An email encryption method and system based on group cryptography
An email and encryption system technology, applied in the information field, can solve the problems of cumbersome certificate verification, complex key management, and low encryption efficiency, and achieve the effects of simple storage and maintenance, simple key management, and a small number of verifications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
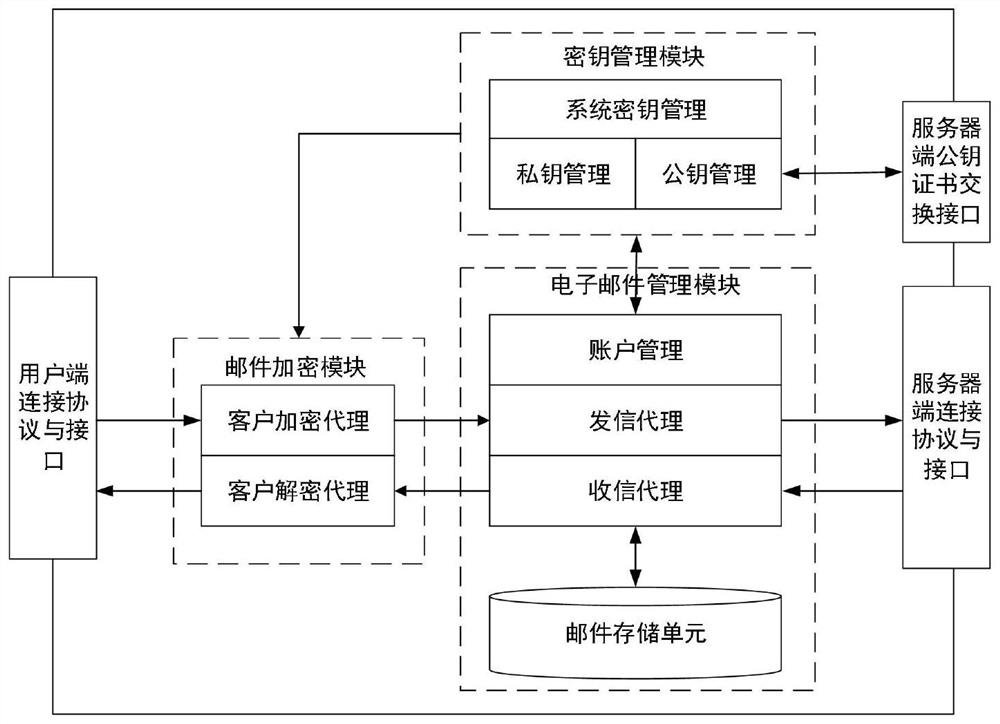
[0088] The email encryption method based on the group cryptosystem comprises a group email encryption scheme, an embodiment of the scheme is as follows:
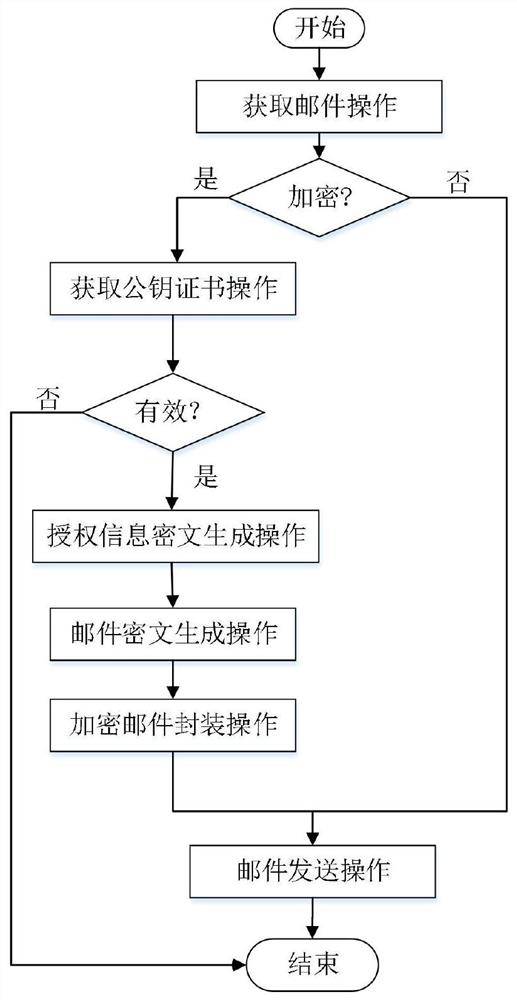
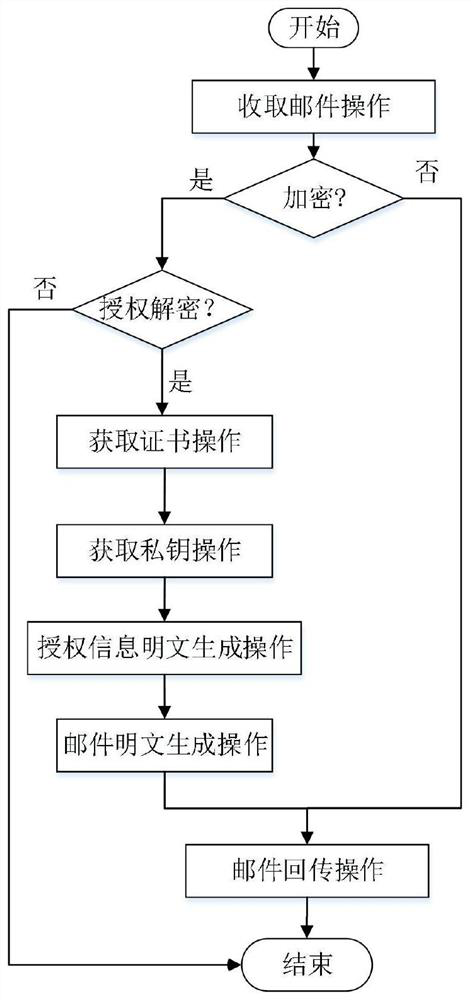
[0089] 1) Get mail operation: Get the mail Mail sent by the user through the client connection protocol and interface UPI.
[0090] 2) Encryption request judging operation: the client encryption agent unit UEPU detects the encrypted identification information from the mail Mail, and if it exists, proceed to step 3); otherwise, execute step 8).
[0091] Among them, the encrypted identification information in this embodiment is defined as follows:
[0092] ①Select the encryption method using the "#" sign and the following form to define:
[0093] {Username 1, Username 2, ..., Username n}#mail server
[0094] ② The exclusion encryption method is defined with the sign "%" and the following form:
[0095] {username1,username2,...,usernamen}% mail server
[0096] Here, {username 1, username 2, ..., username n} represent the us...
Embodiment 2
[0107] Based on the e-mail encryption method based on the group cryptography system comprising encrypted mail encapsulation format, an embodiment of the scheme is as follows:
