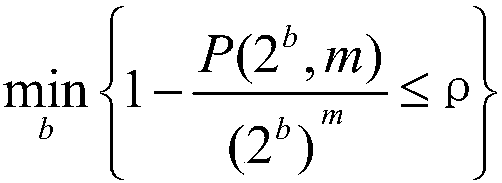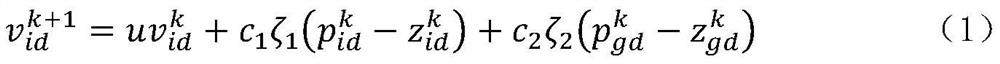Patents
Literature
47 results about "Path reconstruction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
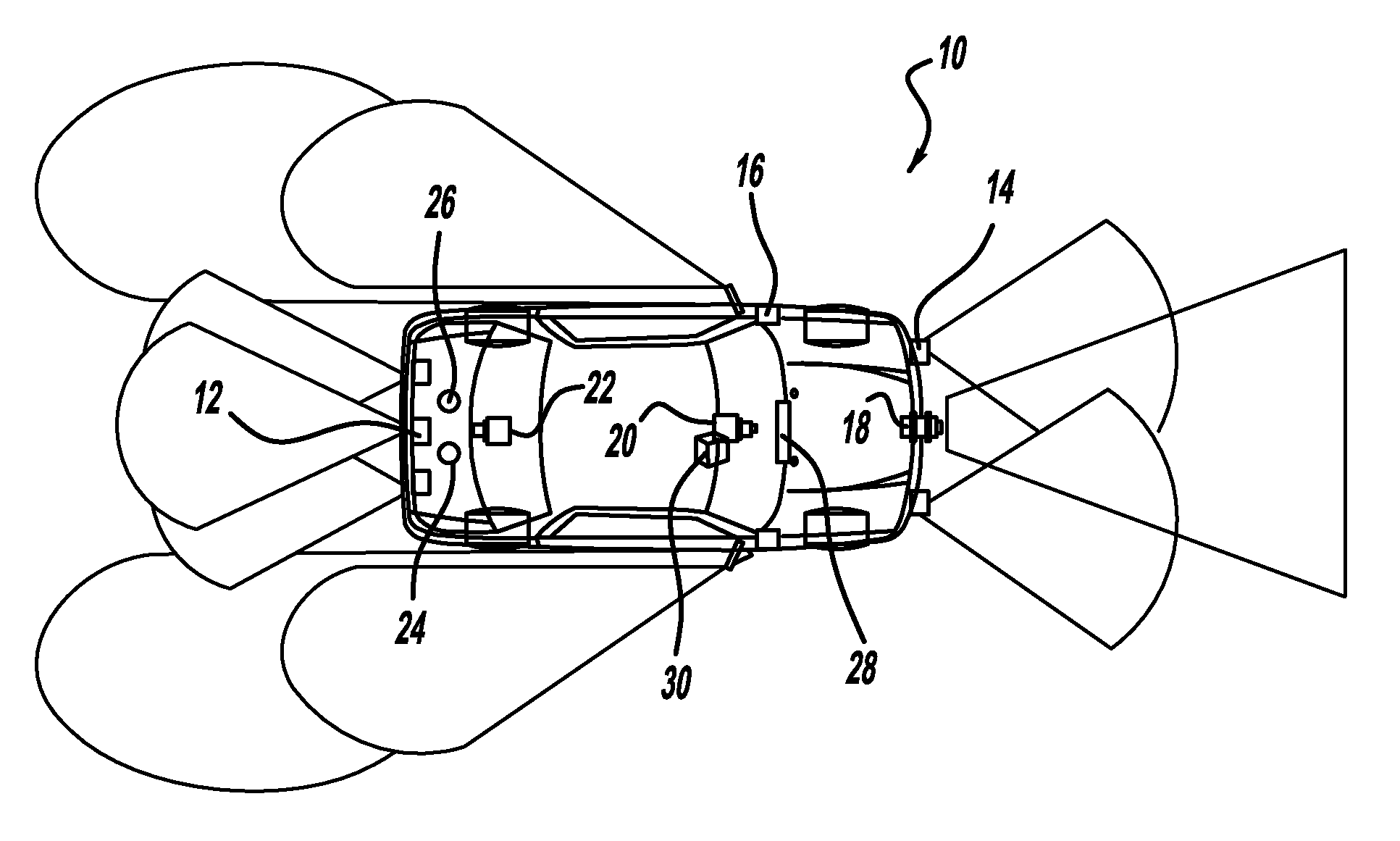
Driving skill recognition based on behavioral diagnosis
A system for classifying a driver's driving skill of a vehicle based on behavioral diagnosis. A plurality of vehicle sensors providing vehicle measurement signals. A maneuver qualification and identification processor qualifies and identifies characteristic maneuver identifying signals and a maneuver index and parameter processor creates a maneuver index and identifies relevant vehicle parameters. A path reconstruction processor reproduces an intended vehicle path for each characteristic maneuver identified by the maneuver characteristic processor. A maneuver model processor models the characteristic maneuvers and a driving skill diagnosis processor provides driving skill signals based on the maneuver model and driver input data. The driving skill diagnosis processor converts the maneuver model signals and the driver command input signal to the frequency domain to provide frequency content discrepancy analysis.
Owner:GM GLOBAL TECH OPERATIONS LLC
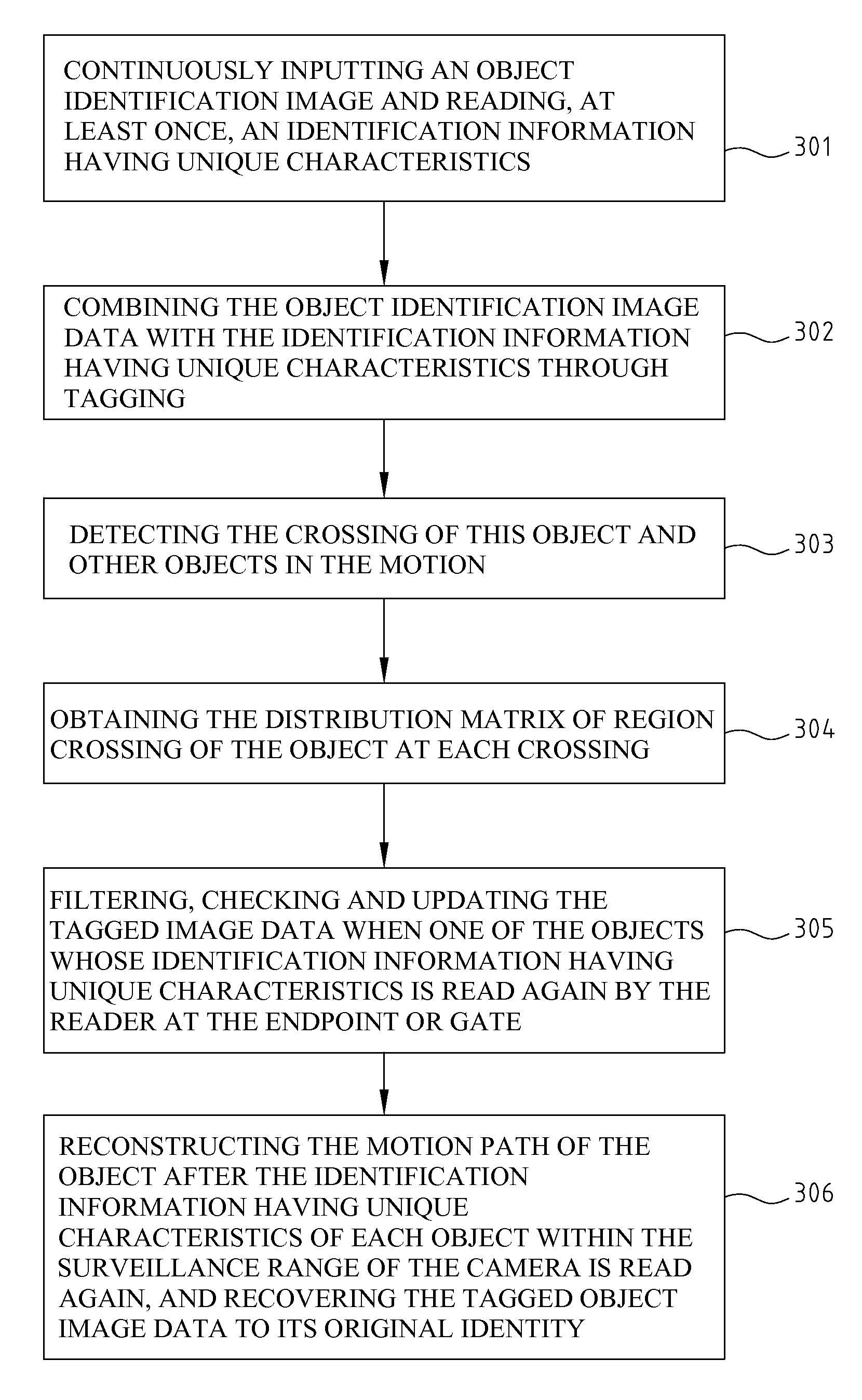
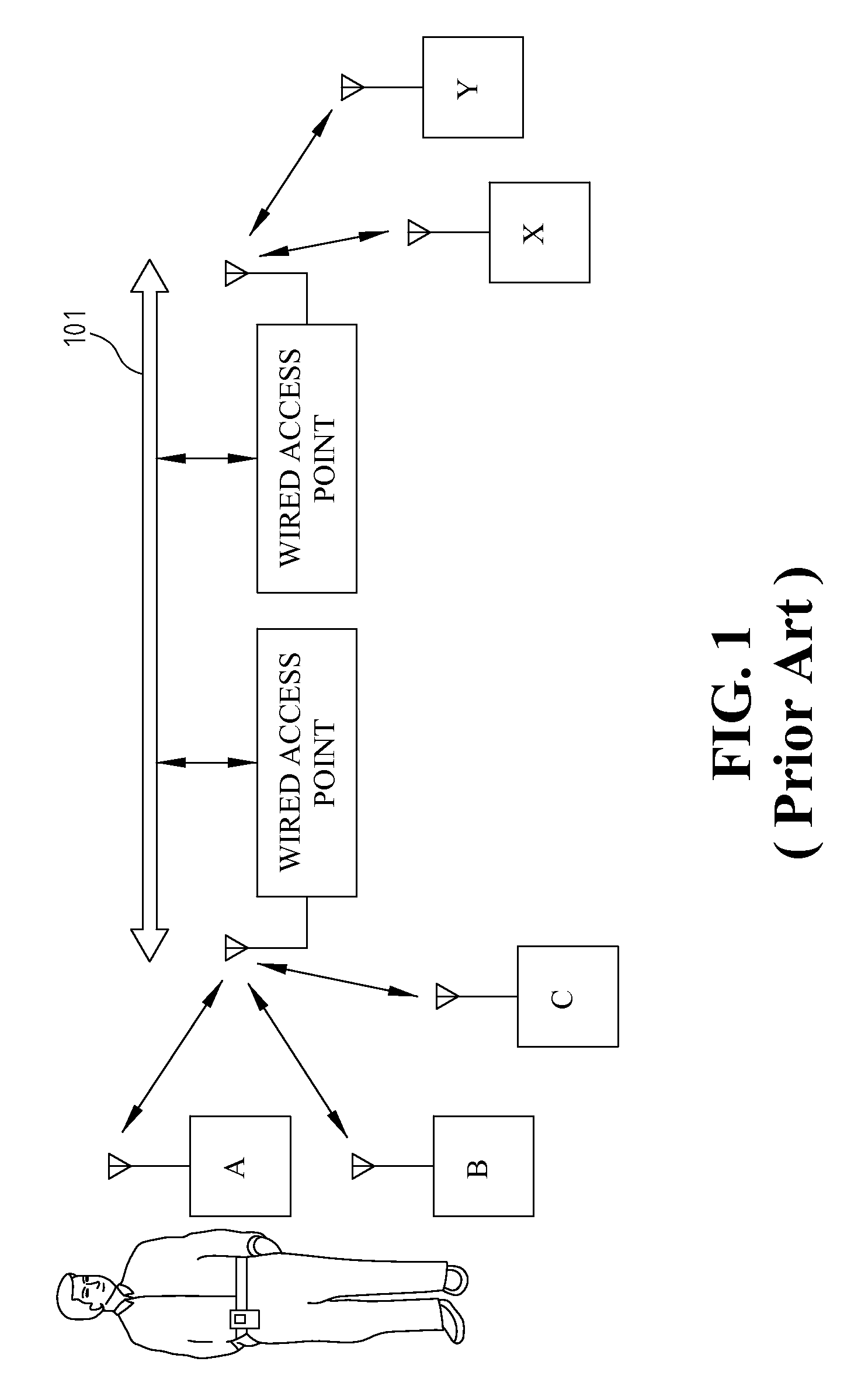
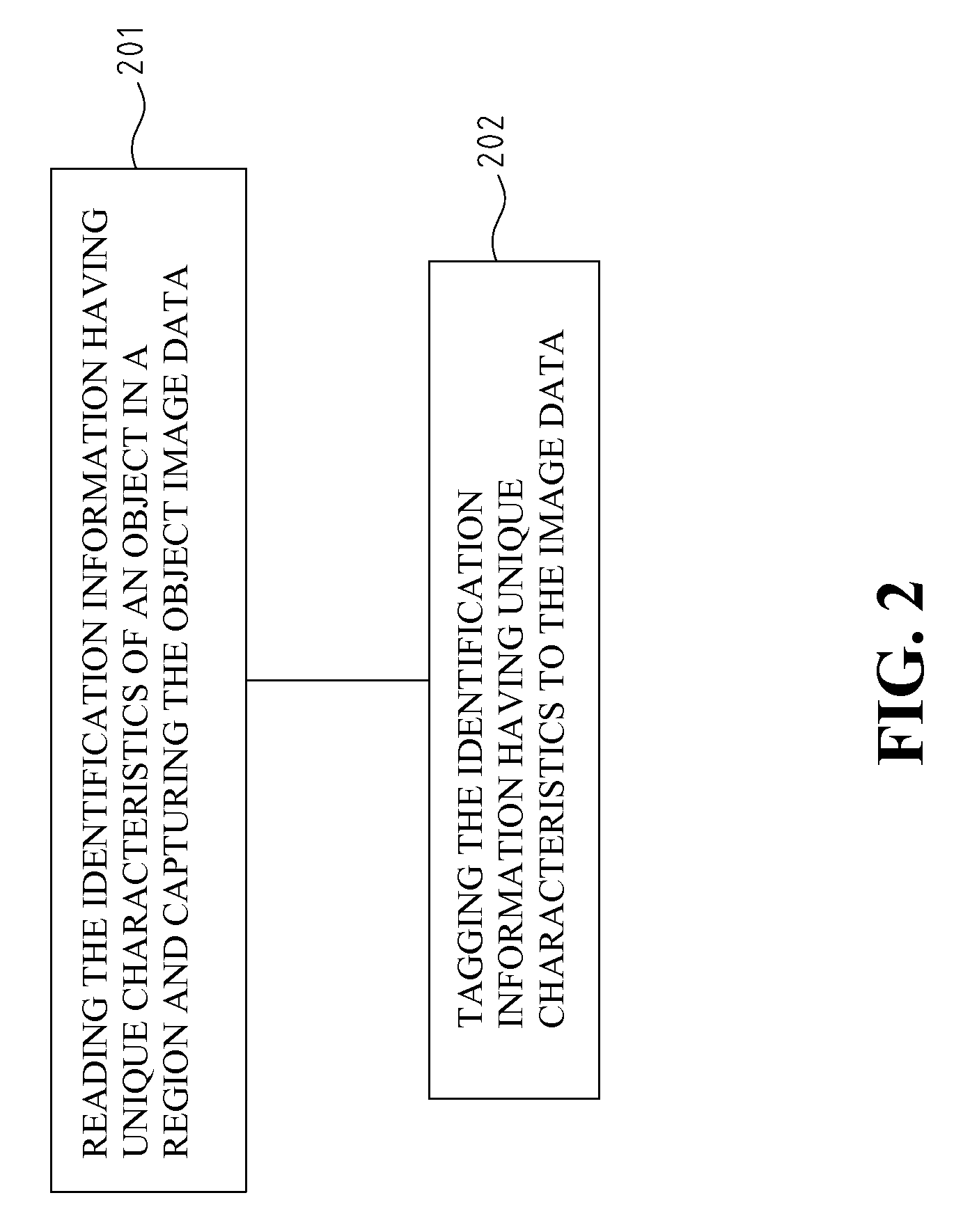
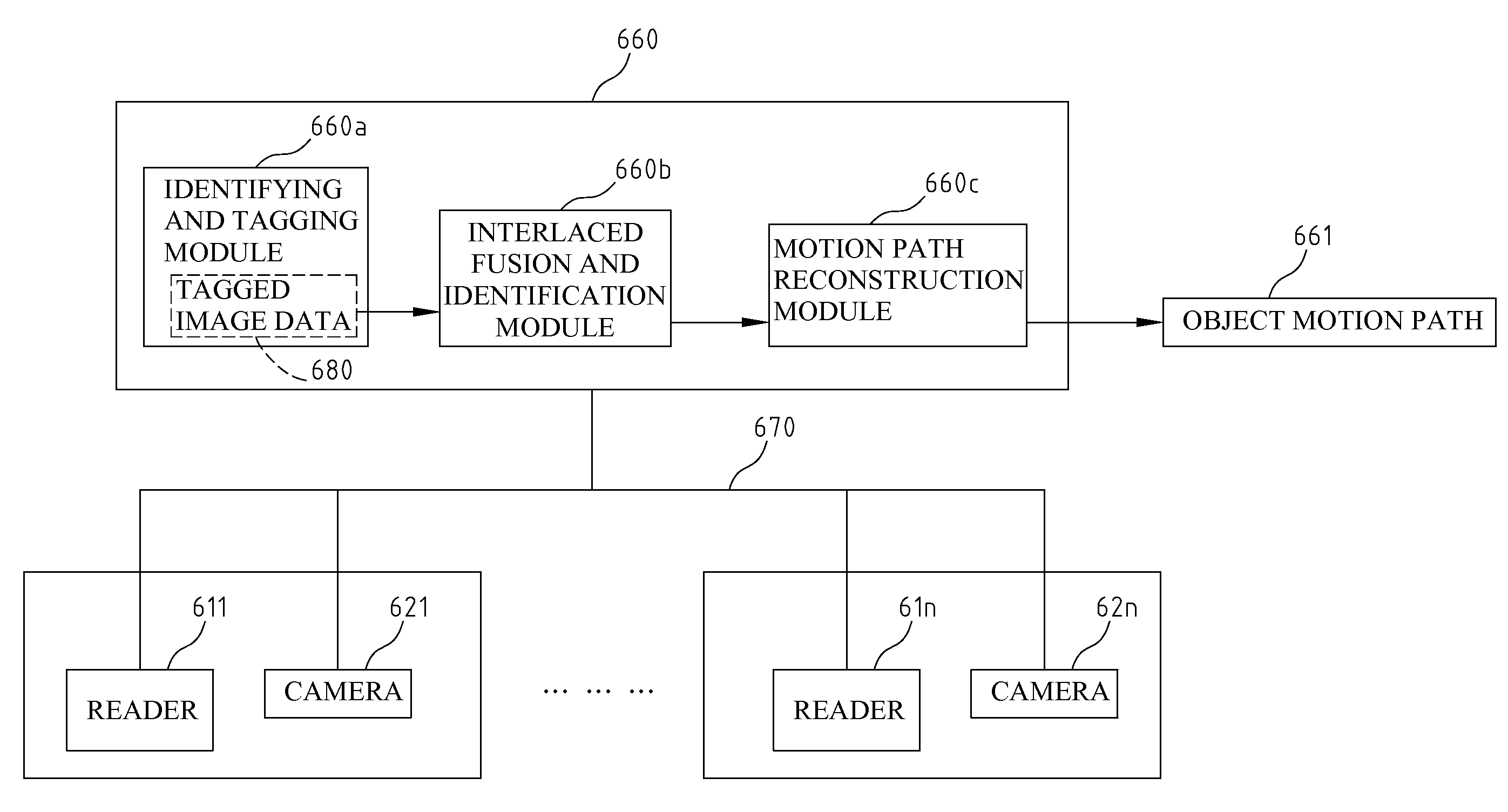
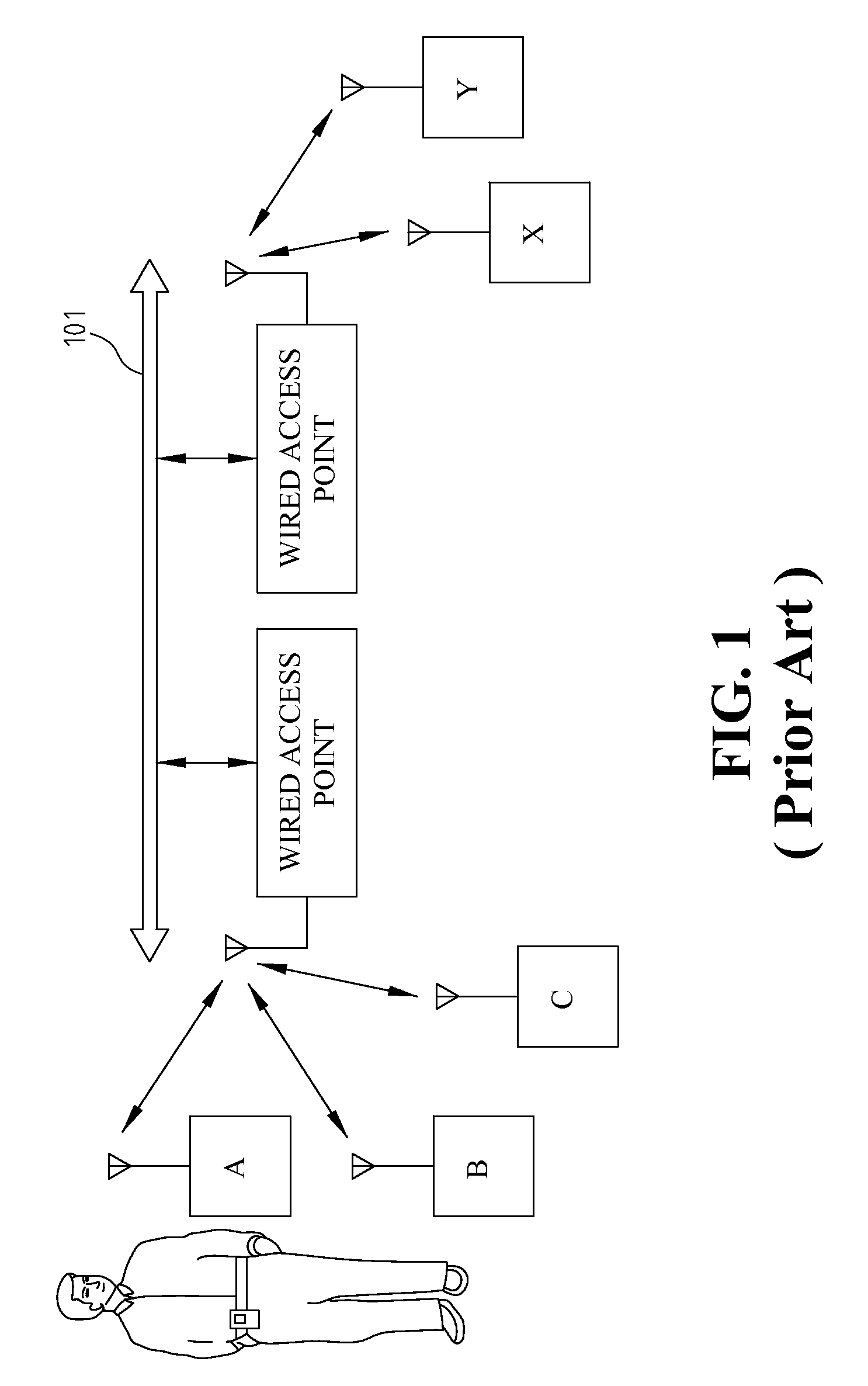
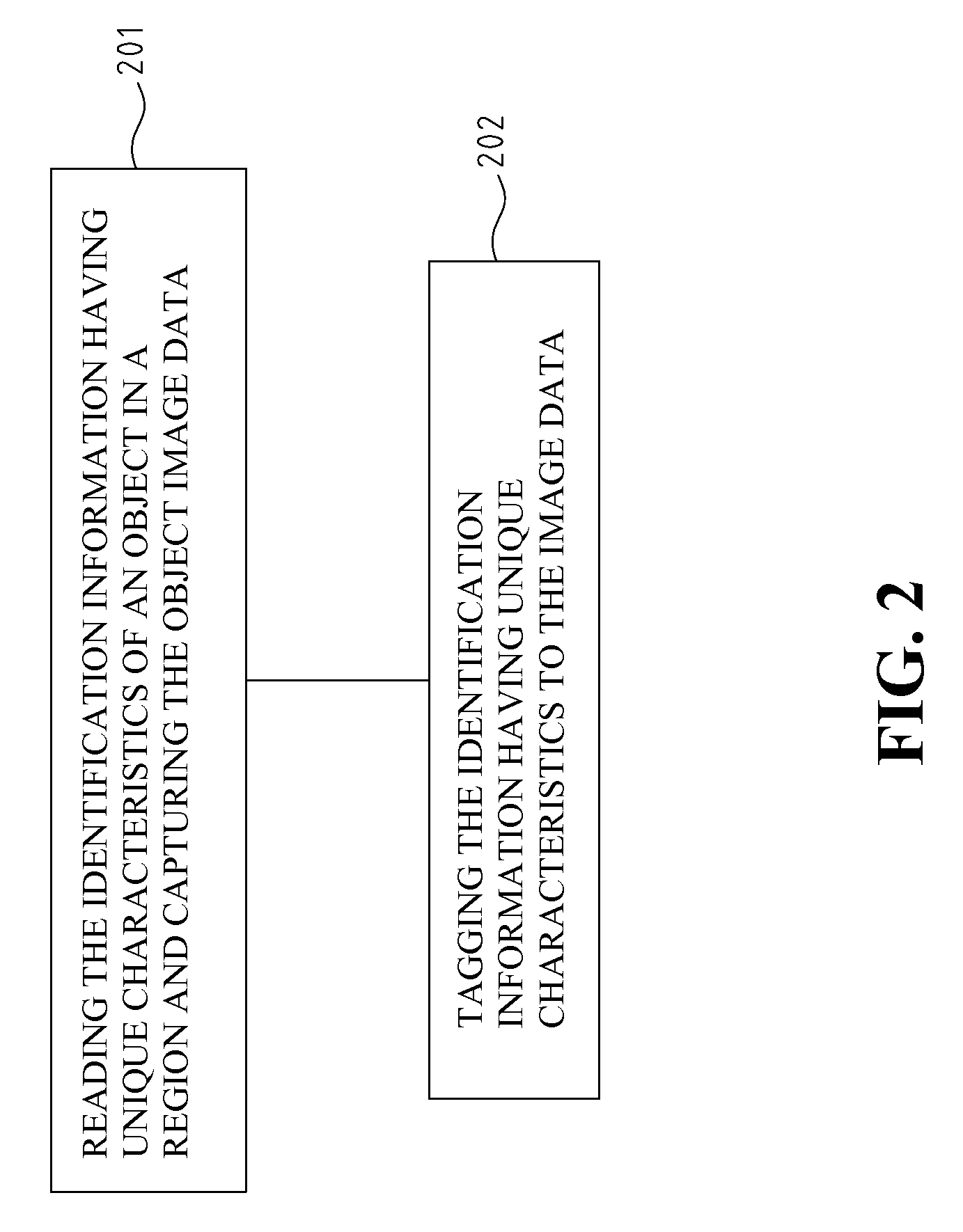
Tagging and path reconstruction method utilizing unique identification and the system thereof
ActiveUS8081215B2Fast rebuildTelevision system detailsPosition fixationPattern recognitionImaging data
Disclosed is a tagging and path reconstruction method utilizing unique identification characteristics and the system thereof. The tagging and path reconstruction system comprises a plurality of readers for reading identification information having unique IDs, a plurality of cameras for taking object's image data, and a server. The server includes an identifying and tagging module, an interlaced fusion and identification module, and a path reconstruction module. The identifying and tagging module identifies and tags the object image data with unique IDs. The interlaced fusion and identification module filters, checks and updates the tagged object image data. The path reconstruction module recovers the tagged object image data, lets them regress to their original identity data, and reconstructs the motion path of each object.
Owner:IND TECH RES INST
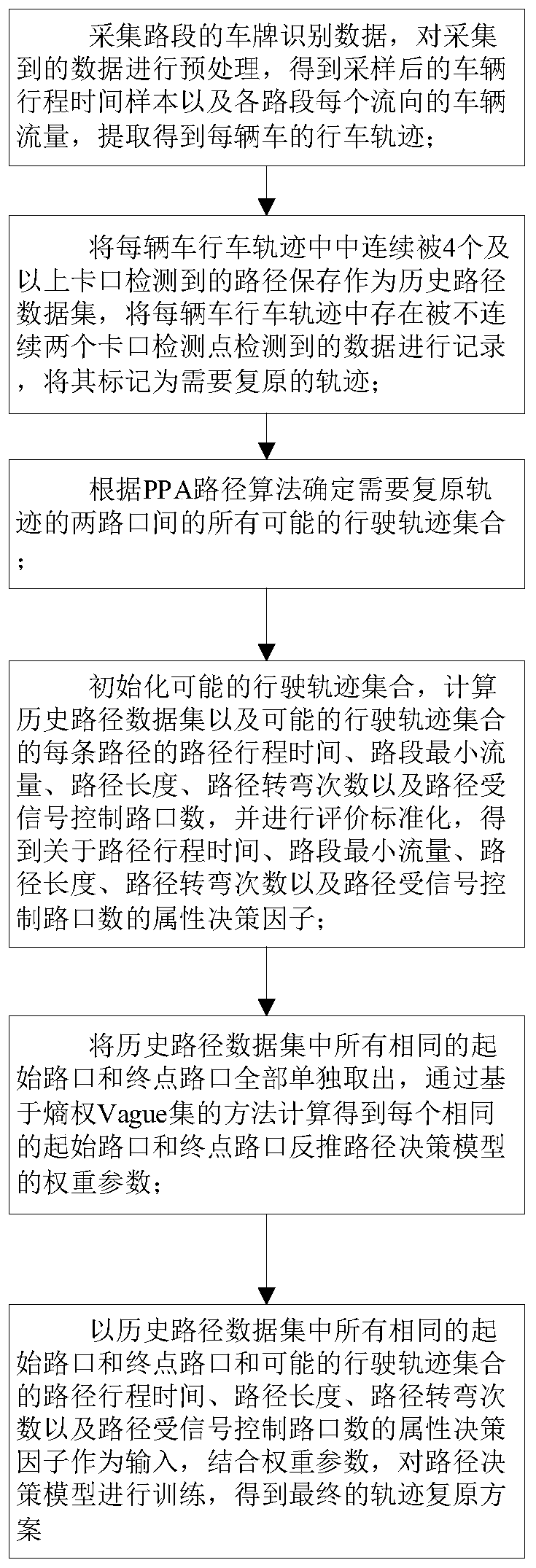
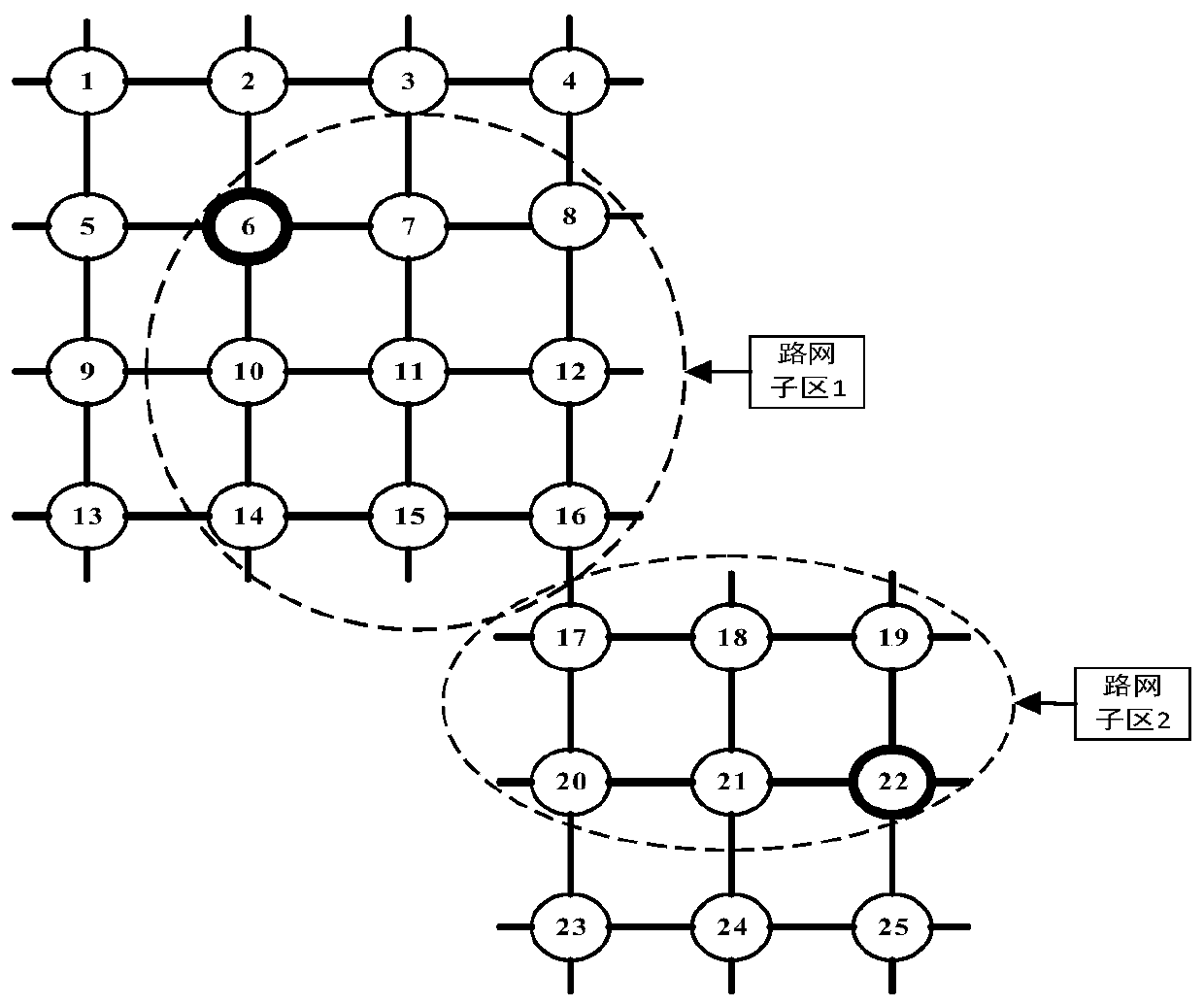
Urban traffic chain reconstruction method based on checkpoint video data
ActiveCN110276950AHigh speedAdaptable to the environmentDetection of traffic movementPath lengthControl signal
