Blockchain architecture security evaluation method and system based on permeability test case set
A test case set and security assessment technology, applied in the field of network security, can solve the problems of blockchain platforms, systems, and application security incidents, etc., to reduce the probability of security incidents, promote security development, quantify and evaluate security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
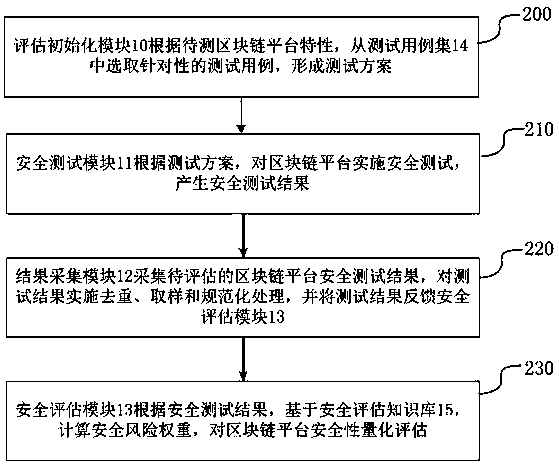
[0043] In order to realize the timely discovery of security risks of blockchain technology architecture, improve the security of blockchain products and services, and promote the security application of blockchain technology, a new set of security evaluation system is designed in the embodiment of this application. Blockchain technical architecture, according to the hierarchical characteristics of the blockchain technical architecture, conduct security tests on it, and evaluate the security of the blockchain technical architecture based on the test results.
[0044] Embodiments of the present application will be described in detail below in conjunction with the accompanying drawings.
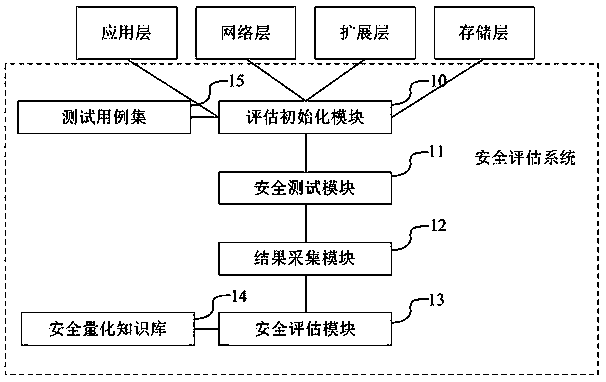
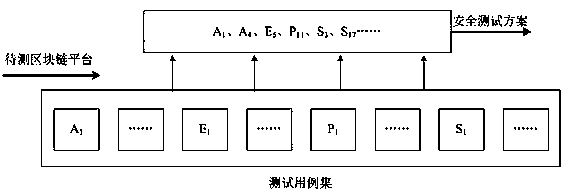
[0045] refer to figure 1 As shown, the security assessment system based on the block chain platform includes at least an assessment initialization module 10, a security test module 11, a result collection module 12, a security assessment module 13, a set of security test cases 14, and a security...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com