Method of tracking DDoS attack in wireless sensor network
A wireless sensor and network technology, applied in the field of network security, can solve the problems of unusability and low efficiency, and achieve the effect of reducing false alarm rate, increasing burden and improving anti-interference ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037]The present invention will be further elaborated below in conjunction with specific examples.
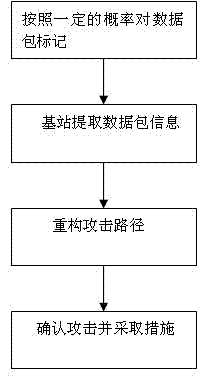
[0038] like figure 1 As shown, the steps of the tracking method include marking the data packets with a certain probability, extracting the data packet information through the base station, reconstructing the attack path, confirming the attack and taking measures.
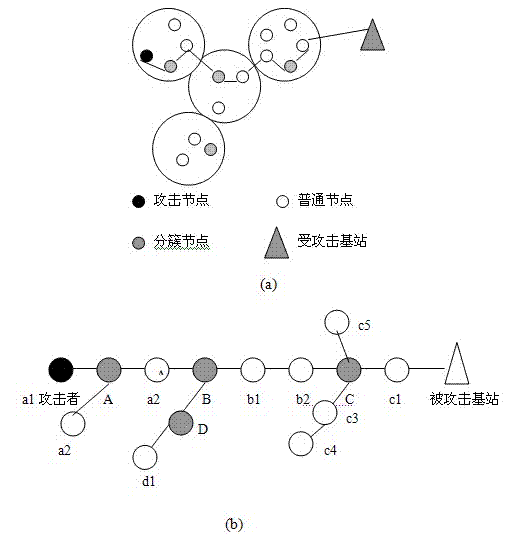
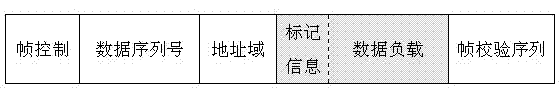
[0039] The tag information (first, top, tail, start, end, distance) of the packet contains six tag fields. The six label domains are divided into two layers. The first layer consists of (first, top, tail), which is mainly used to reconstruct the backbone part of the path. The second layer consists of (start, end, distance), which is used to reconstruct the local path from the common node start to the cluster head node top in the cluster.
[0040] The meanings of these six marked fields: the first field indicates the ID of the first cluster head node that the attack data packet passes through, and the first fiel...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com