Email encryption and decryption method, storage medium and electronic device
An e-mail and encryption method technology, applied in the field of e-mail communication, can solve the problems of inability to select e-mail protection methods, leaking of e-mail servers, and e-mails that cannot reflect differentiated confidentiality requirements, so as to achieve the effect of improving confidentiality and avoiding leaks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
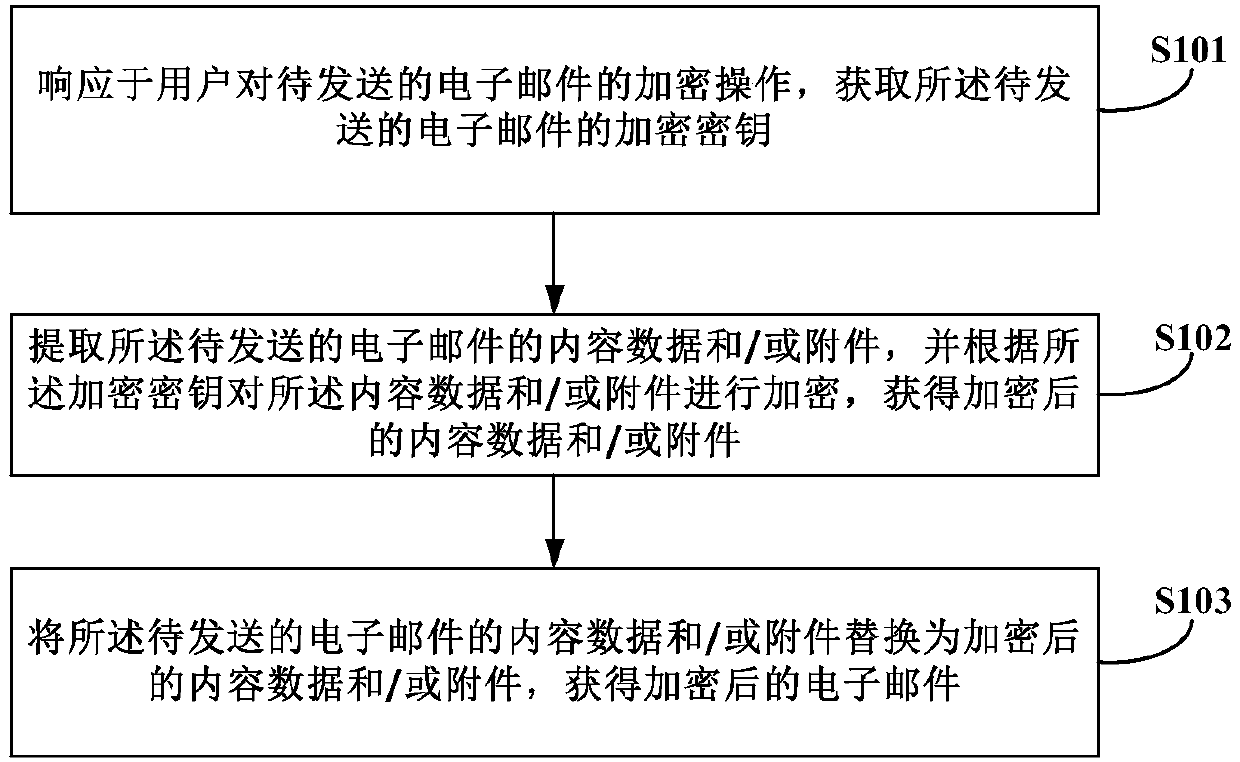
[0032] figure 1 It is a flowchart of an email encryption method provided according to Embodiment 1 of the present invention. Such as figure 1 As shown, the encryption method of the email provided by the embodiment of the present invention comprises the following steps:
[0033]In step S101 , an encryption key of the email to be sent is obtained in response to a user's encryption operation on the email to be sent.
