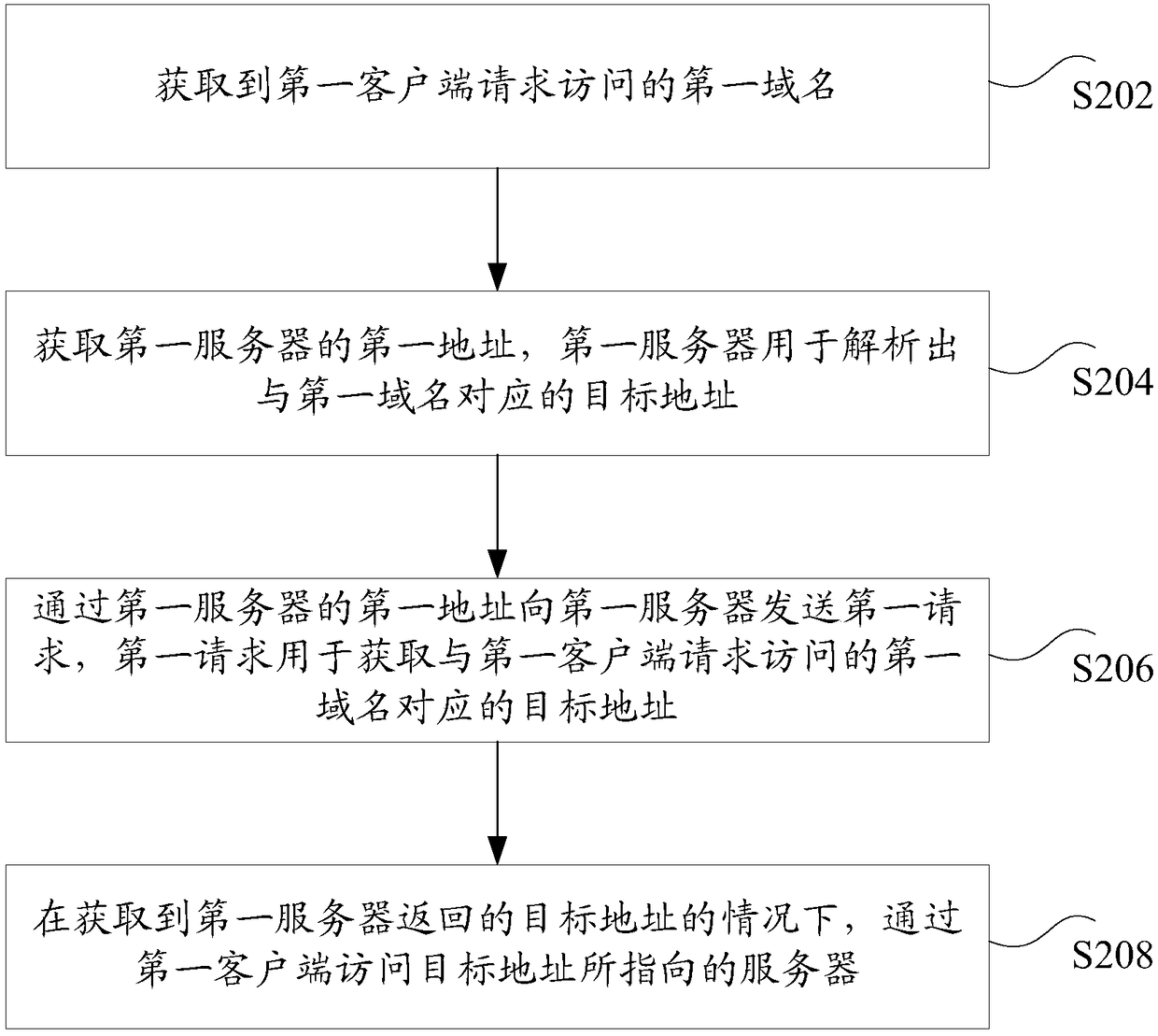
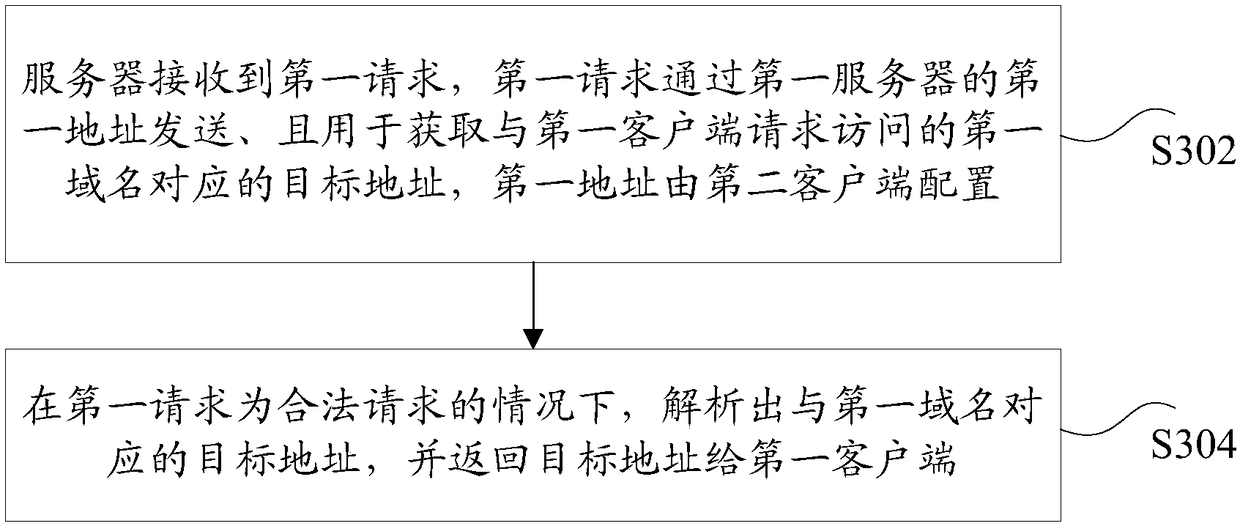
Domain name analysis method and device, storage medium and electronic device
ActiveCN108270882AFix technical issues with less securityImprove securityTransmissionDomain nameDNS hijacking
The invention discloses a domain name analysis method, a domain name analysis device, a storage medium and an electronic device. The method comprises the steps of acquiring a first domain name requested to be accessed by a first client; acquiring a first address of the first server, wherein the first server is used for analyzing a target address corresponding to the first domain name, the first address is configured by a second client, and the first client and the second client are installed on a same terminal; sending a first request to the first server via the first address of the first server, wherein the first request is used for acquiring the target address corresponding to the first domain name requested to be accessed by the first client; and accessing the server to which the targetaddress points via the first client under the condition of receiving the target address returned by the first server. According to the method, device, medium and electronic device provided by the invention, the technical problem that in related technologies, the network security is relatively low due to DNS hijacking is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
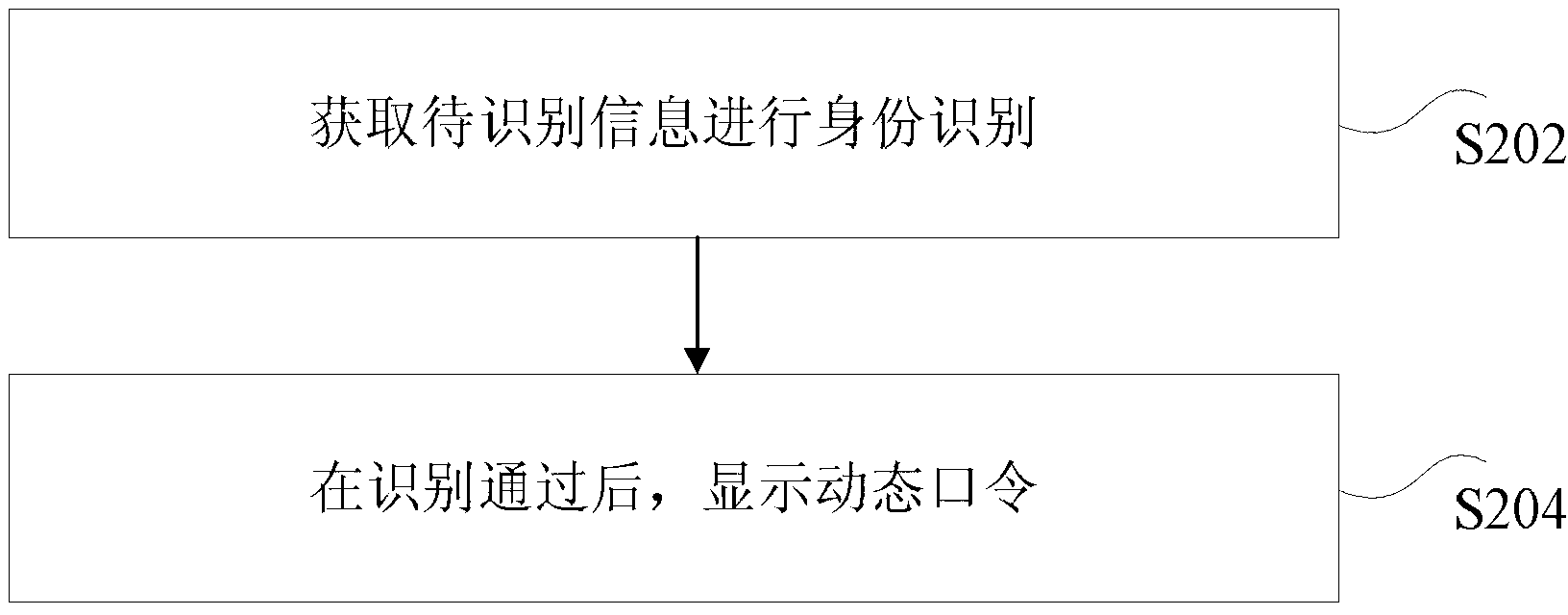
Display method and display device of dynamic token and dynamic password
InactiveCN103312509AFix technical issues with less securityImprove securityUser identity/authority verificationDigital data authenticationPasswordDisplay device
The invention discloses a display method and a display device of a dynamic token and a dynamic password, wherein the dynamic token comprises a biological recognizer and a display screen, wherein the biological recognizer is used for recognizing biological identity and indicating the display screen to display the dynamic token after recognition; and the display screen is used for displaying the dynamic password. With the adoption of the display method and the display device, the technical problem that the safety of the dynamic token is lower as the dynamic token is used without being authenticated, so that the technical effect of improving the safety of the dynamic token is achieved.
Owner:北京九州泰岳科技开发有限公司
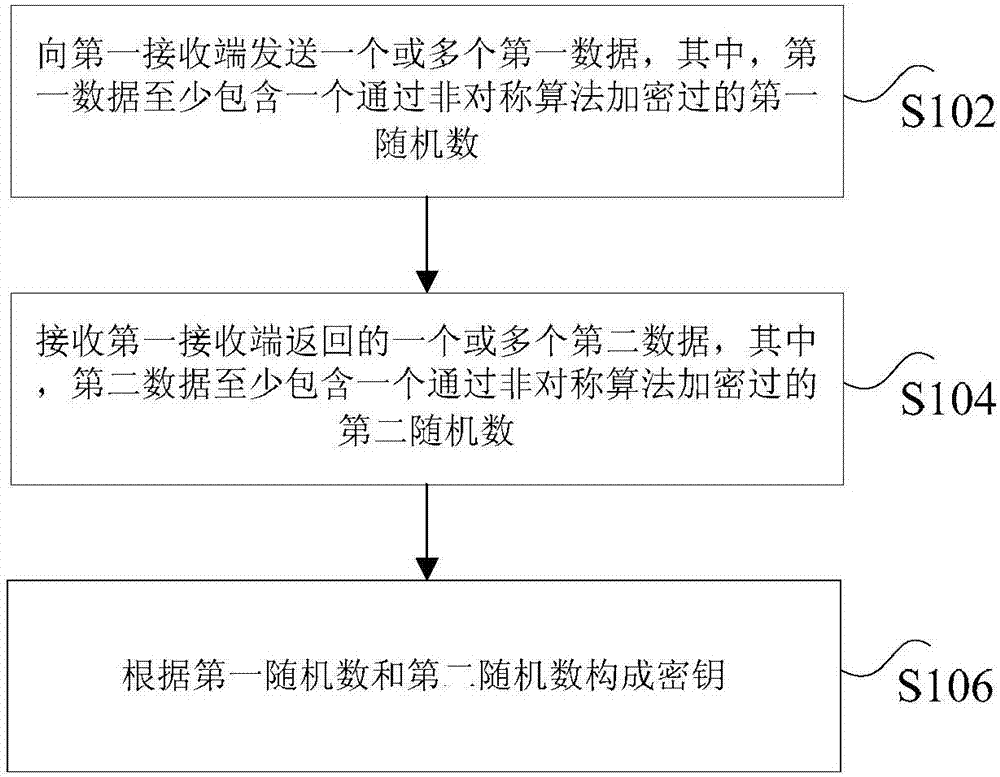
Data encryption method, apparatus and system
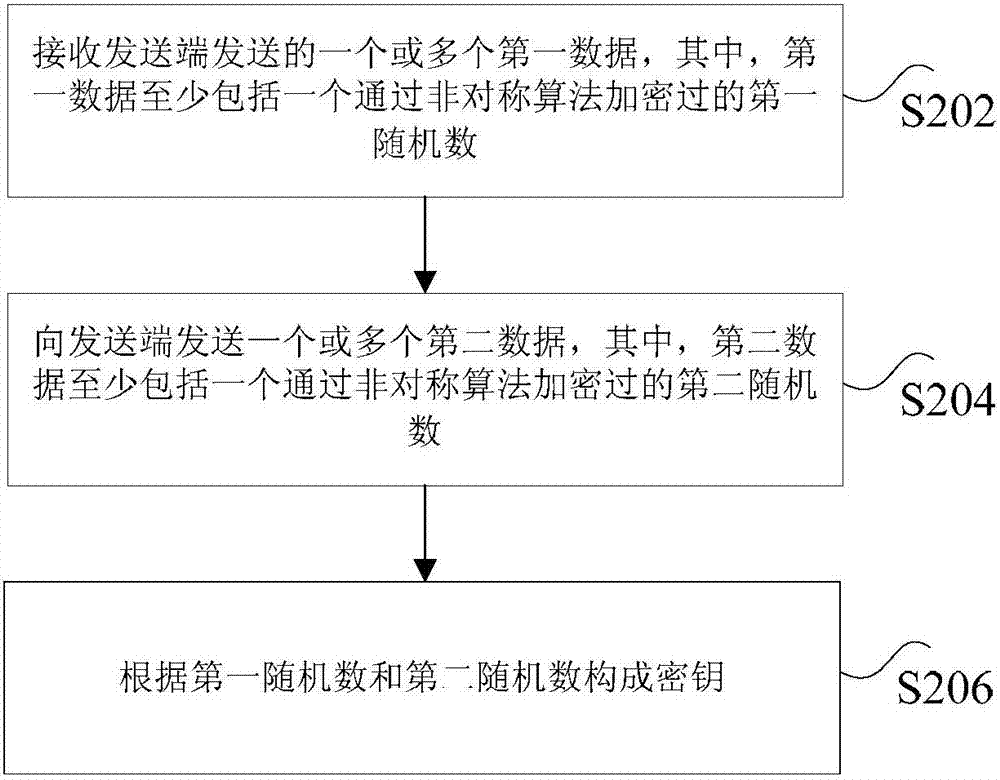
InactiveCN107040536AReduce data volumeImprove efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwarePlaintext
The invention discloses a data encryption method, apparatus and system. The data encryption method includes the steps: sending one or more first data to a first reception end, wherein the first data at least includes a first randomized number which is encrypted through an asymmetric algorithm; receiving one or more second data returned from the first reception end, wherein the second data at least includes a second randomized number which is encrypted through an asymmetric algorithm; and according to the first randomized number and the second randomized number, forming a secret key. The data encryption method, apparatus and system can solve the technical problem that in the prior art, industrial switches and energy control equipment transmit data through a plaintext transmission mode, so that safety is lower.
