Shared file authority control method
A technology for file sharing and authority control, applied to electrical components, instruments, electrical digital data processing, etc., to achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The present invention will be described in detail below in conjunction with the accompanying drawings. As a part of this specification, the principle of the present invention will be described through embodiments. Other aspects, features and advantages of the present invention will become clear at a glance through the detailed description.
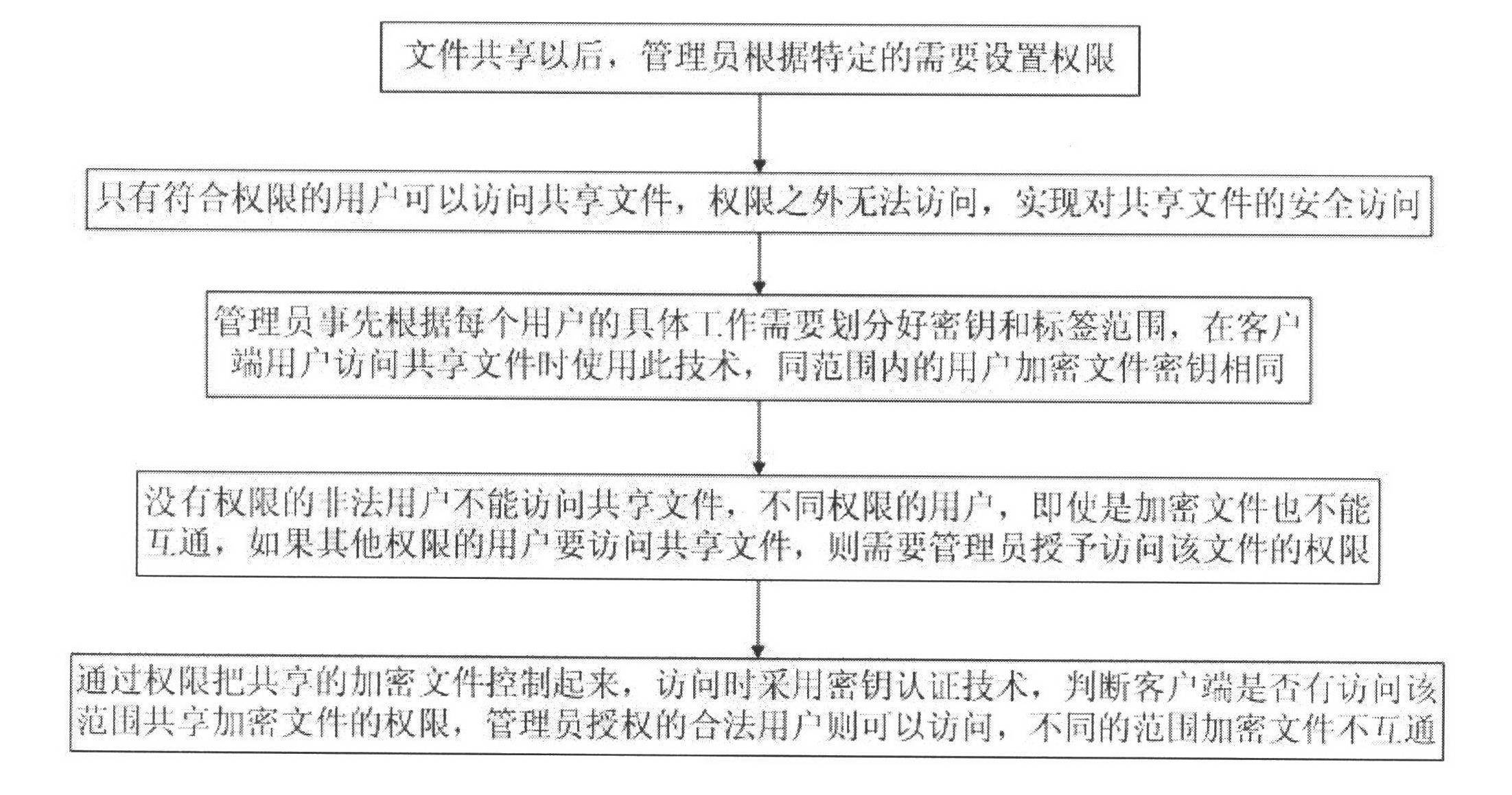
[0020] like figure 1 , 2 , 3, a method for controlling shared file permissions provided by the present invention, which includes the following steps:
[0021] a. After file sharing, administrators can set permissions according to specific needs;
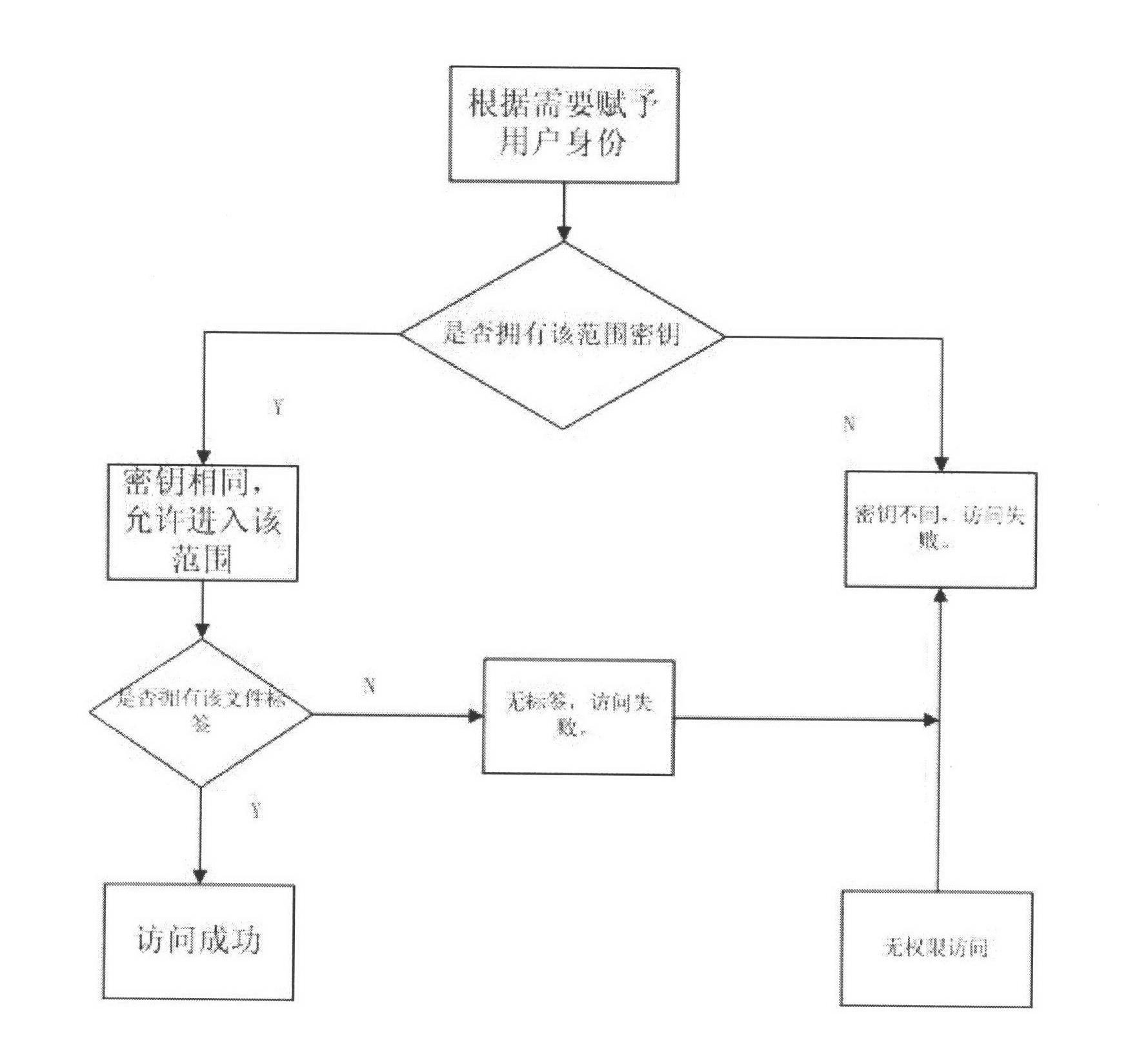
