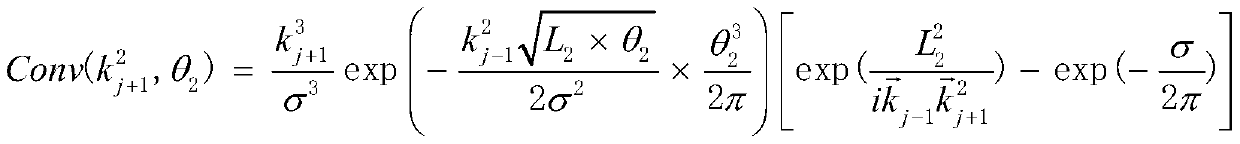Patents
Literature
95results about How to "Reduce the Risk of Confidentiality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
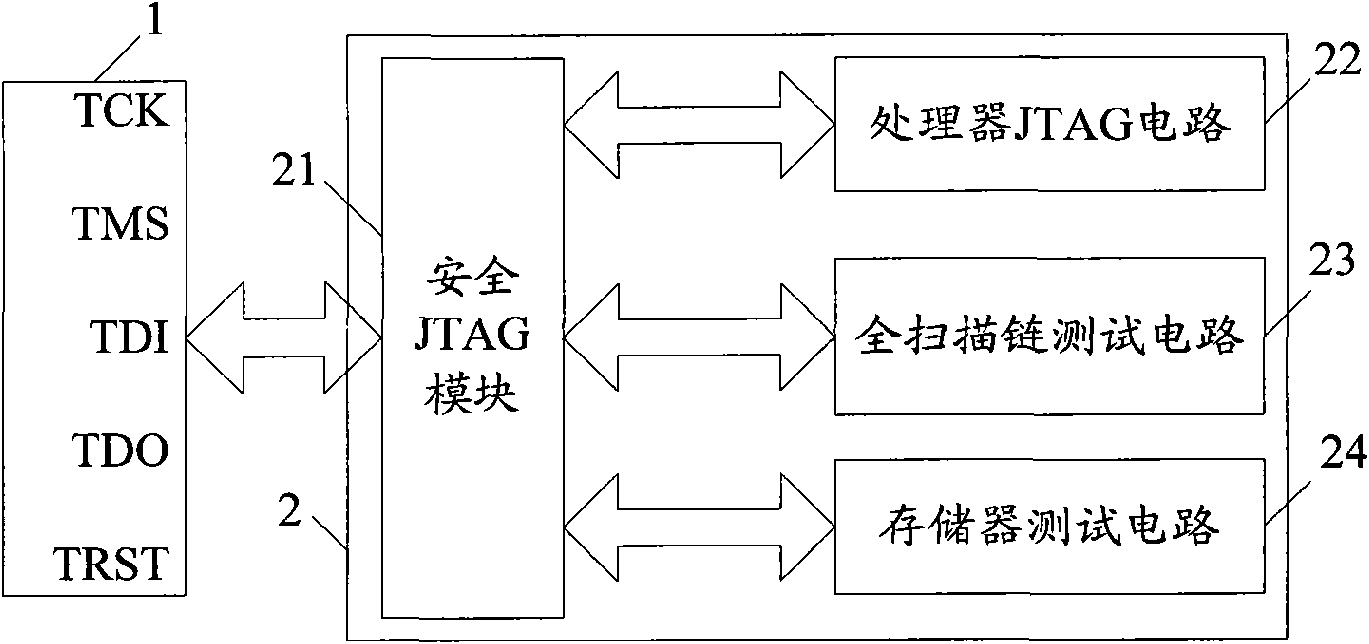
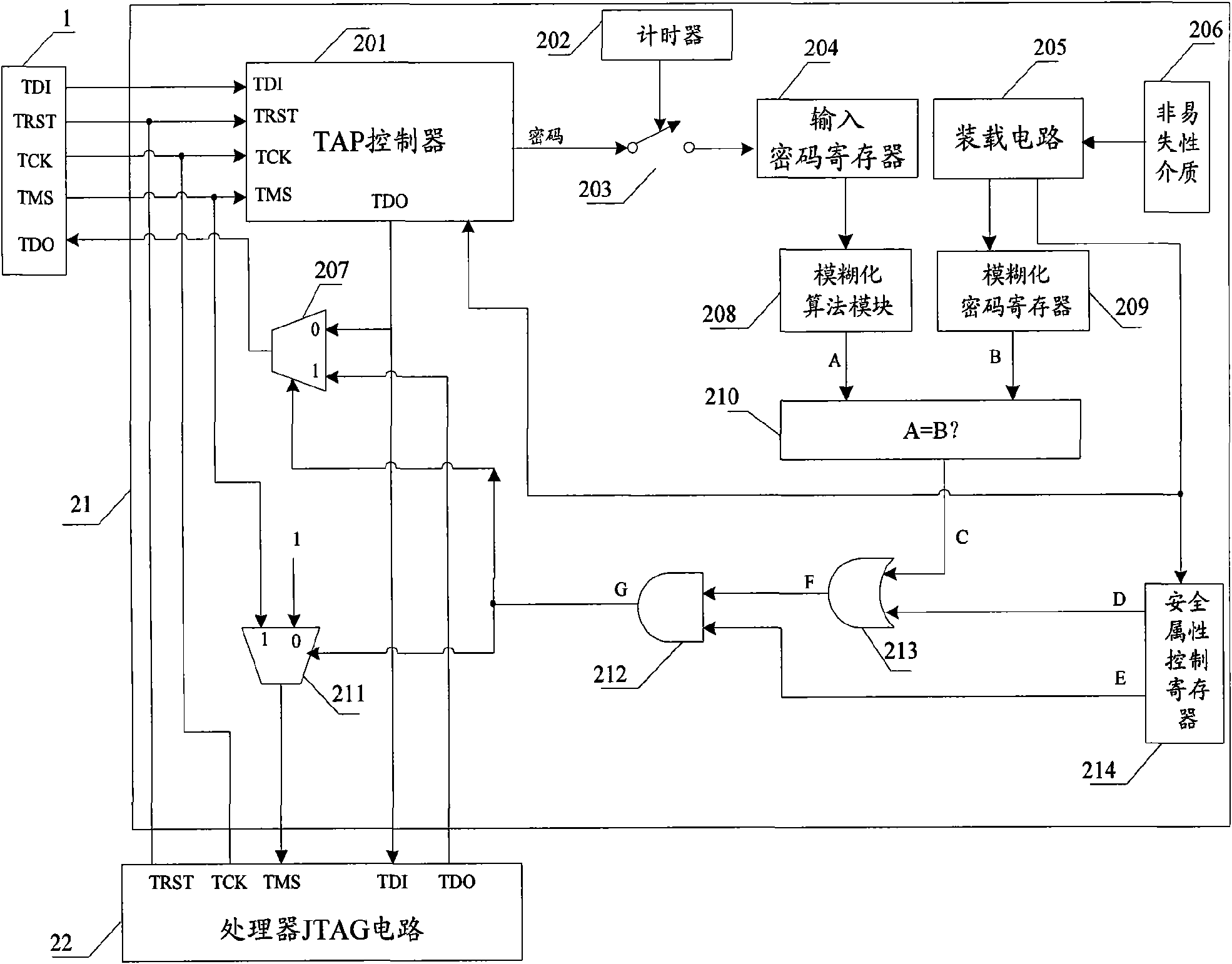
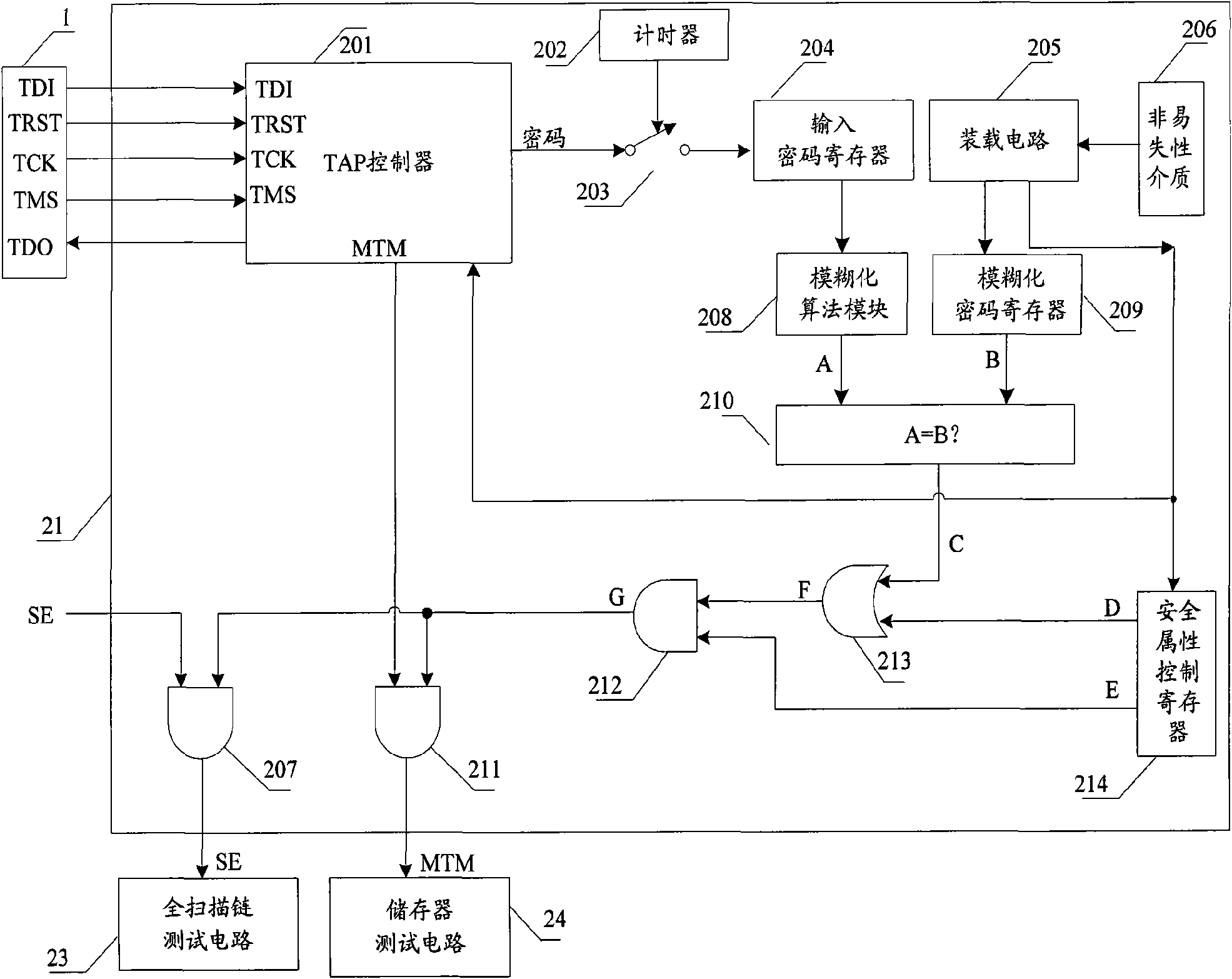
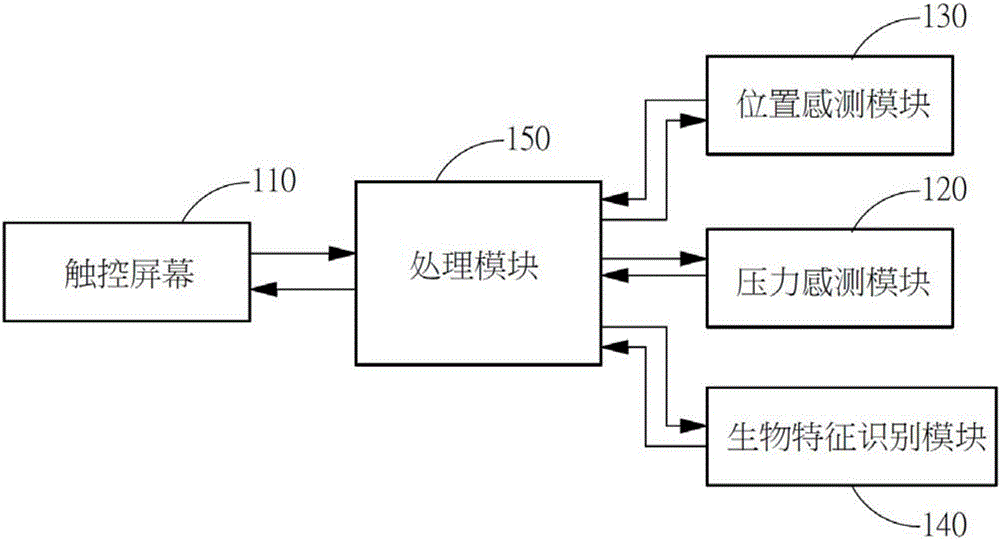
Safety JTAG module and method for protecting safety of information inside chip
InactiveCN101620656AReduce security risksImprove data security featuresInternal/peripheral component protectionProcessor registerPassword
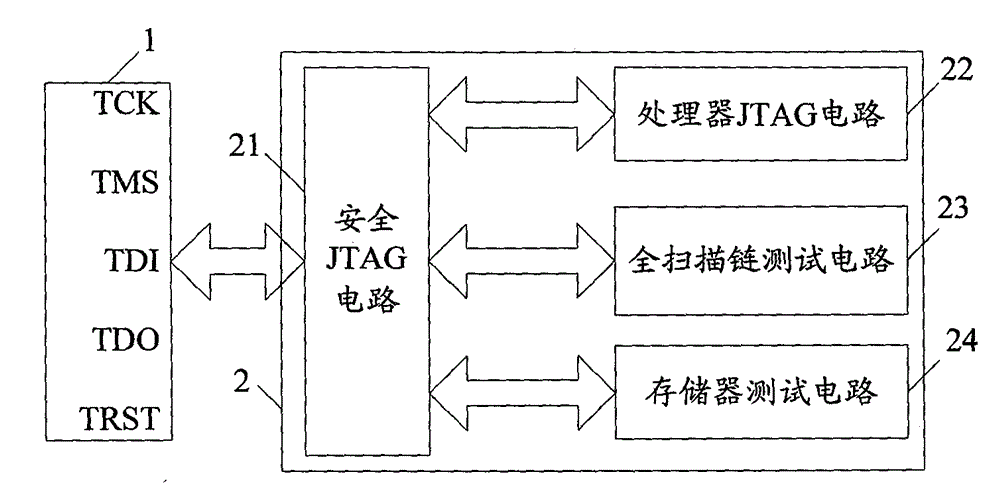
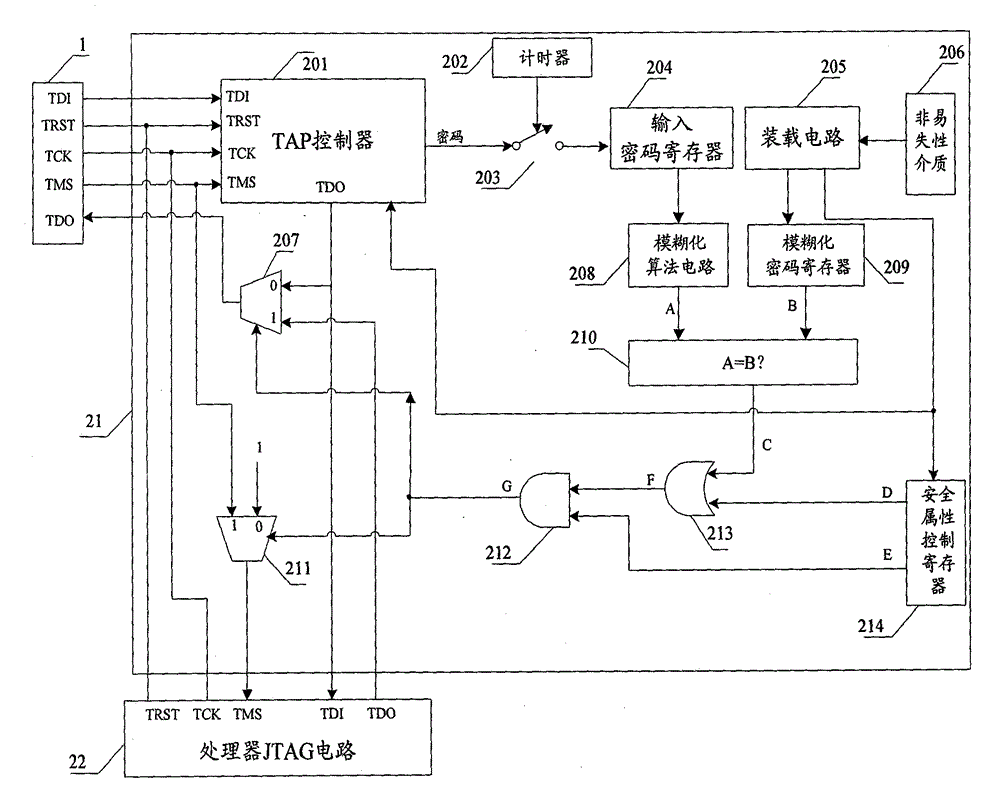
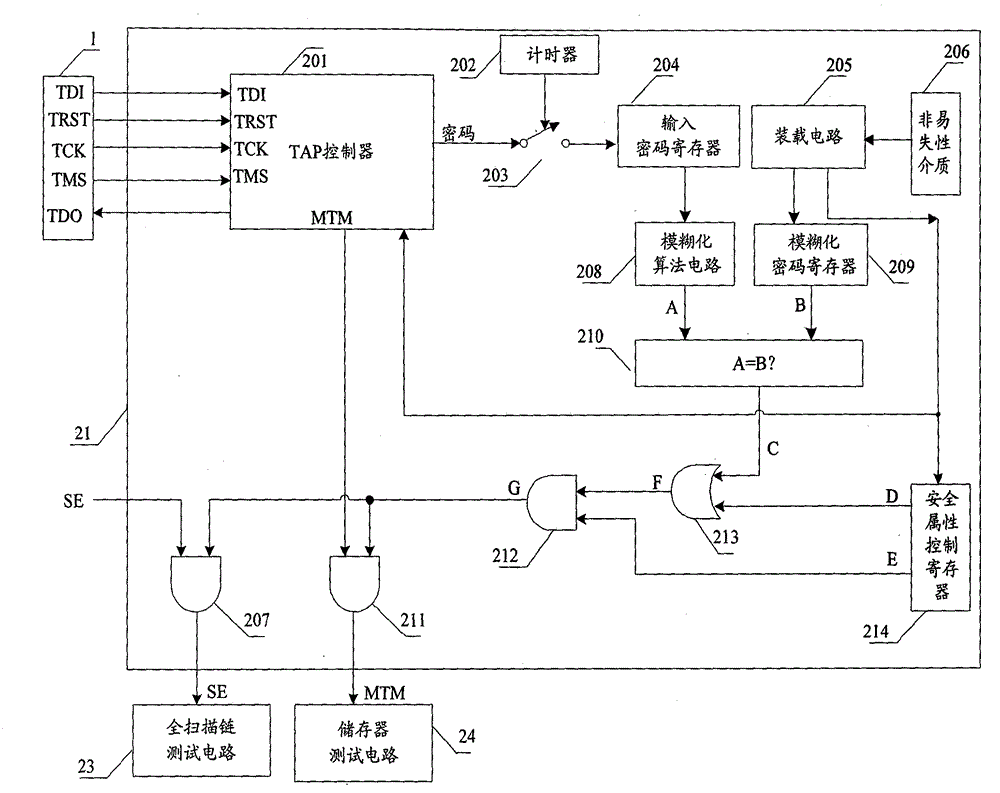
The invention relates to a safety JTAG module and a method for protecting security of information inside a chip, wherein the safety JTAG module comprises a nonvolatile medium (206), a loading circuit (205), a security attribute control register (214), a TAP controller (201), two selectors (207 and 211), a switch (203), a password authentication module and a logic processing module; the TAP controller (201) and the two selectors (207 and 211) are connected between a JTAG port (1) and a protected object inside the chip; the switch (203) is switched by the control of a timer (202); the password authentication module is used for authenticating whether a clear-text password input by a user is accordant with a fuzzification password or not; and the logic processing module is used for logically processing an authentication result output by the password authentication module and an indication signal output by the security attribute control register (214) and outputting an enable signal to the two selectors (207 and 211) so as to control whether the JTAG port (1) is allowed to be connected with the protected object inside the chip through the TAP controller (201) or not. The invention ensures the security and the convenience of an SOC chip in testing and debugging processes, thereby protecting the security of data inside the chip.
