Log encryption method and device and log decryption method and device
An encryption algorithm and log technology, applied in the computer field, can solve problems such as low security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0059] It should be noted that the method provided in this embodiment is applied to the client, and the client and the server are connected through the network to realize communication; in the specific implementation process, the client includes but not limited to mobile terminal equipment (such as mobile phones, tablet ), fixed terminal devices (such as desktop computers), etc., there are not too many restrictions here.
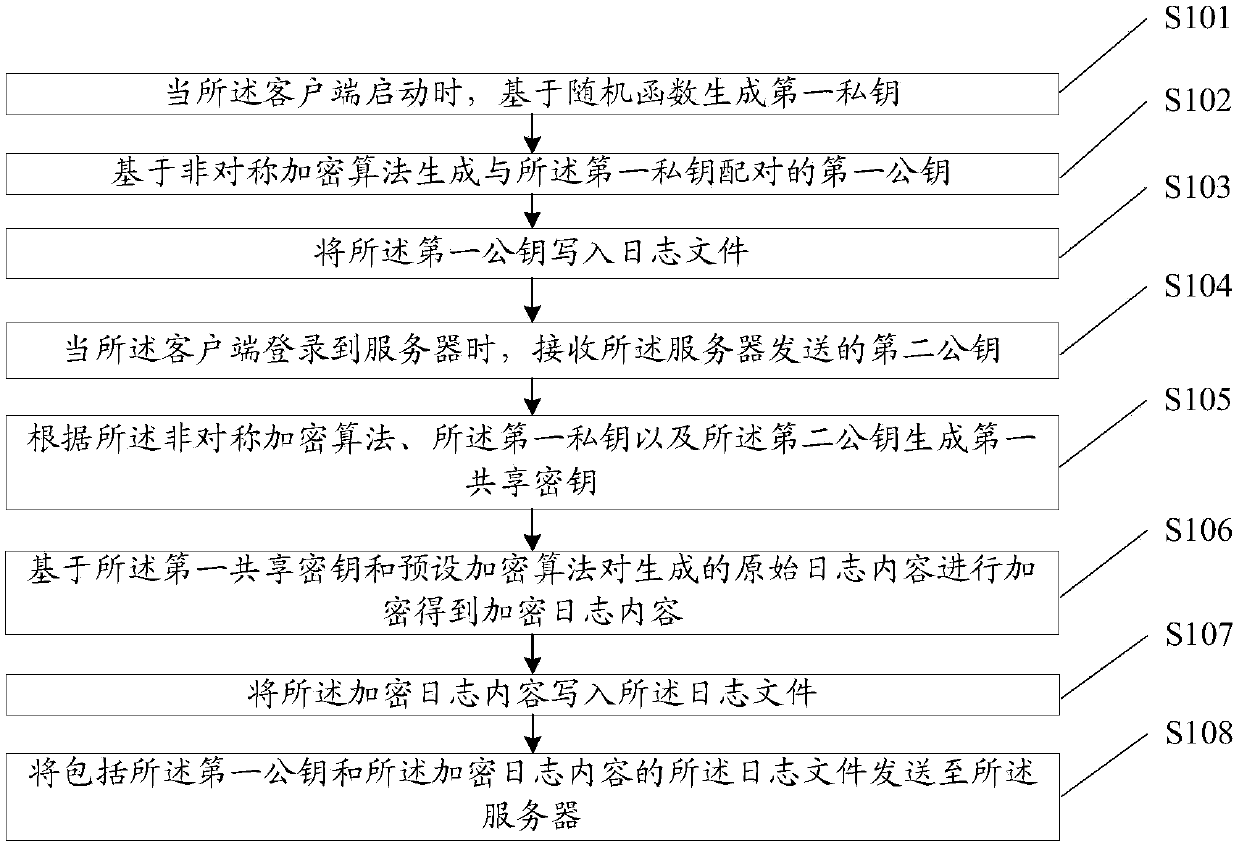
[0060] This embodiment provides a log encryption method, such as figure 1 As shown, the method includes:
[0061] Step S101, when the client starts, generate a first private key based on a random function.
[0062] Specifically, the random number function can be rand, srand(), etc., and the specific algorithm can be set according to the actual situation, such as rounding, remainder, logical operation, etc.
[0063] Step S102, generating a first public key paired with the first private key based on an asymmetric encryption algorithm.
[0064] Asymmetric en...