[0108] 1) Authorization information ciphertext generation operation: for a given mail recipient set S={ID 1 ,...,ID n}, get the receiver ID respectively k The group public key certificate Cert of the mail server where it is located k , and form the certificate set Cert S ={Cert 1 ,...,Cert m},in,
[0109] per Cert k Contains the group public key mpk k ; and then respectively call the encryption algorithm SBE-Encrypt in the logo-based group encryption SBE scheme in "Example 3" to complete the encryption of the session key ek, that is, for all m public keys mpk k (k=1,...,m), calculate respectively
[0110] SBE-Encrypt (mpk k ,Pattern,ek)→C k (1)
[0111] Finally, the ciphertext set C is obtained SBE =(C 1 ,...,C m ), where the session key ek for all ciphertexts C 1 ,...,C m all the same...
Embodiment 3
[0122] The email encryption method based on the group cipher system includes a logo-based group encryption SBE scheme, an embodiment of the scheme is as follows:
[0123] 1) System parameter generation algorithm SBE-Setup(S)→(mpk, msk): given a bilinear mapping group S=(p, G 1 ,G 2 ,G T ,e(·,·)) as input, randomly select two elements G←G 1 and H←G 2 , two random exponents Calculate R=e(G,H) ò and for any k∈[1,m] compute and choose a hash function hash Finally, output the master private key msk=(γ,ò,G,G ò ) and group public key mpk={S,H,R,{G k} k∈[1,m] ,hash()}.
[0124] 2) User key generation algorithm SBE-GenKey(msk, ID k )→sk k : Enter msk and the ID of the kth user k , the given user ID in this example k is the user's Email address, define x k =hash(ID k ) will ID k maps to a random element Calculate the private key of the kth user
[0125]
[0126] And the public information of the kth user and put (ID k ,H k ) to the group public key mpk.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com