Network data security transmission method and system, and electronic device
A technology for secure transmission and network data, applied in the field of network security, can solve problems such as low security, and achieve the effect of solving low security and achieving detection efficiency and accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
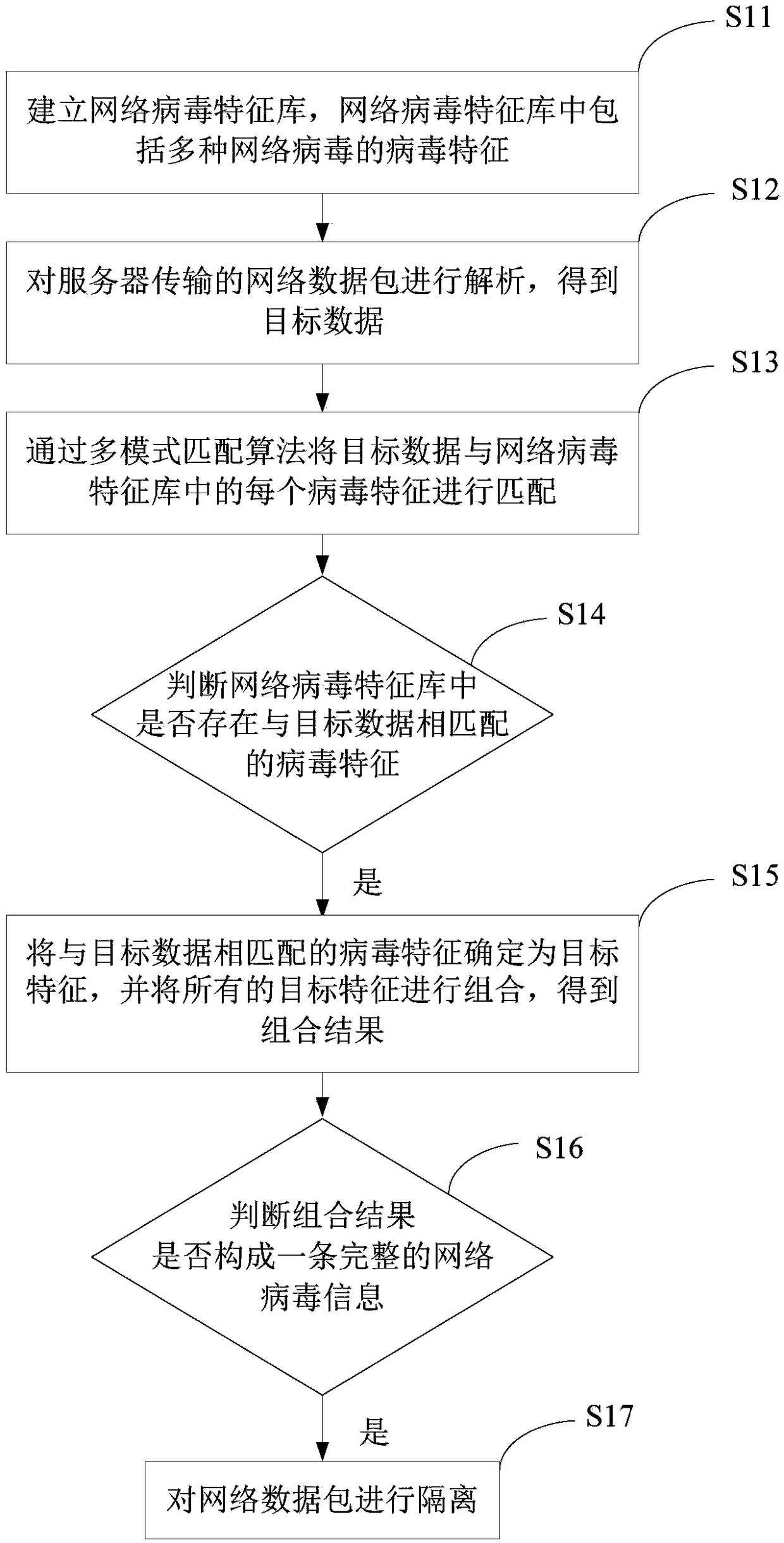
[0054] A method for secure network data transmission provided by an embodiment of the present invention is applied to a server, such as figure 1 shown, including:
[0055] S11: Establish a network virus signature database, which includes virus signatures of various network viruses.
[0056] In this step, a virus signature database is created, and each virus signature corresponds to one or more virus information.
[0057] S12: Analyzing the network data packet transmitted by the server to obtain the target data.
[0058] As a preferred implementation of this embodiment, the collected network data packets are reassembled and analyzed.