According to the invention, the method comprises the steps: employing a PPA path search algorithm (a potential path area path search algorithm) to construct an initial decision path; employing a decision attribute factor model training method to finally output a real path restored by the algorithm; selecting five decision optimization factors, namely path travel time, path length, path turning times and path controlled signal gate number, as decision attributes, so that the decision factors for track recovery have higher environmental adaptability. The setting of the decision weight is comprehensively determined by subjective and objective data, so the method is more scientific and practical, the algorithm speed is high, and large-scale data can be processed; the method is suitable for path reconstruction of small and medium-sized road networks, can complete restoration of missing detection vehicle tracks with high precision, has good robustness, and lays a foundation for further statistics of urban traffic road network microcosmic parameters.
Owner:SOUTH CHINA UNIV OF TECH +2
Routing method and routing system
ActiveCN107959630AGuaranteed continuityFast path refactoringRadio transmissionData switching networksRouting tableBusiness data
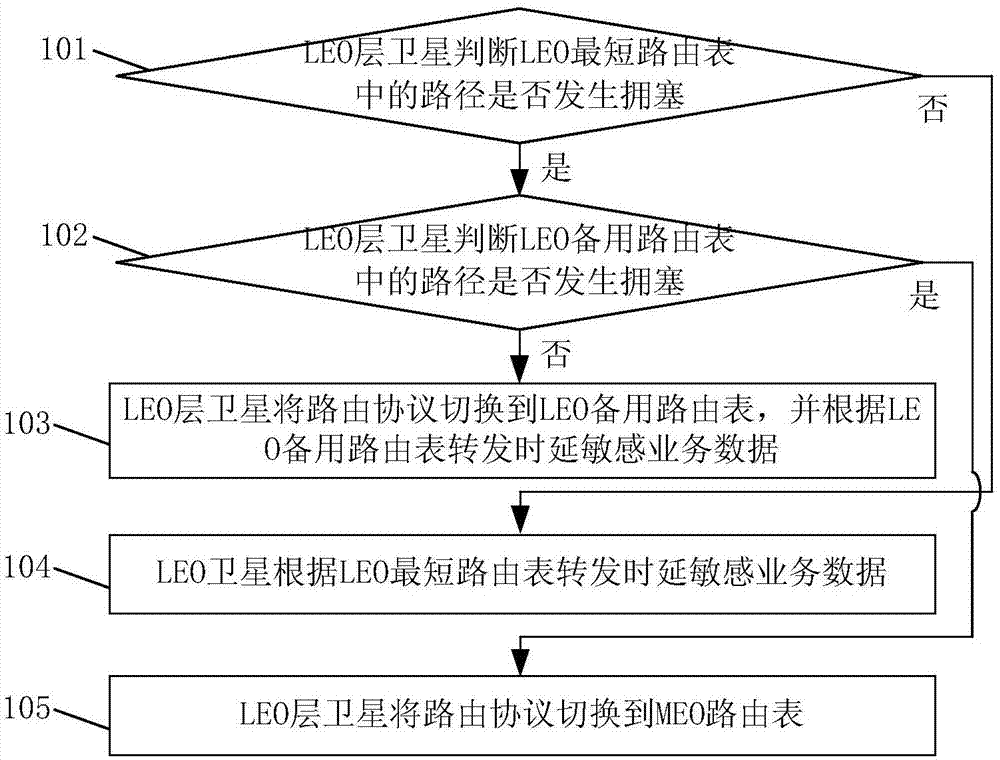
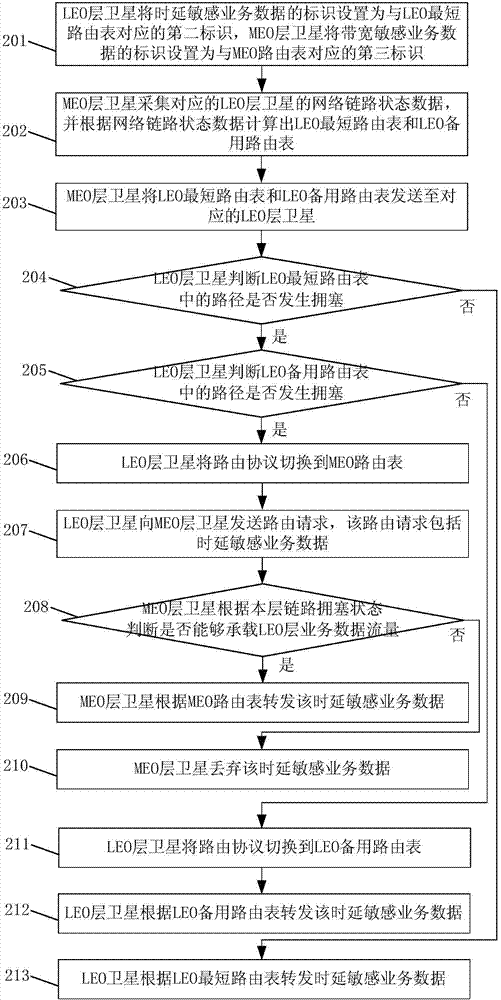
The invention discloses a routing method and a routing system. The method comprises the steps: enabling an LEO layer satellite to judge whether a path in an LEO shortest routing table is congested ornot; judging whether a path in an LEO standby routing table is congested or not if the LEO layer satellite determines that the path in the LEO shortest routing table is congested, or else switching arouting protocol to the LEO standby routing table, and carrying out the forwarding of the time delay sensitive business data according to the LEO standby routing table. The method can achieve the quick solving of the network congestion during congestion, can achieve the quick path reconstruction, and guarantees the continuity of business data.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
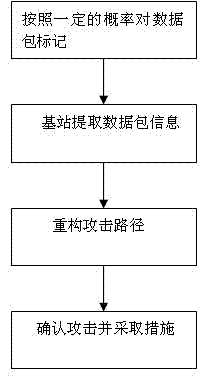
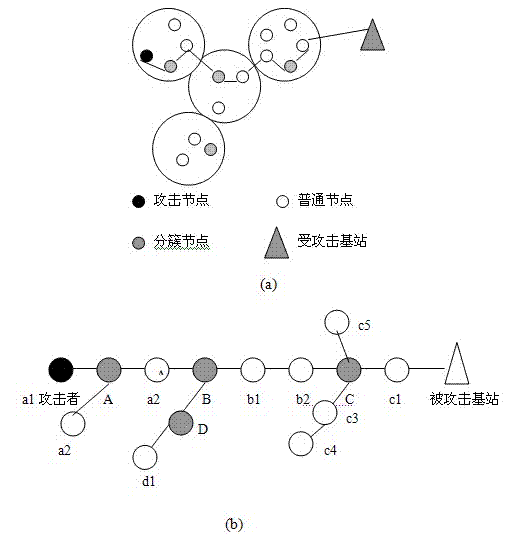
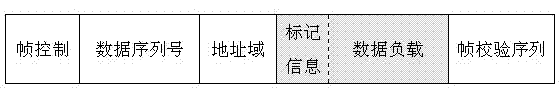
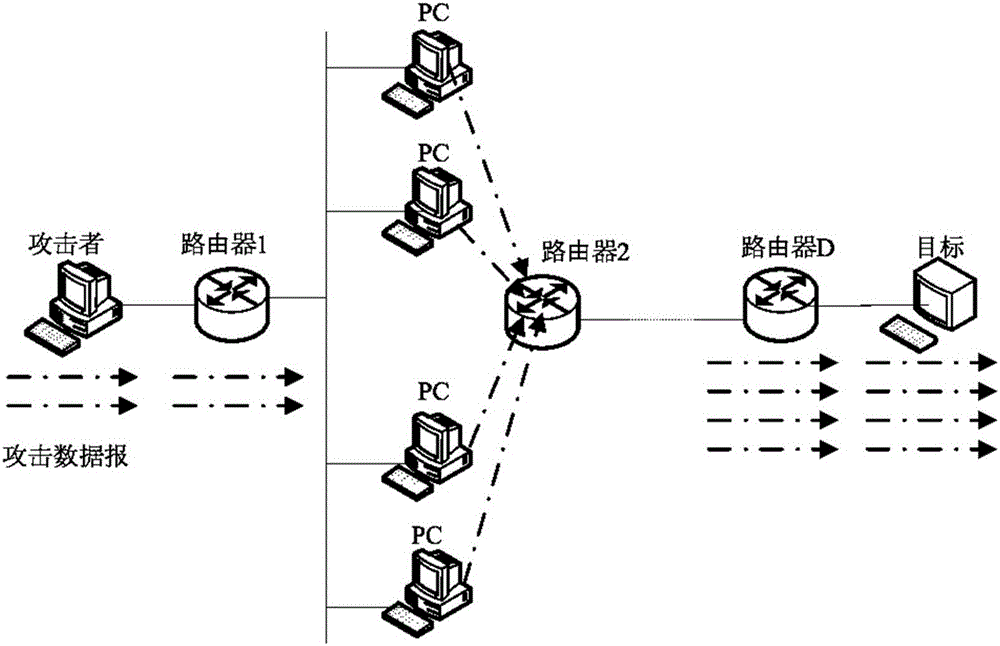
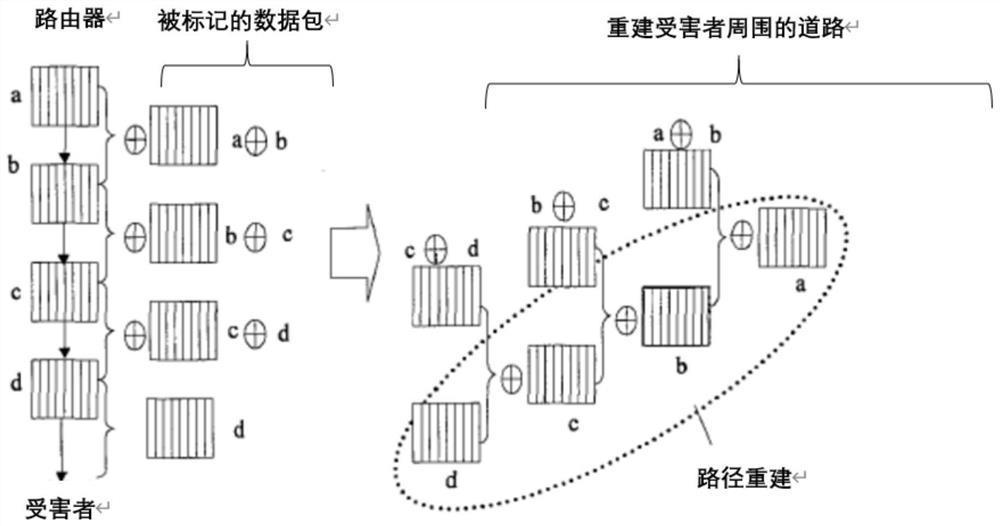
Method of tracking DDoS attack in wireless sensor network
InactiveCN103249177AFast and Efficient TrackingIncrease the burdenNetwork topologiesTransmissionAnti jammingWireless mesh network
The invention discloses a method of tracking DDoS (distributed denial of service) attack in the wireless sensor network. According to the method, data packets are marked, and source tracking is performed by utilizing the marked data packets, so as to identify malicious attack nodes. The marking method comprises the following steps: setting marking information (first, top, tail, start, end, distance) of six marking domains in the data packets, then marking cluster head node data packets and common node data packets, and discovering attack paths and proceeding accordingly through path reconstruction. The method has excellent convergence, reduces uncertainty of the attack source, and improves the anti-jamming capability.