Owner:SHENZHEN STATE MICRO TECH CO LTD
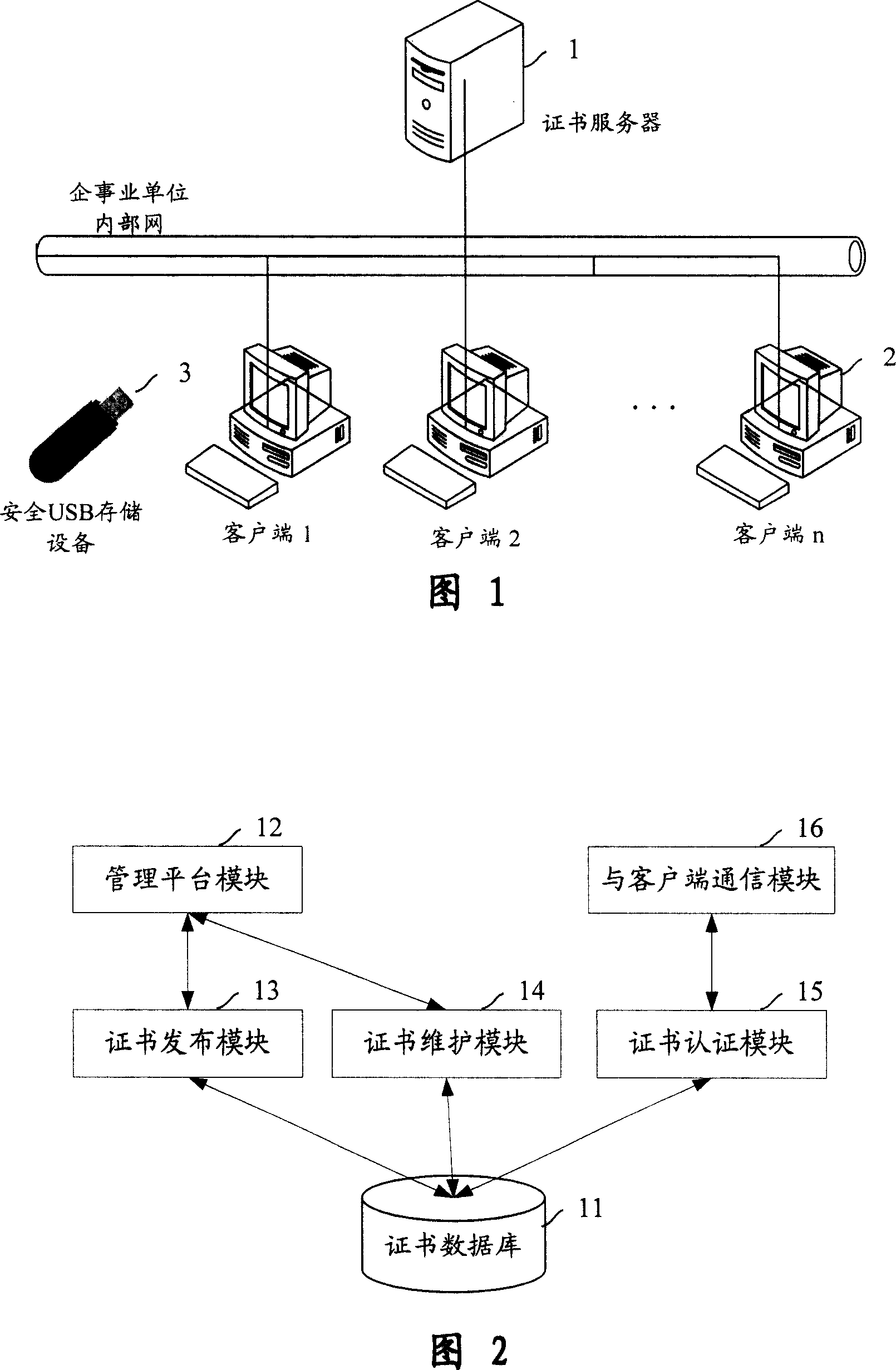
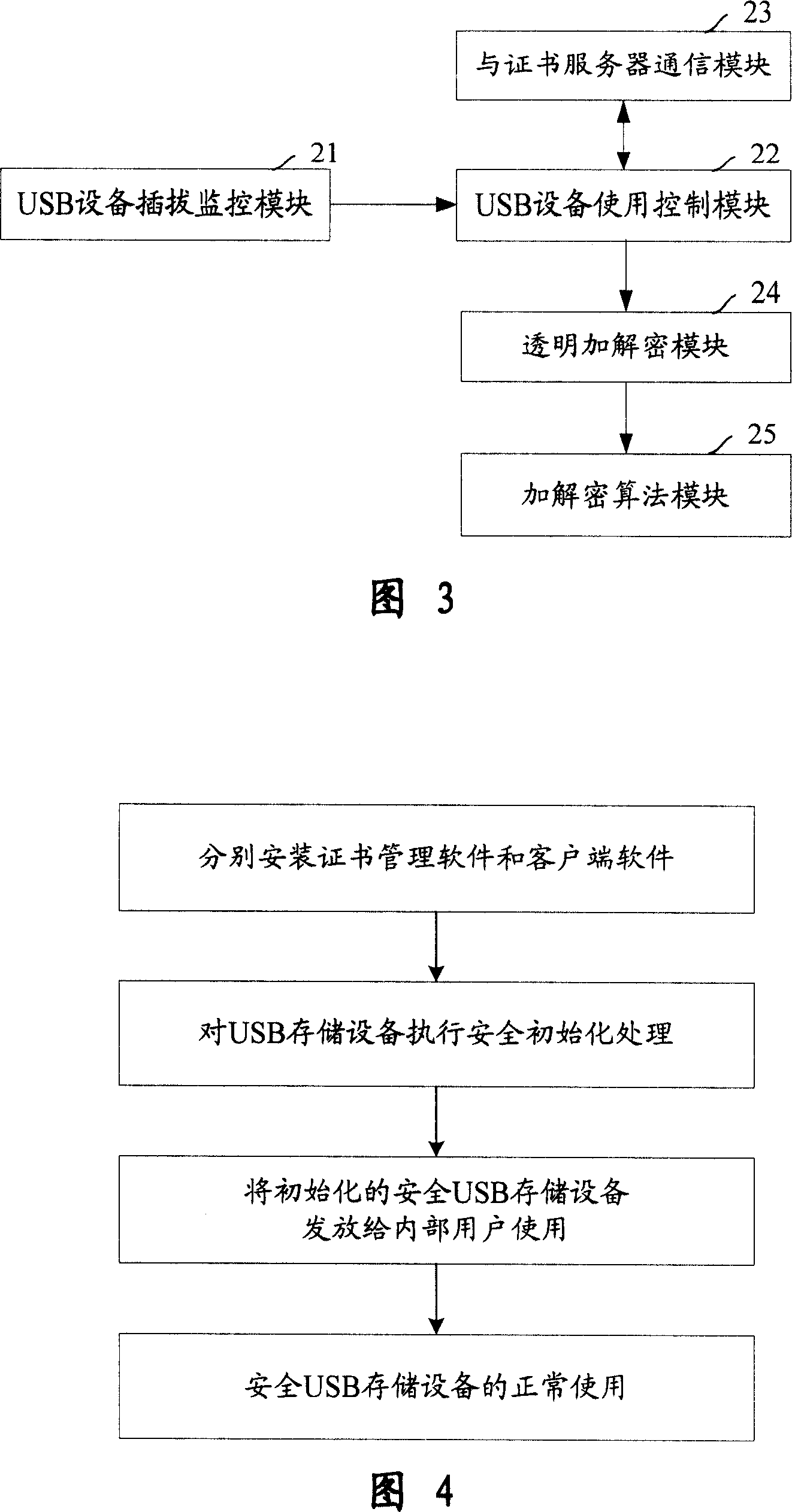
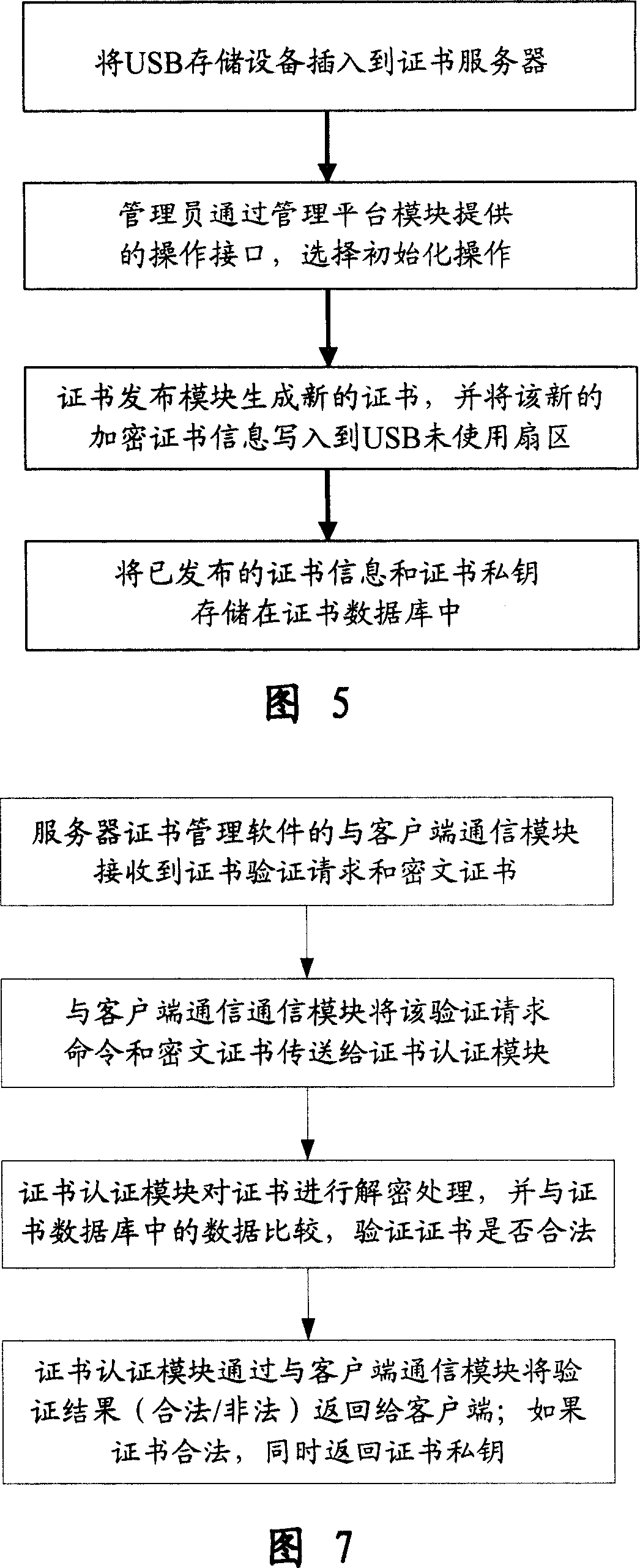
Divulging secrets prevention system of USB storage device date based on certificate and transparent encryption technology
InactiveCN101017525APrevent leak riskReduce the Risk of ConfidentialityUser identity/authority verificationUnauthorized memory use protectionClient-sideUSB
This invention relates to one USB memory data anti-leakage system based on certificate and transparent coding technique, which comprises the following parts: one certificate management software; certificate servo with physical isolation and network protection actions, inner network host to customer end with customer end software; safety USB memory device by multiple common USB devices through the servo. The method comprises the following steps: a, separately fixing certificate management software and customer end software in network servo and each host; b, executing safety initial process in certificate servo on USB memory device; c, sending the memory device to inside user; d, safety USB memory device is for normal use.
Owner:BEIJING UNIV OF POSTS & TELECOMM
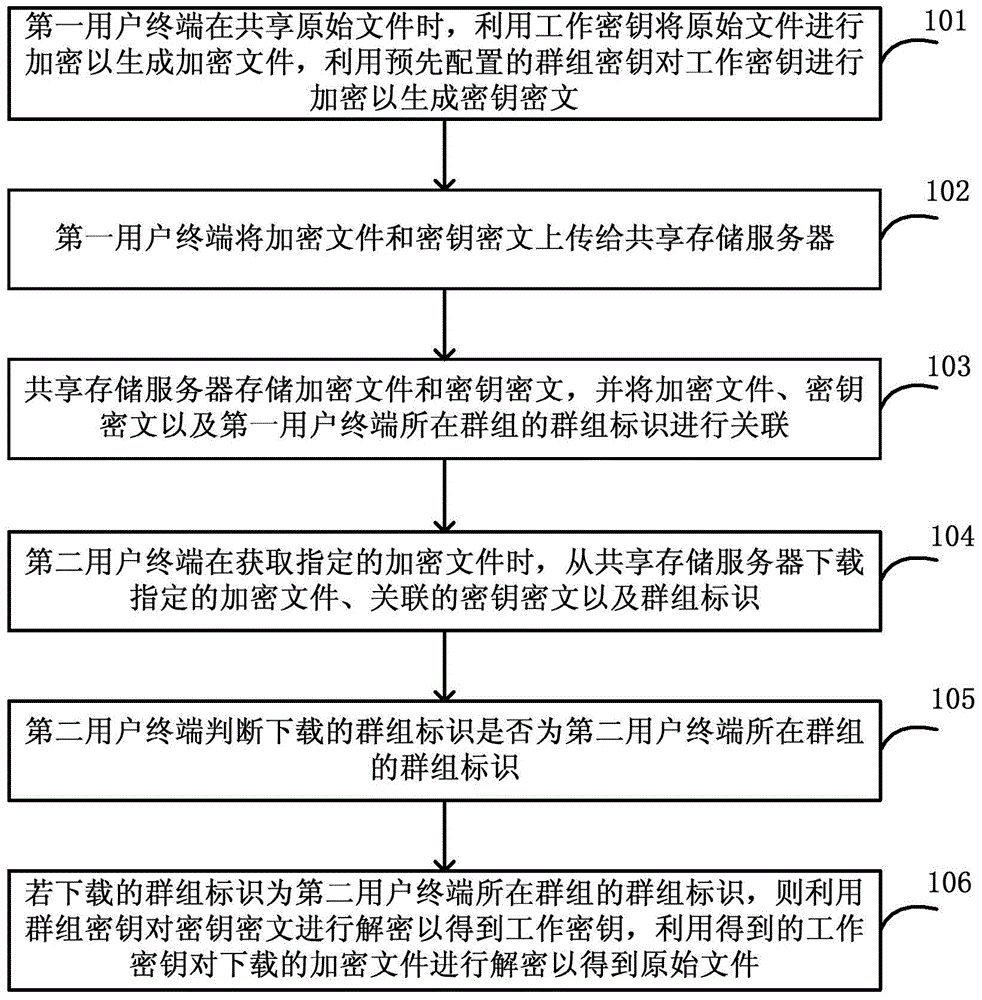
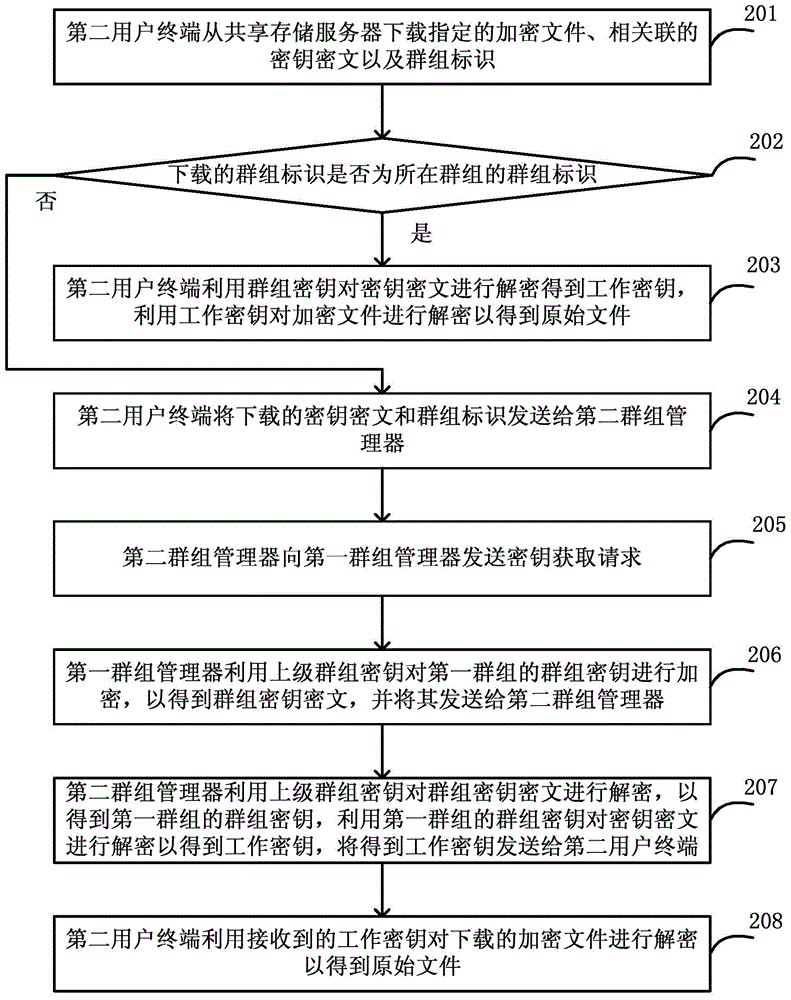
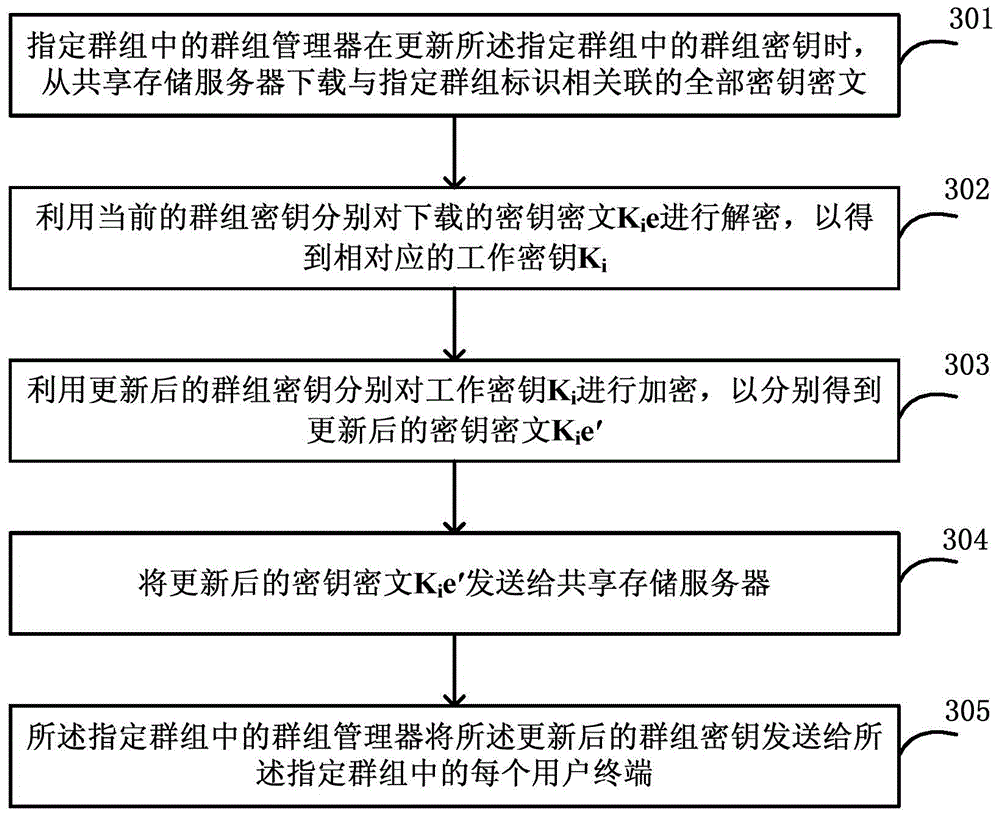
File secure sharing method and system based on group key
ActiveCN104917787AReduce the Risk of ConfidentialityFlexible sharingKey distribution for secure communicationCiphertextControllability
The invention discloses a file secure sharing method and system based on a group key. When a first user terminal shares an original file, the original file is encrypted by use of a work key so as to generate an encryption file, the work key is encrypted by use of the group key so as to generate key cryptograph, and the encryption file and the key cryptograph are uploaded to a shared storage server; a second user terminal downloads a specific encryption file, a key cryptograph associated with the specific encryption file, and a group identification from the shared storage server; and the second user terminal, when determining that the downloaded group identification is the group identification of a group where the second user terminal is located, decrypts the key cryptograph by use of the group key and decrypts the encryption file by use of the work key so as to obtain the original file. According to the invention, the work key is encrypted by use of the group key, the encryption file can be securely and flexibly shared with user controllability and easy key management, and the risk that a user file is leaked in a sharing process is reduced.
Owner:CHINA TELECOM CORP LTD
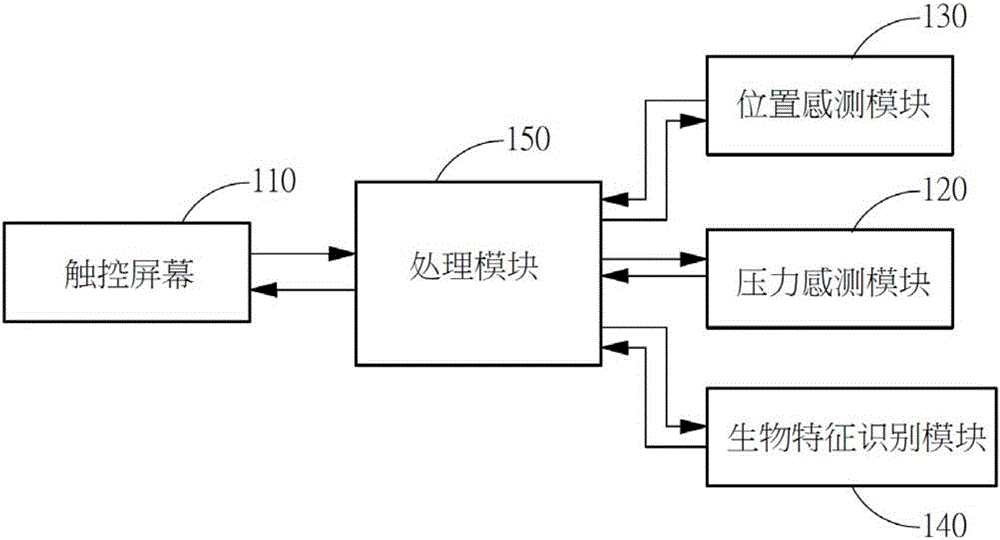
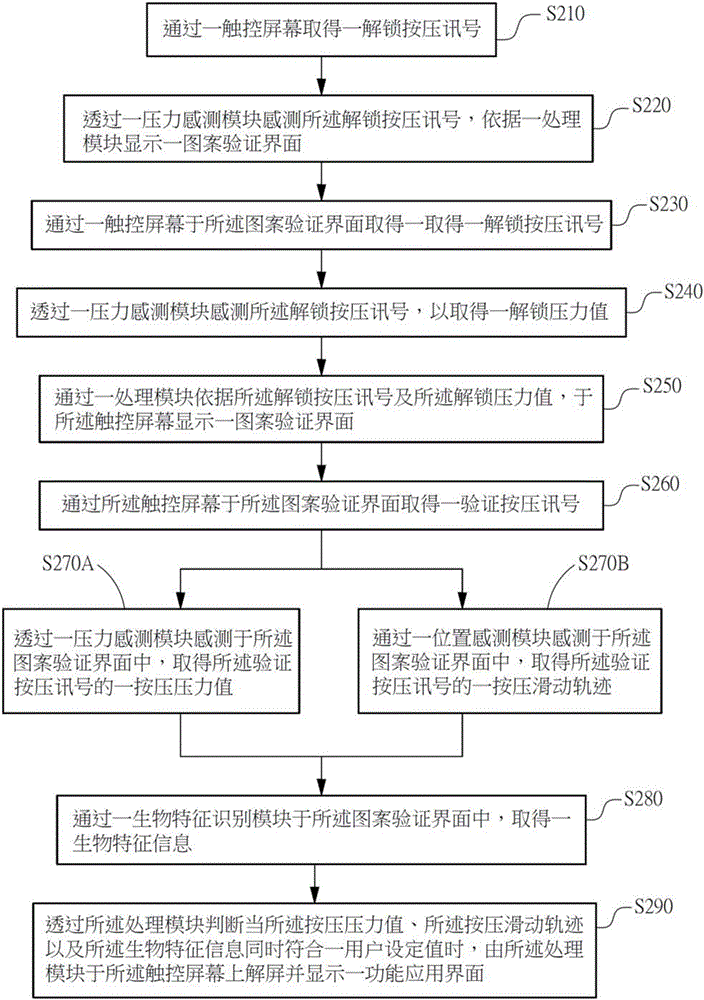
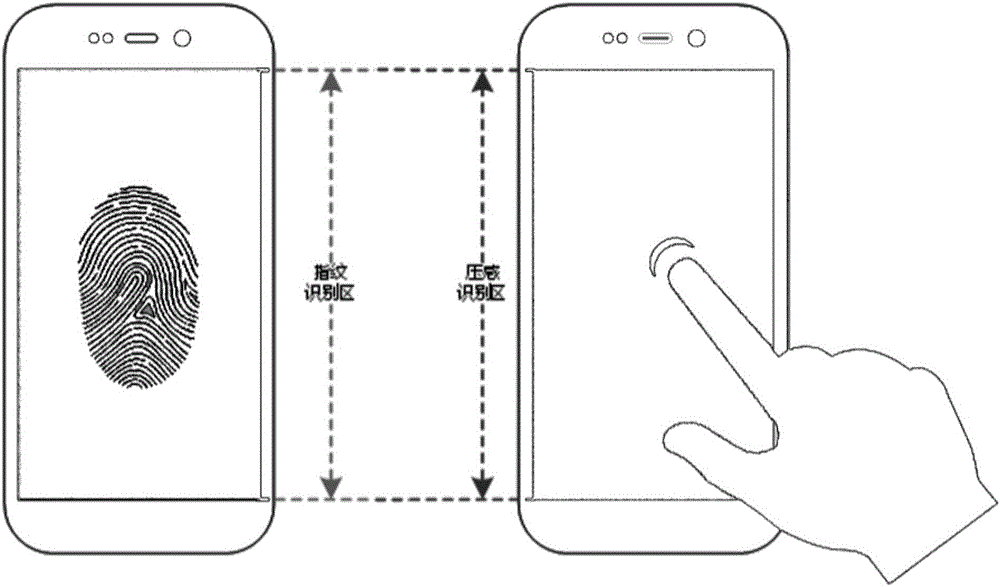
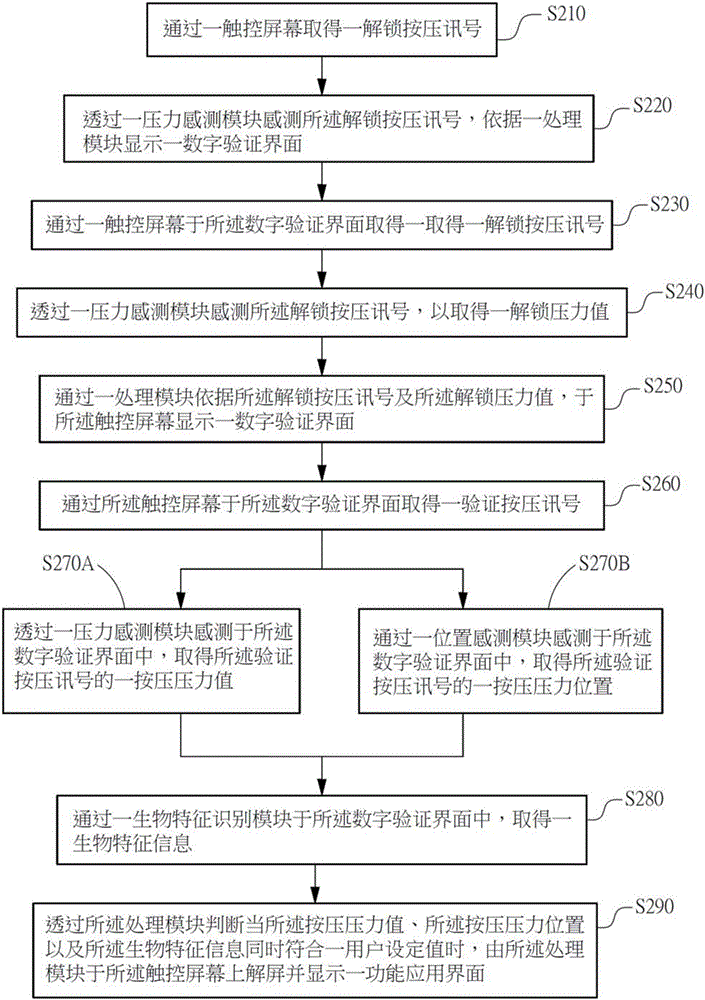
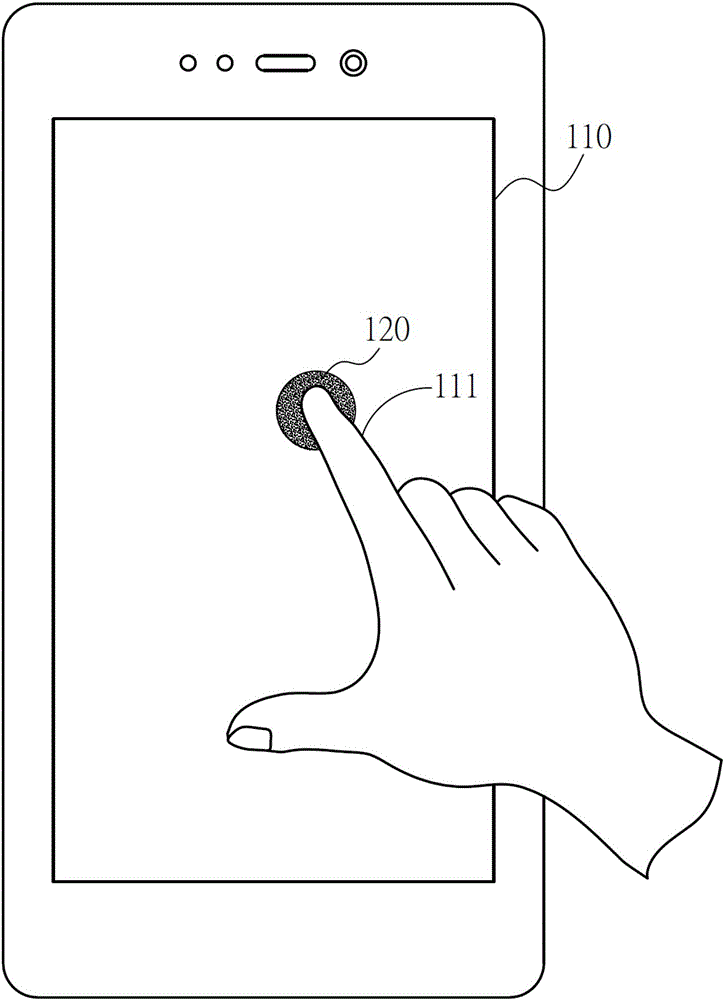
Pattern locus screen unlocking system and method combining strength and biological characteristic identification
InactiveCN105930706AReduce the Risk of ConfidentialityReduce stepsDigital data authenticationComputer modulePressure sense
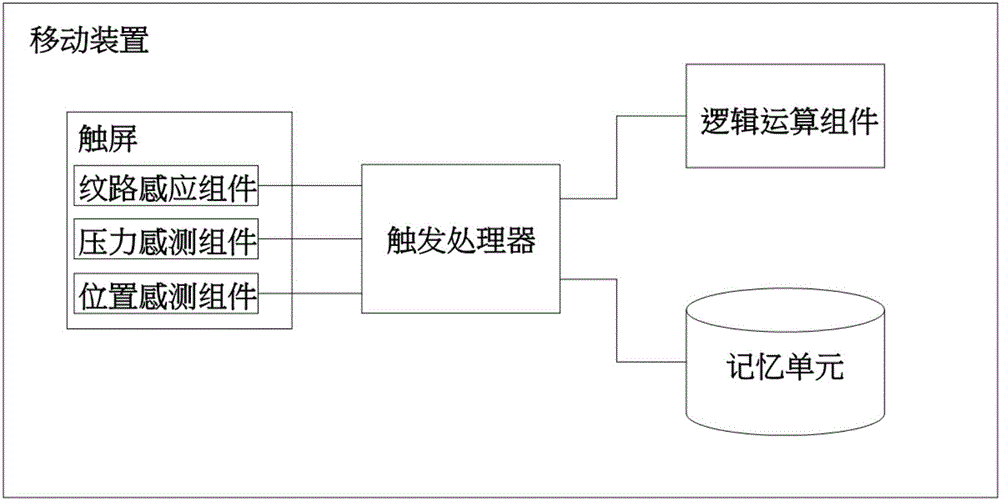
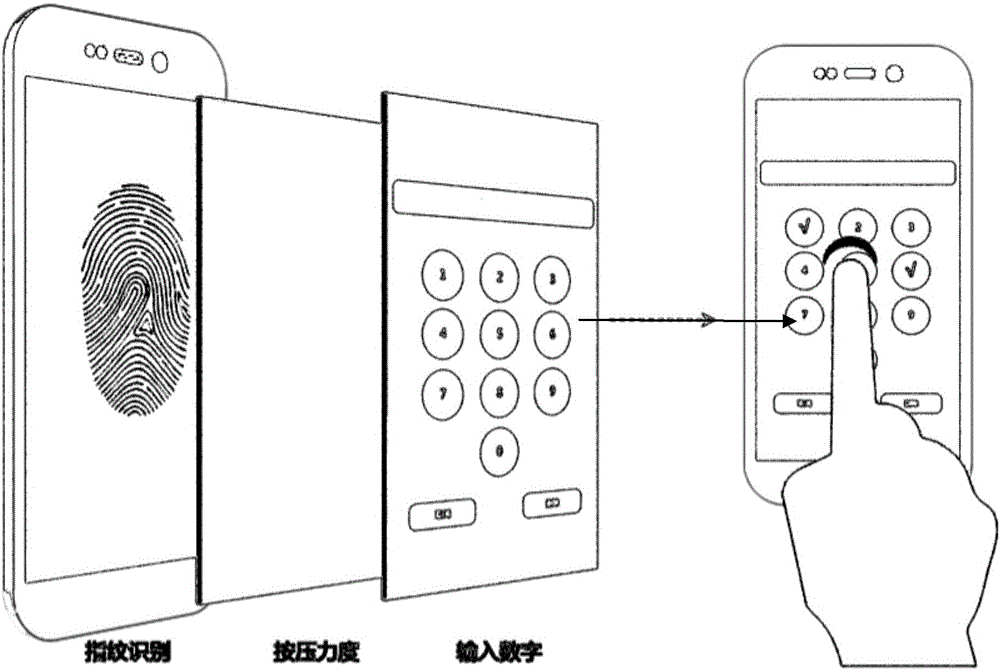
The invention provides a pattern locus screen unlocking system and method combining strength and biological characteristic identification. The system and the method are characterized in that an unlocking pressing signal is obtained through a touch screen, the unlocking pressing signal is sensed by a pressure sensing module to obtain an unlocking pressure value; a pattern authentication interface is displayed on the touch screen and a verification pressing signal is obtained by a processing module according to the unlocking pressing signal and the unlocking pressure value; the pressing pressure value of the verification pressing signal is sensed by the pressure sensing module, the pressing sliding locus is sensed by a position sensing module and the biological characteristic information is obtained through a biological characteristic identification module; the touch screen is unlocked by the processing module and a function application interface is displayed when the processing module determines that the pressing pressure value, the pressing sliding locus and the biological characteristics simultaneously are in consistent with a user set value.