Owner:北京德威特电气科技股份有限公司
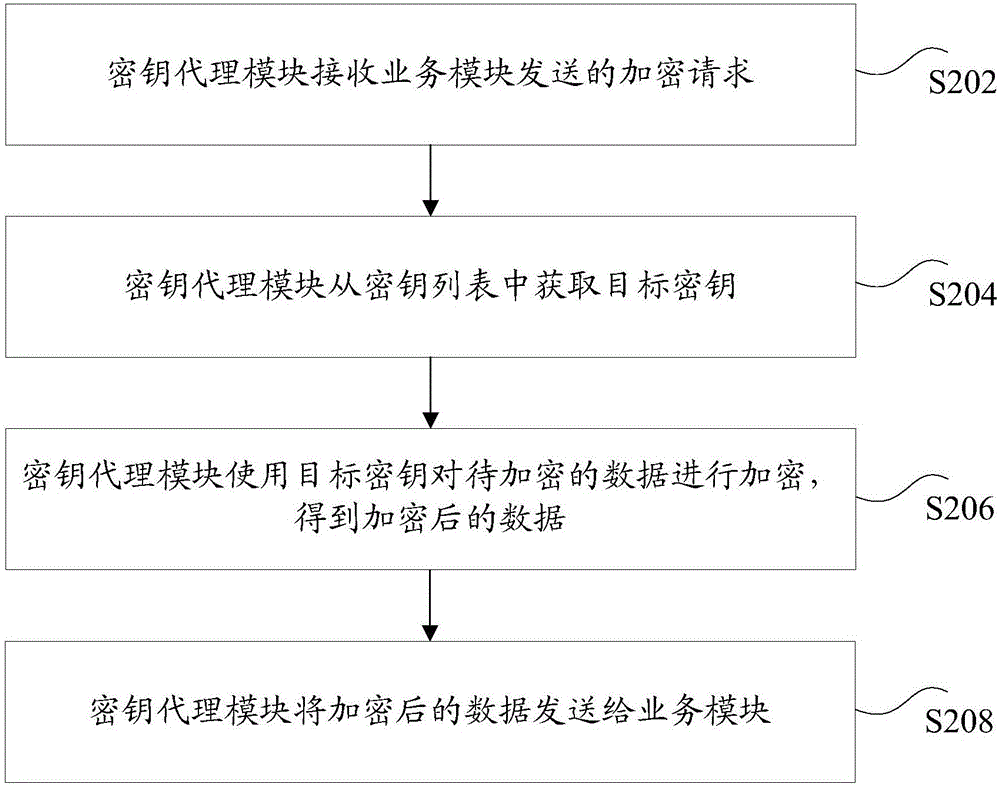
Business encryption/decryption method and device
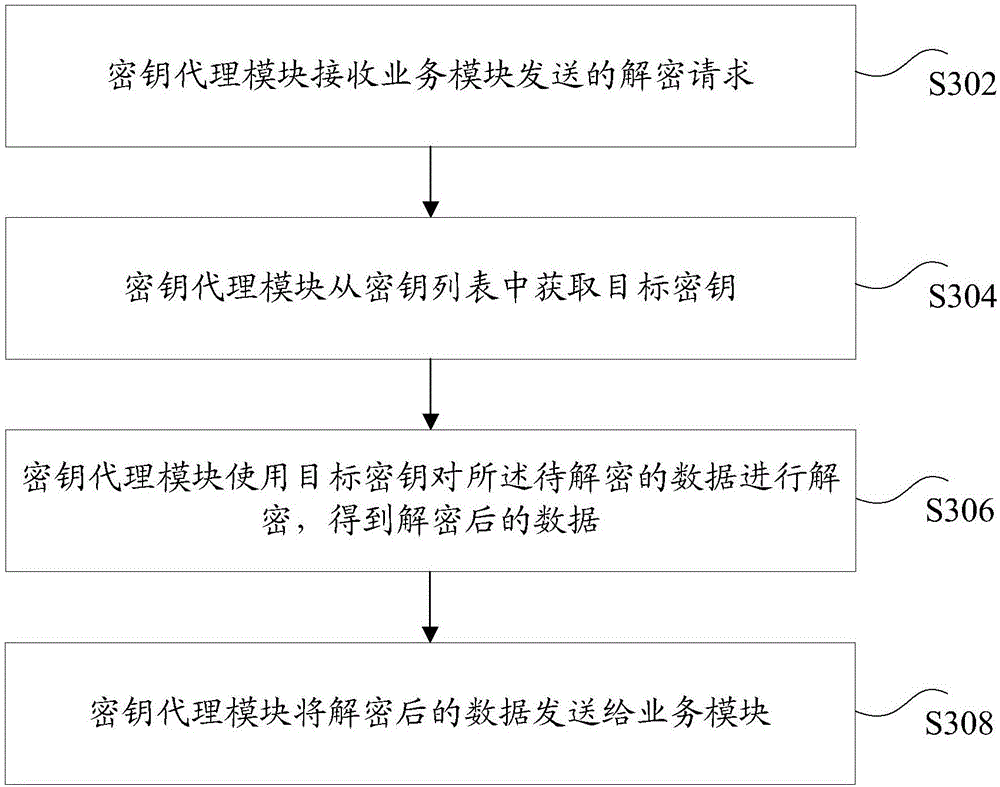
The invention discloses a business encryption / decryption method and a device. The method comprises steps that an encryption request sent by a business module is received by a secret key agent module, and the encryption request contains the to-be-encrypted data; a target secret key is acquired from a secret key list by the secret key agent module, and the secret key list is acquired from a secret key server in advance; the to-be-encrypted data is encrypted by the secret key agent module through utilizing the target secret key to acquire the encrypted data; the encrypted data is sent by the secret key agent module to the business module. Through the method, a technical problem of relatively low security of secret keys during business encryption in the prior art is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Data processing method used for electronic election
ActiveCN105827399AFix technical issues with less securityImprove securityKey distribution for secure communicationPublic key for secure communicationNetwork packetKey signature
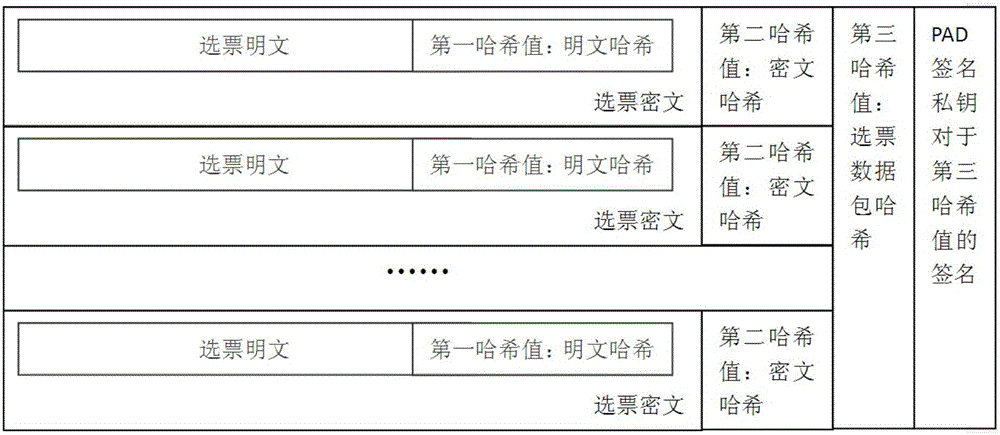
The invention discloses a data processing method used for electronic election. The method includes the following steps: a voting terminal encrypts electronic votes of voters into encrypted votes through an election encryption public key, and packs the encrypted votes into a vote data packet; the vote data packet attached with identification information is encrypted into an encrypted data packet through the election encryption public key, and the encrypted data packet signed by a terminal with a private key signature is sent to an election server; the election server judges the validity of the encrypted data packet through the identification information, verifies signature information of the encrypted data packet, and then stores in a vote database; and after at least two rounds of mixing operation is executed on the encrypted votes in the vote database, vote statistics are conducted, and the mixing operation includes performing re-encryption on each encrypted vote according to a preset encryption algorithm, and after re-encryption, executing disorder operation on each encrypted vote according to a preset disorder algorithm. The data processing method used for electronic election solves the technical problem in related technologies that the security is relatively low when on-site voting is performed.
Owner:JINHUA HONGZHENG TECH CO LTD
Service message transmission method and device, storage medium and electronic device
ActiveCN110099027AFix technical issues with less securityImprove securityTransmissionComputer hardwareNetwork service
The invention discloses a service message transmission method and device, a storage medium and an electronic device. The method comprises: acquiring a first service message sent by a first object to asecond object, and the first service message comprising a watermark feature code and a message load; matching the second group of fields in the watermark feature code through the first group of fields in the watermark feature code to obtain a matching result; and under the condition that the matching result indicates that the second group of fields are successfully matched, forwarding the first service message to the second object. According to the method and the device, the technical problem of low security of the network service in the prior art is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
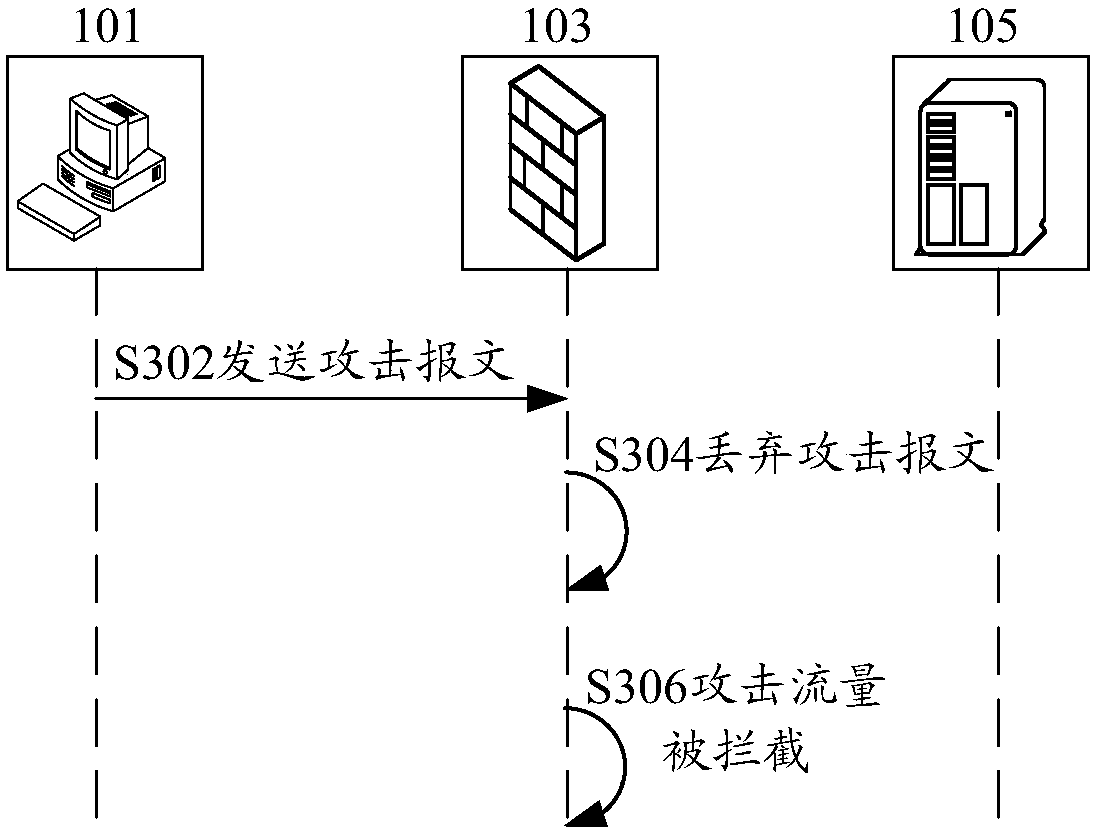
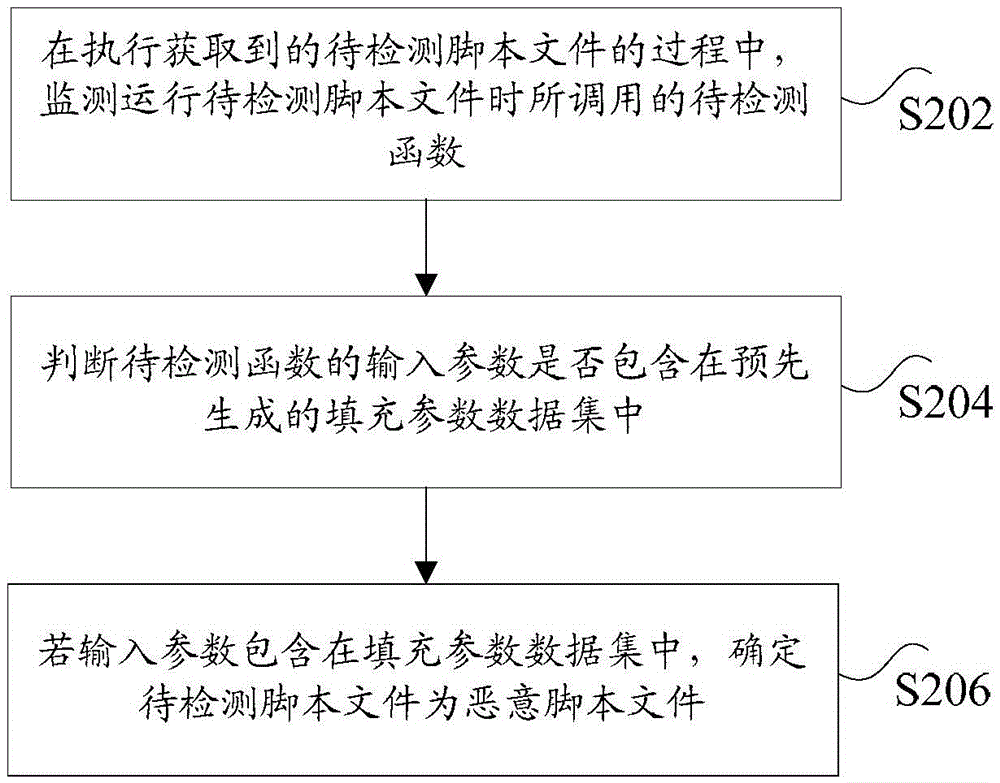
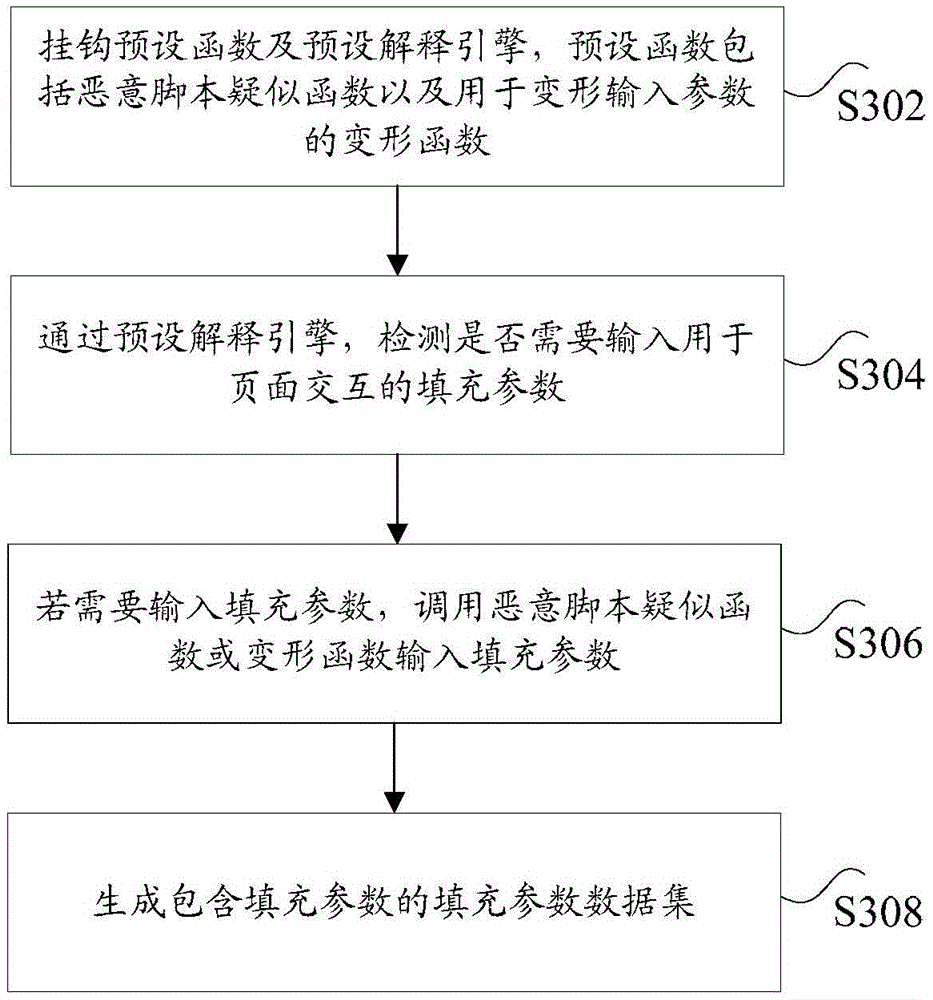
Method and device for detecting malicious script file
ActiveCN106815524AImprove securityFix technical issues with less securityPlatform integrity maintainanceData setFeature extraction
The application of the invention discloses a method and device for detecting a malicious script file. The method comprises the following steps: in the process of executing the acquired script file to be detected, monitoring the invoked function to be detected when running the script file to be detected; judging whether an input parameter of the function to be detected is included in a pre-generated filling parameter data set, wherein the filling parameter data set includes filling parameters for page interaction, the filling parameters are generated based on a pre-hooked default function and a default interpretation engine, the default function is used for inputting the filling parameters, and the default interpretation engine is used for detecting whether the filling parameters need to be input; if the input parameters are included in the filling parameter data set, determining that the script file to be detected is the malicious script file. The application of the invention solves the technical problem of low security of a web server caused by the situation that the malicious script file detection method based on static feature extraction easily fails to report a hidden malicious script file.