Owner:CHANGZHOU UNIV
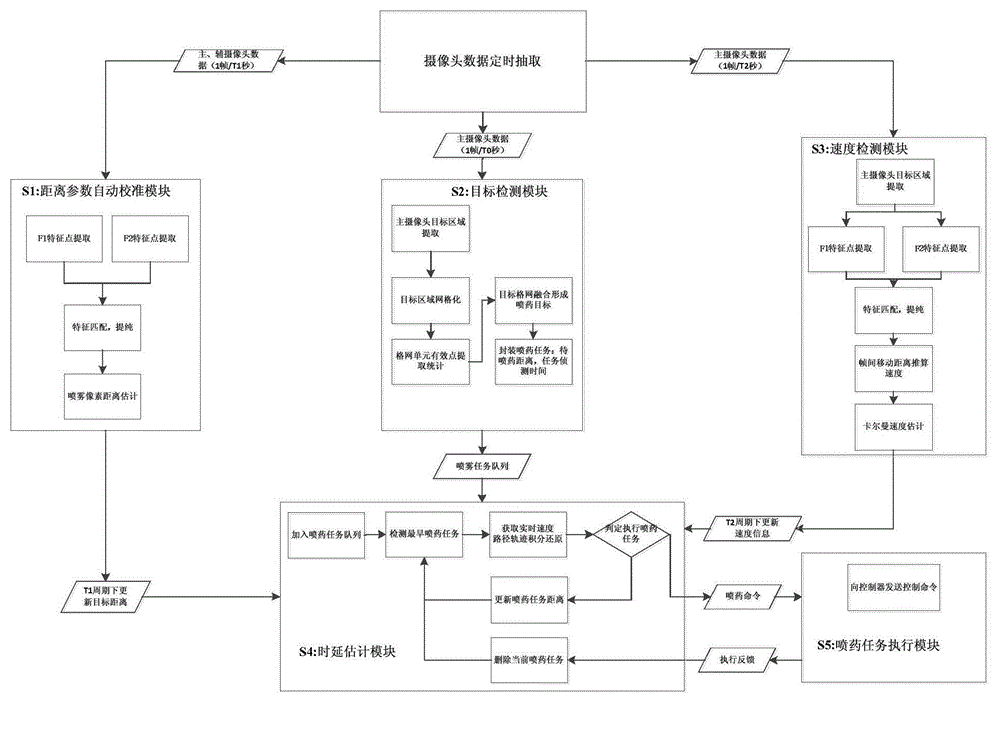
Machine vision based adaptive precise mist spray device and method
InactiveCN104615150ASolve control problemsImprove efficiencyCharacter and pattern recognitionClosed circuit television systemsMachine visionSolenoid valve
The invention relates to machine vision based adaptive precise mist spray device and method. The device comprises a mechanical arm, a housing, a core calculating module, an image acquiring module and a mist spray module; the housing is fixed on the mechanical arm; the core calculating module is fixed into the housing; the image acquiring module comprises a main camera, a secondary camera and a light compensating lamp which are mounted on the housing and connected with the core calculating module; the mist spray module comprises a medicine storing box, a spraying pipe and a nozzle which are mounted on the mechanical arm; a solenoid valve which is connected with the core calculating module is mounted on the spraying pipe. According to the device, the machine vision technology is utilized, the mist spray task target distribution information is acquired on real time when operating an agricultural mechanism, the single camera path reconstruction technology and kalman filtering algorithm are combined and carried out to estimate the real-time moving track of the mechanism, then the accurate mist spray time of a spray head is calculated according to the moving track of the working mechanism, and therefore, the accurate variable mist spray can be achieved, the use efficiency of drugs can be increased, and the environmental pollution can be reduced.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
SDN-based data flow tracing method
ActiveCN107070895AOvercome spaceOvercome the problem of not easy to expandTransmissionData streamData set
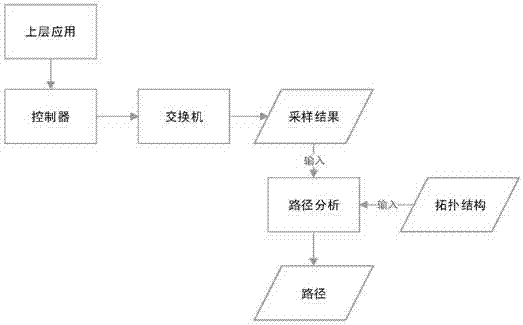
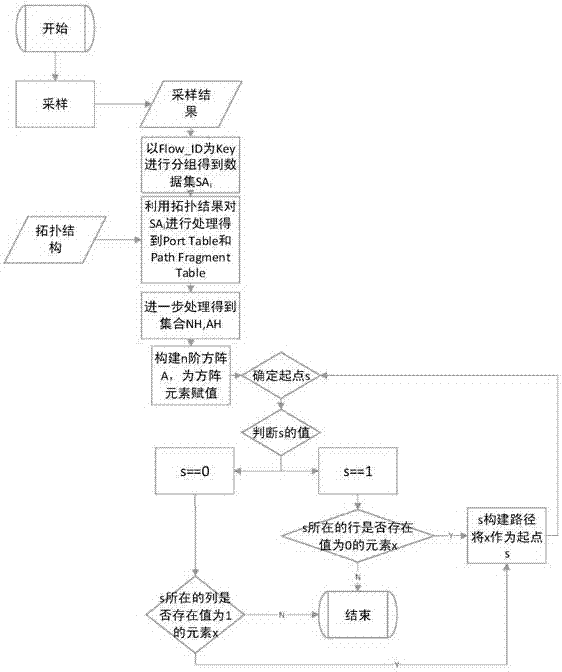
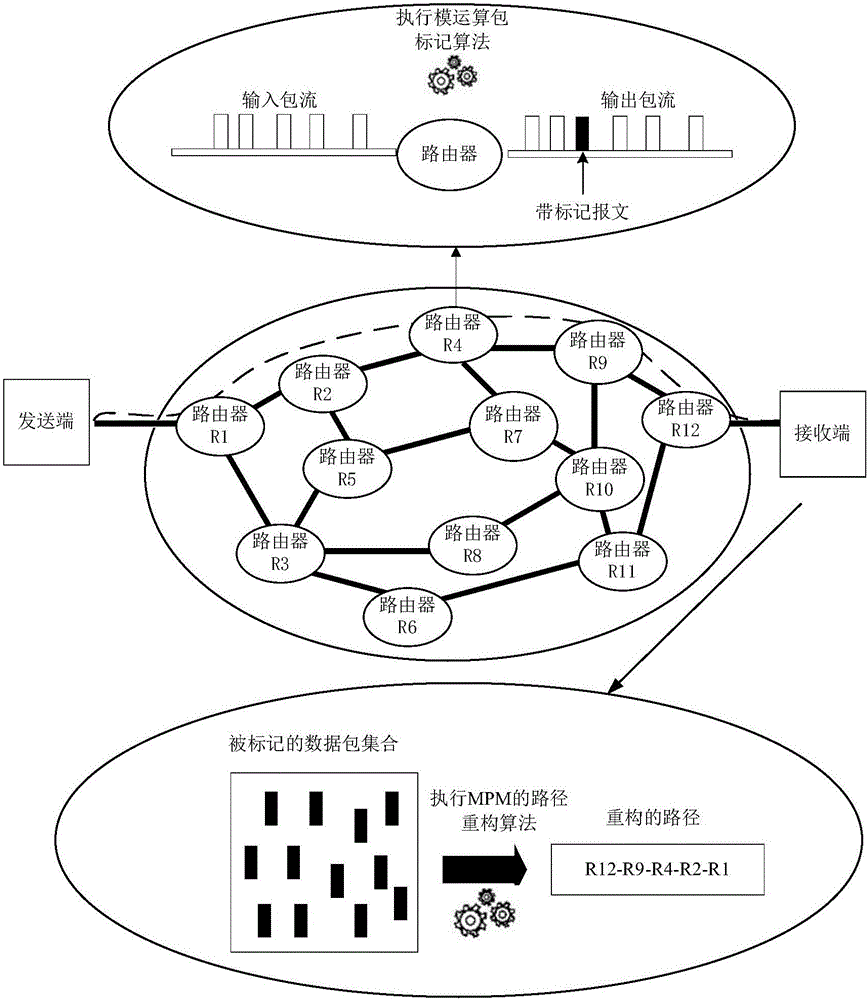
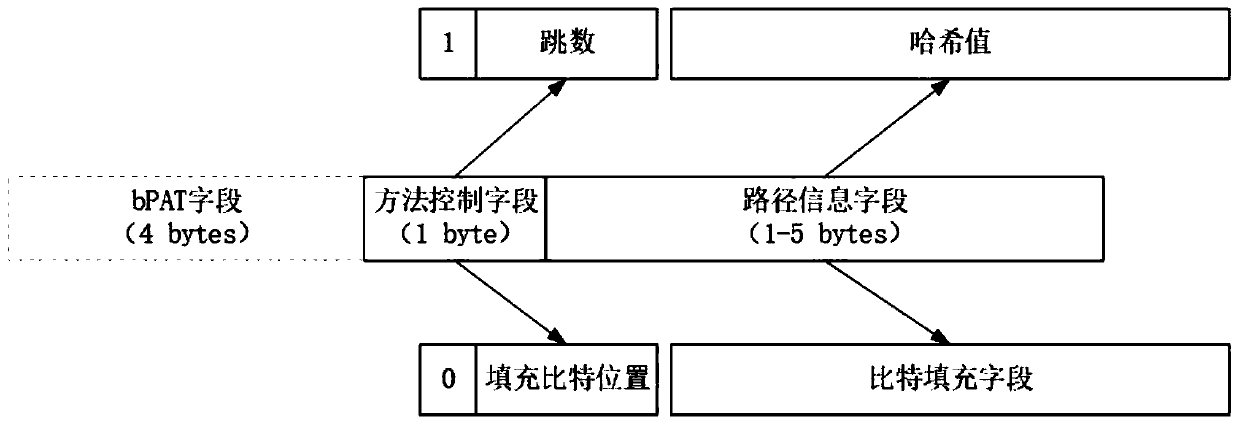
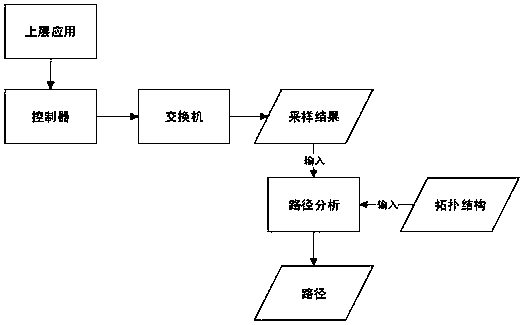
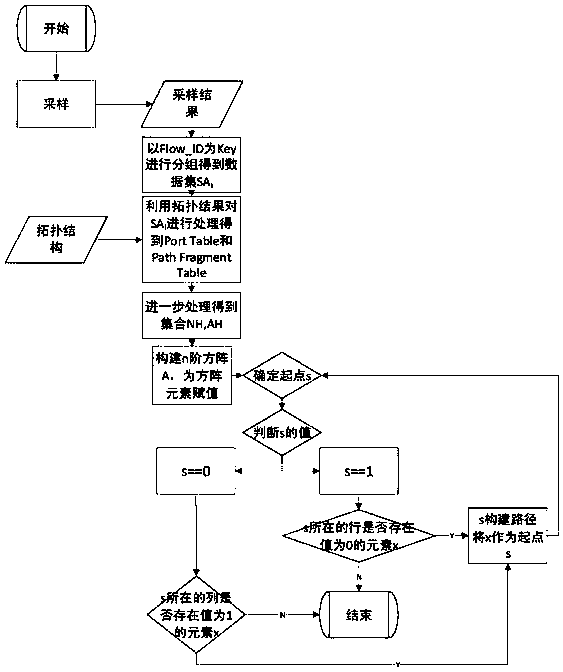
The present invention provides an SDN-based data flow tracing method. The method comprises a first step of sampling a designated field regularly by an SDN switch, so as to obtain data package information Flow_ID and switch information, wherein the switch information comprises a switch identifier Switch_ID and a data package input port; a second step of dividing the data package information Flow_ID and switch information into groups with Flow_ID as a Key, so as to obtain a data set SA of each group, wherein i represents data sets of different groups; a third step of performing path analysis on the data set SA of each group according to a network topological structure G of the SDN; and a fourth step of determining a path start point according to a path analysis result, and performing path reconstruction, so as to obtain a path of a data package or a data flow. In the method, the path of the data package or the data flow is reconstructed, so that a source of an attack source can be traced.
Owner:INST OF INFORMATION ENG CAS
Big data processing method based on interactive cloud computing and artificial intelligence server
InactiveCN112162999AEnsure safetyAvoid incompleteDigital data information retrievalDigital data protectionPathPingData set
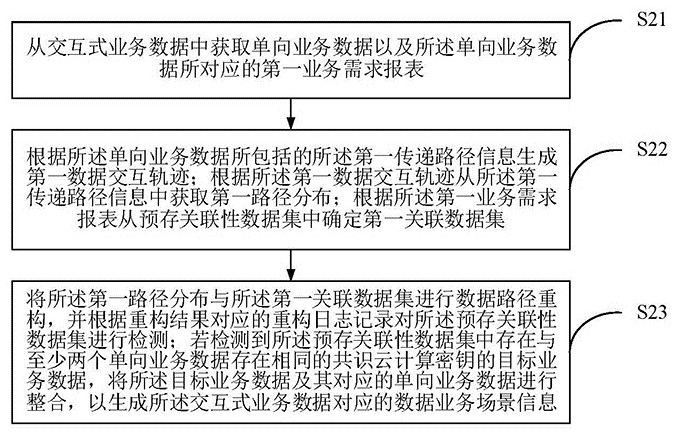
According to the big data processing method based on interactive cloud computing and the artificial intelligence server, the first data interaction track between different data service processing endscan be generated by obtaining the one-way service data and the first service demand report corresponding to the one-way service data, so that the first path distribution and the first associated dataset are determined. Therefore, service association can be carried out on the plurality of data service processing ends, and data path reconstruction is carried out to achieve restoration of a data service scene. According to the invention, by detecting the target service data, the security during service data integration can be ensured based on the consensus cloud computing key; and the unidirectional service data can be comprehensively considered to avoid the incompleteness of a data service scene, and the data security between the target service data and the unidirectional service data canbe ensured through the consensus cloud computing key. By means of the scheme, the scene missing problem and the data security problem existing when the data service scene is restored are solved.
Owner:翁海坤
Self-adaptive delay-sensing energy-saving method of optical wireless mixed broadband access network
ActiveCN105050136ALower latencySatisfaction DelayPower managementNetwork traffic/resource managementOptical wirelessWireless mesh network
The invention discloses a self-adaptive delay-sensing energy-saving method applied to the optical wireless mixed broadband access network. In the prior art, dormancy of an optical network unit can effectively improve the energy efficiency of the optical wireless mixed broadband access network, however, the energy efficiency of a continuous dormant gateway is not high, and delay of a system data packet may be aggravated. Thus, in the downlink direction of the optical wireless mixed broadband access network, the optical network unit can select the growth speed of the dormancy period adaptively according to the arrival rate of the data packet, thereby fully utilizing the delay tolerance of the data packet; and in the uplink direction, a wireless net-shaped network of multiple gateway balance loads can reduce delay and congestion caused of path reconstruction caused by dormancy of optical network unit, thereby reducing delay in the network. The method can enable the energy efficiency of the network to be maximal while satisfying delay of the data packet.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Tagging And Path Reconstruction Method Utilizing Unique Identification And The System Thereof
ActiveUS20090160942A1Fast rebuildTelevision system detailsPosition fixationPattern recognitionImaging data
Disclosed is a tagging and path reconstruction method utilizing unique identification characteristics and the system thereof. The tagging and path reconstruction system comprises a plurality of readers for reading identification information having unique IDs, a plurality of cameras for taking object's image data, and a server. The server includes an identifying and tagging module, an interlaced fusion and identification module, and a path reconstruction module. The identifying and tagging module identifies and tags the object image data with unique IDs. The interlaced fusion and identification module filters, checks and updates the tagged object image data. The path reconstruction module recovers the tagged object image data, lets them regress to their original identity data, and reconstructs the motion path of each object.
