Method for realizing secure access of data in hard disk
A data security and hard disk technology, applied in the fields of digital data protection, electronic digital data processing, computer security devices, etc., can solve the problems of high risk of leakage, leakage of confidential data, increased risk of carrying and storage, etc., so as to reduce the risk of leakage and improve the safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
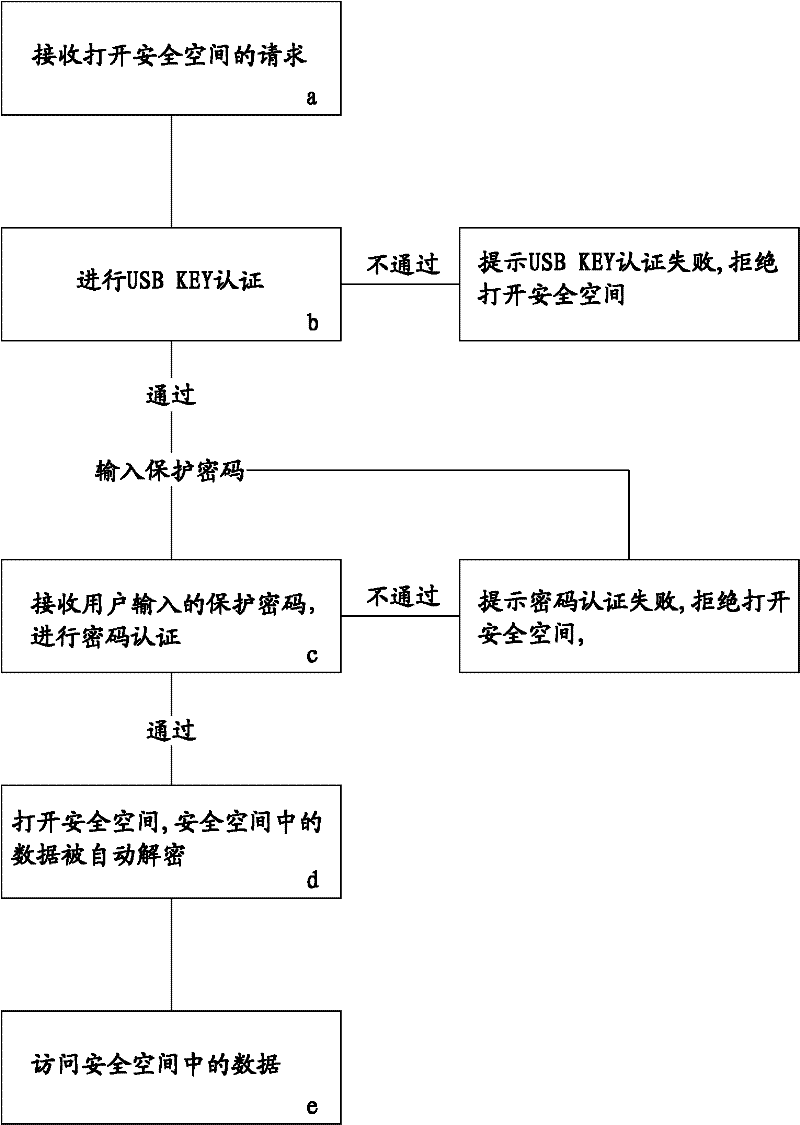
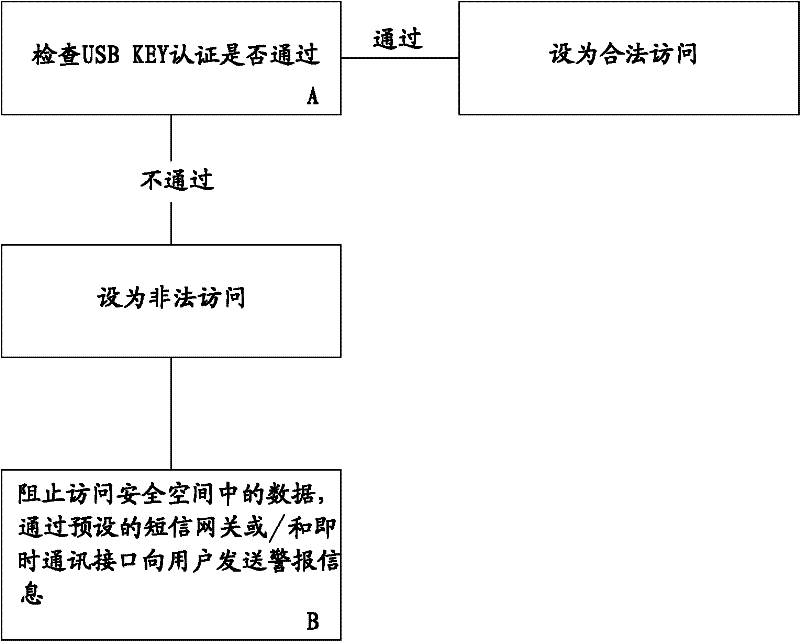
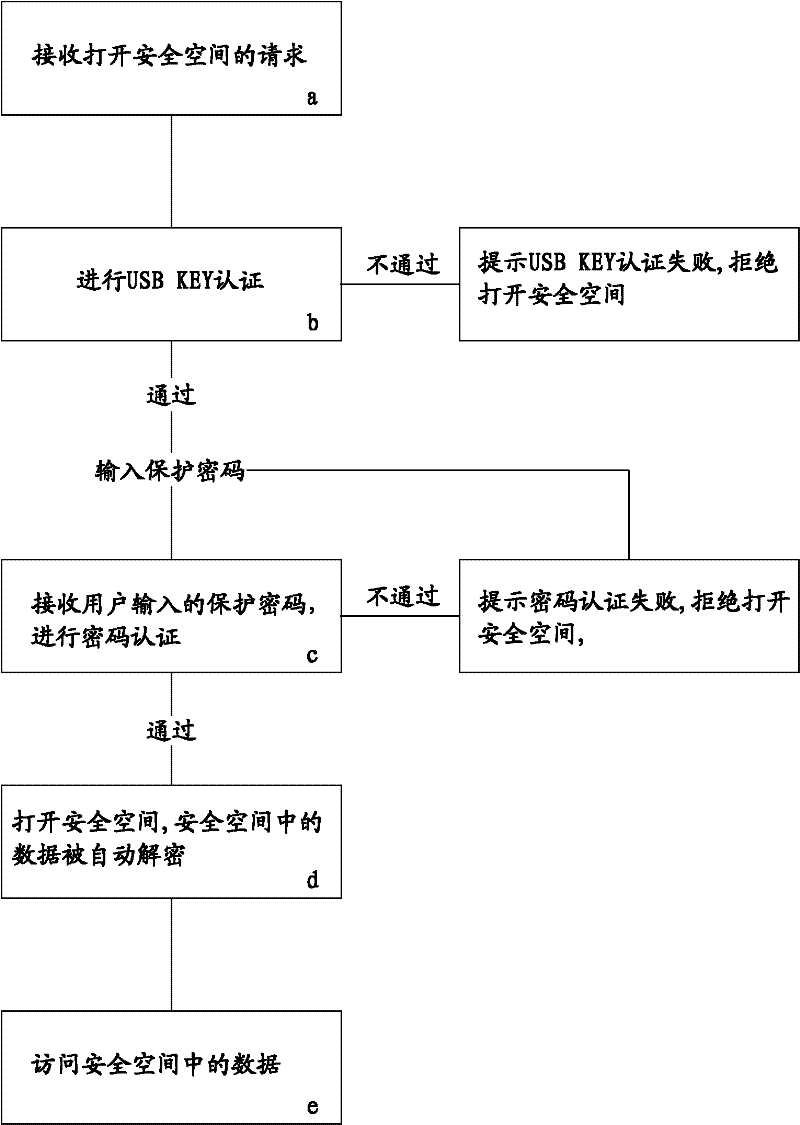
[0030] The present invention is a method for realizing safe access to hard disk data. The method creates a safe space on the hard disk and monitors the safe space. Attributes such as the size of the safe space, the drive letter, and the encryption algorithm can all be set at the time of creation. The encryption algorithm It can be any one of AES, Twofish, and Serpent. After the secure space is created, the data written in the secure space will be automatically encrypted according to the encryption algorithm. This mainly involves the I / O interface call of the WINDOWS operating system and the establishment of a virtual disk. As well as file encryption and other mature common technologies. In order to review the access rights, after the safe space is created, it is necessary to associate the safe space with the USB KEY and set the protection passw...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com