Personnel information safety management method and management device
A technology of information security and management method, applied in the field of personal information security management method and management device, can solve the problems of increasing mobile phone, user loss, leakage, etc., and achieve the effect of reducing leakage risk and improving effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
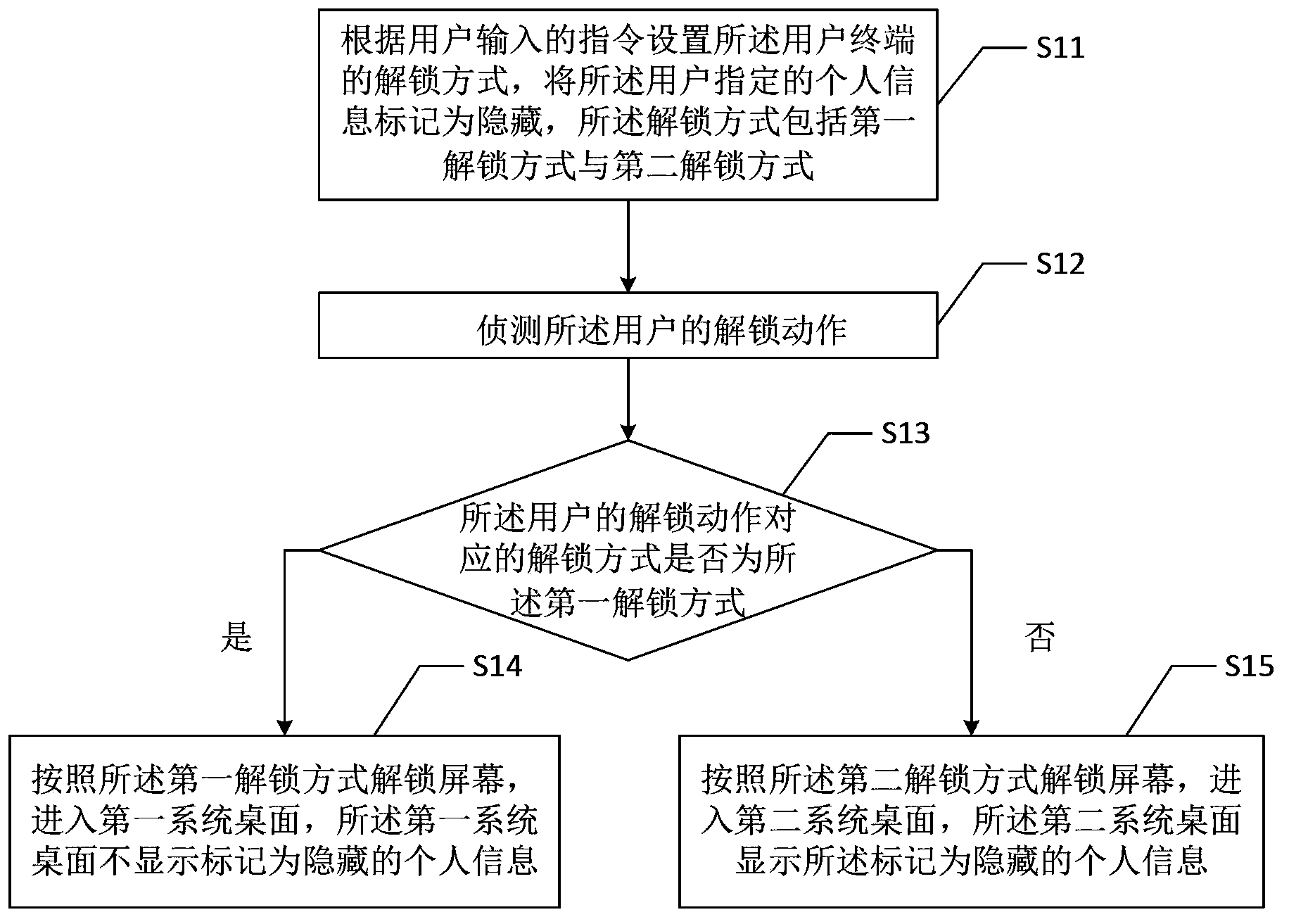
[0018] figure 1 It is a flow chart of the personal information security management method provided in the first embodiment. Such as figure 1 As shown, the personal information security management method in this embodiment includes the following steps:
[0019] Step S11 , setting an unlocking method of the user terminal according to an instruction input by the user, marking the personal information specified by the user as hidden, and the unlocking method includes a first unlocking method and a second unlocking method.
[0020] The unlocking method set according to the instruction input by the user is used to unlock the screen when the user terminal screen is locked, and may include a face recognition unlocking method, a password unlocking method, a fingerprint recognition unlocking method, a voiceprint recognition unlocking method, a graphic code unlocking method, and Gesture unlocking methods, etc. In the embodiment of the present invention, the user terminal can set at le...
no. 2 example
[0037] Figure 4 It is a flow chart of the personal information security management method provided by the second embodiment of the present invention. Such as Figure 4 As shown, the personal information security management method in this embodiment includes the following steps:
[0038] Step S21, responding to a user's boot command, starting the user terminal to enter the desktop of the first system.
[0039] In the embodiment of the present invention, the user terminal enters the desktop of the first system every time it is activated in response to the user's boot command, that is, after each boot, the user terminal does not display the personal information marked as hidden to the current user of the user terminal. Information, so that the illegal user of the user terminal can be prevented from obtaining the personal information of the user of the user terminal by switching on and off, thereby improving the effectiveness of personal information security management in the u...
no. 3 example
[0052] Figure 5 A schematic structural diagram of a personal information security management device provided in the third embodiment. The personal information security management device provided in this embodiment can be used to implement the personal information security management method in the first embodiment. Such as Figure 5 As shown, the personal information security management device 10 includes an unlocking mode and information setting module 11 , a user unlocking motion detection module 12 , an unlocking mode judging module 13 , a first system desktop switching module 14 , and a second system desktop switching module 15 .
[0053] Wherein, the unlocking method and information setting module 11 is used to set the unlocking method according to the instruction input by the user, and mark the personal information specified by the user as hidden, and the unlocking method includes a first unlocking method and a second unlocking method. The user's unlocking action detec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com