Owner:IND TECH RES INST
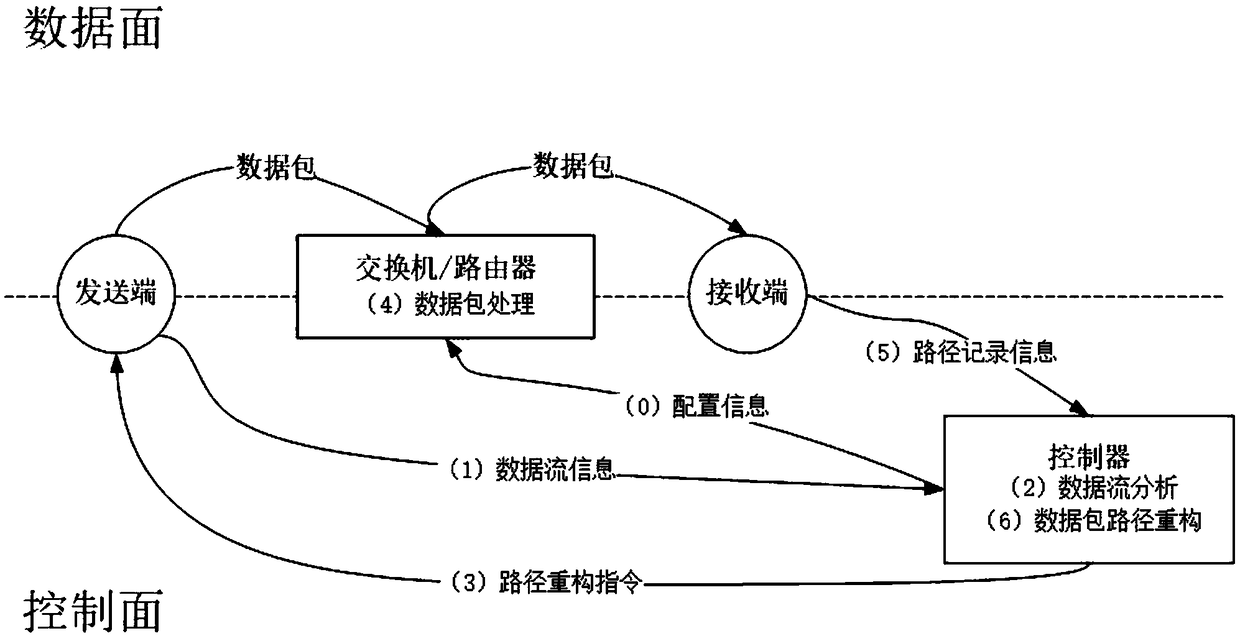
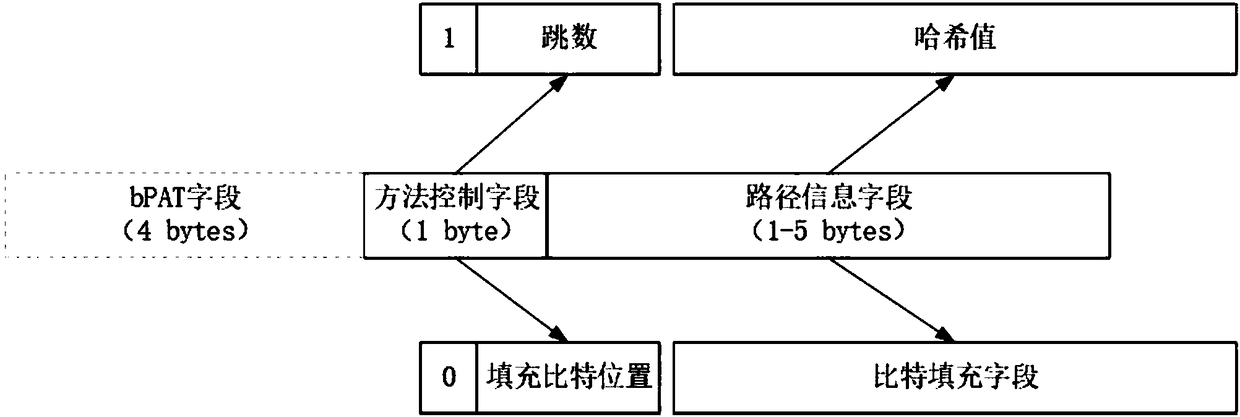
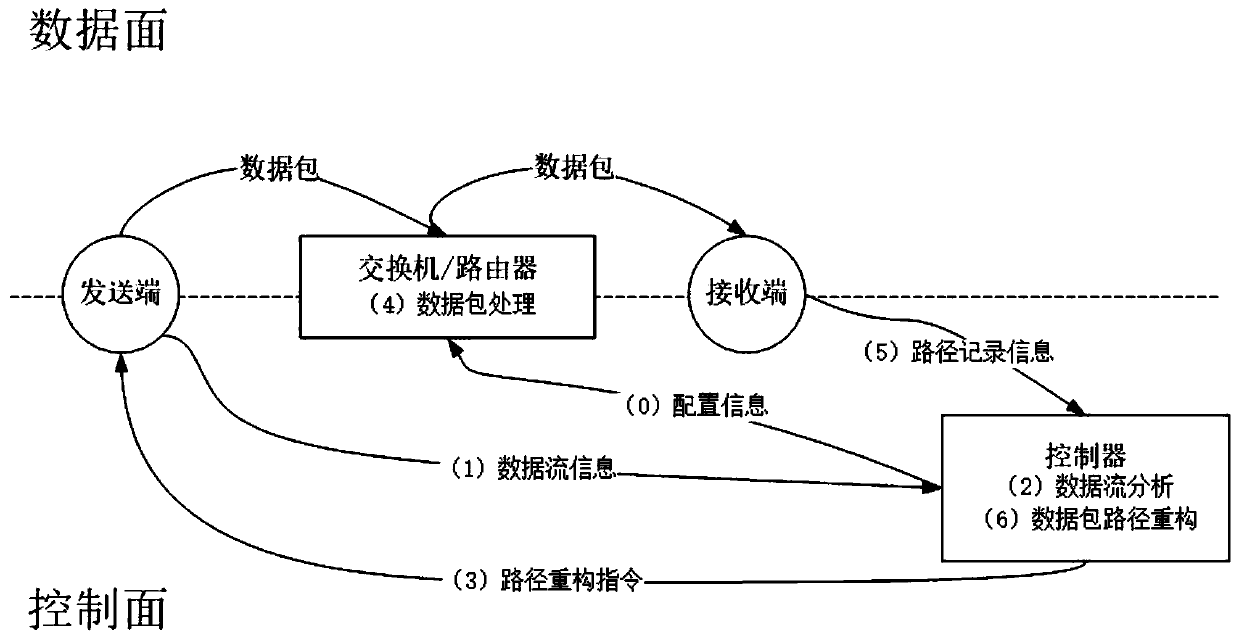
Data packet path reconstruction method in software defined network
ActiveCN108199970ALighten the computational burdenPrecise transmission pathData switching networksNetwork sizeComputer science
The invention discloses a data packet path reconstruction method in a software defined network. In a network initialization stage, a controller allocates an ID to each switch / router according to a network size. When a sending end generates a data packet, related data flow information is sent to the controller, and the controller decides a specifically used path reconstruction method and field allocation of a newly added data packet header, and feeds information back to the sending end. When the switches / routers forward the data packet, corresponding operation is executed according to the newlyadded packet header, and path-related information is recorded in the packet. Finally, an administration server in the network reconstructs a transmission path of the data packet according to the path-related information in the received data packet. The method provided by the invention has no special requirements for the category of the software defined network topology, has the characteristic oflow calculation overheads of the switches / routers, can still precisely reconstruct the transmission path of the data packet under the conditions of network failure and congestion, and greatly facilitates administration and failure checking of the software defined network.
Owner:ZHEJIANG UNIV
Fast alternative route distribution method based on overlay network environment
InactiveCN102055664AFast recoveryIncrease success rateData switching networksDistribution methodNetwork communication
The invention relates to the technical field of network communication, in particular to a fast alternative route distribution method based on overlay network environment. Aiming at the problem that the traditional overlay network alternative route distribution method has low recovery time efficiency, the method disclosed in the invention introduces the delay constraint during route reconstructionas the selection condition of alternative routes, which is beneficial to the selection of an alternative route with fast recovery speed; the process of selecting a unique alternative route is converted into the selection of a set of alternative routes by expanding a failure area, and the success probability of selecting a high quality alternative route can be increased. The fast alternative routedistribution method based on overlay network environment can be used for reducing the delay time of failure route recovery and increase the success rate of route recovery.
Owner:WUHAN UNIV
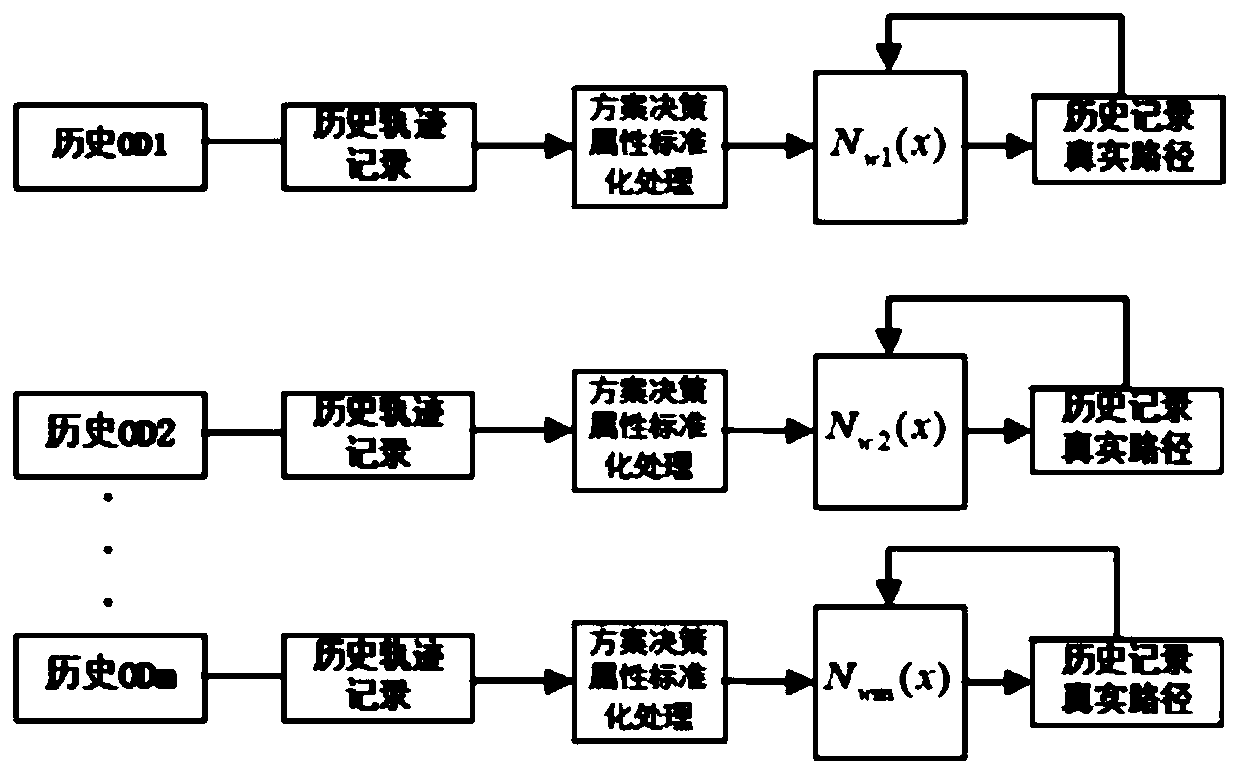
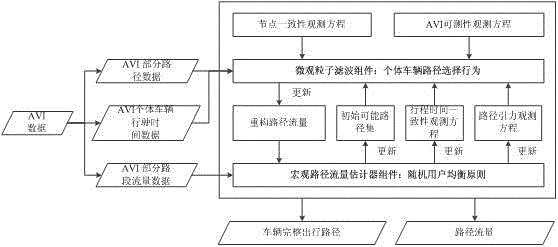
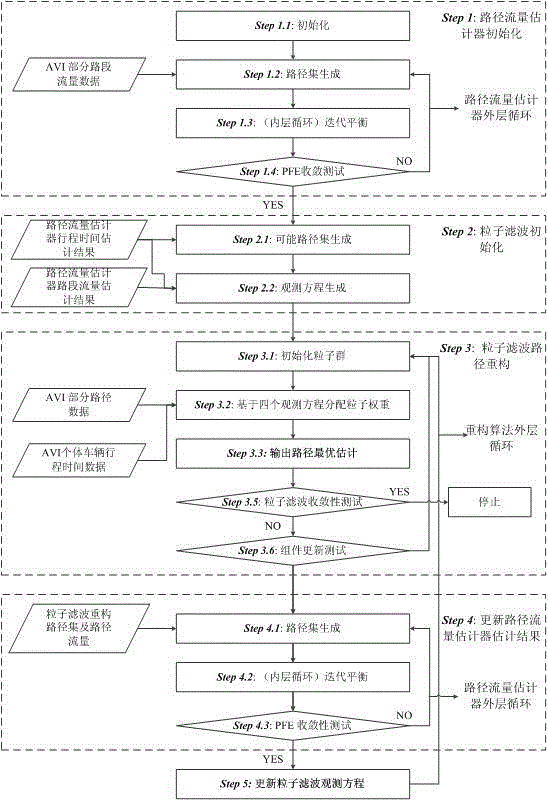
Vehicle travel path reconstruction macro/micro integrated new method based on automatic vehicle identification data
The invention belongs to the field of traffic planning and management and specifically relates to a vehicle travel path reconstruction macro / micro integrated new method based on automatic vehicle identification (AVI) data. The method constructs a macro / micro integrated reconstructed frame only by utilizing the automatic vehicle identification data and is characterized by, in micro level, reconstructing vehicle paths based on individual path selection principle and with particle filter theory being integrated, and increasing a reconstruction path traffic and path set constraint for a path traffic estimator in macro level; and in the macro level, realizing path traffic estimation based on random user equalization principle and with the path traffic estimator being integrated, and updating travel time consistency of particle filter and a path gravitation observation equation. Through the method, high-precision and complete vehicle travel paths and path traffic and road section traffic can be obtained under the conditions that only the AVI data is available and the AVI coverage rate is low.
Owner:TONGJI UNIV
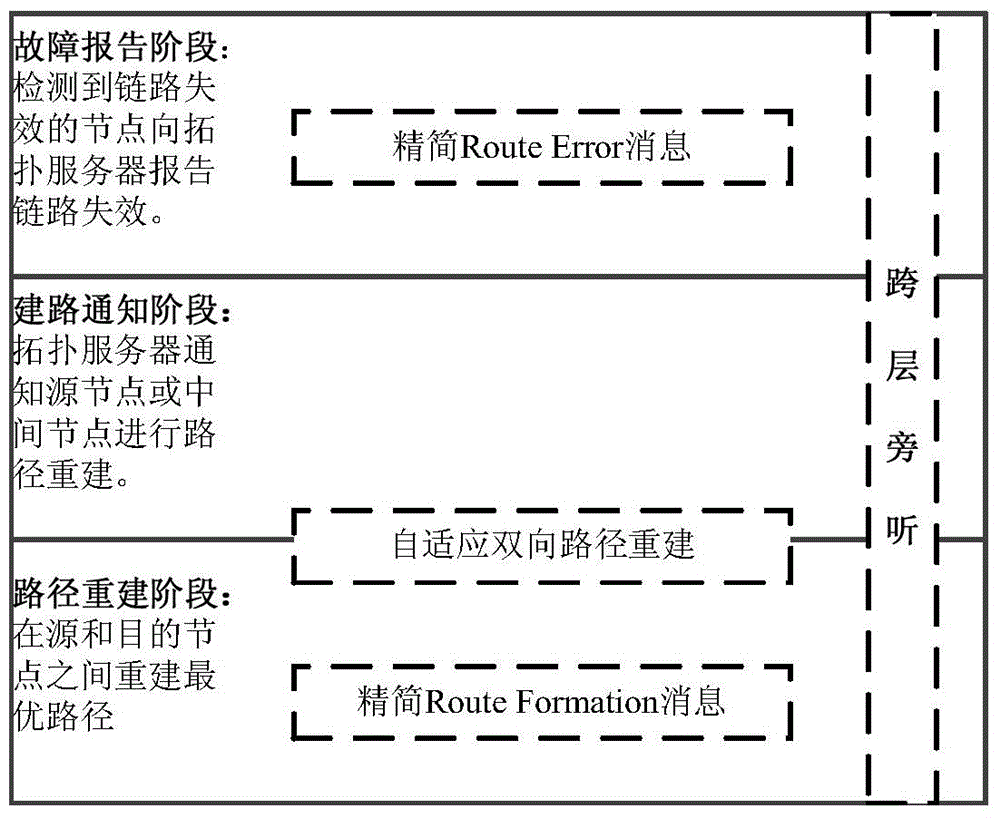
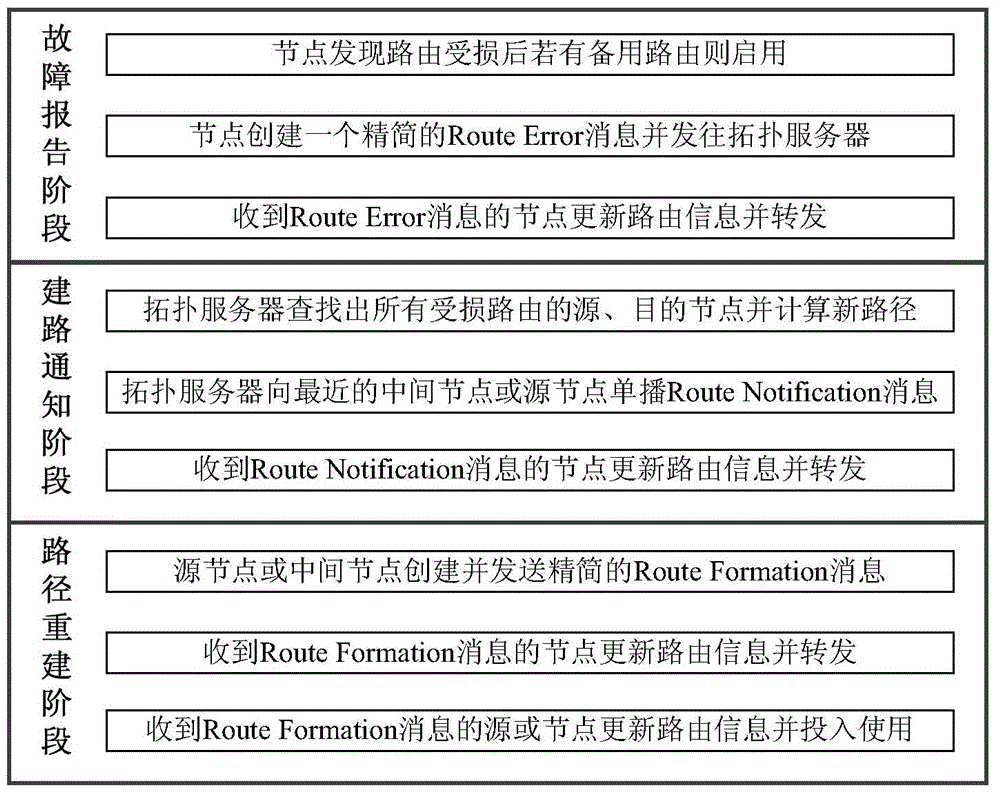
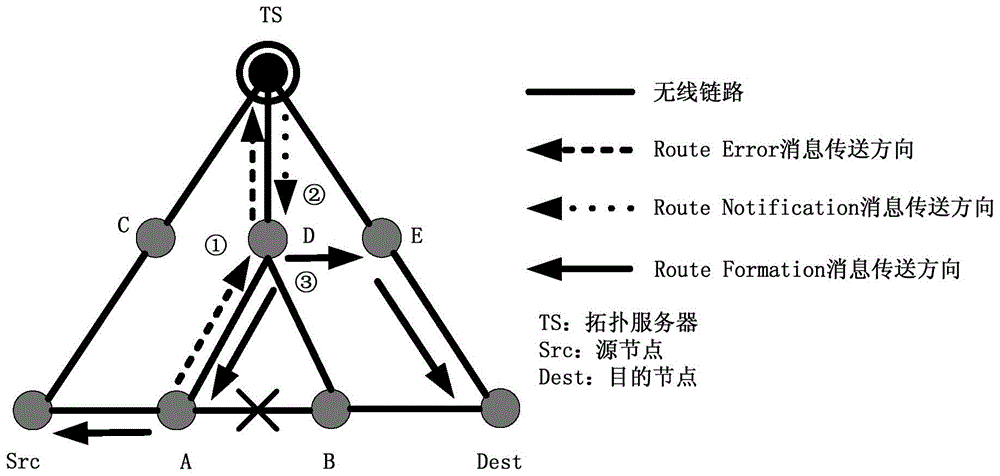
HR-WPAN Mesh (high-rate wireless personal area networks mesh) network efficient route repair method based on self-adaptation two-way path rebuilding
The invention provides an HR-WPAN Mesh (high-rate wireless personal area networks mesh) network efficient route repair method based on self-adaptation two-way path rebuilding. Through adopting four new mechanisms of self-adaptation two-way path re-building, Route Error message simplification, Route Formation message simplification and inter-layer auditing, the method solves the four problems that the existing HR-WPAN Mesh network route repair method based on a topology server adopts a reverse path rebuilding mode, so that the redundancy control expenditure and data grouping waiting delay are caused, when the end points of two damaged paths are mutually used as source and target nodes, the path rebuilding is repeatedly carried out, and when the Route Error message and the Route Formation message have redundancy fields and link failure, data groups cached by the upstream node can be easily lost due to route information limitation. The method has the advantages that the speed of putting the repaired route into use is accelerated, the data grouping transmission success rate is improved, and the control expenditure and the data grouping average time delay are reduced. The fast and efficient route repair method provided by the invention comprises three steps including fault reporting, path building notification and path rebuilding during the operation.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
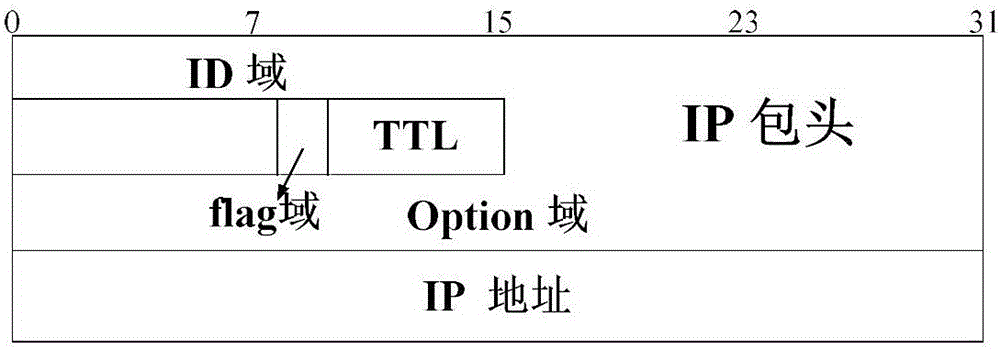
Modulo operation based denial of service attack trace back method
InactiveCN105791275AReduce the numberReduce the burden onData switching networksModulo operationPath reconstruction
The present invention provides a modulo operation based denial of service attack trace back method. The method includes a first step of establishing a modulo operation packet marking method by using an identification domain of an IP header, namely an ID domain; a second step of forwarding node information of a router by using a node sampling method, and writing a routing position and a routing address in a marking space of a data packet; a third step of performing modulo operation by using a value of the ID domain in the IP header, so as to realize routing marking, namely determine that which router on an attack path performs marking operation on a certain data packet; and a fourth step of detecting, by a victim end, marking information in the data packet, so as to reconstruct the path. Through introduction of the modulo operation, it is calculated that which router on the attack path needs to perform marking operation on an existing data packet, so that the burden of each router on a forwarding path is reduced, the quantity of the data packets for path reconstruction is greatly reduced, and a start source of denial of service attack is effectively identified.
