Zombie account management method based on operation and maintenance auditing system
A technology of account management and account, which is applied in the field of zombie account management based on the operation and maintenance audit system, can solve problems such as difficult cleaning, ignorance of operation and maintenance audit system administrators, and influence on user management efficiency, so as to reduce the operation burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
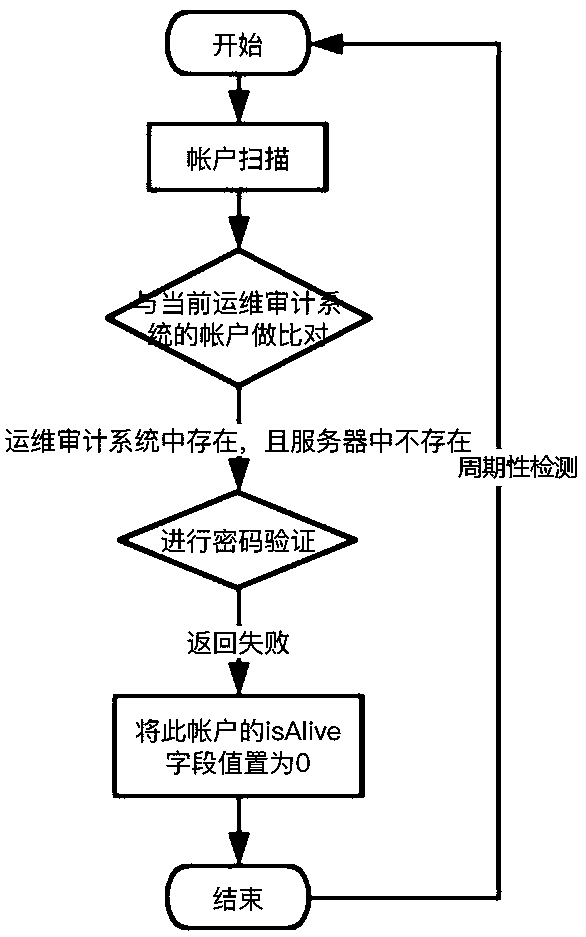
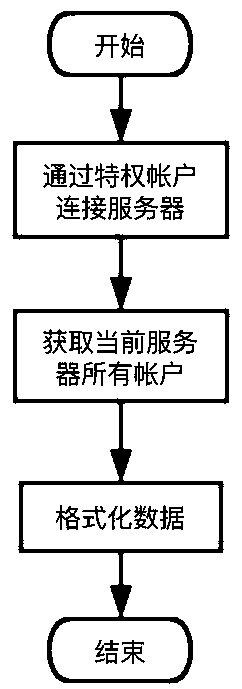
[0028] A zombie account management method based on the operation and maintenance audit system, such as figure 1 and image 3 As shown, after the operation and maintenance audit system is connected to the server to be detected, it scans all accounts in the server to be detected, and compares the scanned accounts with the accounts originally stored in the operation and maintenance audit system, and compares the accounts between the server and the operation and maintenance audit system The accounts that save the account information in both are marked as scanning accounts, and the accounts that are saved in the operation and maintenance audit system but have no account information in the server are marked as non-scanning accounts; The account logged in the server is a non-real account; the last use time of the non-real account is determined, and the zombie account is screened out for cleaning; the zombie account refers to an account that meets the following conditions at the same ...
Embodiment 2
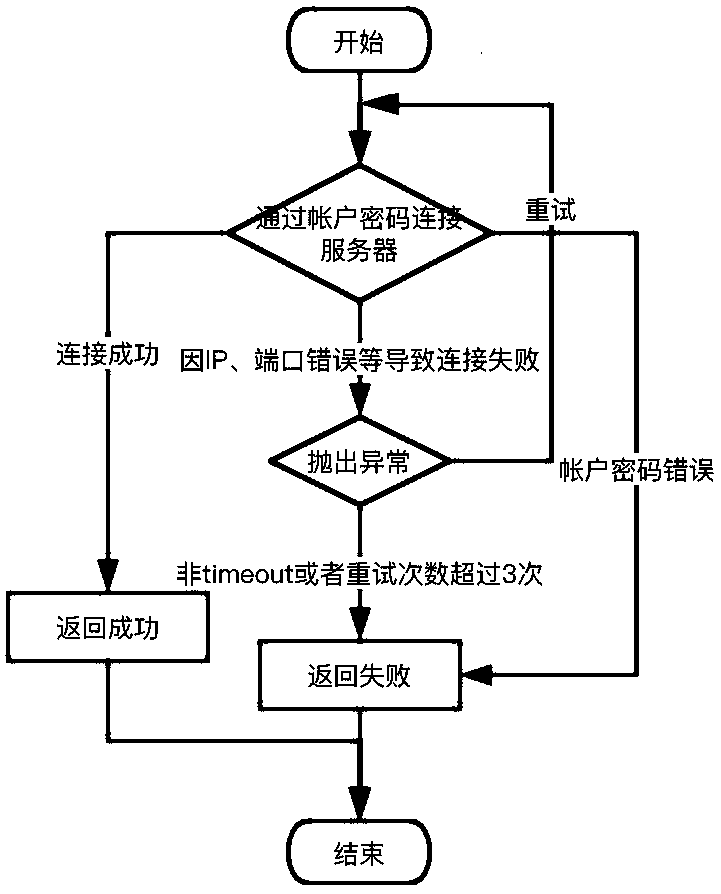
[0033] On the basis of above-mentioned embodiment 1, in order to realize the present invention better, combine figure 1 and figure 2 As shown, further, the password login detection specifically refers to: the operation and maintenance audit system uses the account information stored in the operation and maintenance audit system of the non-scanning account to connect to the server to be detected; Result; if the account login name of the scanning account saved in the operation and maintenance audit system, the account password are inconsistent with the server to be detected and the connection fails, then return the result of the connection failure; the account information includes IP address, SSH port, Account login name, account password; when the connection timeout occurs due to an error in the IP address and SSH port during the password login detection process, the non-scanning account that has timed out will be reconnected; if the connection is still timed out after three r...
Embodiment 3
[0038] On the basis of any one of the above-mentioned embodiments 1-2, in order to better realize the present invention, further, the determination of the last use time of the non-real account specifically refers to: first setting a longest non-login period , and then use the current time to subtract the last use time of the non-real account for the last use time judgment to obtain the actual non-login interval time, and finally compare the actual non-login time with the longest non-login time to filter out zombie accounts.
[0039] Working principle: After determining condition 1 in embodiment 2, determine whether those non-real accounts that meet condition 1 meet condition 2; the longest login period is freely set by the administrator, and the administrator can set it according to actual needs. Set a certain maximum non-login period. If the actual non-login interval is greater than the maximum non-login period, it will be identified as a zombie account. Otherwise, it will not...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com