Patents
Literature
119 results about "Source tracking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Source tracking pertains to the ability of some hypertext systems to rigorously track the exact source of every document or partial document included in the system; that is, they remember who entered the information, when it was entered, when it was updated and by whom, and so on. This allows determining the exact history of every document (and even small parts of documents).
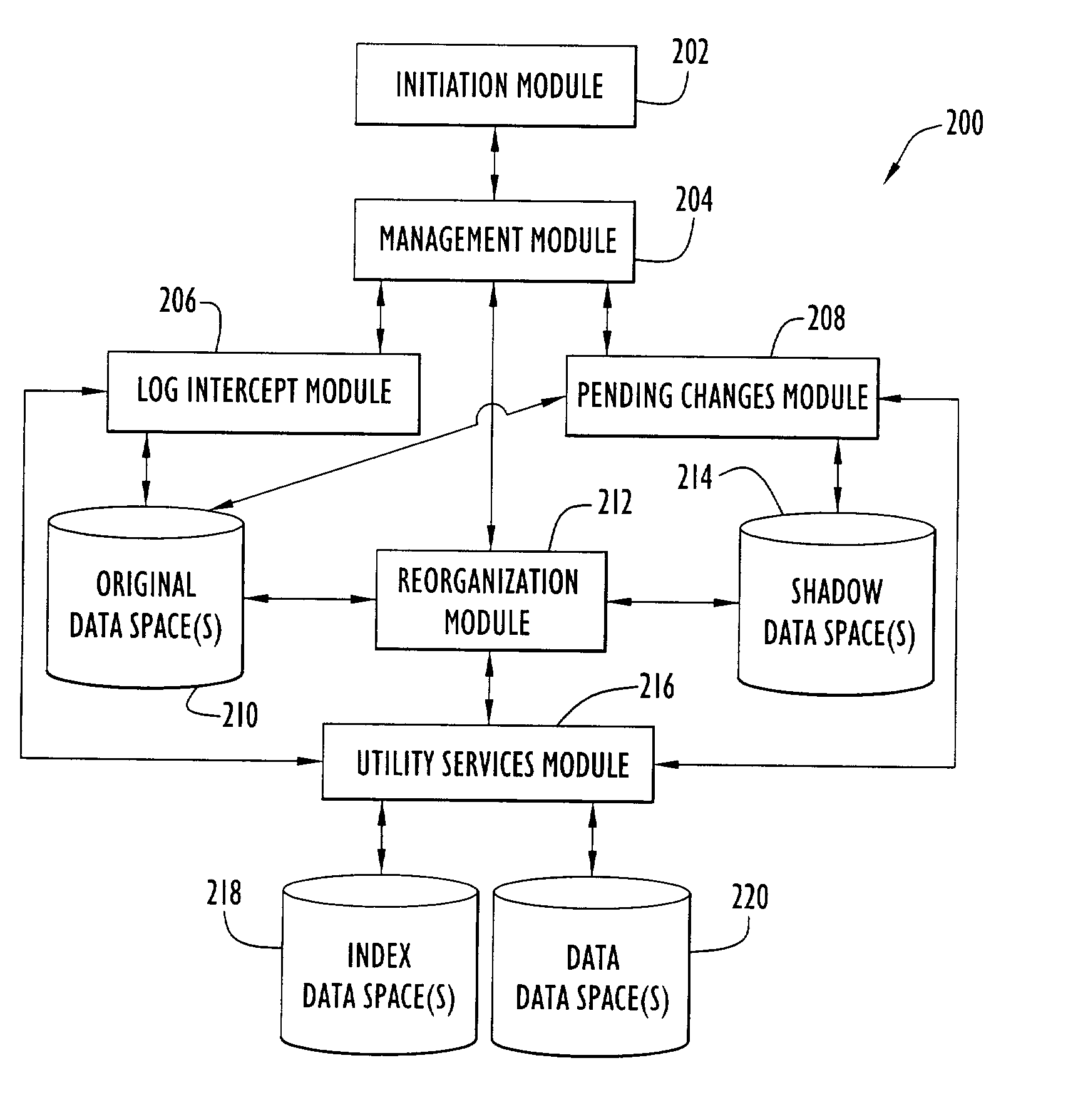
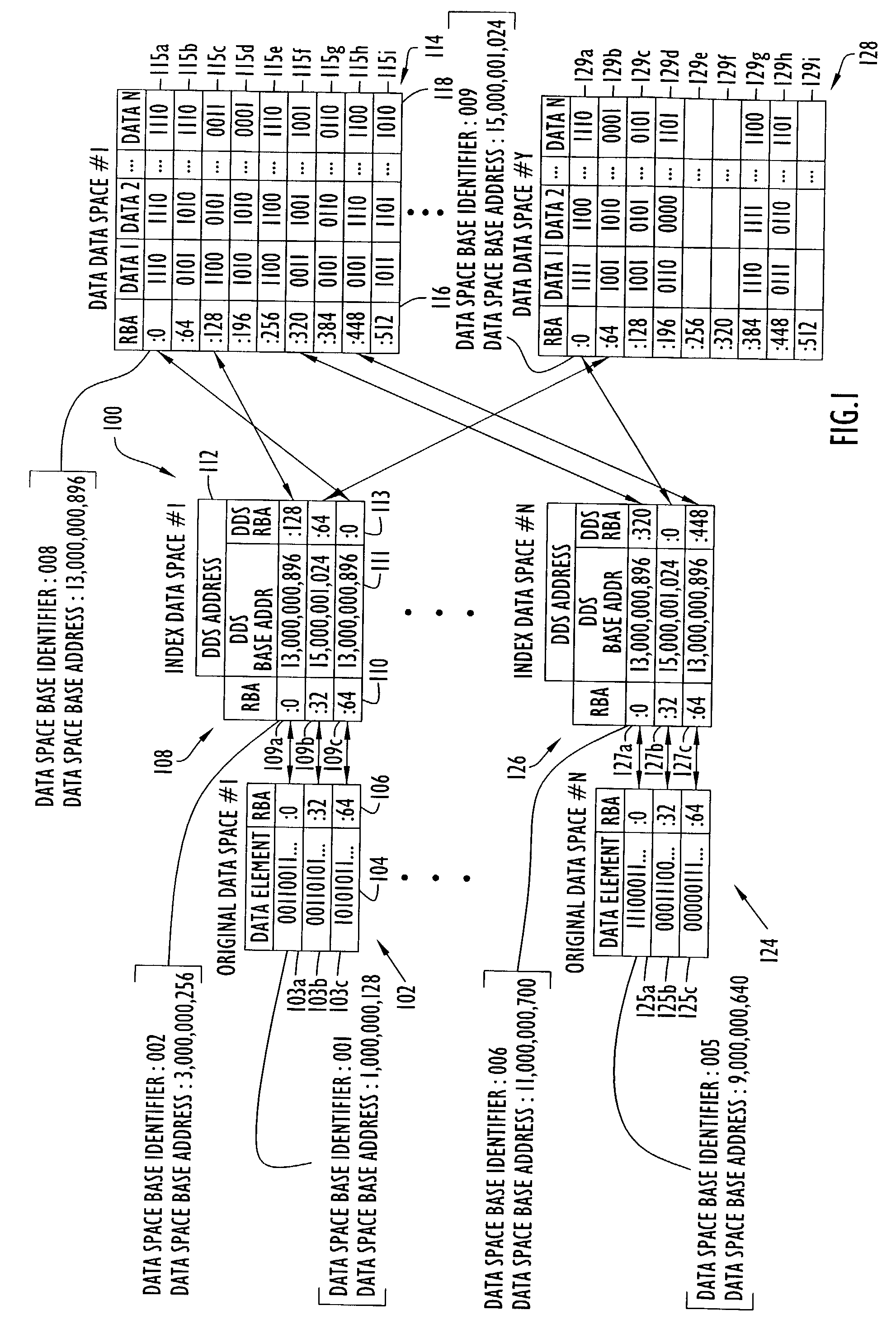
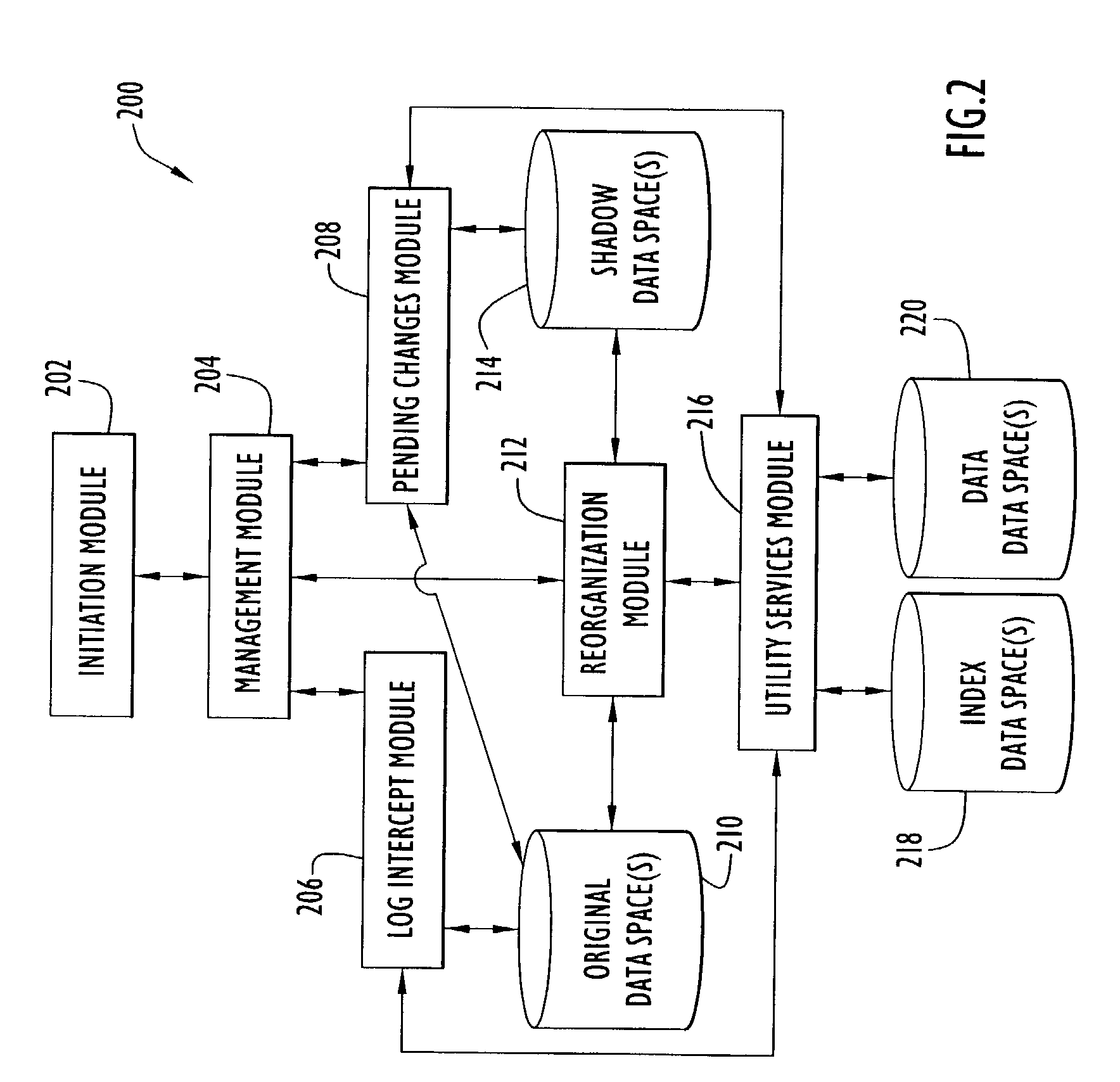
Capturing data changes utilizing data-space tracking
InactiveUS7085787B2Maximum efficiencyData processing applicationsDigital data information retrievalOriginal dataData space
Owner:INT BUSINESS MASCH CORP
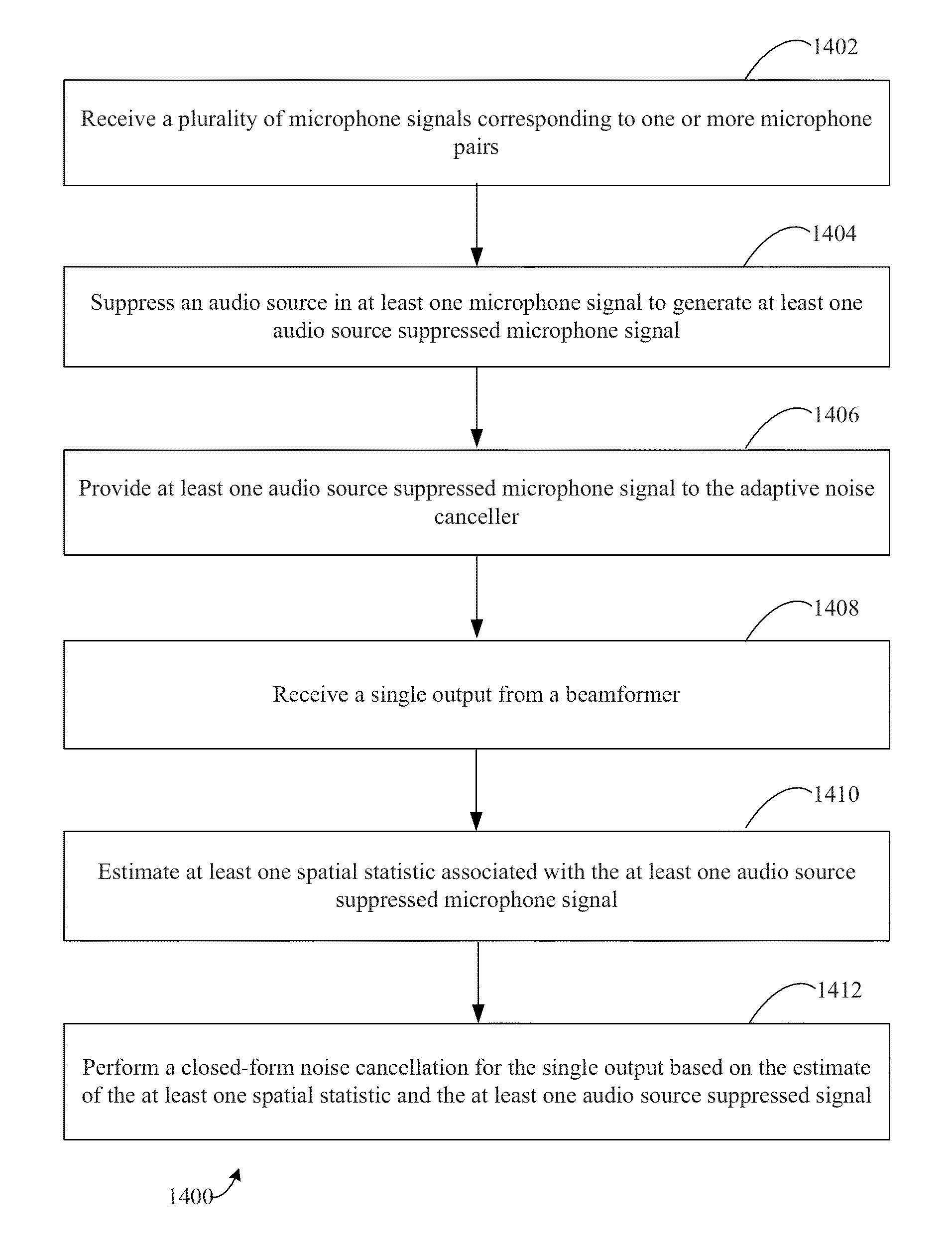
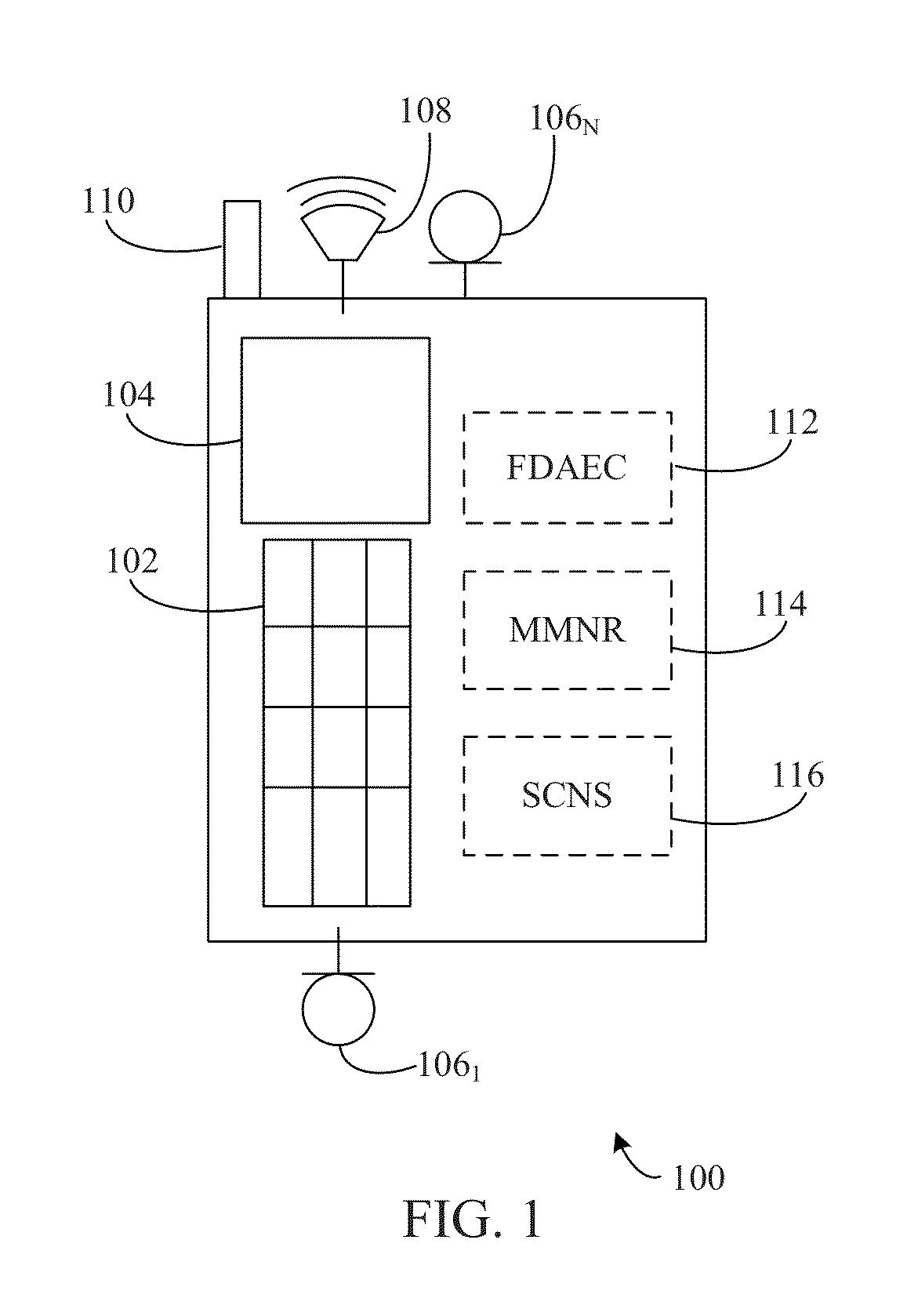
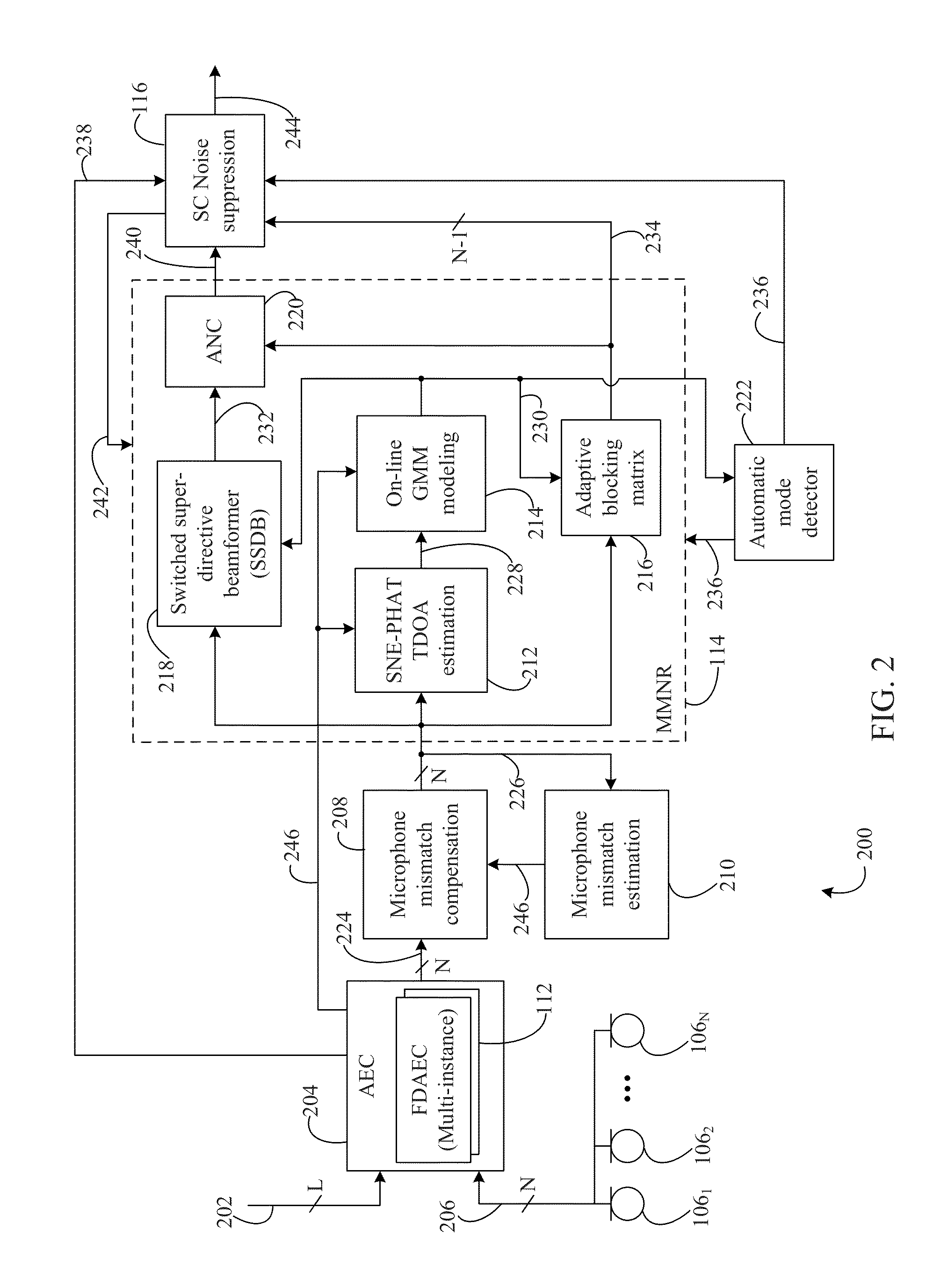
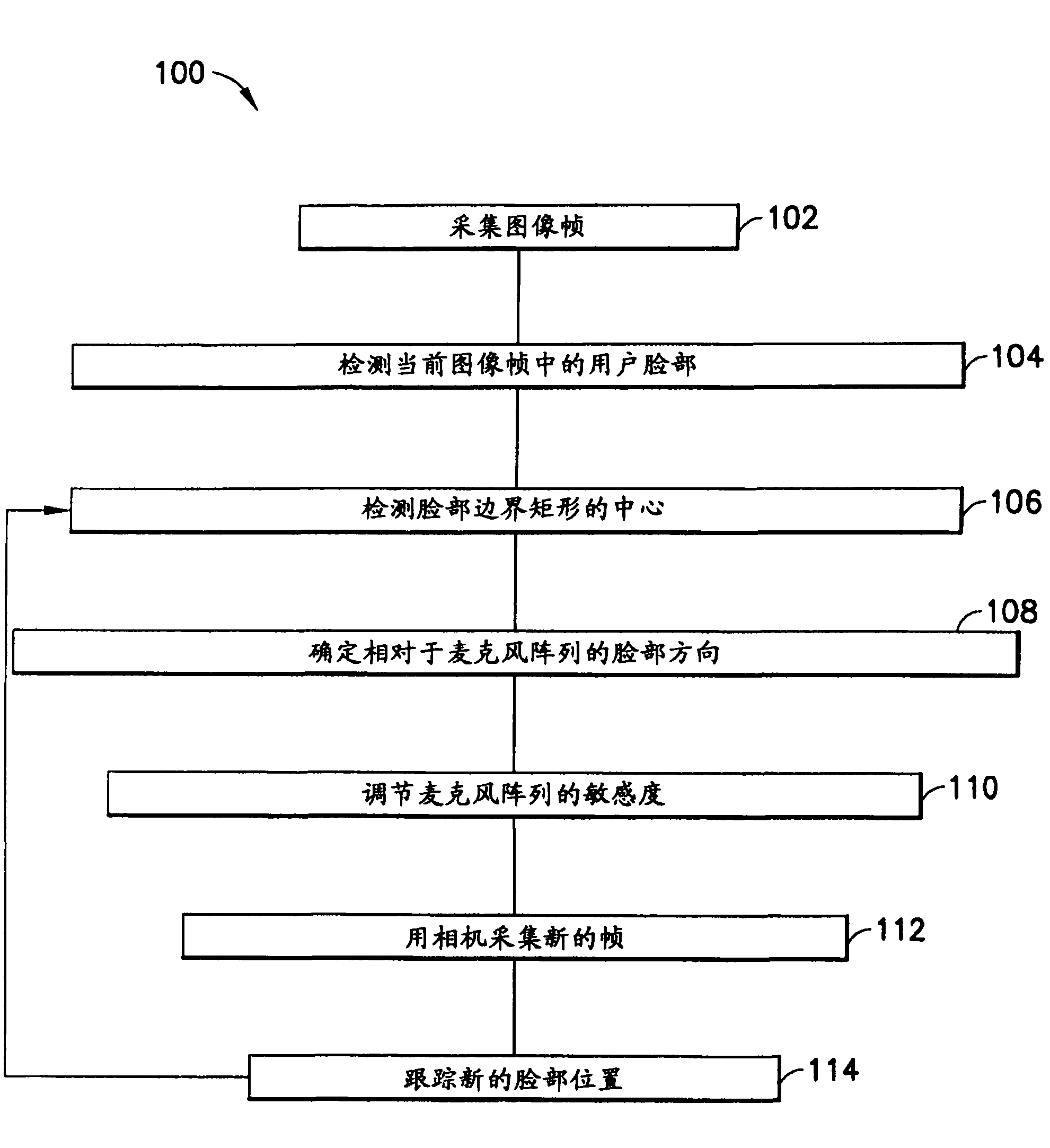
Multi-microphone source tracking and noise suppression
Methods, systems, and apparatuses are described for improved multi-microphone source tracking and noise suppression. In multi-microphone devices and systems, frequency domain acoustic echo cancellation is performed on each microphone input, and microphone levels and sensitivity are normalized. Methods, systems, and apparatuses are also described for improved acoustic scene analysis and source tracking using steered null error transforms, on-line adaptive acoustic scene modeling, and speaker-dependent information. Switched super-directive beamforming reinforces desired audio sources and closed-form blocking matrices suppress desired audio sources based on spatial information derived from microphone pairings. Underlying statistics are tracked and used to updated filters and models. Automatic detection of single-user and multi-user scenarios, and single-channel suppression using spatial information, non-spatial information, and residual echo are also described.
Owner:AVAGO TECH INT SALES PTE LTD
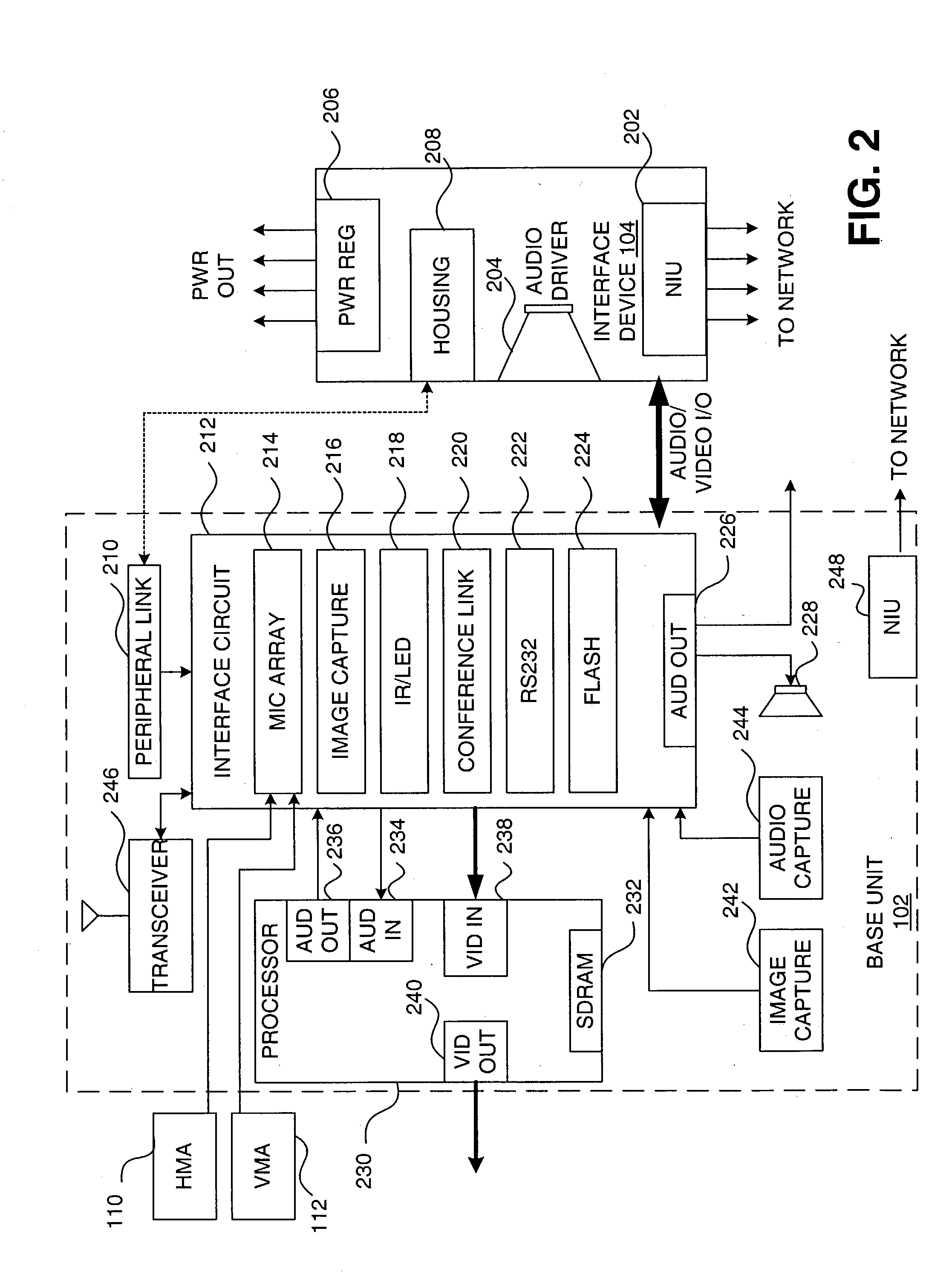
Conferencing system with integrated audio driver and network interface device
ActiveUS20040012669A1Multiplex system selection arrangementsSpecial service provision for substationNetwork interface deviceHuman–computer interaction
A conferencing system with improved audio response, interface, and audio source tracking capabilities includes a low-profile base unit capable of capturing and processing audio and video information and of interfacing with other external devices, and a separate network interface device coupled to the low-profile base unit and capable of connecting to a network, producing audible sound, regulating power, and housing removable interface circuitry.
