A data flow traceability method based on sdn
A data flow and data technology, applied in the field of computer networks, to achieve the effect of efficient attack traceability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to make the above-mentioned features and advantages of the present invention more comprehensible, the following specific embodiments are described in detail in conjunction with the accompanying drawings.
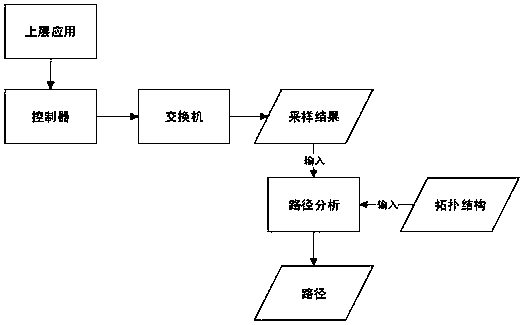
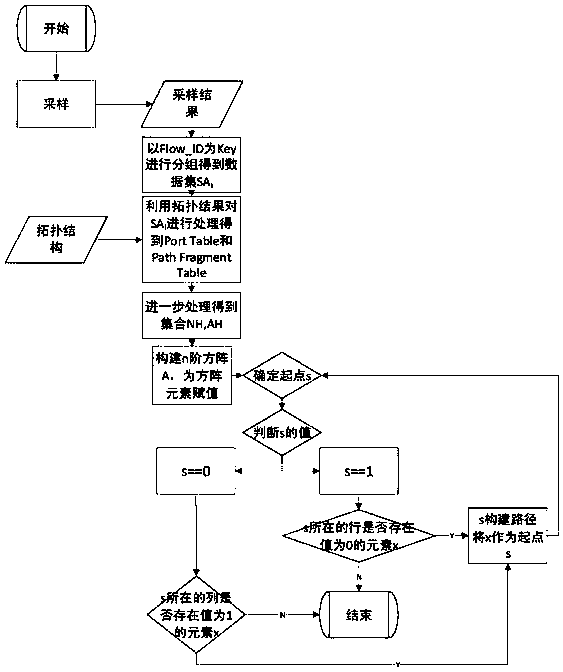
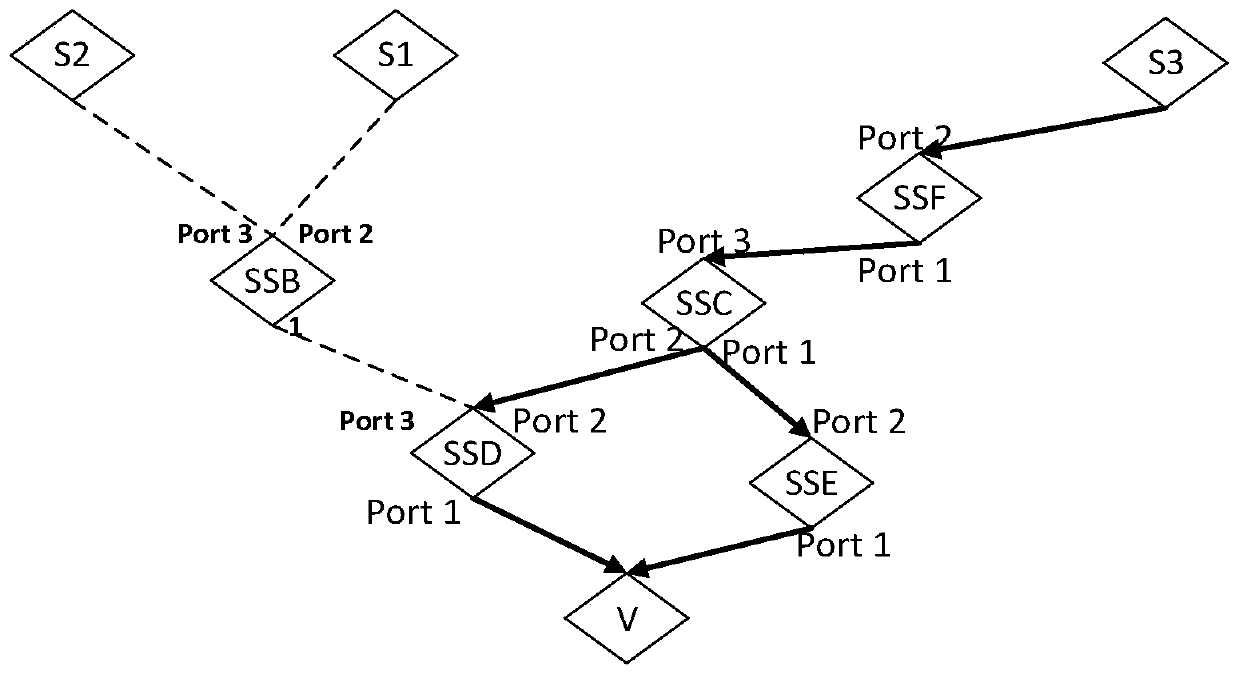
[0036] The present invention provides an SDN-based data flow traceability method, the operation flow chart of which is as follows figure 1As shown, firstly, the SDN switch periodically samples the specified fields, and the sampling results are input to the specified server and wait for processing. The regular sampling of the specified fields means that the controller receives the sampling rules sent by the upper application, and the SDN switch analyzes the sampling rules and performs regular sampling according to the analyzed field parameters that need to be sampled. The adoption rule refers to the displacement and length of certain fields in the data packet to be sampled; for example, field A has a starting position of 16 in the data packet and a length of 8...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com