Software defined opportunity network DDoS defense method based on block chain
A software-defined and blockchain technology, applied in the computer field, can solve the problems of poor resistance to DDOS attacks, achieve the effects of improving accuracy, maintaining data reliability, and preventing tampering or destruction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
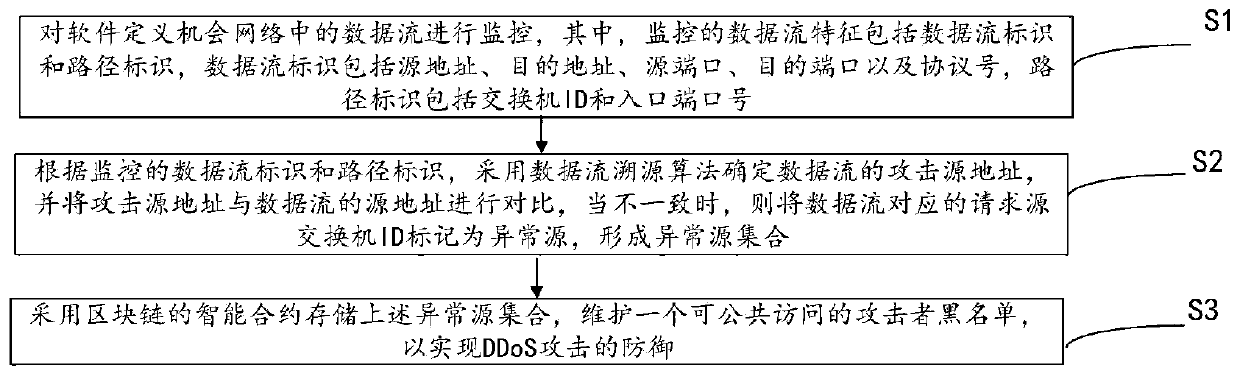
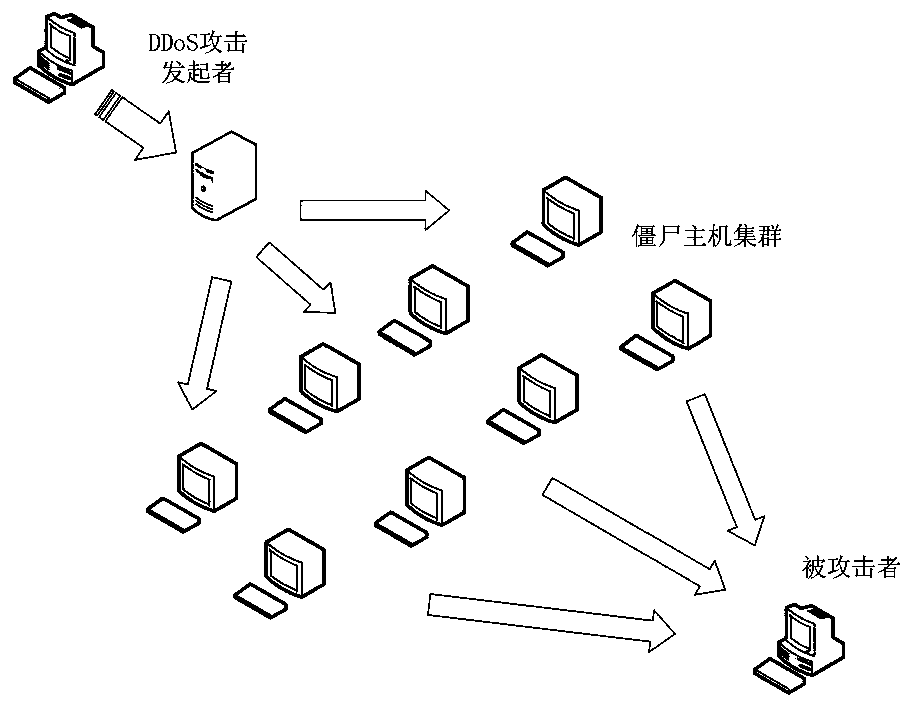
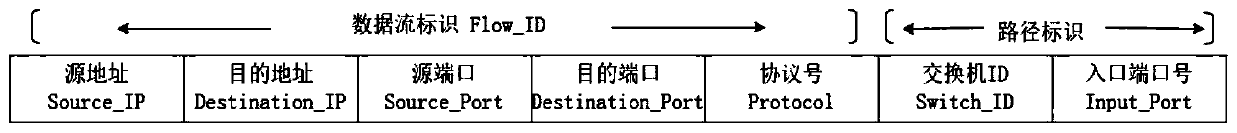
[0048] The inventors of the present application found through a lot of practice that the software-defined opportunistic network is a special network structure that transmits messages through nodes moving freely and meeting randomly. -Forwarding" routing mode to form communication opportunities and communicate hop by hop. But this mode of communication also brings new problems. The software-defined opportunistic network does not require a fixed and reliable transmission channel between two nodes establishing communication, and does not require the network to have full connectivity, and the random movement of nodes will also lead to communication instability. In terms of security, the sparseness of nodes in software-defined opportunistic networks is high, so that malicious nodes can join the current network environment at will. Malicious nodes will spread false information maliciously. Secondly, malicious nodes will capture normal nodes to mislead them to carry out normal news. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com