TTP automatic extraction and attack team clustering method
A team and clustering technology, applied in the field of TTP automatic extraction and attack team clustering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
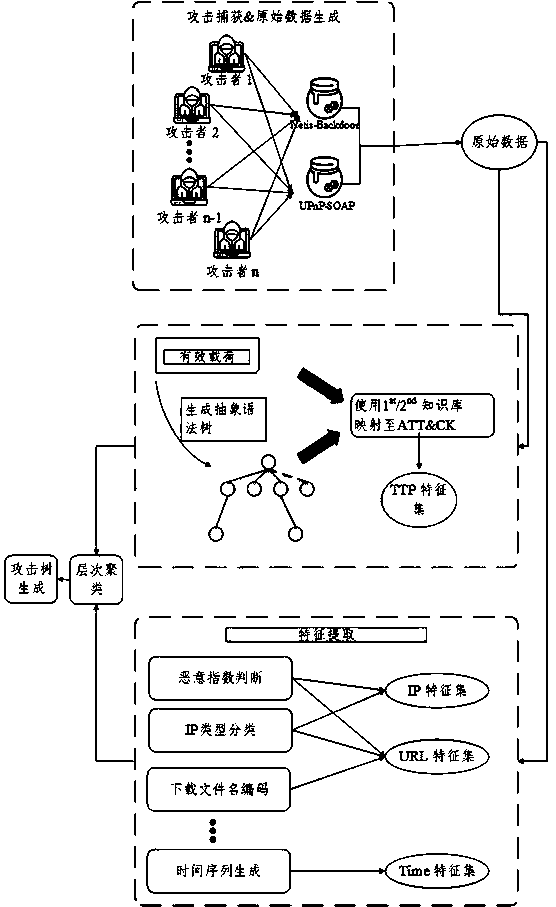
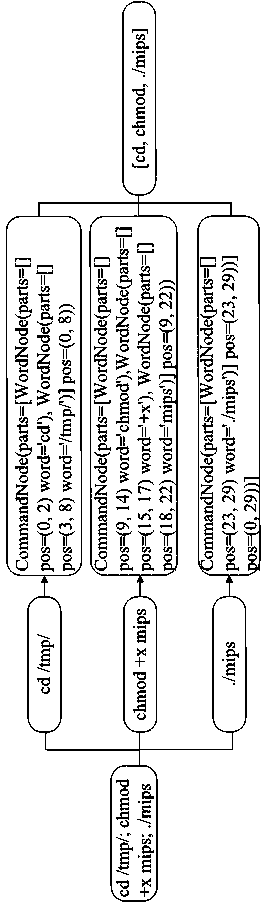
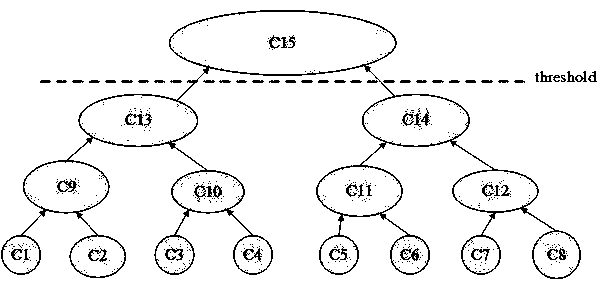
[0014] The present invention will now be further described in conjunction with the accompanying drawings and specific embodiments. Such as figure 1 Shown is a block diagram of the invention. First, the framework captures attacks from the Internet, generates raw data, and extracts features from specific fields such as timestamp, payload, and time zone. Second, it enriches these features. For example, when generating a TTP signature group, it divides the payload into commands, maps these commands to the ATT&CK framework, and then generates an abstract syntax tree of the commands for a second mapping to techniques and tactics. After all feature groups are generated, these string-type features can be vectorized using encoding and TF-IDF. Then, it combines all the eigenvectors and clusters these attackers using a hierarchical clustering algorithm. Finally, the framework utilizes the payloads owned by each attacking team to create an attack tree to visualize team behavior. Nod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com