Owner:ALIBABA GRP HLDG LTD
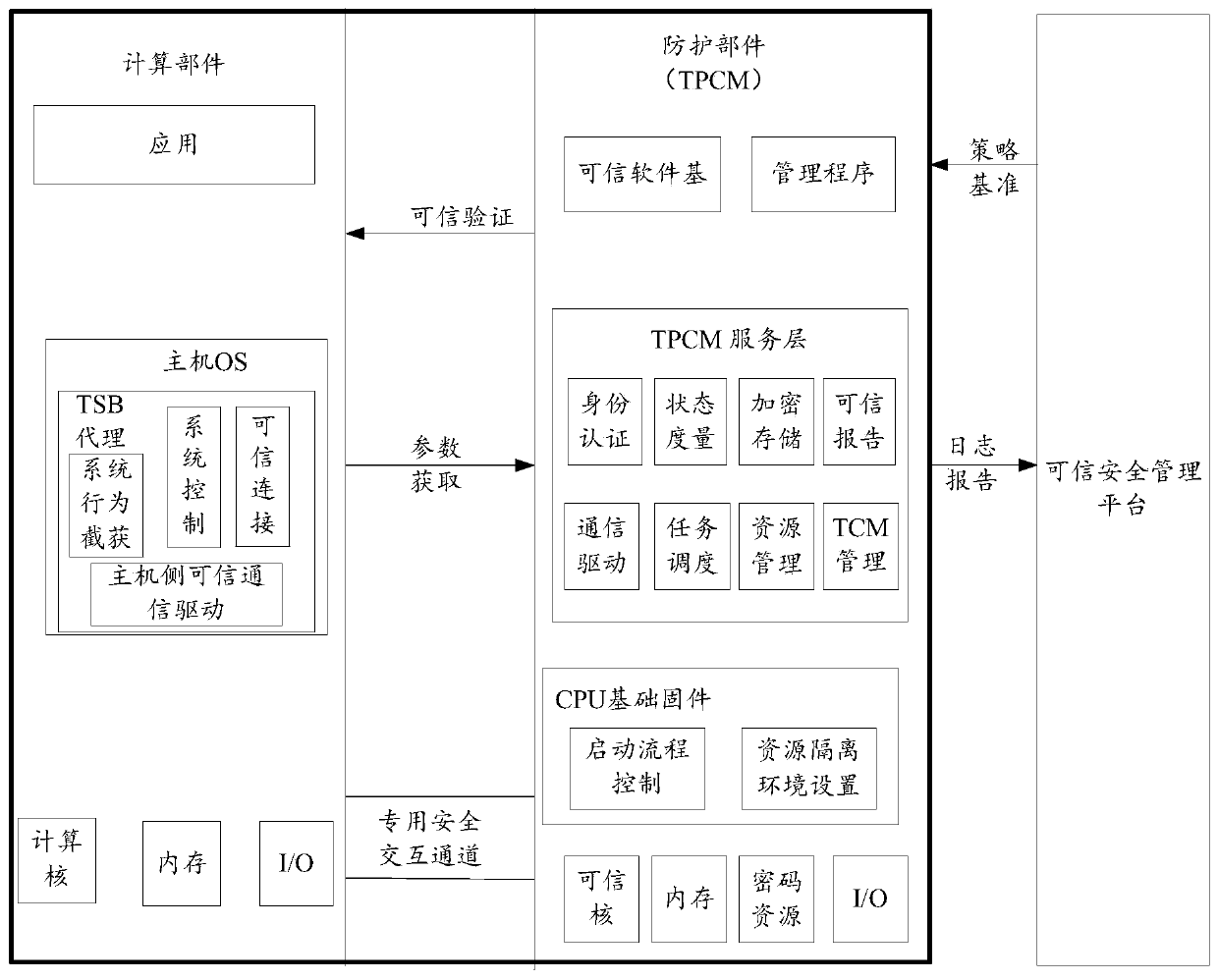
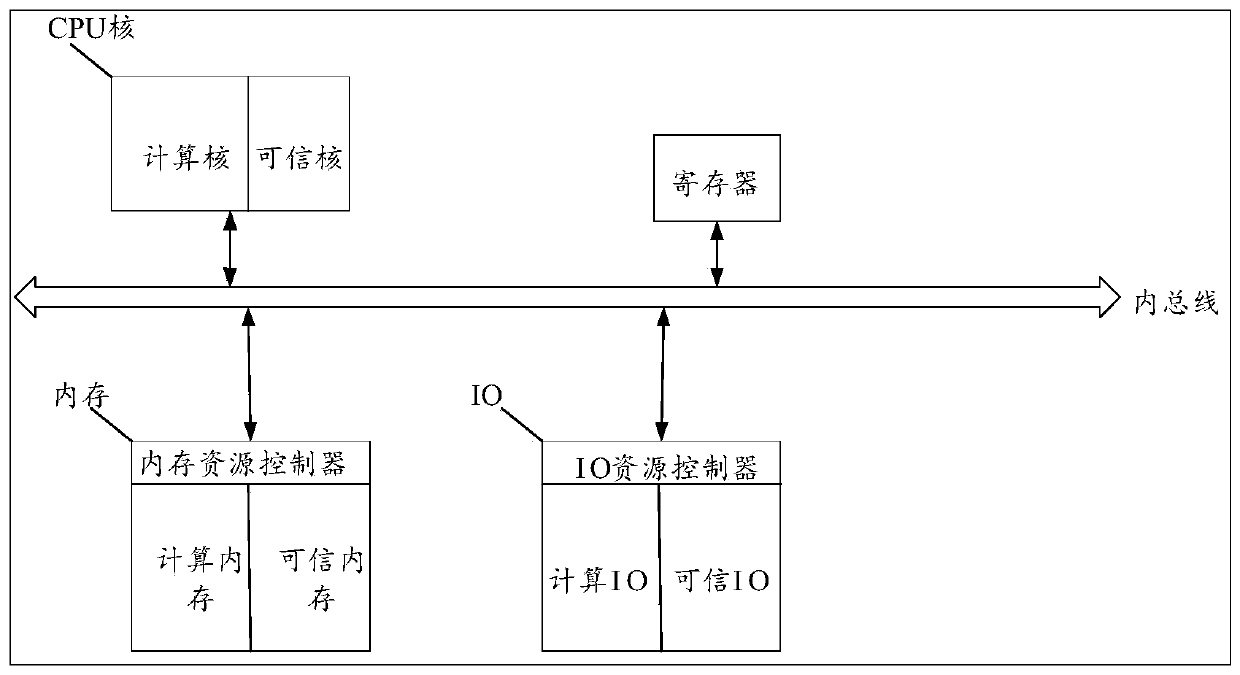
System interaction method and device of trusted computing platform based on dual-system architecture
ActiveCN110321235AFix technical issues with less securityImprove securityInterprogram communicationInternal/peripheral component protectionElectricityTrusted Computing
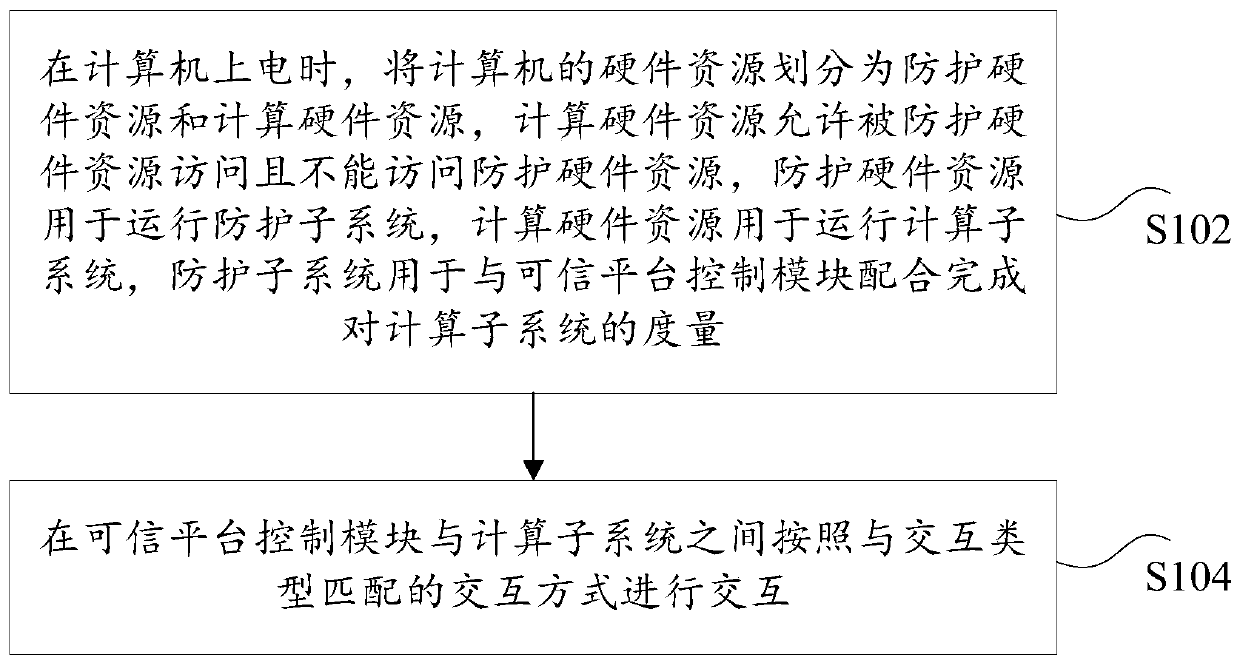
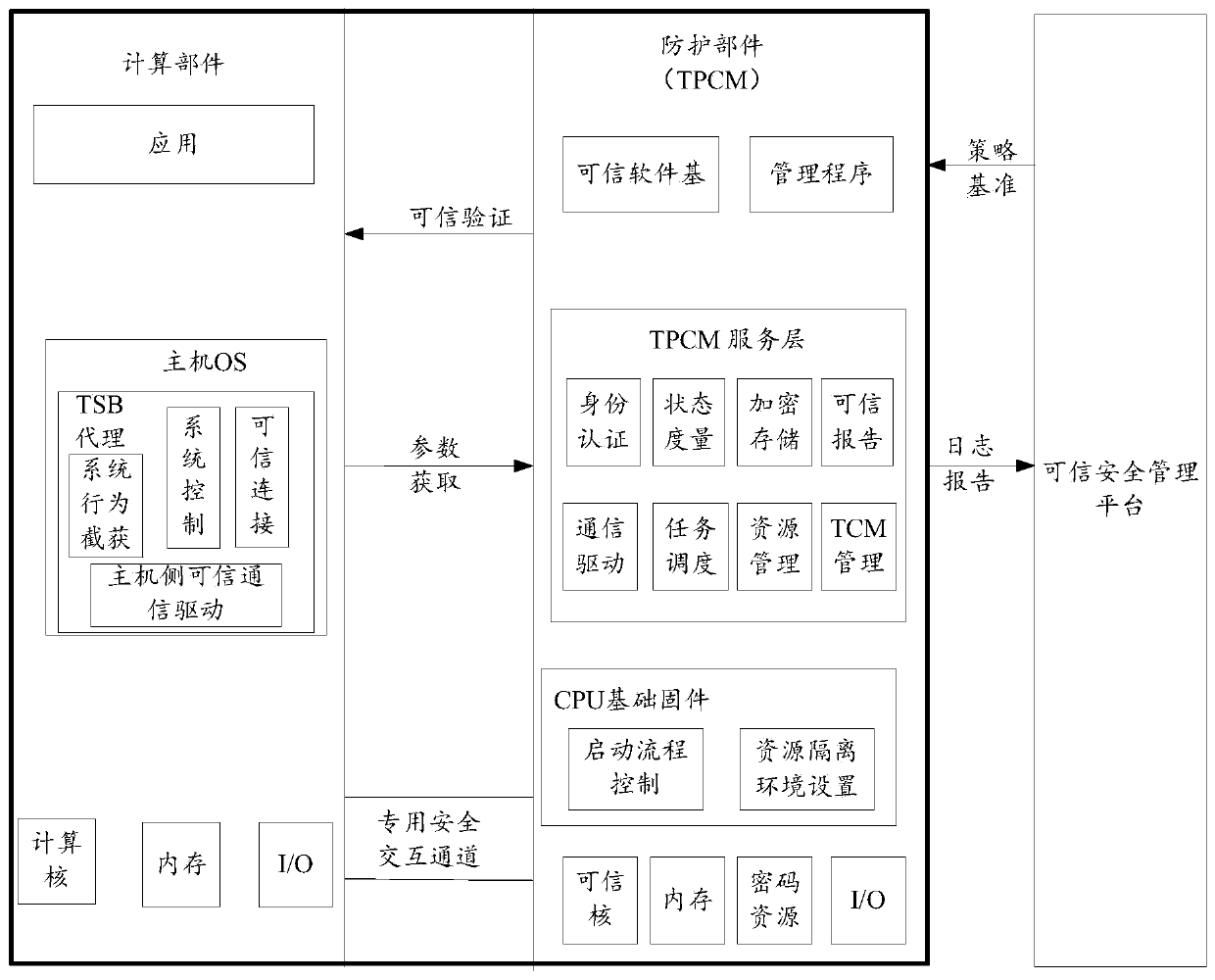
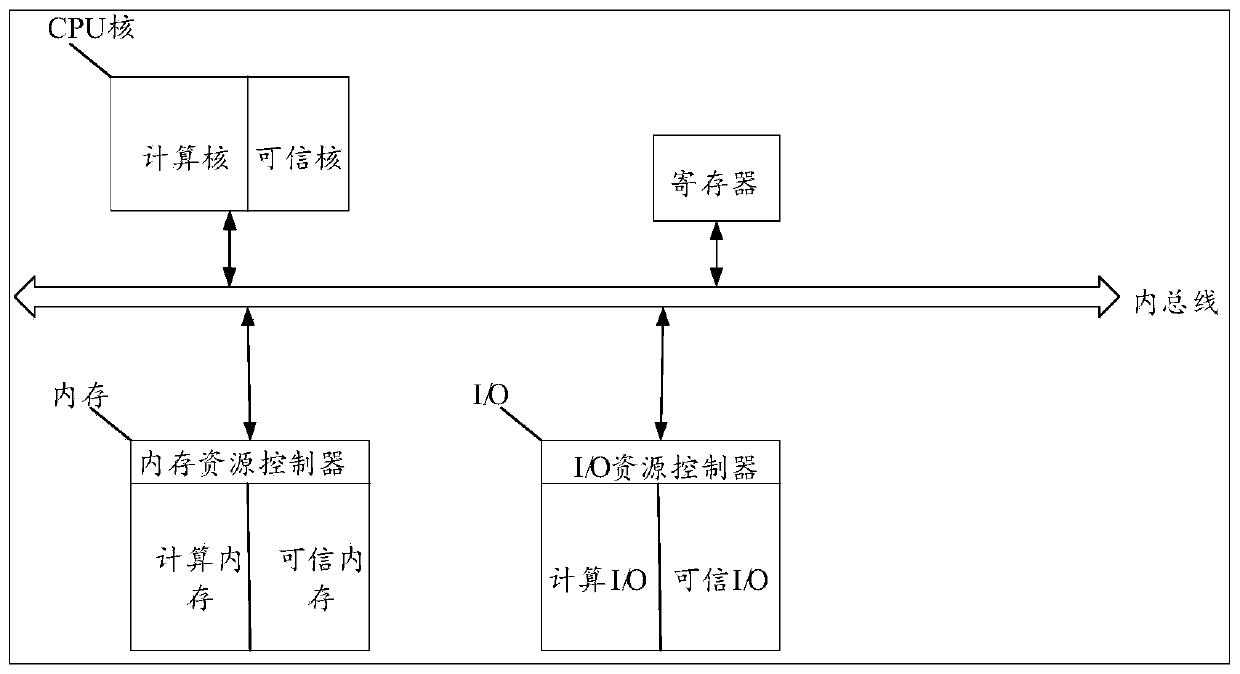
The invention discloses a system interaction method and device of a trusted computing platform based on a dual-system architecture. The method comprises the following steps: powering a computer, dividing hardware resources of a computer into protection hardware resources and calculation hardware resources; wherein the computing hardware resources are allowed to be accessed by the protected hardware resources and cannot be accessed by the protected hardware resources, using the protected hardware resources for operating the protection subsystem, using the computing hardware resources for operating the computing subsystem, and using the protection subsystem for cooperating with the trusted platform control module to complete measurement of the computing subsystem; and interacting between thetrusted platform control module and the computing subsystem according to an interaction mode matched with the interaction type. According to the invention, the technical problem of relatively low computer security in related technologies is solved.
