Patents
Literature
104 results about "Login Name" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer software, logname (stands for Login Name) is a program in Unix and Unix-like operating systems that prints the name of the user who is currently logged in on the terminal. It usually corresponds to the LOGNAME variable in the system-state environment (but this variable could have been modified).
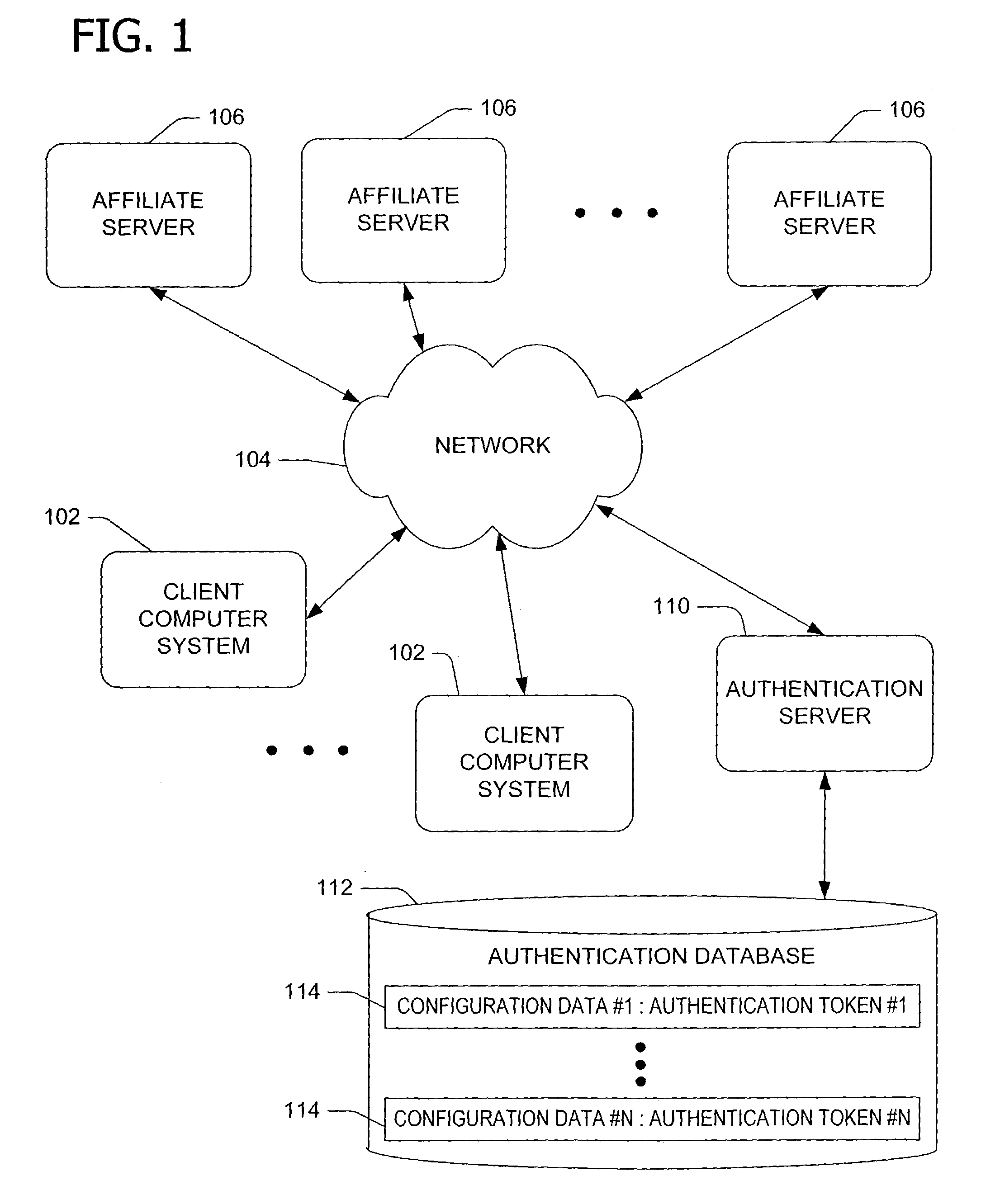
Online commercial transaction system and method of operation thereof
ActiveUS8417642B2Digital data authenticationBuying/selling/leasing transactionsApplication serverLogin Name
Owner:CORK GROUP TRADING
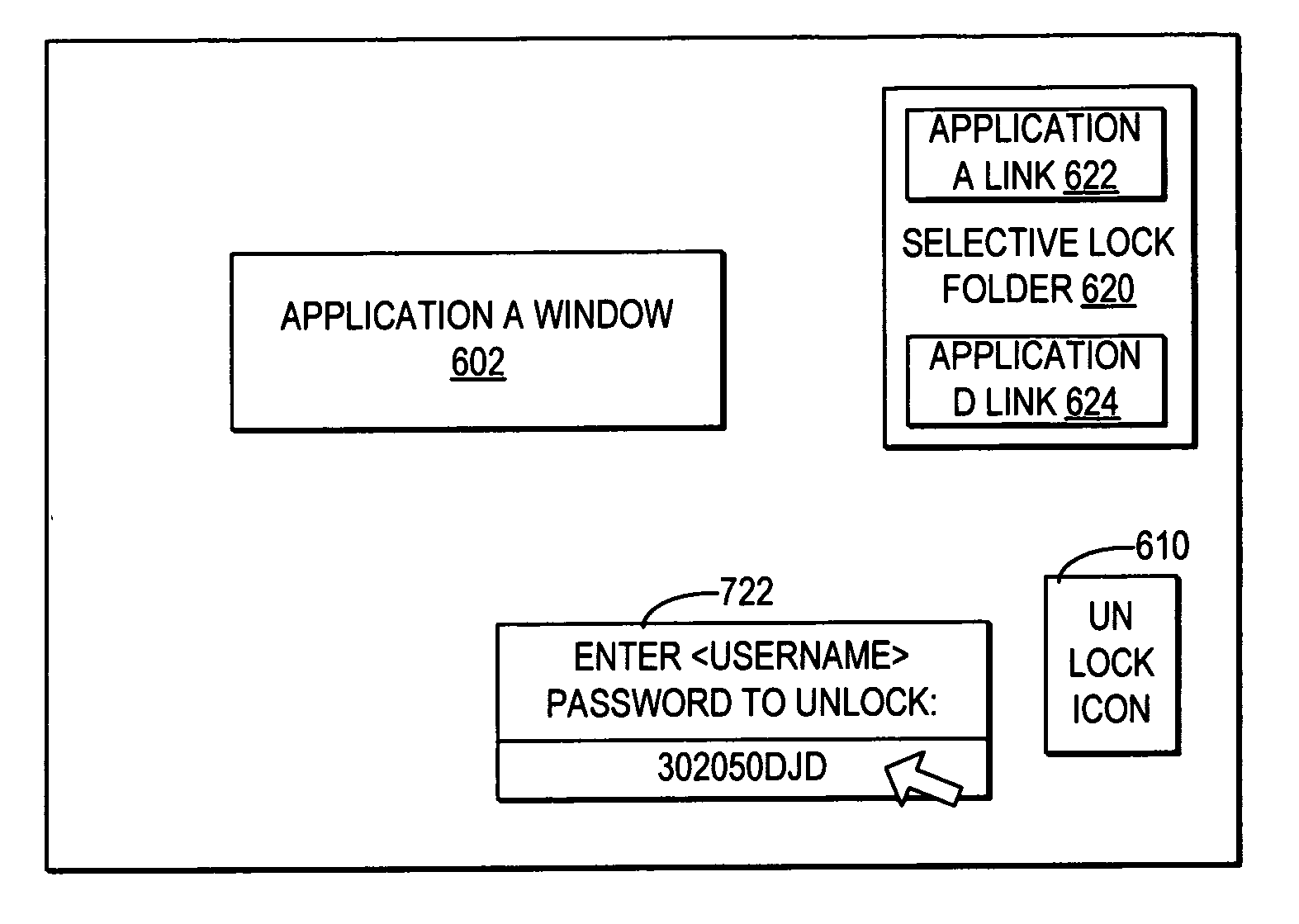
Allowing any computer users access to use only a selection of the available applications
InactiveUS20070016958A1Reduce usageDigital data processing detailsUser identity/authority verificationComputer usersUser input
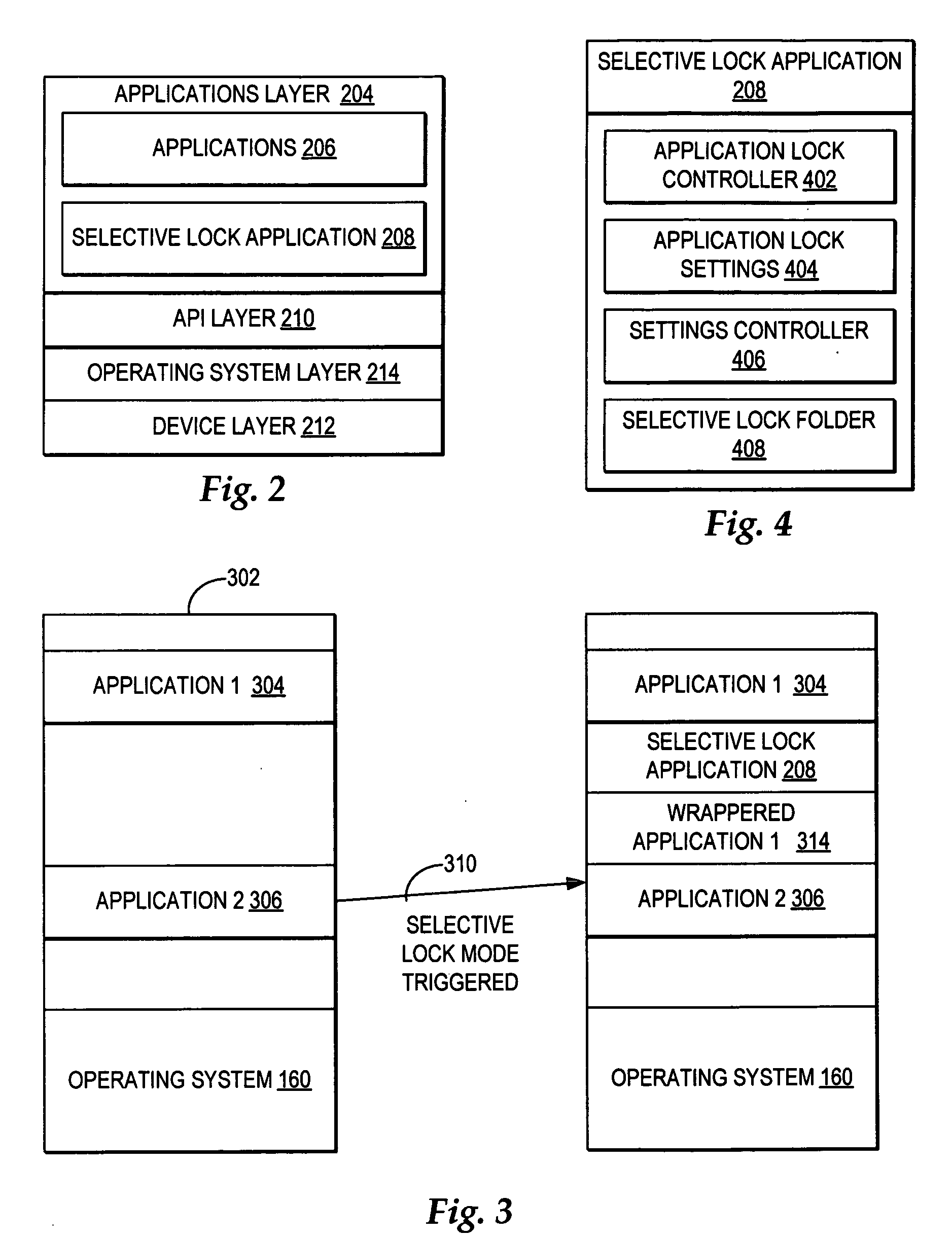
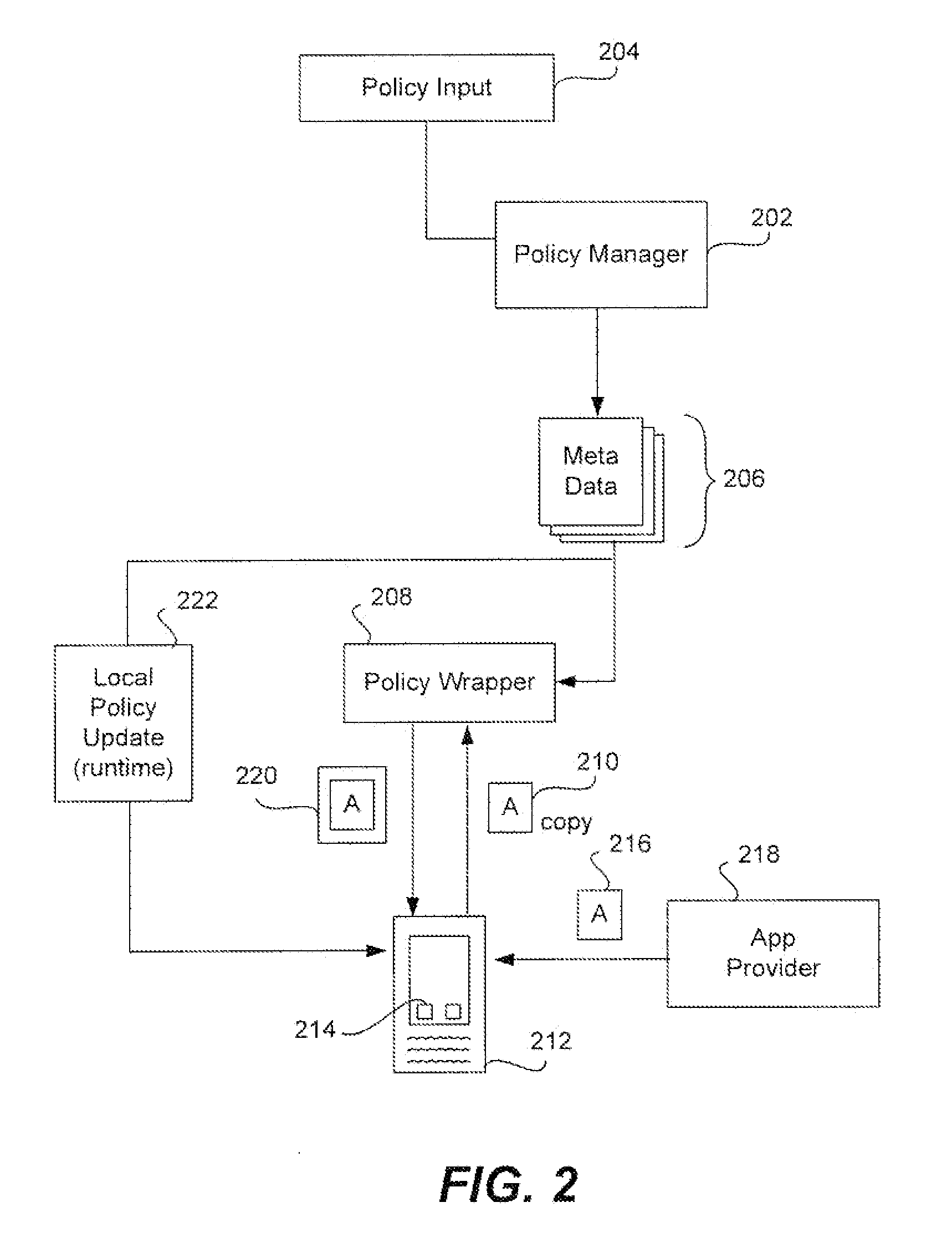
