Risk control method, risk control system and terminal equipment
A risk control and risk control technology, applied in the financial field, can solve the problems of high risk of leakage in the risk control system, models and strategies cannot be changed, etc., to achieve the effect of flexible changes and reduce the risk of leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0023] figure 1 It shows a schematic diagram of the implementation flow of a risk control method provided by the embodiment of the present application, and the details are as follows:
[0024] Step S11, detecting whether there are rules or / and models that need to be updated in the risk control system, wherein the rules and the models are stored in different locations, the rules are used to judge whether the business data is legal, and the models are used to Determine the applicable type of the business data;
[0025] In the risk control system provided by the embodiment of the present application, various rules for judging whether business data is legal are stored in different nodes, and each node is stored in a rule container. Similarly, the rules used for judging business data Types of model storage and different algorithm modules, the above nodes and the above algorithm modules are independent of each other and stored in different locations. For example, if there are 10 r...
Embodiment 2
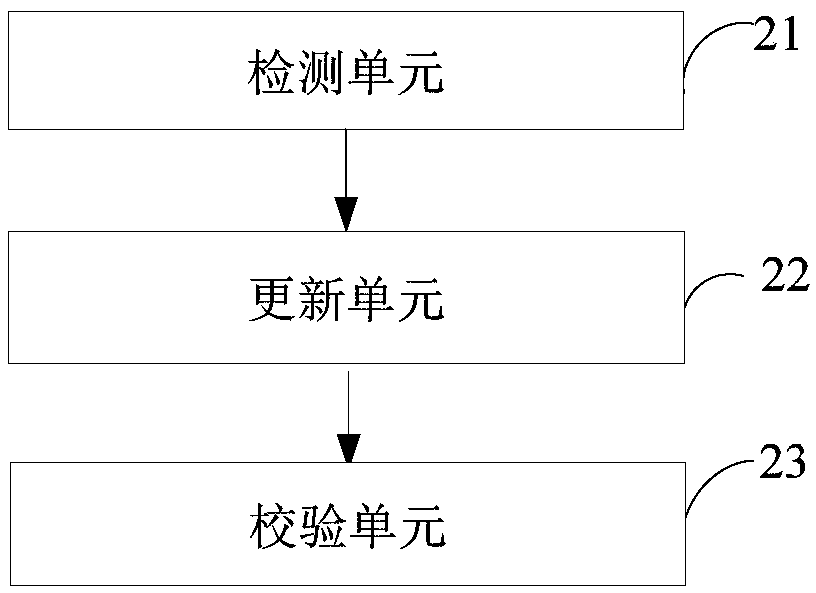
[0053] Corresponding to the risk control method described in the above embodiment, figure 2 A structural block diagram of the wind control system provided by the embodiment of the present application is shown, and for convenience of description, only parts related to the embodiment of the present application are shown.
[0054] refer to figure 2 , the wind control system includes: a detection unit 21, an update unit 22, and a verification unit 23, wherein:
[0055] The detection unit 21 is used to detect whether there are rules or / and models that need to be updated in the risk control system, wherein the rules and the models are stored in different locations, and the rules are used to judge whether the business data is legal. The model is used to determine the applicable type of the business data;
[0056] An updating unit 22, configured to update the rule to be updated to a specified rule if there is a rule or / and model to be updated, and / or update the model to be updated...
Embodiment 3
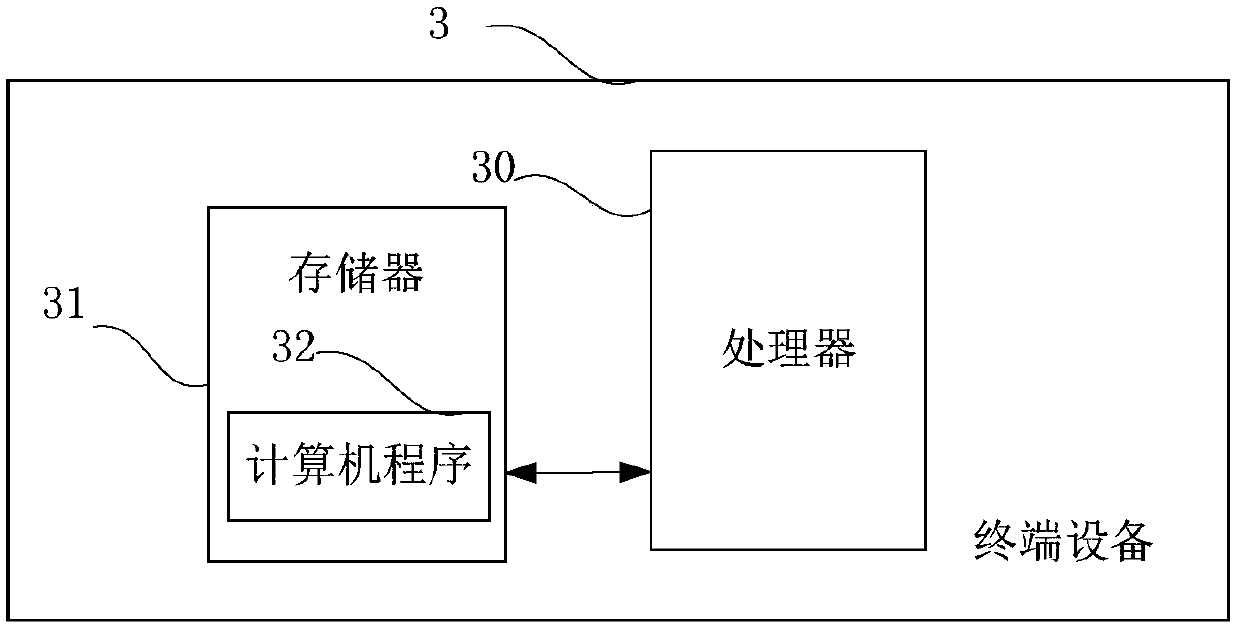
[0073] image 3 It is a schematic diagram of a terminal device provided by an embodiment of the present application. Such as image 3 As shown, the terminal device 3 in this embodiment includes: a processor 30 , a memory 31 , and a computer program 32 stored in the memory 31 and operable on the processor 30 . When the processor 30 executes the computer program 32, it realizes the steps in the above embodiments of the various risk control methods, for example figure 1 Steps S11 to S13 are shown. Alternatively, when the processor 30 executes the computer program 32, it realizes the functions of the modules / units in the above-mentioned device embodiments, for example figure 2 Function of units 21 to 23 shown.
[0074] Exemplarily, the computer program 32 can be divided into one or more modules / units, and the one or more modules / units are stored in the memory 31 and executed by the processor 30 to complete this application. The one or more modules / units may be a series of c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com