Owner:SHENZHEN TINNO WIRELESS TECH
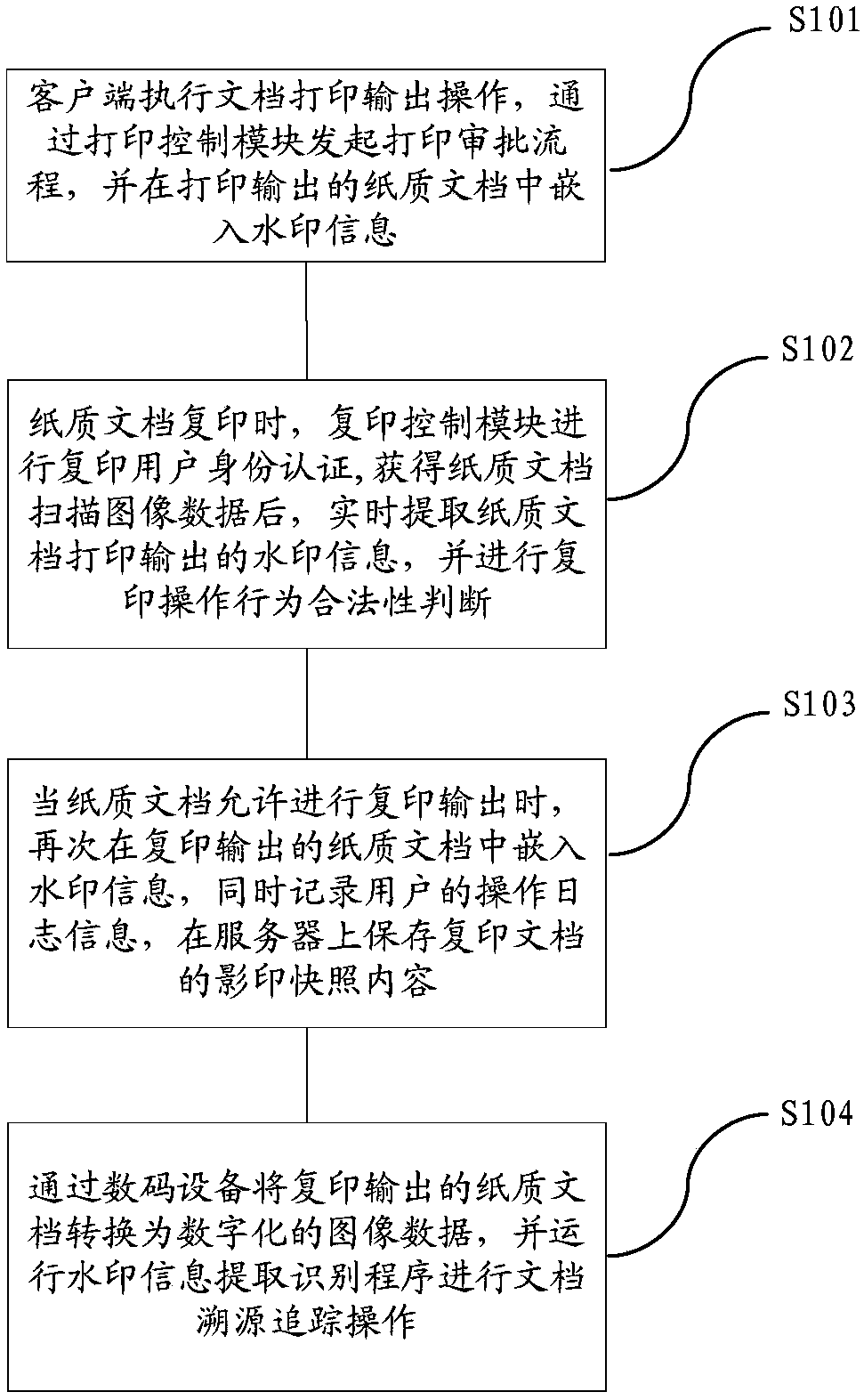
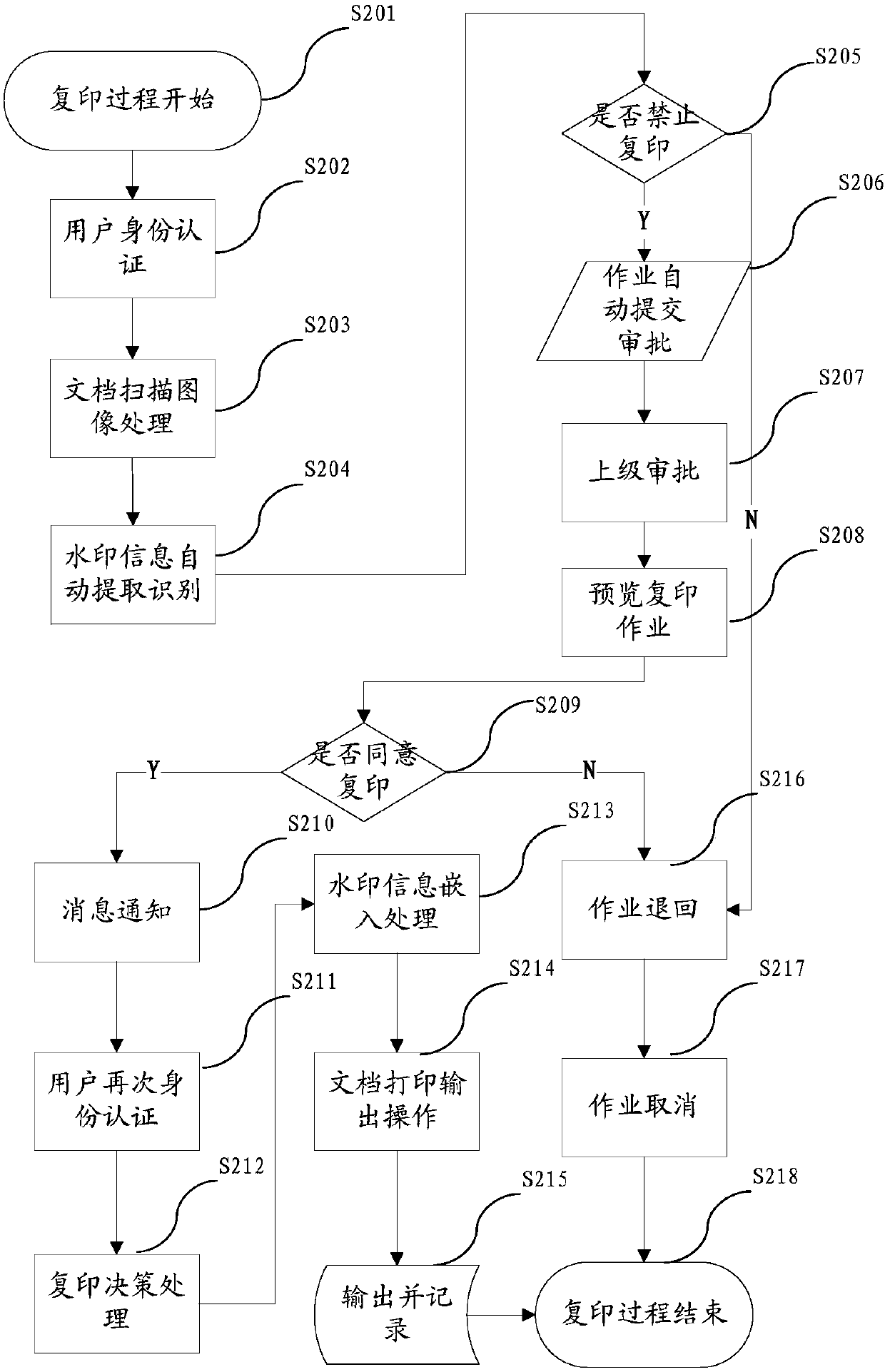
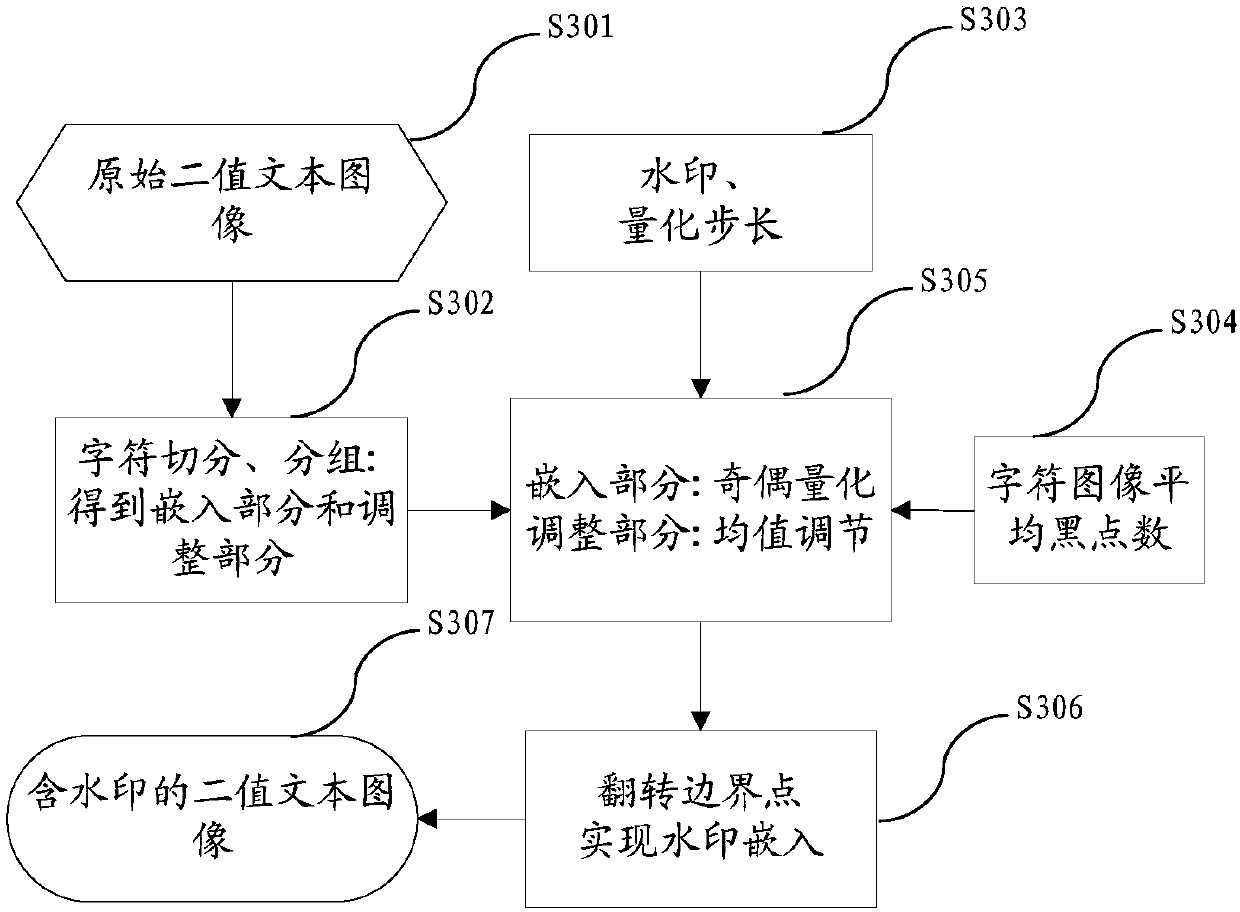
Method and device for safety control and source-tracing tracking of paper document
ActiveCN107066844AReduce the Risk of ConfidentialityReduce Human Intervention FactorsProgram/content distribution protectionDigital output to print unitsSafety controlCopy control
The invention relates to a method and device for safety control and source-tracing tracking of a paper document. The method comprises the steps that (1) a client side inserts watermark information in the printed and output paper document by a printing control module; (2) when the printed paper document is copied, copying user identity authentication will be conducted by a copy control module, a user obtains scanning image data of the paper document after passing the identity authentication, the watermark information inserted into the paper document is extracted in real time, and then legality of a copy operation behavior is judged; (3) when the copy operation behavior of the paper document is judged to be legal, the watermark information will be inserted into the copied and output paper document once again; and (4) the copied and output paper document is converted into digital image data by digital equipment, and a watermark information extraction and recognition program is conducted for a document source-tracing tracking operation. According to the invention, technical puzzles in safety control output, source-tracking tracking of secrete divulgence and so forth during whole processes of paper document printing and copying can be solved uniformly.
Owner:李晓妮
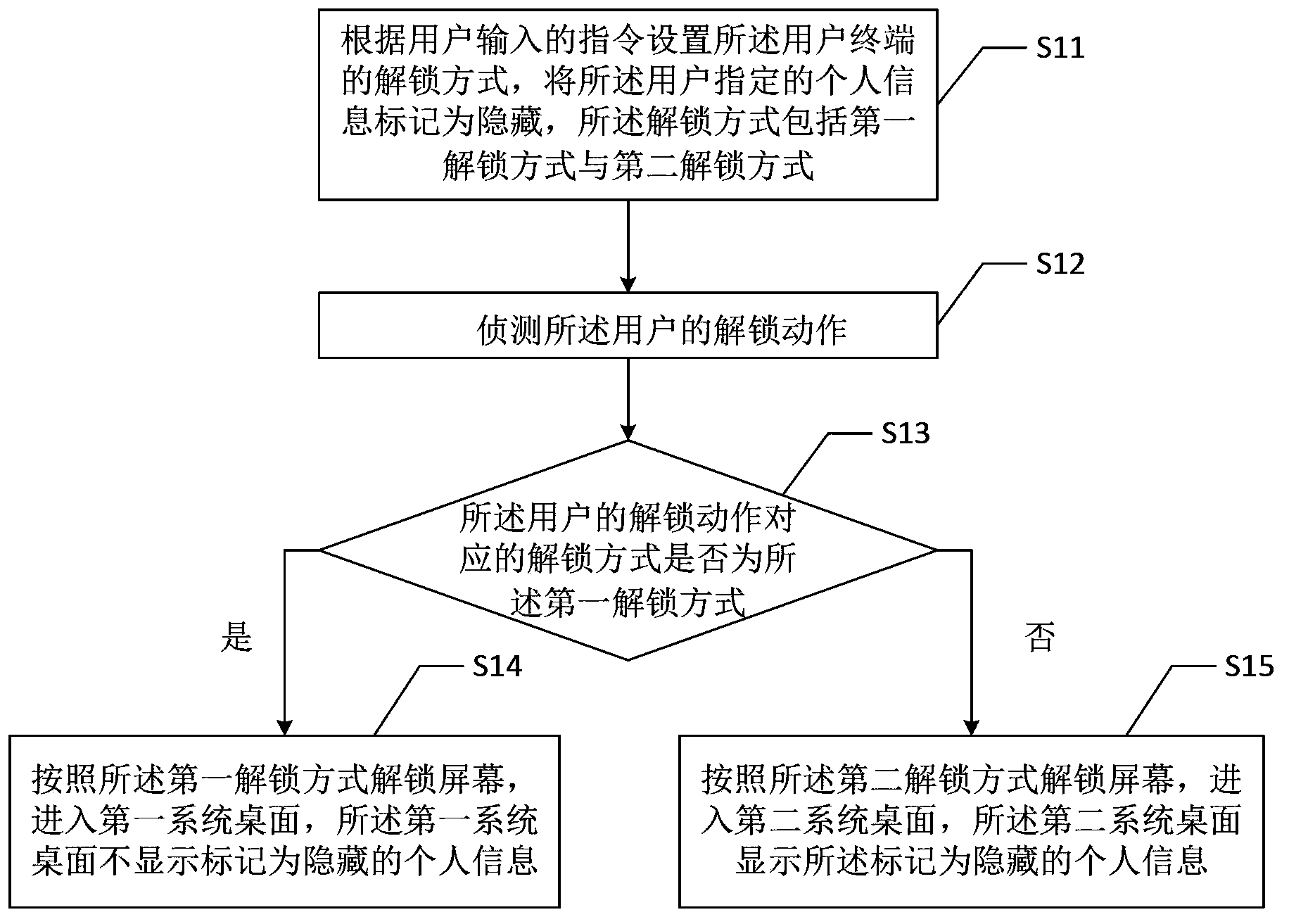
Personnel information safety management method and management device
ActiveCN104077512AImprove effectivenessReduce the Risk of ConfidentialityDigital data authenticationUser inputComputer terminal
The invention provides a personnel information safety management method, which is used for managing personnel information in a user terminal, and comprises the following steps that: an unlocking mode of the user terminal is set according to instructions input by a user, and the personnel information specified by the user is marked into hidden information; the unlocking action of the user is detected; whether an unlocking mode corresponding to the unlocking action of the user is a first unlocking mode or not is detected; if so, a screen is unlocked in the first unlocking mode, and the operation enters a first system desktop; and if not, the screen is unlocked in a second unlocking mode, and the operation enters the second system desktop. In addition, the invention also provides a management device. The personnel information safety management method and the management device have the advantages that the secret leakage risk is lower, and the individual privacy of the user can be more effectively protected.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Screen control system combining strength and fingerprint identification and control mode thereof
InactiveCN105930078AReduce the Risk of ConfidentialityImprove usabilityInput/output processes for data processingControl systemPressure sense
The invention provides a screen control system combining strength and fingerprint identification and a control mode thereof. A triggering processor is sensed by a position sensing assembly in real time, and the triggering processor enables a biological characteristic identification assembly and a pressure sensing assembly; click position information is obtained by the position sensing assembly, biological characteristic information is obtained by the biological characteristic identification assembly, and the pressure information at the click position of a finger is sensed by the pressure sensing assembly; after the triggering processor receives the above information, the information is converted into a secret key according to specific logic, then whether the secret key is reasonable or not is verified for unlocking the screen; a simple and practical advanced ciphering / deciphering strategy is realized by combining three technologies of touch screen, pressure-sensitive touch and fingerprint identification; by combining touch screen, pressure-sensitive touch and fingerprint identification, the security of secret keys is strengthened, operability is stronger, promotion and implementation are easy to achieve, and the system has broader industrial application prospect.