Owner:SHANGHAI JIAO TONG UNIV +1
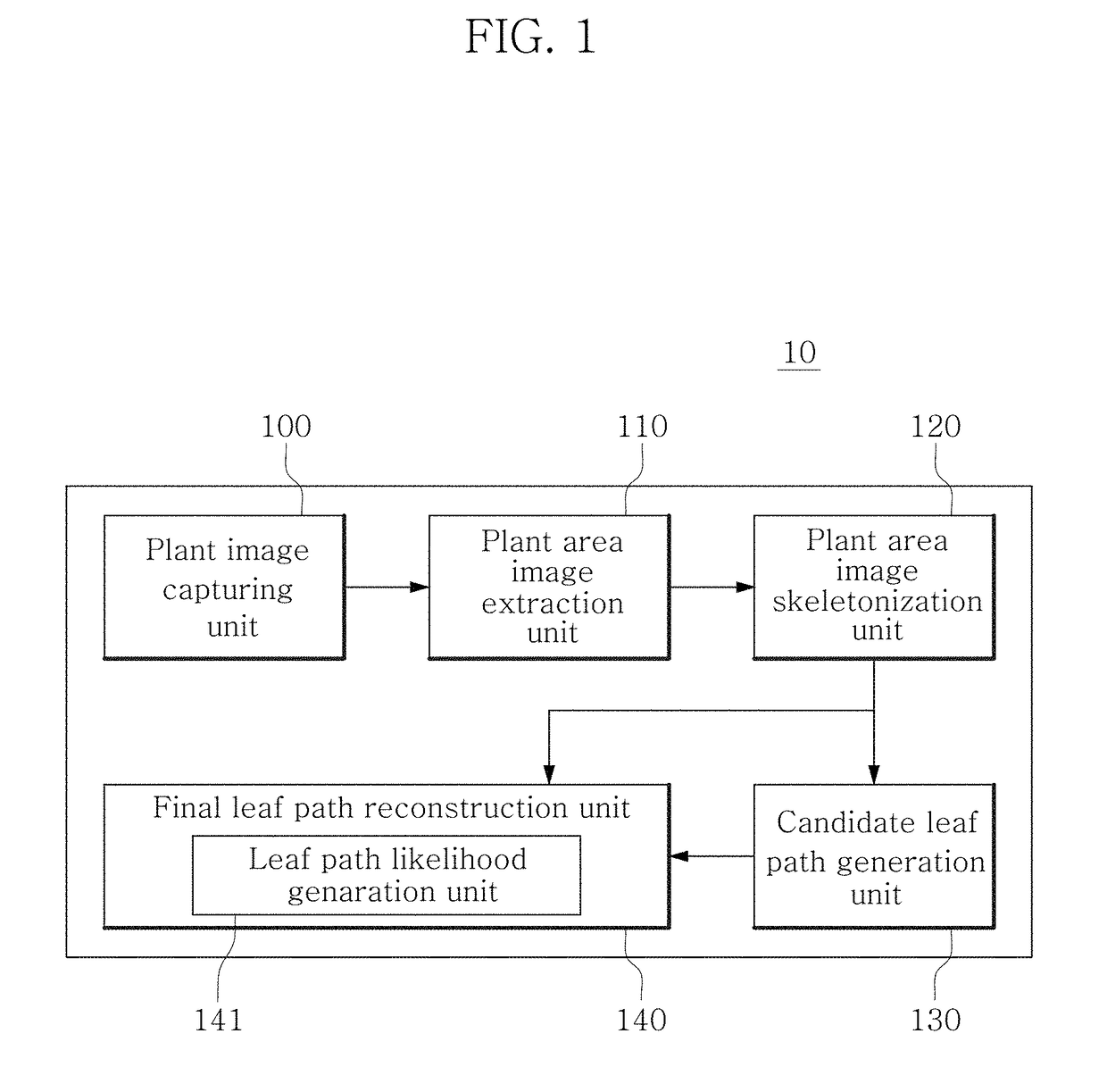
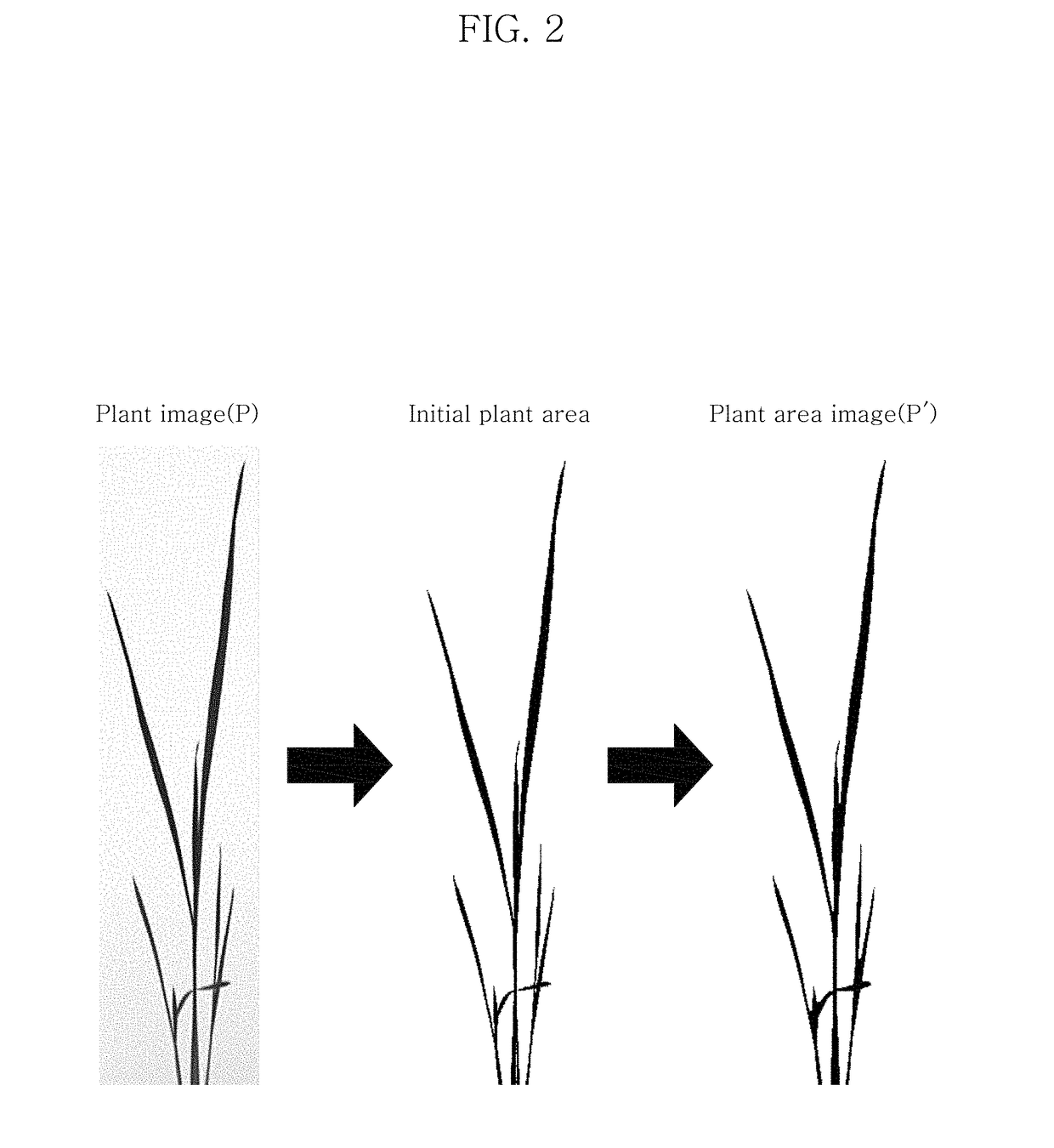
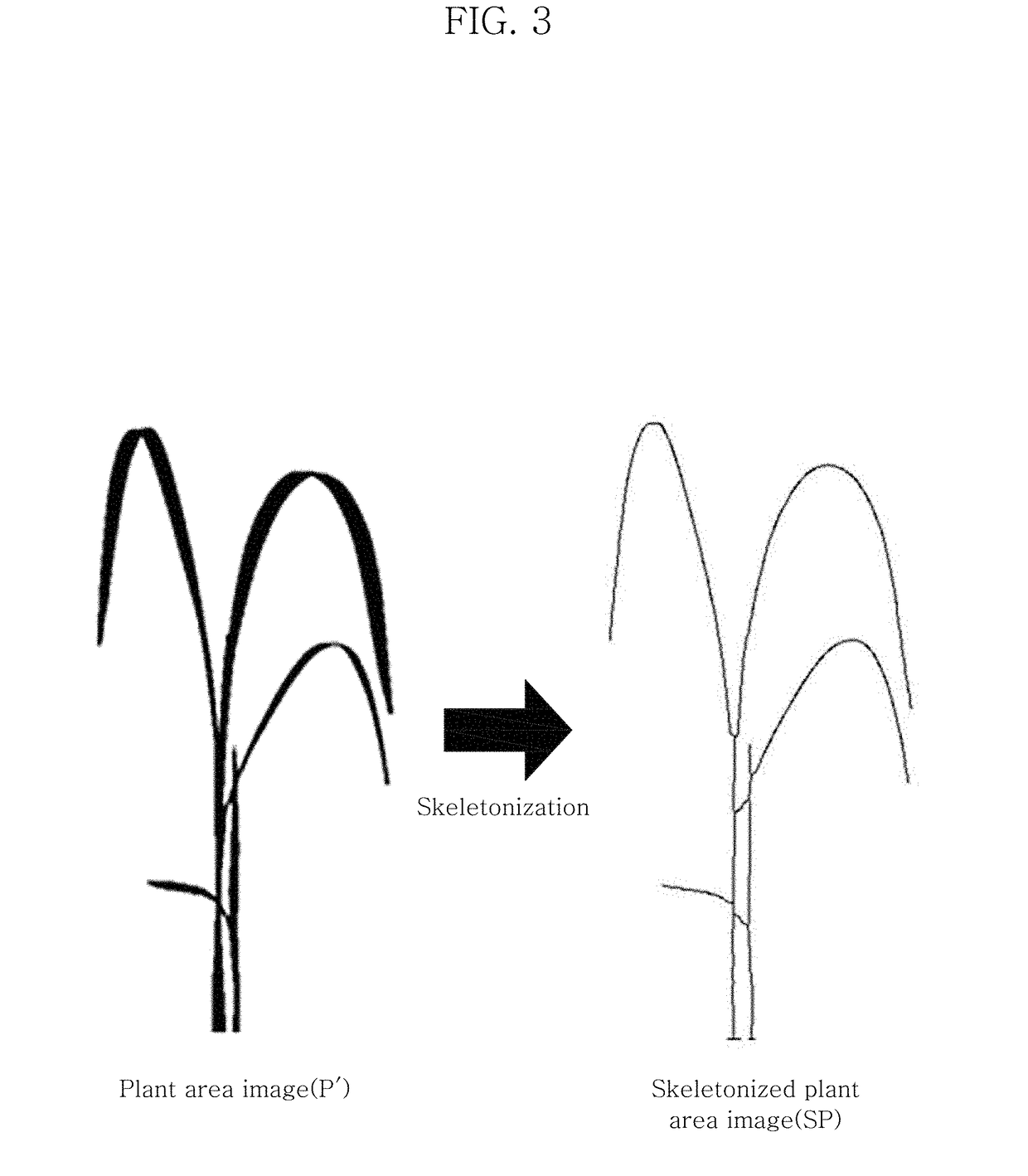
System and method for plant leaf identification
ActiveUS20190065890A1Accurate and easy reconstructionFaster and improved systemImage enhancementReconstruction from projectionImage extractionPath generation
A system for plant leaf identification includes: a plant image capturing unit which captures an image of a target plant to generate a plant image; a plant area image extraction unit which separates a background area and a plant area in the plant image to generate a plant area image including the plant area; a plant area image skeletonization unit which skeletonizes the plant area image to generate a skeletonized plant area image; a candidate leaf path generation unit which identifies a root vertex, a junction vertex and a leaf tip vertex in the skeletonized plant area image, and generates a plurality of candidate leaf paths by calculating all possible paths from the root vertex to the leaf tip vertex; and a final leaf path reconstruction unit which reconstructs a final leaf path matching the plant image by selecting the plurality of candidate leaf paths.
Owner:KOREA INST OF SCI & TECH
Method for reconstructing roundabout path during interruption of wide-area protection communication under heavy load
ActiveCN105847440AProtection start failure signalReal-time transmissionTransmissionWide areaHeavy load
The invention relates to a method for reconstructing a roundabout path during interruption of wide-area protection communication under a heavy load. The method takes a wide-area protection communication network under the heavy load as an object, and constructs an appropriate shunt roundabout communication path quickly based on the left undamaged network when a wide-area protection communication optical fiber is interrupted so as to ensure that a wide-area protection communication service is carried out normally. A single light-load channel roundabout path reconstruction algorithm is designed for a GOOSE message with the highest delay requirement and importance degree by taking satisfaction for requirements of wide-area protection for information as a foundation and taking network load balance after heavy-load communication roundabout as an objective. The algorithm comprehensively considers factors such as the bandwidth, the distance, the channel utilization rate and the like which affect the channel delay, reconstructs a channel weight index, and optimizes a roundabout path with the shortest delay by the aid of a Dijkstra optimization algorithm.
Owner:CHINA THREE GORGES UNIV
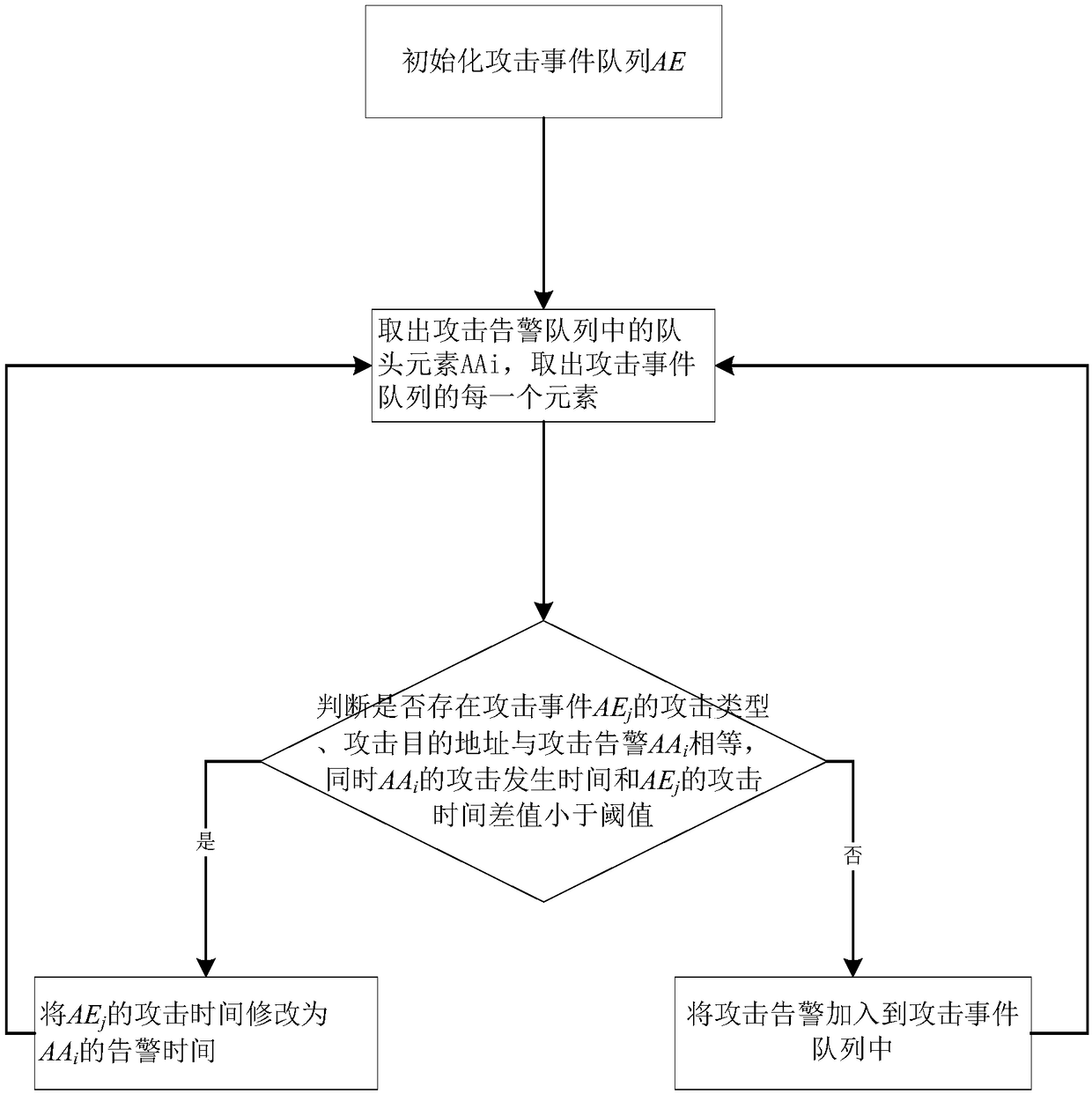
An attack path reconstruction method based on similarity computation
InactiveCN109308409AAccurately detect attacksPlatform integrity maintainanceFile system typesSimilarity computationPath reconstruction
The invention discloses an attack path reconstruction method based on similarity calculation, the invention forms an attack event by integrating multiple attacks in an attack event, Then by forming amultiple attack steps into an attack path, the originally complex network attack process is clarified and organized effectively, which helps to accurately detect the attack behavior, track the attacksource and find the weak links of the network system.
