End-to-end encryption method and system based on mobile network and communication client side
A technology of mobile network and encryption method, which is applied in the field of end-to-end encryption system, which can solve the problems of technical risk in user data security, opacity of encrypted storage users, and moral hazard, so as to reduce security risk and improve safety and security Level, the effect of increasing the security level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] Below in conjunction with accompanying drawing, the present invention will be further described:
[0014] The terms involved in the description of the present invention are explained as follows:
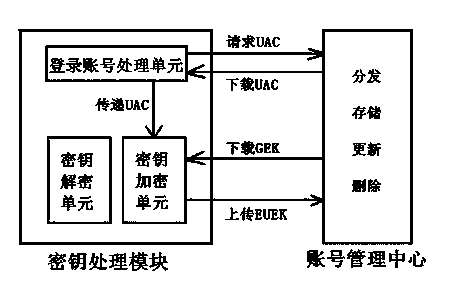
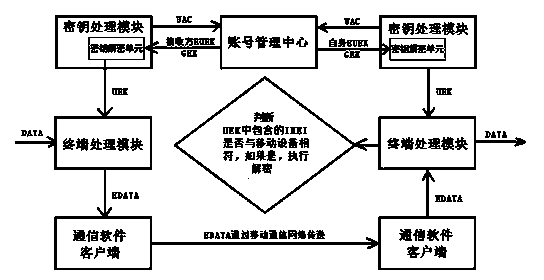
[0015] UAC, that is, User Account, user account, is used to classify different users in the account management center.
[0016] UEK, namely User Encryption Key, is the key used to encrypt user data.
[0017] GEK, the General Encryption Key, master key, is used to encrypt / decrypt the UEK.
[0018] EUEK, the Encrypt User Encryption Key, encrypts the user key and exists in the process of transmission and storage.
[0019] DATA refers to user plaintext data.
[0020] EDATA, Encrypt Data, encrypted user data.
[0021] IMEI, the identification code of GSM mobile equipment, here generally refers to the identification code of mobile communication equipment of various standards, which is globally unique.
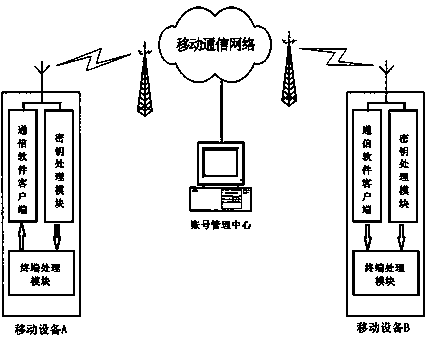
[0022] The invention provides an end-to-end encryption method based on a mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com