Evidence obtaining method and system for DDoS attack
A technology for analyzing algorithms and electronic evidence, applied in the field of computer networks, to achieve the effect of preventing network paralysis and simple and efficient operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The technical solutions provided by the present invention will be described in detail below in conjunction with specific examples. It should be understood that the following specific embodiments are only used to illustrate the present invention and are not intended to limit the scope of the present invention.
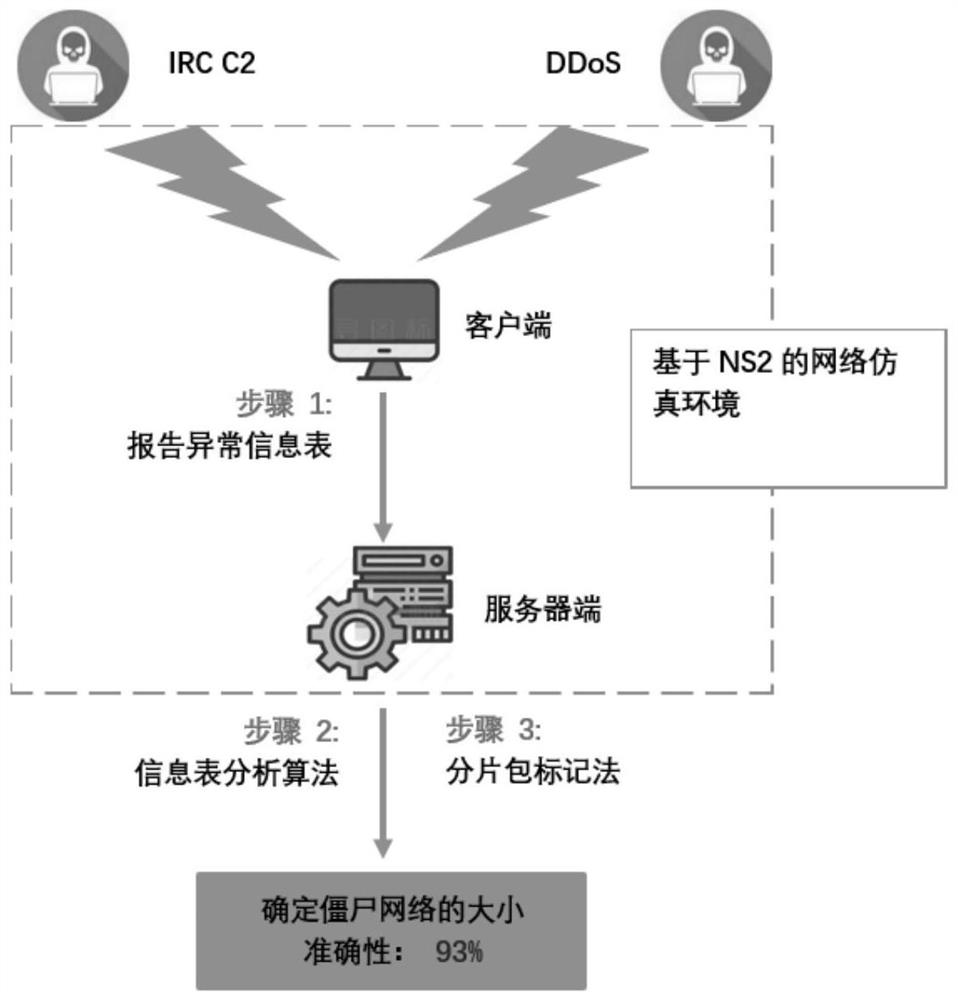
[0048] figure 1 The flow chart of the method for obtaining evidence for DDoS attacks provided by the present invention includes the following steps:
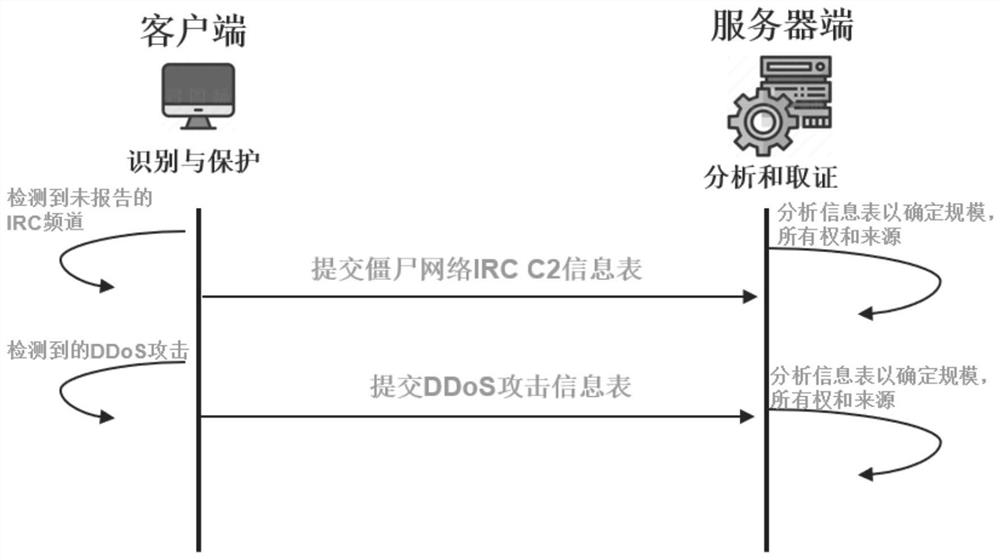
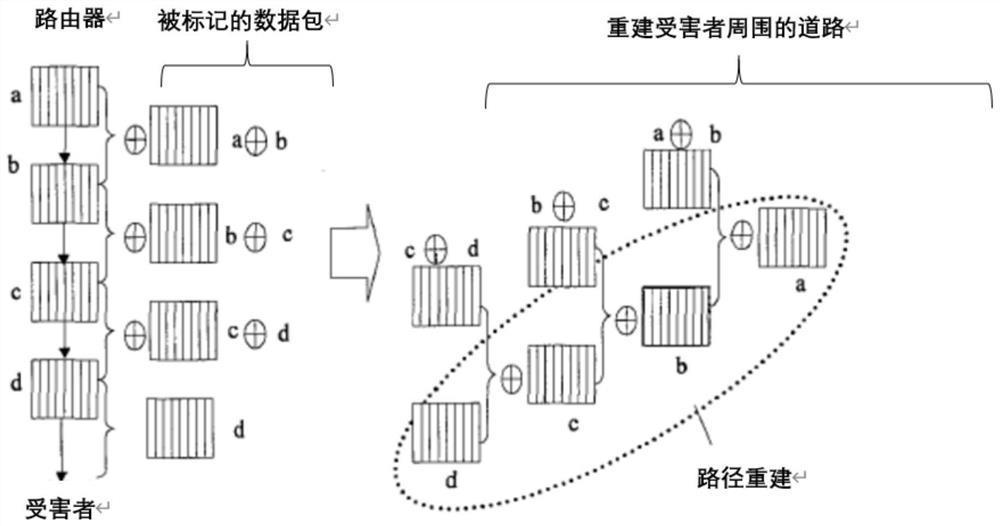
[0049] Step 1: Report exception information form. In our model, the client detects Botnet IRC behavior. If the action involves an unreported IRC channel, it submits the C2 info form to the server. The C2 information table includes the following information: IRC channel, client IP, and botnet ID. If the client detects a new DDoS attack, it submits the attack information table to the server. The DDoS attack information table includes the following information: the host IP that initiates the attack, the host IP th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com