A computer system operates in normal mode where all applications and files are accessible to an authorized user, where an authorized user enters a required log in to access all applications. When a trigger to change the control access from normal mode to selective lock mode is detected, access to the applications and files is blocked and the content within the user interface is cleared to initiate the selective lock mode. Next, content is added to the user interface including a folder with only a selection of the applications each accessible through a separate selectable link, where the selectable links are designated in the particular folder by an authorized user during normal mode. During selective lock mode, any user may only select to open one of the selection of applications by selecting a displayed selectable link for the application. Responsive to a selection of a selectable link, a wrapper function is called that opens the application, wherein any user is enabled to fully access only the wrappered application and the wrapper blocks access to the remainder of the computer system, such that during selective lock mode any user is presented with access, without first logging in, to a fully functioning version of each of the selection of applications designated by the authorized user in the particular folder.
Owner:IBM CORP
Secure single sign-on for a group of wrapped applications on a computing device and runtime credential sharing
ActiveUS20140250511A1Digital data processing detailsMultiple digital computer combinationsArray data structureUser input
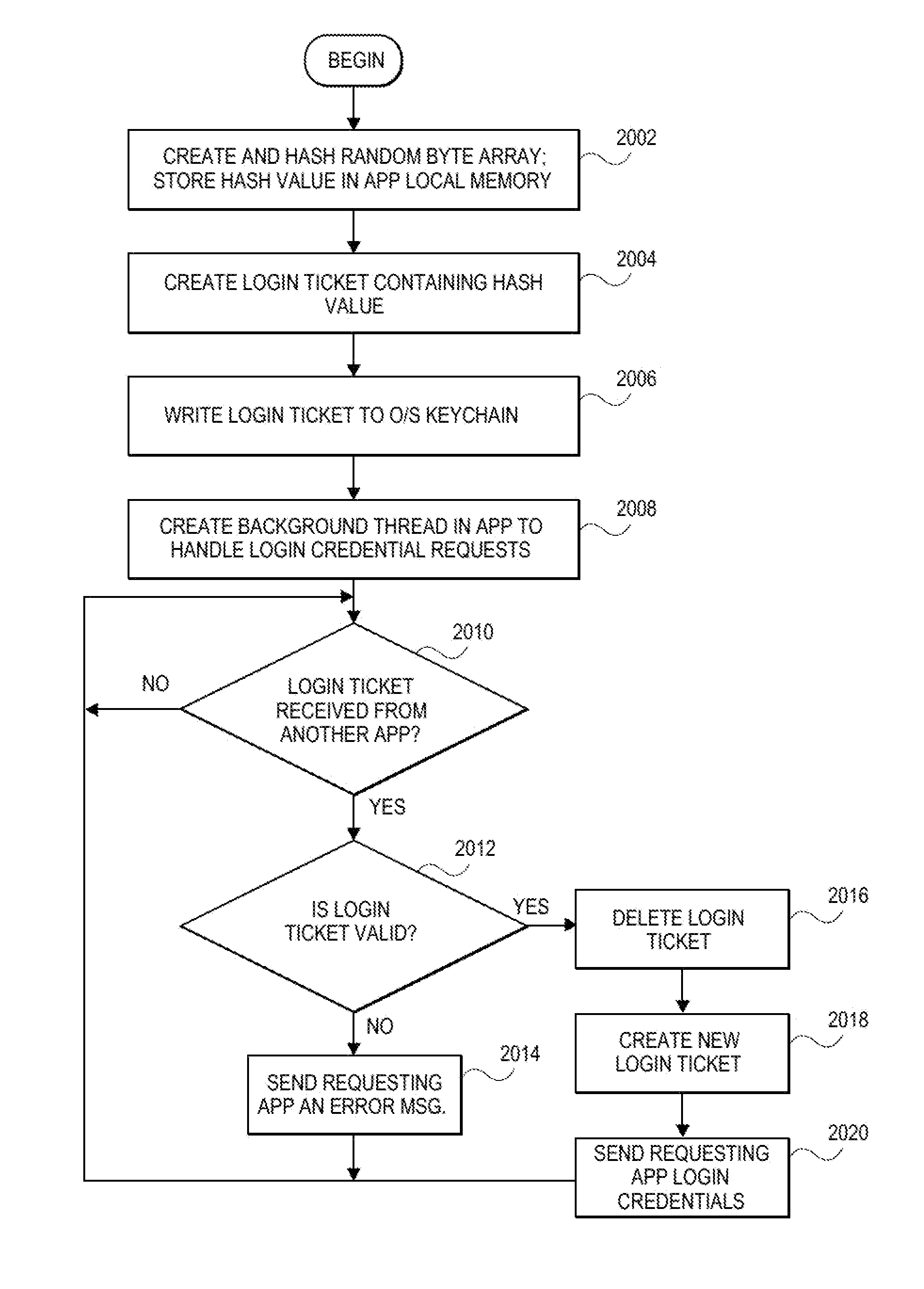
A mobile device user is able to execute an app in a federation of wrapped apps without having to login to that app provided that the user has already logged into another app in that federation. The federation of apps on the device uses multi-app authentication to enable the user to start subsequent apps after explicitly entering