Owner:SHENZHEN TINNO WIRELESS TECH
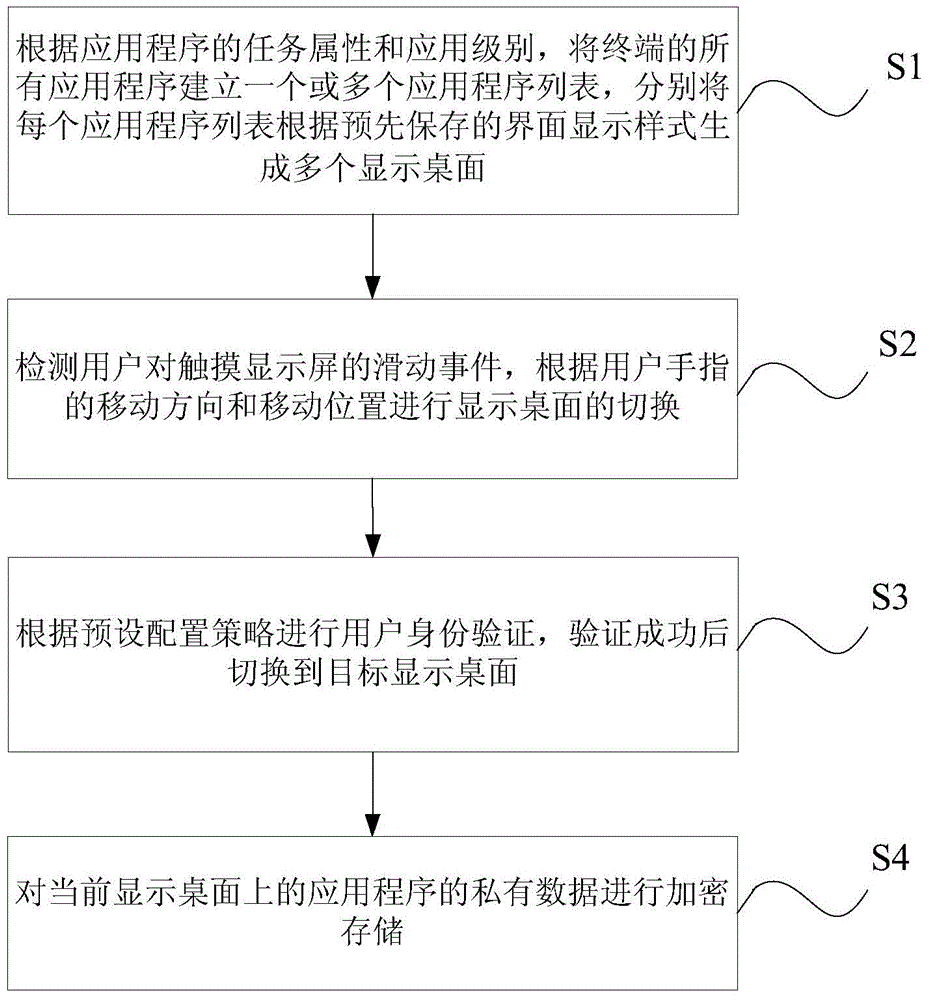
Desktop display control method and device and mobile terminal
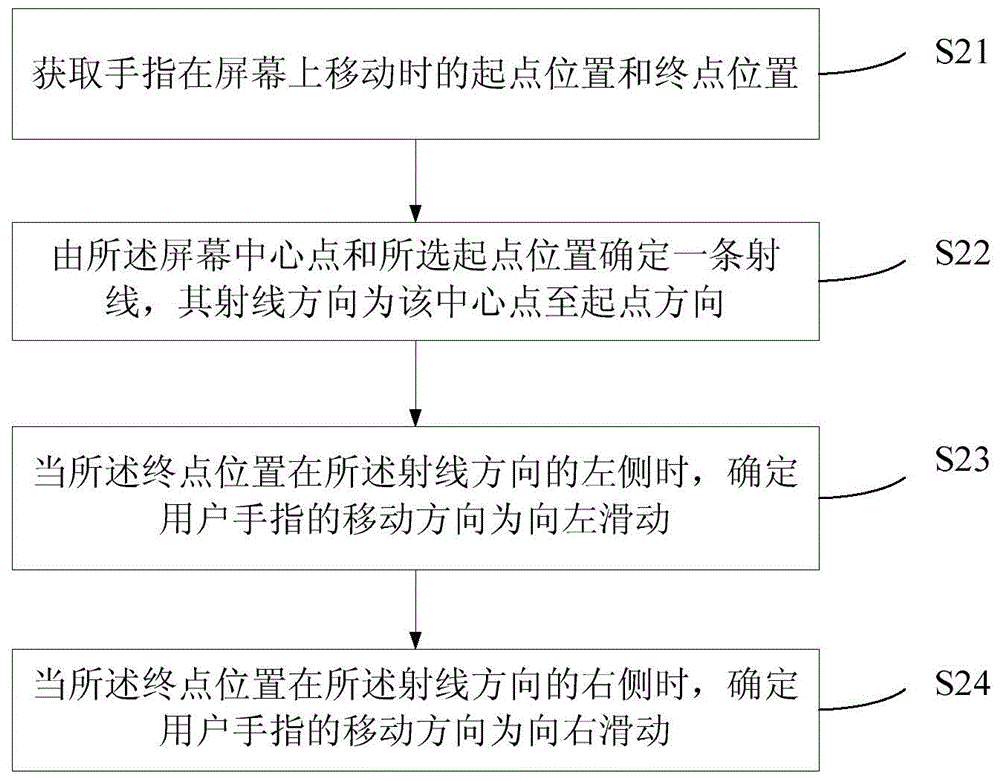
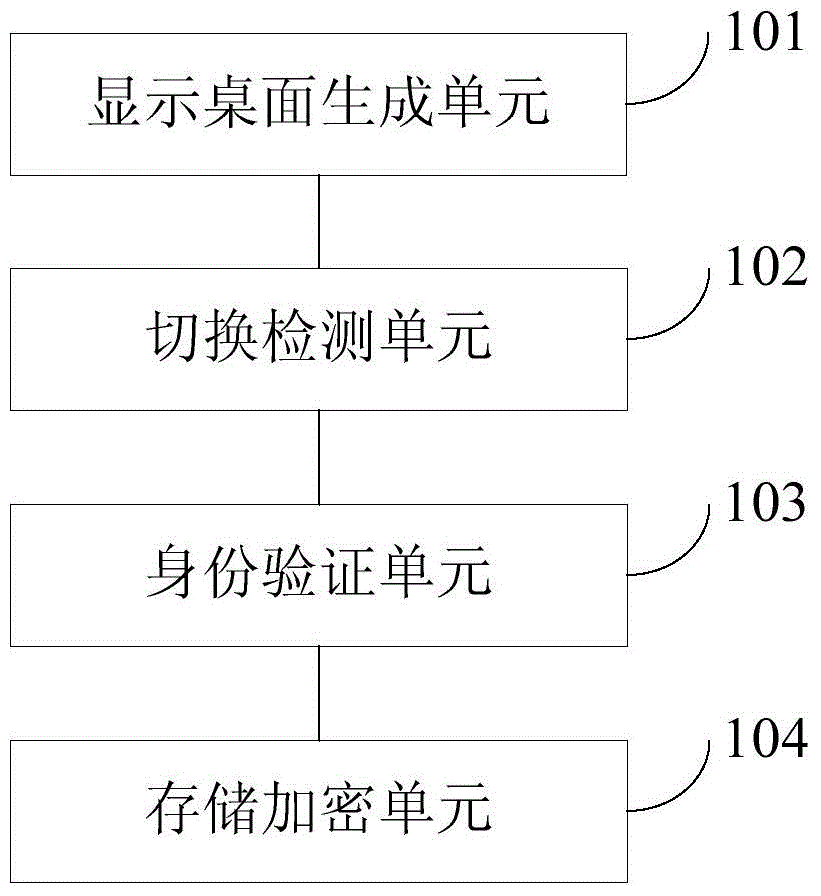
InactiveCN104834460AReduce the risk of information leakageReduce the Risk of ConfidentialityDigital data authenticationInput/output processes for data processingUser privacyUser authentication
The invention provides a desktop display control method and device and a mobile terminal. The method comprises the following steps: according to the task attribute and the application level of an application program, establishing one or a plurality of application program lists by all application programs of a terminal, and independently generating a plurality of display desktops by each application program according to a prestored interface display style; detecting a sliding event to a touch display screen by a user, and switching the display desktops according to the movement direction and the movement position of a finger of the user; according to a preset configuration strategy, carrying out user identity verification, and switching to a target display desktop after the user identity is successfully verified; and carrying out encrypted storage on the private data of the application programs on the current display desktop. The application programs are subjected to centralized management under different tasks, time for users to look up applications is shortened, different desktops are switched through a way of screen sliding, so that the desktop display control method is simple, easy in use and convenient in operation, user privacy can be prevented from being leaked through a setting of encrypted storage, and safety is improved to a certain degree.
Owner:DATA COMM SCI & TECH RES INST
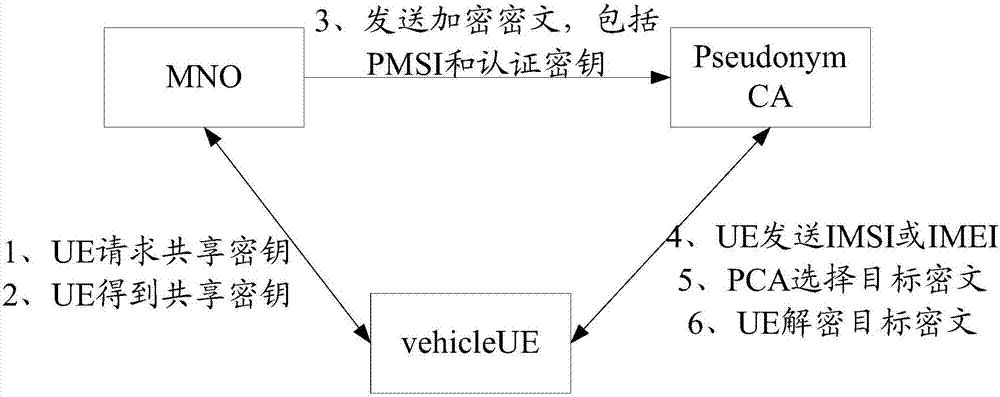
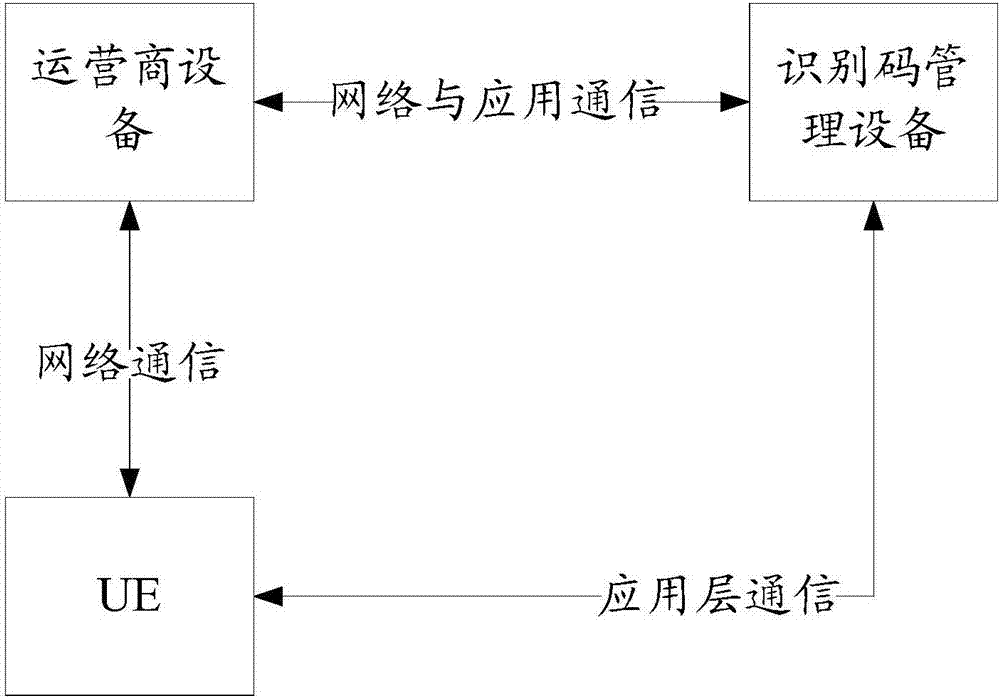
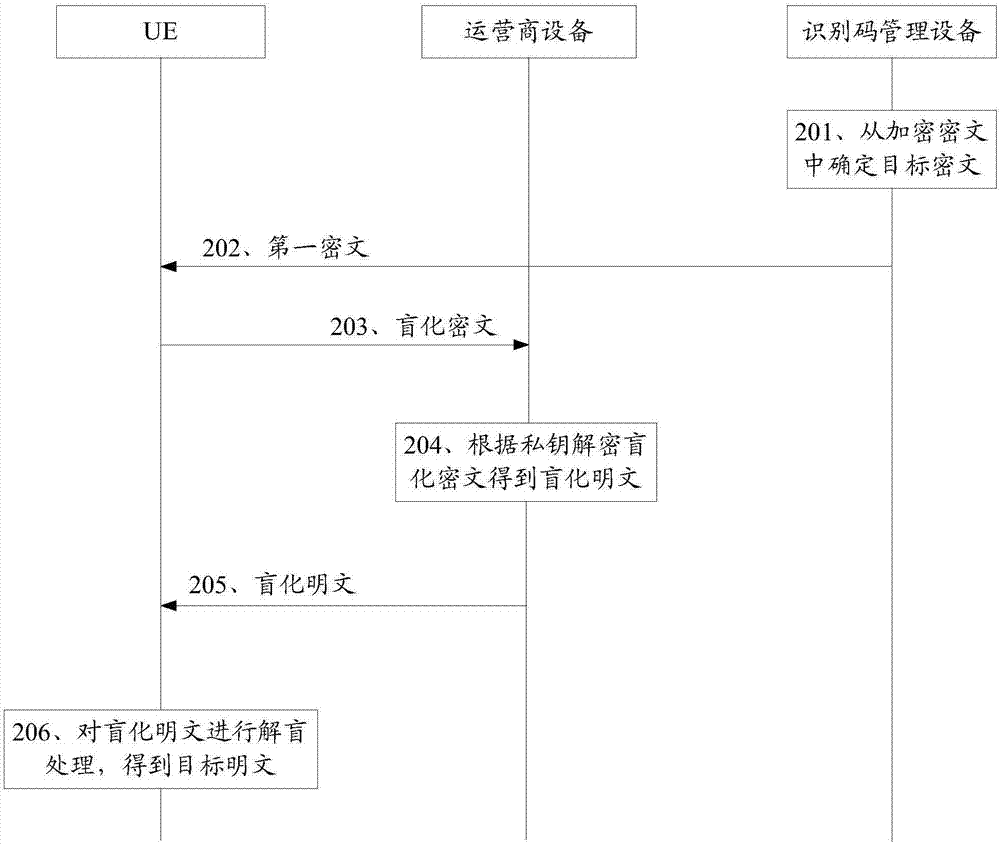
Privacy protection method and related equipment
The embodiment of the invention discloses a privacy protection method and related equipment. The method is used for reducing leakage risk when ciphertext transmission is carried out. The method provided by the embodiment of the invention comprises the steps that operator equipment receives a blind ciphertext sent by user equipment (UE), wherein the blind ciphertext is an identity ID suite obtainedthrough encryption and blinding processing, and the ID suite comprises an identification code and authentication information; and the operator device decrypts the blind ciphertext according to a private key, thereby acquiring a blind plaintext, and the operator equipment sends the blind plaintext to the UE. The embodiment of the invention also provides the related equipment. According to the embodiment of the invention, the leakage risk when ciphertext transmission is carried out can be reduced.
Owner:HUAWEI TECH CO LTD
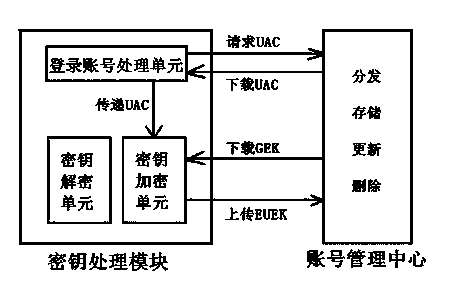
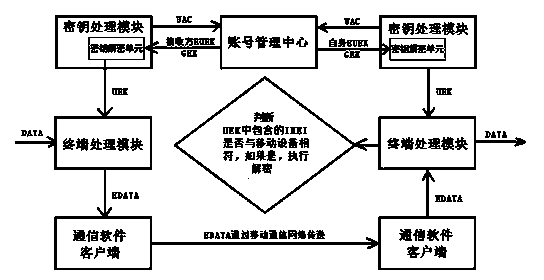
End-to-end encryption method and system based on mobile network and communication client side
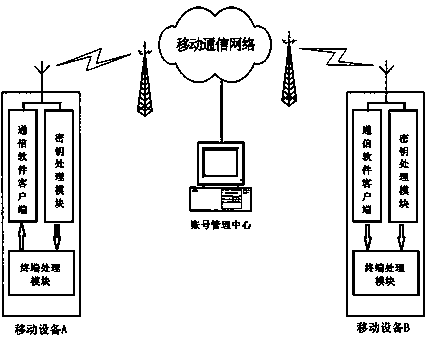
InactiveCN104270380AAvoid the defects of plaintext transmissionAvoid controlTransmissionSecurity arrangementPlaintextEnd-to-end encryption
The invention relates to an end-to-end encryption method based on a mobile network and a communication client side, and further relates to an end-to-end encryption system based on the mobile network and the communication client side. According to the encryption method, the symmetric encryption algorithm is adopted to carry out data encryption, an account number managing center is used for managing the identity and a secret key of an authorized user, a secret key processing module is used for carrying out secret key encryption and decryption on a secrecy system, a terminal processing module is used for carrying out encryption or decryption on the plaintext or ciphertext data information through the symmetric encryption algorithm, and a communication software client side is used for transmitting enciphered data, and accordingly the end-to-end enciphered data interaction is achieved. The encryption system comprises the account number managing center, the secret key processing module and the terminal processing module, the account number management center and the secret key processing module interact through the mobile communication network, the terminal processing module interacts with the enciphered data through the communication software client side, and encryption or decryption on the terminal processing module is achieved. The end-to-end encryption method and the end-to-end encryption system are good in encryption safety and capable of being used for various mobile communication platforms.
Owner:叶涛
Face recognition method and system
ActiveCN104821942AImprove recognition efficiencyReduce computationCharacter and pattern recognitionTransmissionPattern recognitionCiphertext
The invention relates to a face recognition method and system. The method comprises receiving face encryption data, a full homomorphic encryption key, an additive homomorphic encryption key and a key ciphertext; then based on the principle of an additive homomorphic encryption algorithm and the principle of a full homomorphic encryption algorithm, converting average face projection encryption data corresponding to each eigen face, face encryption data and each eigen face into a projection face additive homomorphic encryption ciphertext; encrypting additive values of the encryption ciphertext respectively with a matching threshold ciphertext, the projection face additive homomorphic encryption ciphertext and an additive homomorphic encryption ciphertext of each distance square to generate a full homomorphic ciphertext collection; and based on a preset matching threshold, each distance square and preset matching rules among different face markers, converting the full homomorphic ciphertext collection into a full homomorphic encryption ciphertext containing recognition results of the face markers. The face recognition efficiency and suitable range are improved while leakage risks of face data of users can be reduced.
Owner:GUANGZHOU UNIVERSITY +1
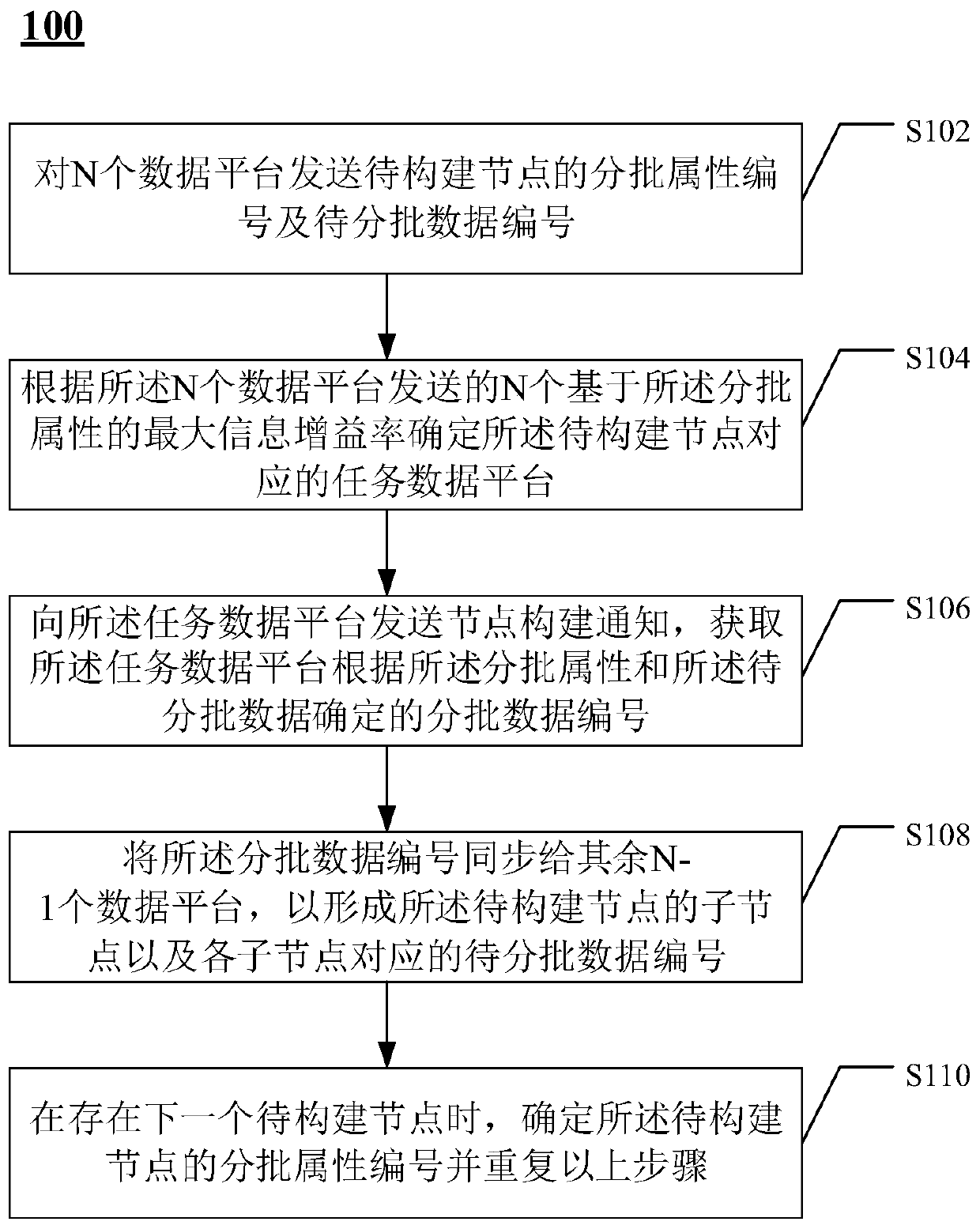
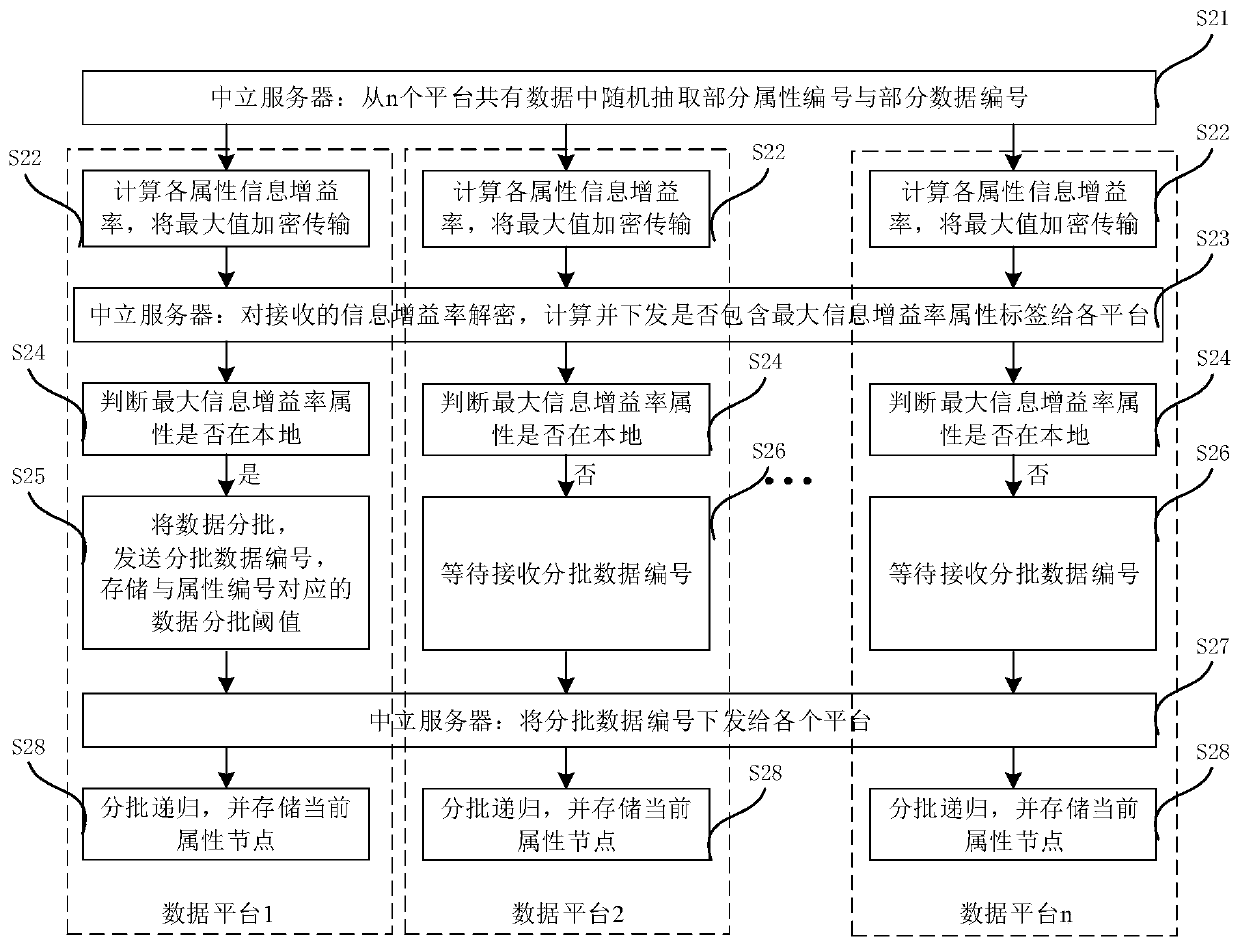
Decision model construction method, decision method and decision model
PendingCN110309587AMaintain data confidentialityReduce interactionCharacter and pattern recognitionDesign optimisation/simulationDecision modelConfidentiality
The invention provides a decision model construction method, a decision method and a decision model. The method comprises the following steps of sending an attribute number and a to-be-batched data number used by a to-be-constructed node in the current iteration to N data platforms; determining a task data platform corresponding to the to-be-constructed node according to the N maximum informationgain rates based on the batch attribute numbers sent by the N data platforms; sending a node construction notification to the task data platform, and obtaining a batch data number determined by the task data platform according to the batch attribute number and the to-be-batched data number; synchronizing the batch data numbers to the rest N-1 data platforms to form the child nodes of the to-be-constructed node and the to-be-batch data numbers corresponding to the child nodes; and when the next to-be-constructed node exists, determining the batch attribute number of the to-be-constructed node and repeating the above steps. According to the decision model construction method provided by the invention, the data interaction during a multi-platform joint modeling process can be reduced, and thedata confidentiality is improved.