Owner:POLYCOM INC
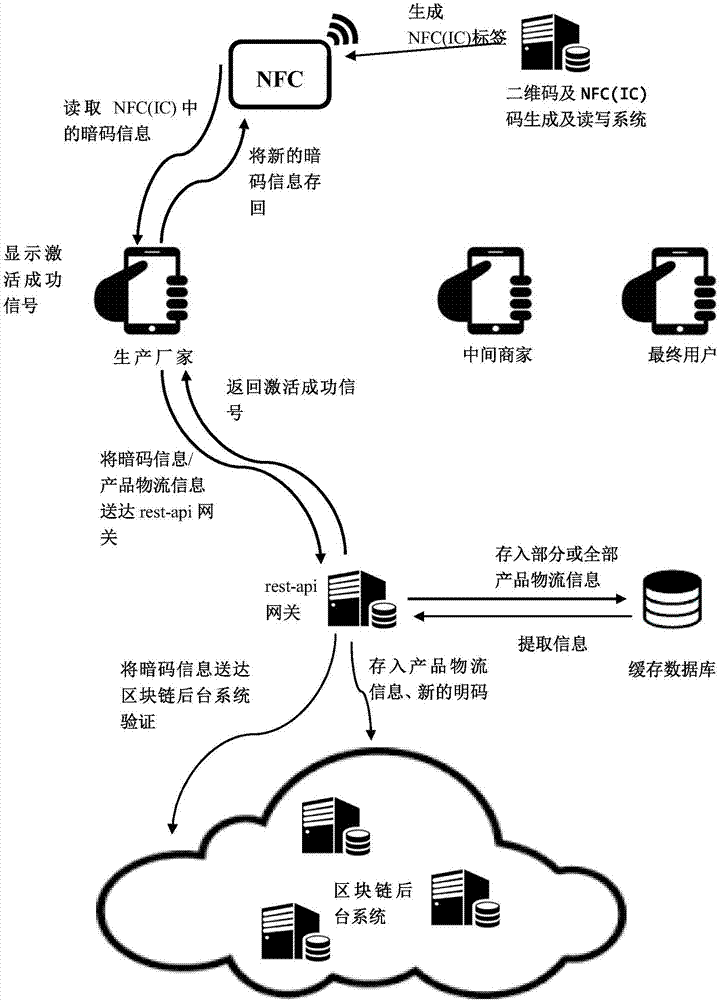
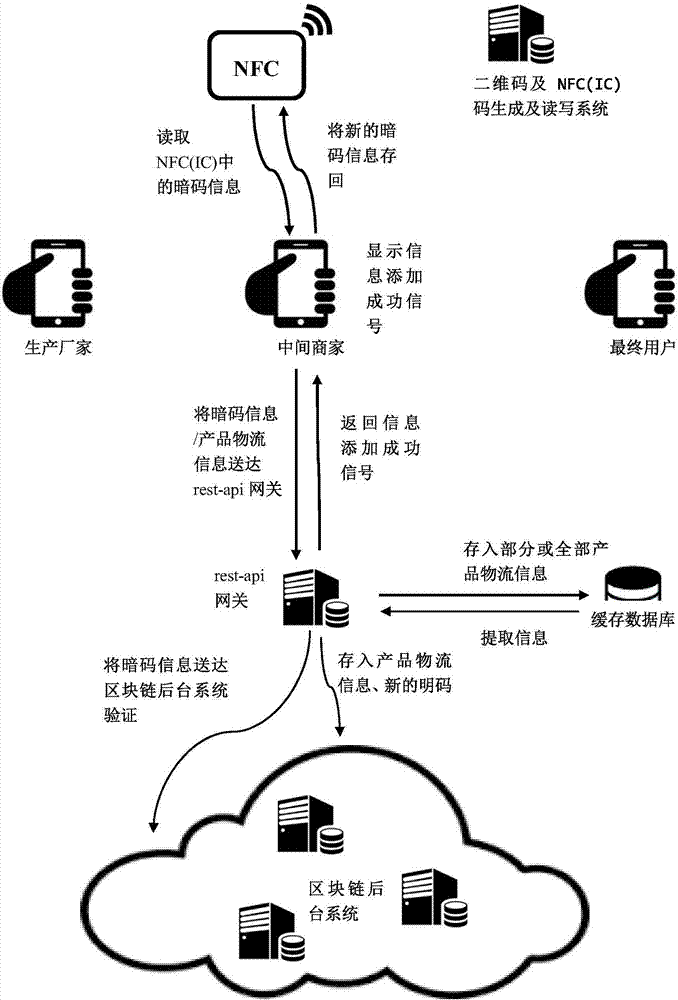
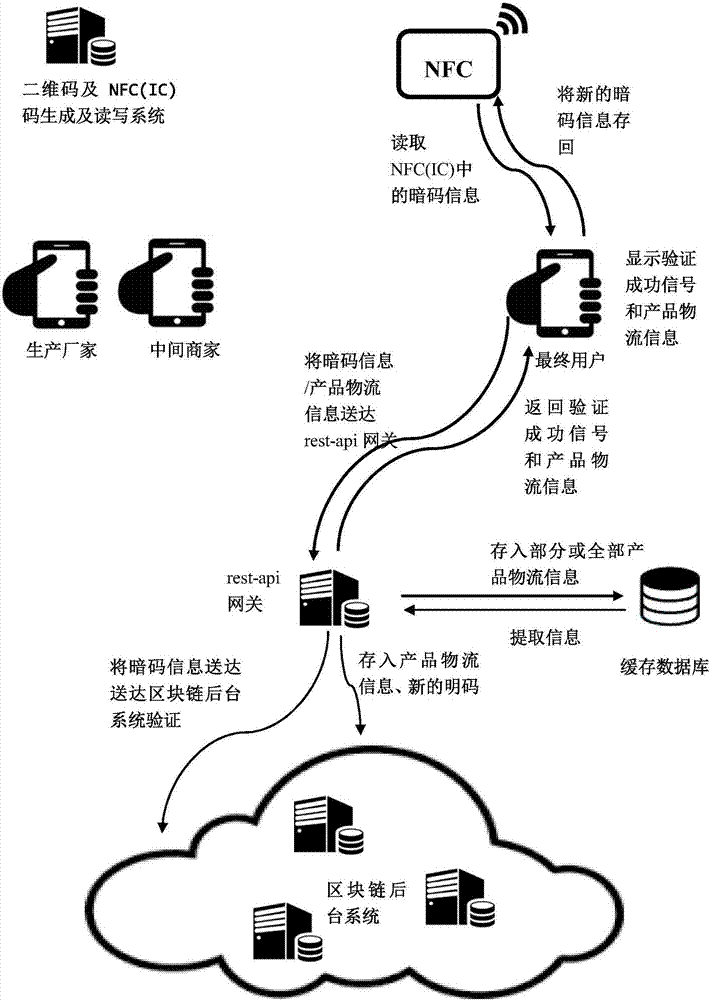
Block chain logistic source tracking anti-fake method based on NFC (Near Field Communication)
InactiveCN107133532AAchieve traceabilityAvoid self-indulgenceCo-operative working arrangementsDigital data protectionThird partyPassword
The invention discloses a block chain logistic source tracking anti-fake method based on NFC (Near Field Communication). The method is based on a source tracking anti-fake system and comprises a publicly verifiable block chain background system, a block chain gateway system, a mobile intelligent read-write terminal, a cash databank and an NFC (IC) (Integrated Circuit) or internal NFC (IC) anti-fake label. The method comprises the following steps: generating an anti-fake label; initializing the anti-fake label; activating by a producer; adding information by a middleman; and verifying by a final user; after the anti-fake label is scanned at the read-write terminal each time, substituting a hidden password on an NFC chip and a corresponding visible password in a block chain by newly generated hidden passwords and visible passwords, and disabling the used hidden password and the visible password. By adopting the method, problems of trust dependence of users upon nodes in different product logistic procedures, trust dependence upon a third party, dependence upon techniques, trust dependence upon anti-fake labels and trust target deviation are solved, the introduction threshold is low, and the anti-fake security and reliability can be greatly improved.
Owner:无锡井通网络科技有限公司
Method and apparatus for acoustic source tracking using a horizontal line array
InactiveUS20060133211A1Improve abilitiesEasy to solveSignal processingMicrophones signal combinationSound sourcesEnvironmental acoustics
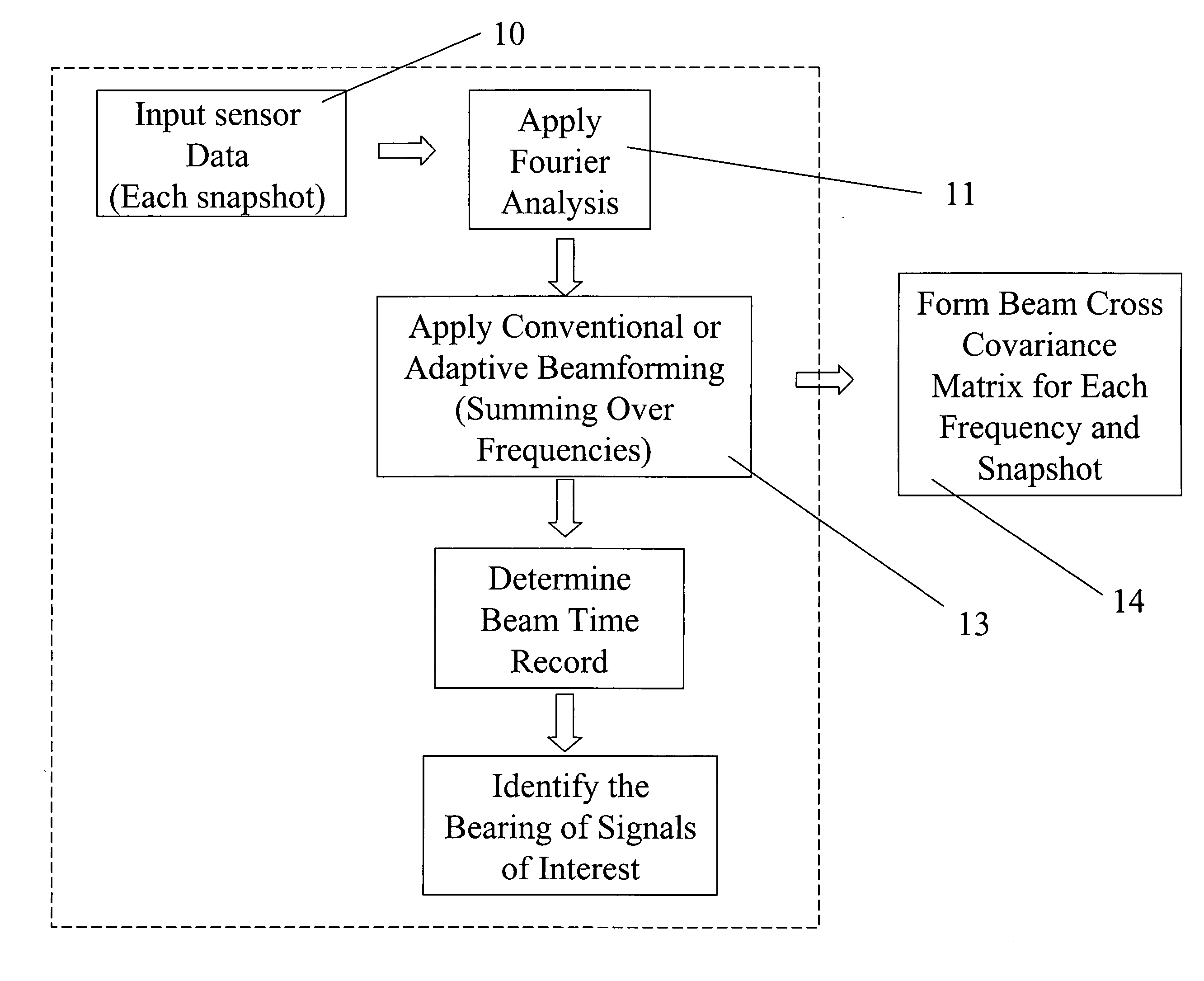
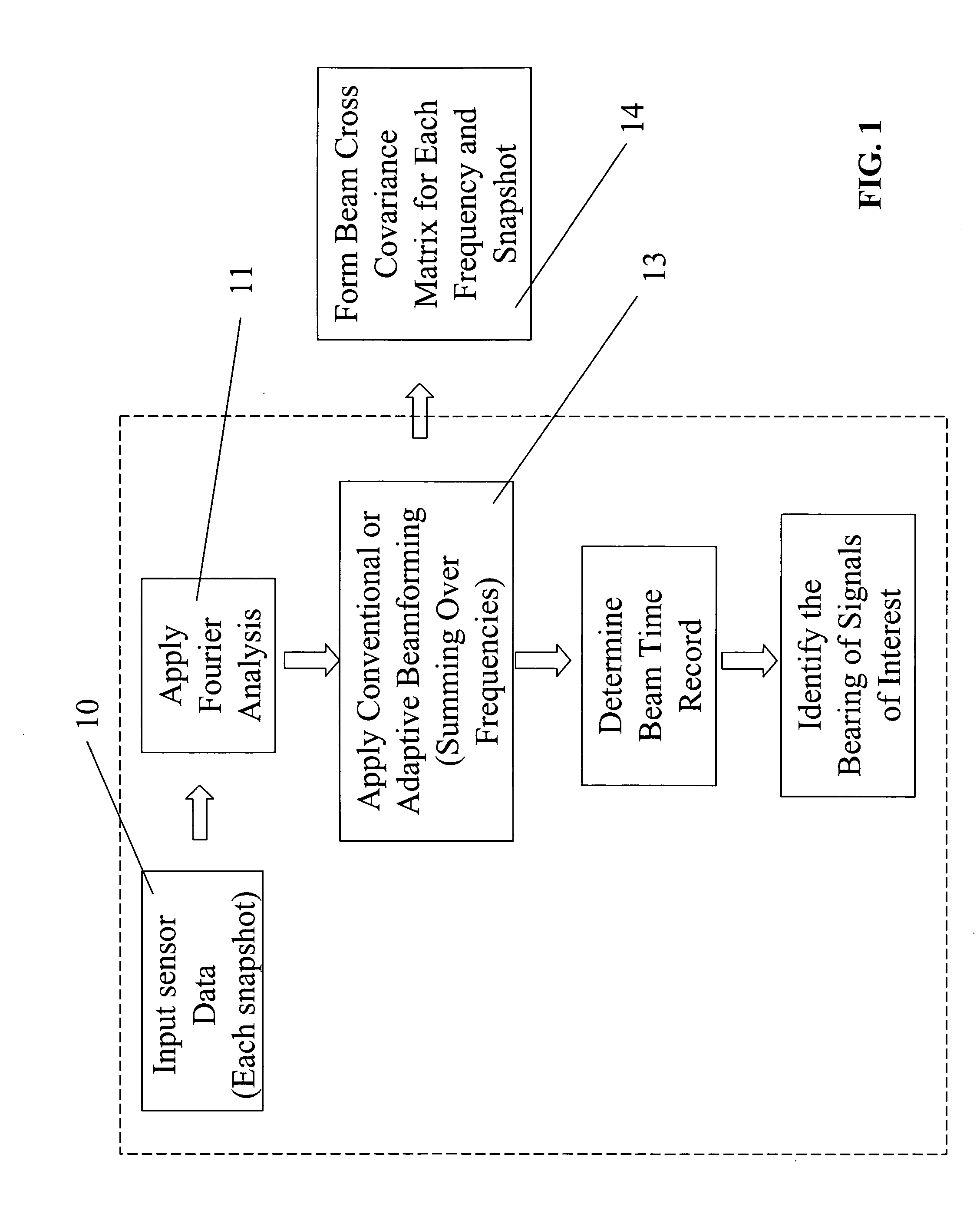
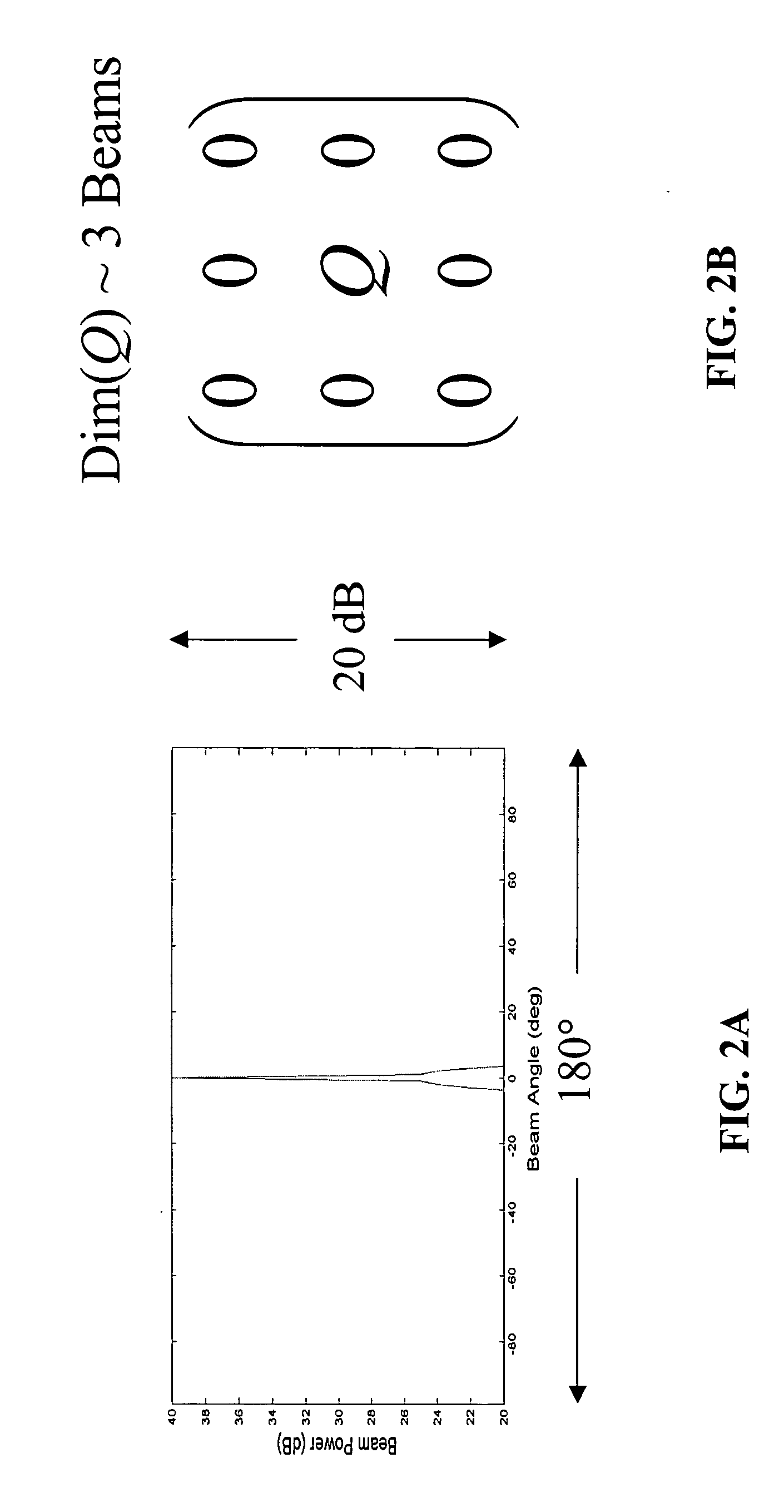
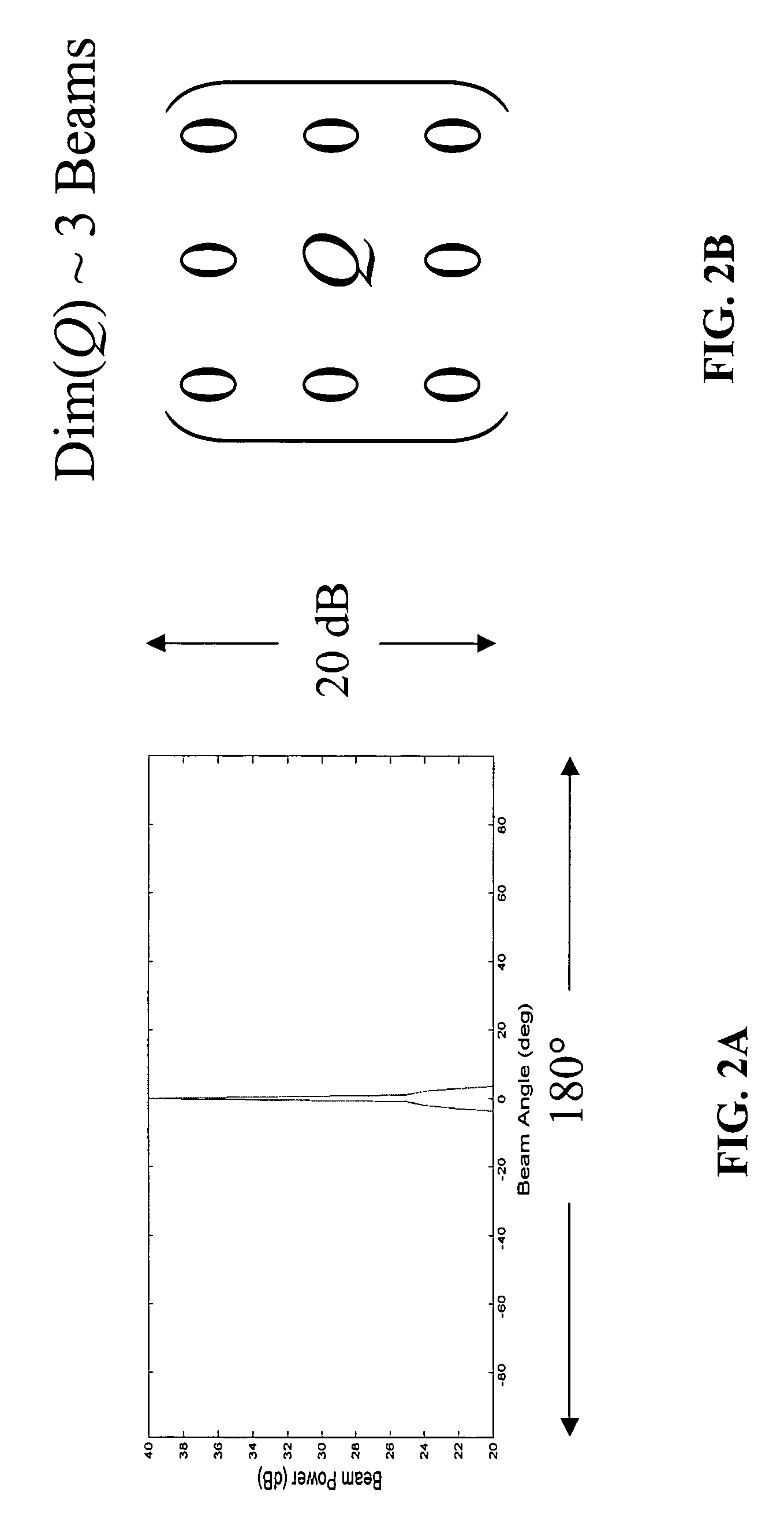
An apparatus for processing passive acoustic signals received on a horizontal line array that were either emitted from an underwater object or echo returned from an object, is proposed to track the motion (bearing change and range change) of an object (target) relative to the receiver horizontal line array. Adaptive array processing for a moving object is biased for a moving source when the number of data samples is limited by the stationariness condition. Motion compensation can be carried out in the beam domain by beam shifting for a bearing changing object and frequency shifting for a range changing object. The method includes receiving acoustic signals from the target, determining the beam covariance matrices, determining the target bearing rate and range rate, processing the beam covariance matrices by compensating for the target motion, and producing a beam power plot versus time. Interference signal is suppressed when the interference source does not have the same motion (bearing and range rate) as the target. The method does not need detailed environmental acoustic information of the sound channel normally required to model the sound propagation.
Owner:USA AS REPRESENTED BY THE SEC OF THE NAVY THE
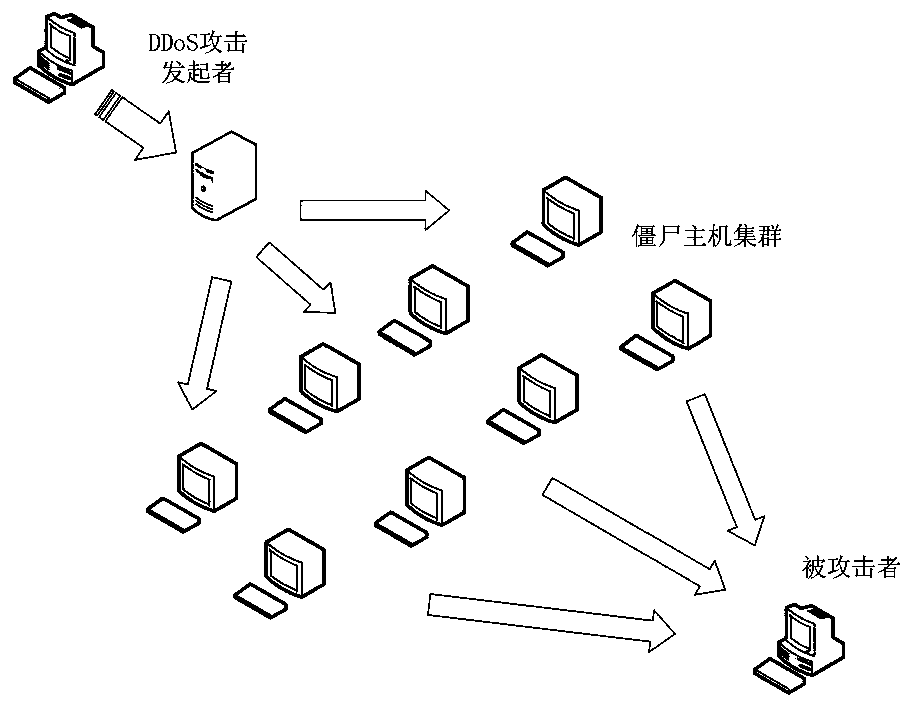
Software defined opportunity network DDoS defense method based on block chain
ActiveCN110113328AGuaranteed reliabilityPrevent tamperingTransmissionTraffic characteristicControl layer
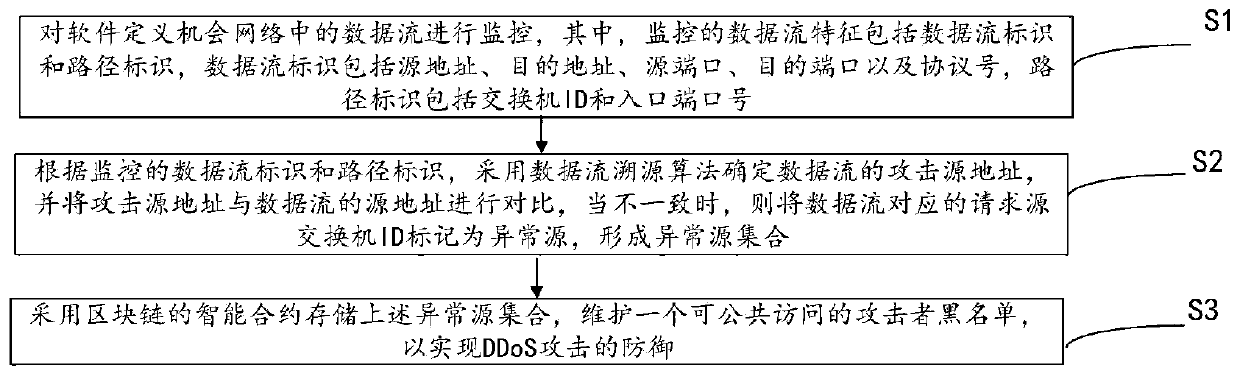
The invention discloses a software defined opportunity network DDoS defense method based on a block chain. Firstly, the characteristic that the SDN can perform logic centralized management and controlon a control layer is utilized; the network state is dynamically monitored in real time; then, the possibility of existence of a DDoS amplification attack is analyzed by analyzing the traffic characteristics obtained by monitoring, an attacker address is determined according to a traceability algorithm, and finally, a public accessible attacker blacklist is maintained by using a block chain architecture to assist an application layer in malicious traffic filtering so as to realize defense of the DDoS attack. According to the method, the attack source tracking accuracy is improved, the storage of the attack source blacklist address is realized in combination with the block chain architecture, and the attack source storage architecture based on the distributed account book technology can effectively prevent the data from being tampered or damaged while maintaining the data reliability. The whole network can perform filtering in a data packet receiving stage by inquiring a blacklist address, so that the DDoS attack is prevented from the source.