Owner:BEIJING KEXIN HUATAI INFORMATION TECH
Static measurement method and device for trusted computing platform based on dual-system architecture
ActiveCN110334512AFix technical issues with less securityImprove securityPlatform integrity maintainanceTransmissionElectricityTrusted Computing
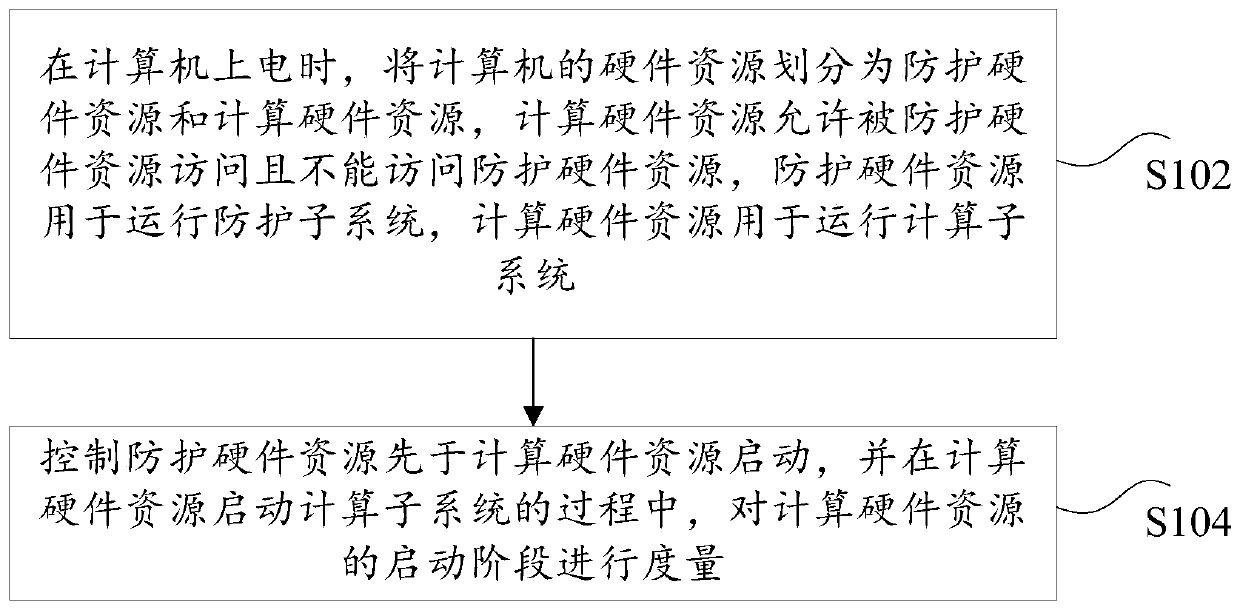
The invention discloses a static measurement method and device for a trusted computing platform based on a dual-system architecture. The method comprises the steps that when a computer is powered on,hardware resources of the computer are divided into protection hardware resources and calculation hardware resources, the calculation hardware resources allow the protected hardware resources to access and cannot access the protection hardware resources, the protection hardware resources are used for operating a protection subsystem, and the calculation hardware resources are used for operating acalculation subsystem; and the protection hardware resources are controlled to be started before the computing hardware resource, and he starting stage of the computing hardware resources is measuredin the process of starting the computing subsystem by the computing hardware resources. According to the invention, the technical problem of relatively low computer security in related technologies issolved.
Owner:BEIJING KEXIN HUATAI INFORMATION TECH
Management method and device for terminal permission
InactiveCN107872560AFix technical issues with less securityUnauthorised/fraudulent call preventionDigital data authenticationApproaches of managementComputer science
Owner:ZTE CORP
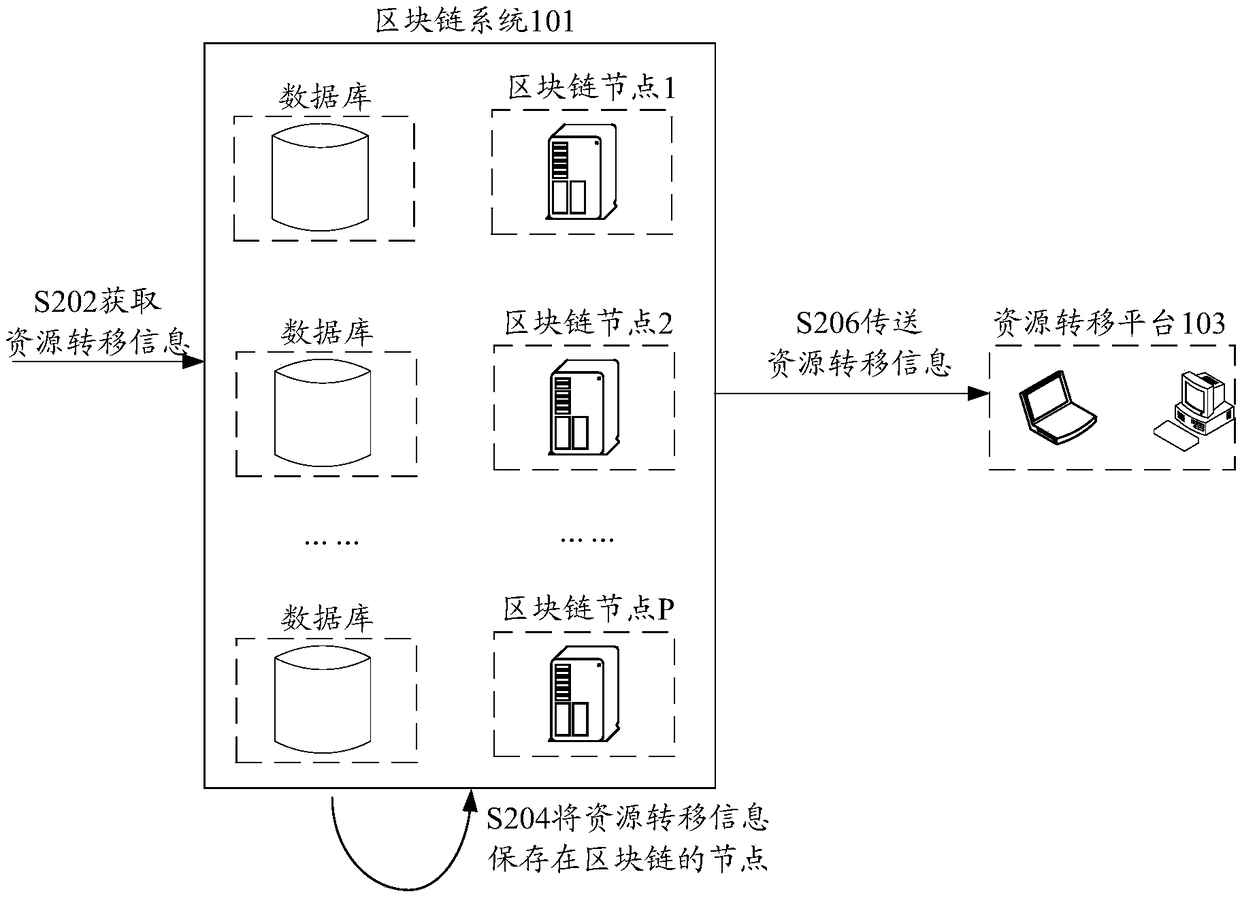
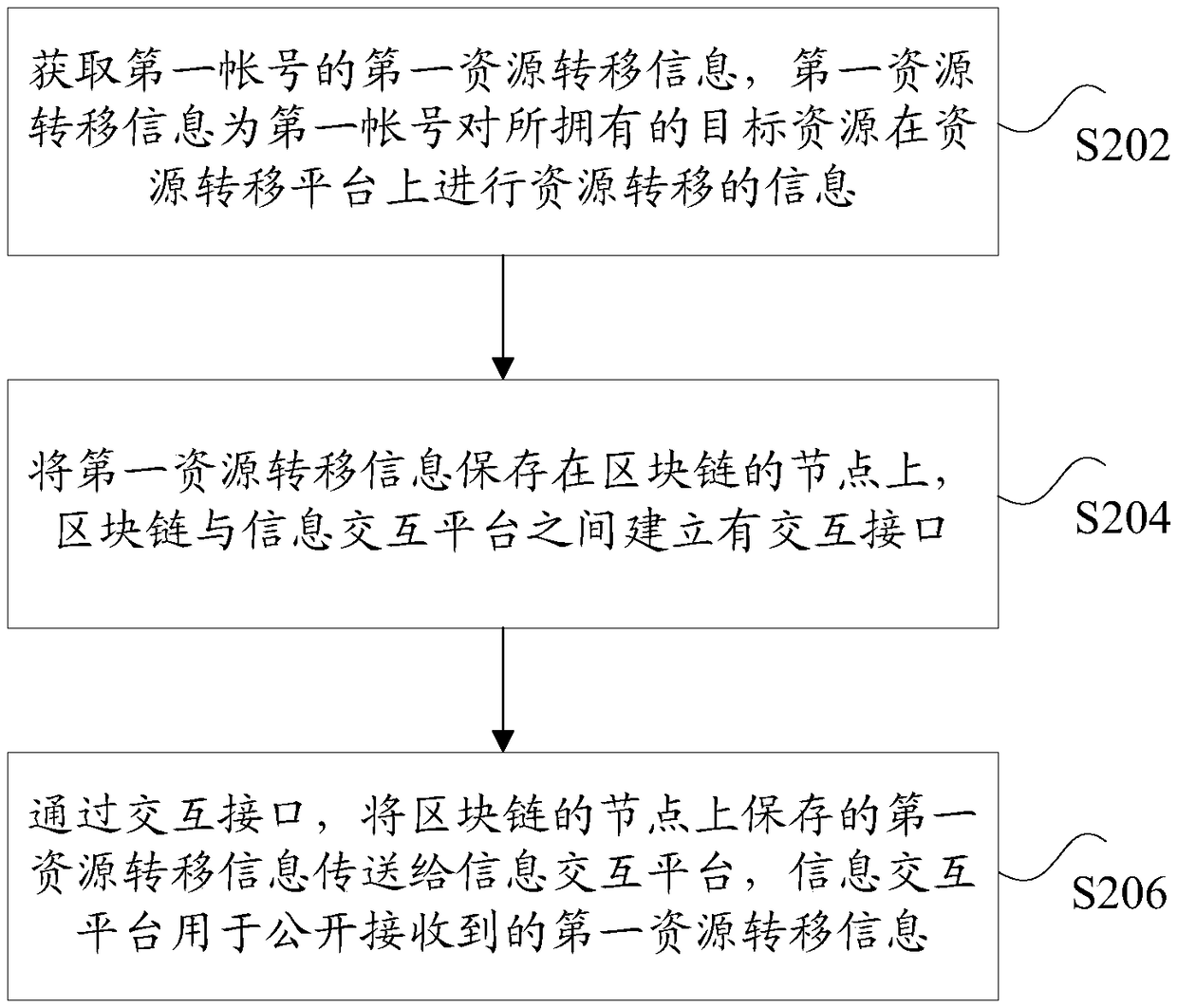
Transmission method and device of resource transferring information, storage medium and electrode device
ActiveCN108615195ACan not be tampered withTraceableFinancePayment protocolsResource transferBlockchain
The invention discloses a transmission method and device of resource transferring information, a storage medium and an electrode device. The method comprises steps of acquiring first resource transferring information of a first account, wherein the first resource transferring information is the information about resource transferring of target resources own by the first account on a resource transferring platform; storing the first resource transferring information to a node of a block chain, wherein an interaction port is arranged between the block chain and an information interaction platform; and through the interaction port, transmitting the first resource transferring information stored in the node of the block chain to the information interaction platform, wherein the information interaction platform is used for opening the received first resource transferring information. According to the invention, a technical problem of quite low safety of a resource transferring system in theprior art is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
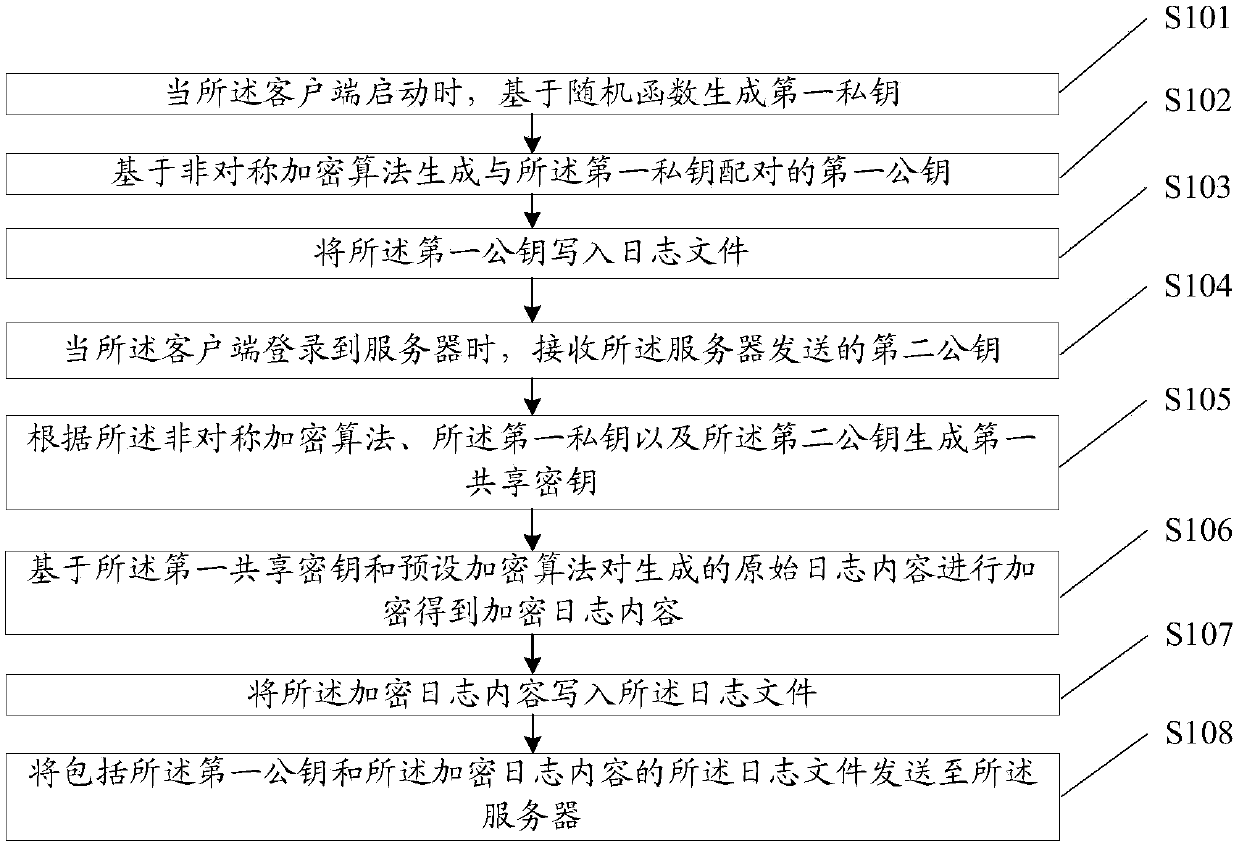
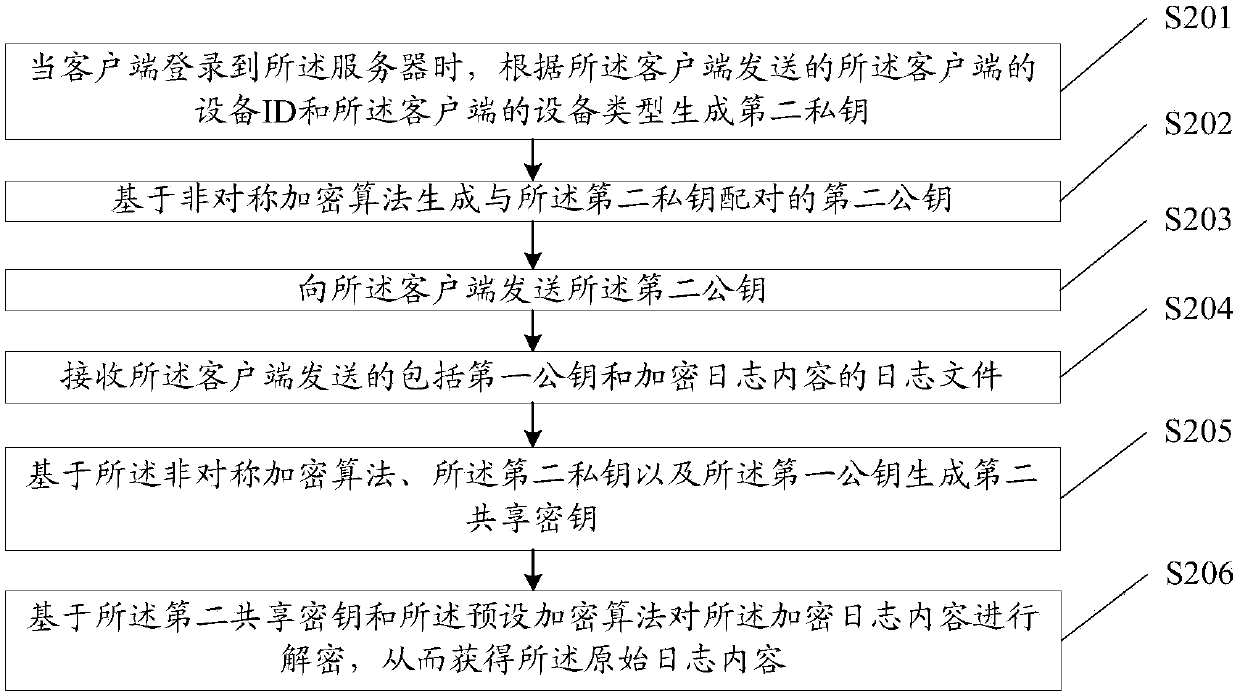
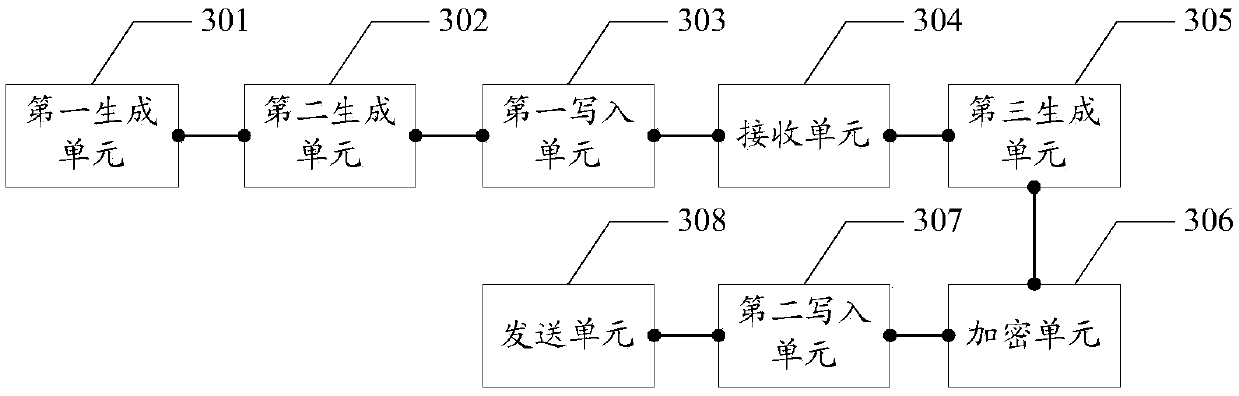
Log encryption method and device and log decryption method and device
ActiveCN110661748AImprove protectionIncrease the difficulty of crackingData switching networksLogfileEngineering
The embodiment of the invention provides a log encryption method and device and a log decryption method and device. The encryption method comprises the following steps: encrypting; client startup, generating a first private key based on the random function, generating a first public key paired with the first private key based on an asymmetric encryption algorithm, generating a first shared key according to an asymmetric encryption algorithm, the first private key and the second public key; and encrypting the original log content based on the first shared key and a preset encryption algorithm to obtain encrypted log content, writing the encrypted log content and the first public key into a log file, and sending the log file to the server, so that the server generates a second shared key based on the first public key, and decrypts the original log content based on the second shared key to obtain the original log content. The first shared key and the second shared key are changeable, so that the protection degree of the log file can be improved, and the safety is improved.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
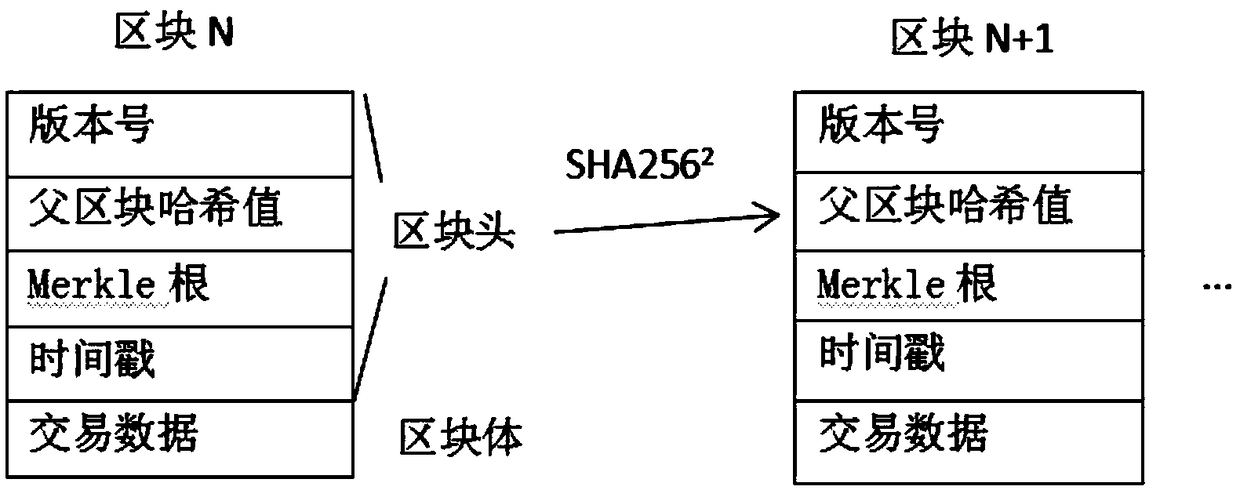
Block chain access authentication method and device, storage medium and electronic device
ActiveCN110602050AGuaranteed traceabilityFix technical issues with less securityDatabase distribution/replicationTransmissionSmart contractIndex system