Owner:JINGDONG CITY BEIJING DIGITS TECH CO LTD
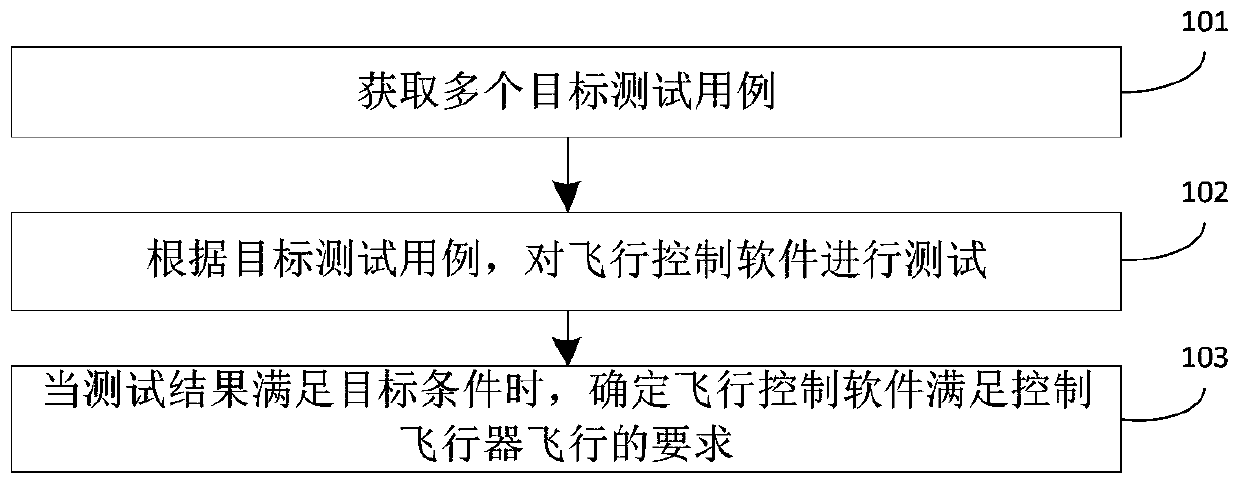
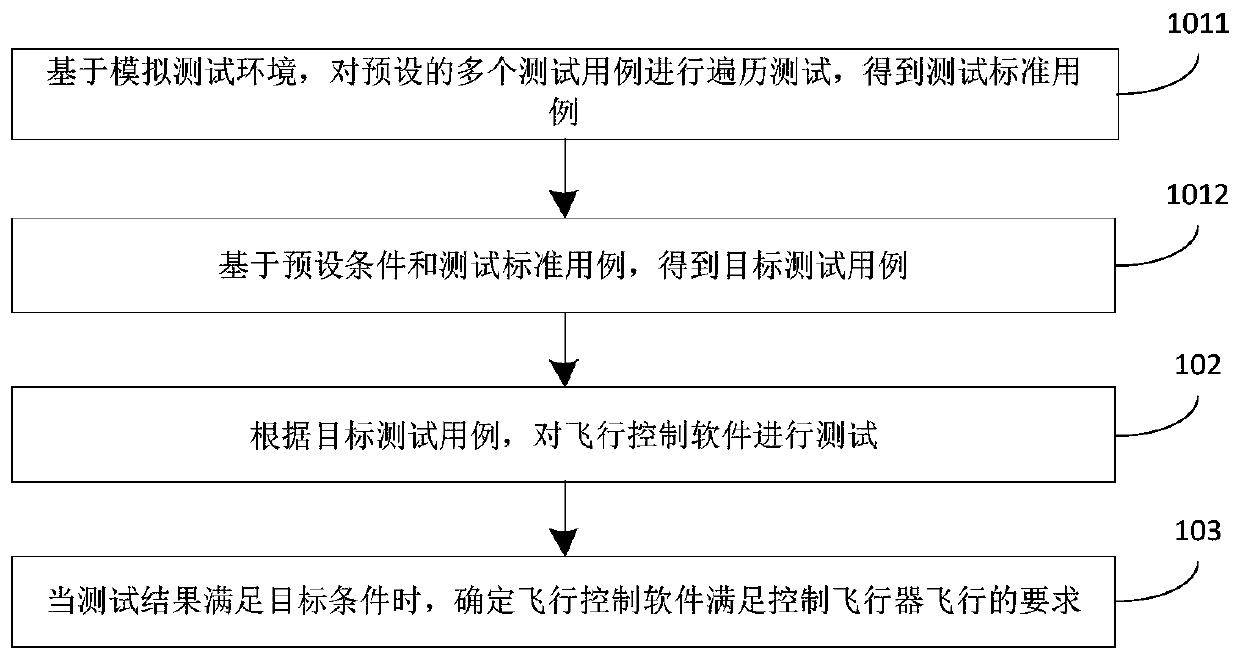
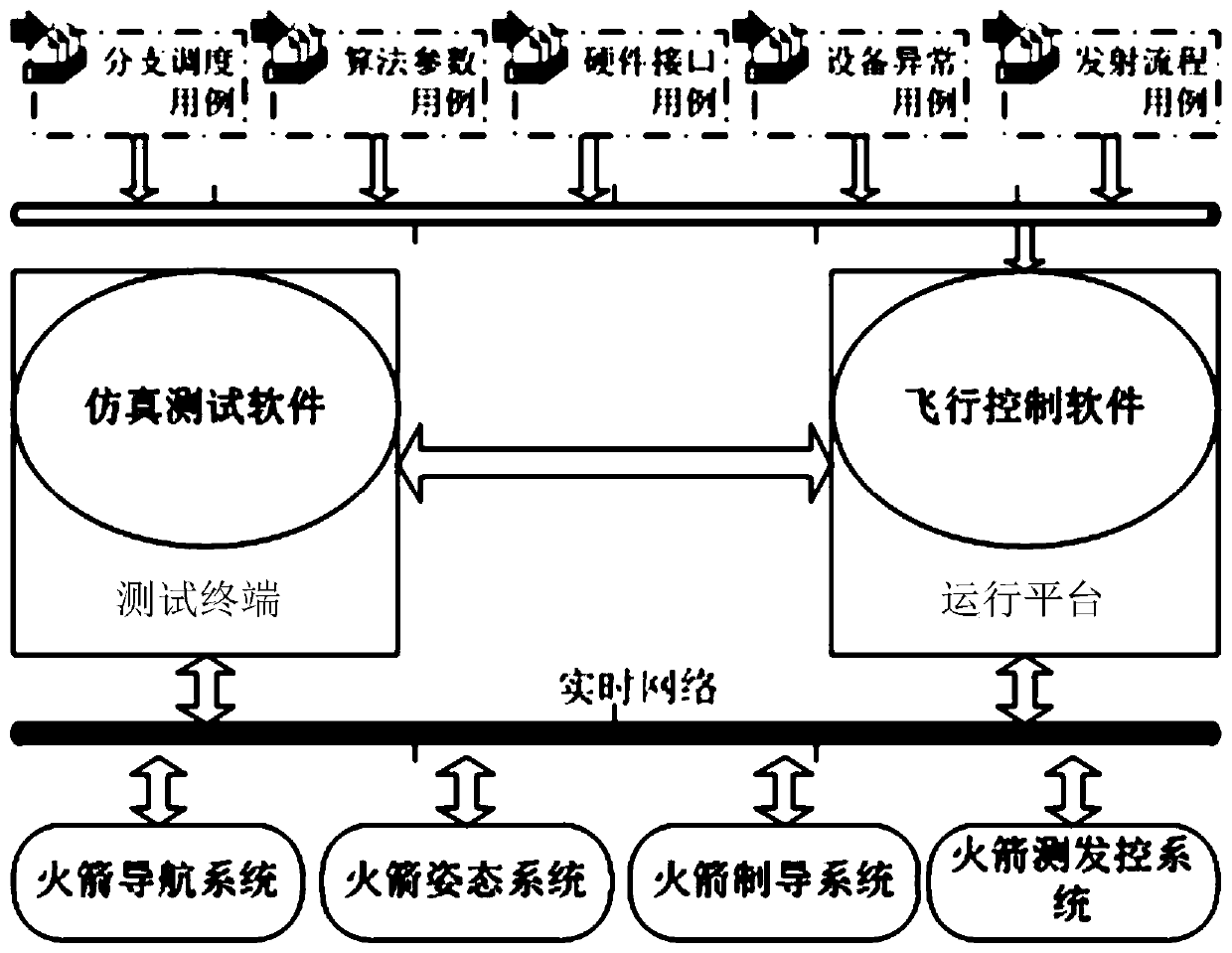
Flight control software evaluation method, device and system
InactiveCN110941561AIncrease coverageImprove accuracySoftware testing/debuggingThird partyTest efficiency
The invention discloses a flight control software evaluation method, device and system. An operation platform where flight control software is located is in communication connection with a target simulation system, and the flight control software evaluation method comprises the steps: obtaining a plurality of target test cases; testing flight control software according to the target test case; andwhen the test result meets the target condition, determining that the flight control software meets the requirement of controlling the flight of the aircraft. In the process of testing the flight control software, a control result of the flight control software in the actual target simulation system is acquired in real time; the problems that when a traditional third party is adopted for flight control software evaluation, the algorithm of flight control software cannot be tested, control parameters are inaccurate, software and hardware are not matched and the like are solved, and the test result coverage rate, the test result accuracy and the test efficiency of the flight control software are improved.
Owner:BEIJING XINGJI RONGYAO SPACE TECH CO LTD +1
Key management method and system
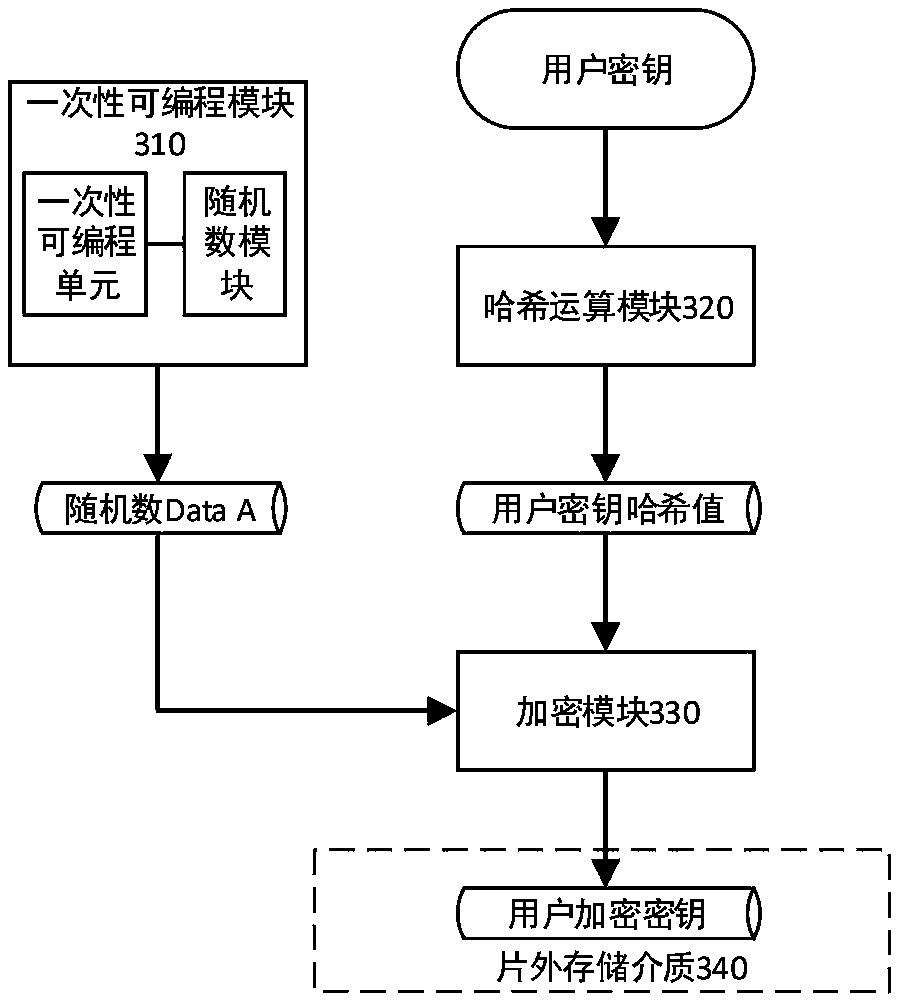
ActiveCN111131130AReach hardware level protectionReduce the Risk of ConfidentialityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesEngineeringInformation security
The invention discloses a key management method and system, and relates to the field of information security. According to the main technical scheme of the invention, the method comprises the steps ofreceiving an input user key, and carrying out Hash operation on the user key to obtain a user key Hash value; and reading an encrypted value of a data key from a storage medium, decrypting the encrypted value of the data key by using the user key hash value to obtain the data key, and encrypting or decrypting user data by using the data key. By adopting the key management method and system provided by the invention, software running in storage equipment cannot directly access the key for encrypting and decrypting the data, so that hardware-level protection of the key is achieved, and the riskof secret leakage is reduced.
Owner:BEIJING STARBLAZE TECH CO LTD
Method for realizing secure access of data in hard disk
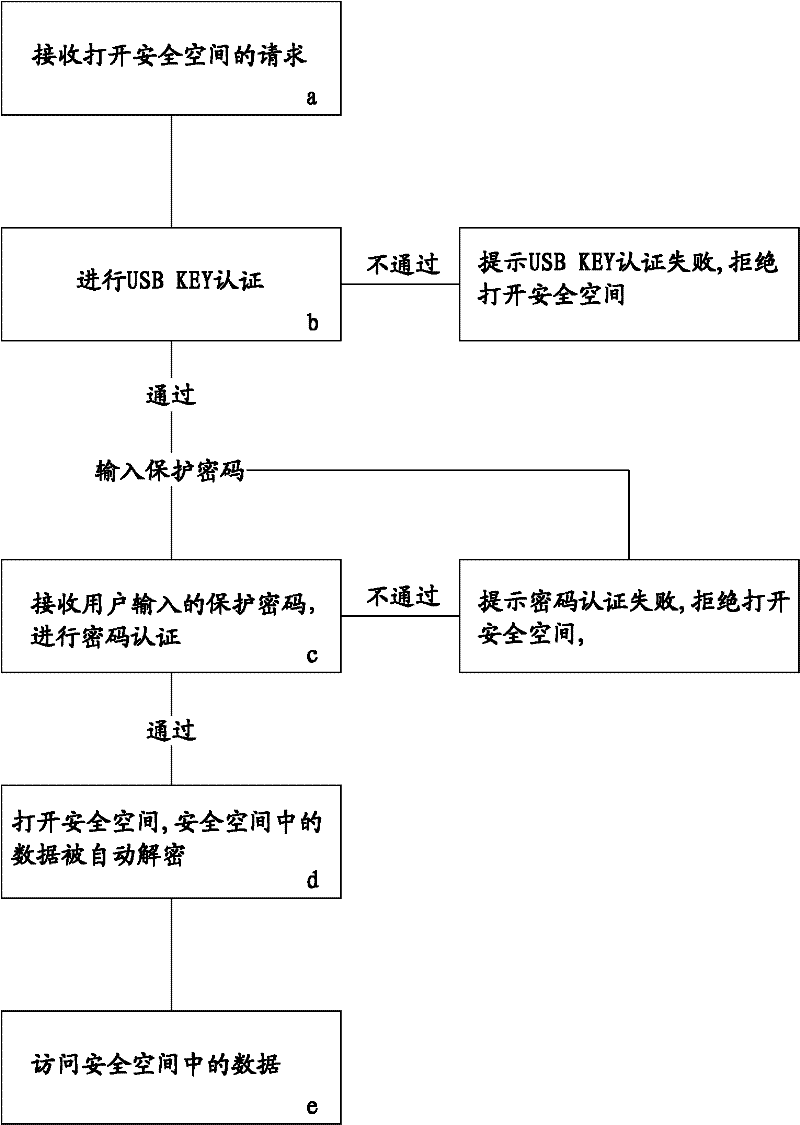
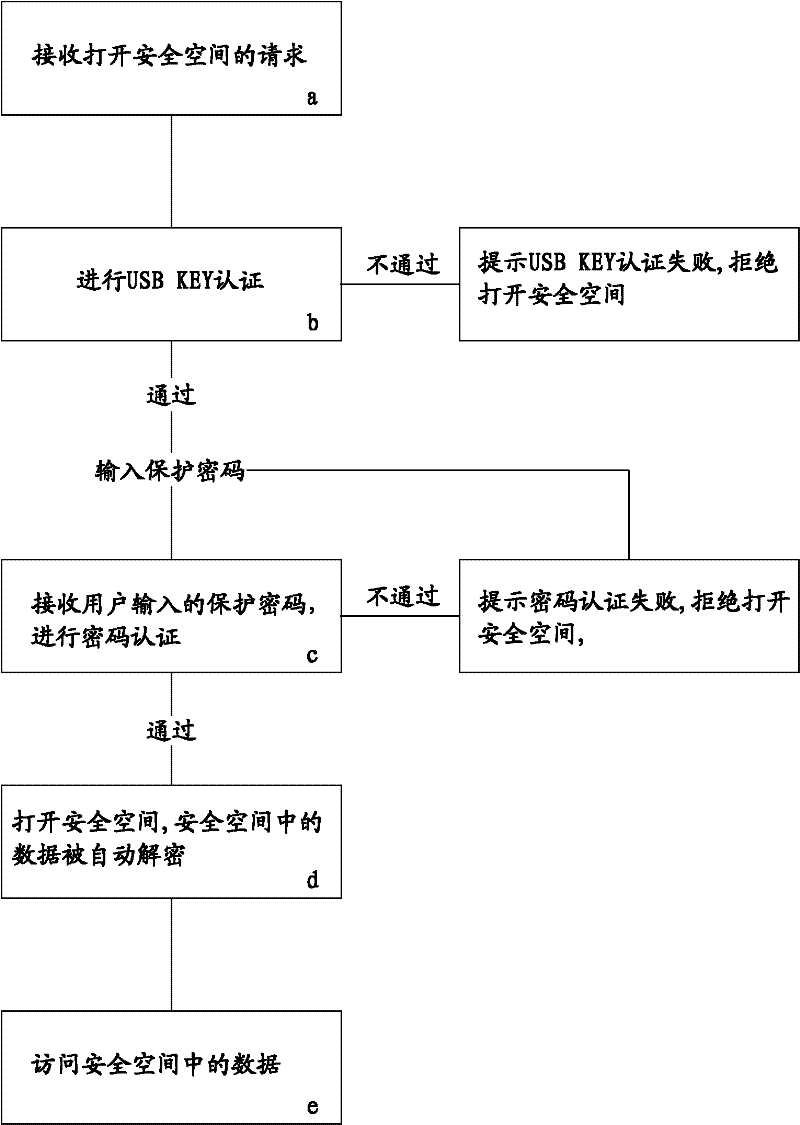
ActiveCN102508792ARealize active defenseImplement proactive alertsUnauthorized memory use protectionDigital data protectionPasswordSecret code
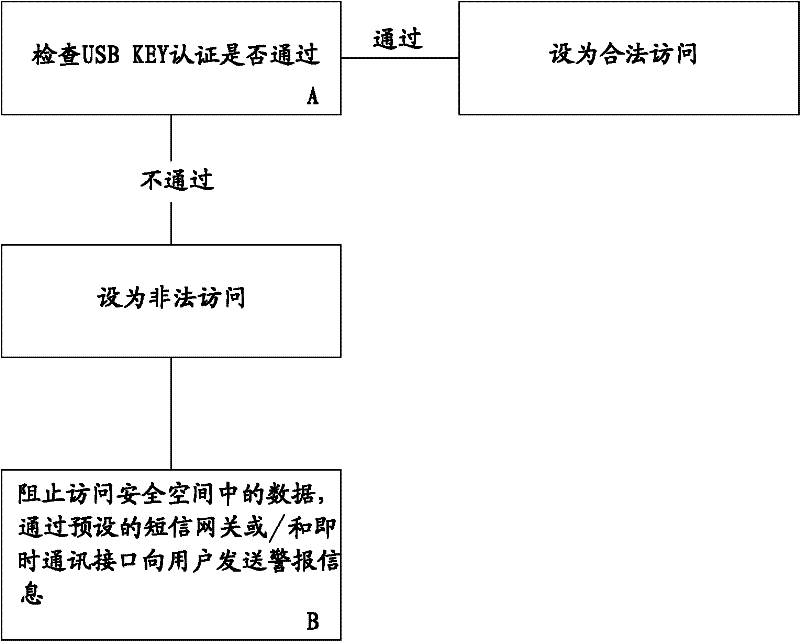
The invention discloses a method for realizing secure access of data in a hard disk. The method is realized by the following steps: establishing a secure space on the hard disk and monitoring the secure space; automatically encrypting the data written in the secure space; associating the secure space with a USBKEY; and setting protection passwords required for opening the secure space. When the data in the secure space is accessed, USBKEY authentication and passwords authentication are carried out in sequence, the secure space can be opened only after the double authentication; and when the situation that the data in the secure space is accessed but the secure space is not opened is monitored, whether the USBKEY authentication passes or not is checked, if not, the accessing is blocked, and a preset ISMG (internet short message gateway) or / and an instant communication port is / are used for sending an alarm information to a user. In the invention, by virtue of the double authentication and the monitoring on the secure space, the secret-divulging risk is reduced, the effects of safety, rapidness and easiness in use are achieved, and the active defense and active alarming are also realized, therefore, the safety is improved to the maximum extent.
Owner:GUANGZHOU SHINE TECH
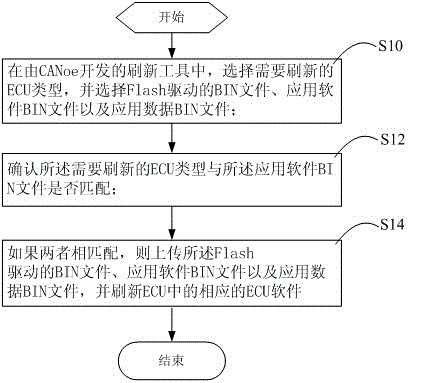
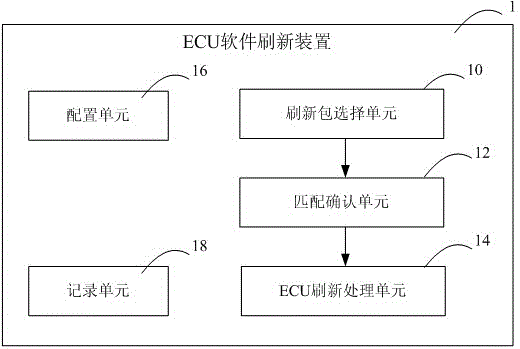
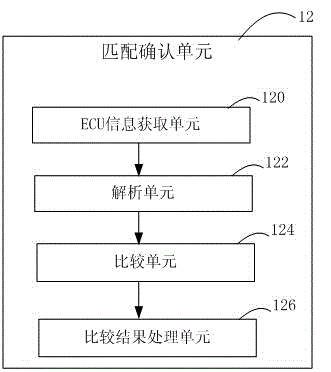
CANoe based ECU (Electronic Control Unit) software refresh method and apparatus
ActiveCN105278978AReduce development costsRealize independent developmentProgram loading/initiatingSoftware engineeringApplication software
An embodiment of the present invention provides a CANoe based ECU (Electronic Control Unit) software refresh method. The method comprises the following steps: in a refresh tool developed by using CANoe, selecting the type of an ECU that needs refreshing, and selecting a Flash drive BIN file, an application software BIN file and an application data BIN file; determining whether the type of the ECU that needs refreshing matches the application software BIN file or not; and if the two matches each other, uploading the Flash drive BIN file, the application software BIN file and the application data BIN file, and refreshing corresponding ECU software in the ECU. An embodiment of the present invention provides a CANoe based ECU software refresh apparatus. With implementation of the CANoe based ECU software method and apparatus provided by the embodiments of the present invention, refresh cost of the ECU software can be reduced, dependence on a provider can be reduced, and security is improved.