[0034] In this embodiment, in response to the encryption operation of the email to be sent by the user, the encryption key of the email to be sent can be obtained through a plug-in in the email sending and receiving system. In a specific implementation, when a user's request to send an email is received, an encryption decision interface is displayed to the user on the screen of the terminal device, so that the user can choose whether to encrypt the email to be sent according to the requirement. If the user chooses to encrypt the email to be sent according to requ...
Embodiment 2
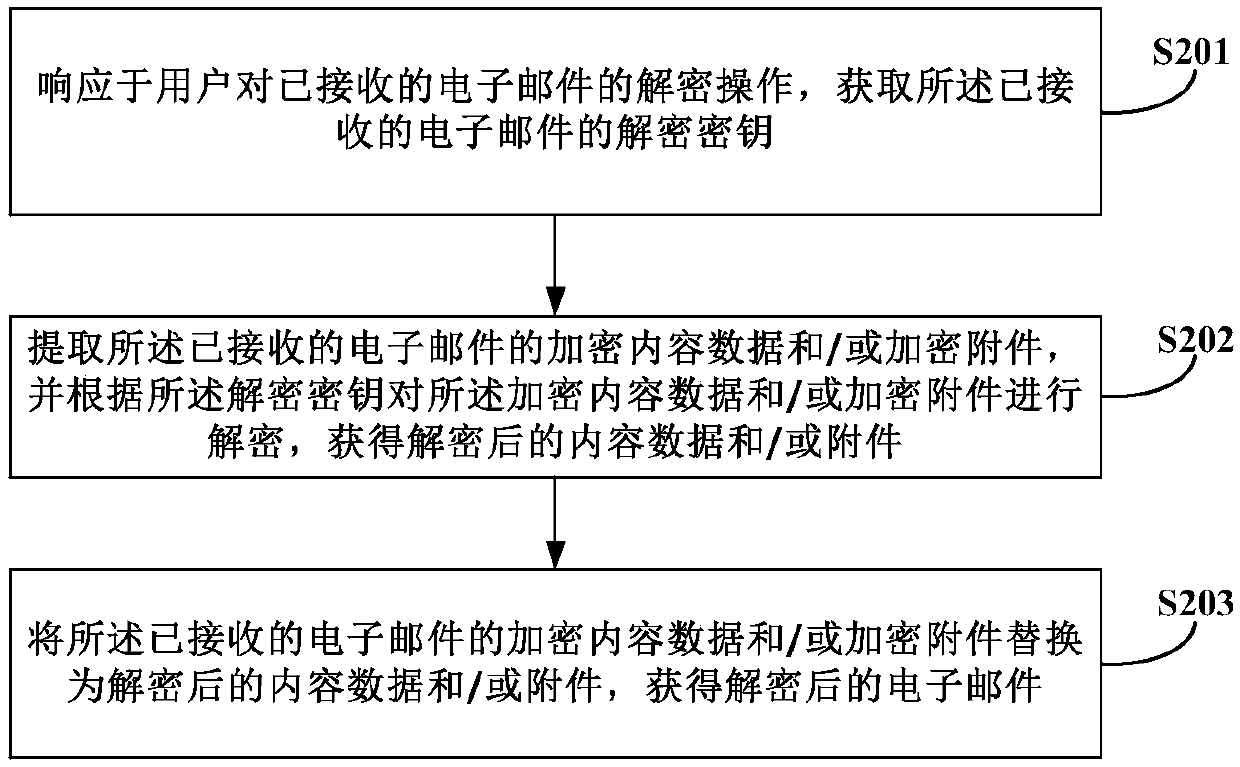
[0052] figure 2 It is a flow chart of the email decryption method provided according to Embodiment 2 of the present invention. Such as figure 2 As shown, the decryption method of the email provided in this embodiment includes the following steps:
[0053] In step S201, a decryption key of the received email is acquired in response to a user's decryption operation on the received email.
[0054]In this embodiment, in response to the user's decryption operation on the received email, the decryption key of the received email can be obtained through a plug-in in the email sending and receiving system. In a specific embodiment, when the receiving end receives the encrypted email, the user opens the email to display the email subject name and encrypted content data. At the same time, it also gives a reminder that this email is an encrypted email and a link to decrypt the terminal device. Wherein, the link for decrypting the terminal device will be provided when the email sendi...