login credentials for another app in that federation. This feature is loosely referred to as single sign-on for apps in the federation. The multi-app authentication is implemented by giving the second app a chance to prove two facts. One that it knows where in the operating system keychain a login ticket is stored and two, what the hash value of a random byte array is. By showing these facts, the logged-into app can safely provide login credentials to subsequent app without the user having to enter a login name or password.
Owner:BLUE CEDAR NETWORKS INC
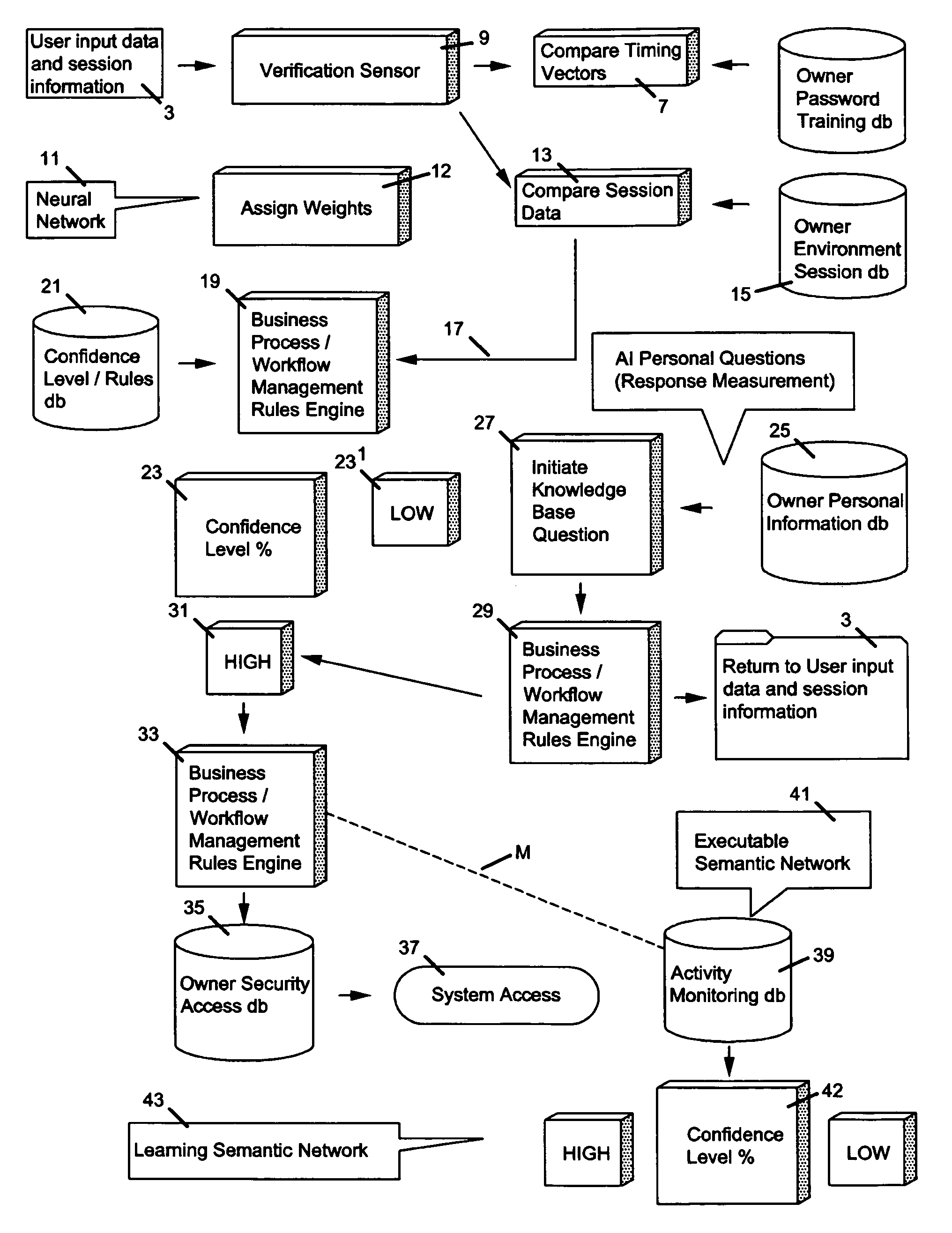
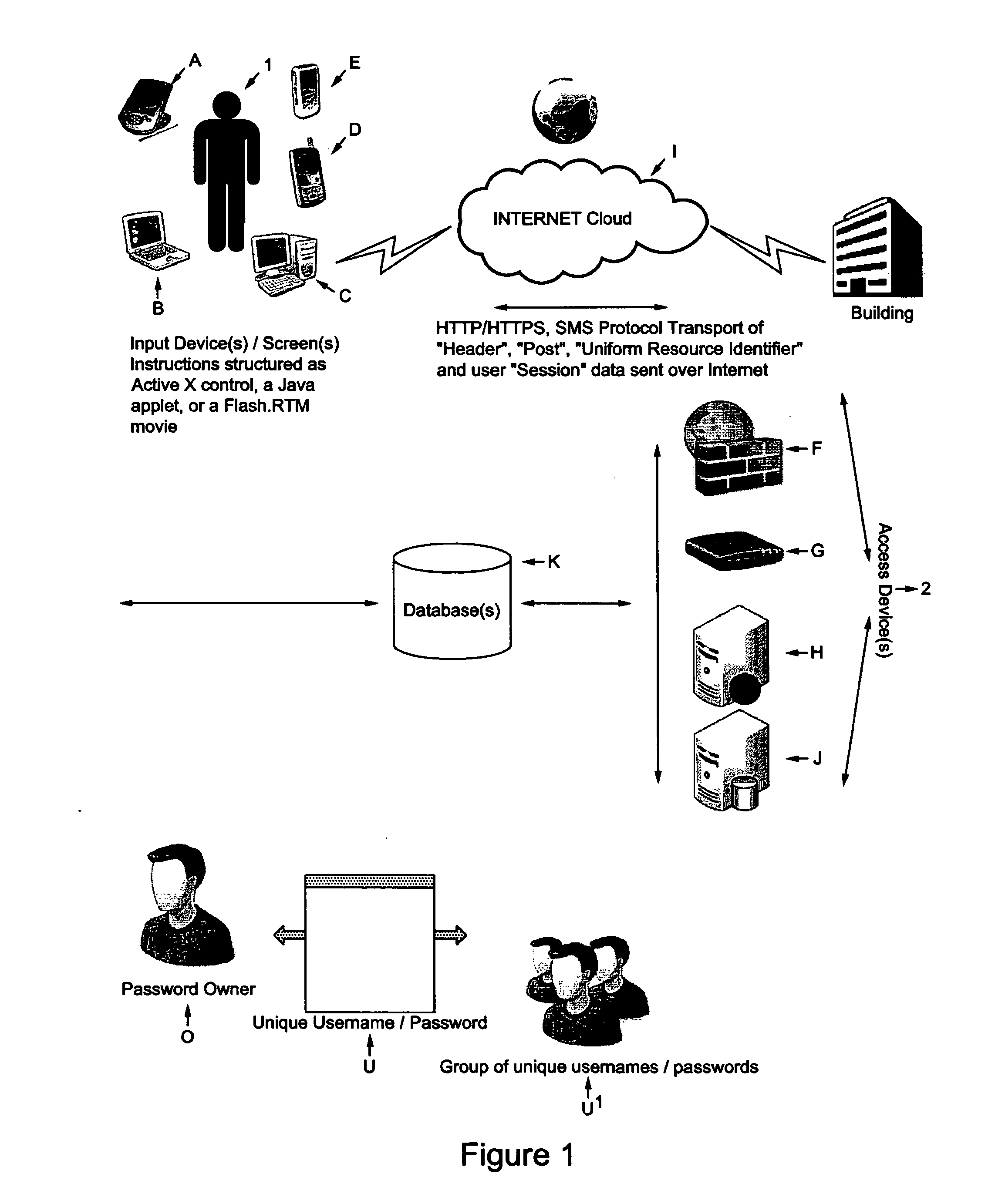
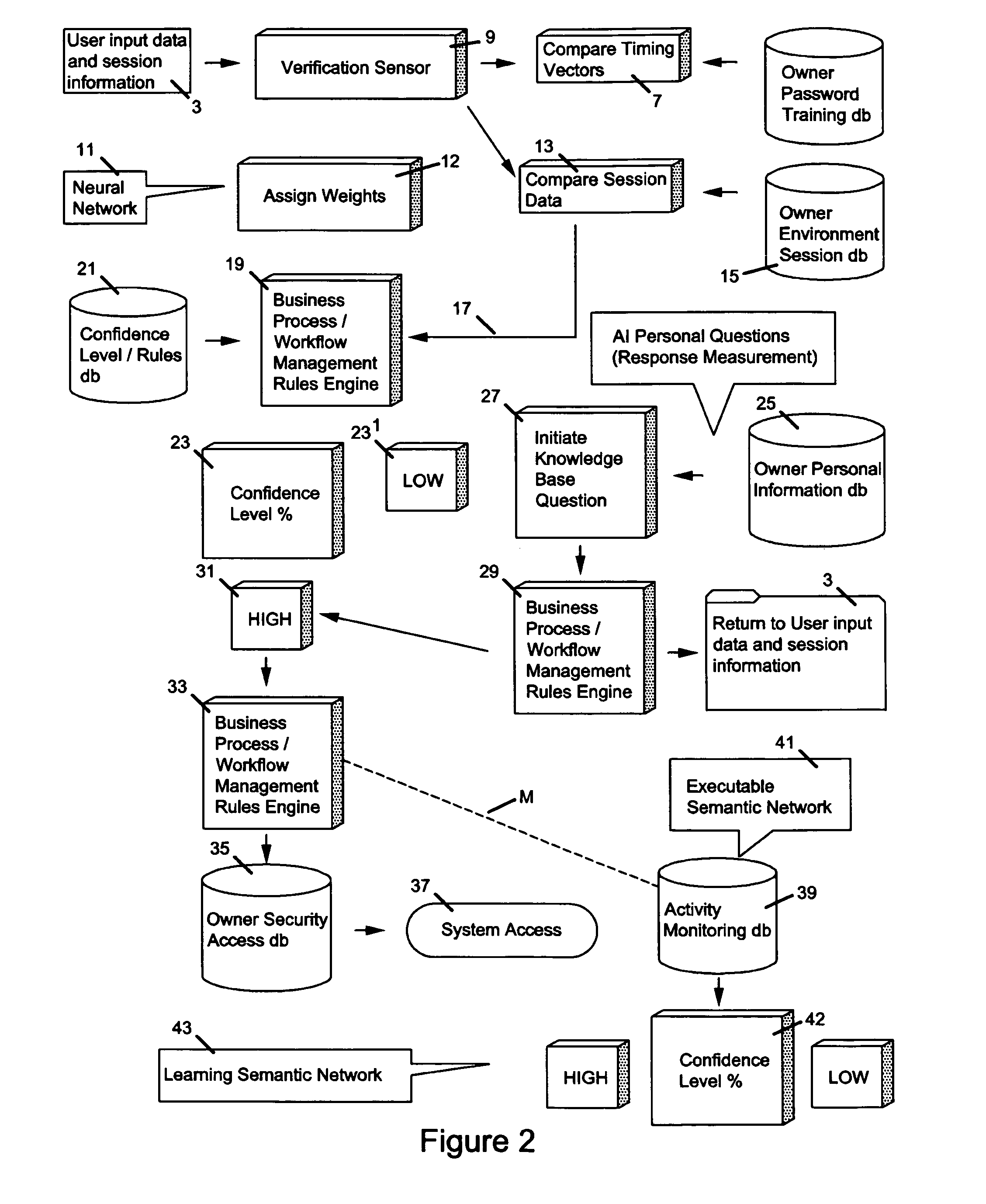
Method of and apparatus for combining artificial intelligence (AI) concepts with event-driven security architectures and ideas
ActiveUS20100036783A1Improve security levelDigital data processing detailsUser identity/authority verificationNerve networkAlgorithm
