Network security equipment knowledge reasoning method, device and system and storage medium
A technology of network security and knowledge reasoning, which is applied in the field of data processing of network security equipment, can solve problems such as process dispersion and reasoning result errors, and achieve accurate results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
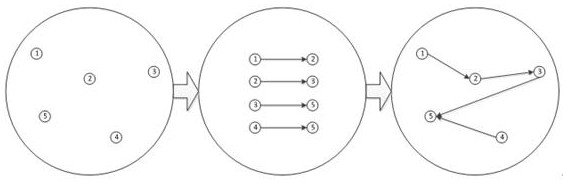
[0037] refer to figure 1 This example discloses a network security device knowledge reasoning method, and the method includes:
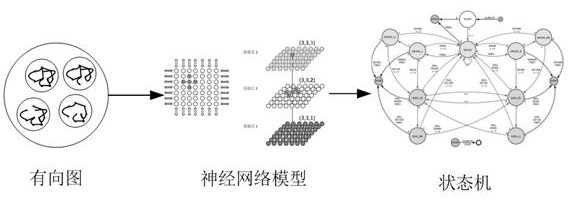
[0038] S101: Real-time network security device acquired data acquired data, multi-fused the acquired data to obtain a directional view of the relationship between the network security devices;
[0039] It should be noted that the entire method of the present invention is to operate in real time, and the data acquisition of the network security device acquired in step S101, and the data acquired every time the subsequent steps are performed.
[0040] Among them, the distributed network security device includes a distributed network controller, a host controller, a core controller, a host security agent, a firewall, a secure communication module, and more.
[0041] Among them, the acquired data includes various work information of the device ID, the device, such as the network controller receives job information from the host controller. Each network secur...
Embodiment 2
[0065] This embodiment is mainly to disclose a network security device knowledge, including a processor, and a memory, the memory being stored with a computer program, the computer program is implemented when executed by a processor. . The processor can be one or more processors, the memory can be one or more memories, and the specific implementation process can be referred to the above method embodiment, and details are not described herein again.
Embodiment 3
[0067] This embodiment discloses a computer readable storage medium, which is characterized in that a computer program is stored, and the computer program is executed by the processor to perform the method steps described herein. The specific implementation process can be referred to the above method embodiments, and details are not described herein again.
[0068] The storage medium can be a disk, an optical disk, a read only memory, a ROM or Random Abbssmemory, RAM, and the like.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com