Embodiment 3
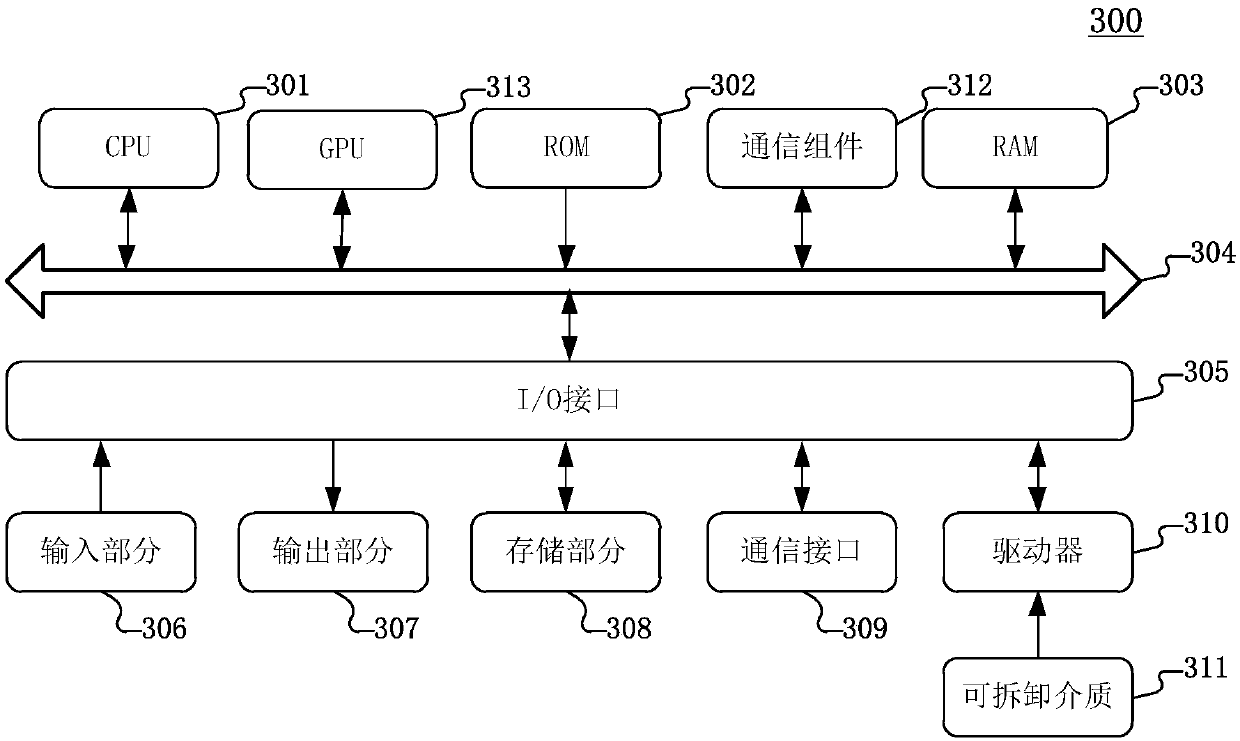
[0069] The embodiment of the present invention also provides an electronic device, which may be, for example, a mobile terminal, a personal computer (PC), a tablet computer, a server, and the like. Refer below image 3 , which shows a schematic structural diagram of an electronic device 300 suitable for implementing a terminal device or a server according to an embodiment of the present invention. Such as image 3 As shown, the electronic device 300 includes one or more first processors, a first communication element, etc., and the one or more first processors are, for example: one or more central processing units (CPU) 301, and / or one or a plurality of graphics processors (GPU) 313, etc., the first processor can be stored in the read-only memory (ROM) 302 in accordance with the executable instruction or loaded from the storage section 308 into the random access memory (RAM) 303 Various appropriate actions and processing are executed according to the instruction. In this em...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com