Embodiment 2
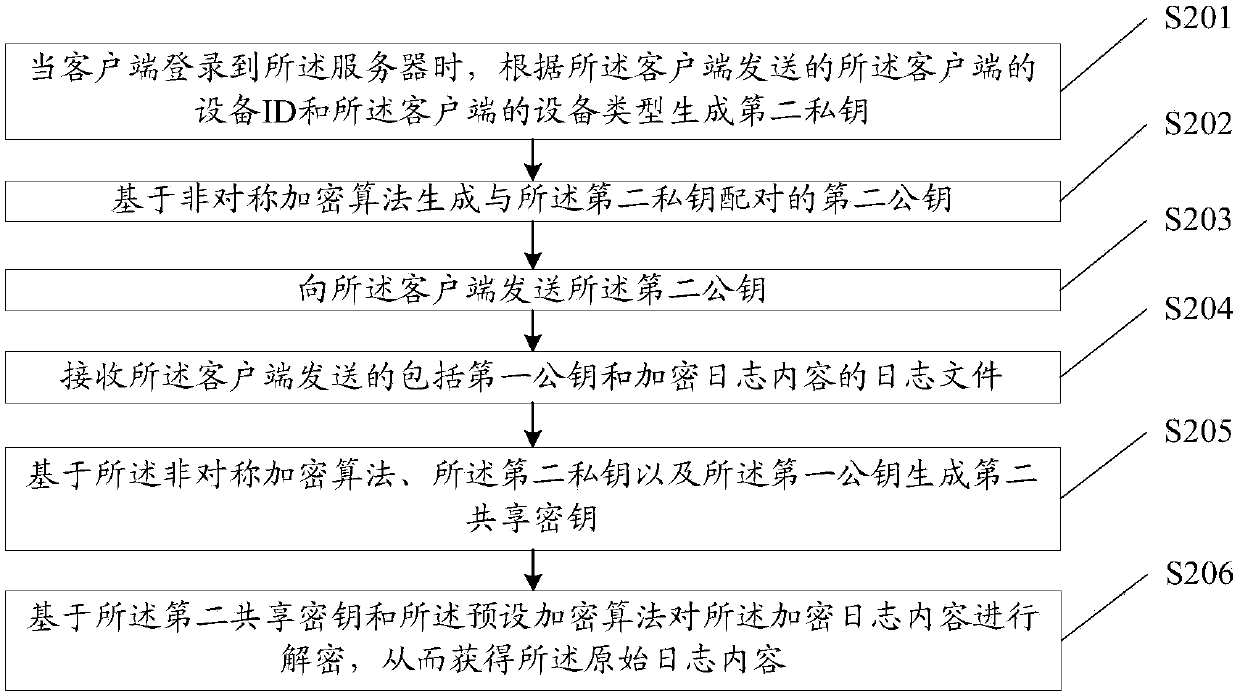
[0110] This embodiment provides a log decryption method, such as figure 2 As shown, the method is applied to the server, and the method includes:
[0111] S201. When a client logs in to the server, generate a second private key according to the device ID of the client and the device type of the client sent by the client.
[0112] S202. Generate a second public key paired with the second private key based on an asymmetric encryption algorithm.
[0113] S203. Send the second public key to the client.
[0114] Specifically, sending the second public key to the client, so that the client generates a first shared key according to the asymmetric encryption algorithm, the first private key, and the second public key, and the The first private key is generated by the client based on a random function.
[0115] S204. Receive a log file including the first public key and encrypted log content sent by the client.
[0116] Specifically, the encrypted log content is generated by the c...
Embodiment 3
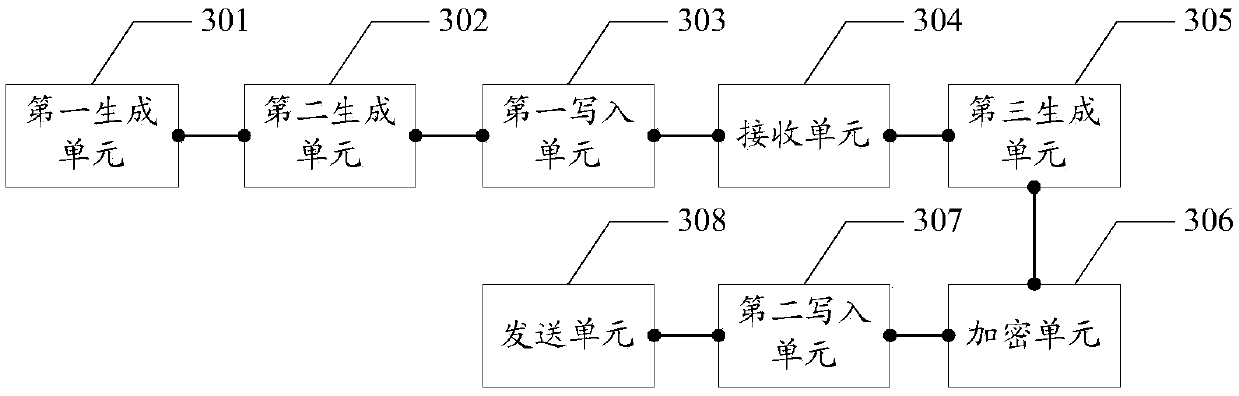
[0124] This embodiment provides a log encryption device, the device is applied to the client, such as image 3 As shown, the above-mentioned devices include:
[0125] The first generating unit 301 is configured to generate a first private key based on a random function when the client is started;
[0126] The second generating unit 302 is configured to generate a first public key paired with the first private key based on an asymmetric encryption algorithm;
[0127] A first writing unit 303, configured to write the first public key into a log file;
[0128] A receiving unit 304, configured to receive a second public key sent by the server when the client logs in to the server, the second public key is generated by the server based on the asymmetric encryption algorithm and the second private key , the second private key is generated by the server according to the device ID of the client and the device type of the client sent by the client;
[0129] A third generating unit 305...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com