Owner:WUHAN UNIV OF TECH
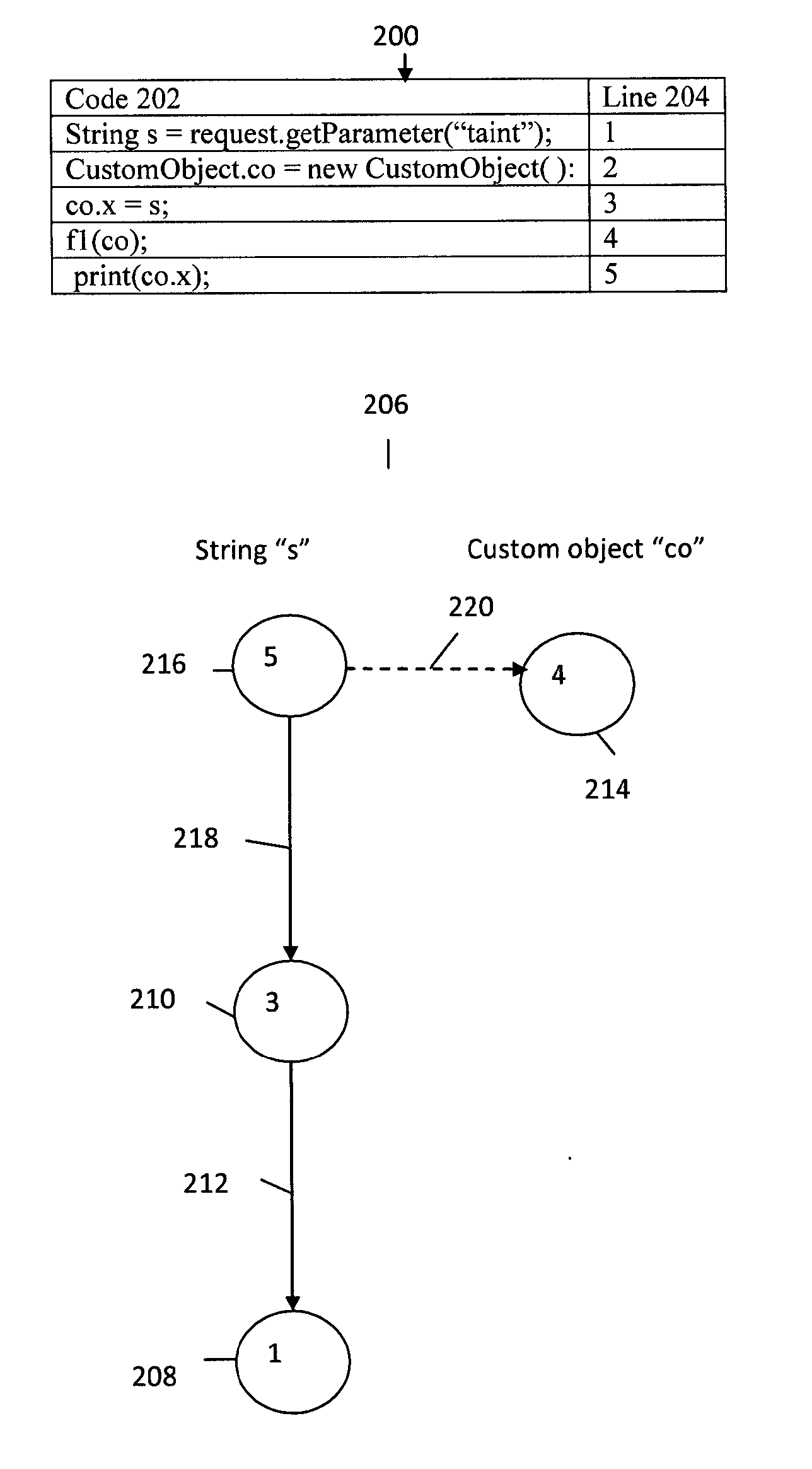
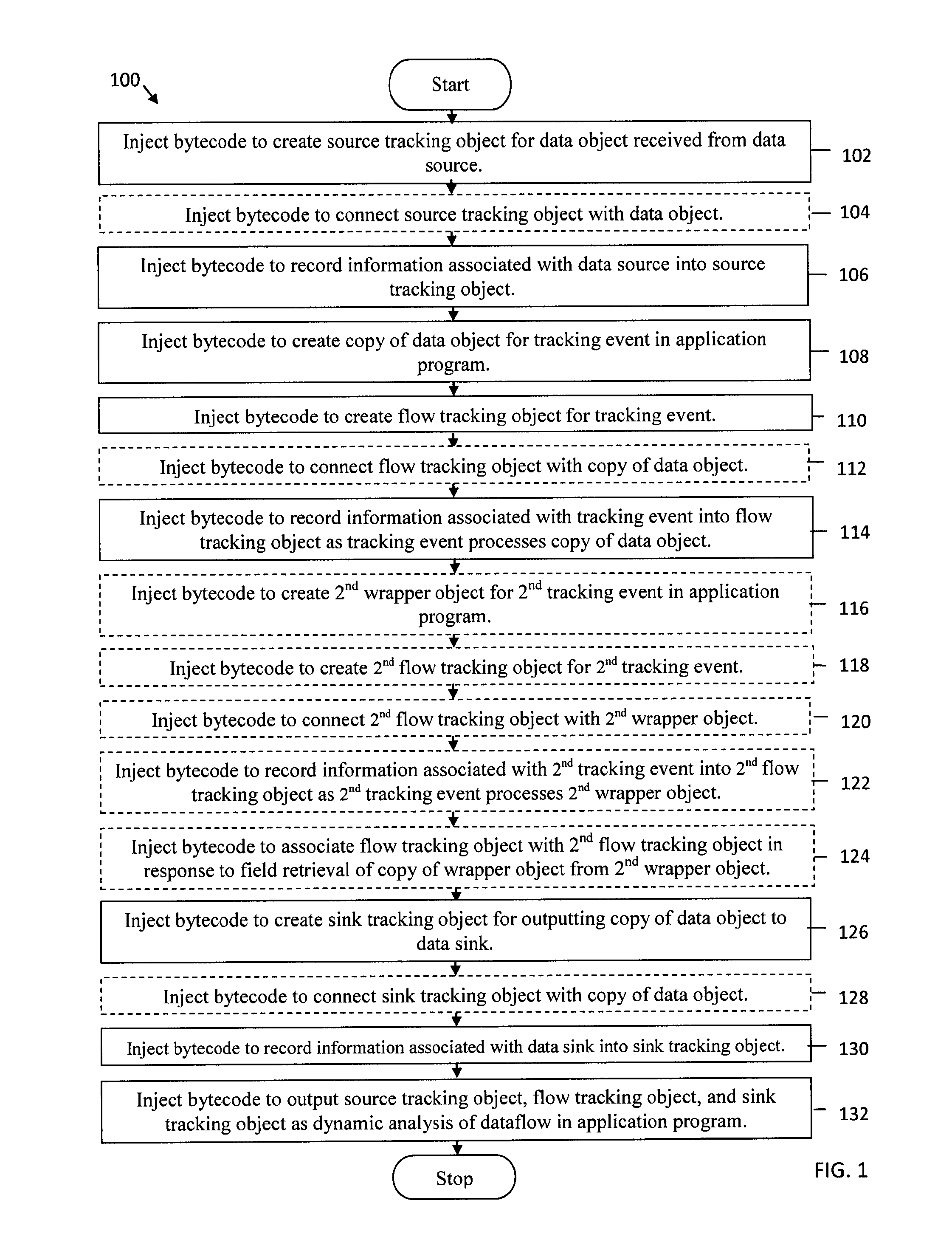
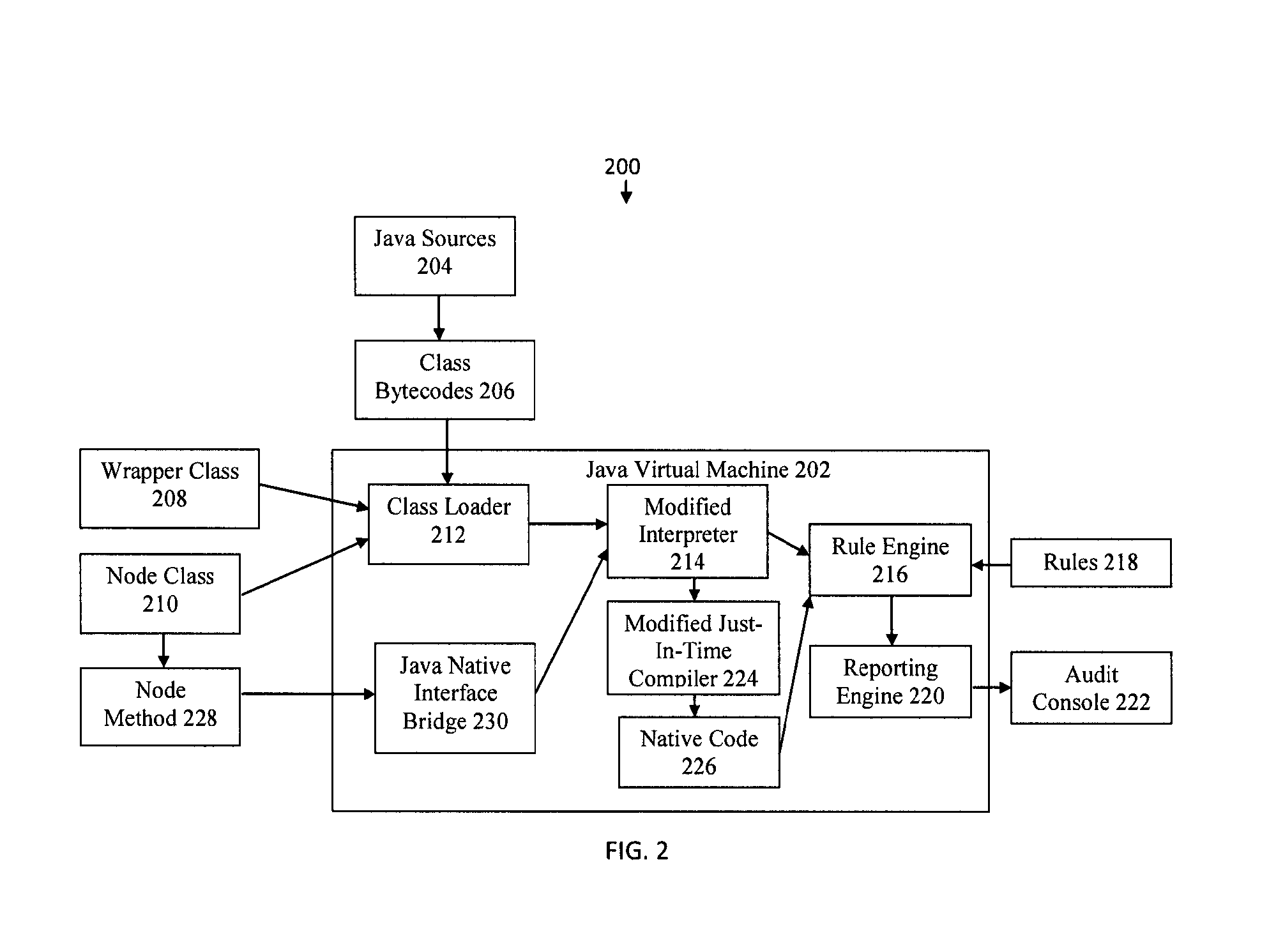
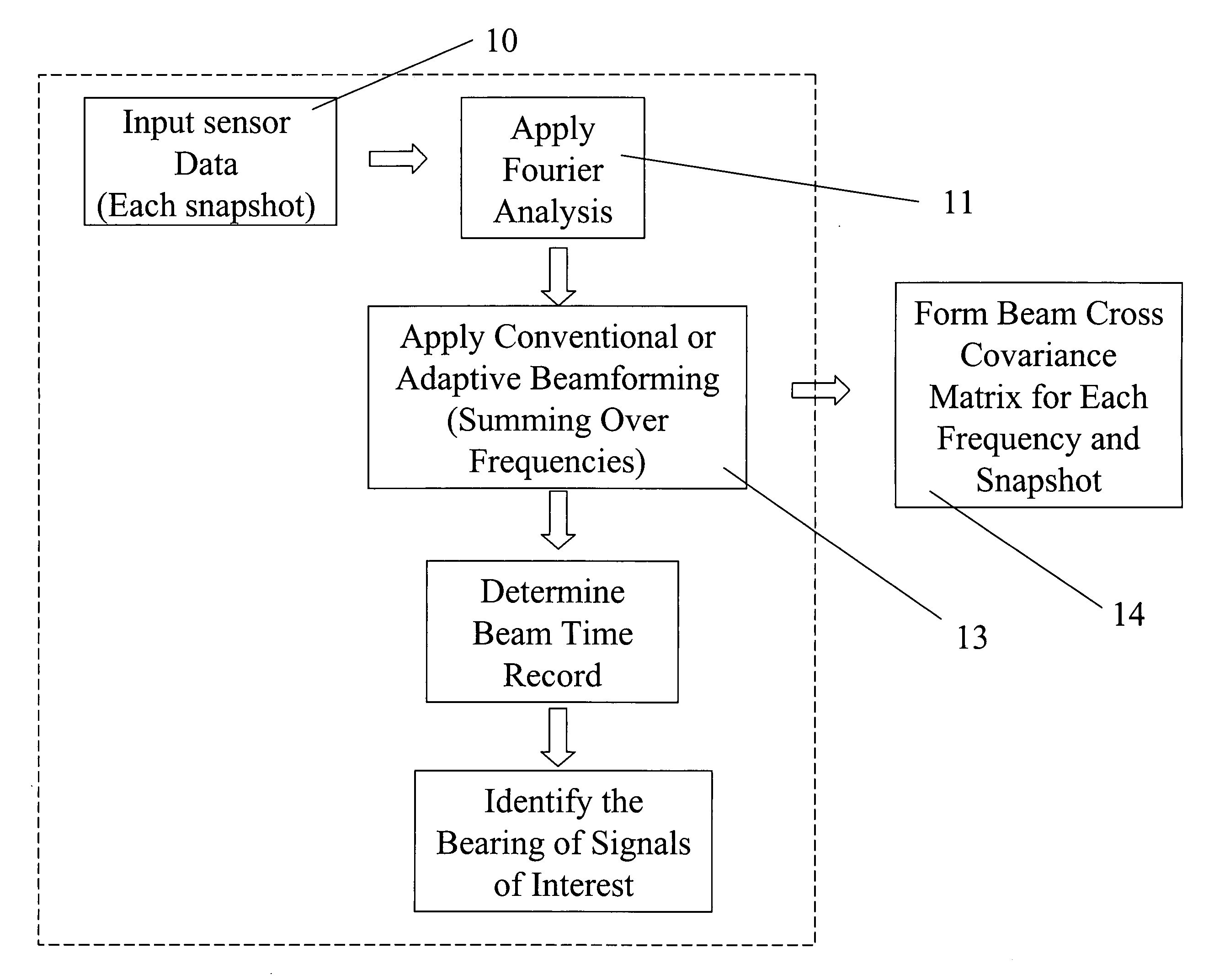
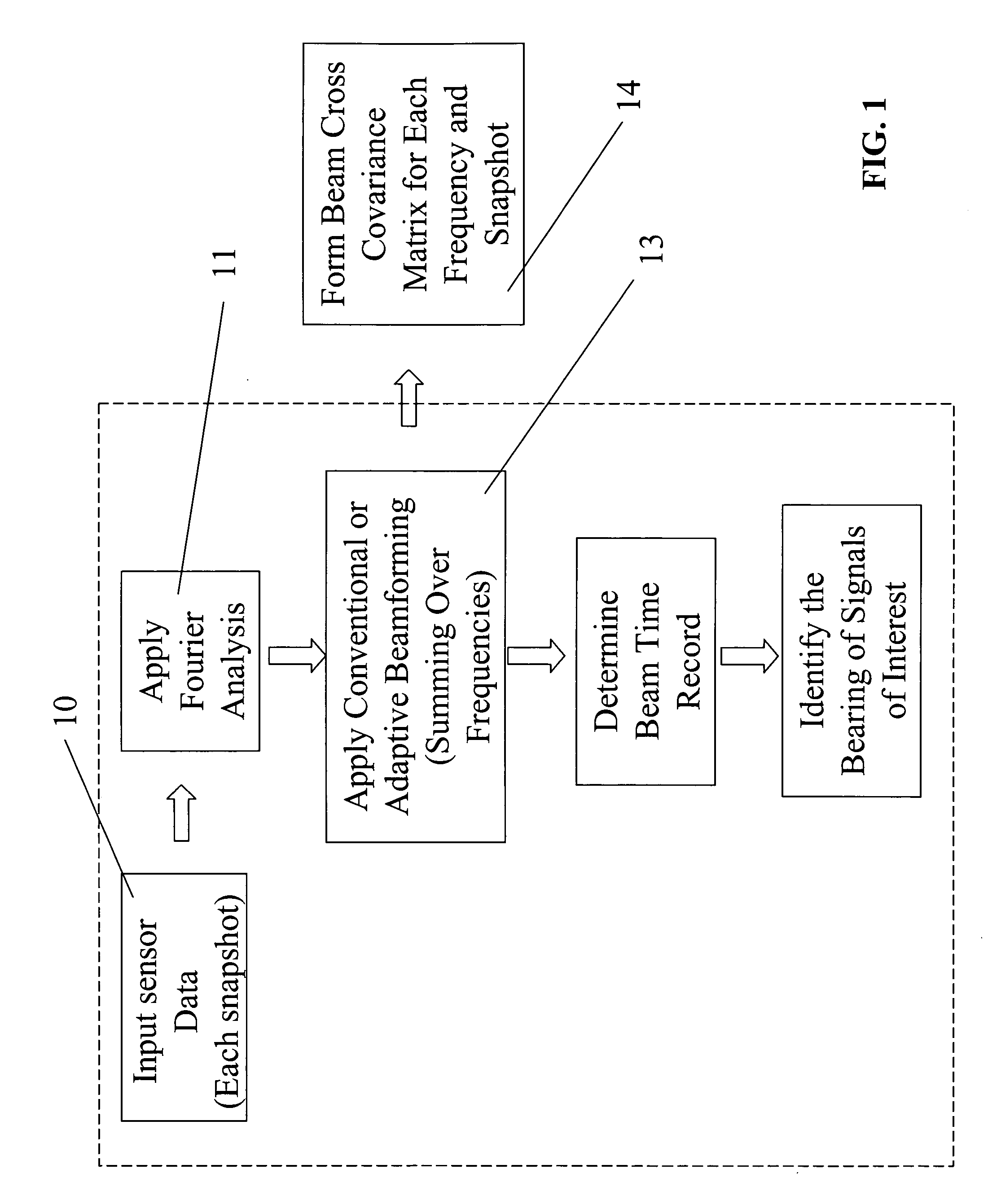
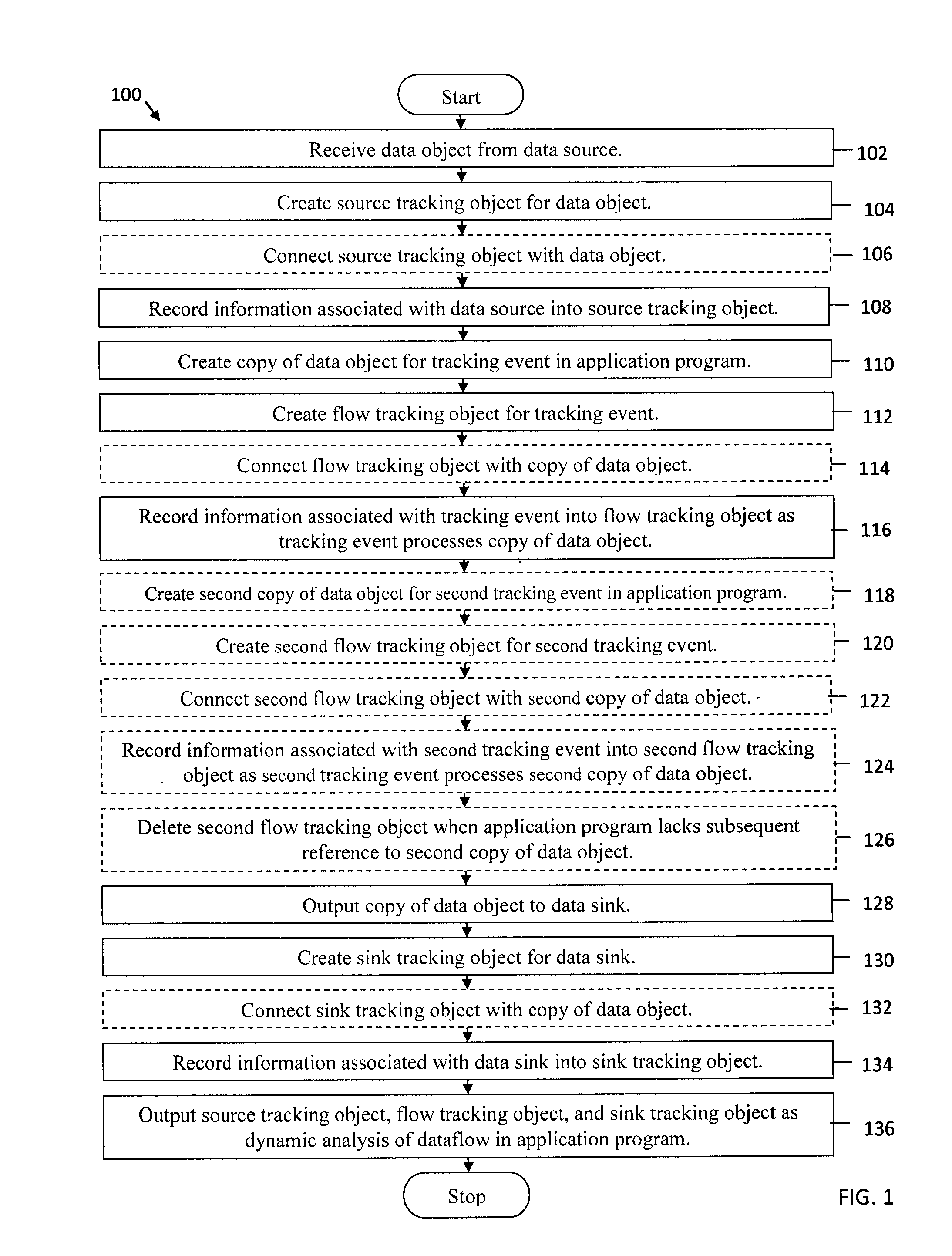
System and method for dynamic analysis bytecode injection for application dataflow
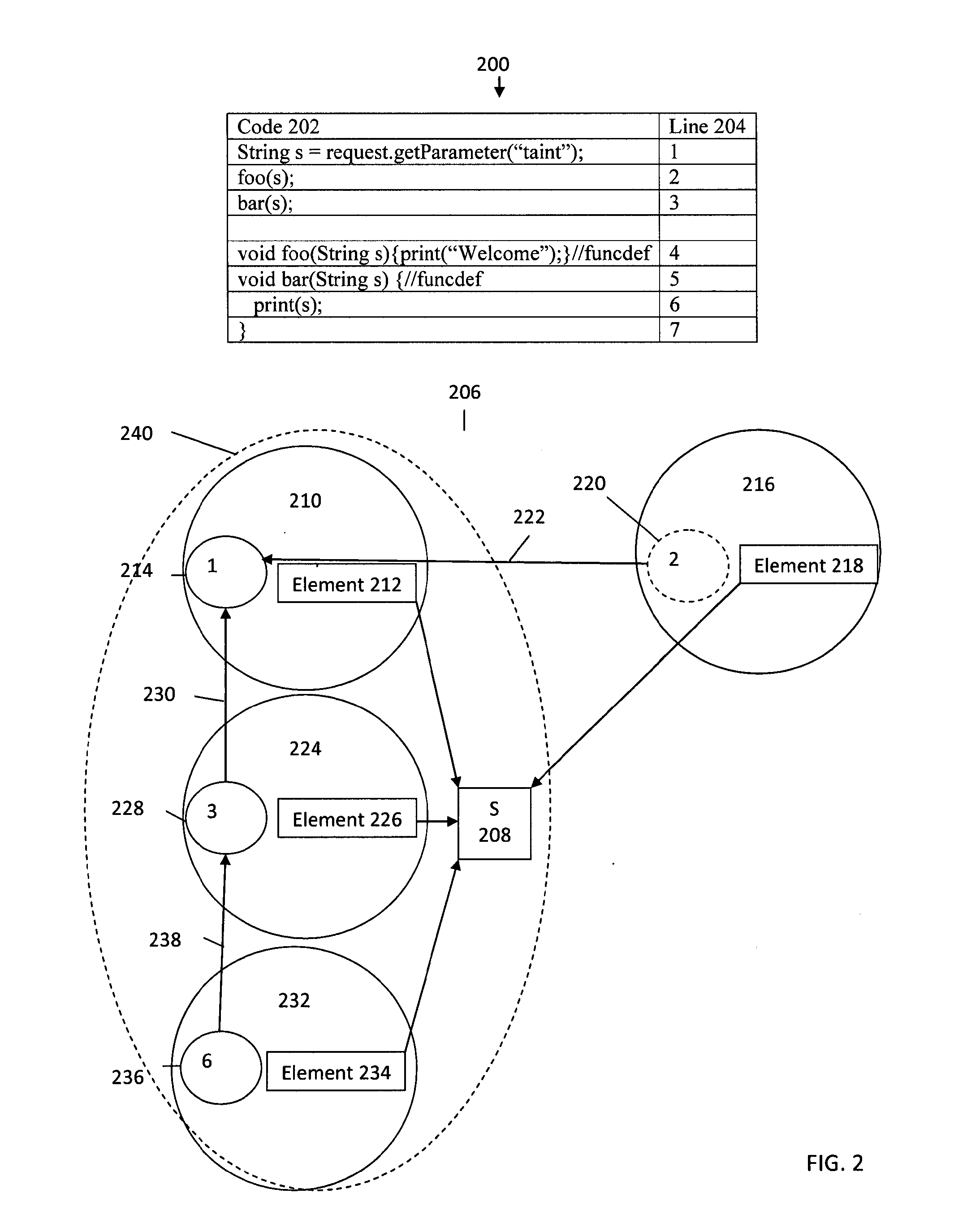
Bytecode is injected to create a source tracking object for a data object received from a data source and to record information associated with the data source into the source tracking object. Bytecode is injected to create a copy of the data object for a tracking event in an application program, to create a flow tracking object for the tracking event, and to record information associated with the tracking event into the flow tracking object as the tracking event processes the copy of the data object. Bytecode is injected to create a sink tracking object for outputting the copy of the data object to a data sink and to record information associated with the data sink into the sink tracking object. Bytecode is injected to output the source tracking object, the flow tracking object, and the sink tracking object as dynamic analysis of dataflow in the application program.
Owner:SALESFORCE COM INC
Arrangement and method for audio source tracking
ActiveUS7586513B2The process is fast and accurateLess sophisticatedTelevision conference systemsPublic address systemsImage resolutionLocation Equipment
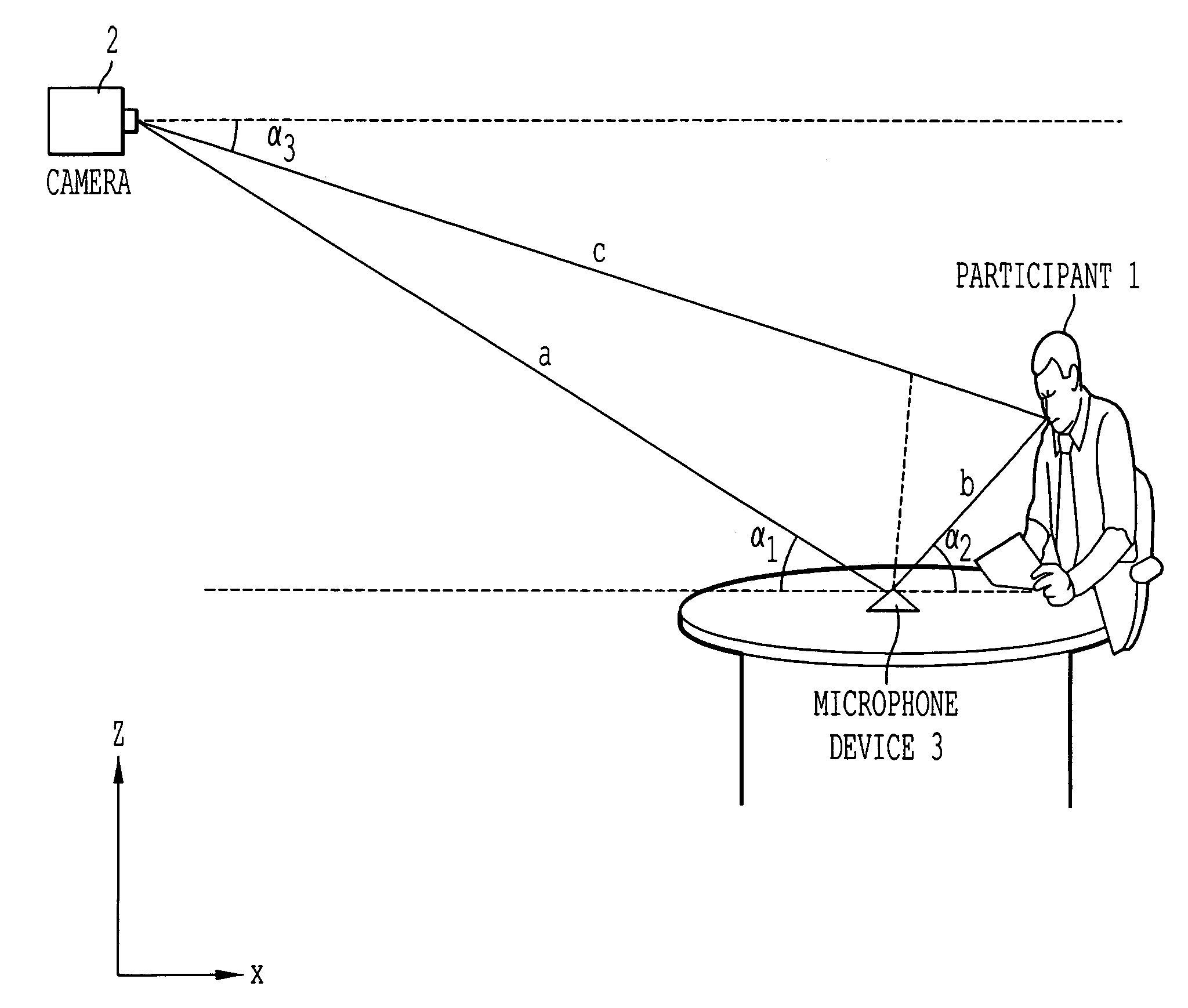
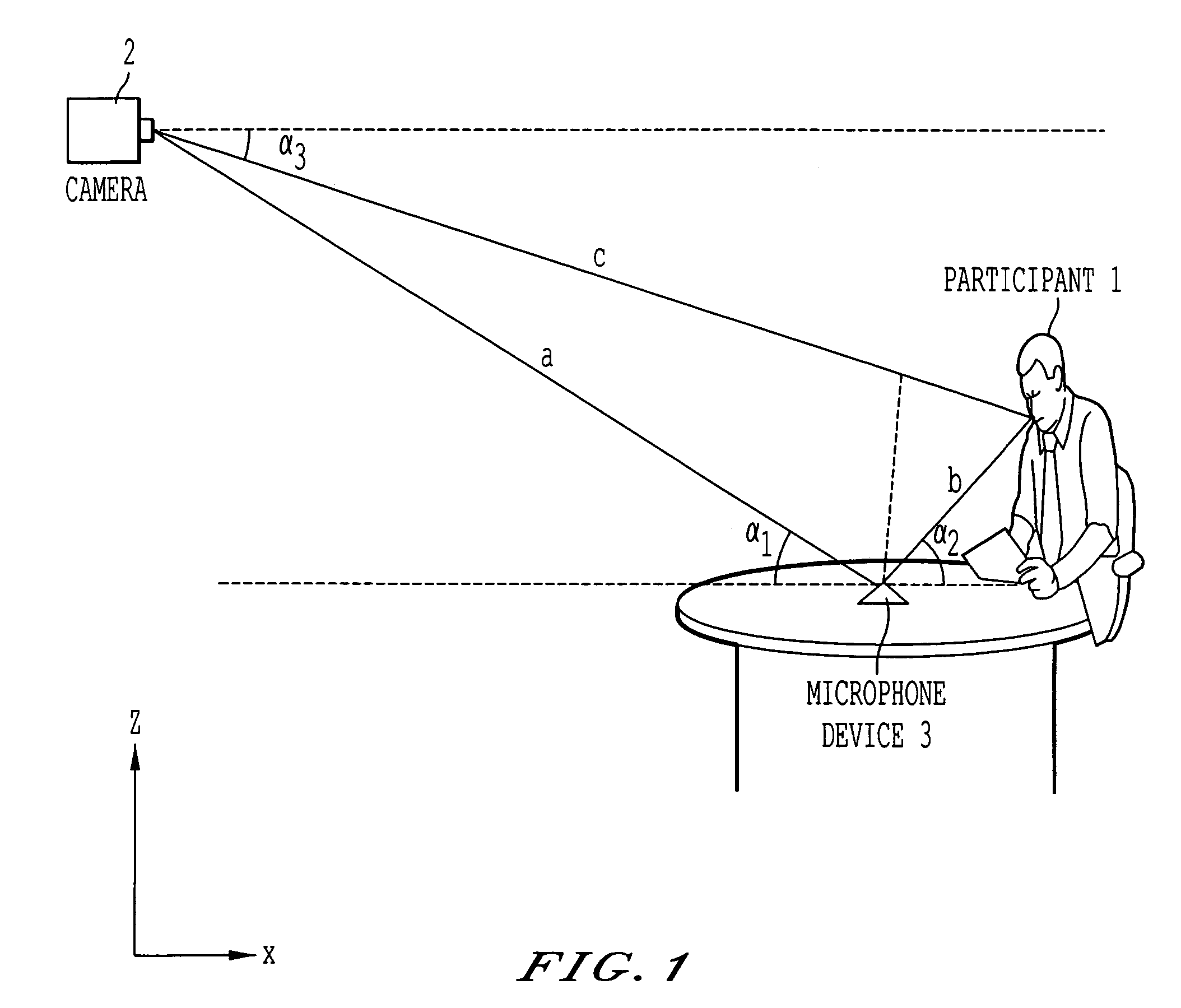
An arrangement and a method of localizing active speakers in a video conference includes a localization device that locates at least one microphone relative to the camera, while the at least one microphone in turn localizes the relative positions of audio sources. As the microphones are usually positioned close to the audio source in a video conference, the ratio of the distance between microphones relative to the distance between table microphone and audio source is reduced. Thus, the microphones are able to determine the positions of the audio sources with a higher resolution than if placed close to the camera. When the respective positions of the microphones relative to the camera and the audio source are known, the position of the audio source relative to the camera is then determined by means of geometrical calculations.