User authentication apparatus controlling access to systems, inputs owner's login name and password and then extracts the owner's timing vectors from keystroke characteristics with which the owner forms a training set. A semantic network uses multiple links to indicate that different pattern components of user's behavioral access create different kinds of relationships and “symbolic representations”. A neural network is trained by using each of the owner's timing vectors in the training set as an input. When a user inputs the owner's login name and password, it's checked and the user's timing vector is extracted to type the user's password if checked and demoted in confidence level if otherwise. The user's timing vector is applied to neural network and difference between the input / output is compared with a predetermined threshold; and if the difference is greater than the threshold, is prohibited. Preferably this is aided by response time to personal questions.
Owner:DELFIGO CORP
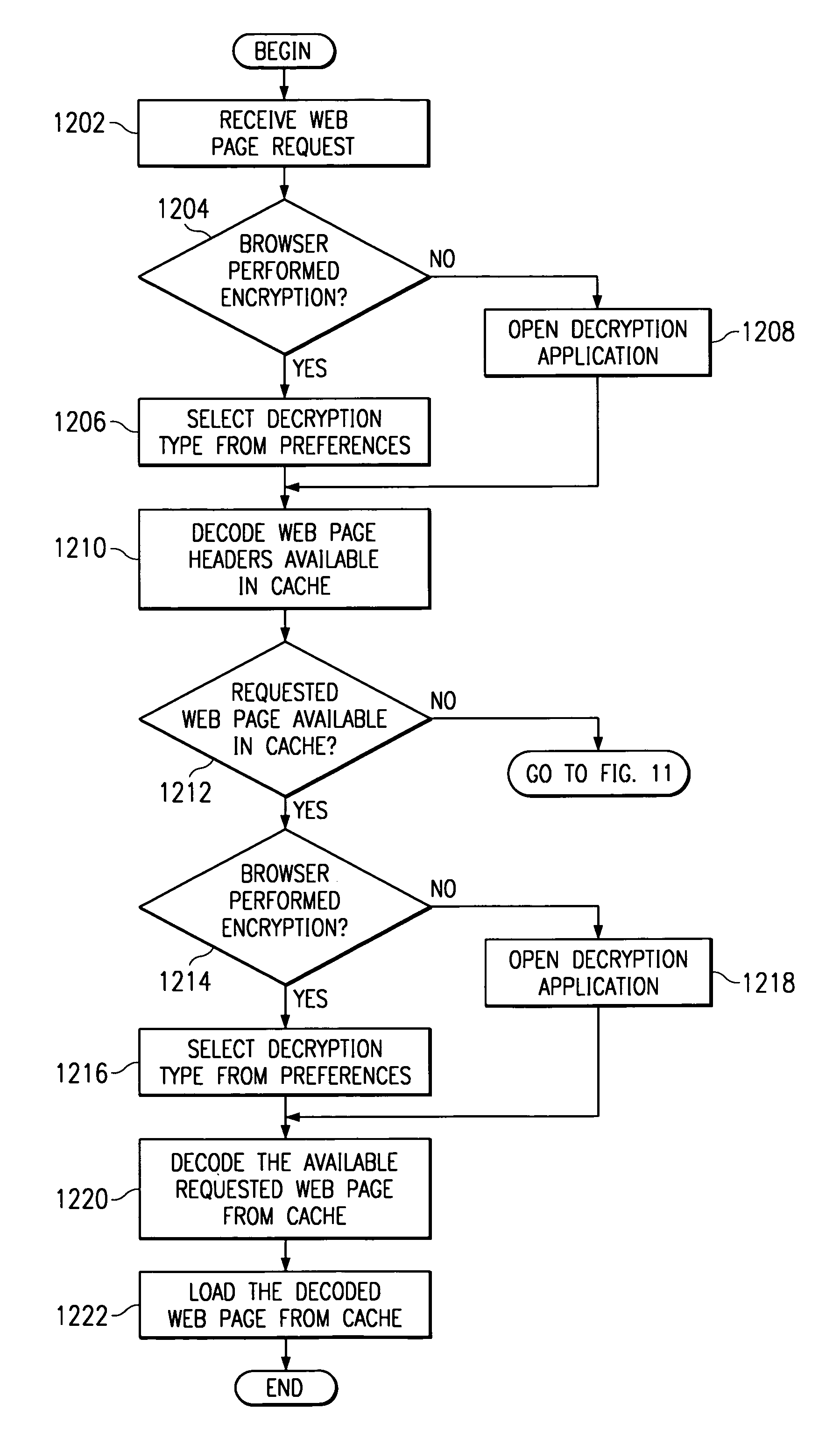
Method and system for encryption of web browser cache
A user normally logs on to a distributed network, such as the user's Internet service, using the user's unique login name and password. The user must then be authorized to write to and read from encrypted information stored in the browser defined cache. The browser cache may be defined as either system memory or disk memory. The user might be required to enter a second password. Information requested by the user is then encrypted, either as a browser function or as an application function of the memory portion defined by the browser. Once authorized by the browser, the user can both read and write to the encrypted information in the cache. Thus, as the user browses network nodes or web pages on a network, the pages are encrypted by the browser before they are cached. Information requested by the user and stored in the cache is first decrypted by the browser and then displayed by the browser.