The invention discloses a block chain access authentication method and device, a storage medium and an electronic device. The method comprises the following steps: the control center acquires an access request sent by the first account for requesting to access the block chain data, verifies a user certificate carried in the access request, obtains the position of the authority information of the first account in the block chain from an index system, and sends the position of the permission information in the block chain to the permission management smart contract, the permission management smart contract reads permission information of the first account at the position of the permission information in the block chain, and authenticates a first function to be accessed by the first account by using the permission information, sends an obtained authentication result to the control center, and allows the first account to access the first function by the control center according to the authentication result or refuses the first account to access the first function by the control center according to the authentication result. According to the method and the apparatus, the technical problem of relatively low security of permission data in related technologies is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Video stream address authentication method and device
ActiveCN108235067AGuaranteed legalityImprove securitySelective content distributionComputer hardwareUser authentication
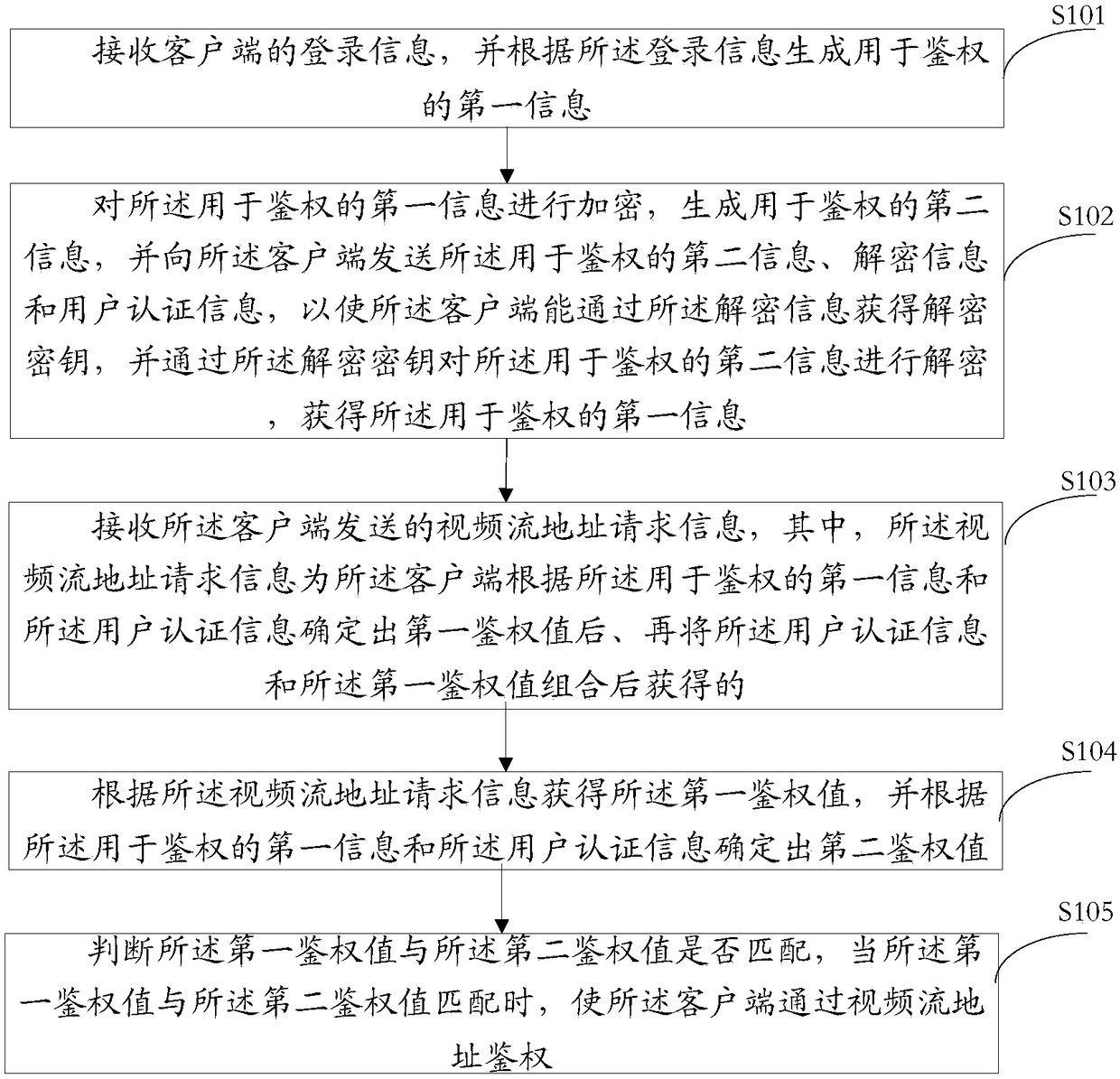
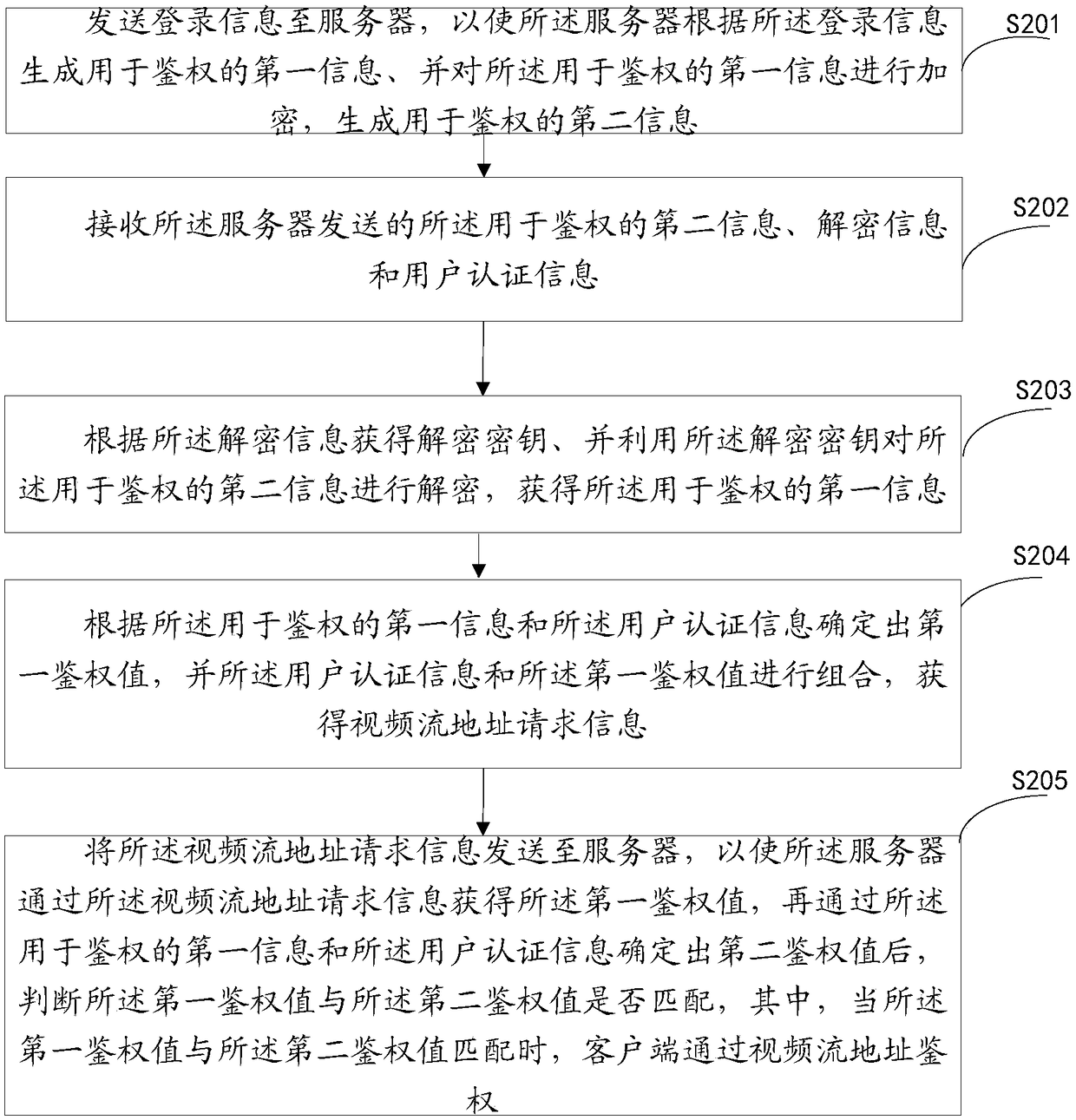
The embodiment of the invention provides a video stream address authentication method and device, wherein the method comprises the steps of: receiving the login information of a client side, and generating first information for authentication according to the login information; encrypting the first information for authentication, generating second information for authentication, and sending the second information for authentication, decryption information and user authentication information to the client side; receiving the video stream address request information sent by the client side; obtaining a first authentication value according to the video stream address request information, and determining a second authentication value according to the first information for authentication and the user authentication information; and, judging whether the first authentication value is matched with the second authentication value or not, and if so, enabling the client side to pass video streamaddress authentication. By means of the method provided in the invention, the technical problem that the security is relatively low due to the fact that a hacker easily obtains video stream address information in the prior art can be solved.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Data releasing method and device and terminal
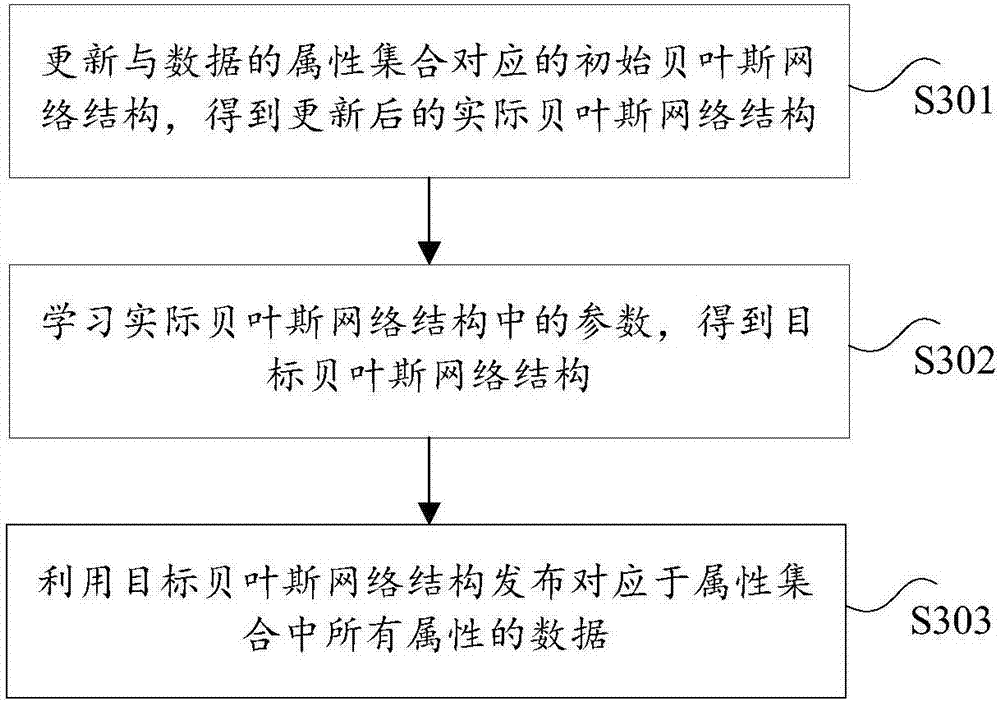
ActiveCN108009437AFix technical issues with less securityImprove securityMathematical modelsDigital data protectionDistribution methodNetwork structure
The invention provides a data releasing method and device and a terminal, wherein the method comprises the steps of updating an initial Bayesian network structure corresponding to an attribute set ofdata to obtain an updated actual Bayesian network structure; learning parameters in the actual Bayesian network structure to obtain a target Bayesian network structure; using the target Bayesian network structure to release the data corresponding to all of the attributes in the attribute set. The data distribution method and device and the terminal solve the technical problem of low security whenmulti-party data is released under a big data environment in related technologies.
Owner:ZTE CORP
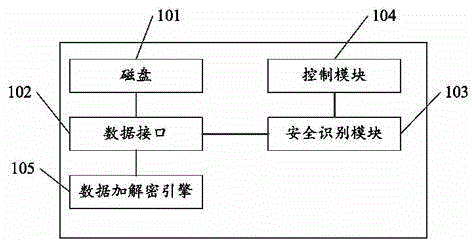
Data encrypted mobile hard disk
InactiveCN104318184AFix technical issues with less securityImprove securityInternal/peripheral component protectionSecurity levelData interface
The invention relates to the technical field of storage device security and discloses a data encrypted mobile hard disk comprising a disk, a data interface, a security identification module connected with the data interface, a control module and a data encryption and decryption engine. The data interface is arranged on the disk and used for data interaction with the outside; when the security identification module identifies that the security level of a device performing data interaction with the disk is lower than the preset security level, the control module controls to cut off connection of the device with data interaction with the disk; the data encryption and decryption engine is arranged to the data interface and used for performing encryption and decryption on data inputted to and outputted from the disk when the security identification module identifies that the security level of the device with data interaction with the disk is higher than or equal to the preset security level. Further, the technical effect of improvement of mobile hard disk security is realized.
