Device and method for implementing endogenous security of forwarding flow table
An implementation method and flow forwarding technology, applied in the field of data communication, can solve problems such as algorithm vulnerability and untrustworthiness, and achieve the effect of active defense, meeting business needs, and avoiding vulnerability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
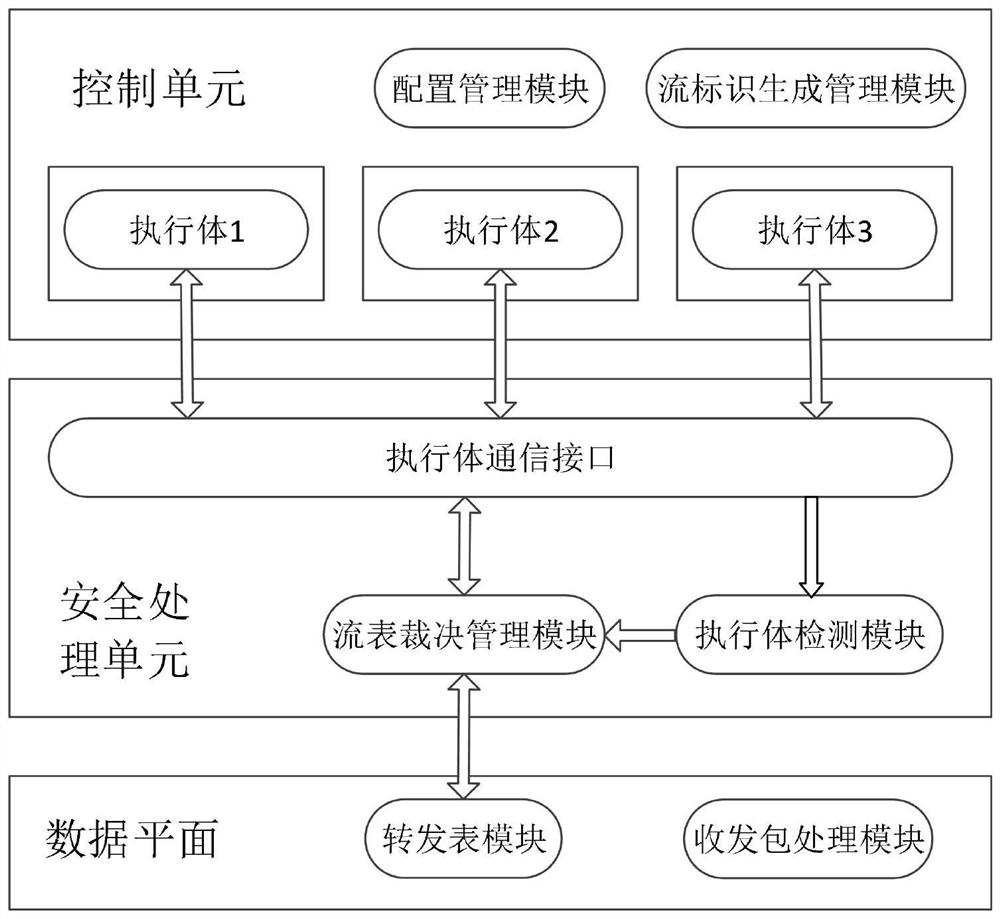
[0060] In order to solve the technical problem that a single algorithm is vulnerable and untrustworthy, and realize the endogenous security of network equipment in a better heterogeneous manner, the embodiment of the present invention provides an endogenous security implementation device for forwarding flow table, such as: figure 1 As shown, it mainly includes a control unit, a security processing unit and a data plane.
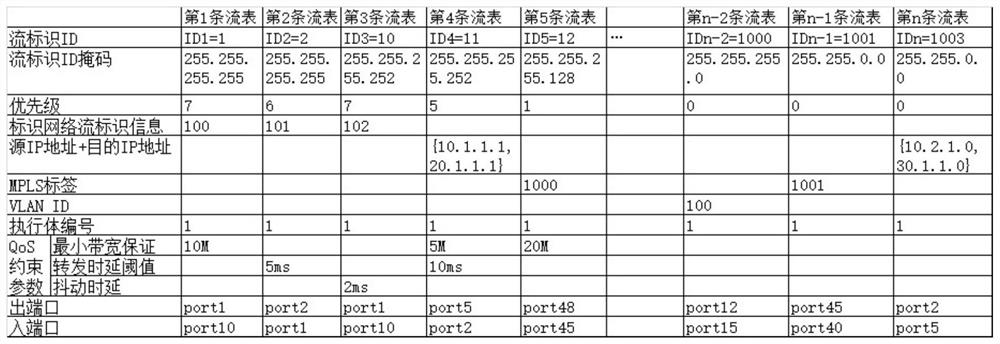
[0061] The control unit calculates the forwarding flow table of the current network device separately based on different algorithms through different executors, and allocates a unified flow identification ID to each forwarding flow table according to the service flow attribute, and sends each forwarding flow table to all the forwarding flow tables after the allocation is completed. The security processing unit; wherein, the forwarding flow table includes one or more entries including a flow ID, and each service corresponds to an entry in the forwarding flow ta...