[0059] S13: Match the target data with each virus signature in the network virus signature database through a multi-pattern matching algorithm.
[0060] In practical applications, a multi-pattern matching algorithm is used to match the virus signatures in the virus signature database.
[0061] S14: Determine whether there is a virus signature...
Embodiment 2
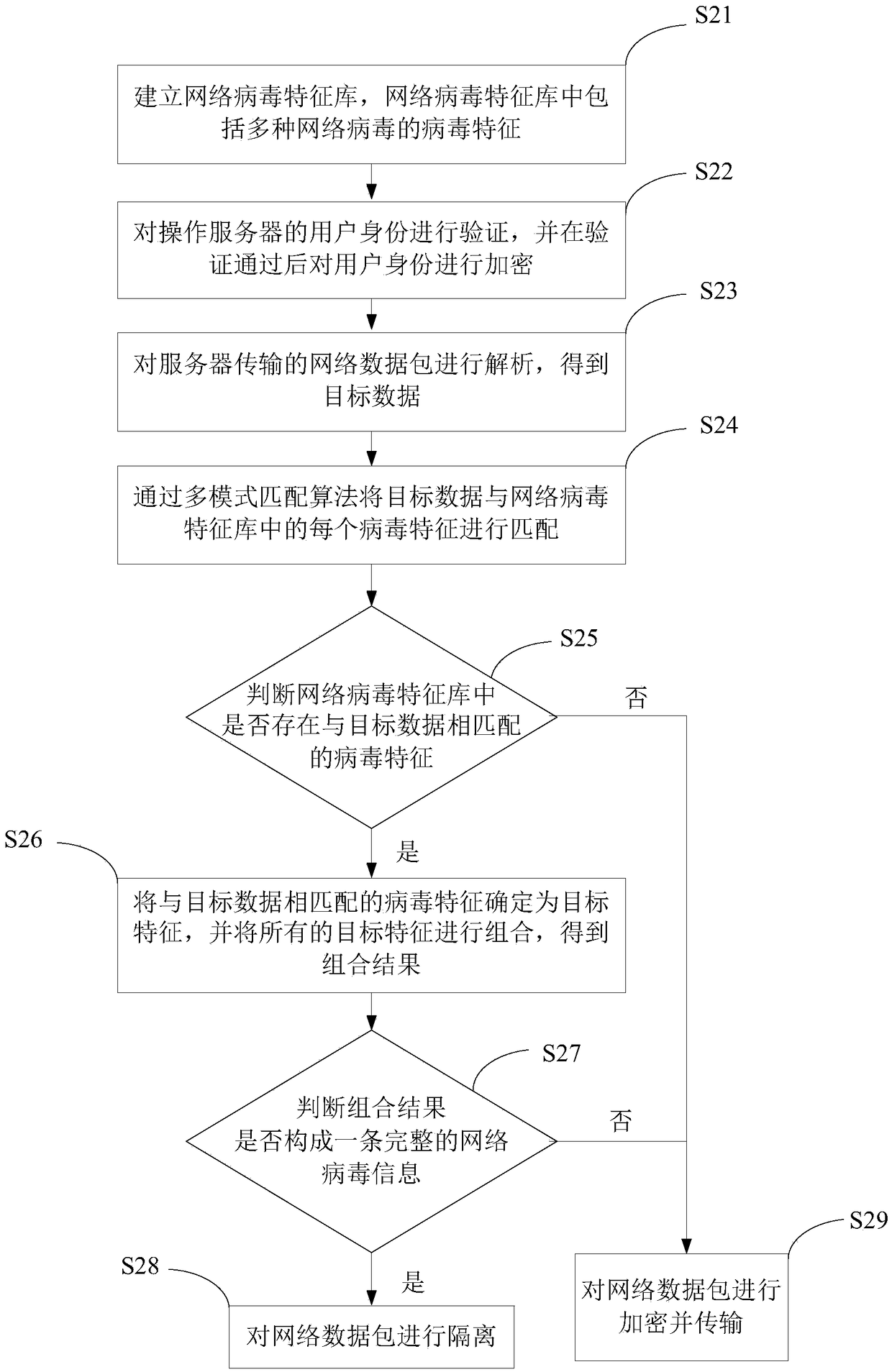
[0070] A method for secure network data transmission provided by an embodiment of the present invention is applied to a server, such as figure 2 shown, including:
[0071] S21: Establish a network virus signature database, which includes virus signatures of various network viruses.
[0072] As a preferred solution, a virus signature database is created, and each virus signature corresponds to one or more virus information.