Owner:成都卓微科技有限公司
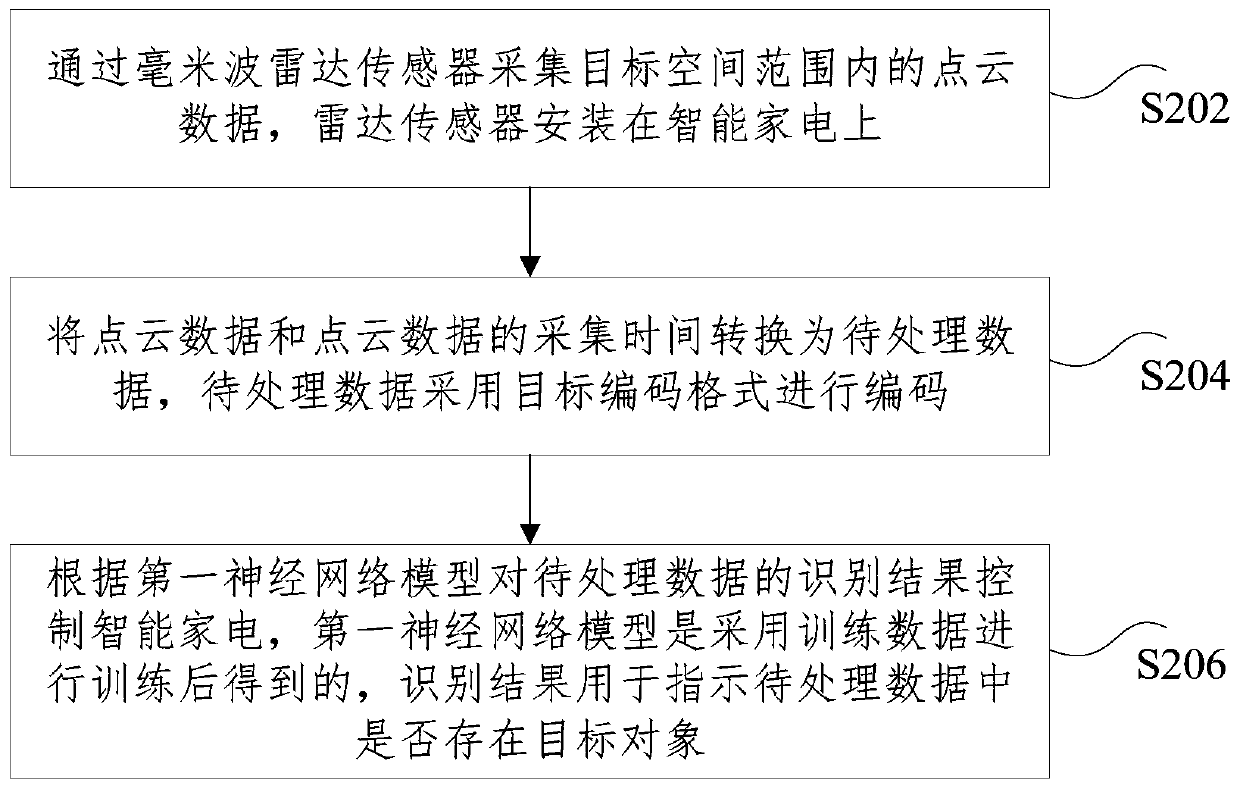
Intelligent household appliance, a control method and device thereof and a storage medium
ActiveCN110632849AHigh sensitivityPenetrableComputer controlProgramme total factory controlPoint cloudAcquisition time
The invention discloses an intelligent household appliance, a control method and device thereof and a storage medium. The method comprises the steps as follows: point cloud data in a target space range is collected through a millimeter wave radar sensor which is installed on an intelligent household appliance; the point cloud data and the collection time of the point cloud data are converted intoto-be-processed data, and the to-be-processed data is encoded in a target encoding format; and the intelligent household appliance is controlled according to an identification result of the to-be-processed data by a first neural network model, wherein the first neural network model is obtained after training by adopting training data, the training data with mark information is encoded in the target encoding format, the mark information is used for marking whether a target object exists in the training data or not, and the identification result is used for indicating whether the target object exists in the to-be-processed data or not. According to the invention, the technical problem of low safety of the intelligent household appliance in the prior art is solved.
Owner:GREE ELECTRIC APPLIANCES INC +1
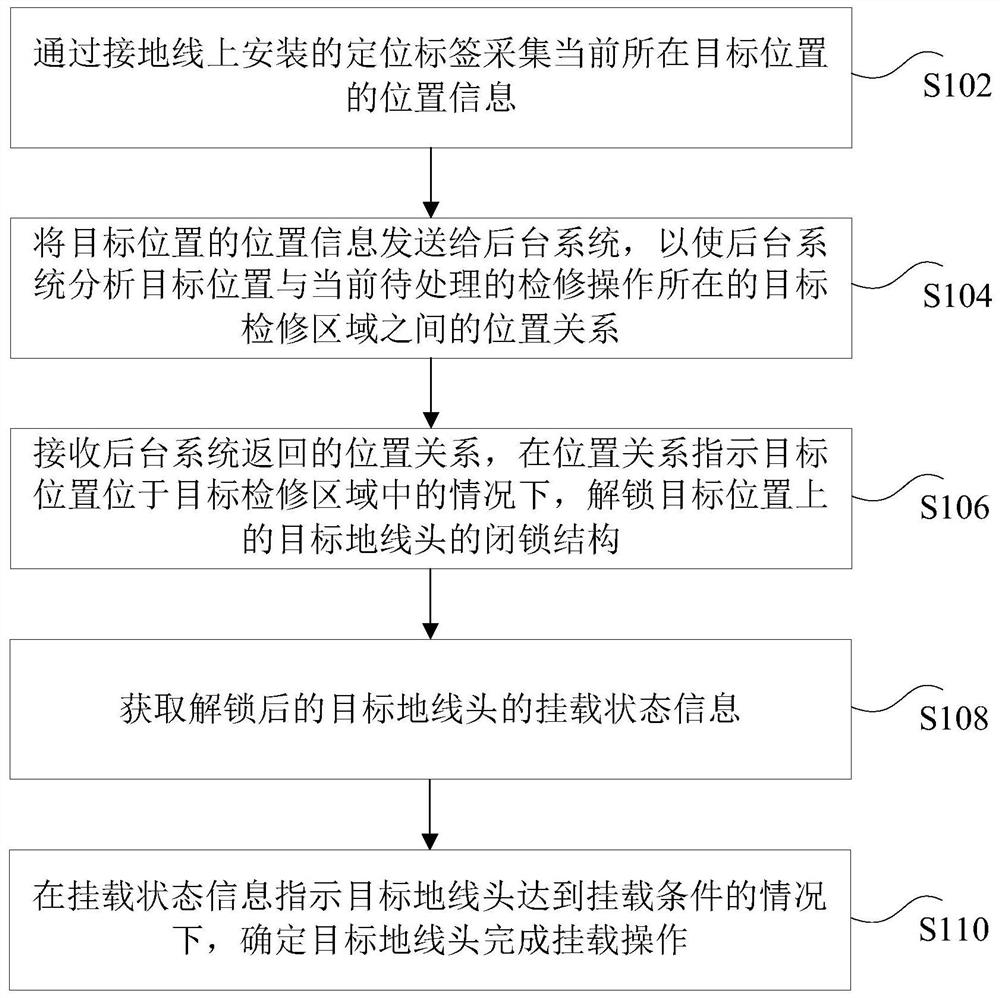
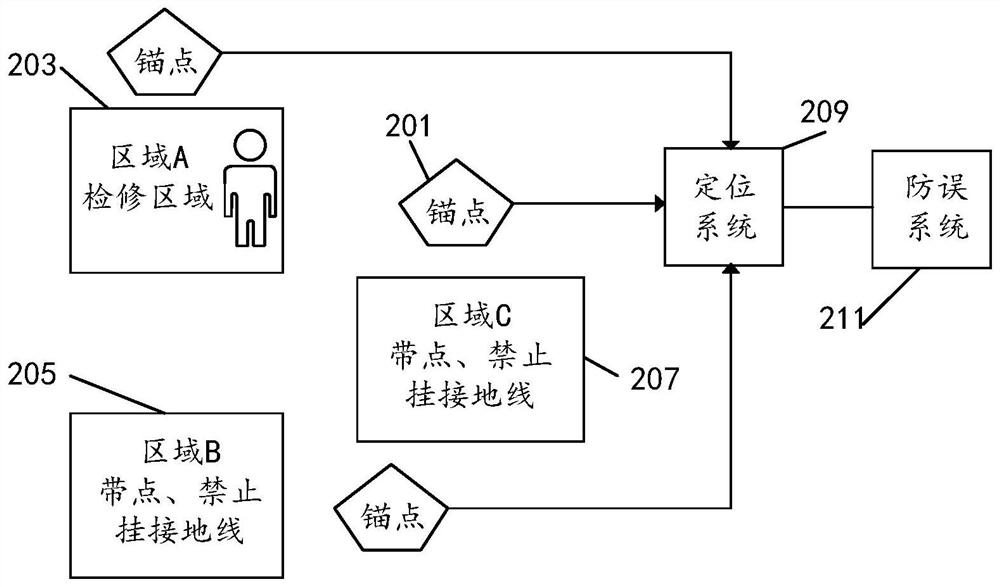
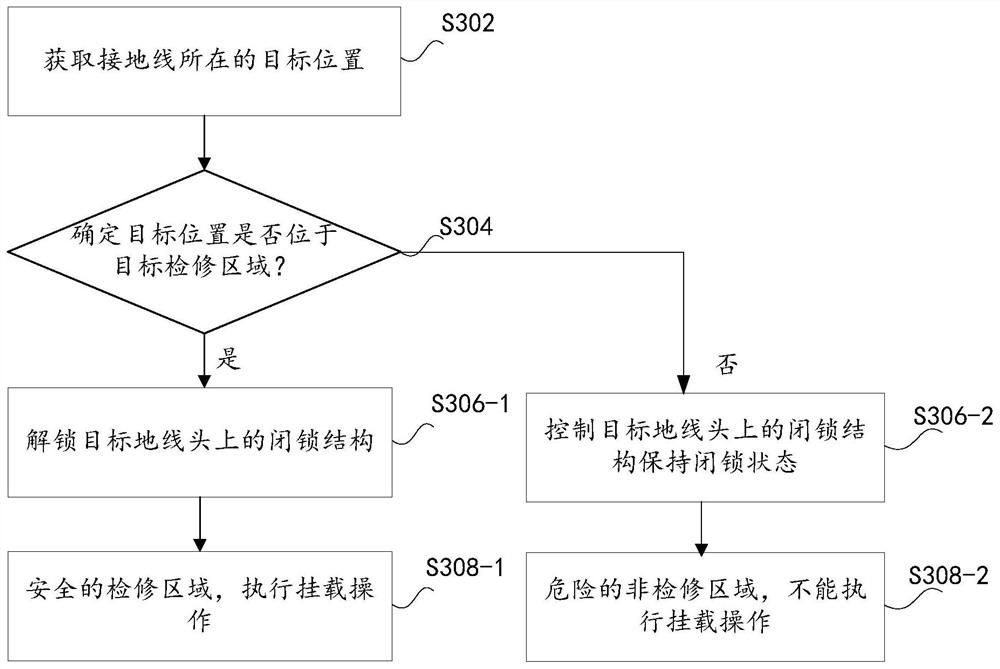
Grounding wire hanging method and device, and storage medium
PendingCN112072525AEnsure safetyAccurately determineMeasurement devicesCo-operative working arrangementsControl theoryMechanical engineering
The invention discloses a grounding wire hanging method and device, and a storage medium. The method comprises the following steps: acquiring position information of a current target position througha positioning label mounted on a ground wire; sending the position information of the target position to a background system, and enabling the background system to analyze a position relationship between the target position and a target maintenance area where the current to-be-processed maintenance operation is located; receiving the position relationship returned by the background system, and unlocking a locking structure of a target ground wire head at the target position under the condition that the position relationship indicates that the target position is located in the target maintenance area; acquiring mounting state information of the unlocked target ground wire head; and under the condition that the mounting state information indicates that the target ground wire head reaches themounting condition, determining that the target ground wire head completes the mounting operation. The technical problem that in the prior art, the safety of hanging operation is low is solved.
Owner:ZHUHAI UNITECH POWER TECH CO LTD
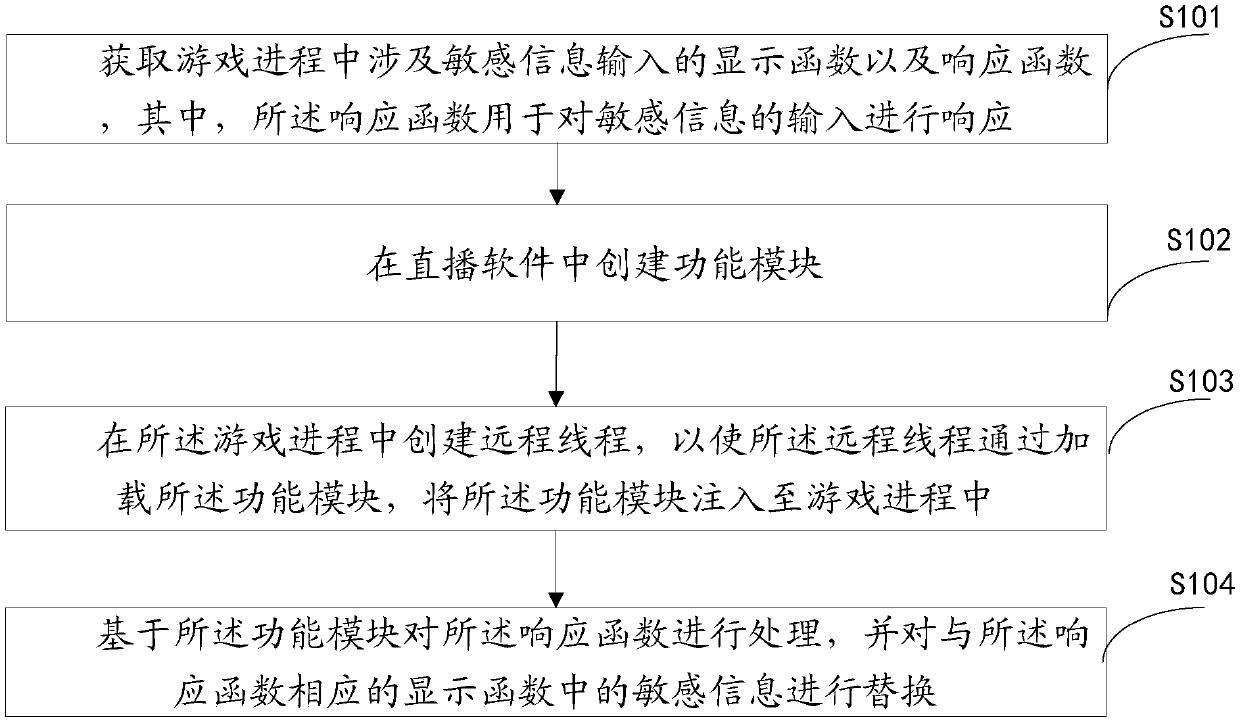
Method and device for preventing information leakage in live game broadcasting
ActiveCN107742077AImprove securityPrevent leakagePlatform integrity maintainanceTransmissionComputer moduleHuman–computer interaction
The invention discloses a method and device for preventing information leakage in live game broadcasting. The method includes the steps of obtaining a display function and response function which relate to input of sensitive information in a game process, wherein the response function is used for responding to the input of the sensitive information; creating a function module in live software; creating a remote thread in the game process to make the remote thread inject the function module into the game process by loading the function module; on the basis of the function module, processing theresponse function, and replacing the sensitive information in the display function corresponding to the response function. The method and device for preventing the information leakage in live game broadcasting solve the technical problem that in live game broadcasting methods of the prior art, the safety is low since information is easy to leak.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
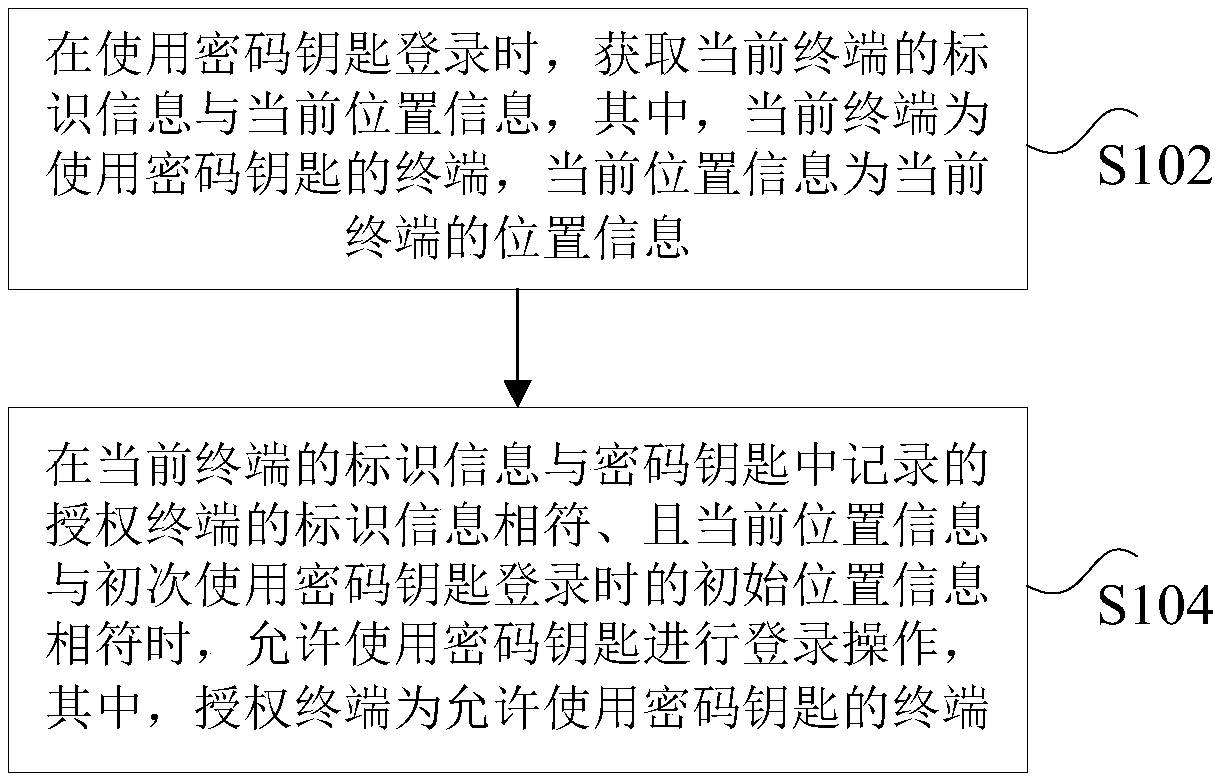
Method and device for logging using password key, storage medium and processor
ActiveCN108985040AImprove information securityImprove securityDigital data authenticationInitial UsagePassword
The invention discloses a method and a device for logging using a password key, a storage medium and a processor. The method comprises the following steps: obtaining identification information and current position information of a current terminal when logging in with a password key, wherein the current terminal is a terminal using the password key, and the current position information is positioninformation of the current terminal; , and allowing the login operation to be performed using the password key when the identification information of the current terminal coincides with the identification information of the authorized terminal recorded in the password key and the current position information coincides with the initial position information at the time of first login using the password key, wherein the authorized terminal is a terminal permitting the use of the password key. The invention solves the technical problem that the use range of the password key is not limited by therelated technology, and the information security is low.