Owner:CISCO TECH INC
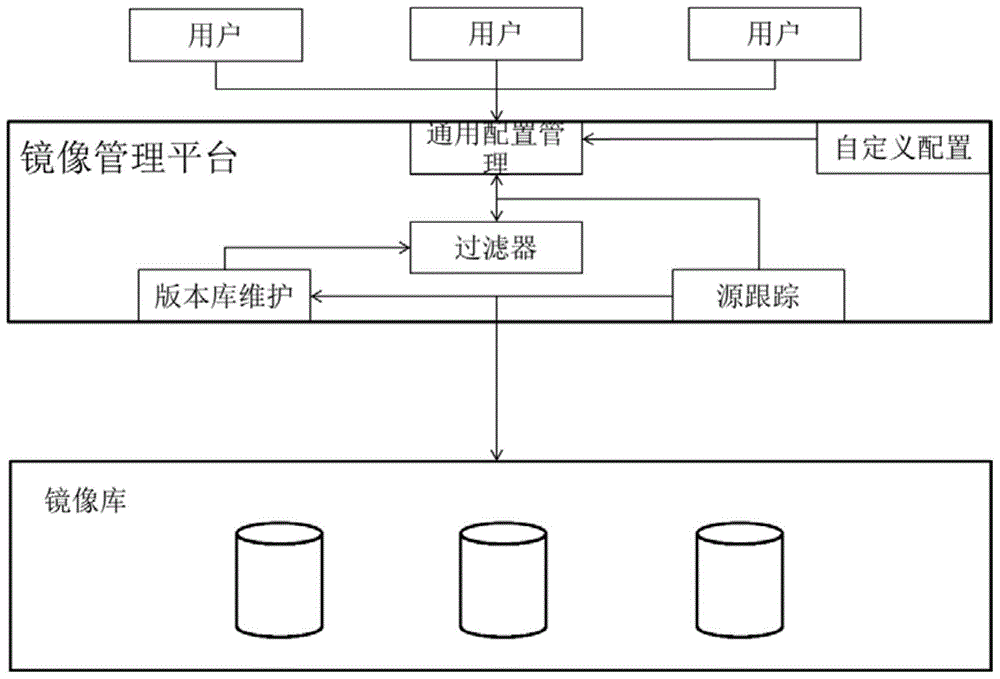
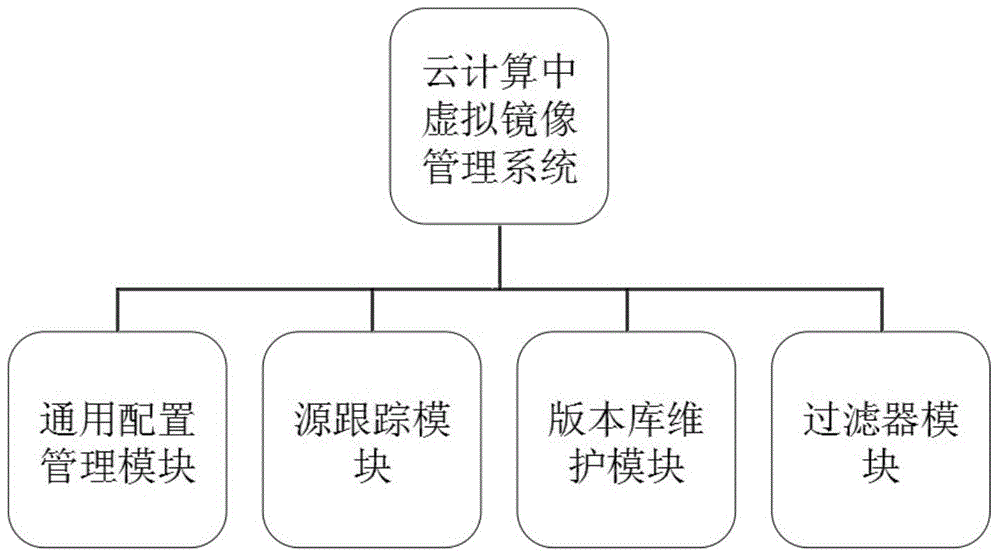
Virtual machine image management system in cloud computing
InactiveCN104679574AIncrease flexibilityAchieve efficiencyTransmissionSoftware simulation/interpretation/emulationComputer moduleManagement system
The invention provides a virtual machine image management system in cloud computing. The system comprises an image repository and an image management platform, wherein a general configuration management module, a source tracking module, a version repository maintenance module and a filter module are arranged in the image management platform; through adoption of a strategy of the virtual machine image file management on the basis of a general configuration management tool, a source tracking mechanism and a version repository maintenance service, the flexibility and the high efficiency of the virtual machine image file management are realized, and the virtual machine image management system has the advantages of being novel in design, favorable in market popularization prospect, convenient for a user to use and good in perception performance and is a good design scheme.
Owner:谢蓉
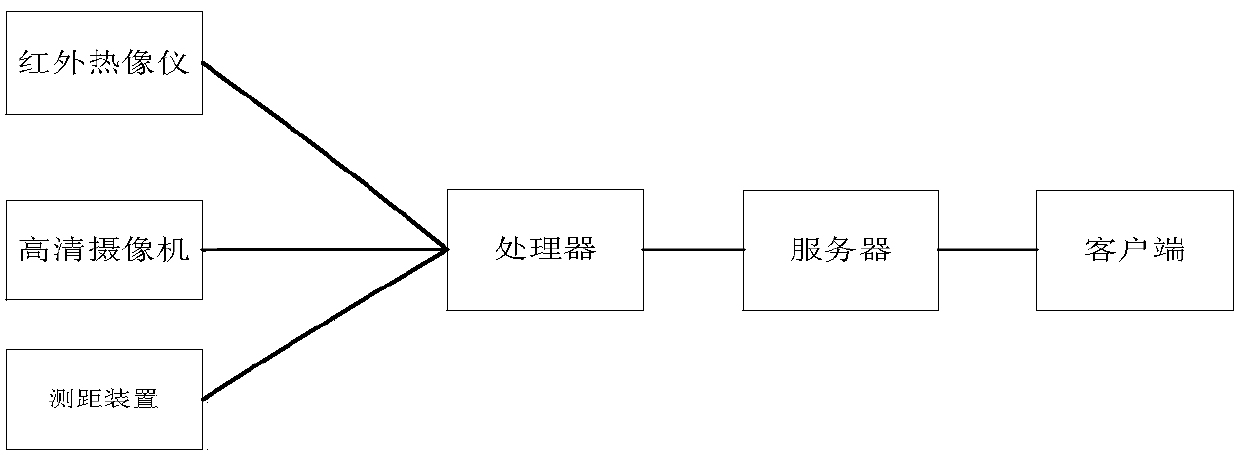
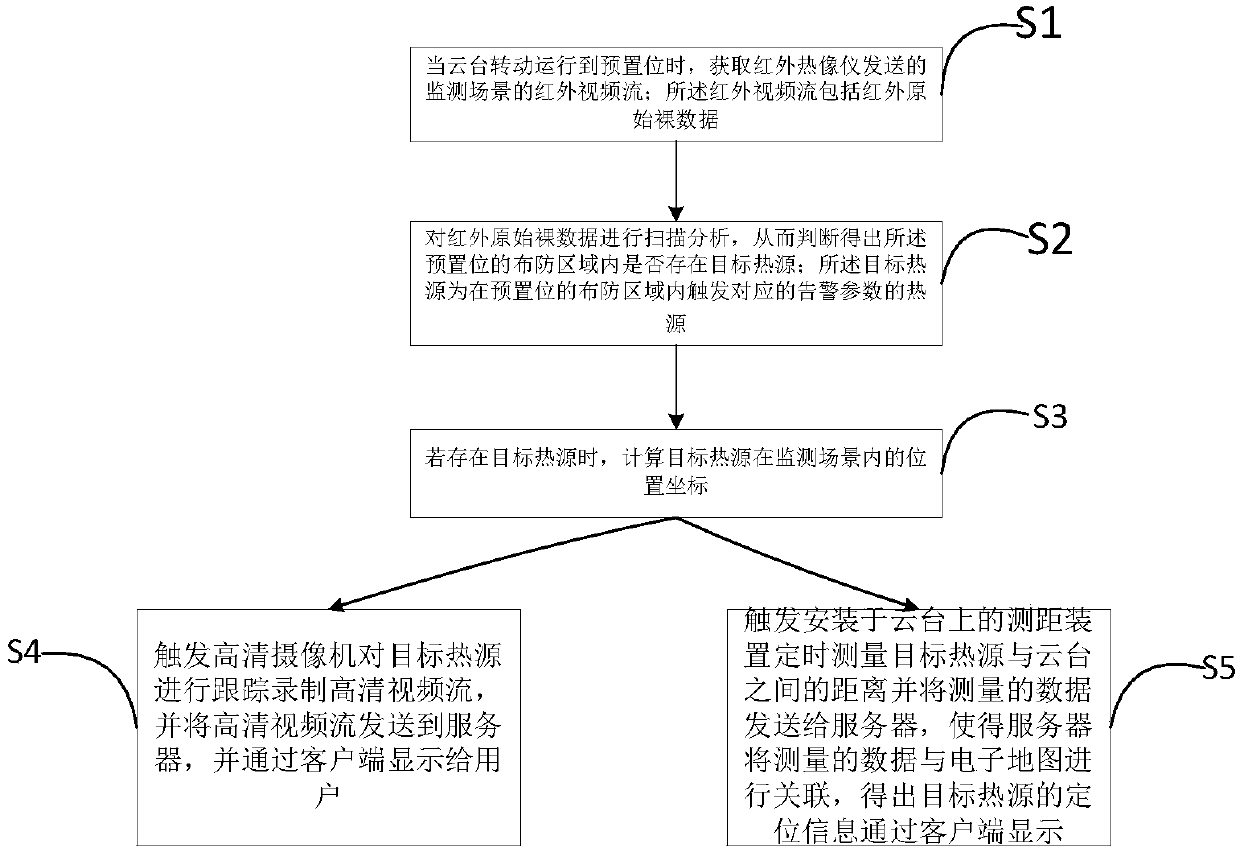
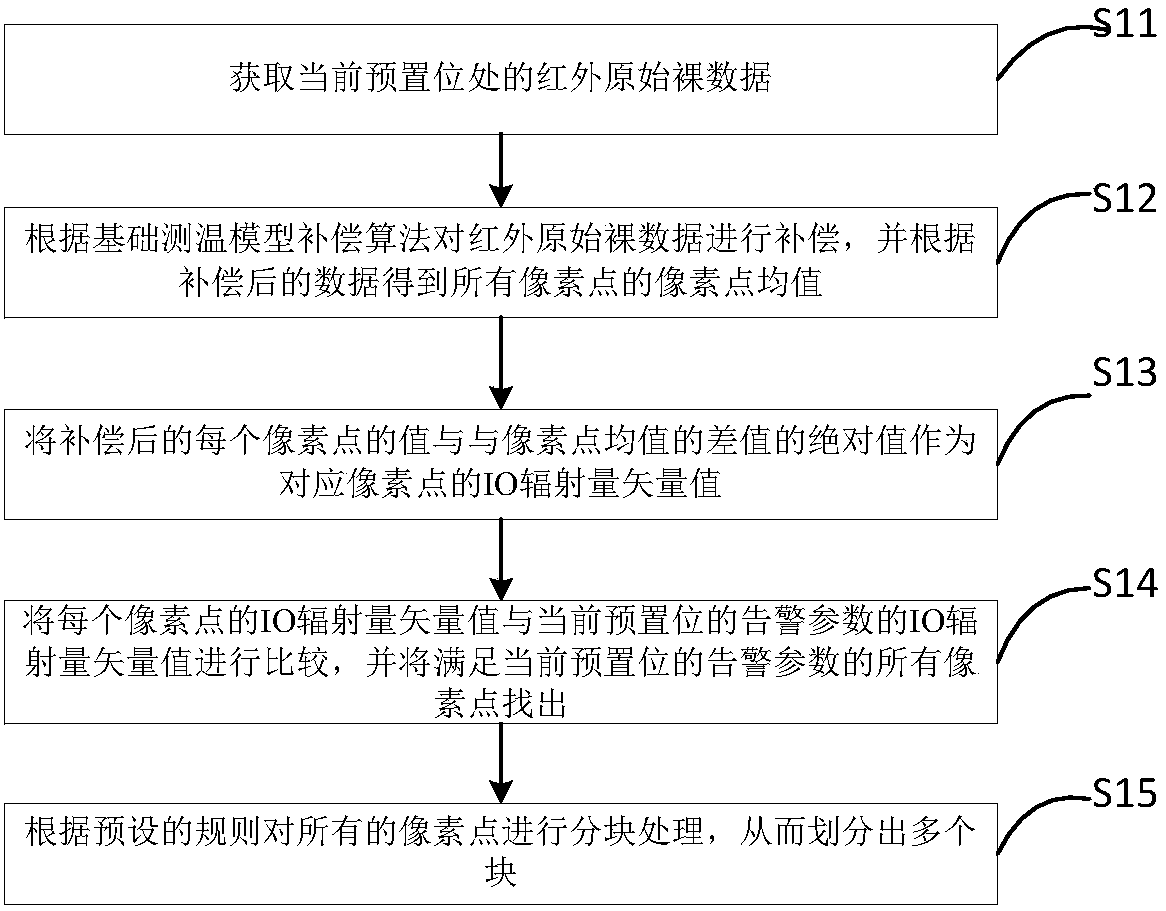
Heat source tracking method, apparatus and system based on thermal infrared imager
ActiveCN107707810AAvoid not being able to fully monitor problemsImage enhancementTelevision system detailsHigh-definition videoComputer science
The invention discloses a heat source tracking method based on a thermal infrared imager. The method comprises the following steps: when a holder rotationally runs to a preset position, obtaining an infrared video stream of a monitoring scene sent by the thermal infrared imager, wherein the infrared video stream comprises infrared original raw data; performing scanning analysis on the infrared original raw data to judge whether a target heat source exists in a deployment area of the preset position; when the target heat source exists, calculating position coordinates of the target heat sourcein the monitoring scene; triggering a high definition camera, and rotating the holder according to the position coordinates of the target heat source, so that the target object is always located at the video central points of the thermal infrared imager and the high definition camera, and then the high definition camera tracks the target heat source and records a high definition video stream, wherein both of the thermal infrared imager and the high definition camera are installed on the holder. The invention further discloses an electronic device, a storage medium and a heat source tracking system. By adoption of the heat source tracking method disclosed by the invention, the defects of heat source tracking based on the high definition camera in the prior art are solved.
Owner:GUANGZHOU ZICHUAN ELECTRONICS TECH CO LTD
Electronic device directional audio-video capture
Disclosed herein is an apparatus. The apparatus includes a housing, electronic circuitry, and an audio-visual source tracking system. The electronic circuitry is in the housing. The audio-visual source tracking system includes a first video camera and an array of microphones. The first video camera and the array of microphones are attached to the housing. The audio-visual source tracking system is configured to receive video information from the first video camera. The audio-visual source tracking system is configured to capture audio information from the array of microphones at least partially in response to the video information. The audio-visual source tracking system might include a second video camera that is attached to the housing, wherein the first and second video cameras together estimate the beam orientation of the array of microphones.
Owner:NOKIA TECHNOLOGLES OY
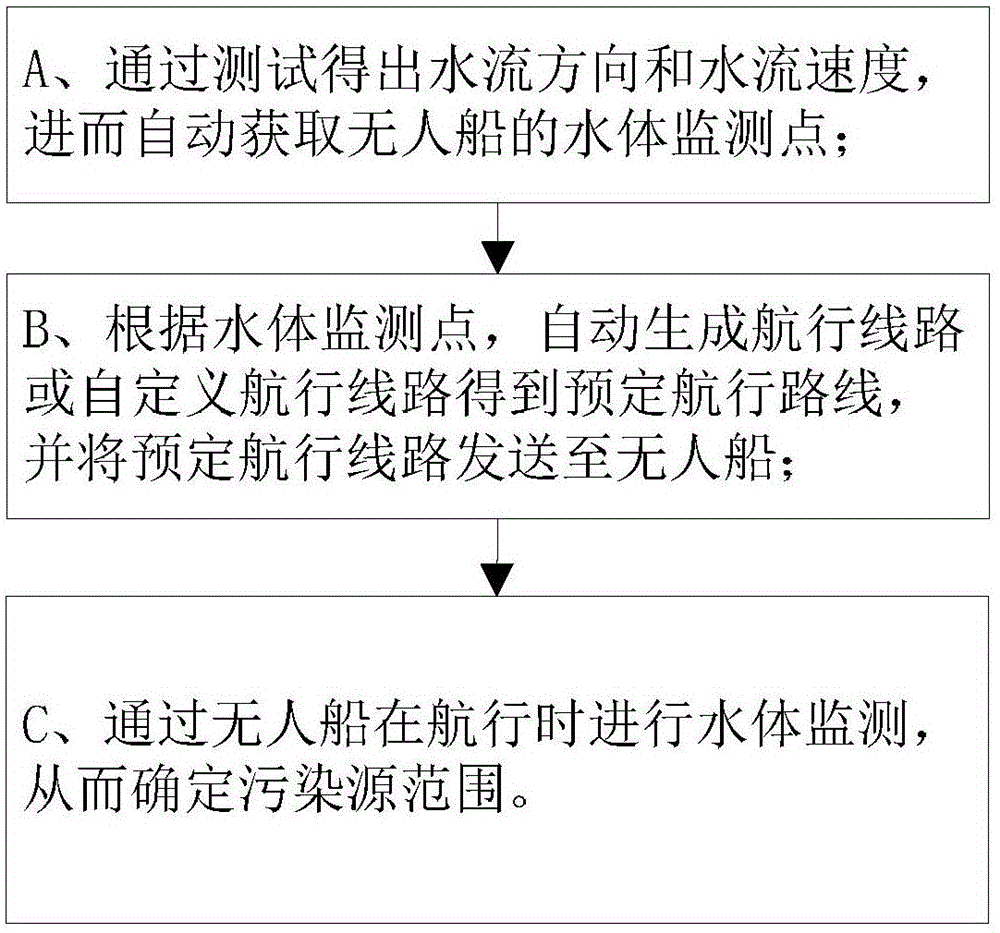
Pollution source tracking method and system used for unmanned ship
ActiveCN105137993AImprove securityReal-time monitoring of wind and wave conditionsPosition/course control in two dimensionsDiffusionWater velocity
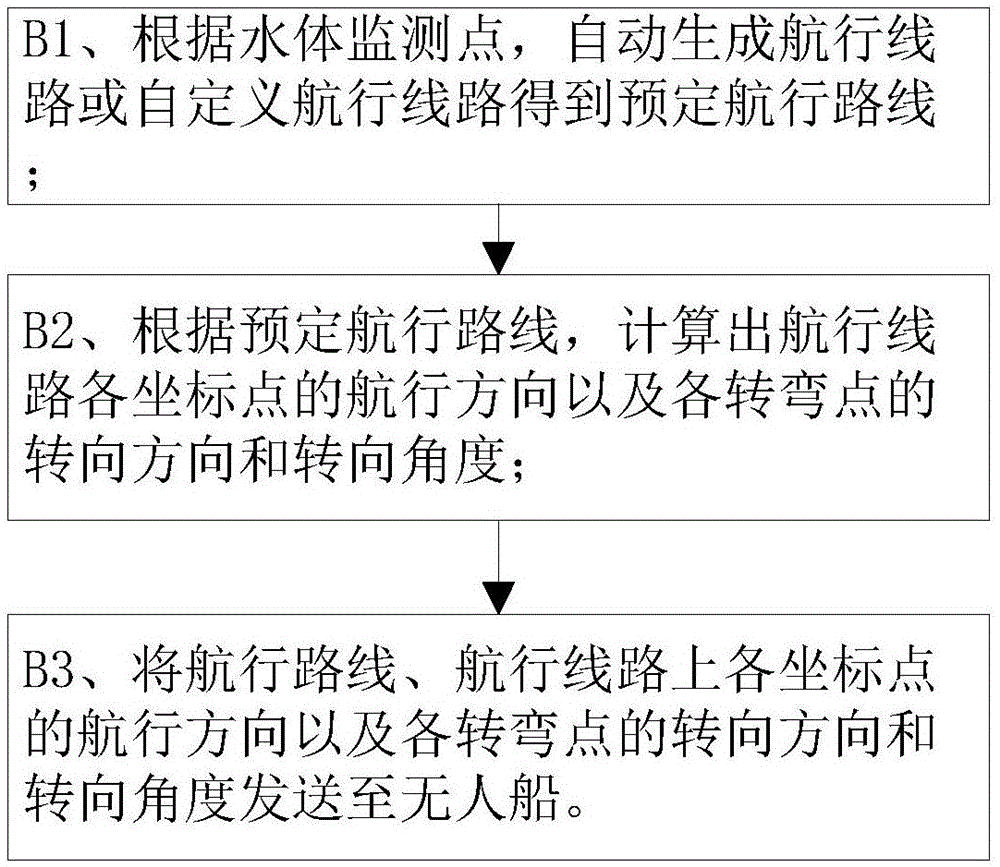
The invention discloses a pollution source tracking method and system used for an unmanned ship. The method includes the steps of: obtaining a water flow direction and water velocity by testing, and then automatically obtaining a water body monitoring point of the unmanned ship; according to the water body monitoring point, automatically generating a sailing route or self-defining a sailing route to obtain a predetermined sailing route; and performing water body monitoring when the unmanned ship sails, thereby determining a pollution source range. The system includes a monitoring point acquisition unit, a ship route formulation unit and a pollution source tracking unit. The pollution source tracking method and system formulate the sailing route, and perform water body monitoring when the unmanned ship sails, thereby determining the pollution source range, so that the diffusion degree and range of the pollution source can be tracked through the unmanned ship, and researchers can know the situation of the pollution source in time and take effective measures to the pollution source in time. The pollution source tracking method and system can be widely applied to unmanned ship products.
Owner:中船古伽(浙江)科技有限公司
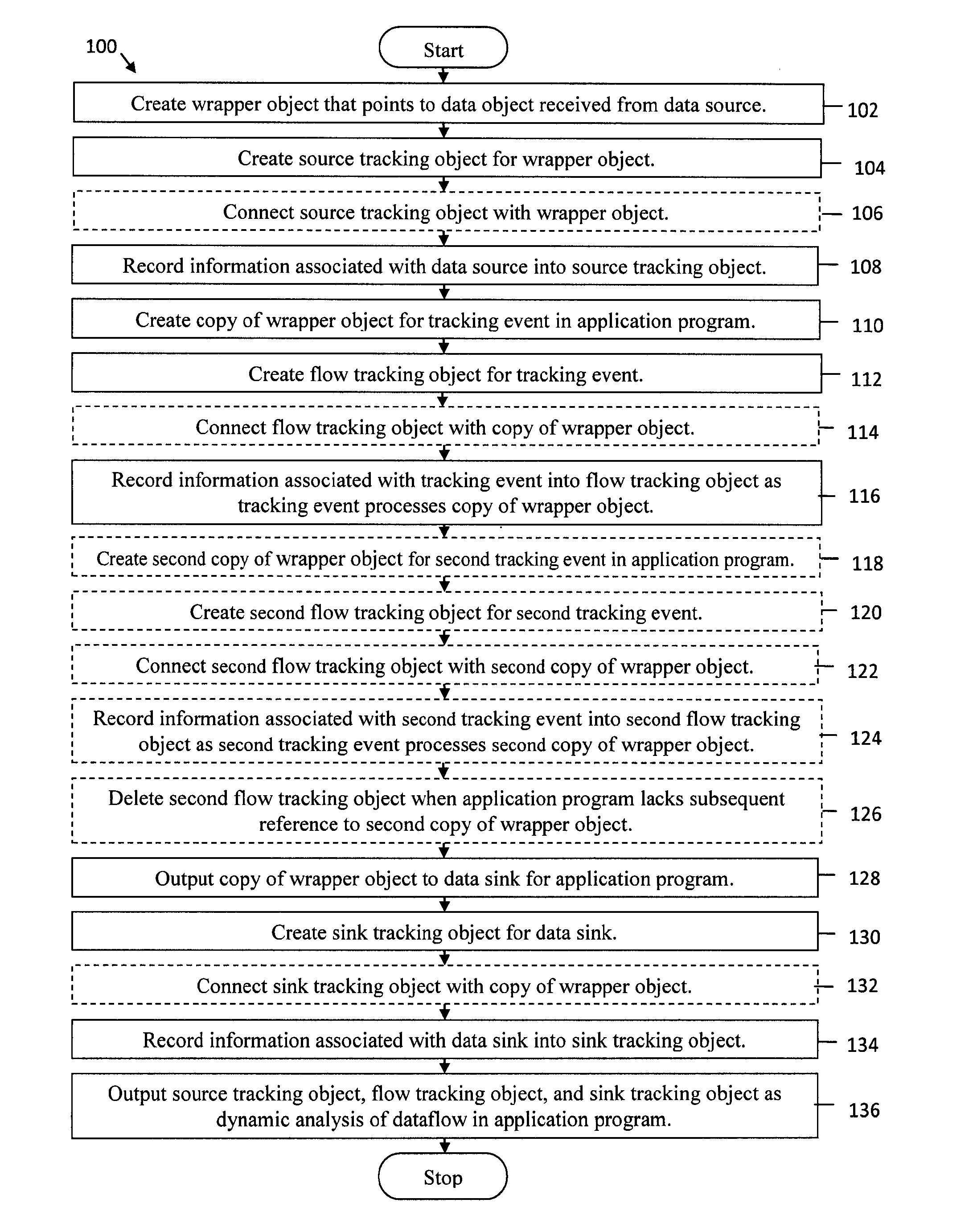
System and method for dynamic analysis wrapper objects for application dataflow
ActiveUS20140173742A1Improve performanceImprove efficiencyMemory loss protectionError detection/correctionData streamData source
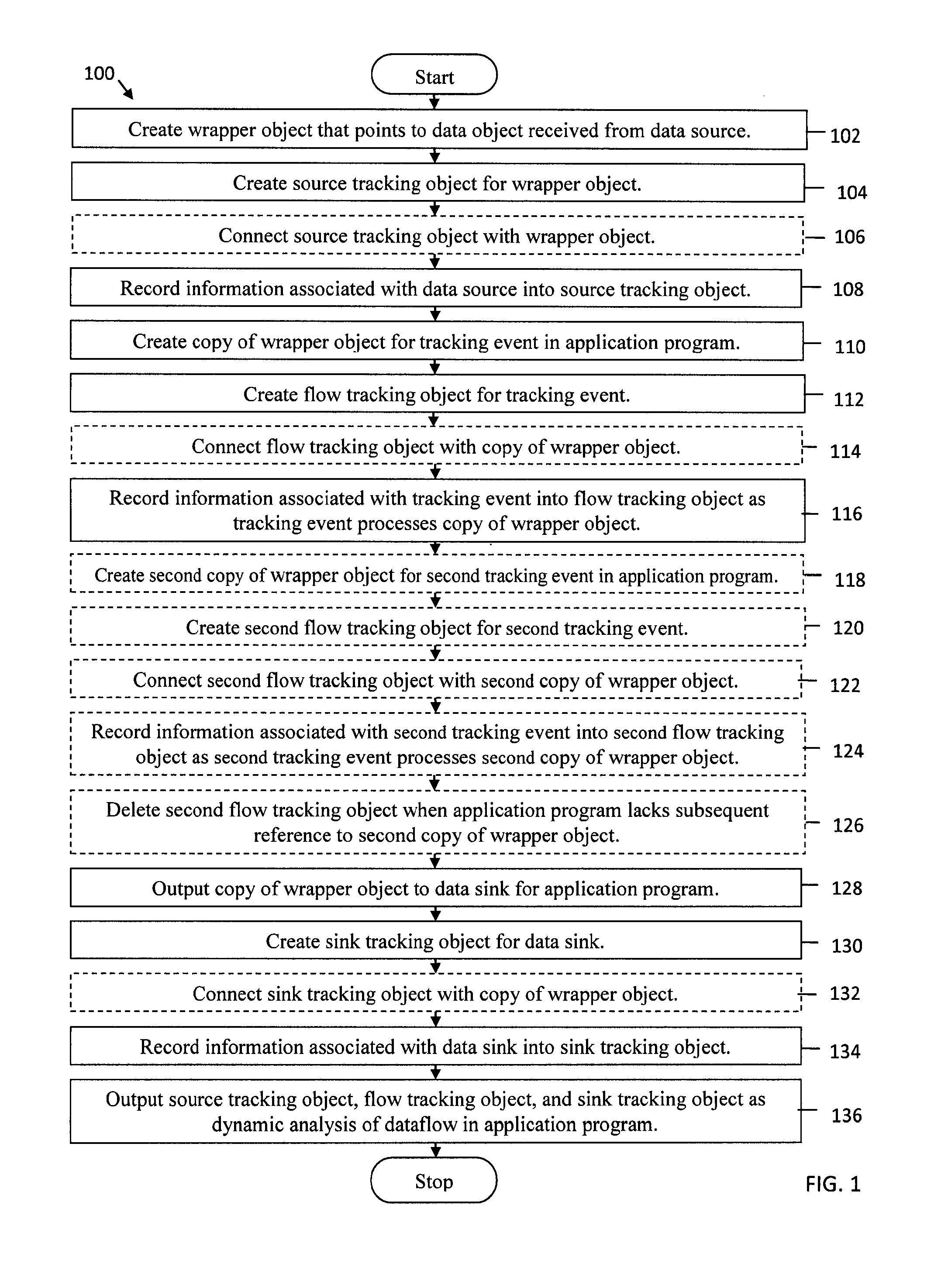
Systems and methods are provided for dynamic analysis wrapper objects for application dataflow. A system creates a wrapper object that points to a data object received from a data source, creates a source tracking object for the wrapper object, and records information associated with the data source into the source tracking object. The system creates a copy of the wrapper object for a tracking event in an application program, creates a flow tracking object for the tracking event, and records information associated with the tracking event into the flow tracking object as the tracking event processes the copy of the wrapper object. The system outputs the copy of the wrapper object to a data sink for the application program, creates a sink tracking object for the data sink, and records information associated with the data sink into the sink tracking object. The system outputs the source tracking object, the flow tracking object, and the sink tracking object as dynamic analysis of dataflow in the application program.