Owner:GUANGZHOU AUTOMOBILE GROUP CO LTD
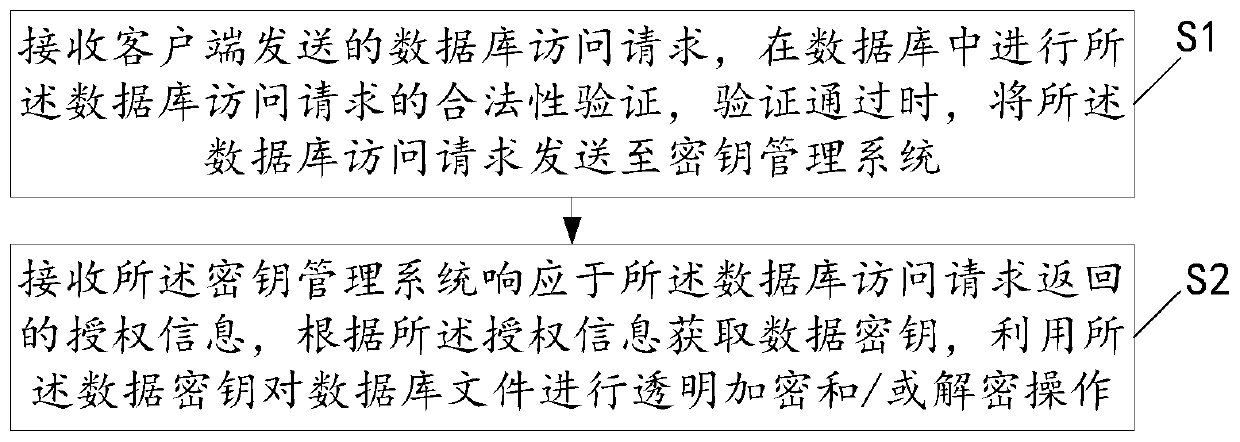
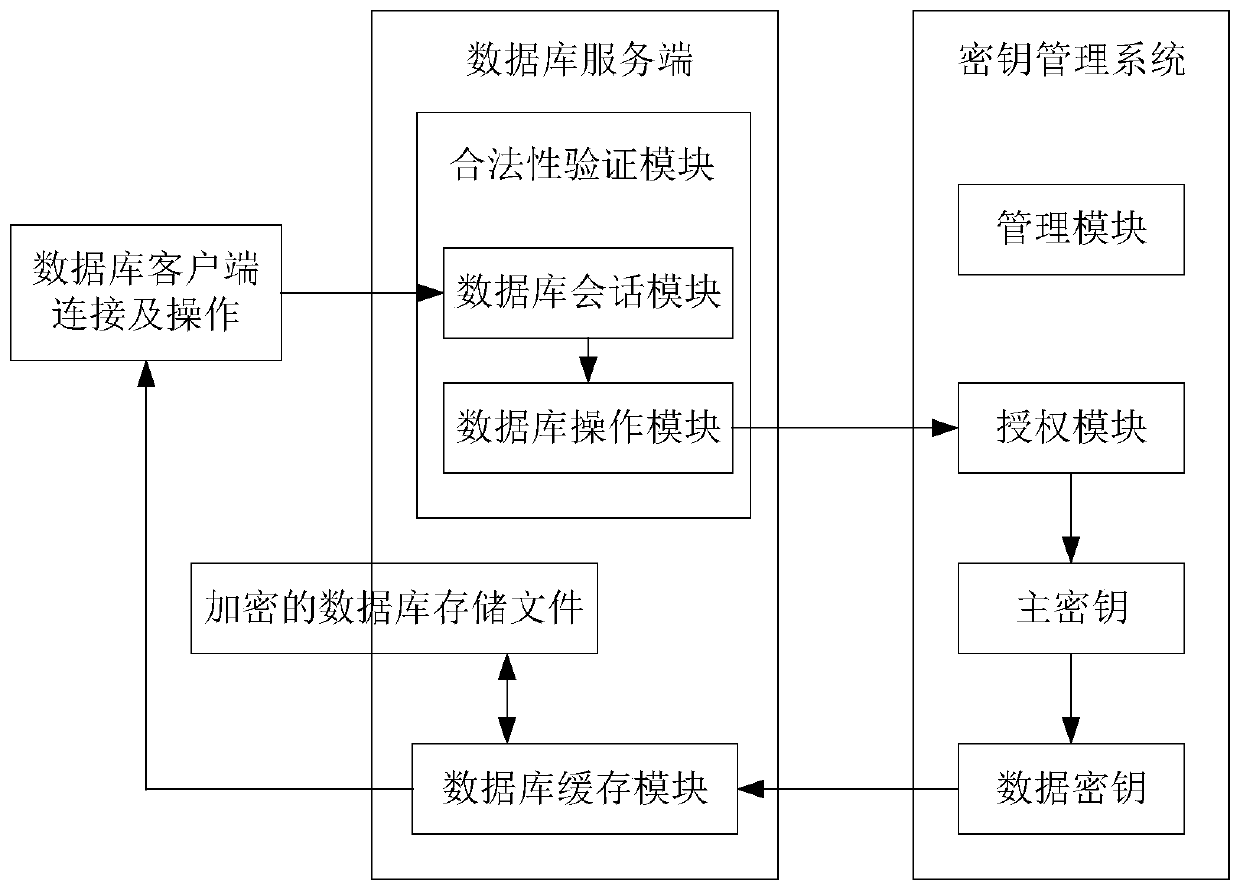
Database data safety management method and system
ActiveCN110489996AGuaranteed speedReduce the Risk of ConfidentialityDigital data protectionSafety management systemsDatabase file
The invention relates to the technical field of information safety, and discloses a database data safety management method. The method comprises the following steps: receiving a database access request sent by a client, carrying out legality verification on the database access request, and sending the database access request to a key management system when the verification is passed; and receivingauthorization information returned by the key management system in response to the database access request, obtaining a data key according to the authorization information, and performing transparentencryption and / or decryption operation on a database file by utilizing the data key. According to the invention, transparent encryption and decryption operation is carried out by using the data key from the system file level, so that the quickness of data encryption and decryption can be ensured; and the permission of the data key is controlled through the key management system, so that the safety is considered under the condition of ensuring the data encryption and decryption rapidness. The invention further discloses a database data safety management system.
Owner:山东三未信安信息科技有限公司
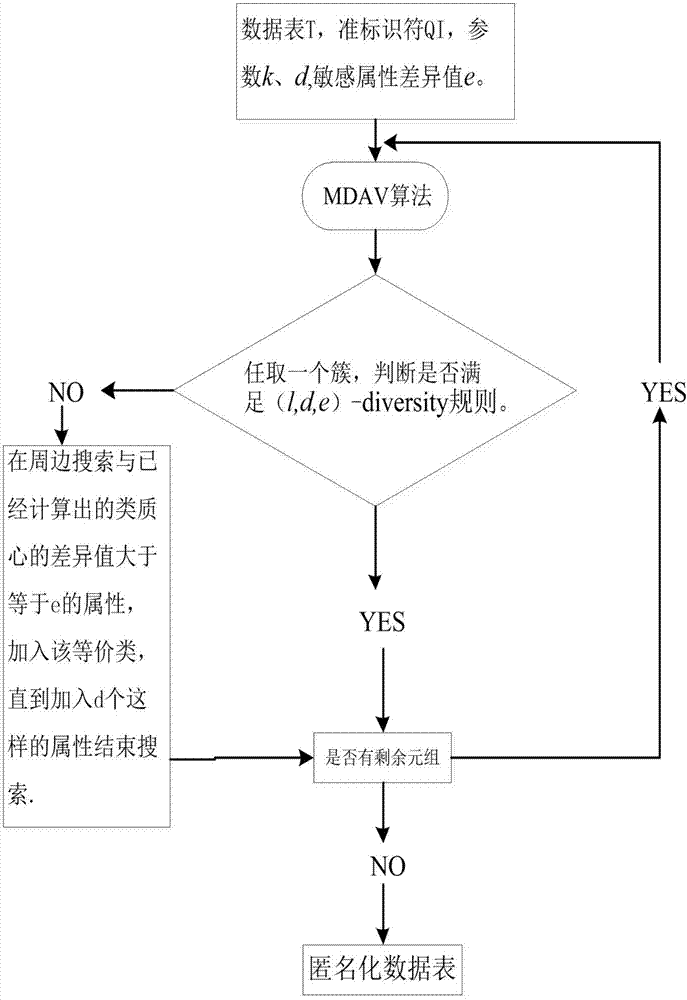
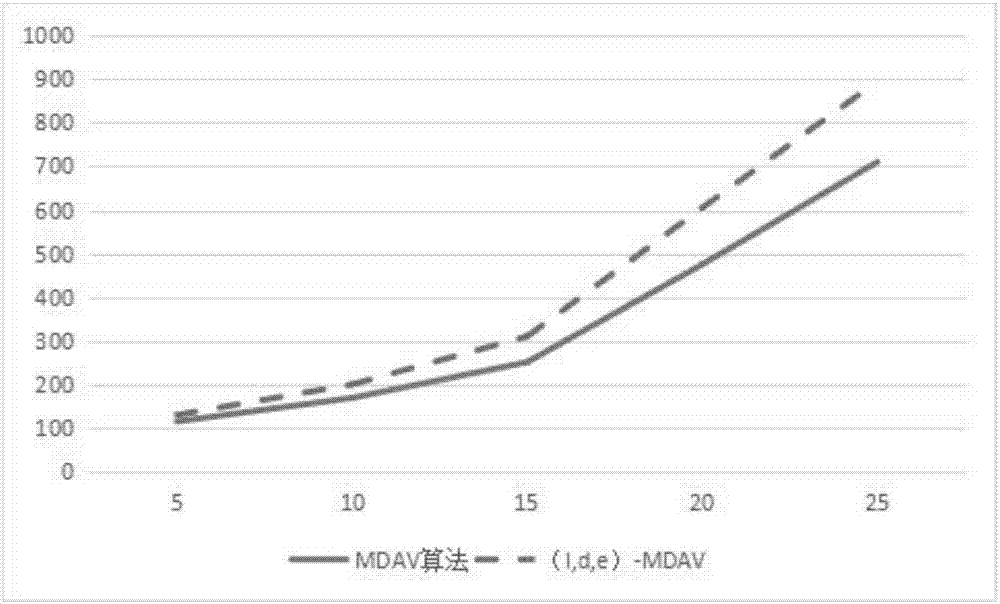
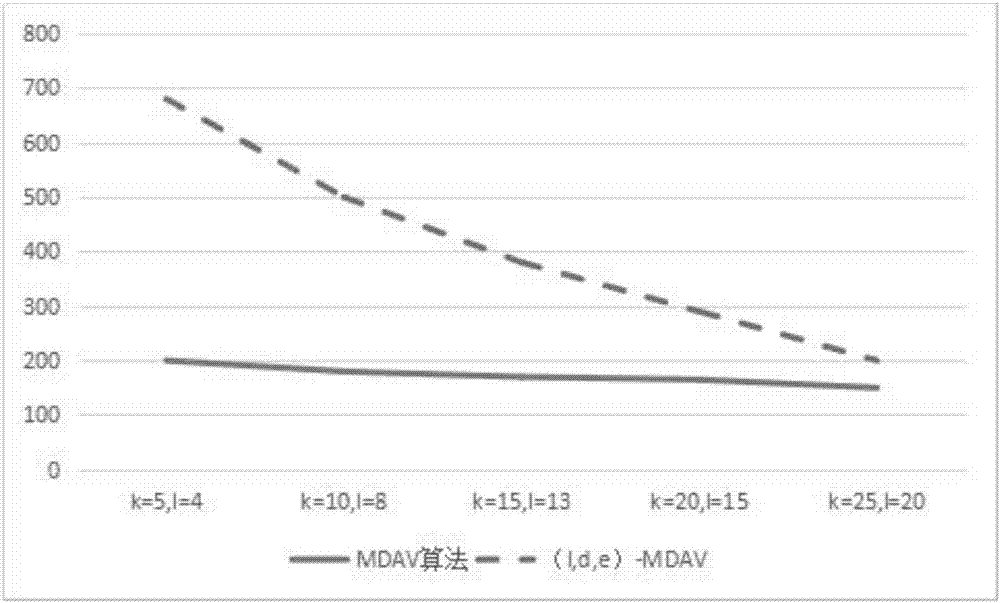
Method for processing big data based on l-diversity rules and MDAV algorithm
ActiveCN107273757AMaximize privacy protectionShort calculation timeDigital data protectionPrivacy protectionPersonalization
The invention belongs to the technical field of privacy protection of a database and discloses a method for processing big data based on l-diversity rules and an MDAV algorithm. According to the method, the MDAV algorithm is improved, a new algorithm, namely an ''(l,d,e)-MDAV algorithm'' is generated, and compared with MDAV, the new algorithm can resist homogeneity attacks and effectively reduce information leakage risks while guaranteeing high efficiency and low information loss. It is proved through experiments that the new algorithm has a good effect on processing anonymization of data tables. According to the method, a manually-given difference value with a center of mass has personalized further research value. A user can set an e value according to the demand for self-confidentiality, and maximum privacy protection and a minimum leakage risk can be realized.
Owner:XIDIAN UNIV
Information full-text retrieval method and system based on intra-domain information access permission
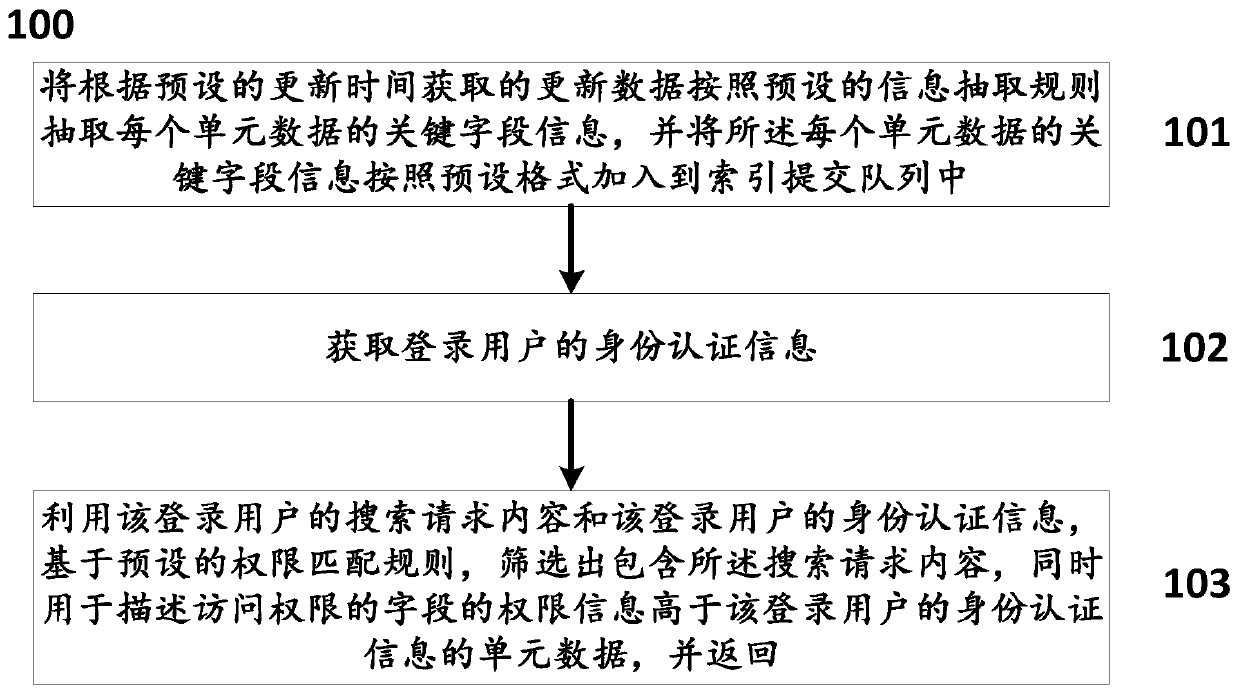
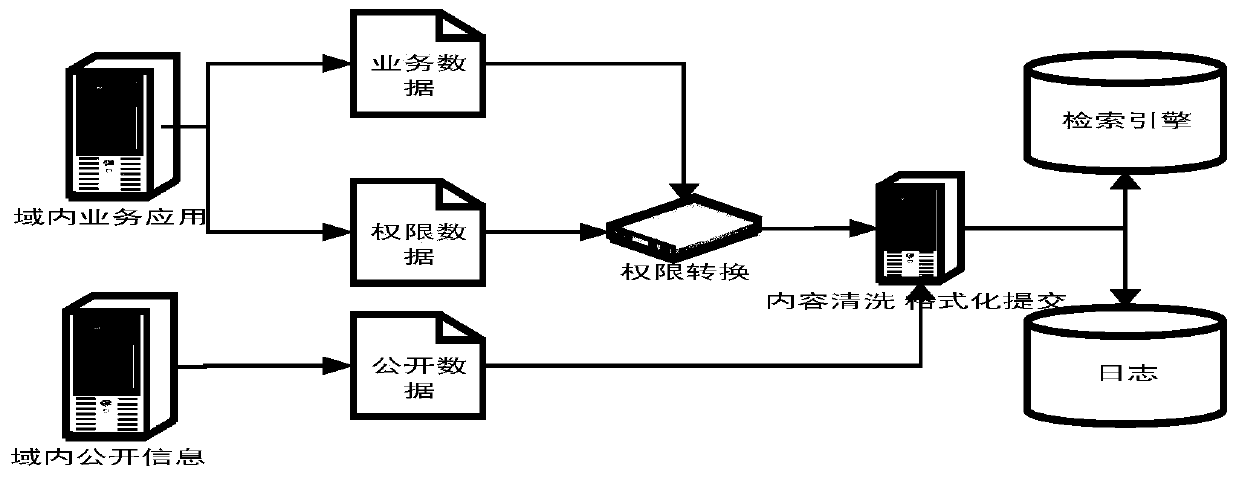
InactiveCN109857754AReduce the Risk of ConfidentialityImprove accuracyDatabase management systemsDigital data protectionInformation accessData mining
The invention discloses an information full-text retrieval method based on intra-domain information access permission, which comprises the following steps: extracting key field information of each unit data from updated data according to a preset information extraction rule, and adding the key field information into an index submission queue according to a preset format; obtaining identity authentication information of a login user; and screening unit data containing the search request content and a field for describing the access authority, the authority information of which is higher than the identity authentication information of the login user, based on a preset authority matching rule by utilizing the search request content of the login user and the identity authentication informationof the login user, and returning the unit data. The method is based on the Lucene search engine, the engine only returns data with right access during retrieval, secondary screening is not needed, and the risk of data leakage is reduced to the maximum extent. Meanwhile, the index is established through the keywords, the matching speed is high, the accuracy is high, high concurrency support of Lucene is quite good, and the search efficiency in the high concurrency environment is guaranteed.
Owner:HUADI COMP GROUP
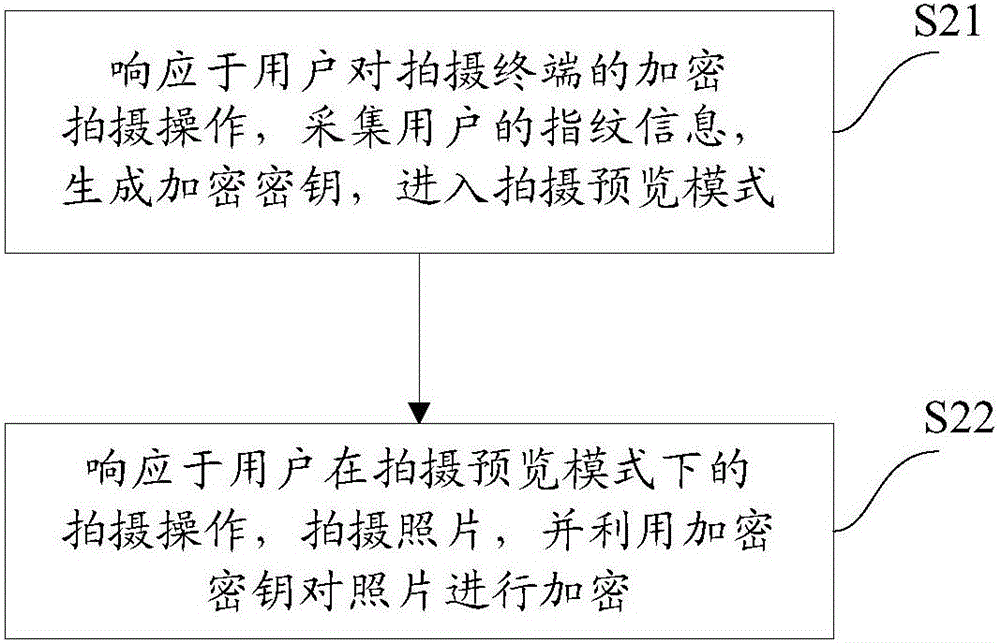
Photograph encryption method for shooting terminal and system
InactiveCN106161947AImprove encryption efficiencyImprove securityTelevision system detailsColor television detailsEncryption system
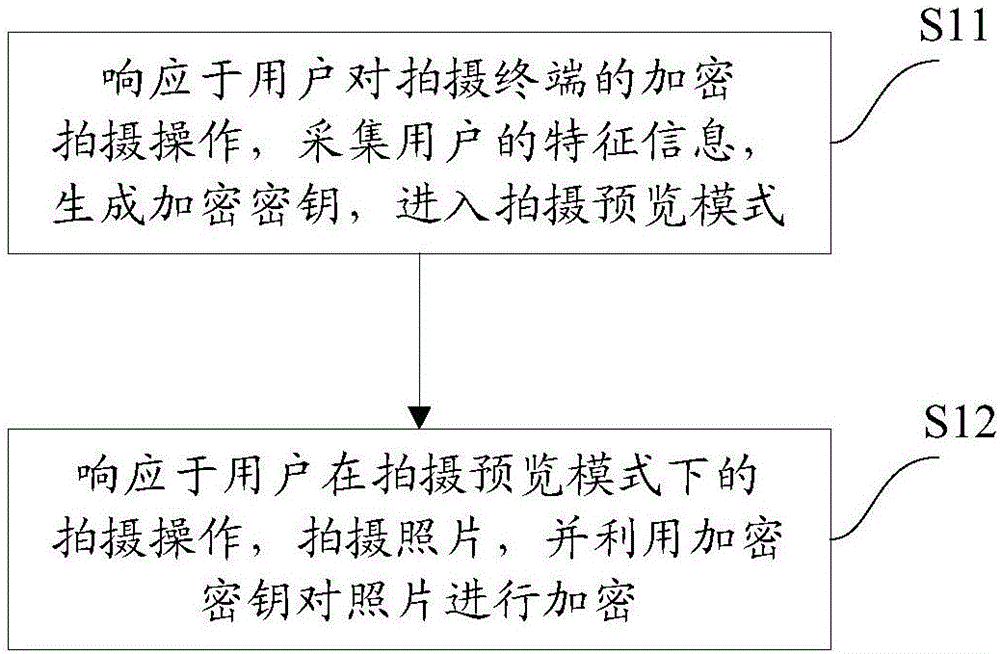
The embodiment of the invention provides a photograph encryption method for a shooting terminal. The method comprises the following steps: responding to an encryption shooting operation of the user for the shooting terminal; collecting characteristic information of the user; generating an encryption key; entering into a shooting preview mode; responding to the shooting operation of the user under the shooting preview mode; shooting photos and utilizing the encryption key to encrypt the photos. The embodiment of the invention also provides a photograph encryption system for the shooting terminal. According to the method and system, the user characteristic information is collected for generating the encryption key, and meanwhile, the shot photograph is encrypted, so that the user operation can be effectively reduced, the encryption efficiency is increased, the personal privacy leakage risk of the user is effectively reduced and the function of the shooting terminal is added.