Owner:BEIJING HAITAI FANGYUAN HIGH TECH
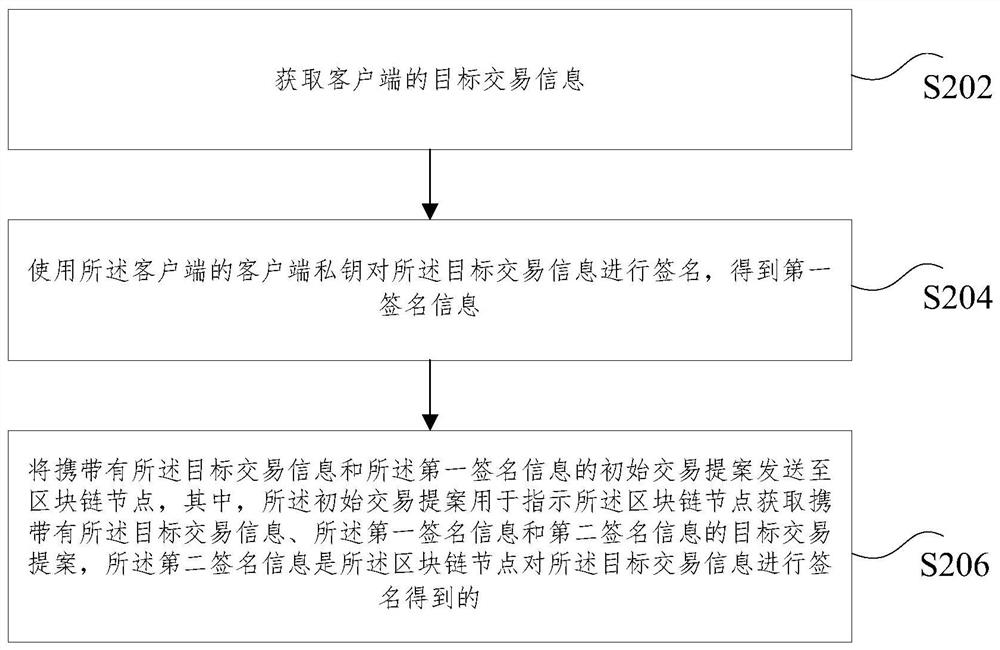
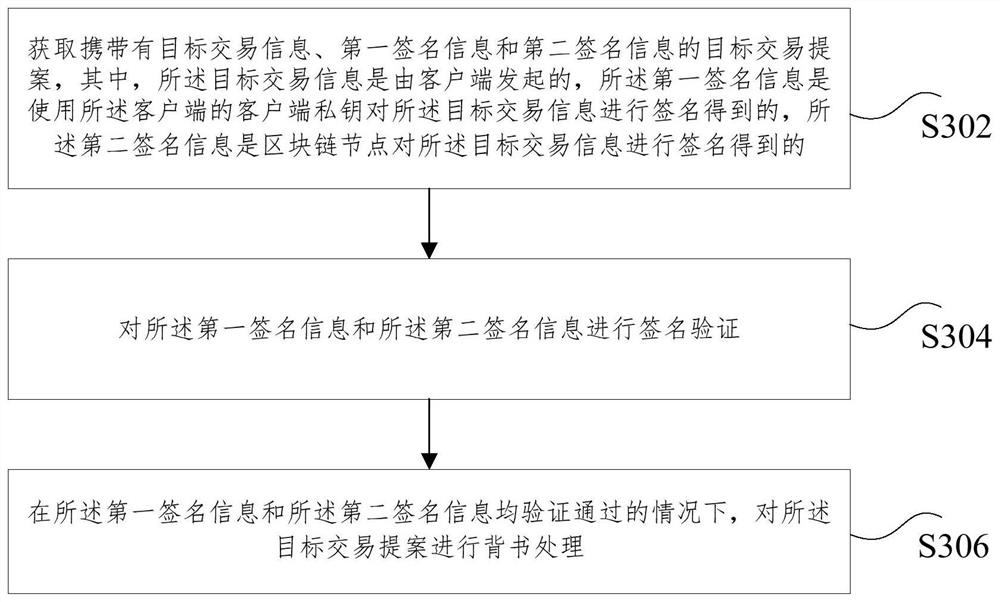
Transaction proposal processing method, device and system, storage medium and electronic device
PendingCN111815321AImprove securityFix technical issues with less securityUser identity/authority verificationDigital data protectionComputer networkEngineering
The invention relates to a transaction proposal processing method, device and system, a storage medium and an electronic device. The method comprises the steps: obtaining target transaction information of a client; signing the target transaction information by using a client private key of the client to obtain first signature information; sending an initial transaction proposal carrying the targettransaction information and the first signature information to the blockchain node, wherein the initial transaction proposal is used for indicating the blockchain node to obtain a target transactionproposal carrying target transaction information, first signature information and second signature information, and the second signature information is obtained by signing the target transaction information by the blockchain node. According to the application, the technical problem that the verification process of the transaction proposal is relatively low in safety in related technologies is solved.
Owner:BEIJING KINGSOFT CLOUD NETWORK TECH CO LTD
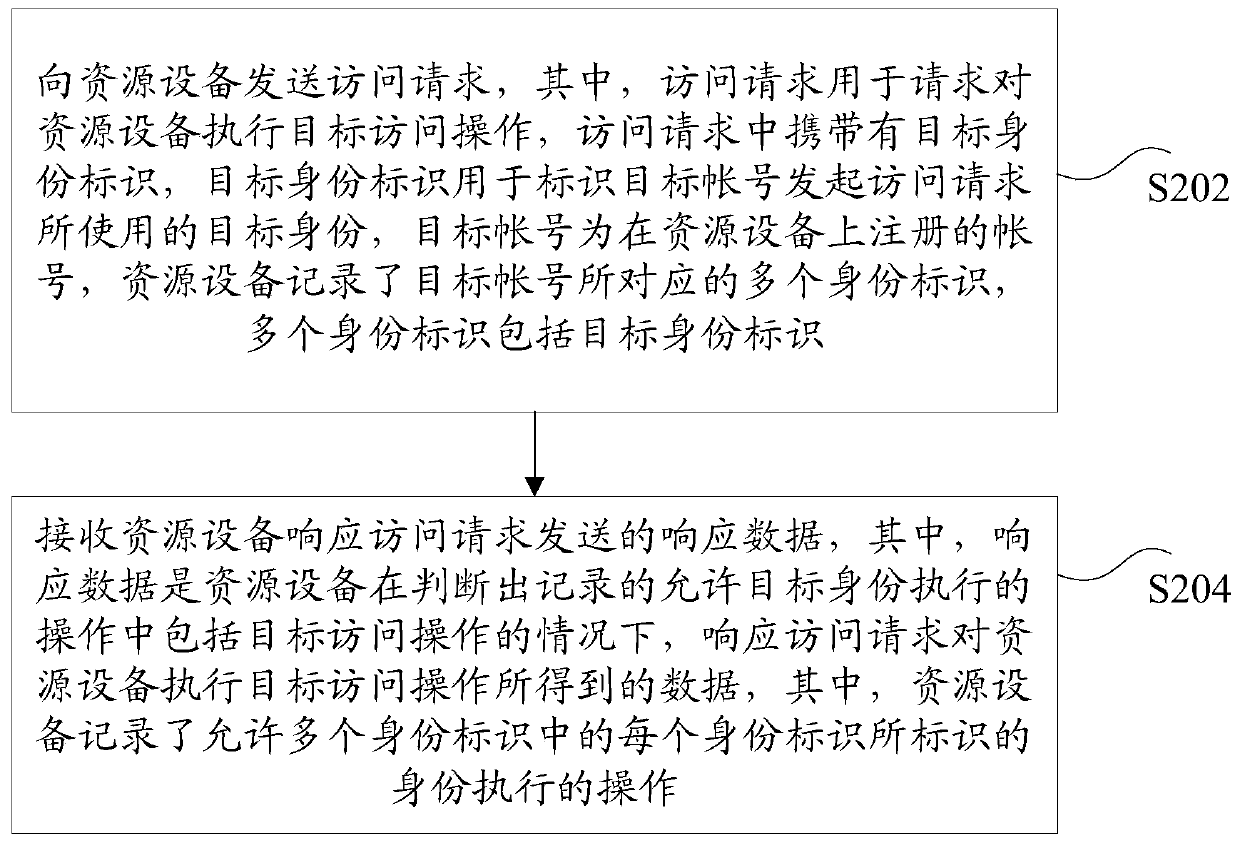
Method and device for executing access operation
ActiveCN110351254AImprove securityFix technical issues with less securityTransmissionOperating systemService system
The invention discloses a method and a device for executing an access operation. The method comprises the following steps: receiving an access request sent by a target account; judging whether the operation which is recorded by the service system and allows the target identity to be executed comprises a target access operation, wherein the service system records the operation which allows the identity identified by each identity identifier in the plurality of identity identifiers to be executed; and under the condition that it is judged that the operation allowed to be executed by the target identity and recorded by the service system comprises the target access operation, responding to the access request to execute the target access operation on the service system. According to the methodand the device, the technical problem of relatively low security of executing the access operation on the service system is solved.
Owner:朗新数据科技有限公司
Equipment capable of controlling smart household appliances wirelessly
InactiveCN105487400AFix technical issues with less securityImprove securityComputer controlProgramme total factory controlWireless controlInductor
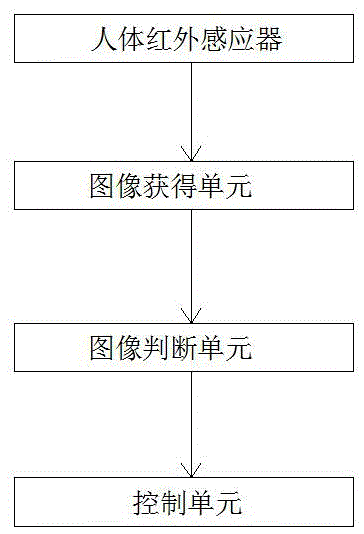
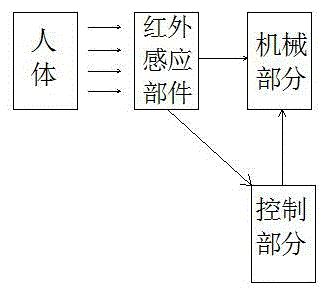
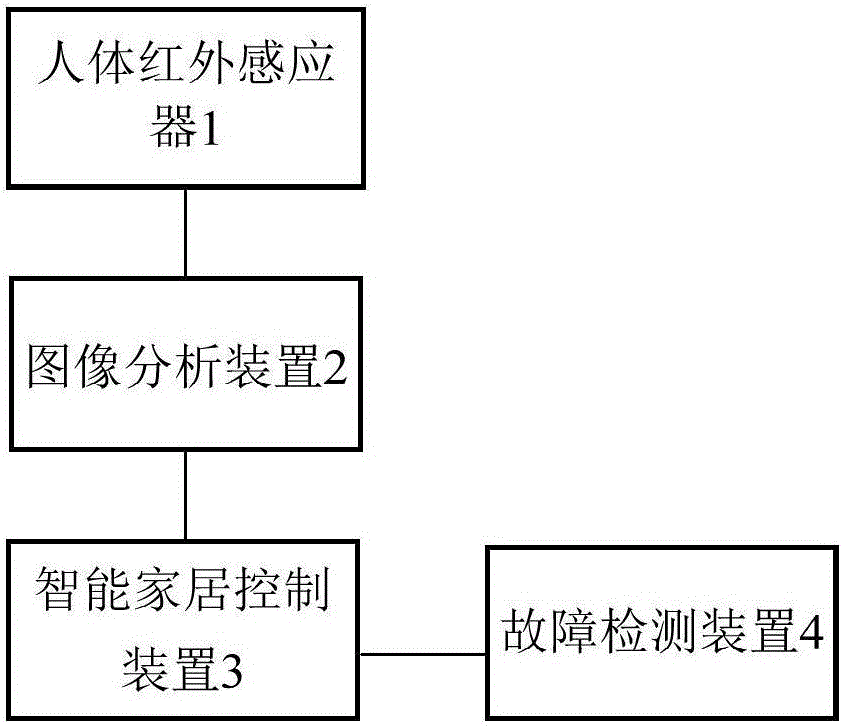
The invention relates to the field of smart home, in particular to equipment capable of controlling smart household appliances wirelessly. Smart home control center equipment is connected with N smart home devices and comprises a human body infrared inductor, an image acquiring unit, an image judging unit and a control unit which are connected in sequence, the human body infrared inductor comprises a lens, a photosensitive element and a photosensitive circuit and further comprises a mechanical part driven by a control part, and the photosensitive element is arranged on the mechanical part. By the adoption of the equipment capable of controlling smart household appliances wirelessly, the technical problem that the safety performance of smart home equipment is low in the prior art is solved, and the technical effect of improving the safety performance of smart home equipment is realized.
Owner:CHENGDU ZHONGFU LIXIANG TECH
File transmission system for electric power system
ActiveCN105471977AFix technical issues with less securityImprove securityDigital data protectionInternal/peripheral component protectionElectric power systemTerminal equipment
The invention discloses a file transmission system for an electric power system. The file transmission system comprises a mobile terminal used for acquiring a first data file including accident field information, an encryption U disk stored with an encryption file, a mobile terminal female seat used for fixing the mobile terminal, a storage server used for receiving the encrypted first data file sent by the mobile terminal female seat through the Internet, and a decryption server provided with a decryption chip, wherein the mobile terminal female seat is provided with a USB female port, after the encryption U disk is connected with the mobile terminal female seat, if a correct cipher for access to the encryption U disk is received, the first data file is encrypted on the basis of the encryption file, and the decryption server is used for decrypting the encrypted first data file through the decryption chip and sending the first data file after decryption to terminal equipment initiating a decryption request. The file transmission system solves a technical problem of relatively low safety existing in an electric power system employing a mobile terminal to transmit audio video files in the prior art.
Owner:STATE GRID BEIJING ELECTRIC POWER +2
Human body infrared sensor based smart home control center equipment
ActiveCN106444689AEnsure safetyLow securityComputer controlProgramme total factory controlEmbedded systemImage analysis
The invention provides human body infrared sensor based smart home control center equipment. The smart home control center equipment is connected with N smart home devices, and the control center equipment comprises a human body infrared sensor, an image analysis device and a smart home control device connected in sequence; the image analysis device is used for acquiring indoor smart home environment status monitored by a smart sensor arranged indoors, and analyzing and judging whether the indoor smart home environment status meets preset operation trigger conditions or not; the smart home control device is used for controlling working status of smart home according to operation rules corresponding to the operation trigger conditions when the indoor smart home environment status meets the preset operation trigger conditions. By the equipment, the technical problem of low safety in smart home equipment in the prior art is solved, and the technical effect of improving safety of the smart home equipment is realized.