Owner:STATE GRID HUNAN ELECTRIC POWER +2
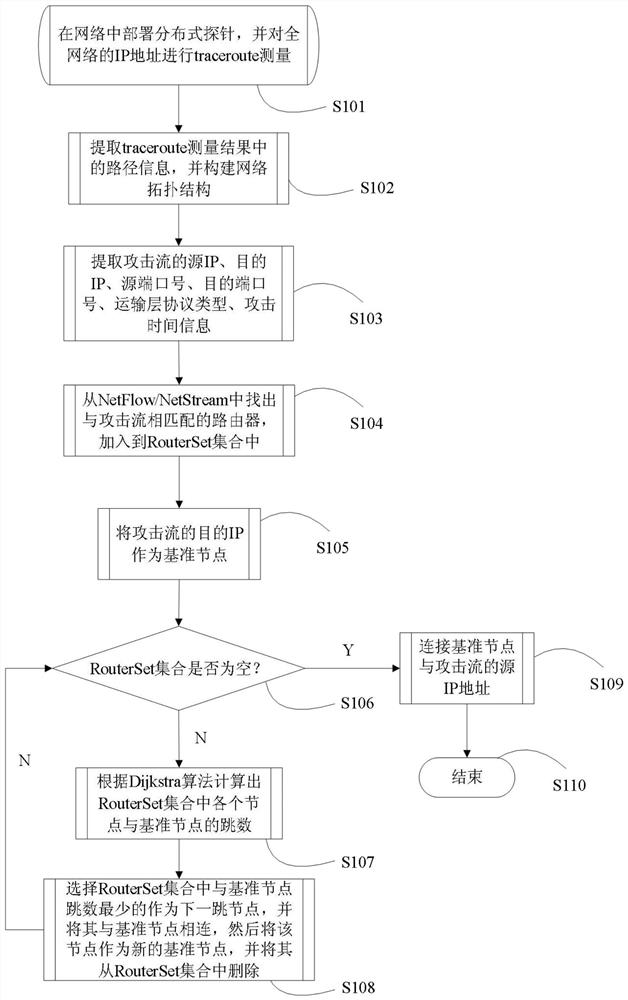
Network attack path reconstruction method based on topological information
InactiveCN113132377AAccurate and complete drawingGuaranteed correctnessData switching networksPathPingTraceroute
The invention relates to the technical field of network space security, in particular to a network attack path reconstruction method based on topological information, which comprises the following steps of: firstly, obtaining a network topological structure by utilizing topological measurement probes distributed in each area of a network through a traceroute technology, then extracting router information through which an attack flow passes through through a NetFlow / NetStream technology, and finally reconstructing a network attack path according to the extracted router information, and then, according to the extracted routers and related network topology data, adopting a Dijkstra shortest path selection algorithm to gradually reconstruct an attack path of the whole attack flow. According to the method, active and passive network measurement methods are comprehensively utilized, the path information of the network attack can be accurately and completely drawn, and the correctness of a reconstruction structure is ensured.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
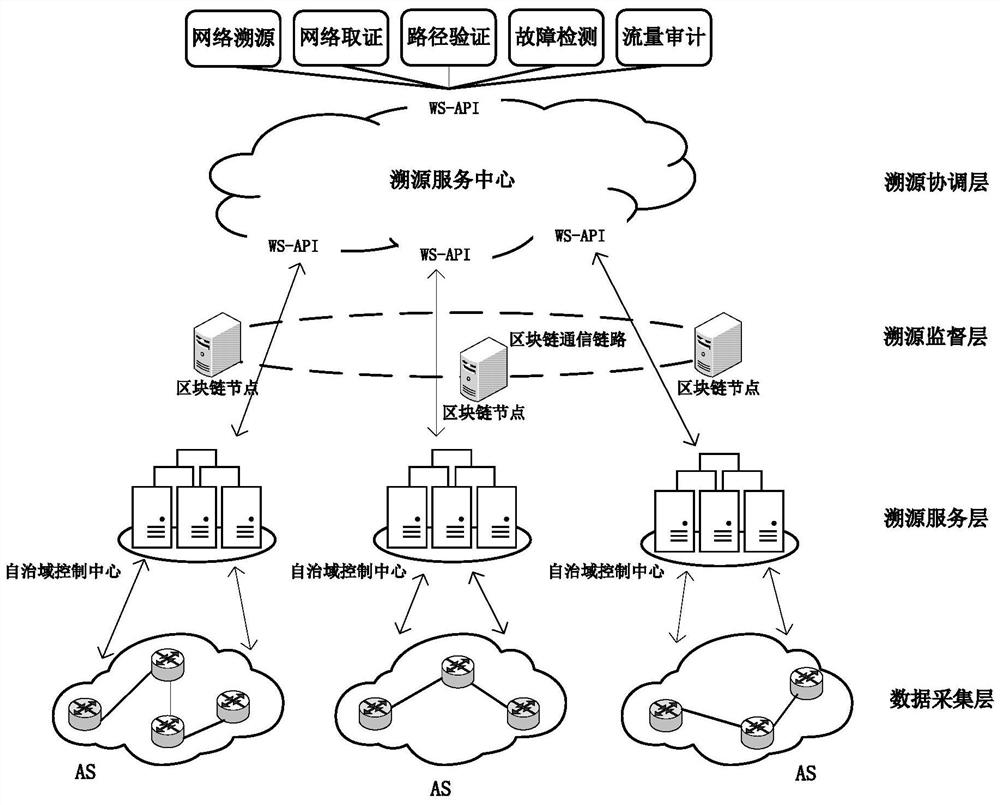
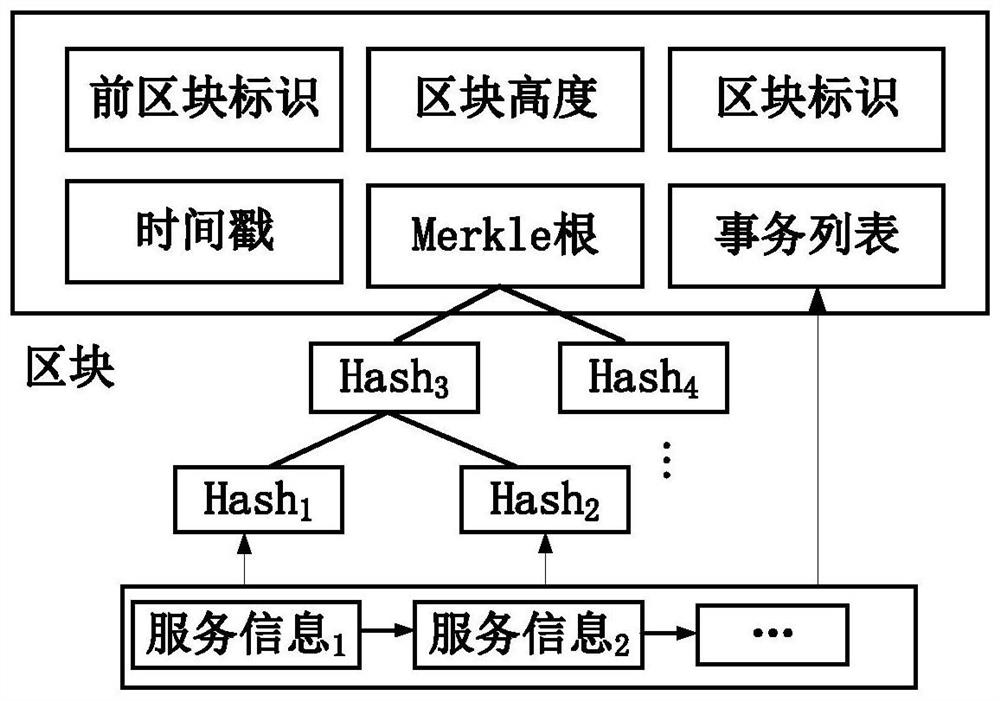
Universal IP traceability system and method based on block chain
PendingCN114079567AFacilitate large-scale deploymentPrivacy protectionUser identity/authority verificationDatabase distribution/replicationData packPathPing
The invention belongs to the field of network security, and particularly relates to a universal IP traceability system and method based on a block chain. The system is divided into a data acquisition layer, a traceability service layer, a traceability supervision layer and a traceability coordination layer, and a credible service-oriented universal IP traceability system is provided by referring to a business mode of immediate collection and immediate payment in a block chain so as to promote large-scale deployment of the traceability system; the traceability supervision layer comprises a data module, a consensus module and a verification module; the data module simplifies block data, the consensus module improves the working efficiency and performance of the block chain and reduces the deployment cost, and the verification module prevents malicious nodes from tampering transaction information and ensures the data integrity. The traceability method comprises a traceability trace establishment stage and an attack path reconstruction stage. A concurrent backtracking mechanism is adopted, so that the traceability efficiency is improved; the system is also suitable for a traceability method based on a data packet, is compatible with most of current IP traceability methods, and has universality.
Owner:东北大学秦皇岛分校
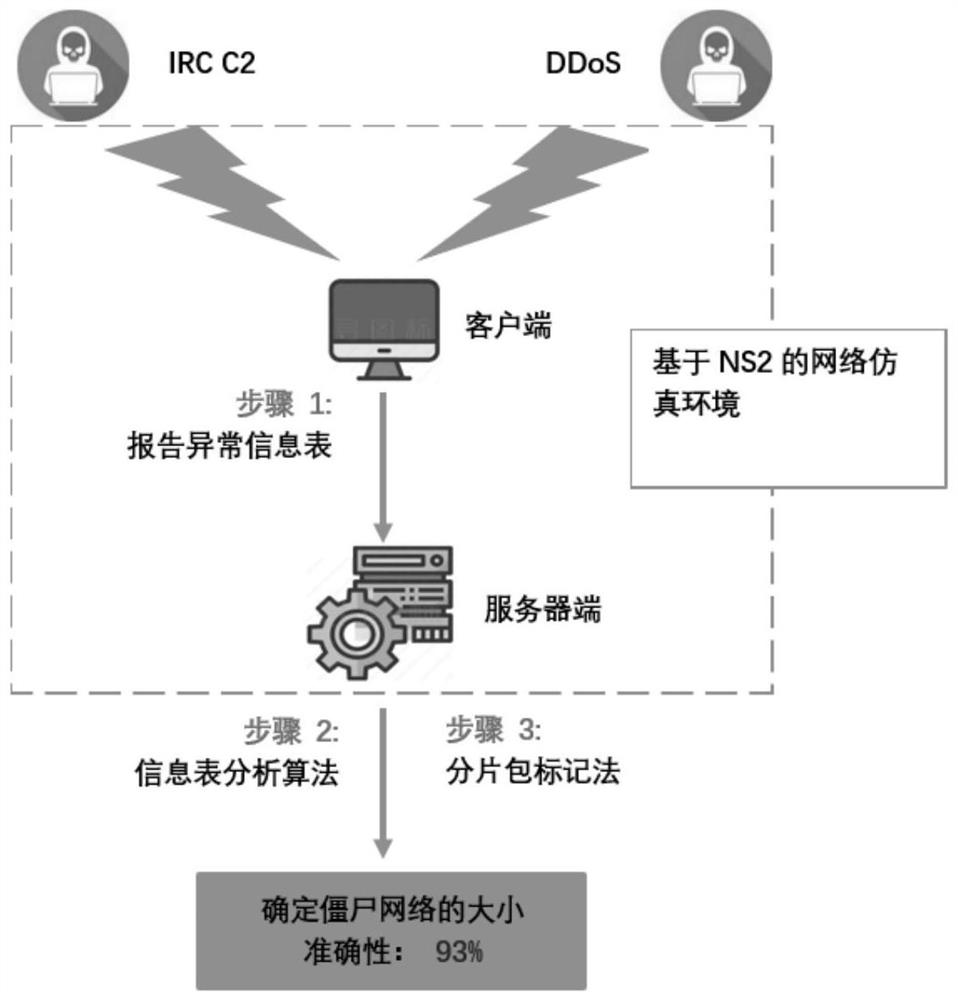
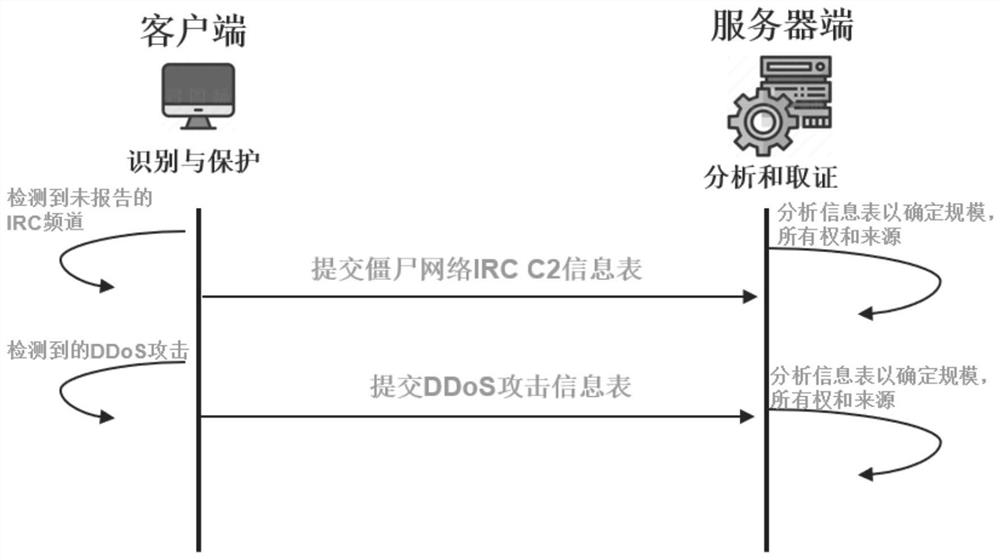
Evidence obtaining method and system for DDoS attack
The invention discloses an evidence obtaining method and system for a DDOS attack. The method comprises the following steps: reporting an abnormal information table; analyzing the information table; and representing a FMS data packet. The system comprises an NS2 simulation module, an anomaly reporting module, an analysis algorithm module and a fragment packet marking method module. According to the system, the network environment and the network nodes are simulated by using the NS2, so that not only can the real network environment be simulated, but also network paralysis caused by actual attacks can be prevented. All analysis algorithms can be realized in NS2 simply and efficiently without complex tools. According to the method, a botnet and DDoS attack electronic evidence analysis methodis used, fragment data packet marks are used when a server analyzes the electronic evidences so as to track the source and path reconstruction of a router, and therefore the scale recognition rate isincreased to 93%.
Owner:NANJING UNIV
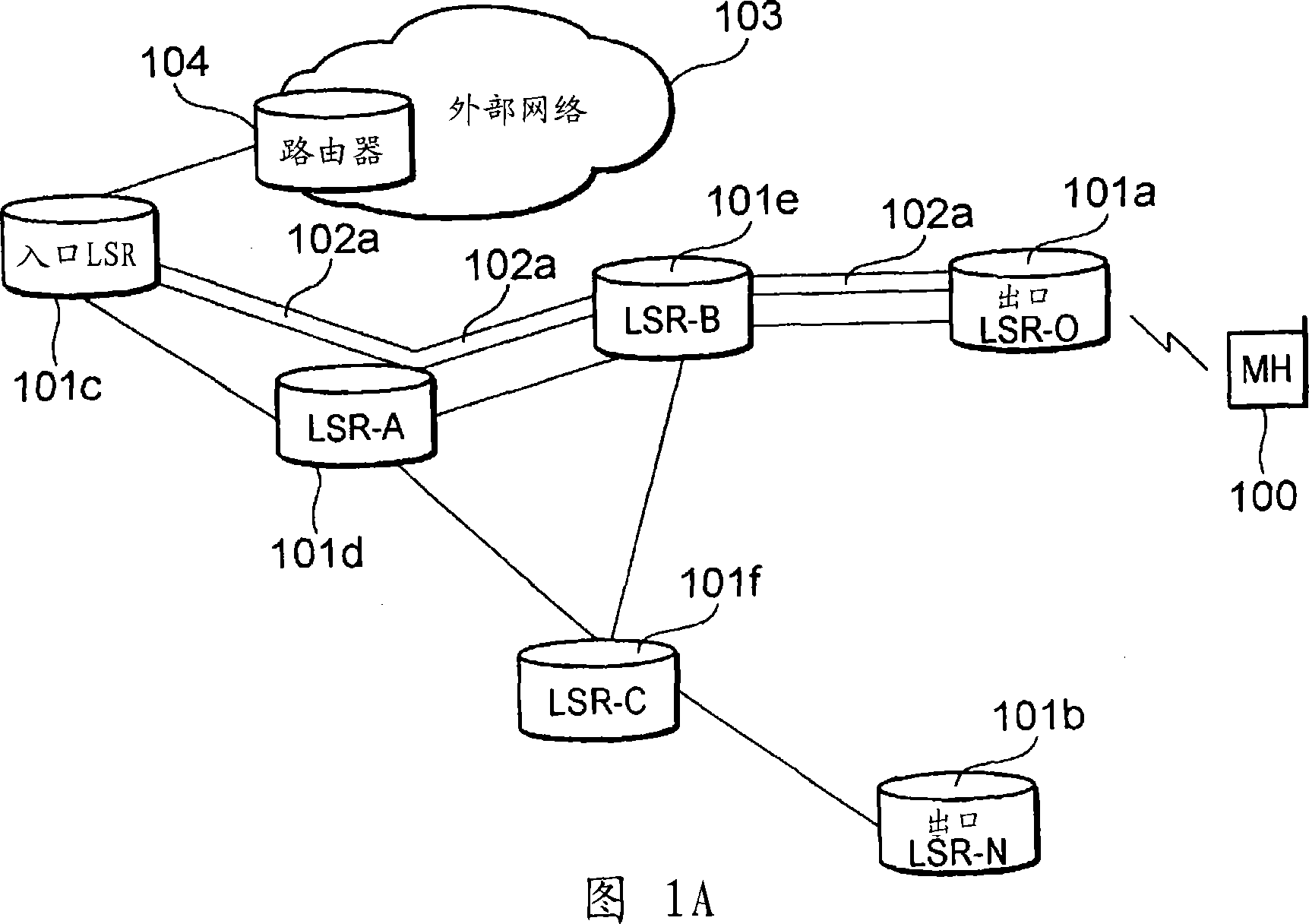
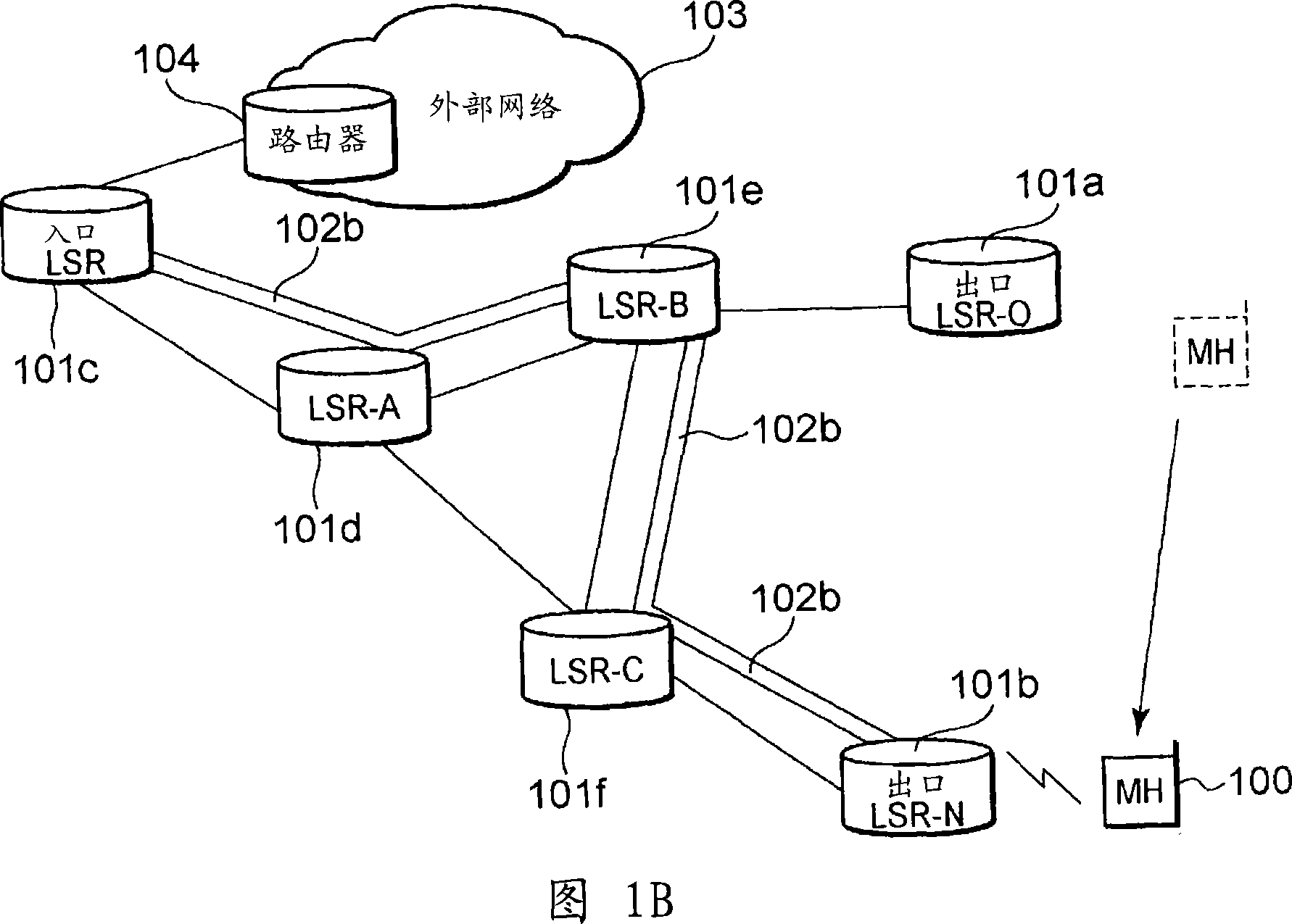
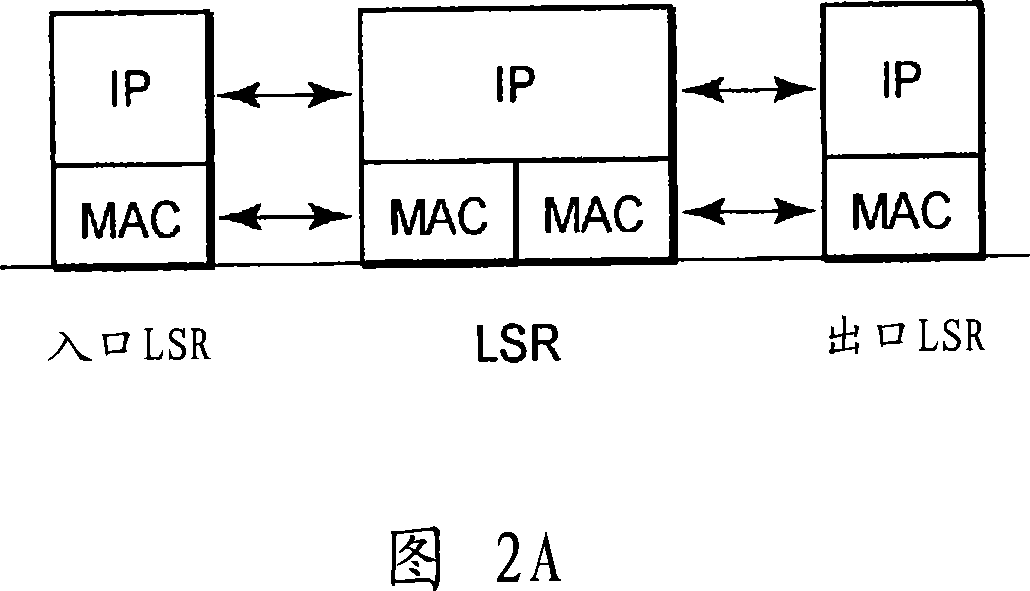
Mobile communication access system, packet transfer device, and path re-establishing method
InactiveCN1993939AAvoid consumptionIncrease the lengthData switching networksWireless communicationPathPingFast handover
Disclosed is a technique for providing a mobile communication access system, etc., that can eliminate the useless consumption of resources due to route redundancy, reduce the load on the processing, such as the setup of an LSP, performed by an ingress LSR, avoid an increase in the length of a signal route for setting up an LSP, suppress a delay in providing a notification of a change for an egress LSR to which a mobile terminal is to be connected, and perform a rapid handover process. According to this technique, based on identification information for a second edge device 101b that is received from a mobile terminal 100, a first edge device 101a determines whether an output interface that has been decided on for the second edge device is the same as an input interface for a path that has been established for the mobile terminal, and when the interfaces are the same, transmits a path request message to the other packet transfer device. This packet transfer device determines whether the output interface that has been decided on for the second edge device is the same as the input interface for the path that has been established for a mobile terminal, and when the interfaces are not the same, transmits the path message to the output interface and re-establishes the path in accordance with a reserve message.
