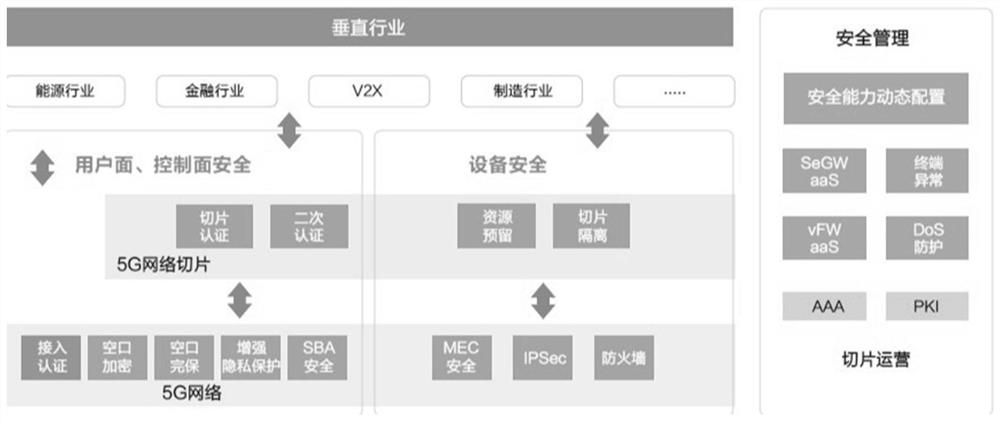
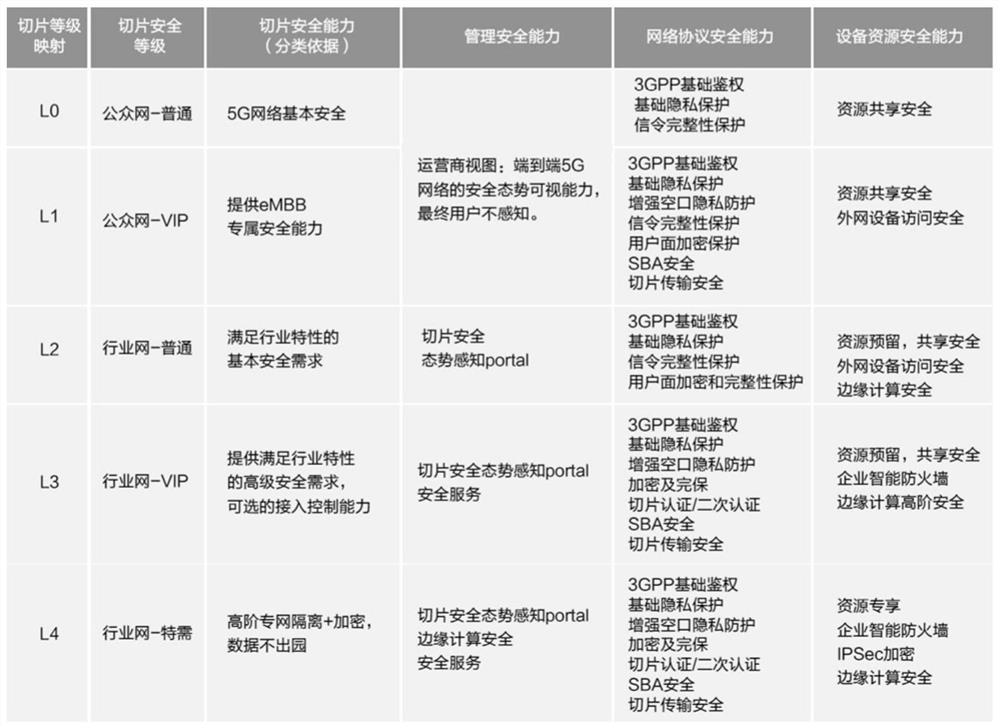
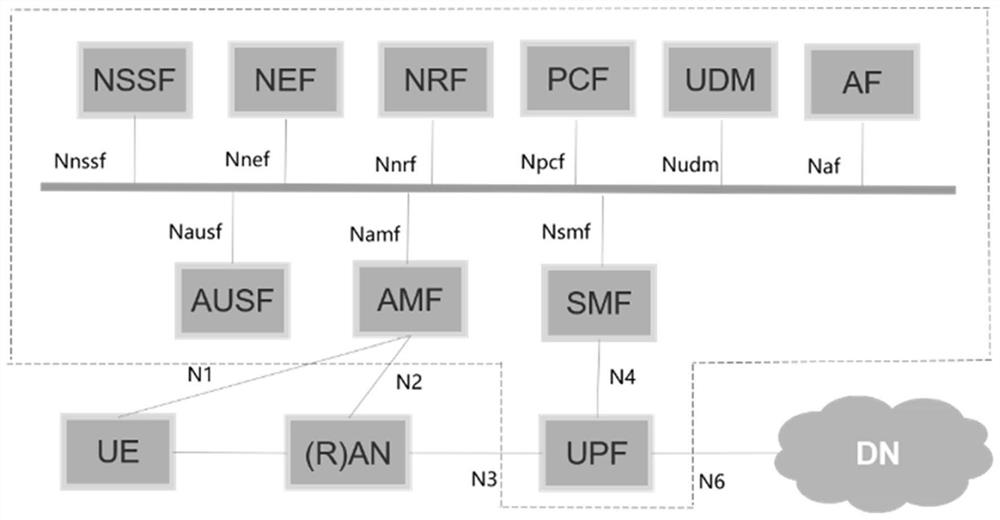
Core network security penetration test method, system and equipment based on ontology rule
A technology of penetration testing and core network, applied in the field of 5G network security, it can solve the problems of penetration testing dependence and lack of establishing a vulnerability attack and defense rule base.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0078] An embodiment of the present invention is a core network security penetration testing method based on ontology rules. The architecture of core network security penetration testing system based on ontology rules is as follows: Figure 4 As shown, it consists of three subsystems, which are domain modeling subsystem, security detection rule subsystem and penetration testing subsystem. in,
[0079] The domain modeling subsystem, including the domain model construction subsystem, is used to complete the construction of the domain model that reflects the semantics of the core network in the core network security penetration test, so as to complete the analysis of attackers, attack methods, attack techniques, damage targets and damage consequences knowledge structure. The domain modeling subsystem also provides a user interface to operate the security penetration testing system based on ontology rules. Furthermore, users can also customize domain models that meet specific n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com