Owner:极友家居科技(上海)有限公司
Secret key generation method and system, storage medium and electronic device
PendingCN112564901AFix technical issues with less securityImprove securityKey distribution for secure communicationShort range communication serviceEngineeringKey generation
The invention provides a secret key generation method and system, a storage medium and an electronic device, and the method comprises the steps: transmitting an updating request to a server, the updating request being used for requesting the server to update an original root sequence corresponding to target slave equipment; sending a target updating instruction is sent to the target slave equipment, wherein the target updating instruction comprises an encrypted first root sequence, the first root sequence is obtained after the server responds to the updating request to update the original rootsequence, the target updating instruction is used for indicating the target slave equipment to update the original root sequence stored in the target slave equipment into the first root sequence, andthe first root sequence is used for generating a dynamic key; and receiving first data sent by the target slave equipment, the first data being obtained by encrypting a new dynamic key, and the new dynamic key being generated by the target slave equipment according to a key generation algorithm stored in the target slave equipment and the first root sequence. According to the invention, the technical problem of low security of the secret key in the prior art is solved.
Owner:SUNWAVE COMM
Vehicle automatic driving method and device and vehicle
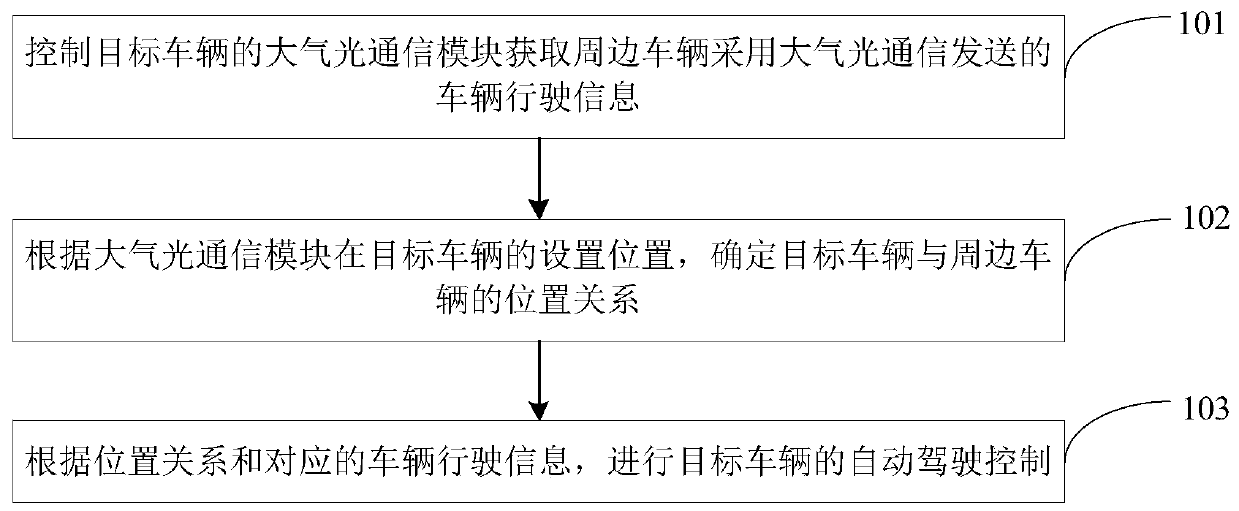
ActiveCN110134125AFix technical issues with less securityAccurate acquisition of driving informationPosition/course control in two dimensionsVehiclesEngineeringOptical communication
The application provides a vehicle automatic driving method and device and a vehicle. The method comprises the following steps: acquiring vehicle running information transmitted by a surrounding vehicle through atmospheric optical communication by controlling an atmospheric optical communication module on a target vehicle; determining a position relationship between the target vehicle and the surrounding vehicle according to the set position of the atmospheric optical communication module on the target vehicle; and perform automatic driving control on the target vehicle according to the position relationship and the corresponding vehicle running information. According to the method, the running information of the surrounding vehicle is acquired through the atmospheric optical communicationmodule arranged on the target vehicle in order to perform automatic driving control on the target vehicle, so that the technical problem of incapability of correctly planning a running route in the automatic driving process of the vehicle since the running information of a vehicle in a certain area is acquired while the running information of the surrounding vehicle cannot be accurately acquiredwhen the wireless communication module is used for acquiring the running information of the surrounding vehicle in the prior art is solved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
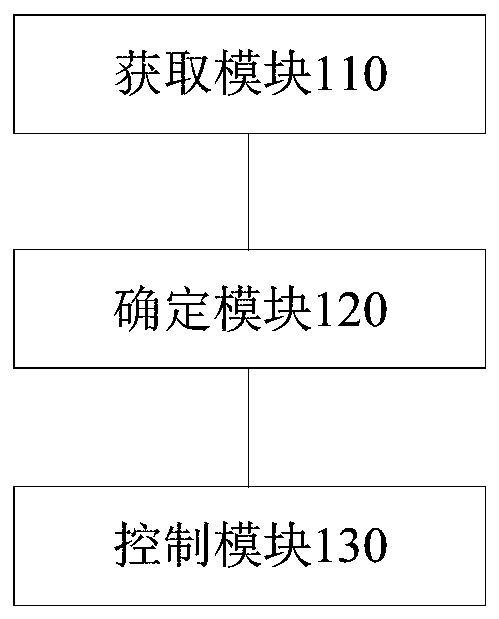
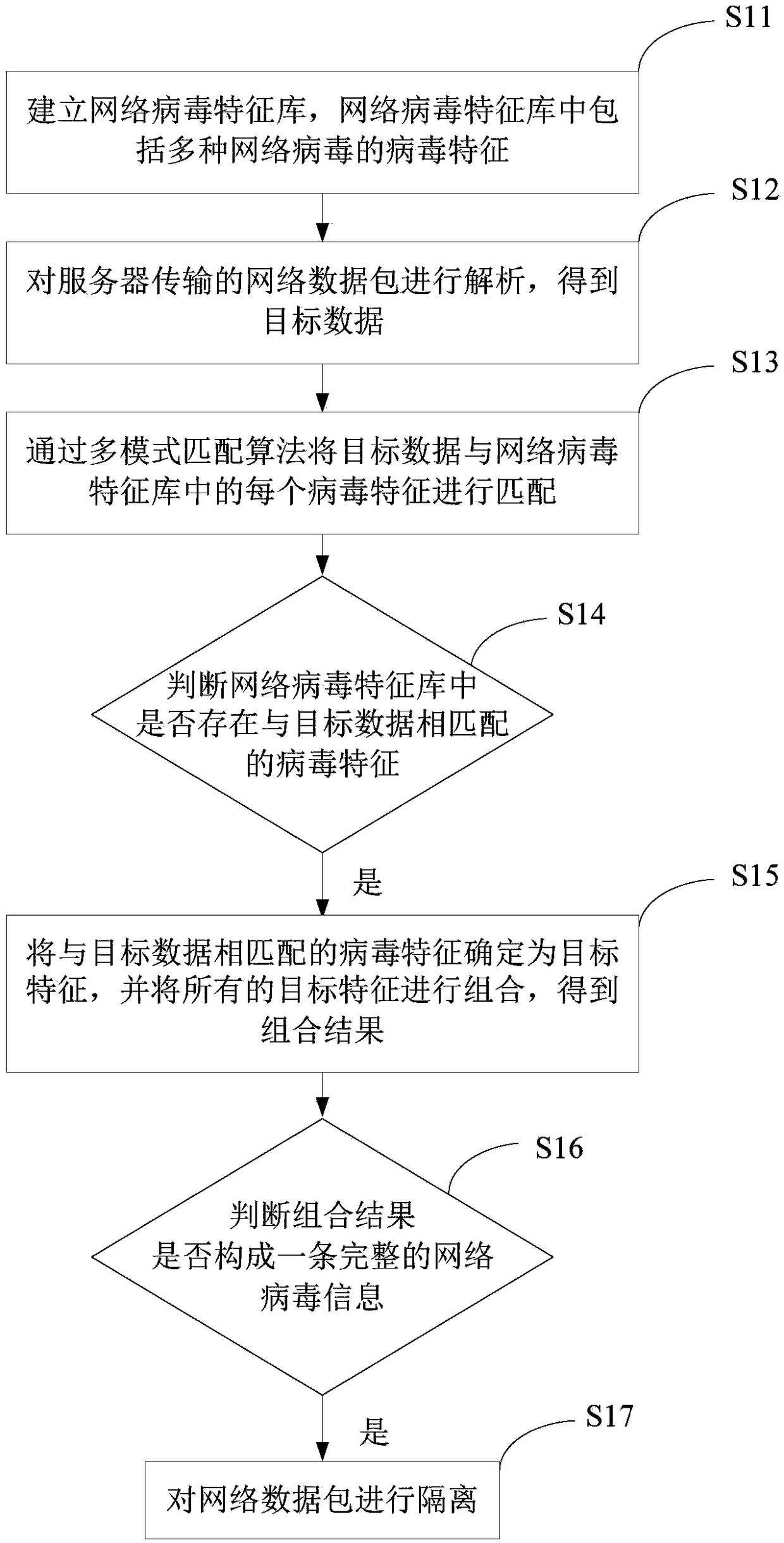
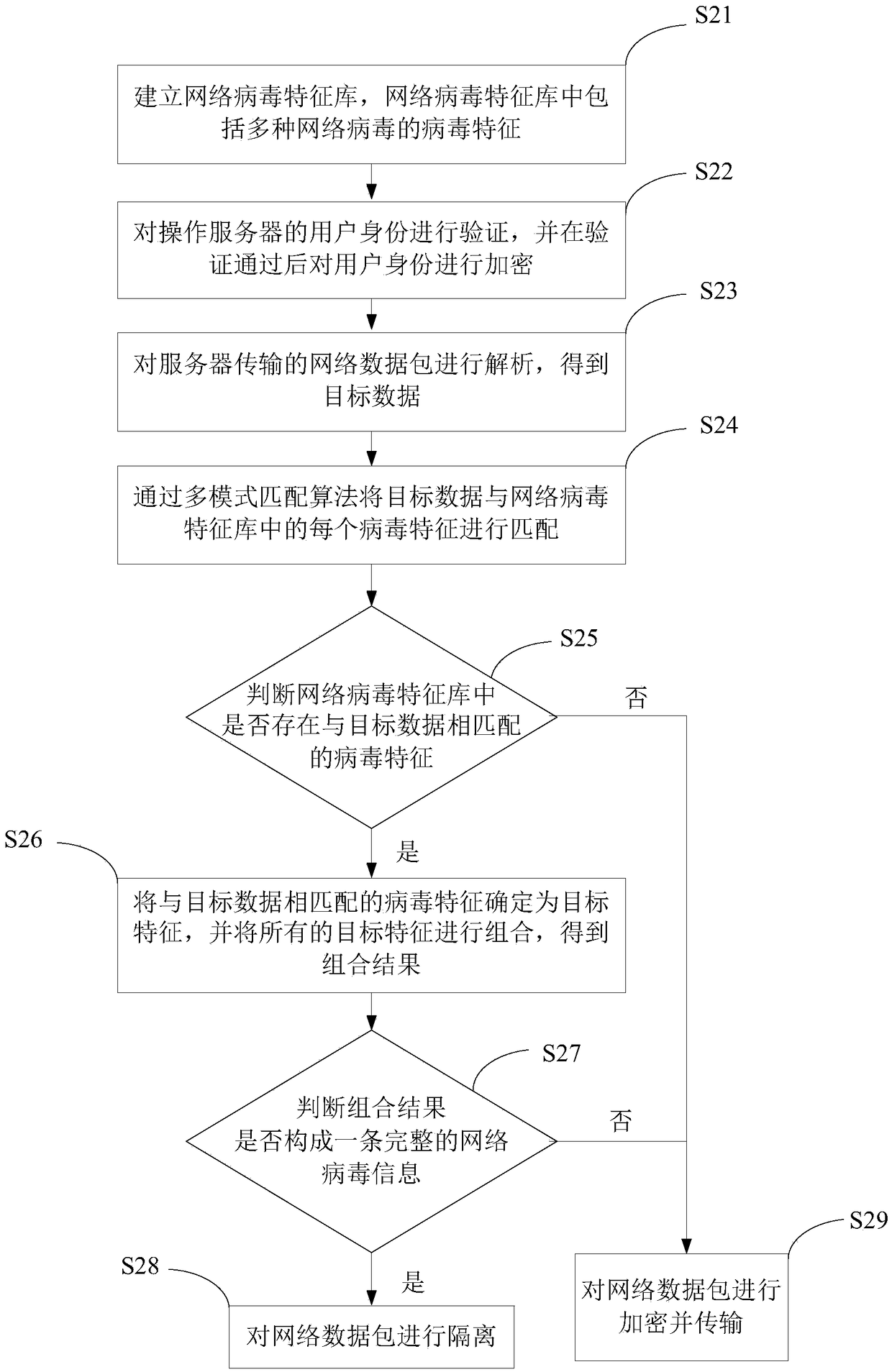
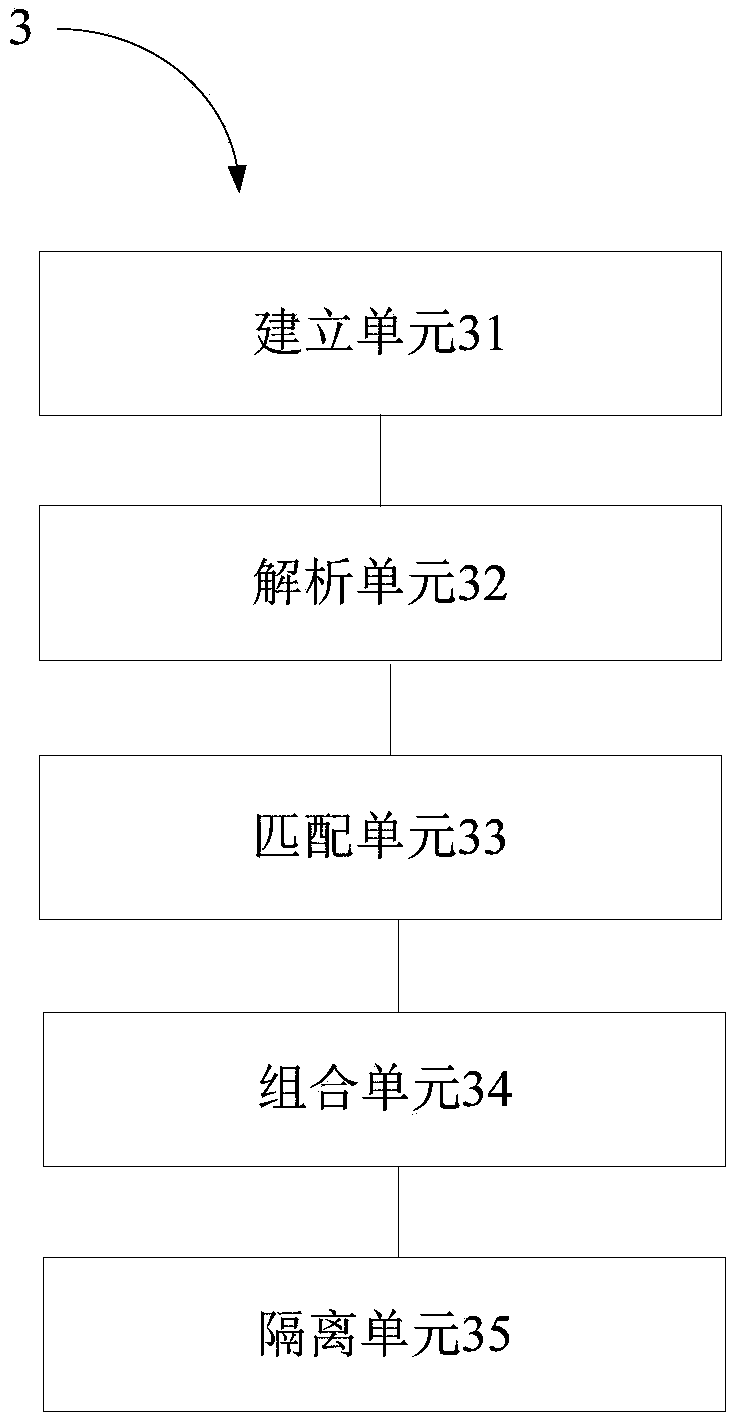
Network data security transmission method and system, and electronic device
InactiveCN109302420AFix technical issues with less securityImprove detection efficiencyTransmissionNetwork packetNetwork security policy
The invention provides a network data security transmission method and system and an electronic device, related to the technical field of network security. The network data security transmission method comprises the following steps: establishing a network virus feature library, and the network virus feature library includes virus features of a plurality of network viruses; parsing a network data packet transmitted by a server to obtain target data; matching the target data with each virus feature in the network virus feature library through a multi-mode matching algorithm; if the virus featurematching the target data exists in the network virus feature library, determining the virus feature matching the target data as a target feature, and combining all the target features to obtain a combined result; and isolating the network data packet if the combined result constitutes a piece of complete network virus information. The invention solves the technical problem that the security of the network data transmission process in the prior art is low.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com