Owner:LETV HLDG BEIJING CO LTD +1
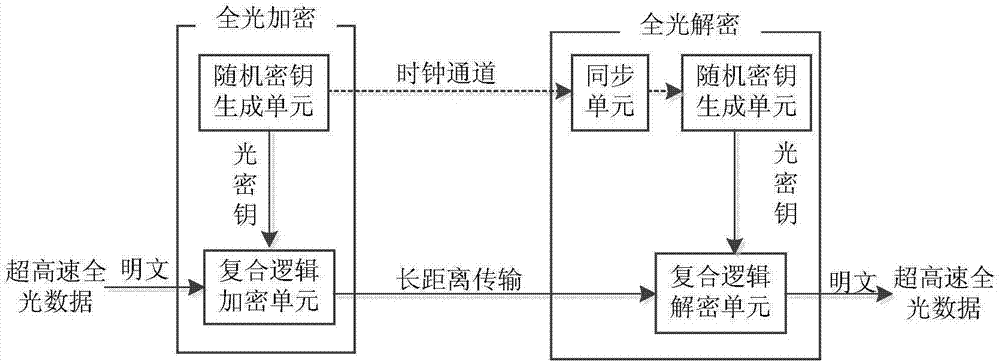
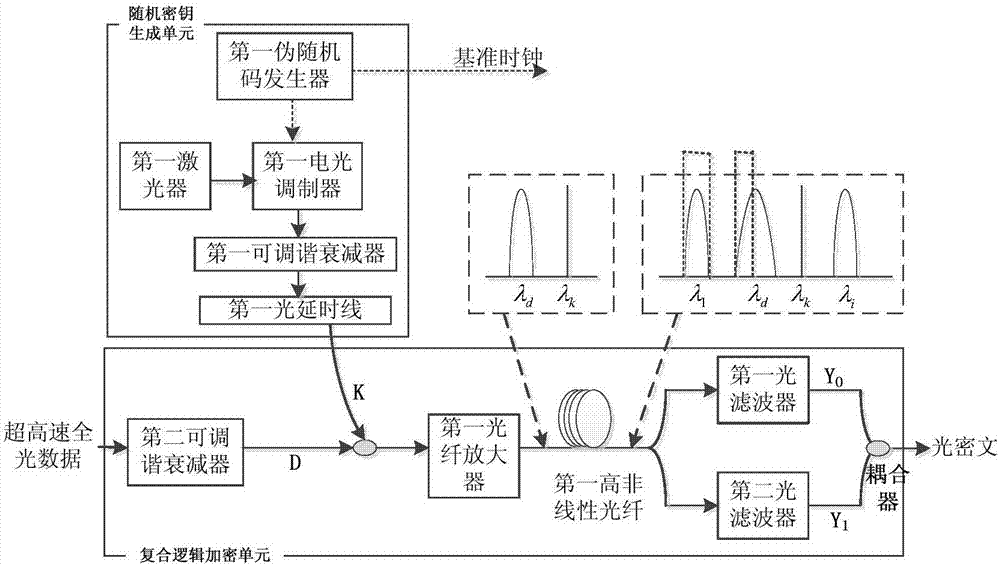
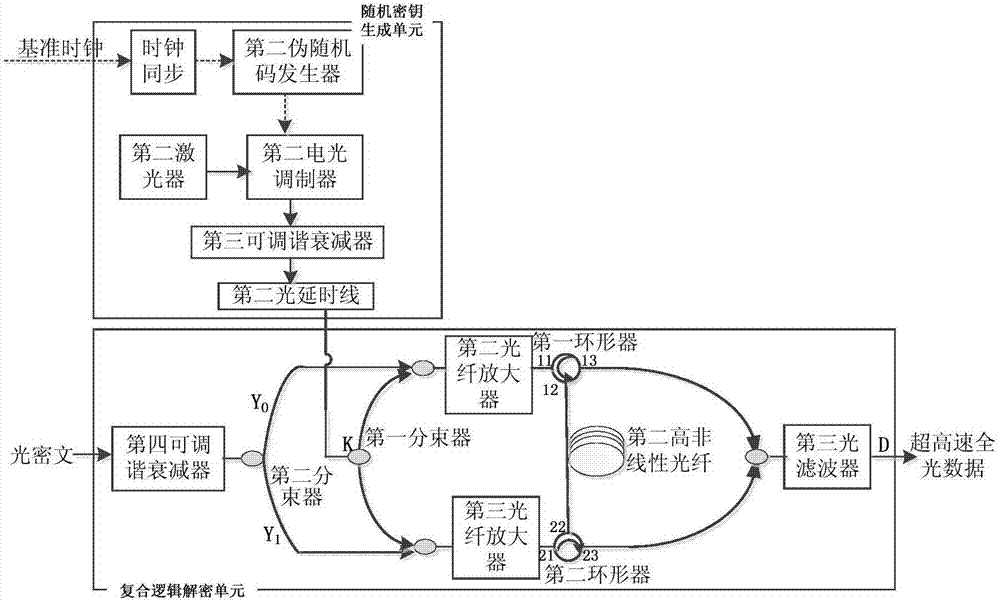
Ultrahigh-speed all-optical data real-time encryption/decryption systems and methods based on composite logic
ActiveCN106888053ARealize secure transmissionNot easy to interceptKey distribution for secure communicationFibre transmissionCiphertextCarrier signal
In order to solve the problems in the prior art, for example, all-optical data in the physical layer is easy to crack, and it is difficult to encrypt ultrahigh-speed data in real time, the invention provides ultrahigh-speed all-optical data real-time encryption / decryption systems and methods based on composite logic. The encryption method comprises the following steps: (1) generating a first electrical domain pseudo-random sequence and a reference clock; (2) loading the first electrical domain pseudo-random sequence onto a pulse laser carrier output by a first laser to produce an optical domain random encryption key; (3) injecting the optical domain random encryption key and to-be-encrypted ultrahigh-speed all-optical data together into a first optical fiber amplifier for optical power amplification; (3) injecting the amplified optical domain random encryption key and the amplified ultrahigh-speed all-optical data together into a first high-nonlinearity optical fiber to produce different logic in real time between the optical domain random encryption key and the ultrahigh-speed all-optical data; and (4) carrying out filtering at different wavelengths at the output end of the first high-nonlinearity optical fiber, and coupling two filtered wavelengths to form an optical cipher text with composite logic.
Owner:XI'AN INST OF OPTICS & FINE MECHANICS - CHINESE ACAD OF SCI
Digital number screen unlocking system and method combining strength and biological characteristic identification
InactiveCN105930708AReduce the Risk of ConfidentialityReduce stepsDigital data authenticationDigital numberPressure sense
The invention relates to a digital number screen unlocking system and method combining strength and biological characteristic identification. The system and the method are characterized in that an unlocking pressing signal is obtained through a touch screen, the unlocking pressing signal is sensed by a pressure sensing module to obtain an unlocking pressure value; a digital authentication interface is displayed on the touch screen and a verification pressing signal is obtained by a processing module according to the unlocking pressing signal and the unlocking pressure value; the pressing pressure value of the verification pressing signal is sensed by the pressure sensing module, the pressing pressure position is sensed by a position sensing module and the biological characteristic information is obtained through a biological characteristic identification module; the touch screen is unlocked by the processing module and a function application interface is displayed when the processing module determines that the pressing pressure value, the pressing pressure position and the biological characteristic information are simultaneously in consistent with a user set value.
Owner:SHENZHEN TINNO WIRELESS TECH
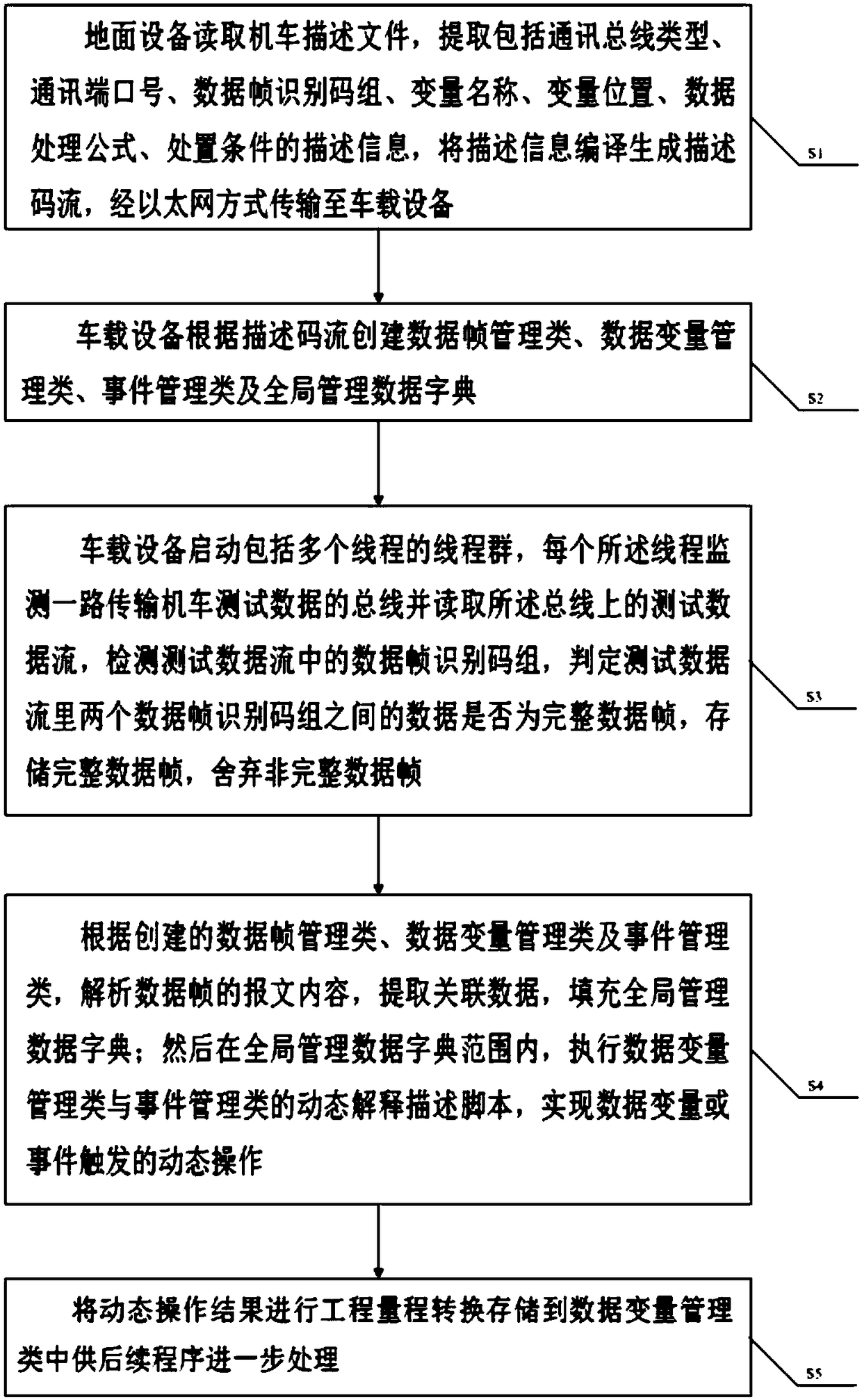
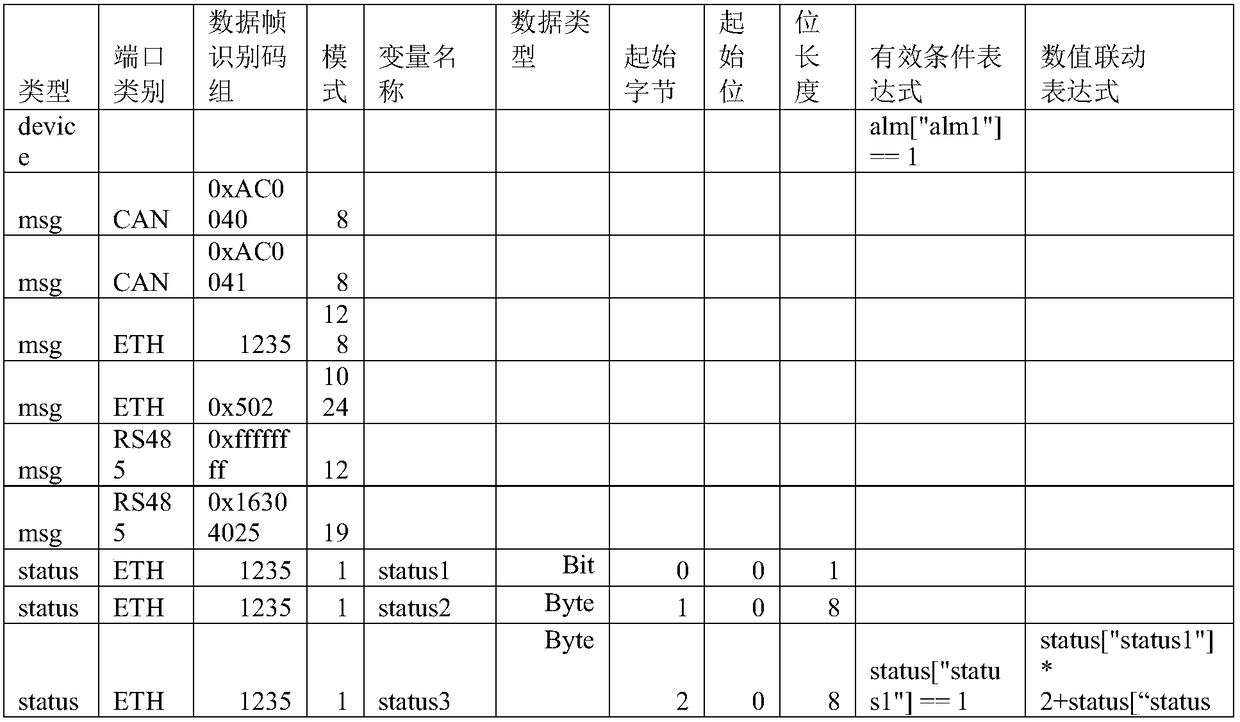
A method for dynamically analyze locomotive event data
ActiveCN109491660AClear business boundariesMeet data analysis needsCode compilationConfidentialityData acquisition
The invention provides a method for dynamically analyzing locomotive event data suitable for locomotive event data acquisition and processing system, a locomotive description file is use to store thatcommunication bus type, communication port number, data frame identifier group, variable position, data processing formula, description information such as disposal conditions, each description information corresponds to various buses and data transmission protocols of the buses. The ground equipment reads the description information and transmits it to the vehicle-mounted equipment. The vehicle-mounted equipment creates a data frame management class, a data variable management class, an event management class and a global management data dictionary according to the description information, and extracts, processes and stores the locomotive event information. When the data transfer format on the locomotive is updated, Modifying the locomotive description file can meet the needs of data analysis without modifying the software, which reduces the test requirements after the locomotive data change, saves the cost, makes the business boundary between the locomotive integration unit and thedata acquisition and processing system supplier clearer, and reduces the risk of confidentiality leakage of the locomotive integration unit.
Owner:大连莱克科技发展有限公司
Information processing method, device and system
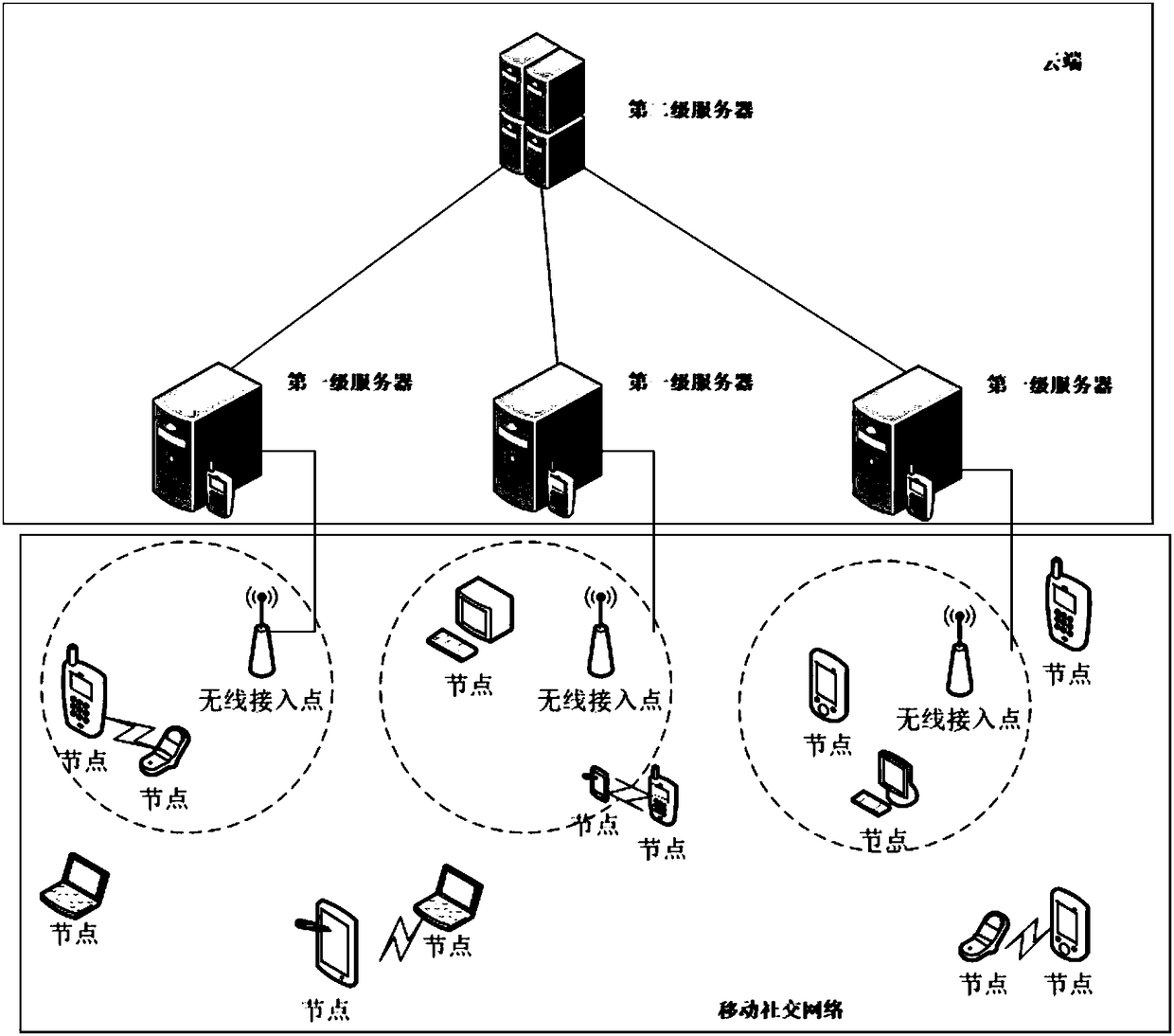
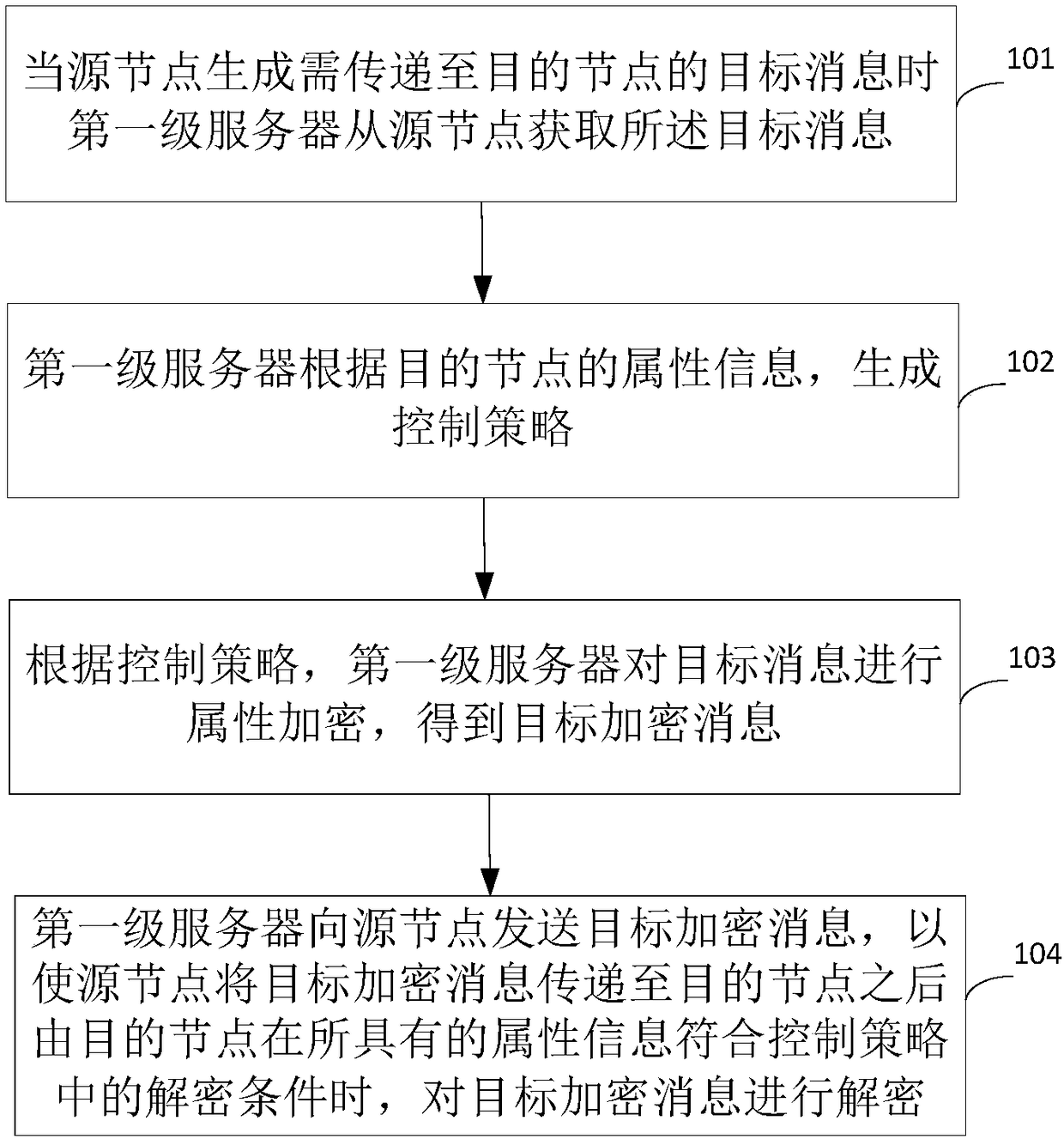
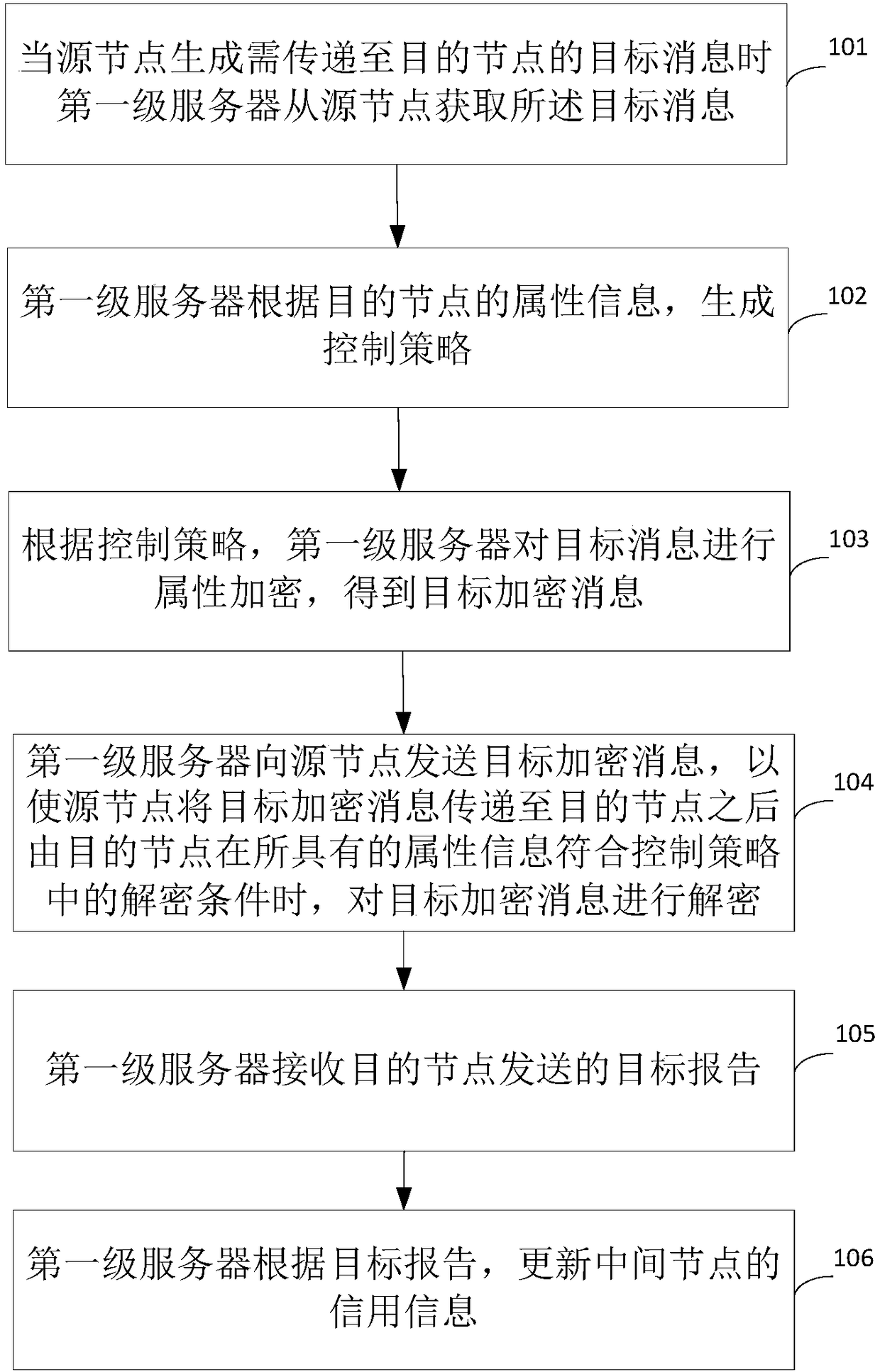
ActiveCN108737077AReduce loadReduce the Risk of ConfidentialityKey distribution for secure communicationPublic key for secure communicationInformation processingComputer hardware
The invention provides an information processing method, device and system. The method comprises the following steps that a first-level server acquires a target message from a source node in a processof transmitting the target message, so that a control strategy is generated according to attribute information of a destination node; and attribute encryption is carried out on the target message according to the control strategy, so that the source node transmits the target encrypted message. Due to the fact that the first-level server is adopted to encrypt the target message, a process of nodeencryption is avoided, and the load of the node is reduced. Meanwhile, due to the fact that an attribute encryption mode is adopted, even if a private key is leaked, decryption can be carried out onlywhen the attribute information of the decrypted node conforms to a decryption condition, and the risk of leakage is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Risk control method, risk control system and terminal equipment
InactiveCN110533268AReduce the Risk of ConfidentialityOnline flexible change flexibleFinanceResourcesRisk ControlTerminal equipment
The method is suitable for the financial field, provides a risk control method, a risk control system and terminal equipment, and the method comprises the steps: detecting whether there is a to-be-updated rule or / and model in the risk control system or not, wherein the rule and the model are stored at different positions, the rule is used for judging whether service data is legal or not, and the model is used for judging the application type of the service data; if the rule or / and model needing to be updated exist, updating the rule needing to be updated to be a specified rule, and / or updatingthe model needing to be updated to be a specified model, and obtaining the updated risk control system; and when service data is received, verifying the service data through the updated risk controlsystem. The rule and the model in the risk control system are subjected to module division, so that online flexible change of each module of the risk control system is realized, and meanwhile, the risk of leakage of service data is also reduced.