[0073] S22: Authenticate the identity of the user operating the server, and encrypt the identity of the user after the authentication is passed.
[0074] As another implementation of this embodiment, the user verifies the login identity through the identity verification module, and after passing the verification, the identity is encrypted by the encryption unit to enter the server.
[0075] S23: Analyzing the network data packet transmitted by the server to obtain the target data.
[0076] In this step, the collected network data packets are reassemble...
Embodiment 3
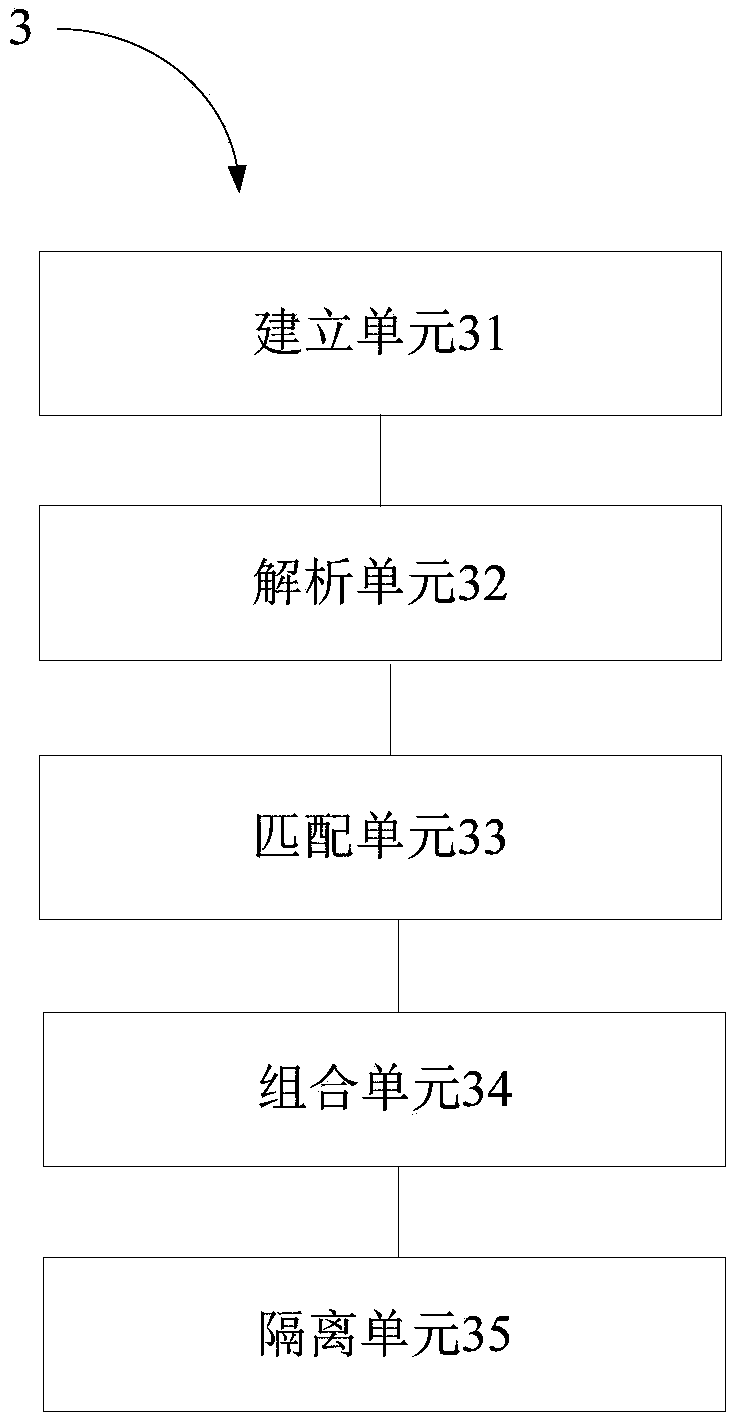
[0091] A network data security transmission system provided by an embodiment of the present invention is applied to a server, such as image 3 As shown, the network data secure transmission system 3 includes: an establishment unit 31 , an analysis unit 32 , a matching unit 33 , a combination unit 34 and an isolation unit 35 .
[0092] Wherein, the establishing unit is used to establish a network virus signature database, which includes virus signatures of various network viruses. The parsing unit is used for parsing the network data packets transmitted by the server to obtain target data.
[0093] It should be noted that the matching unit is used to match the target data with each virus signature in the network virus signature database through a multi-pattern matching algorithm. The combination unit is used to determine the virus signature matching the target data as the target signature if there is a virus signature matching the target data in the network virus signature dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com