Owner:SALESFORCE COM INC
Dynamic analysis interpreter modification for application dataflow
ActiveUS20150121533A1Improve performanceImprove efficiencyMemory loss protectionError detection/correctionData sourceDataflow
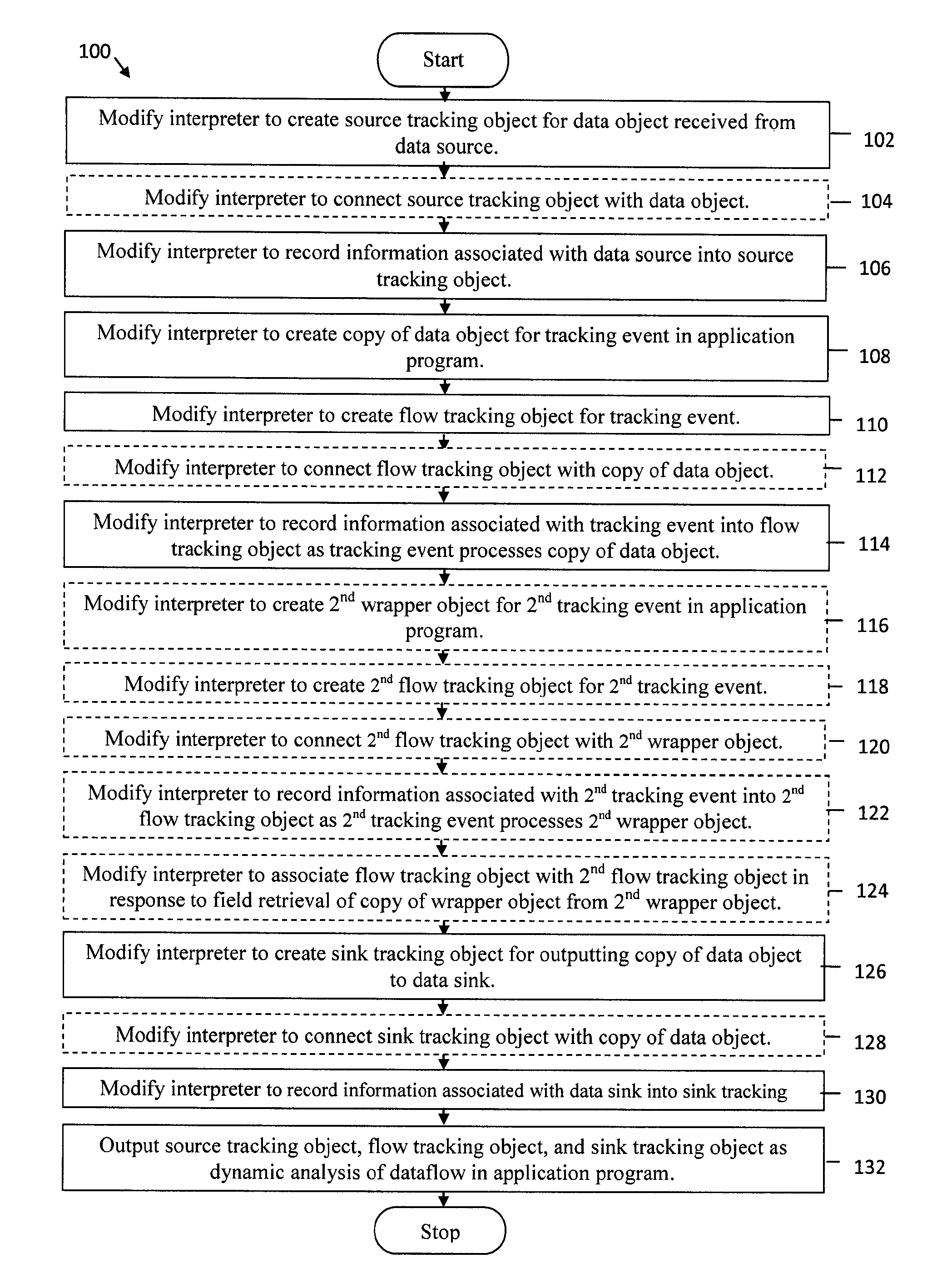
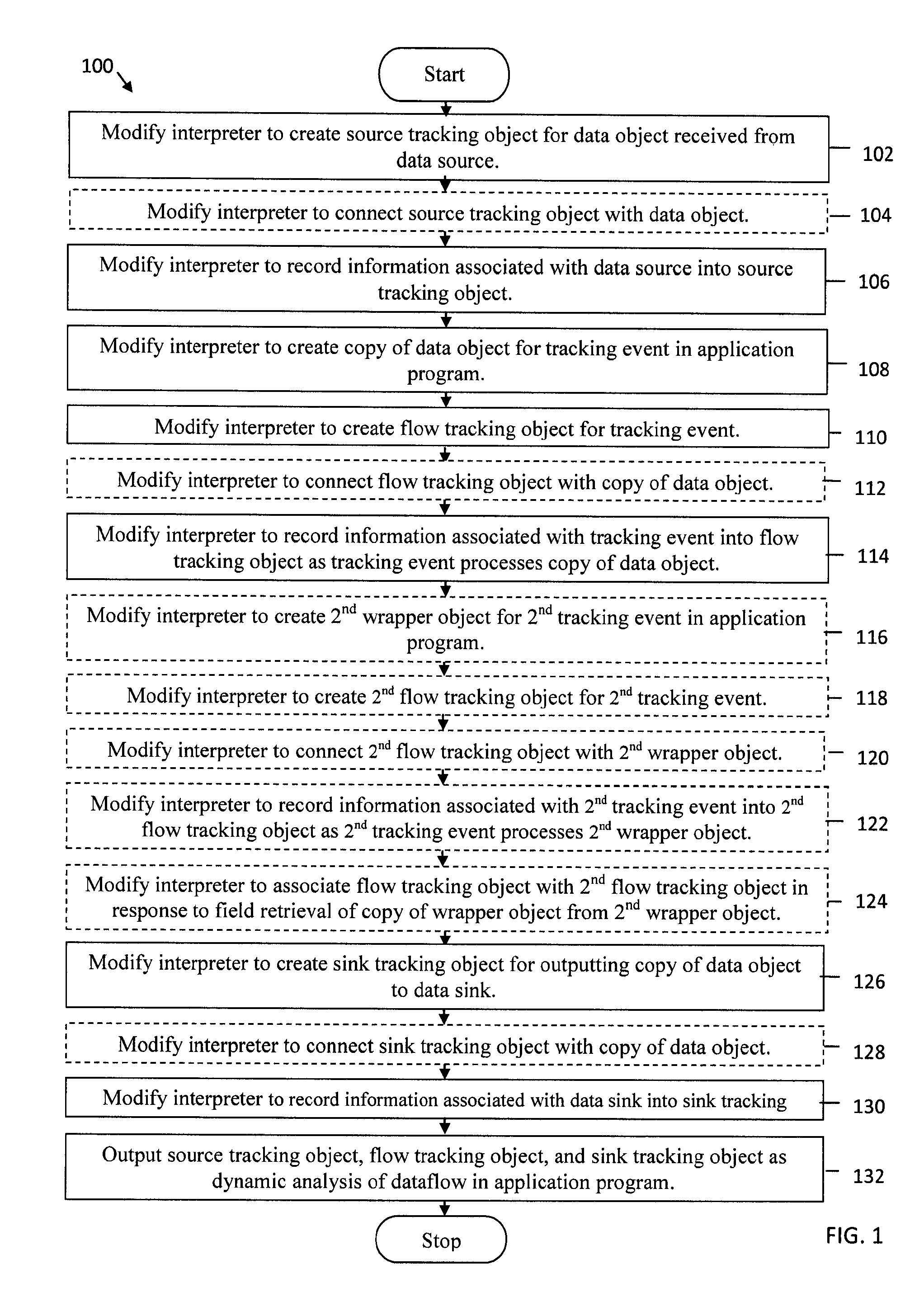
An interpreter is modified to create a source tracking object for a data object received from a data source and to record information associated with the data source into the source tracking object. The interpreter is modified to create a copy of the data object for a tracking event in an application program, to create a flow tracking object for the tracking event, and to record information associated with the tracking event into the flow tracking object as the tracking event processes the copy of the data object. The interpreter is modified to create a sink tracking object for outputting the copy of the data object to a data sink and to record information associated with the data sink into the sink tracking object. The source tracking object, the flow tracking object, and the sink tracking object are output as dynamic analysis of dataflow in the application program.
Owner:SALESFORCE COM INC
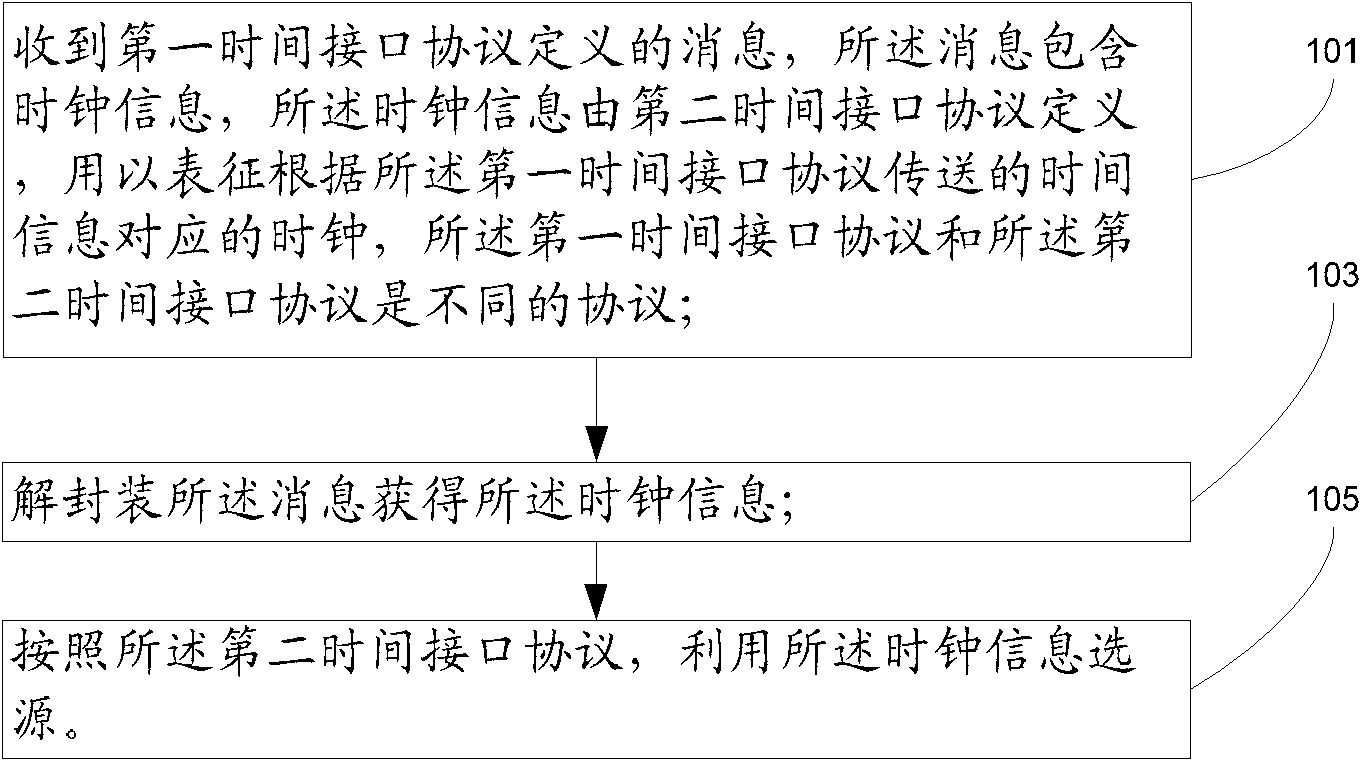
Method, device and system for processing clock information
ActiveCN102130736AReduce the possibility of tracking loopsReduce configuration workloadTime-division multiplexSynchronising arrangementTime informationInterface protocol
The invention discloses a method, device and system for processing clock information. The method comprises the following steps of: receiving a message defined by a first time interface protocol, wherein the message comprises clock information which is defined by a second time interface protocol and used for indicating a clock corresponding to the time information transmitted by the first time interface protocol, and the first time interface protocol is different from the second time interface protocol; performing de-capsulation on the message to obtain the time information; and selecting a source by using the time information according to the second time interface protocol. By adopting the embodiment of the invention, the configuration work amount and the configuration technical requirement can be lowered, and the probability of clock source tracking looping is lowered by performing uniform source selection on clocks including the clock.
Owner:汕头市丽盛实业有限公司
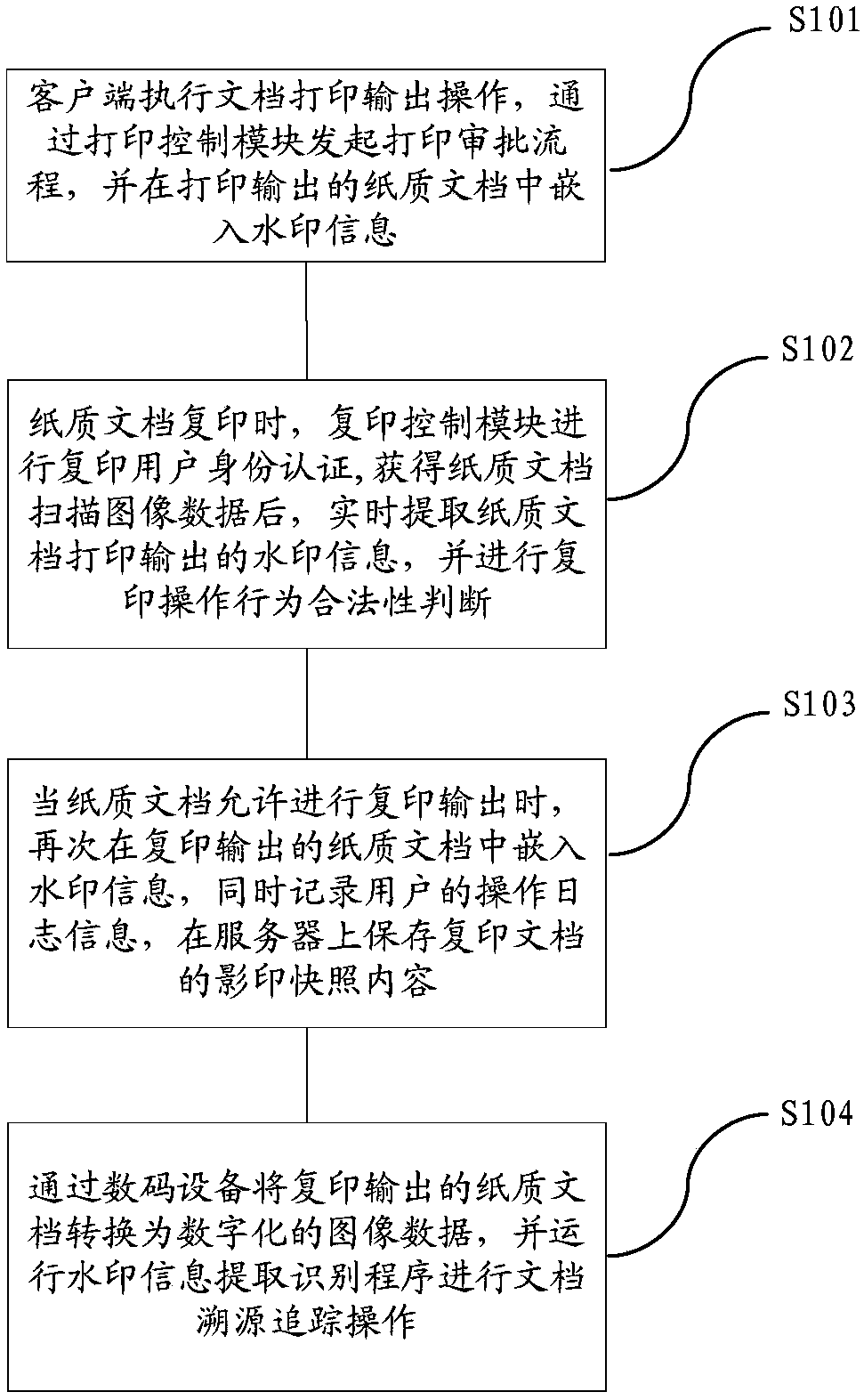
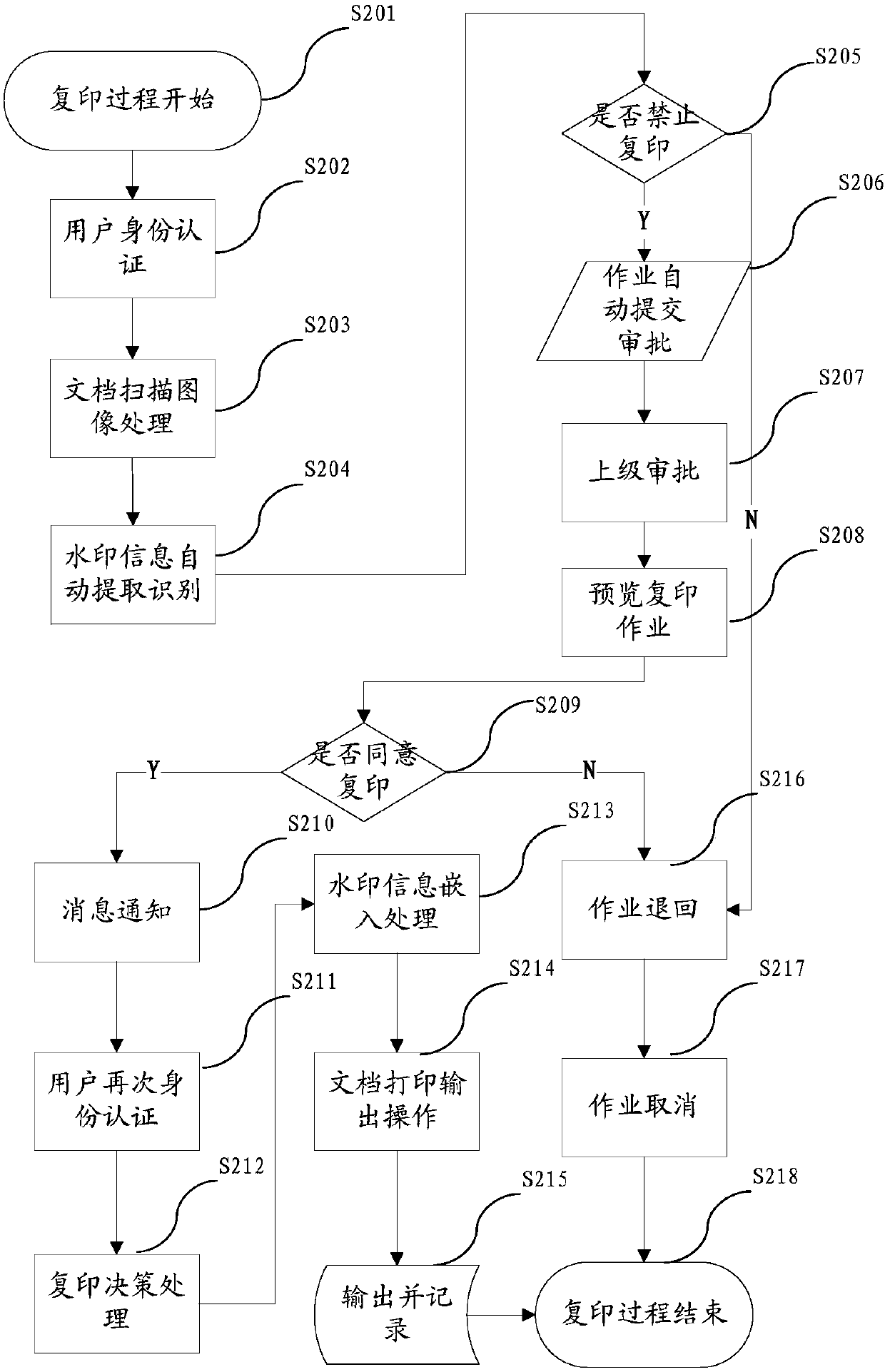
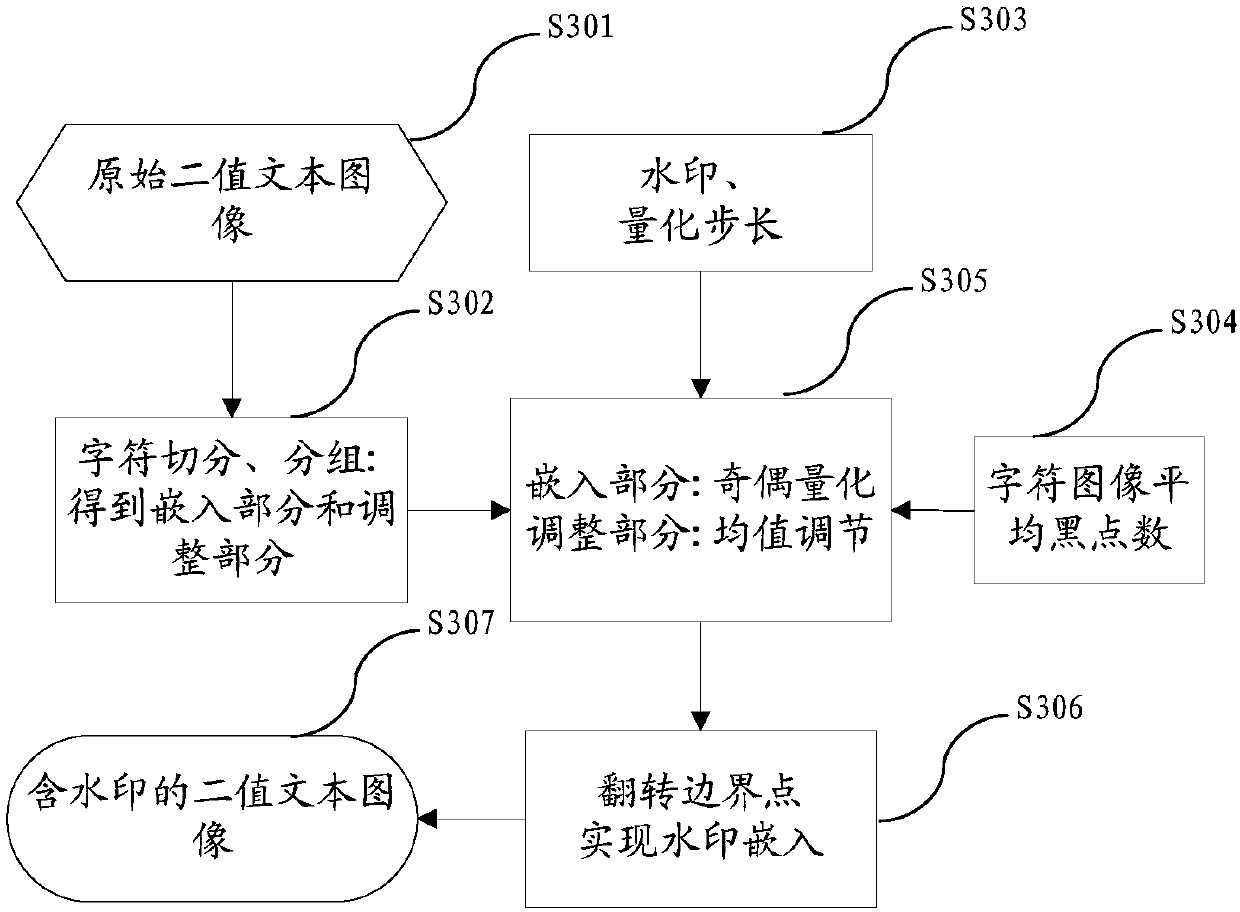
Method and device for safety control and source-tracing tracking of paper document
ActiveCN107066844AReduce the Risk of ConfidentialityReduce Human Intervention FactorsProgram/content distribution protectionDigital output to print unitsSafety controlCopy control
The invention relates to a method and device for safety control and source-tracing tracking of a paper document. The method comprises the steps that (1) a client side inserts watermark information in the printed and output paper document by a printing control module; (2) when the printed paper document is copied, copying user identity authentication will be conducted by a copy control module, a user obtains scanning image data of the paper document after passing the identity authentication, the watermark information inserted into the paper document is extracted in real time, and then legality of a copy operation behavior is judged; (3) when the copy operation behavior of the paper document is judged to be legal, the watermark information will be inserted into the copied and output paper document once again; and (4) the copied and output paper document is converted into digital image data by digital equipment, and a watermark information extraction and recognition program is conducted for a document source-tracing tracking operation. According to the invention, technical puzzles in safety control output, source-tracking tracking of secrete divulgence and so forth during whole processes of paper document printing and copying can be solved uniformly.
Owner:李晓妮
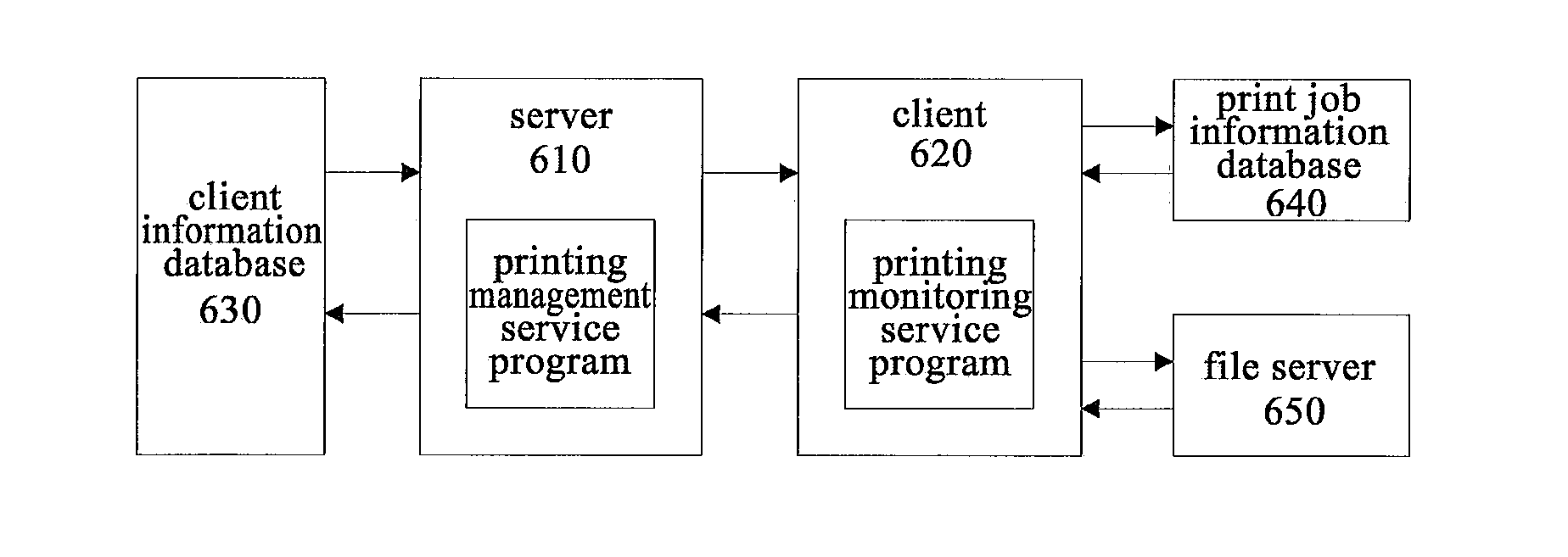
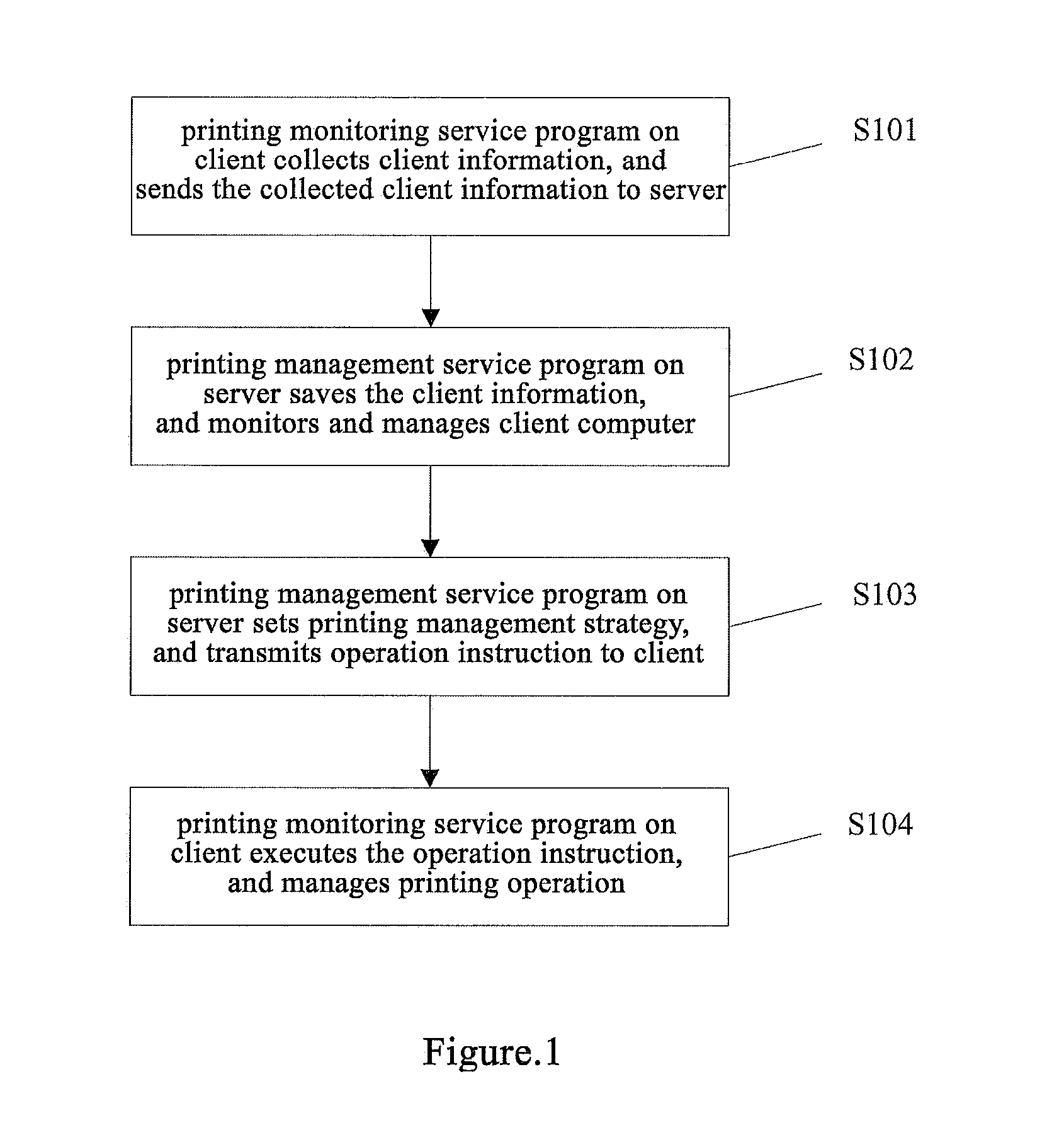
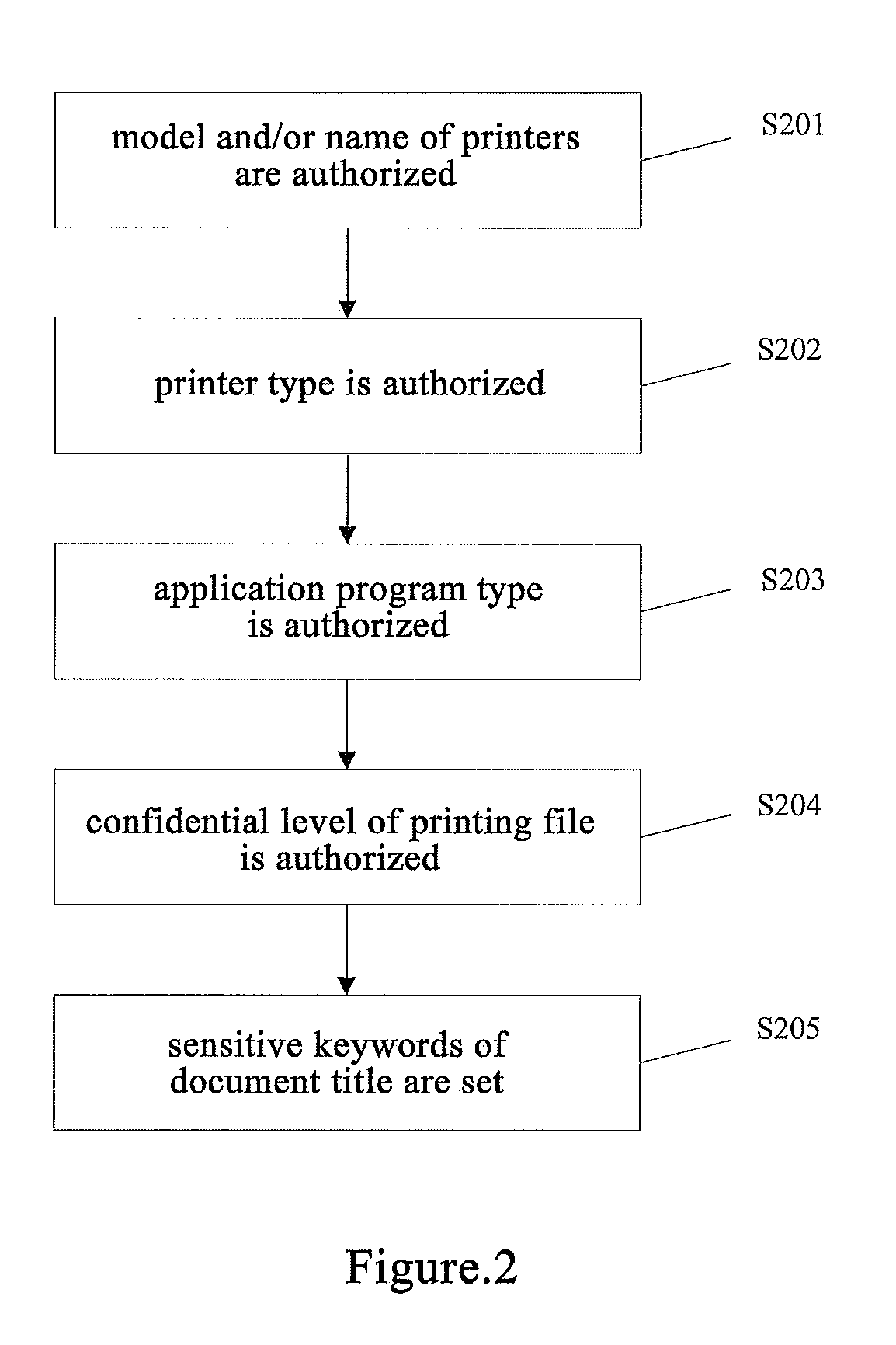
Method and system for document printing management and control, and document source tracking
InactiveUS20130335785A1Accurate and quicker and effective content auditingImprove securityVisual presentationTransmissionClient-sideServer-side
Disclosed is a method and system for document printing management and control and source tracking. A printing management service program runs at a server end. A printing monitoring service program runs at a client end. The printing management service program saves client end information, monitors and manages a client end computer, sets a printing management policy, and delivers operation instructions to the client end. The printing monitoring service program collects the client end information, sends the client end information to the server end, and executes the operation instruction.