Owner:PANASONIC CORP
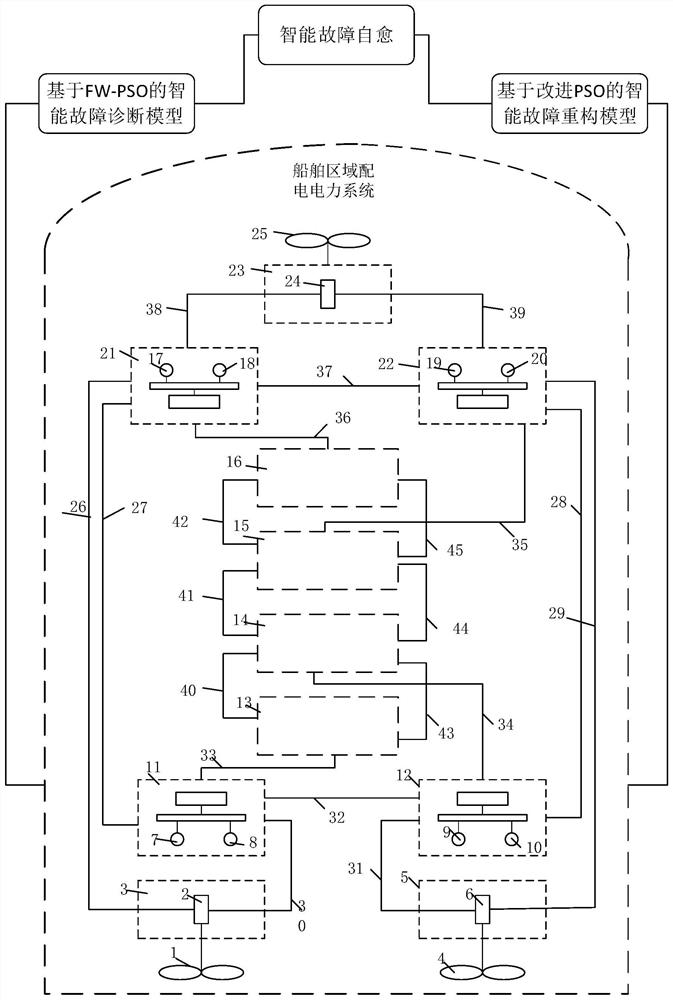
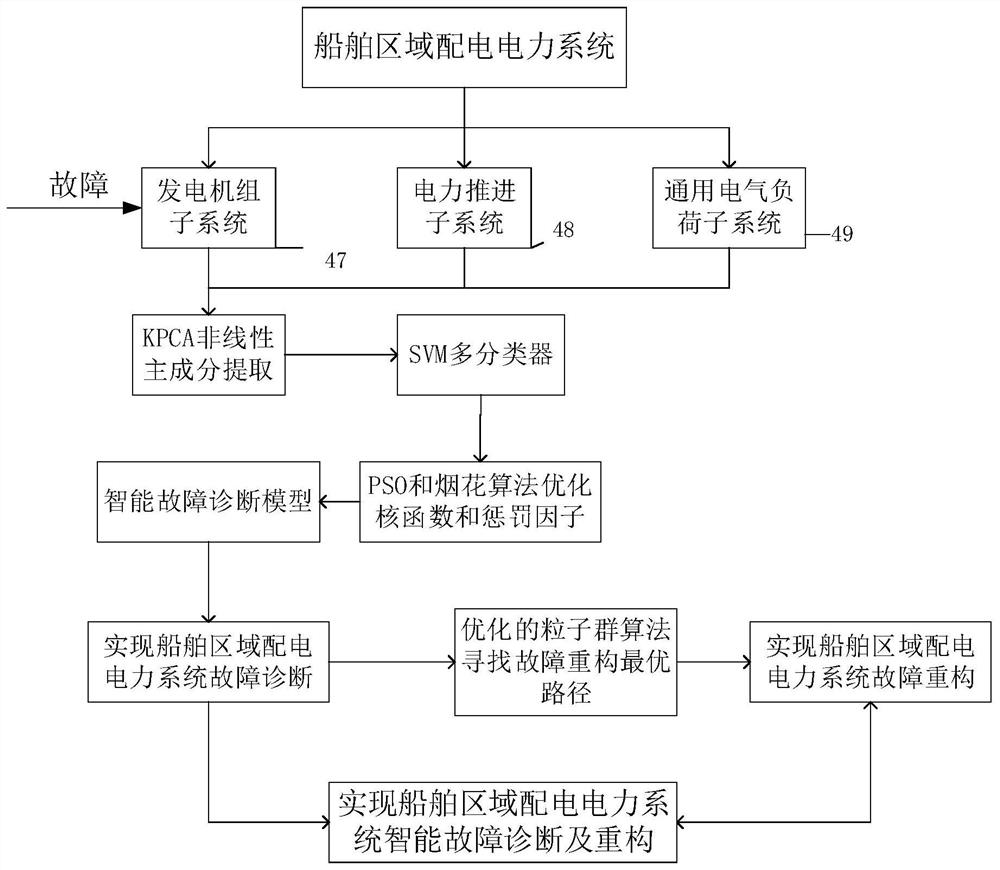
Intelligent fault diagnosis and reconstruction method for ship area distribution power system
InactiveCN112733962AImplement failure reconstructionImprove power supply reliabilityCharacter and pattern recognitionArtificial lifeAlgorithmReconstruction method
The invention discloses a ship area distribution power system intelligent fault diagnosis method based on an FWASSO algorithm and a ship area distribution power system intelligent fault reconstruction method based on an optimization particle swarm algorithm. According to the method, a ship area distribution power system is taken as a control object, and diagnosis problems during main switch faults and circuit breaker faults are researched. The method comprises the following steps: according to data fed back by a system sensor, firstly, carrying out preliminary processing on the data through a fuzzy neural network adaptive Kalman filtering method, and removing interference parts such as noise; and optimizing a kernel function and a penalty factor in kernel principal part analysis through a firework algorithm and a particle swarm algorithm to obtain a diagnosis model for improving the model training speed and the classification accuracy, thereby improving the diagnosis speed and reliability. And finally, an optimal path reconstruction model is constructed by using the improved particle swarm algorithm, so that the speed and precision of fault reconstruction are improved.
Owner:SHANGHAI MARITIME UNIVERSITY
A method for reconfiguring data packet paths in software-defined networks
ActiveCN108199970BLighten the computational burdenPrecise transmission pathData switching networksPathPingData pack
The invention discloses a data packet path reconfiguration method in a software-defined network. In the network initialization phase, the controller assigns an ID to each switch / router according to the network scale. When the sender generates a data packet, the relevant data flow information is sent to the controller, and the controller decides the path reconstruction method to be used and the field allocation of the newly added data packet header, and feeds back the information to the sender. When the switch / router forwards the data packet, it performs corresponding operations according to the newly added packet header, and records path-related information in the packet. Finally, the management server in the network reconstructs the transmission path of the data packet according to the path-related information in the received data packet. The present invention has no special requirements on the types of software-defined network topology, has the characteristics of low calculation overhead of switches / routers, and can accurately reconstruct the transmission path of data packets under the condition of network failure and congestion, which greatly facilitates the Defines the management and troubleshooting of the network.
Owner:ZHEJIANG UNIV
A data flow traceability method based on sdn
The present invention provides an SDN-based data flow tracing method. The method comprises a first step of sampling a designated field regularly by an SDN switch, so as to obtain data package information Flow_ID and switch information, wherein the switch information comprises a switch identifier Switch_ID and a data package input port; a second step of dividing the data package information Flow_ID and switch information into groups with Flow_ID as a Key, so as to obtain a data set SA of each group, wherein i represents data sets of different groups; a third step of performing path analysis on the data set SA of each group according to a network topological structure G of the SDN; and a fourth step of determining a path start point according to a path analysis result, and performing path reconstruction, so as to obtain a path of a data package or a data flow. In the method, the path of the data package or the data flow is reconstructed, so that a source of an attack source can be traced.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
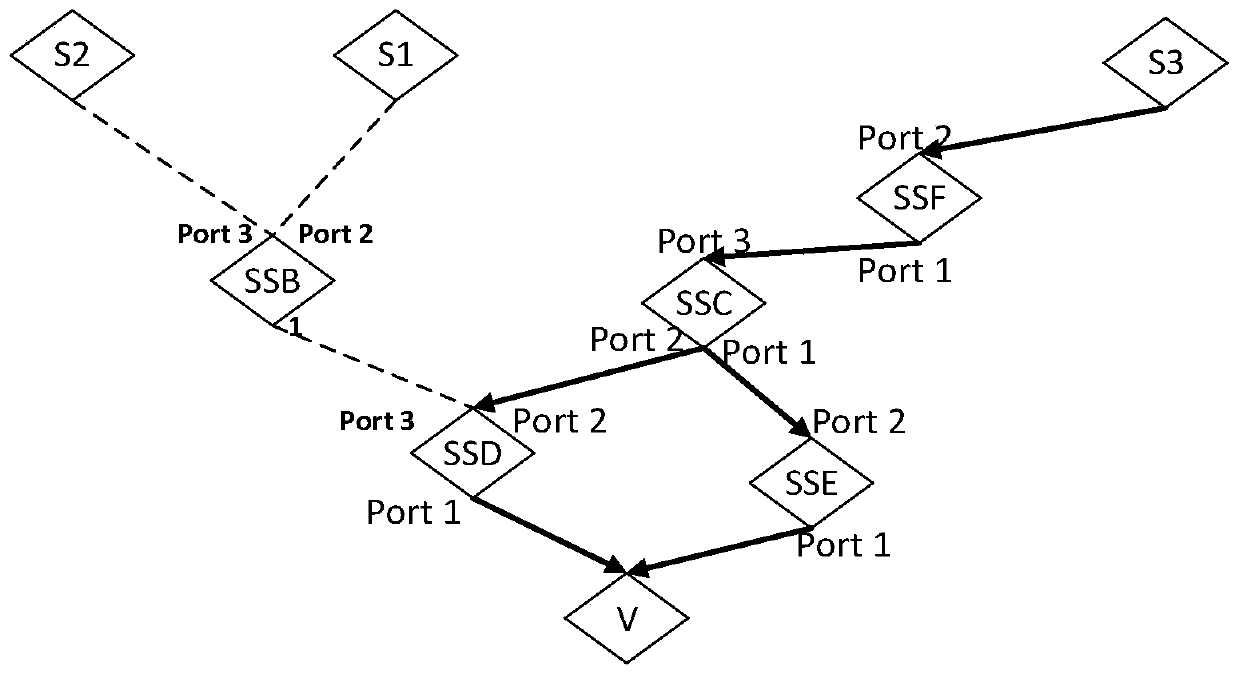
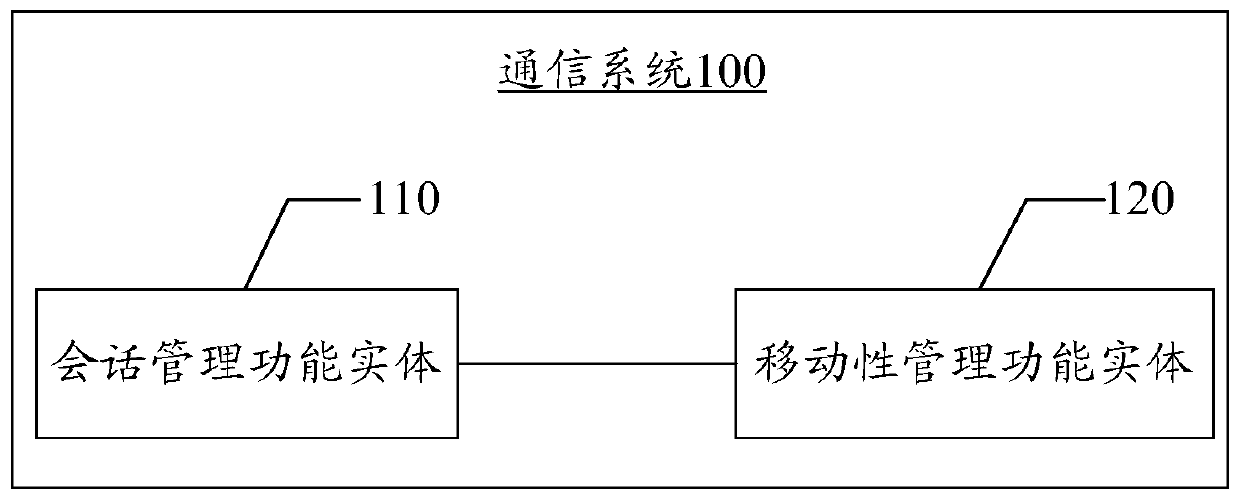
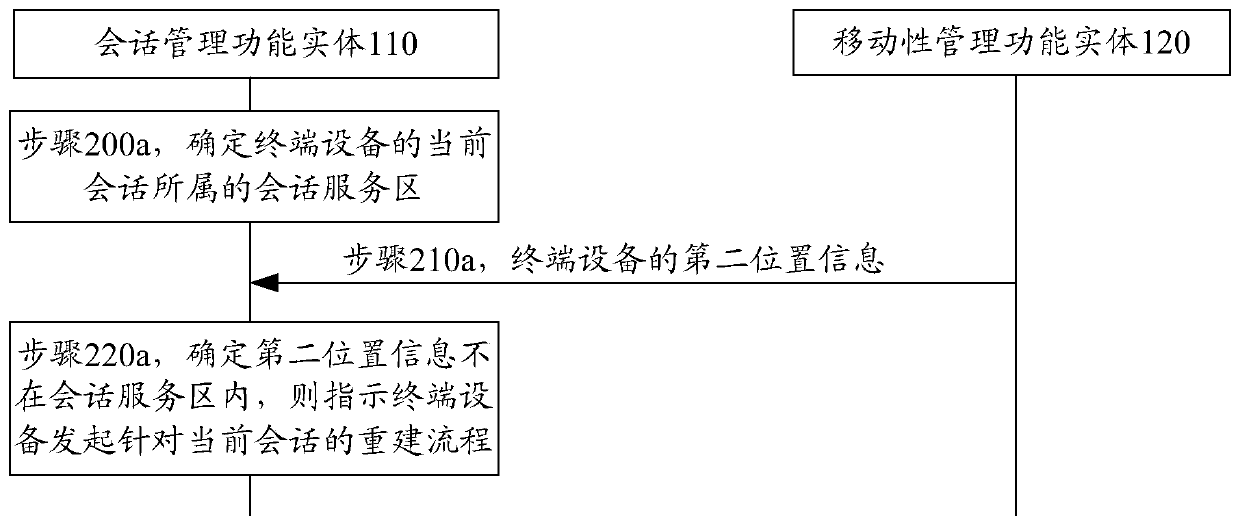
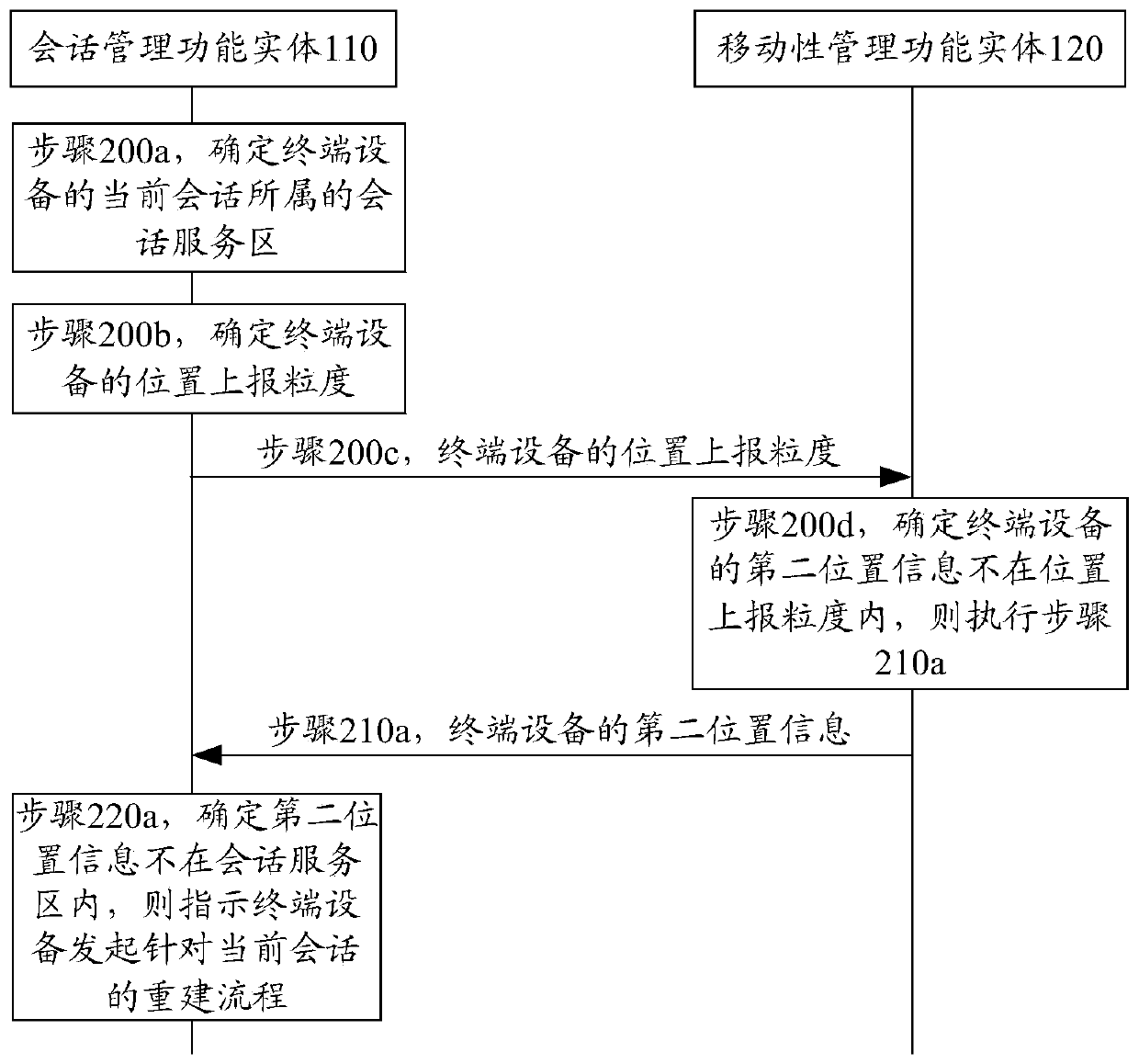
A method, device and communication system for initiating user plane path reconstruction
ActiveCN108696822BConnection managementWireless network protocolsSession managementCommunications system
Owner:HUAWEI TECH CO LTD
Communication system and communication method
InactiveCN104205943BReduce usageEfficient constructionNetwork topologiesTransmissionCommunication unitCommunications system
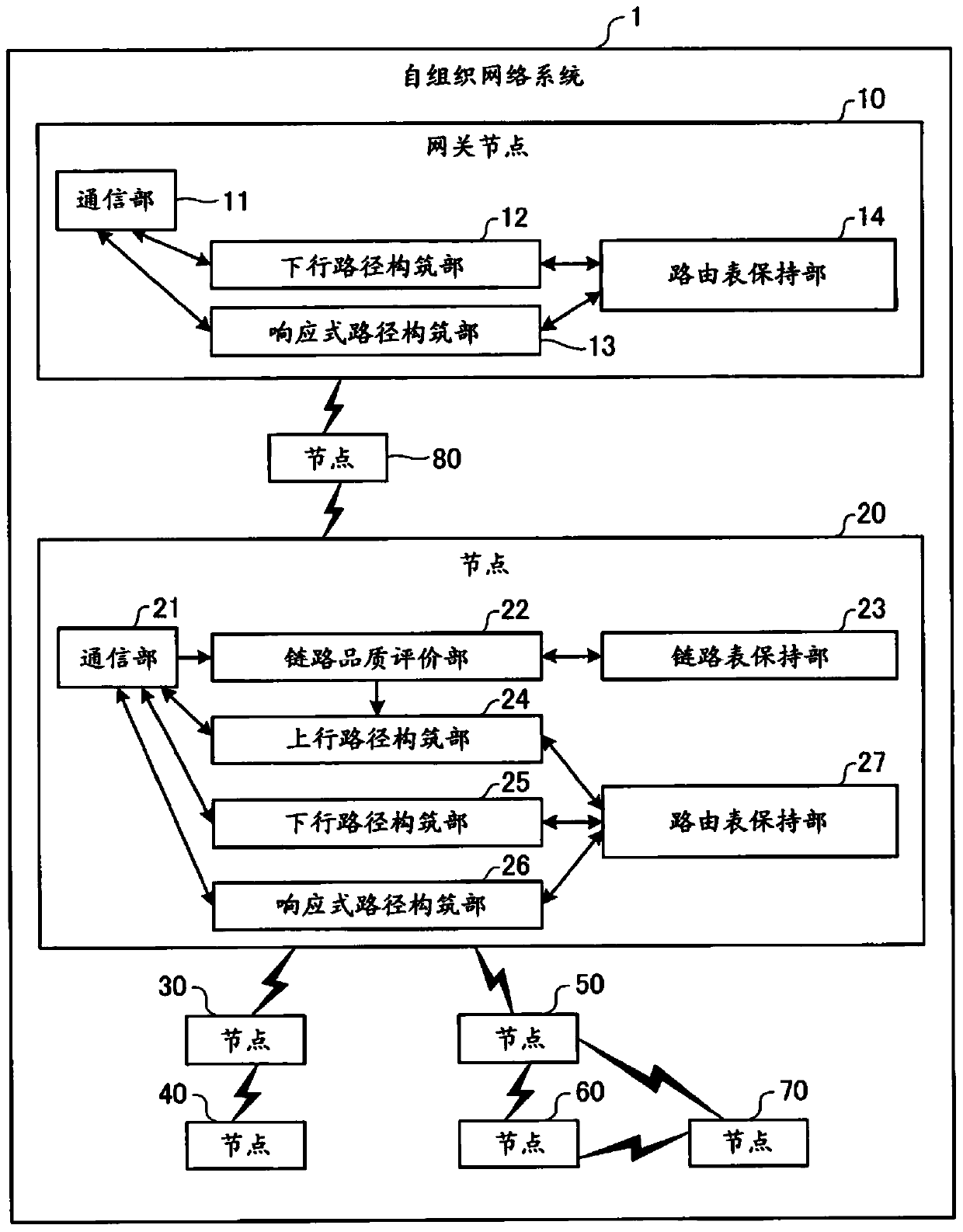
An ad hoc network system (1) has a gateway node (10), and a plurality of nodes (20) to (80) that perform ad hoc wireless communication with the gateway node (10) and have fixed installation positions. A node (20) has a link quality evaluation unit (22), an uplink path construction unit (24), a communication unit (21), and a downlink path construction unit (25). A link quality evaluation unit (22) performs a route evaluation based on the hello frame based on only the reception result record of the hello frame for network formation, and the route evaluation is used for uplink communication to the gateway node (10). An uplink path construction unit (24) constructs an uplink path based on the above-mentioned path evaluation. The communication unit (21) performs uplink communication to the gateway node (10) regularly and at a predetermined frequency. A downlink path construction unit (25) constructs a downlink path from the gateway node (10) based on an uplink communication path to the gateway node (10).