Embodiment 2
[0098] In order to solve the technical problem that a single algorithm is vulnerable and untrustworthy, and realize the endogenous security of network devices in a more optimal heterogeneous manner, the embodiment of the present invention further provides a method for realizing endogenous security of a forwarding flow table, which can be implemented by The apparatus described in Example 1 was completed.
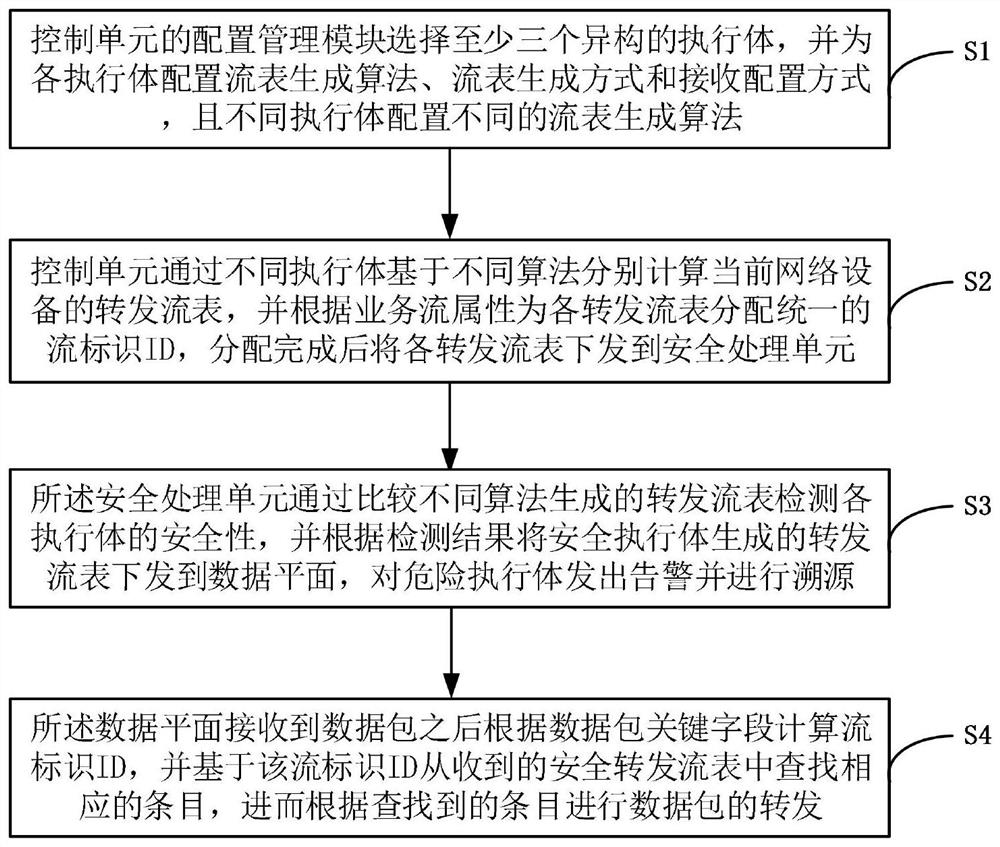
[0099] like image 3 As shown, the method for implementing the endogenous security of the forwarding flow table provided by the embodiment of the present invention mainly includes the following steps:
[0100] Step S1: The configuration management module of the control unit selects at least three heterogeneous executive bodies, and configures a flow table generation algorithm, a flow table generation method, and related QoS constraint parameters for each executive body, and different executive bodies are configured with different flow table generation algorithm.
[0101] Th...
Embodiment 3
[0113] On the basis of the foregoing Embodiment 1, this embodiment of the present invention further introduces the process of "generating a forwarding flow table by each executor" corresponding to step S2. combine Figure 4 , the process of generating the forwarding flow table by each executor is as follows:
[0114] Step S201: Each executor receives the flow table generation algorithm, flow table generation method, and related QoS constraint parameters, such as delay and jitter requirements, configured by the configuration management module. It can be seen from the introduction in Embodiment 2 that the configuration management module will pre-configure the flow table generation algorithm, flow table generation method and relevant QoS constraint parameters that need to be satisfied for each executor. Leave 10M bandwidth, etc.; then each executive body can directly receive and use the parameters configured by the configuration management module. When the priority is pre-confi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com