Owner:NEW FOUNDER HLDG DEV LLC +3
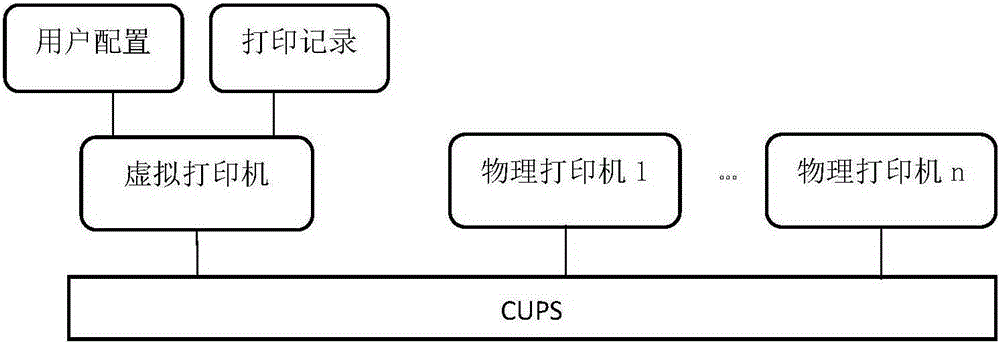
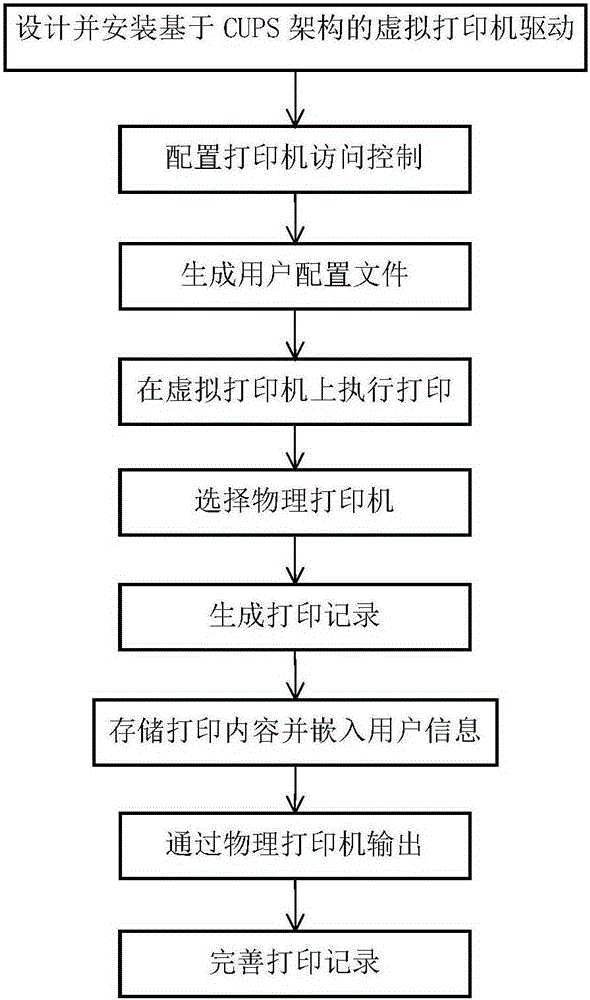
Printing management and control method based on CUPS framework
ActiveCN105183403AConvenient queryEasy to operateDigital output to print unitsUnixOperational system
The invention discloses a printing management and control method based on a CUPS framework. The printing management and control method includes the steps of firstly, designing and installing a virtual printer drive based on the CUPS framework; secondly, controlling the access to a virtual printer and a physical printer through a CUPS; thirdly, configuring the physical printer capable of being used by different users; fourthly, monitoring user printing operation; fifthly, selecting the physical printer by a user; sixthly, generating printing records; seventhly, storing printing content and embedding user information; eighthly, outputting the printing content through the physical printer; ninthly, completing the printing records. The method is suitable for all operation systems using the CUPS framework including the Unix system, the Linux operation system, the domestic operation system and the Mac system. By controlling the access to the physical printer, printing management is achieved, and basic data are provided for subsequent file source tracking and auditing by processing and storing the printing content.
Owner:XIDIAN UNIV
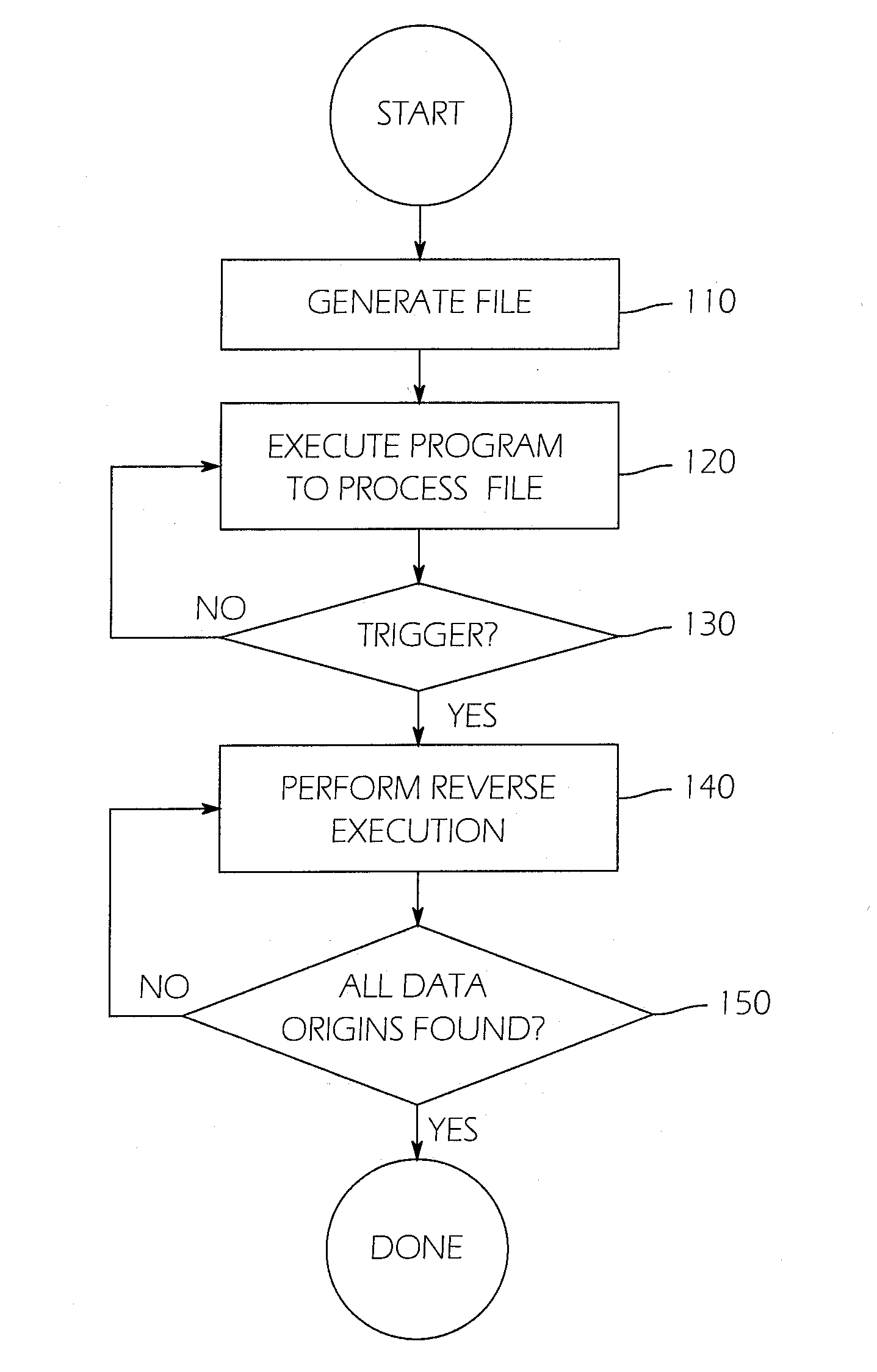
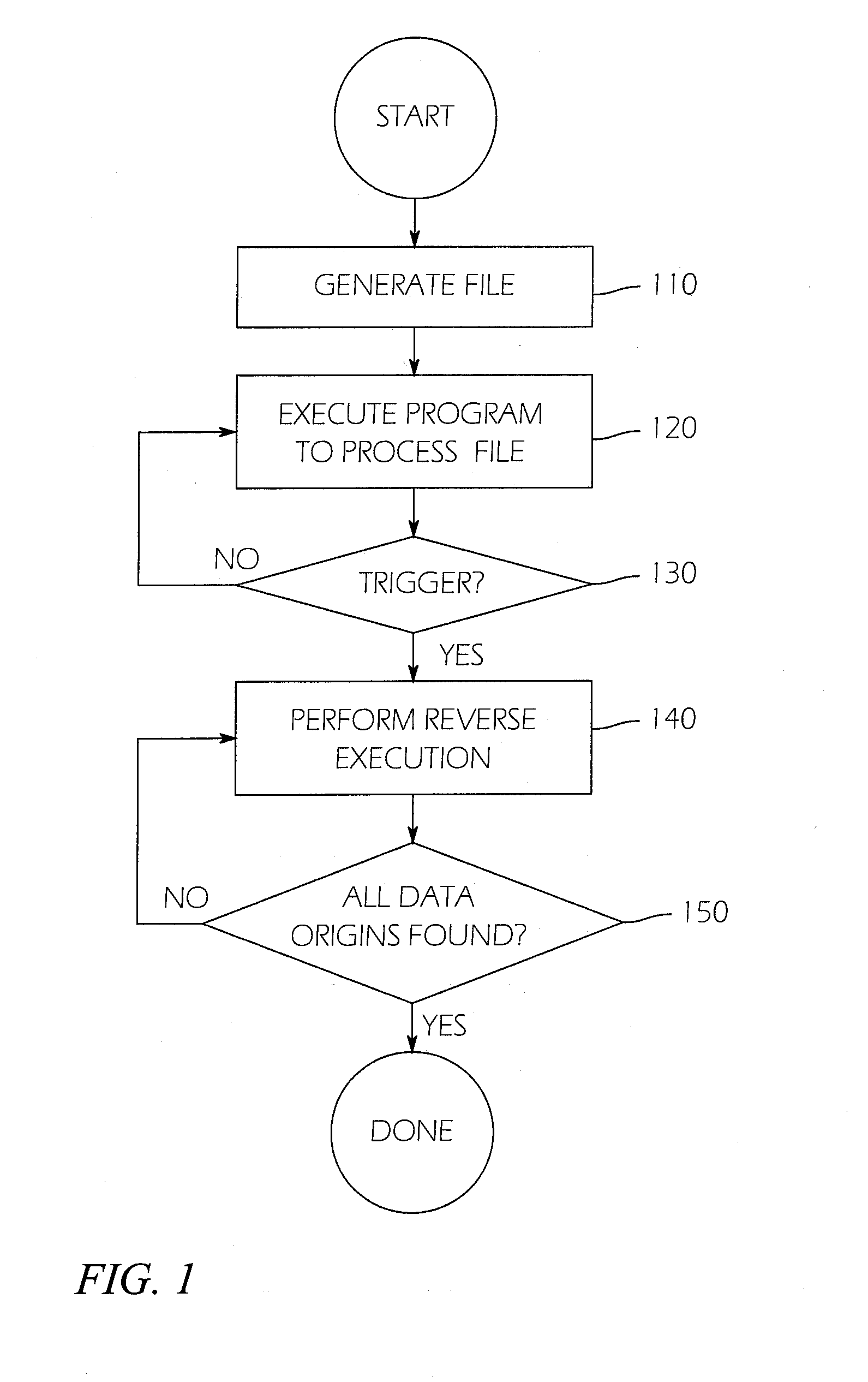
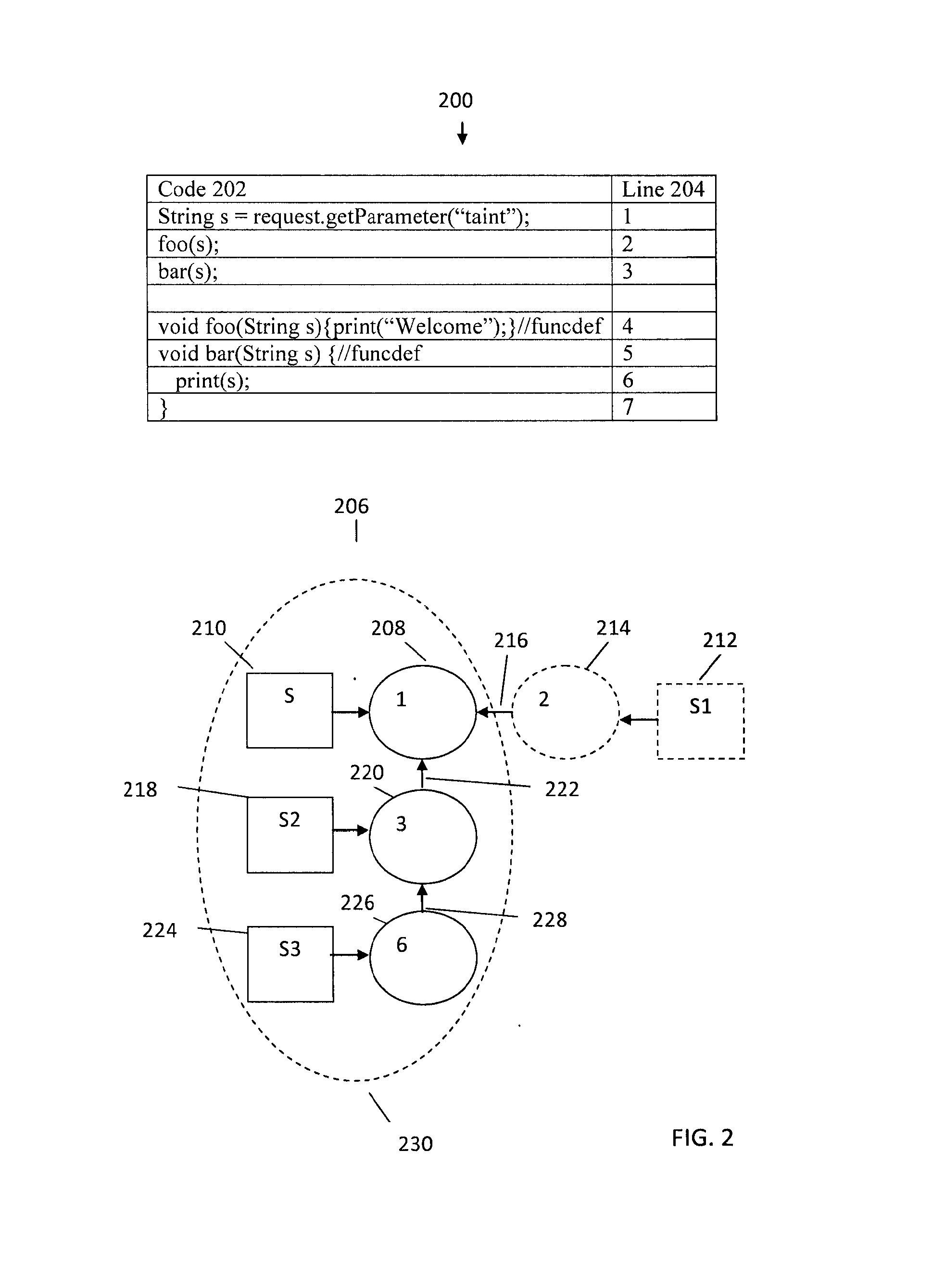
Automatic algorithm discovery using reverse dataflow analysis
ActiveUS20150047045A1Memory loss protectionError detection/correctionAutomated algorithmTheoretical computer science
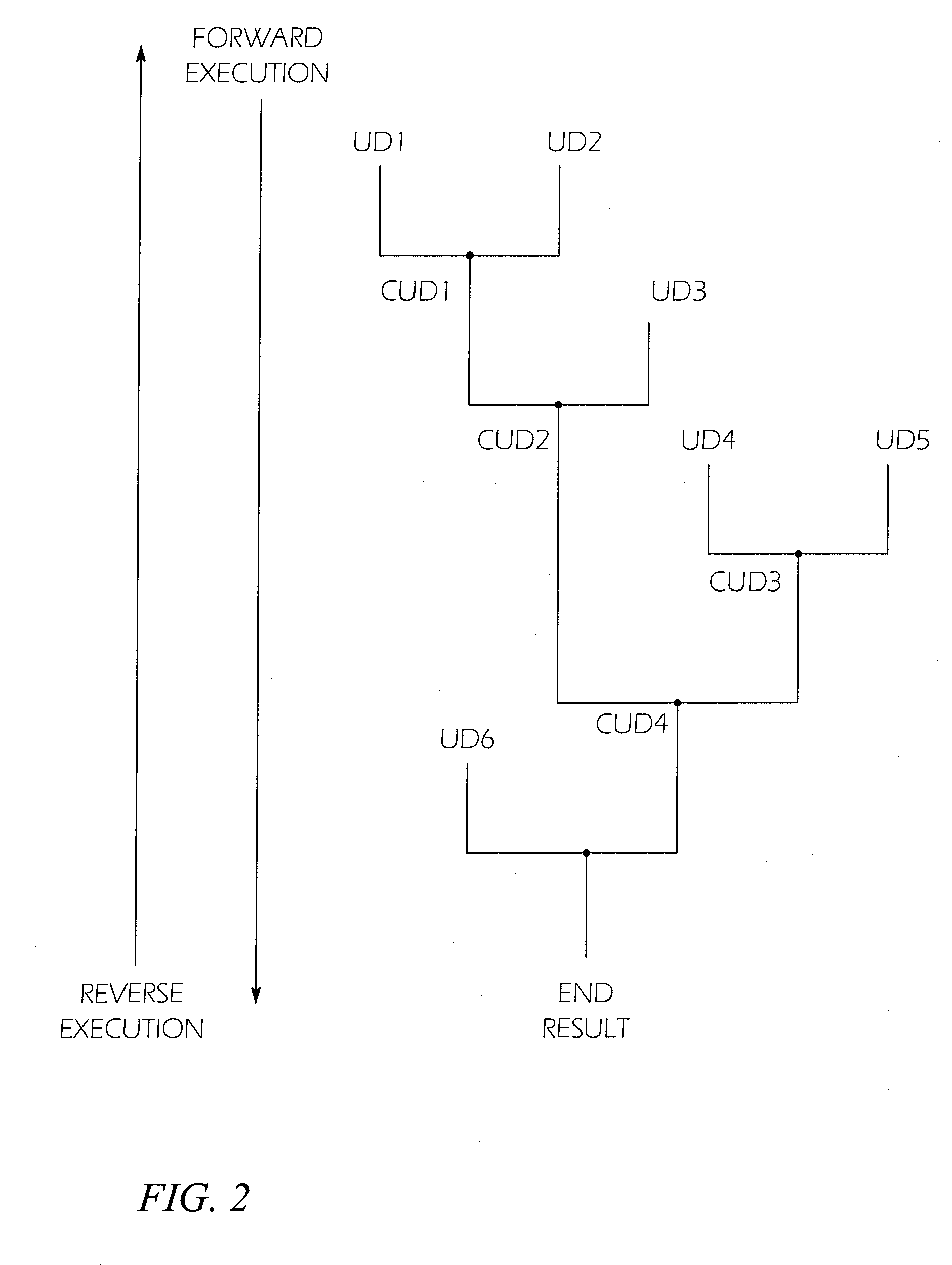
A system and method for finding vulnerabilities and tracing an end result associated with a vulnerability to its origins in user data. A user data source containing an ordered sequence of user data items may be a data file. In one embodiment the method for identifying, in the user data source, the origins of the end result, includes associating with each user data item a location identifier identifying the location of the user data item in the sequence of user data items executing instructions with a virtual machine, associating with each result the location identifier of the data item when one argument is a user data item and a tag when more than one argument is a user data item. This process may be continued until the end result is obtained. Subsequently, the method may include stepping through instructions with the virtual machine in reverse order, to tracing the origins of the end result to each of the user data items contributing to the result.
Owner:RAYTHEON CO
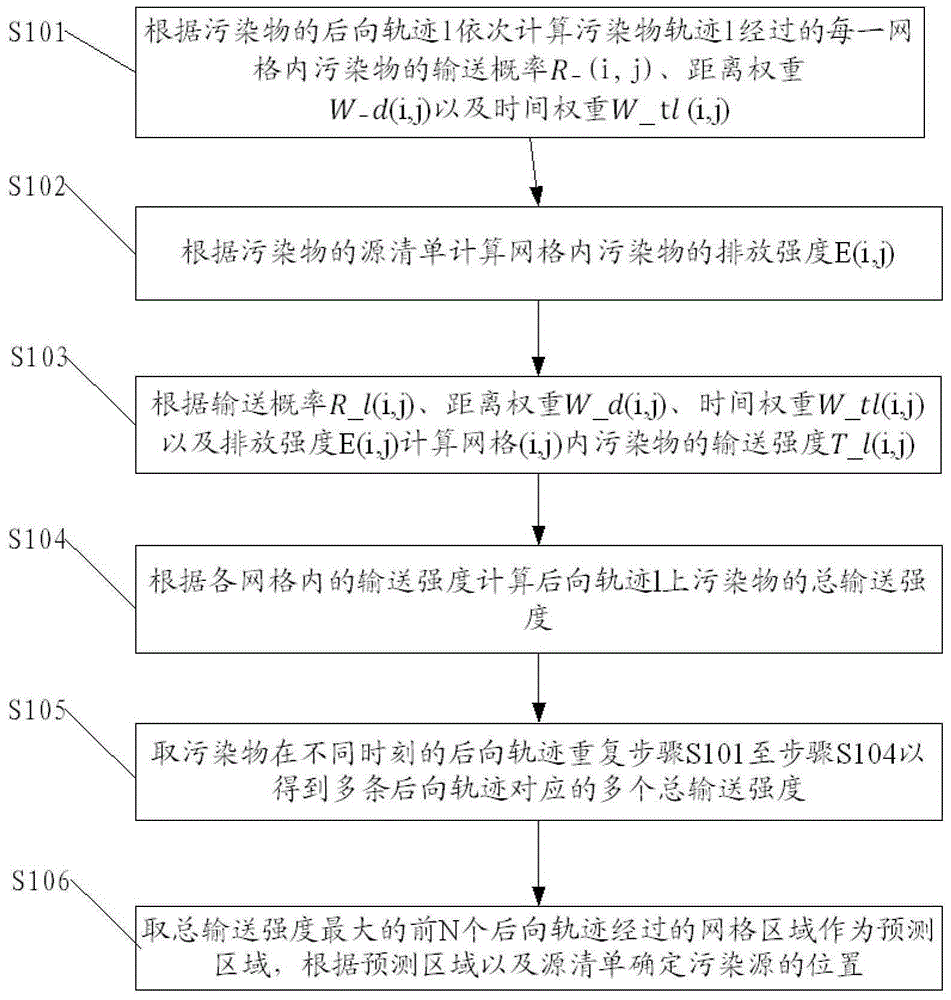
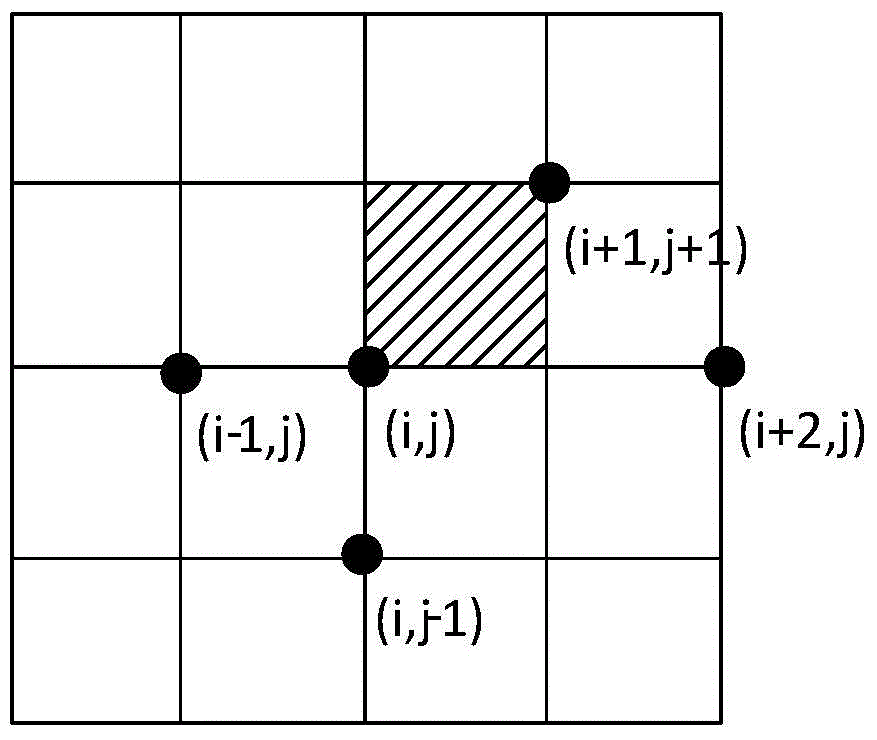
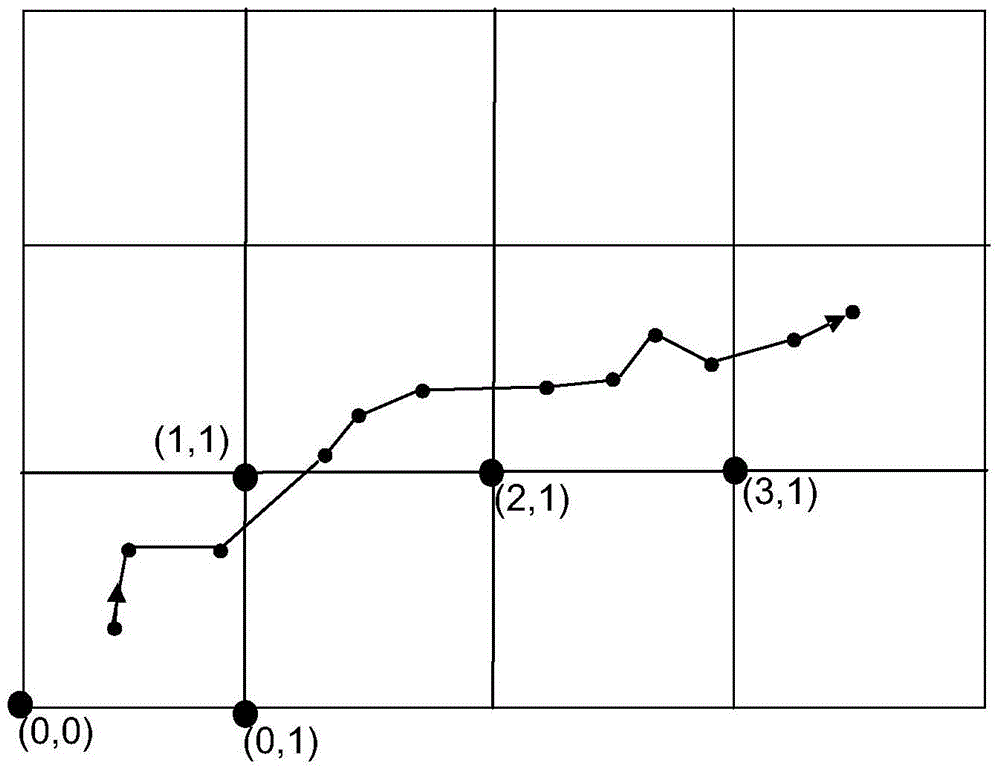
Pollution source tracking method based on backward trajectory and system thereof
ActiveCN104702685ARealize location trackingThe result is accurateTransmissionLocation trackingAir pollution
The invention discloses a pollution source tracking method based on a backward trajectory. The method comprises the steps: S1, calculating the conveying probability, distance weight and time weight of a pollutant in each grid which is passed by the backward trajectory according to the backward trajectory of the pollutants; S2, calculating the conveying strength of the pollutants in the grids in accordance with the conveying probability, distance weight, time weight and discharge intensity; S4, calculating the total conveying intensity of the pollutants on the backward trajectory according to the conveying intensities of all grids; S5, repeating a plurality of backward trajectories to repeat the steps S1 to S4 so as to obtain a plurality of total conveying intensities; and S6, taking grid area with maximum total conveying intensity which the front N backward trajectories are passed as a prediction area, and the geographic position of the pollution source can be determined according to the prediction area and a source list. Compared with the prior art, the location tracking of the pollution source can be realized, and the important basis can be provided for solving an air pollution problem. Meanwhile, the invention discloses a pollution source tracking system based on the backward trajectory.