Owner:FUJITSU LTD
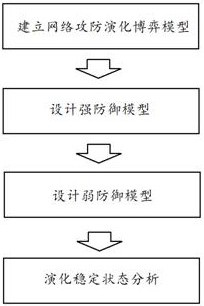
Attack and defense evolution method of uploading channel under DoS attack in microgrid secondary control
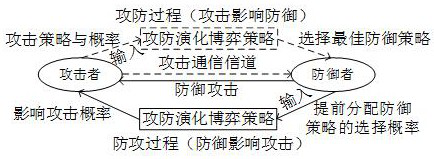
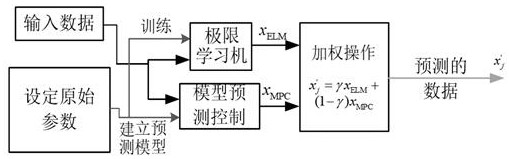
ActiveCN112422552AAvoid cost wasteJamming attack probabilityTransmissionInformation technology support systemLearning machineInformation layer
The invention discloses an attack and defense evolution method of an uploading channel under DoS attack in microgrid secondary control. The method comprises the following steps: S1, establishing a network attack and defense evolution game model; S2, designing a strong defense model by adopting a prediction mechanism combining an extreme learning machine and model prediction control; S3, designinga weak defense model, and designing related control parameters; and S4, respectively constructing a replication dynamic equation of the defense party and a replication dynamic equation of the attack party, carrying out simultaneous solution on equations, and carrying out evolution stability state analysis according to results. The method gives full play to the function of an information layer, proposes a passive defense strategy of adjacent prediction and path reconstruction, gives out a design method of related parameters, and can efficiently and reasonably cope with the DoS attack problem.
Owner:NANJING UNIV OF POSTS & TELECOMM
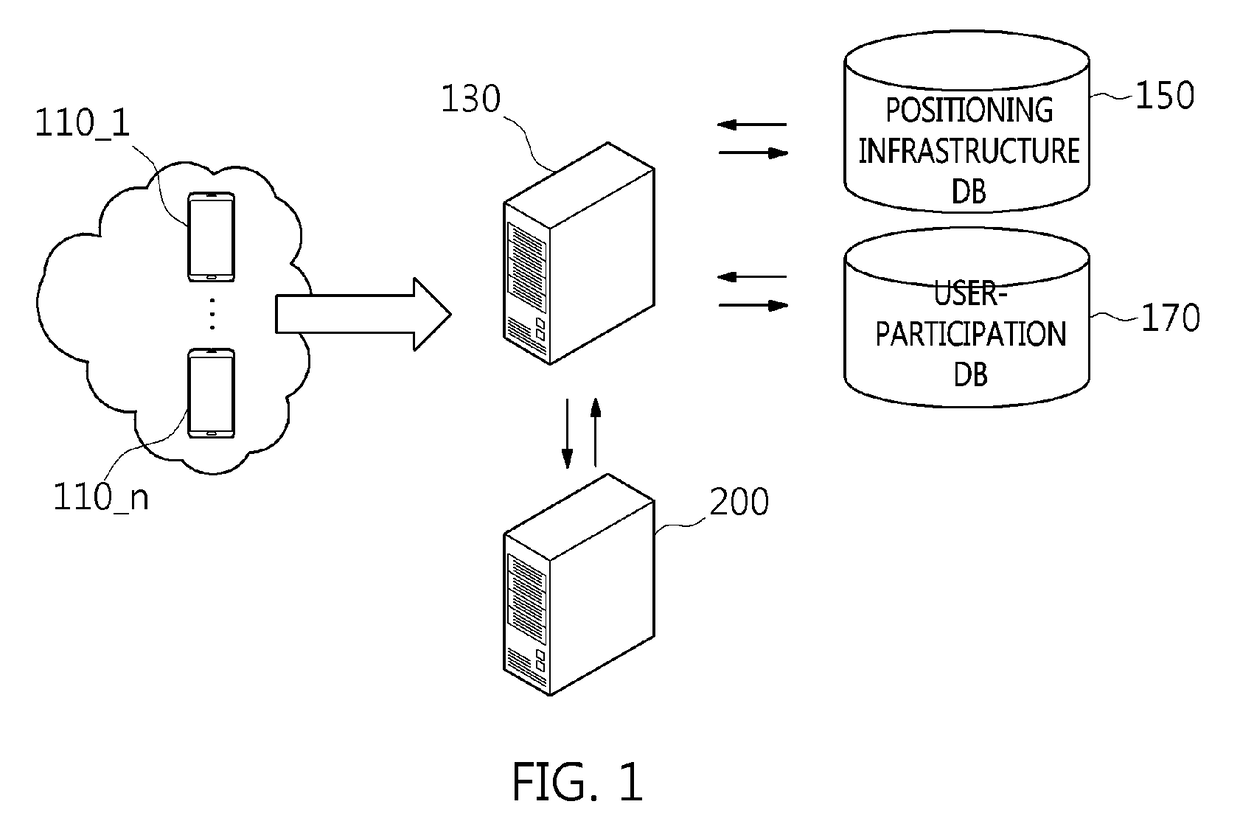
User-participation data sorting apparatus and method for updating positioning infrastructure database
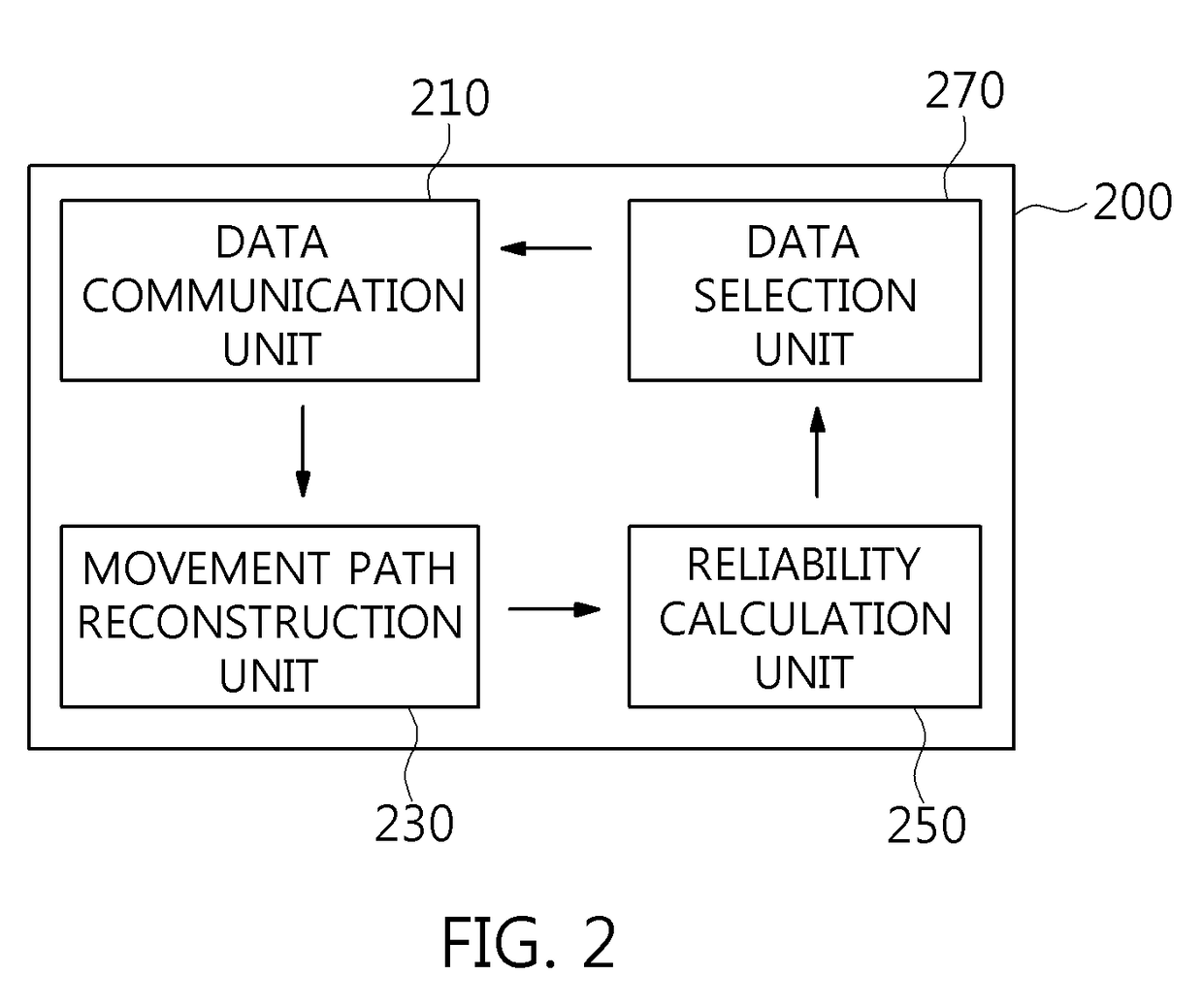
ActiveUS20180262881A1Particular environment based servicesGeographical information databasesCommunication unitData selection
Disclosed herein are a user-participation data selection apparatus and method for updating a positioning infrastructure DB. The user user-participation data selection apparatus includes a data communication unit for transmitting and receiving user-participation data, a movement path reconstruction unit for reconstructing an entire information movement path corresponding to the user-participation data using all information included in the user-participation data, a reliability calculation unit for calculating reliability corresponding to the entire information movement path, and a data selection unit for selecting update-use data for updating a positioning infrastructure DB based on the reliability.
Owner:ELECTRONICS & TELECOMM RES INST
Method and system for traceability of WSN data transmission path based on orthogonal identification
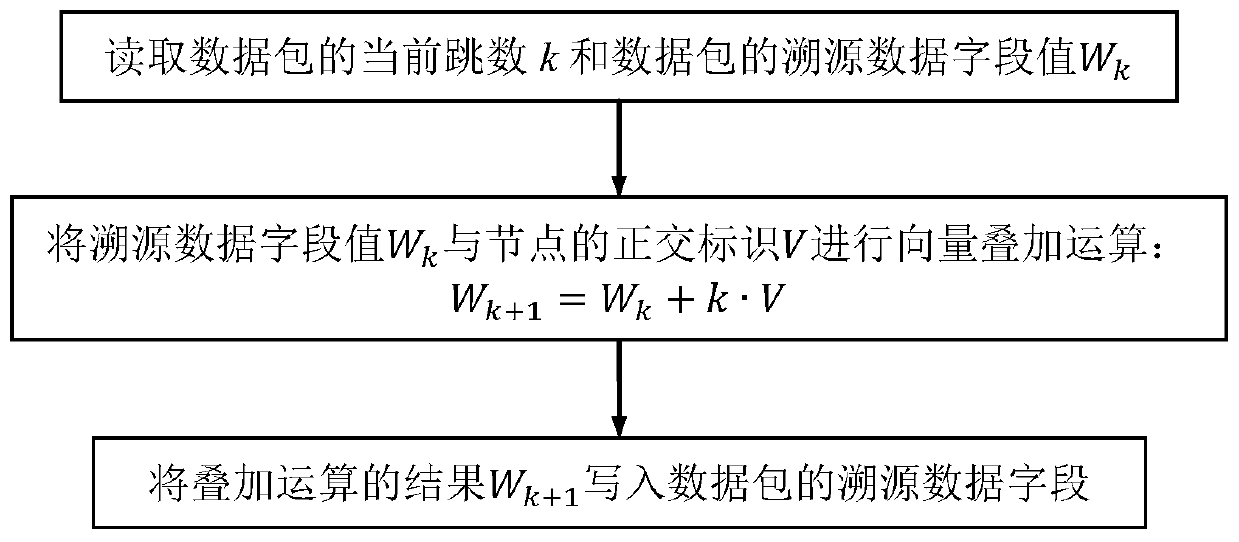
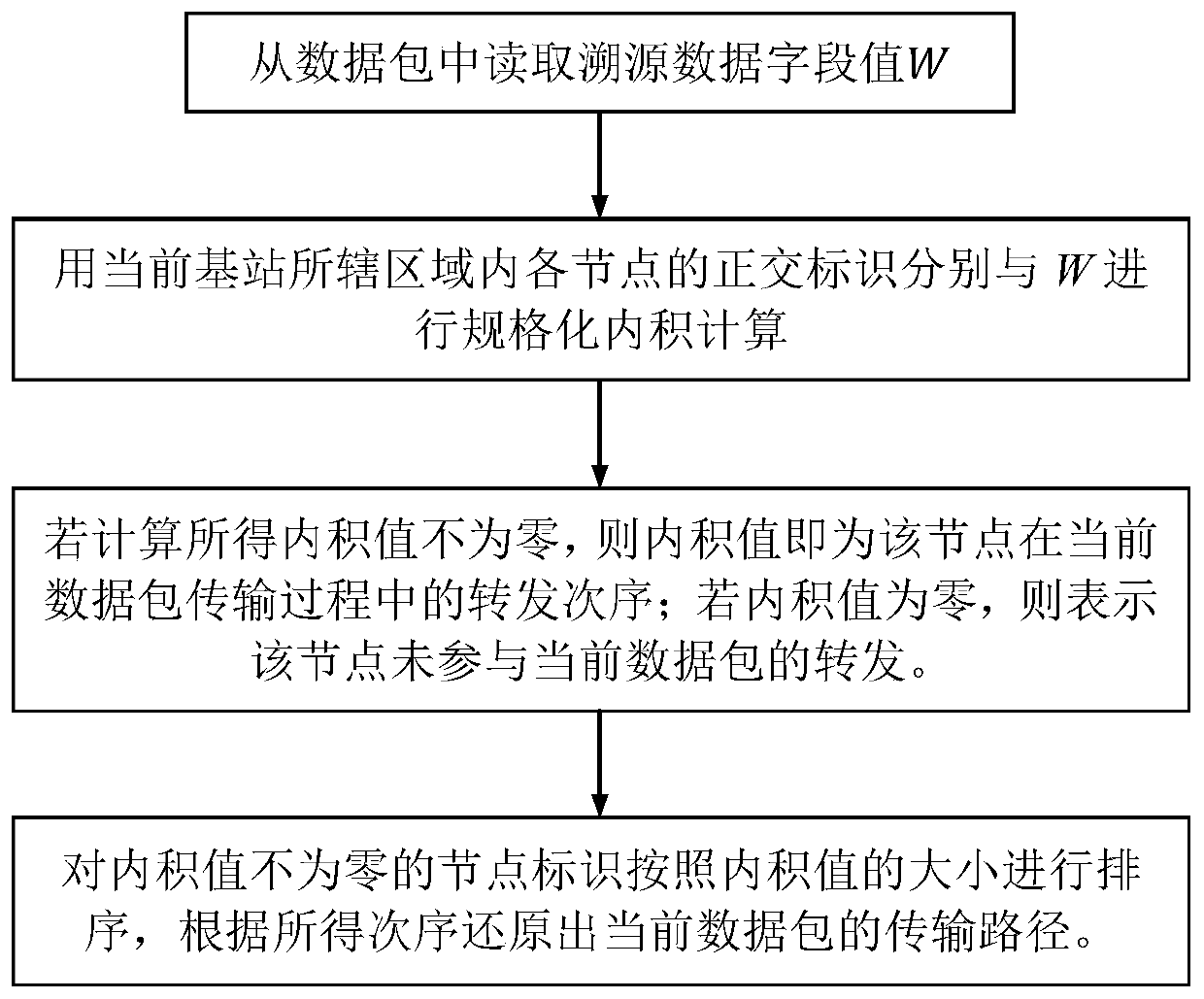
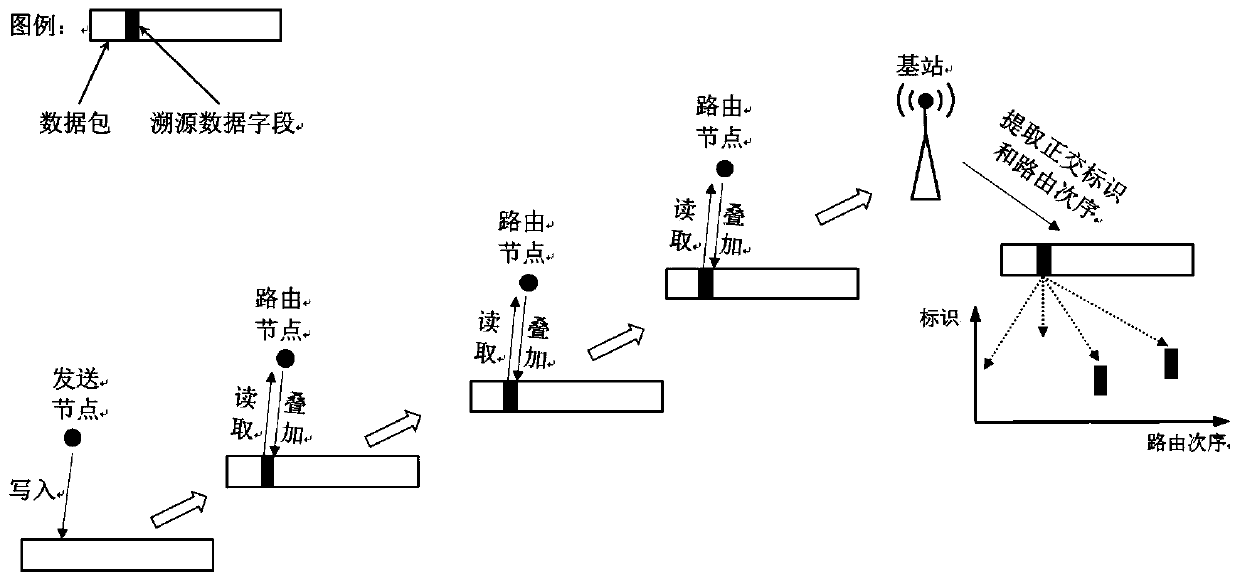
ActiveCN107105471BSolve problems that cannot be accurately restoredIngenious designNetwork topologiesData packMultiplexing
The invention discloses a WSN data transmission path traceability method and system based on orthogonal identification, which is divided into two stages of traceability information labeling and transmission path reconstruction: the stage of traceability information labeling includes: allocating all sensor nodes in the wireless sensor network Orthogonal identification, selection of a carrier protocol for carrying traceability information, and realization of superposition and multiplexing of traceability information in data packets by routing nodes; the transmission path reconstruction stage includes: reading traceability data fields of data packets, extracting and participating in forwarding The identification of the sensor node of the current data packet and its forwarding order, and restore the transmission path of the data packet according to the obtained order. The invention integrates the routing sequence information of the data packets in the wireless sensor network into the traceability information based on orthogonal superposition, and realizes the accurate traceability of the data transmission path of the wireless sensor network with limited space cost.
Owner:SHANDONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com