[0022] b. Only users who meet the authority can access the shared files, and those outside the authority cannot access, so as to realize the safe access to the shared files;
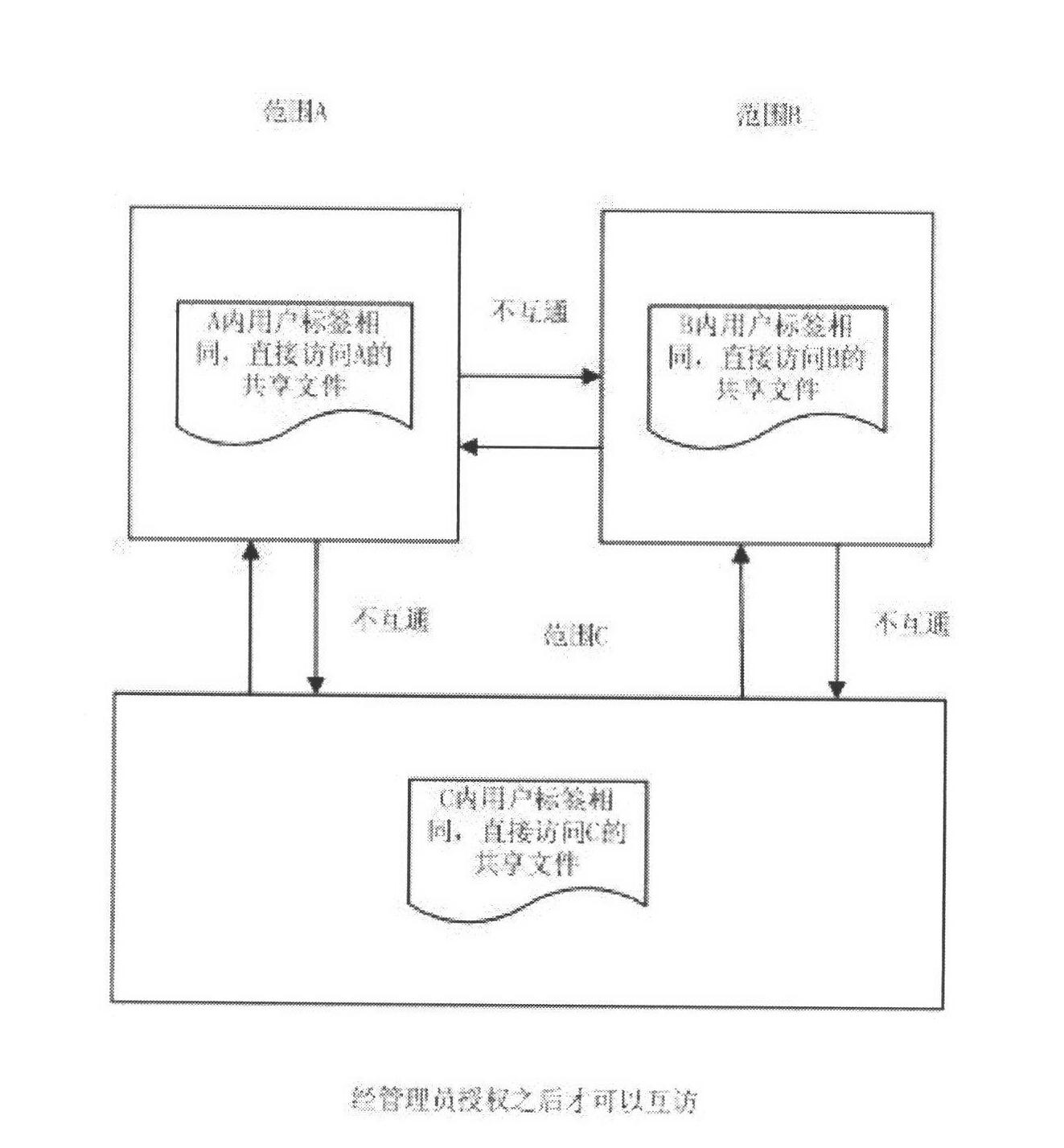
[0023] c. The administrator divides the key and label range according to the specific work needs of each user in advance, and uses this technology when the client user accesses the shared file, and the encrypted fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com