Owner:SUN YAT SEN UNIV +1
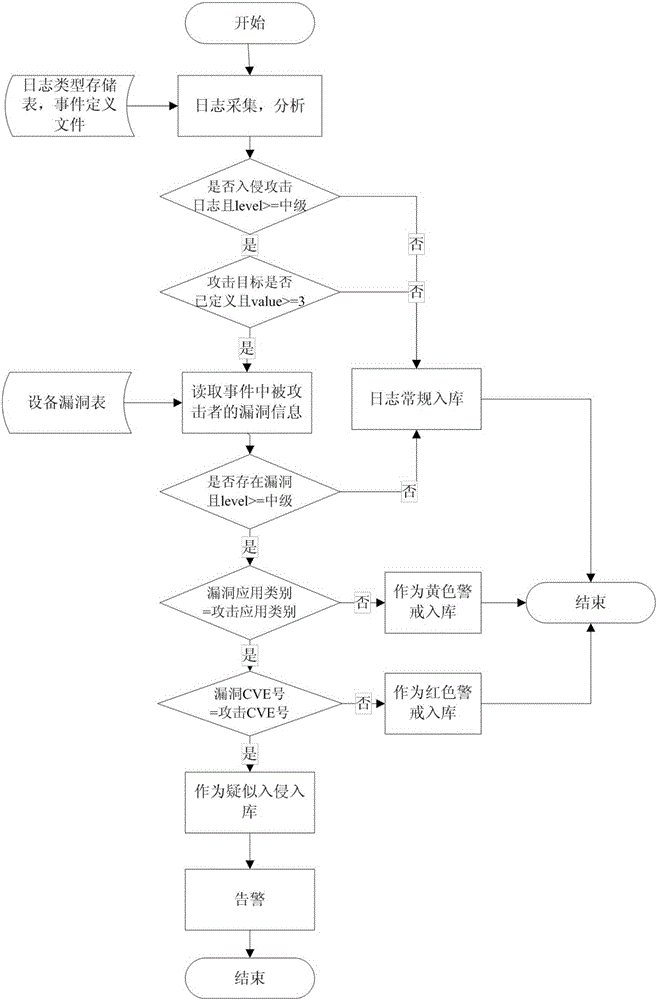
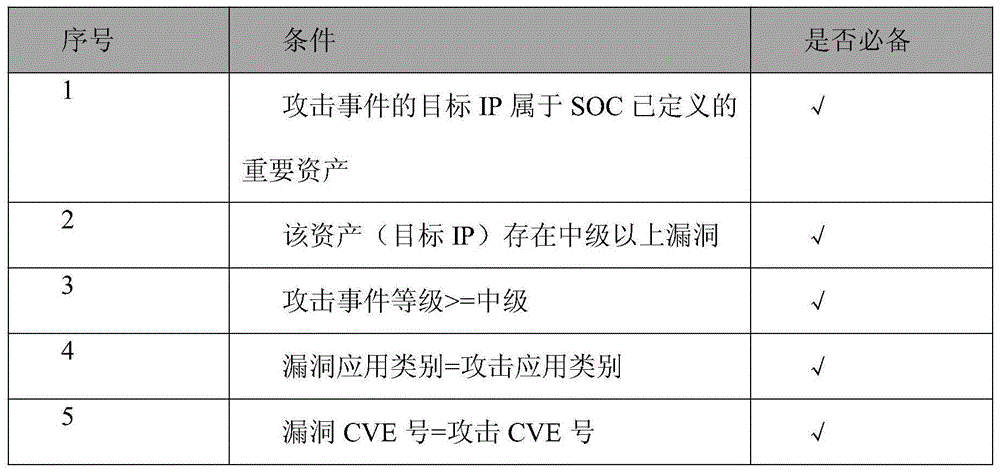
Hacker behavior discovery and analysis based on linkage of intrusion detection and vulnerability scanning
InactiveCN105227582AReduce false positivesAvoid subsequent attacksTransmissionVulnerability scanningLinkage concept
The invention discloses a method for hacker behavior discovery and analysis based on linkage of intrusion detection and vulnerability scanning. Through linkage of an intrusion detection technology and a vulnerability scanning technology, an attack is accurately positioned or a suspicious hacker behavior is discovered, so that the hacker intrusion behavior is timely intervened to avoid loss before the hacker intrusion behavior is successful, and furthermore, an attack source is analyzed and discovered through an attack source tracking technology, and the subsequent attack behavior of the attack source is prevented by utilizing the technologies, such as blacklist.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
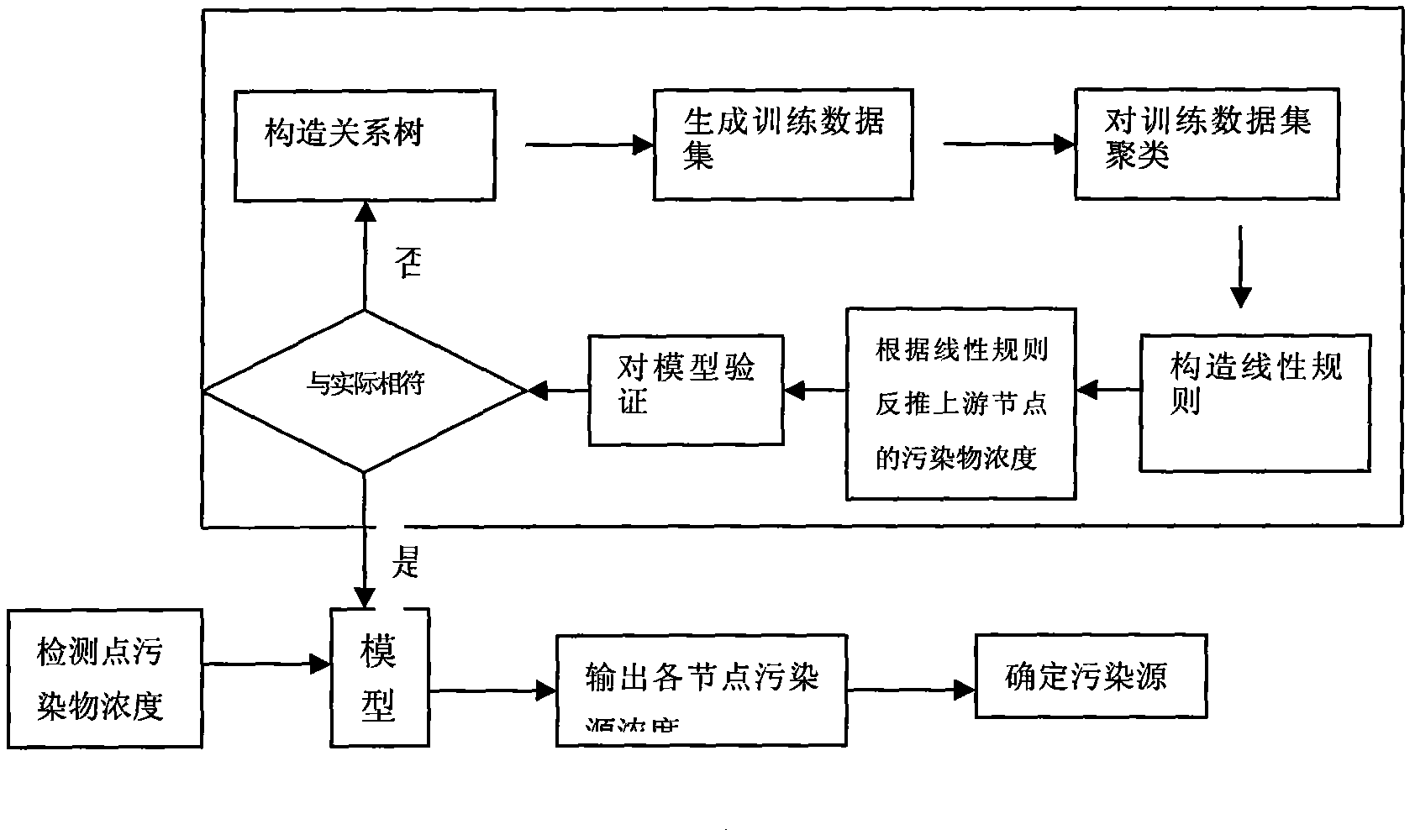
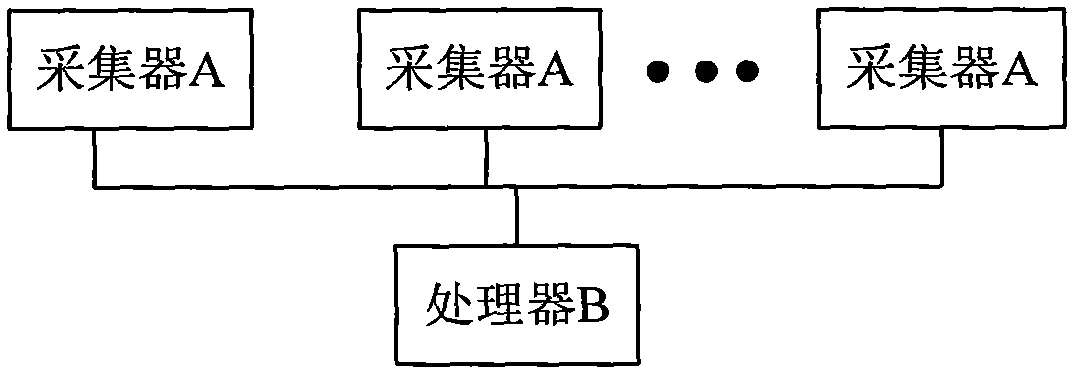
Pollution source tracking and positioning information processing method of sudden water supply pipe network pollution accident
InactiveCN102467605AAccurate and fast positioningQuickly and accurately determineSpecial data processing applicationsInformation processingMaximum Allowable Concentration
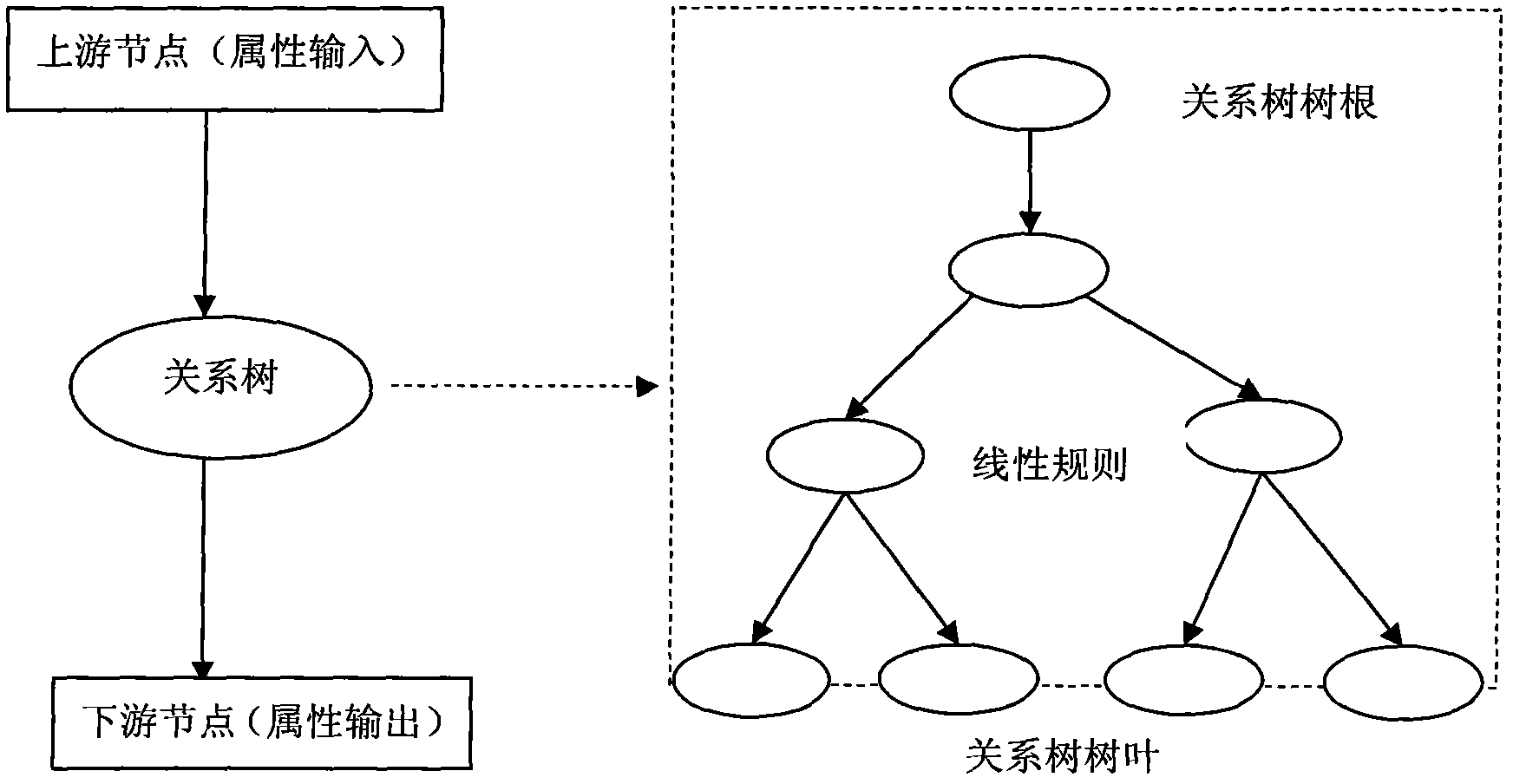
The invention relates to a pollution source tracking and positioning information processing method of a sudden water supply pipe network pollution accident, which comprises the following steps that: 1) acquisition devices acquire pollutant concentration information monitored by monitoring points and transmit the pollutant concentration information to a processor; 2) the processor works out the maximum pollutant concentration of all nodes in a pipe network and the occurrence time of the maximum pollutant concentration according to the linear rule model of a node relation tree, and by conducting solution step by step, the maximum pollutant concentration of all nodes in the pipe network and the occurrence time of the maximum pollutant concentration can be worked out; and 3) the processor judges a node with the highest pollutant concentration and determines the node to be a pollutant injection node. Compared with the prior art, the method has the advantages that the pollution resource in the water supply pipe network can be rapidly and accurately positioned and the like.
Owner:TONGJI UNIV
Unmanned ship used for water quality monitoring and pollution source tracking and pollution source tracking method
PendingCN108107176AAutomatic IdentificationAchieve early warningWaterborne vesselsGeneral water supply conservationWater qualitySolar cell
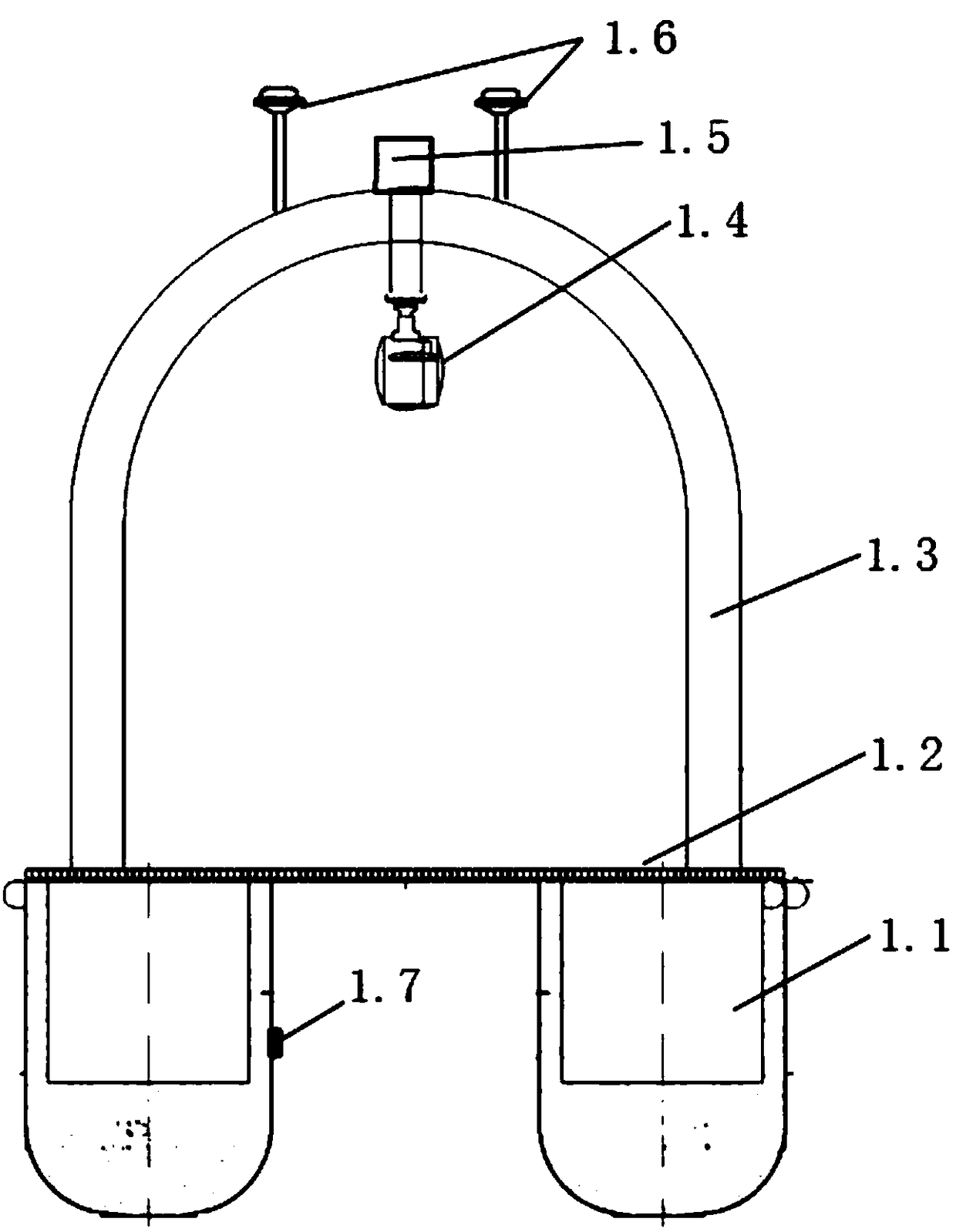
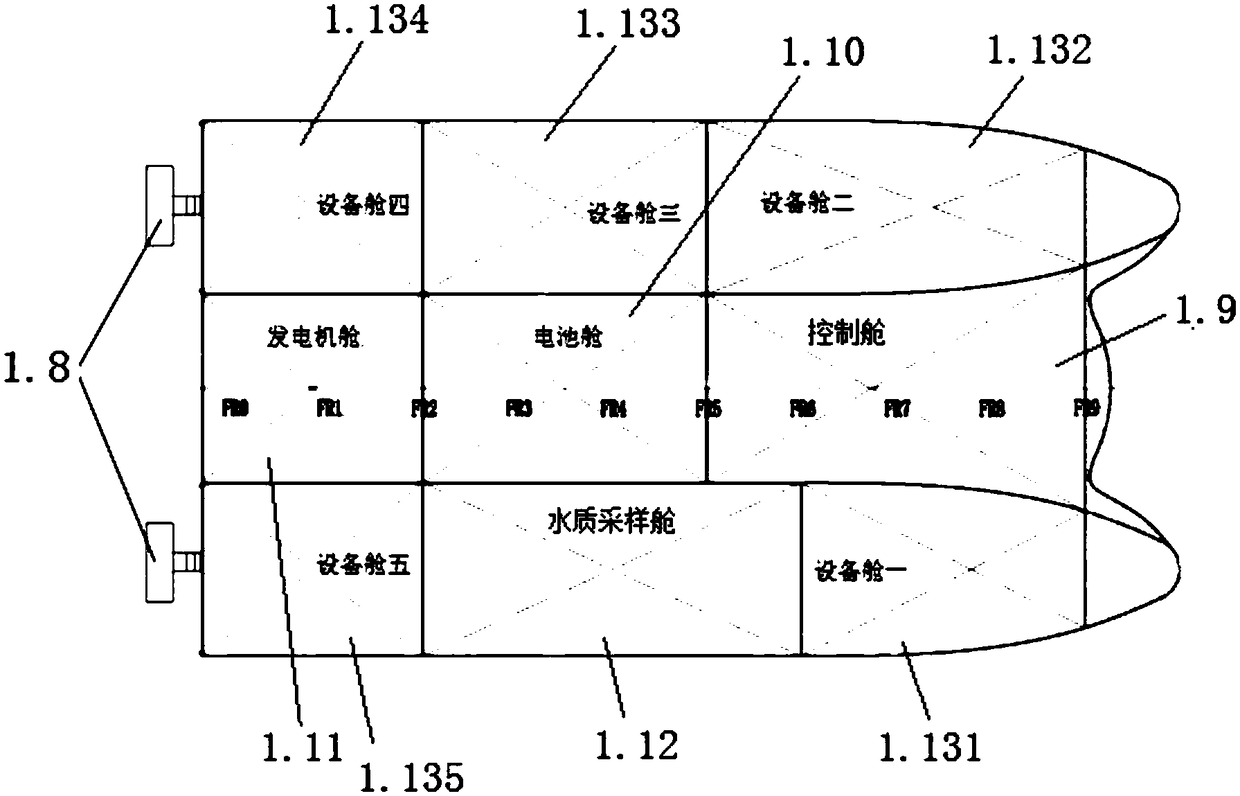
The invention discloses an unmanned ship used for water quality monitoring and pollution source tracking and a pollution source tracking method. The unmanned ship comprises a catamaran composed of twoclosed cabins and a connecting plate; a solar cell panel for charging lithium batteries is laid on the upper surface of the catamaran; a U-shaped equipment rack is arranged above the catamaran; a video camera, a radar and an antenna are fixedly arranged on the equipment rack; and a control cabin, a battery cabin, a generator cabin, a water quality sampling cabin and five equipment cabins for placing water quality monitoring instruments are arranged inside each of the two closed cabins respectively. The unmanned ship disclosed by the invention has the functions of tracking and tracing water pollution sources, the concentration field of pollutants inside water is detected through a full spectrum water quality analyzer due to the tracking and tracing functions, in combination with the turbulent model of the high Reynolds coefficient of a water flow, a Bayesian reasoning algorithm with the optimal vector of phi is adopted, and the unmanned ship is automatically controlled to cruise to thesource of the pollution source, so that the tracking and tracing of water pollution are realized.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
Method and apparatus for acoustic source tracking using a horizontal line array
An apparatus for processing passive acoustic signals received on a horizontal line array that were either emitted from an underwater object or echo returned from an object, is proposed to track the motion (bearing change and range change) of an object (target) relative to the receiver horizontal line array. Adaptive array processing for a moving object is biased for a moving source when the number of data samples is limited by the stationariness condition. Motion compensation can be carried out in the beam domain by beam shifting for a bearing changing object and frequency shifting for a range changing object. The method includes receiving acoustic signals from the target, determining the beam covariance matrices, determining the target bearing rate and range rate, processing the beam covariance matrices by compensating for the target motion, and producing a beam power plot versus time. Interference signal is suppressed when the interference source does not have the same motion (bearing and range rate) as the target. The method does not need detailed environmental acoustic information of the sound channel normally required to model the sound propagation.
Owner:USA AS REPRESENTED BY THE SEC OF THE NAVY THE
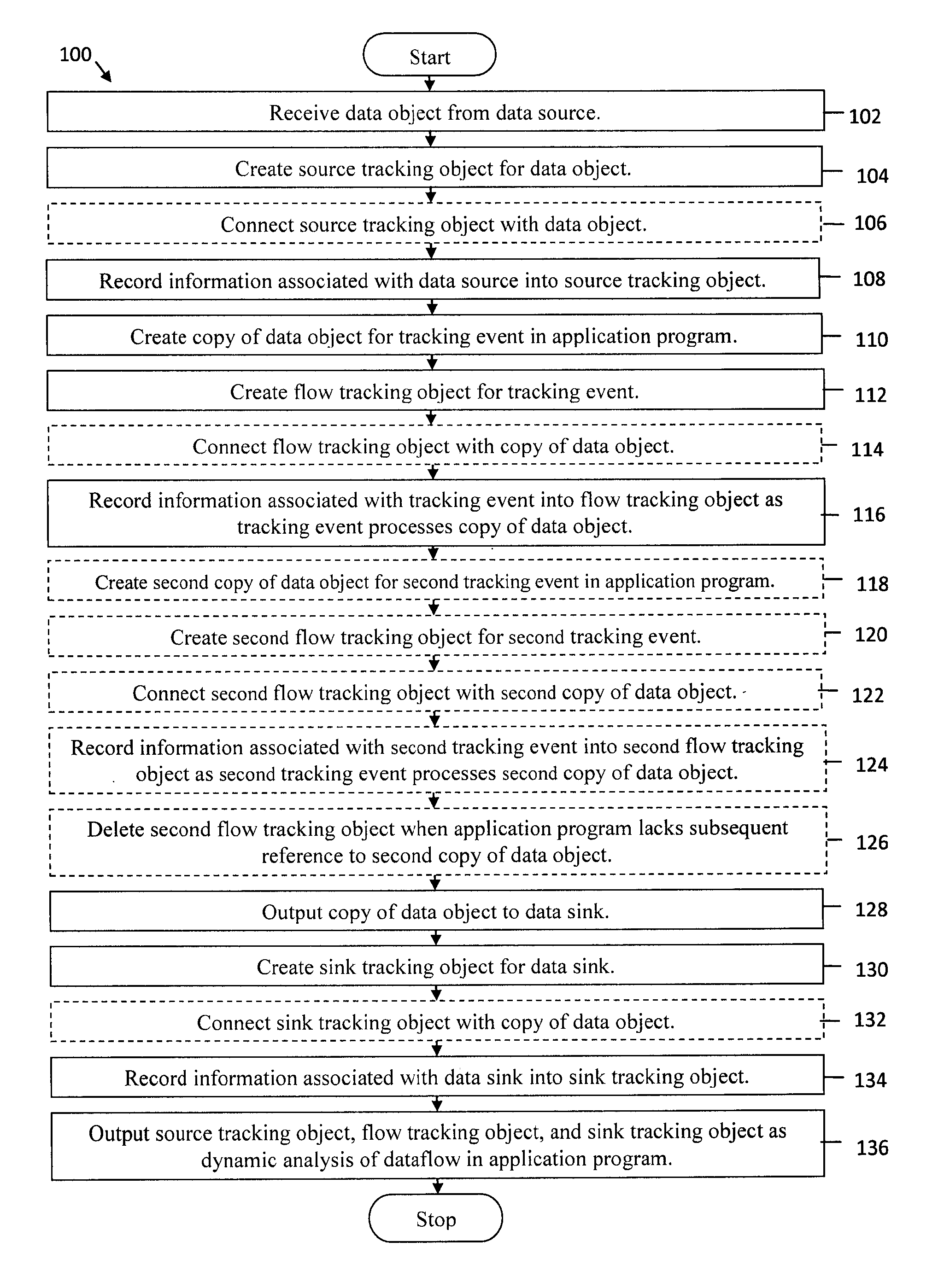
System and method for dynamic analysis tracking objects for application dataflow
ActiveUS20140173741A1Improve performanceImprove efficiencyMemory loss protectionError detection/correctionData streamData source
Systems and methods are provided for dynamic analysis tracking objects for application dataflow. A system receives a data object from a data source, creates a source tracking object for the data object, and records information associated with the data source into the source tracking object. The system creates a copy of the data object for a tracking event in the application program, creates a flow tracking object for the tracking event, and records information associated with the tracking event into the flow tracking object as the tracking event processes the copy of the data object. The system outputs the copy of the data object to a data sink, creates a sink tracking object for the data sink, and records information associated with the data sink into the sink tracking object. The system outputs the source tracking object, the flow tracking object, and the sink tracking object as dynamic analysis of dataflow in the application program.
Owner:SALESFORCE COM INC
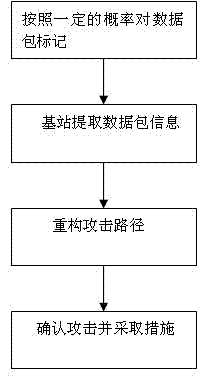
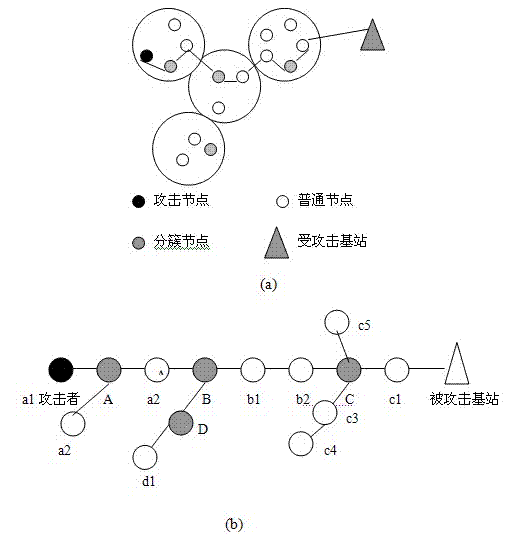
Method of tracking DDoS attack in wireless sensor network
InactiveCN103249177AFast and Efficient TrackingIncrease the burdenNetwork topologiesTransmissionAnti jammingWireless mesh network
The invention discloses a method of tracking DDoS (distributed denial of service) attack in the wireless sensor network. According to the method, data packets are marked, and source tracking is performed by utilizing the marked data packets, so as to identify malicious attack nodes. The marking method comprises the following steps: setting marking information (first, top, tail, start, end, distance) of six marking domains in the data packets, then marking cluster head node data packets and common node data packets, and discovering attack paths and proceeding accordingly through path reconstruction. The method has excellent convergence, reduces uncertainty of the attack source, and improves the anti-jamming capability.