Owner:深圳福莱信息科技有限公司
Safety JTAG module and method for protecting safety of information inside chip
InactiveCN101620656BReduce security risksImprove data security featuresInternal/peripheral component protectionPasswordUser input
Owner:SHENZHEN STATE MICRO TECH CO LTD
Anti-theft alarm device of intelligent compact shelf
InactiveCN109801462AImprove reliabilityReduce the risk of personal information leakageCharacter and pattern recognitionBurglar alarmAnti theftAlarm device
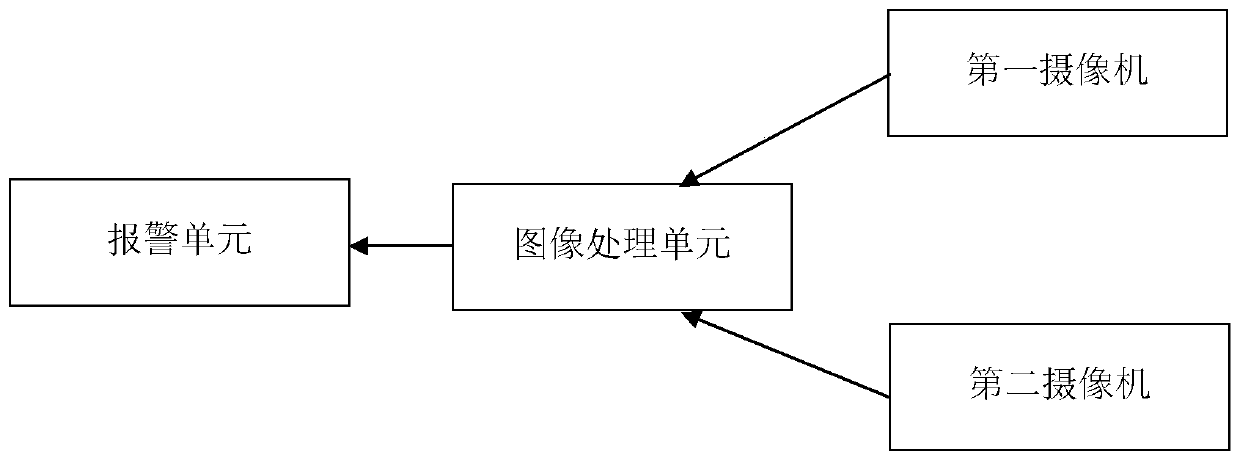
In order to enhance the safety of a compact shelf, the invention provides an anti-theft alarm device of an intelligent compact shelf. The device comprises an alarm unit, a first camera, a second camera and an image processing unit, wherein the image processing unit processes video frame information shot by the first camera and the second camera; and the alarm unit determines whether to generate analarm signal according to information output by the image processing unit.
Owner:JIANGXI SUNSHINE SAFETY EQUIP GRP CO LTD
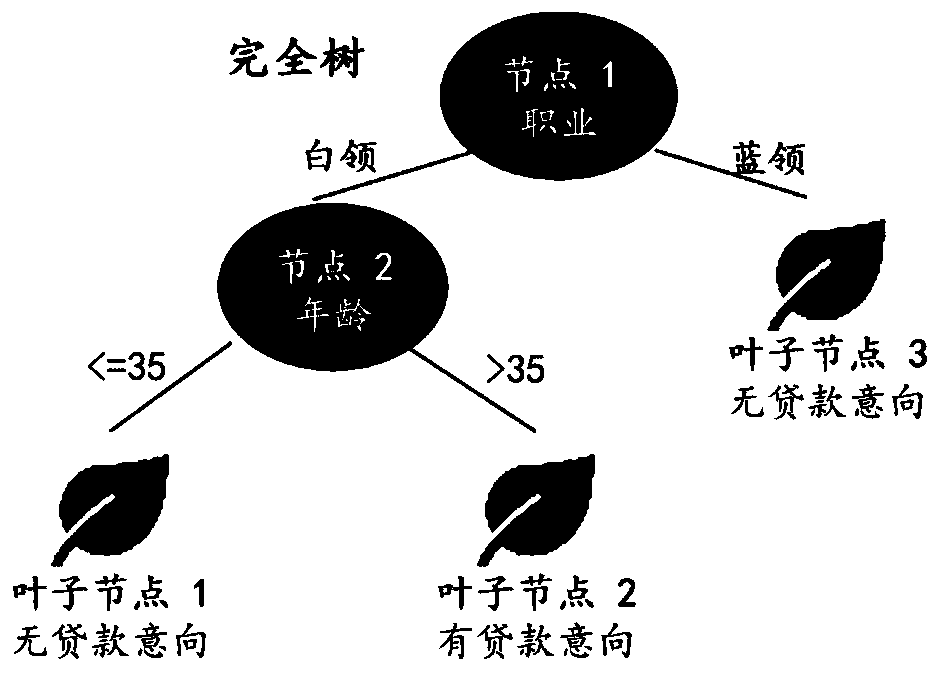
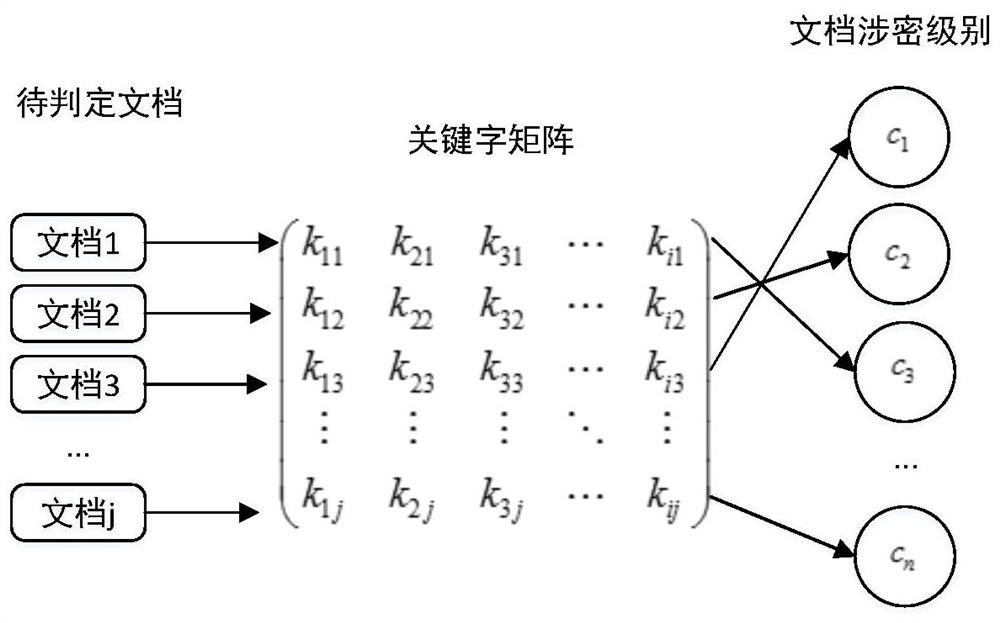
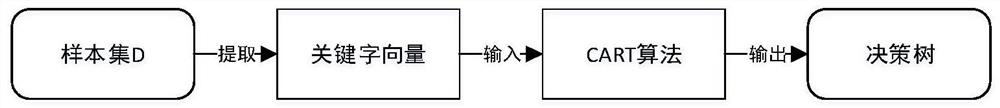
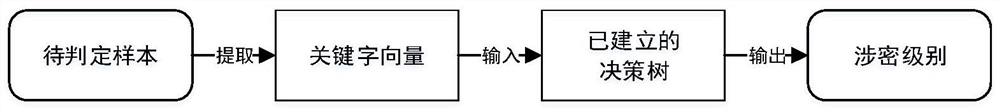
Document security level division method based on decision tree
PendingCN113158206ARealize automatic judgmentReduce the Risk of ConfidentialityDigital data protectionMachine learningOperations researchData science
The invention provides a document security level division method based on a decision tree, which comprises the following specific steps: step 1, traversing all conditions in a sample set, calculating Gini indexes of the sample set under different conditions, and selecting a condition corresponding to a minimum value as a first segmentation point, so as to divide a leaf node and remaining child nodes; step 2, continuing to calculate the Gini index of the new sample set for the remaining conditions for the child nodes, performing further subdivision, selecting a value with the minimum Gini index as a second segmentation point, and continuing to screen out leaf nodes and the child nodes; step 3, repeating the process until division of all conditions is realized, and realizing establishment of a decision tree; and step 4, re-capturing the sample for determination, and verifying the new sample according to the decision tree established by the training set to realize determination of the document security level. According to the method, automatic judgment of the document security level is realized, the workload of judgment personnel is greatly reduced, the judgment accuracy is improved, and a powerful guarantee is provided for a company to reduce the document leakage risk.
Owner:STATE GRID CORP OF CHINA +1
Electronic seal anti-counterfeiting method
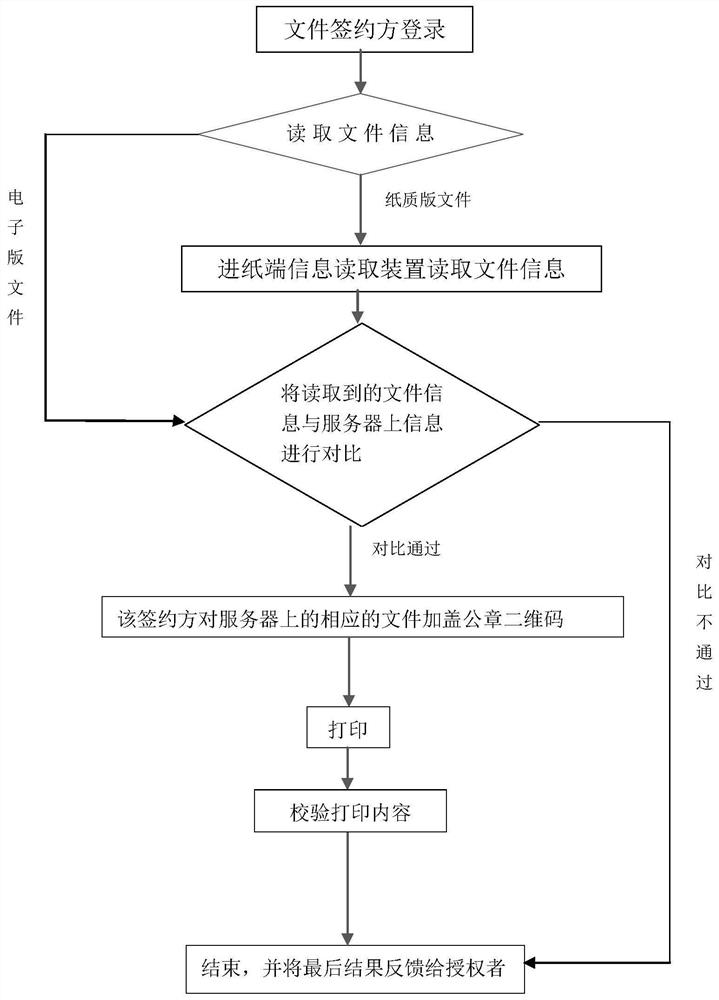
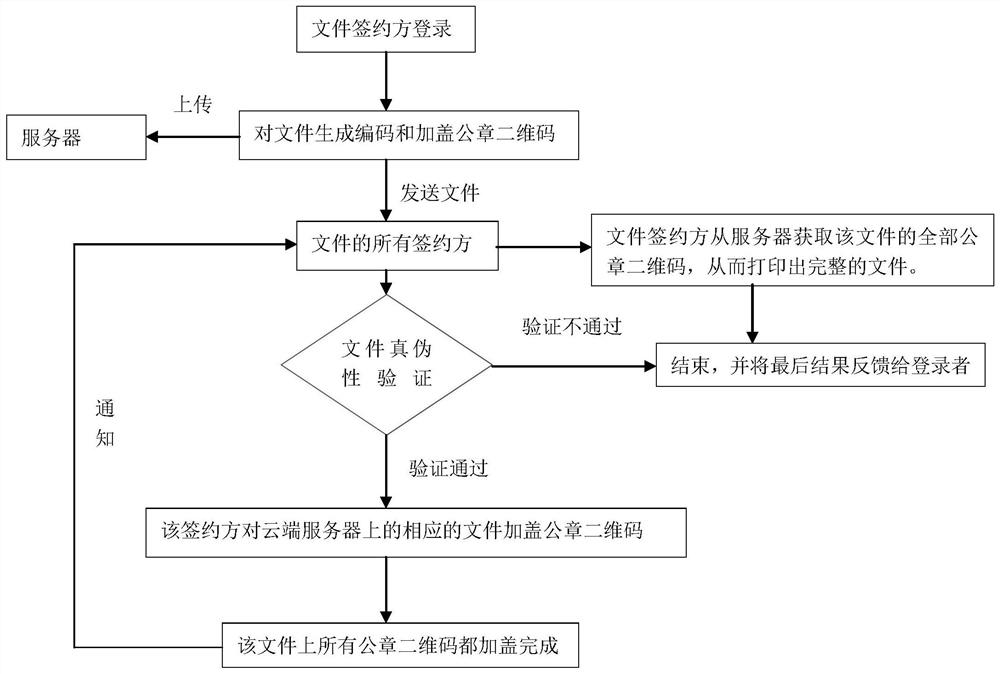
ActiveCN112699347AImprove reading accuracyEasy to takeDigital data authenticationProgram/content distribution protectionInformation processingFile transmission
The invention discloses an electronic seal anti-counterfeiting method which can automatically perform authenticity verification and printing on a file, can reduce the risk of leakage of file content from a server, and can also reduce the time wasted in the file transmission process. The system comprises a server, an information reading module, an information processing module, a printing module, a two-dimensional code, a transmission module and an encryption module. The movement of the paper is controlled by the automatic paper feeding device in the process of printing and reading the content of the file, and the paper, namely other equipment, does not need to be moved manually; the file content uploaded to the server can only contain all necessary content of the file and a part of content randomly selected from the rest part of content of the file; and the files with the same content can be signed by multiple persons online at the same time, and paper edition files can be printed after signing is completed.
Owner:王天平
Computer information transmission intelligent encryption method
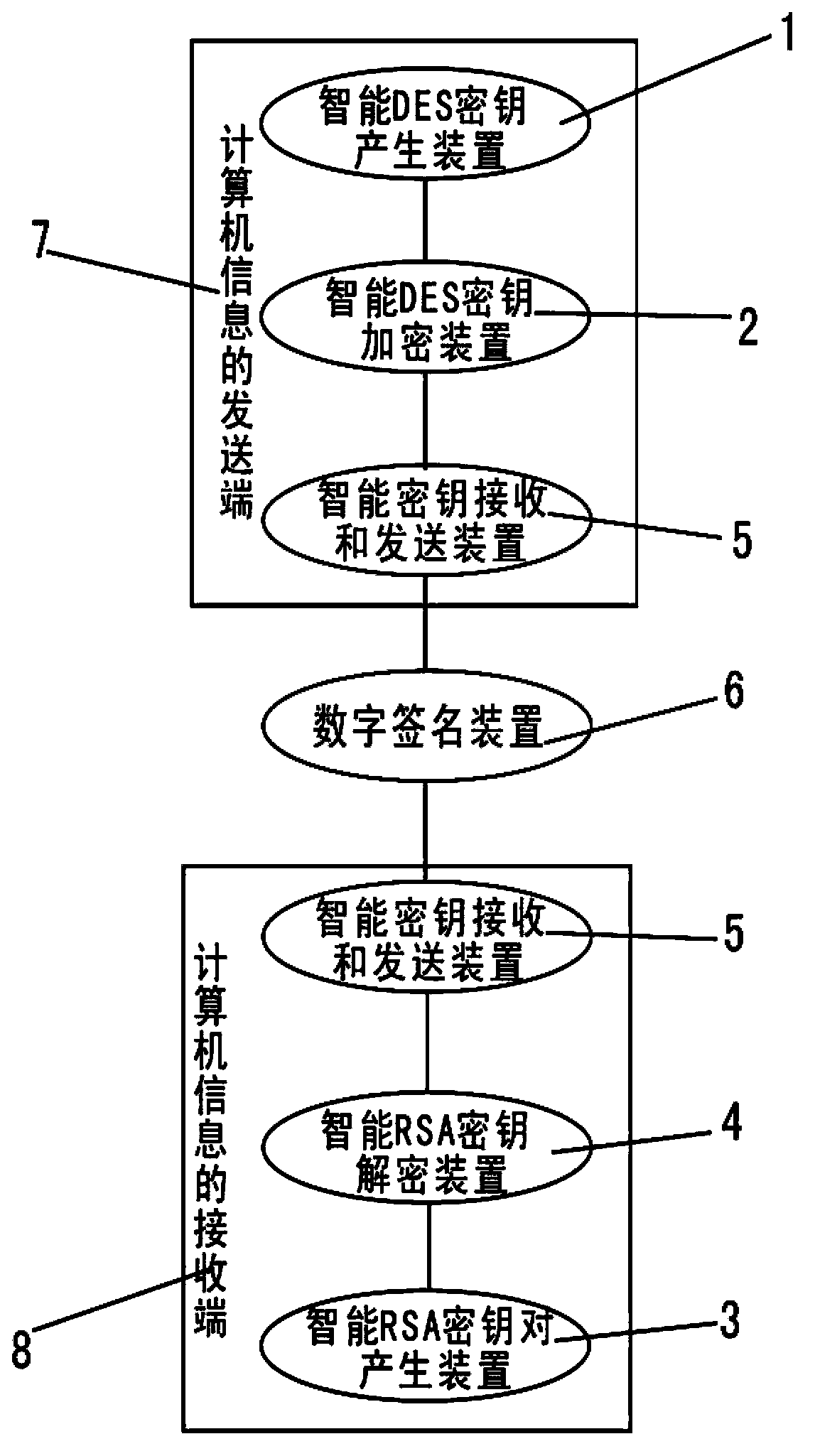
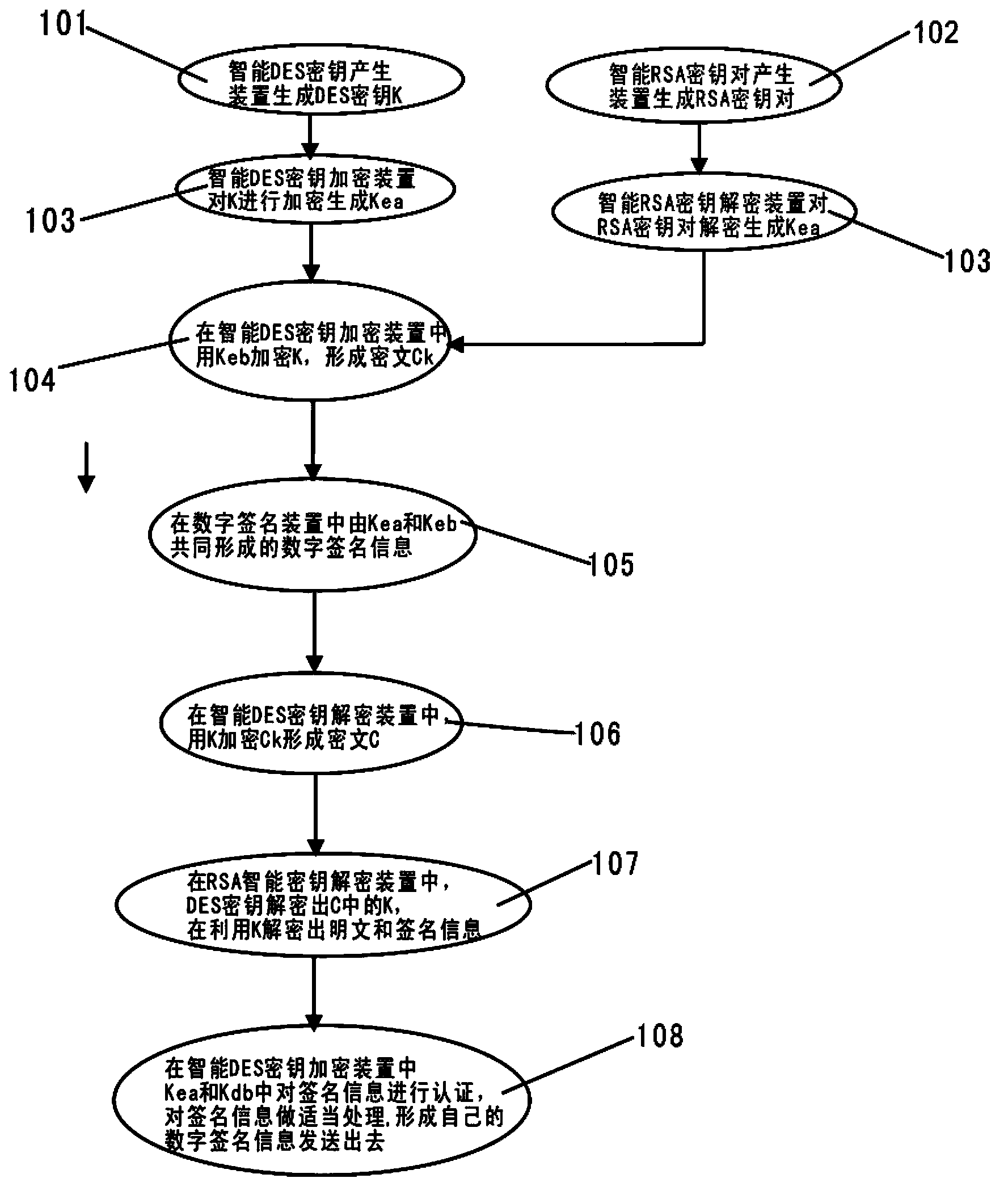
InactiveCN103812652AFast encryption and decryptionReduce the Risk of ConfidentialityEncryption apparatus with shift registers/memoriesUser identity/authority verificationInformation transmissionTransfer procedure
The invention relates to a computer information transmission intelligent encryption method. According to the method, the encryption and decryption speed of files during transmission can be increased; transmitted encrypted messages carry RSA-encrypted DES (data encryption standard) keys, so that the risks of divulgence of the keys during the transmission can be reduced, and the threat of network monitoring on information security can be effectively avoided; meanwhile, by means of a signature and authentication function and an RSA algorithm, both communicating parties can send the personal signature information to each other for reservation and authentication; the keys are convenient to manage, every communicating object simply needs to secretly keep the personal RSA decryption key.
Owner:NINGXIA XINHANG INFORMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com