Owner:CHANGZHOU UNIV
Microphone for audio source tracking
InactiveCN101449593ATelevision conference systemsTwo-way working systemsSound sourcesCommunications system
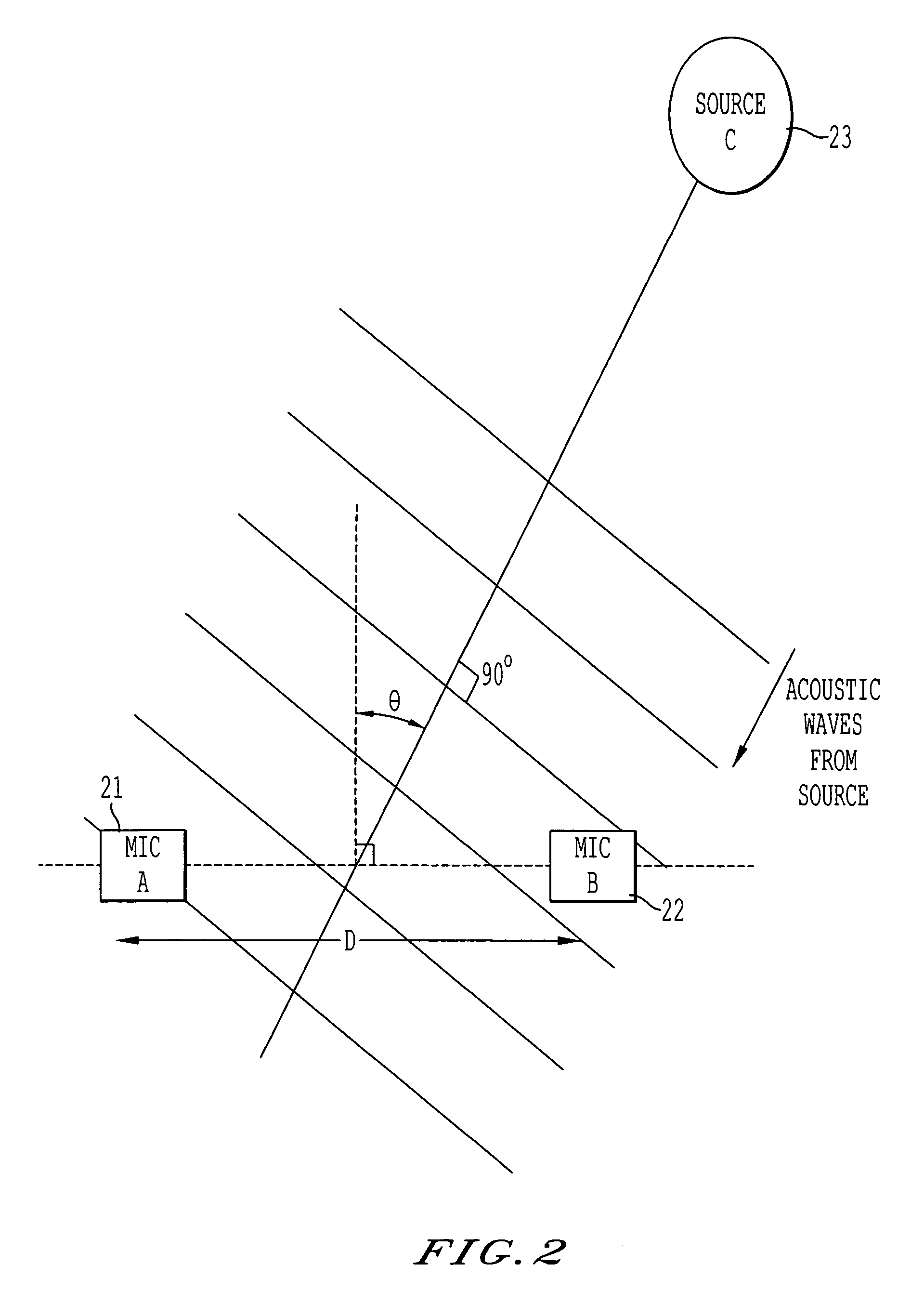
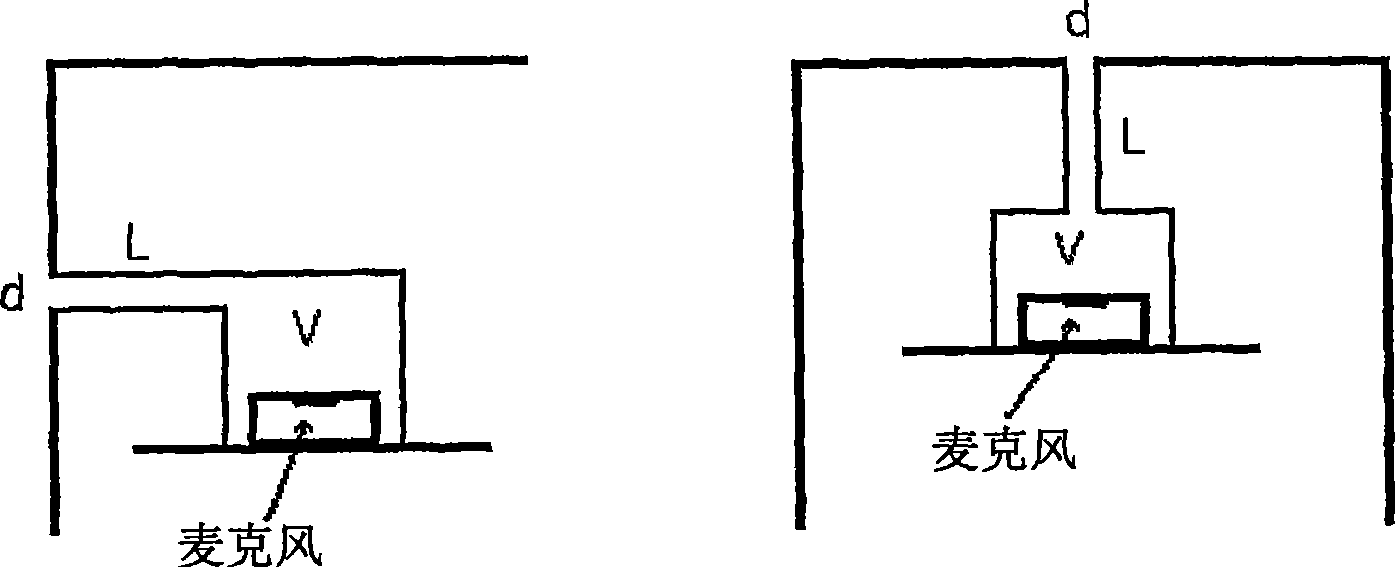
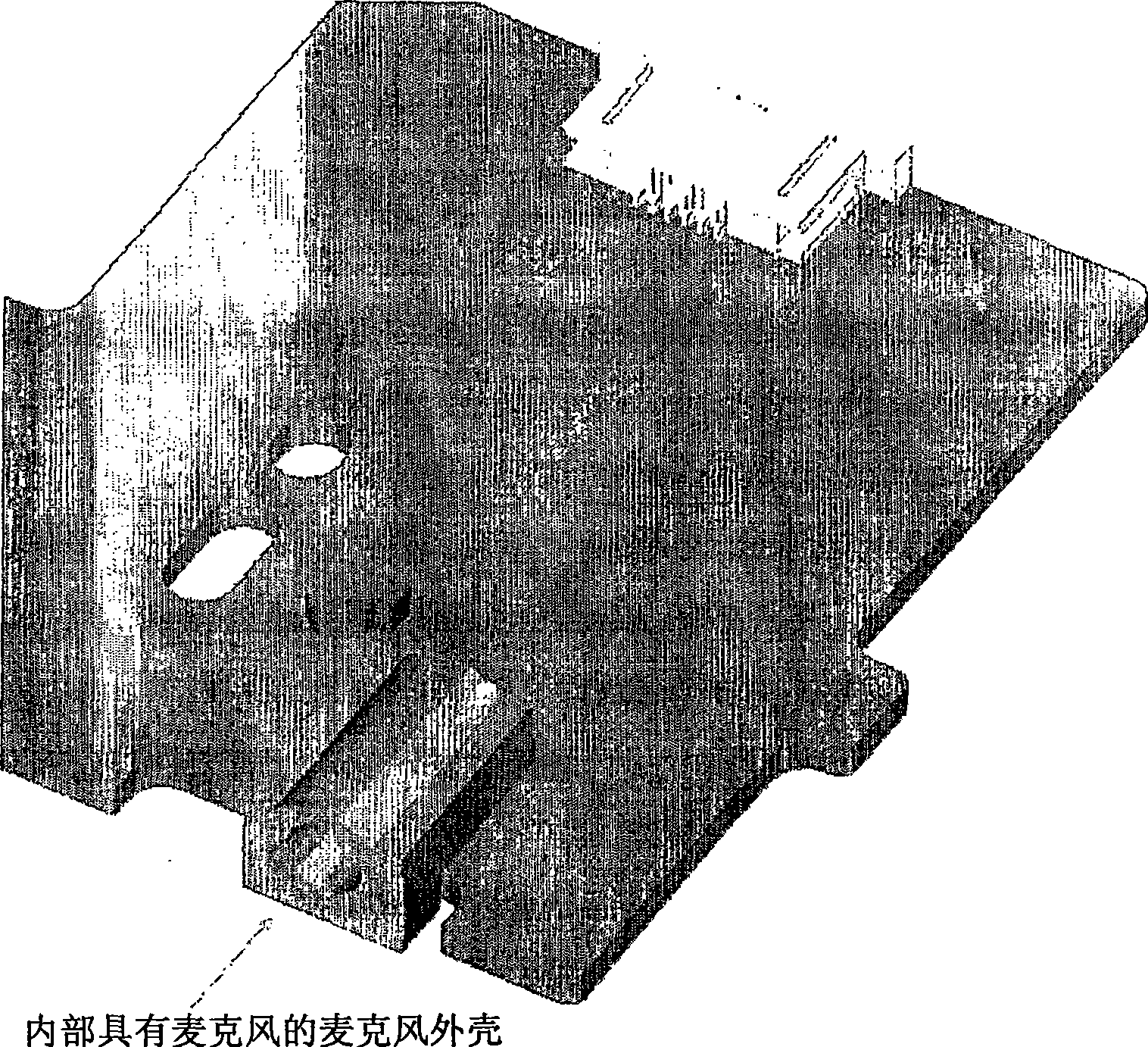
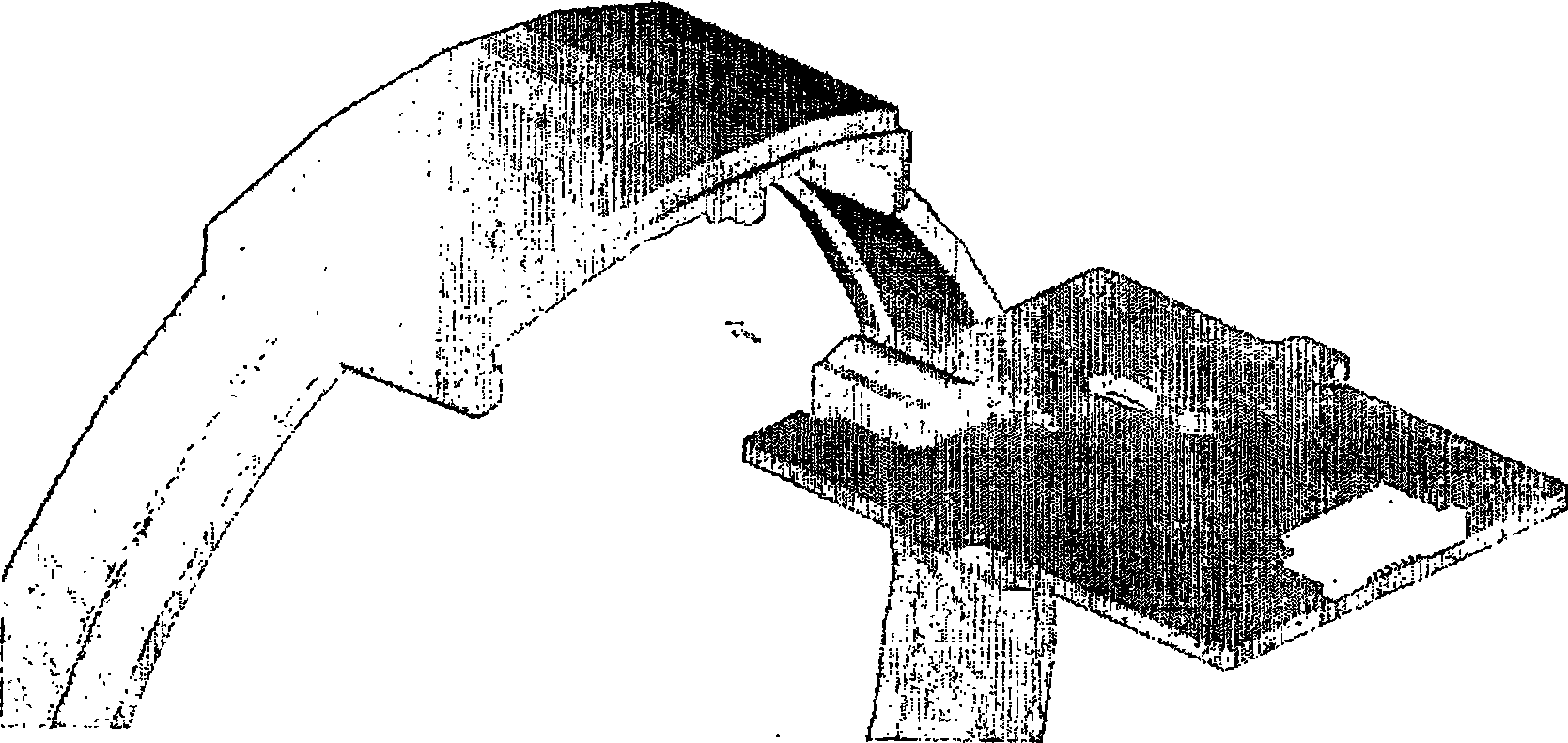
The present invention discloses an arrangement utilizes a certain microphone assembly for facilitating audio source tracking systems in communication systems. It can be applied to both single and array microphones. The principal idea is to enhance the sound level acoustically in the critical high frequency range, thereby increasing the effective signal-to-noise ratio both for sound pickup and localization algorithms. This is done by enclosing the microphone into a channel or a small cavity (a Helmholtz-resonator), thereby introducing a high-frequency response peak (resonance), fairly broad-band.
Owner:TANDBERG TELECOM AS
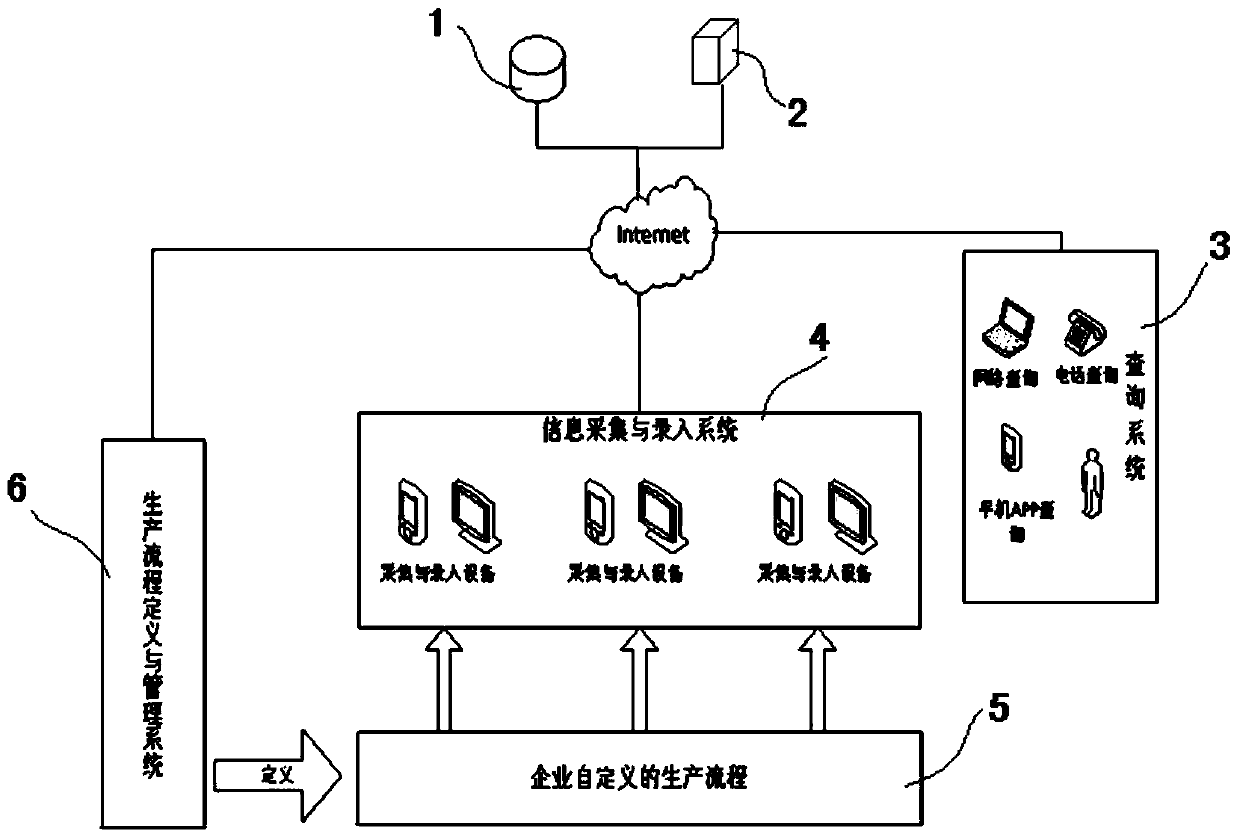
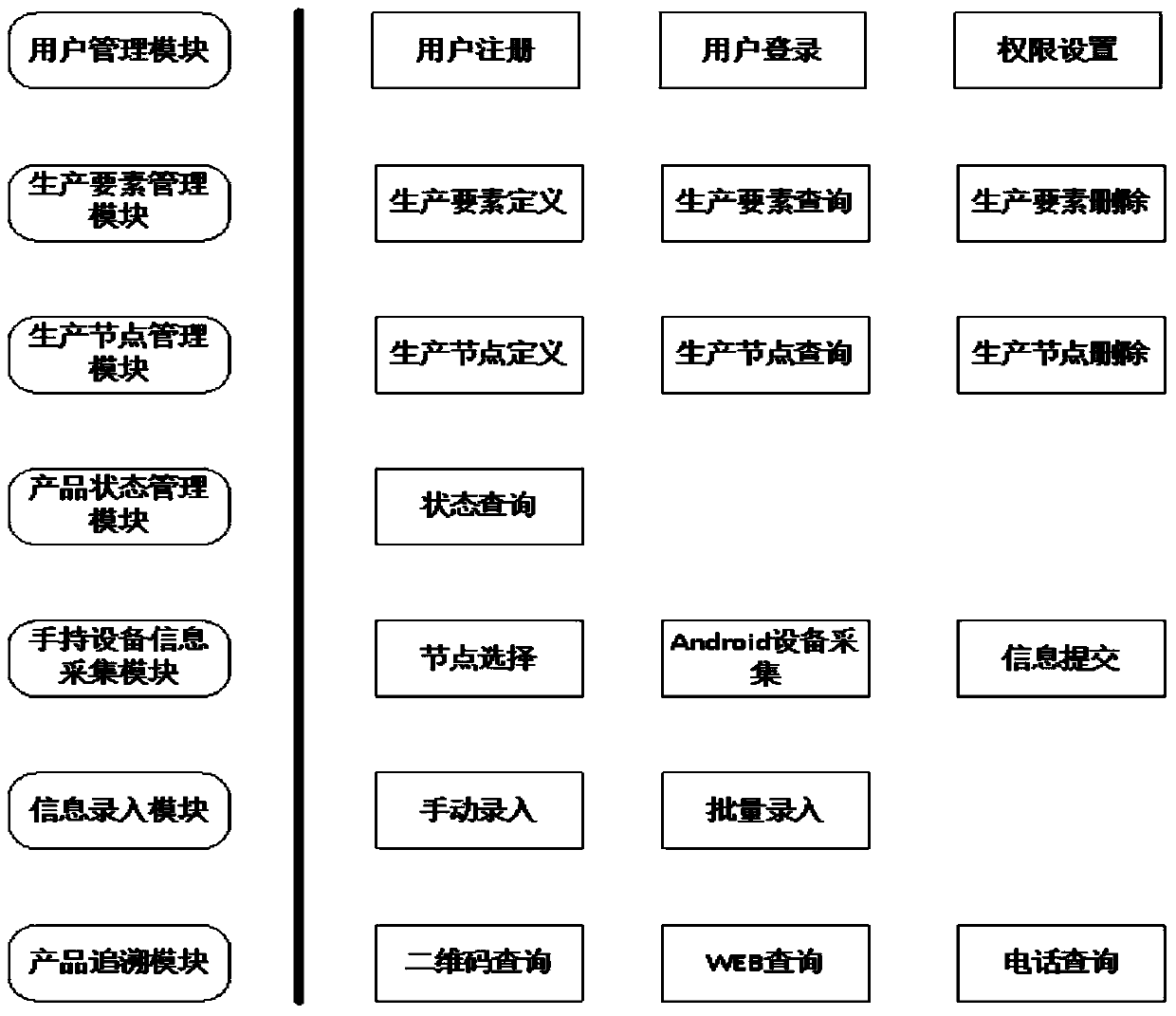
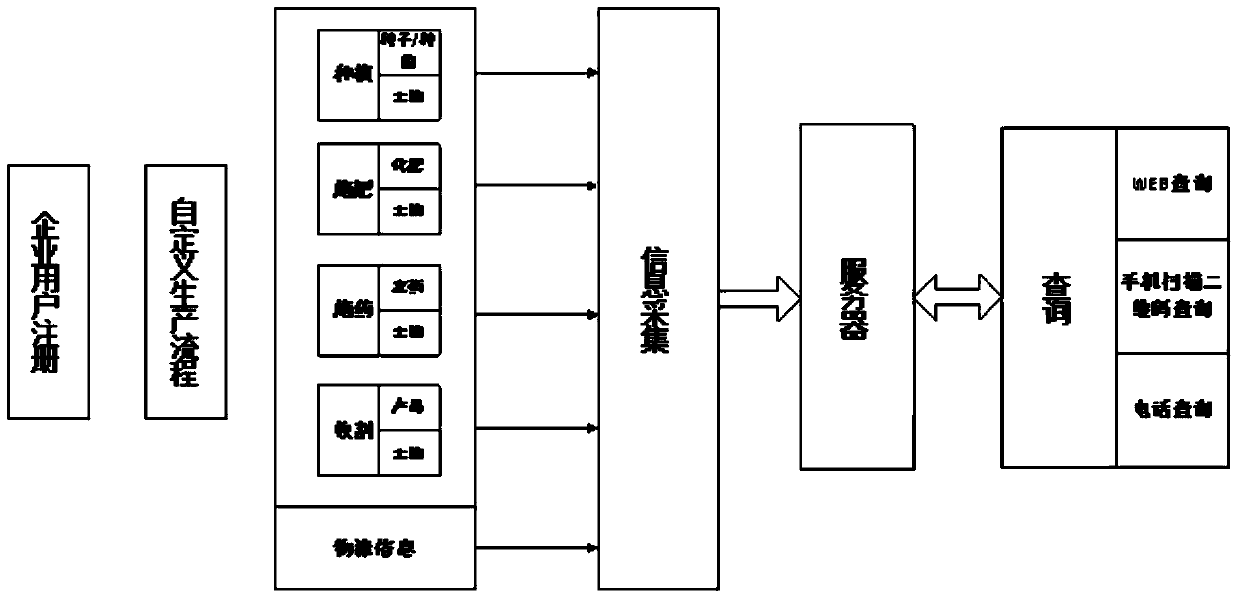
Information recording and source-tracing system with production process customizable
InactiveCN103996104AIncrease flexibilityReasonably change the level of detailResourcesLogisticsComputer scienceSerial code
The invention relates to an information recording and source-tracing system with production process customizable. The system is characterized in that an enterprise customizes names of production factors and attributes, needing recording, incidental to the production factors according to production demands, and customizes names of production nodes and attributes, needing recording, incidental to the production nodes according to production demands; node operation of each step has a unique ID number, when operation is carried out, the ID number of the previous node is input, front-and-back relevance is carried out according to the ID number, and information of the whole production process is stored in a database; the unique source-tracking serial number will be given to a product which leaves a factory, the serial number is related to the node ID of the last node in the production nodes, source tracing is carried out through node IDs step by step in source tracing query, and a complete production information link is formed according to relevancy.
Owner:HUAZHONG UNIV OF SCI & TECH
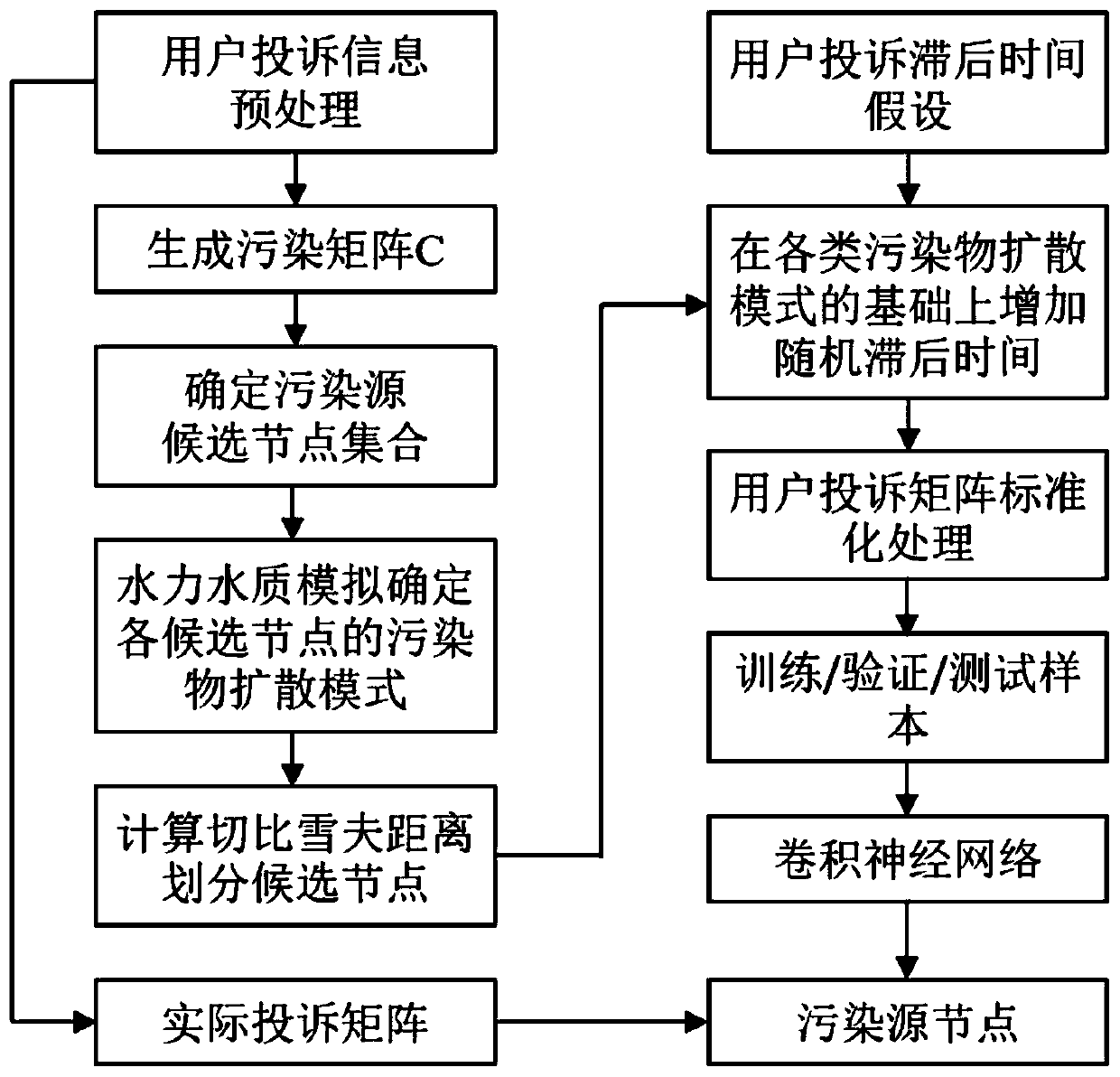
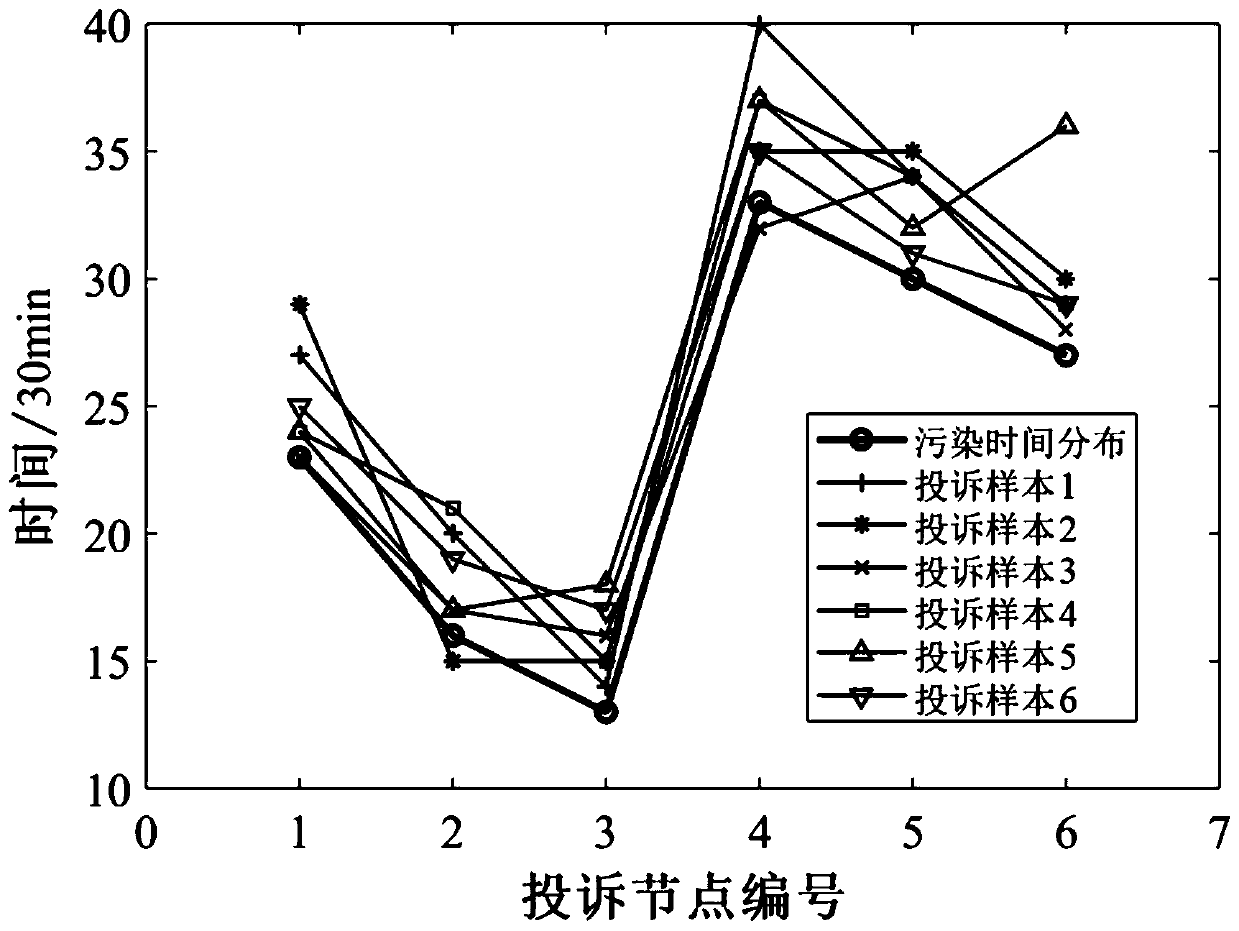
A water supply network pollution source tracking and positioning method based on user complaint information
ActiveCN109886830ARapid positioningImprove emergency response capabilitiesData processing applicationsGeneral water supply conservationWater sourceWater quality
The invention relates to a water supply pipe network pollution source tracking and positioning method based on user complaint information. The method comprises the following steps of S1, generating apollution matrix by using position information complained by a user; S2, judging the similarity among the candidate nodes and dividing the similarity; S3, increasing random complaint lag time and constructing a user complaint sample; And S4, carrying out training verification test on the convolutional neural network by using the complaint sample of the user, and applying the convolutional neural network to actual pollution source tracking and positioning. Compared with the prior art, according to the real-time user complaint information after the pollution accident happens, the user complaintmode recognition is adopted for pollution source positioning, the good pollution source recognition capability is achieved for water source pollution and non-water-source pollution, and certain robustness is achieved for uncertainty of the user complaint lag time. In the cities with incomplete pipe network water quality on-line monitoring equipment, the system has the advantages that the pollutionsource position can be quickly positioned, and the emergency response capability of cities to pipe network water quality accidents is enhanced.
Owner:TONGJI UNIV
Multi-microphone source tracking and noise suppression
Methods, systems, and apparatuses are described for improved multi-microphone source tracking and noise suppression. In multi-microphone devices and systems, frequency domain acoustic echo cancellation is performed on each microphone input, and microphone levels and sensitivity are normalized. Methods, systems, and apparatuses are also described for improved acoustic scene analysis and source tracking using steered null error transforms, on-line adaptive acoustic scene modeling, and speaker-dependent information. Switched super-directive beamforming reinforces desired audio sources and closed-form blocking matrices suppress desired audio sources based on spatial information derived from microphone pairings. Underlying statistics are tracked and used to updated filters and models. Automatic detection of single-user and multi-user scenarios, and single-channel suppression using spatial information, non-spatial information, and residual echo are also described.
Owner:AVAGO TECH INT SALES PTE LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com