Owner:IBM CORP
Authentication of a server by a client to prevent fraudulent user interfaces
ActiveUS7685631B1Trust decisionReduce riskDigital data processing detailsUser identity/authority verificationClient-sideWeb page
Protecting a user against web spoofing in which the user confirms the authenticity of a web page prior to submitting sensitive information such as user credentials (e.g., a login name and password) via the web page. The web page provides the user with an identifiable piece of information representing a shared secret between the user and the server. The user confirms the correctness of the shared secret to ensure the legitimacy of the web page prior to disclosing any sensitive information via the web page.
Owner:MICROSOFT TECH LICENSING LLC
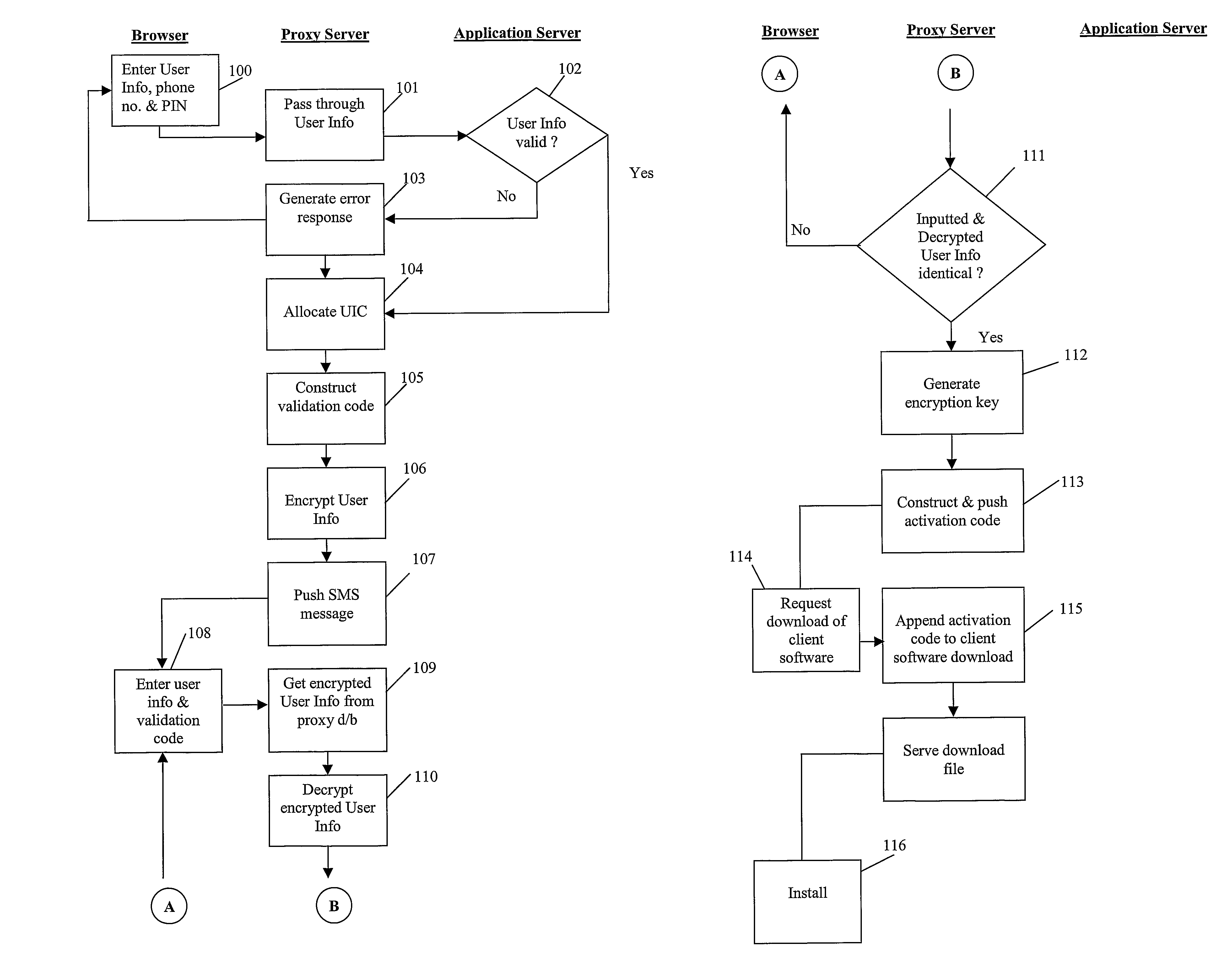
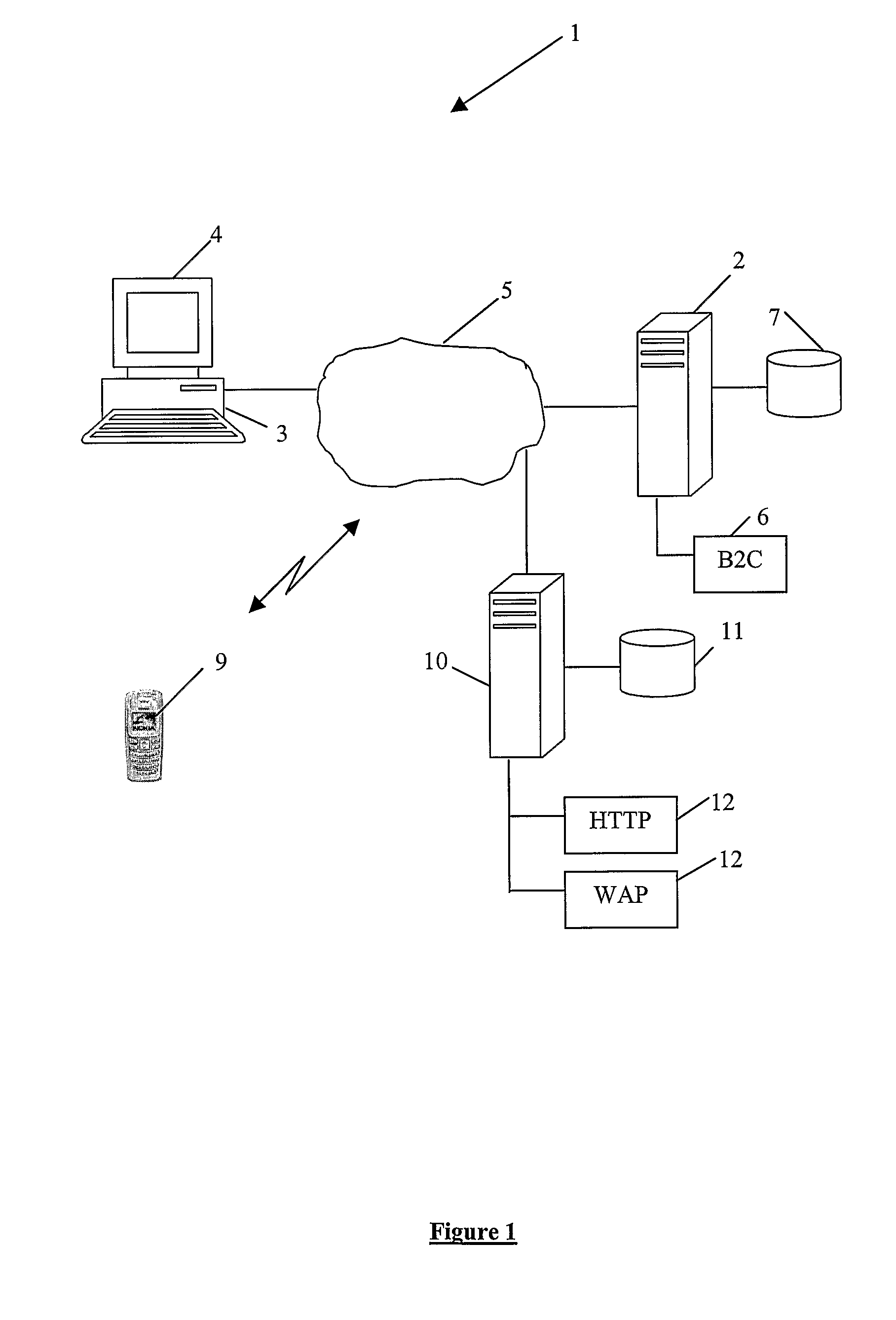
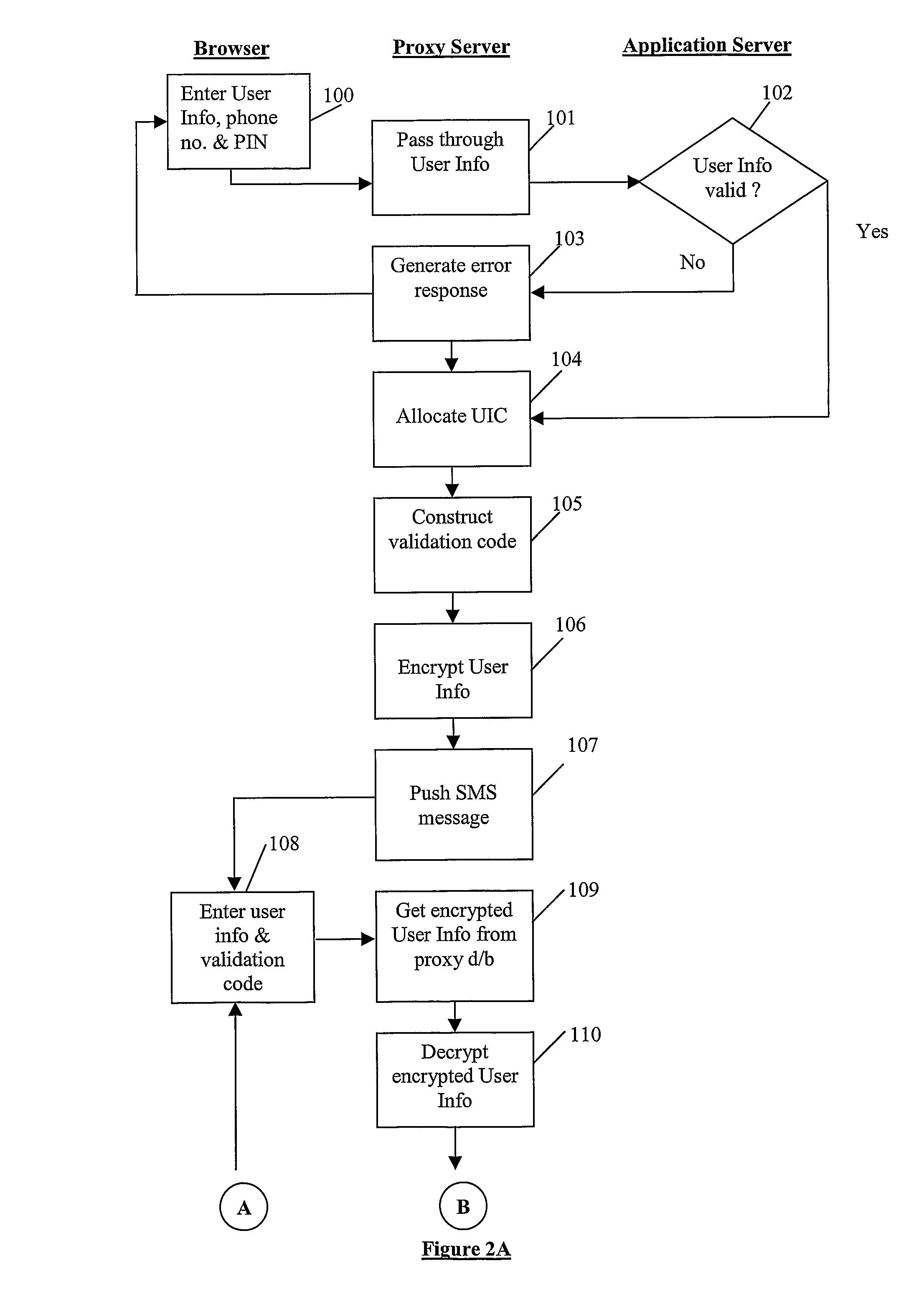
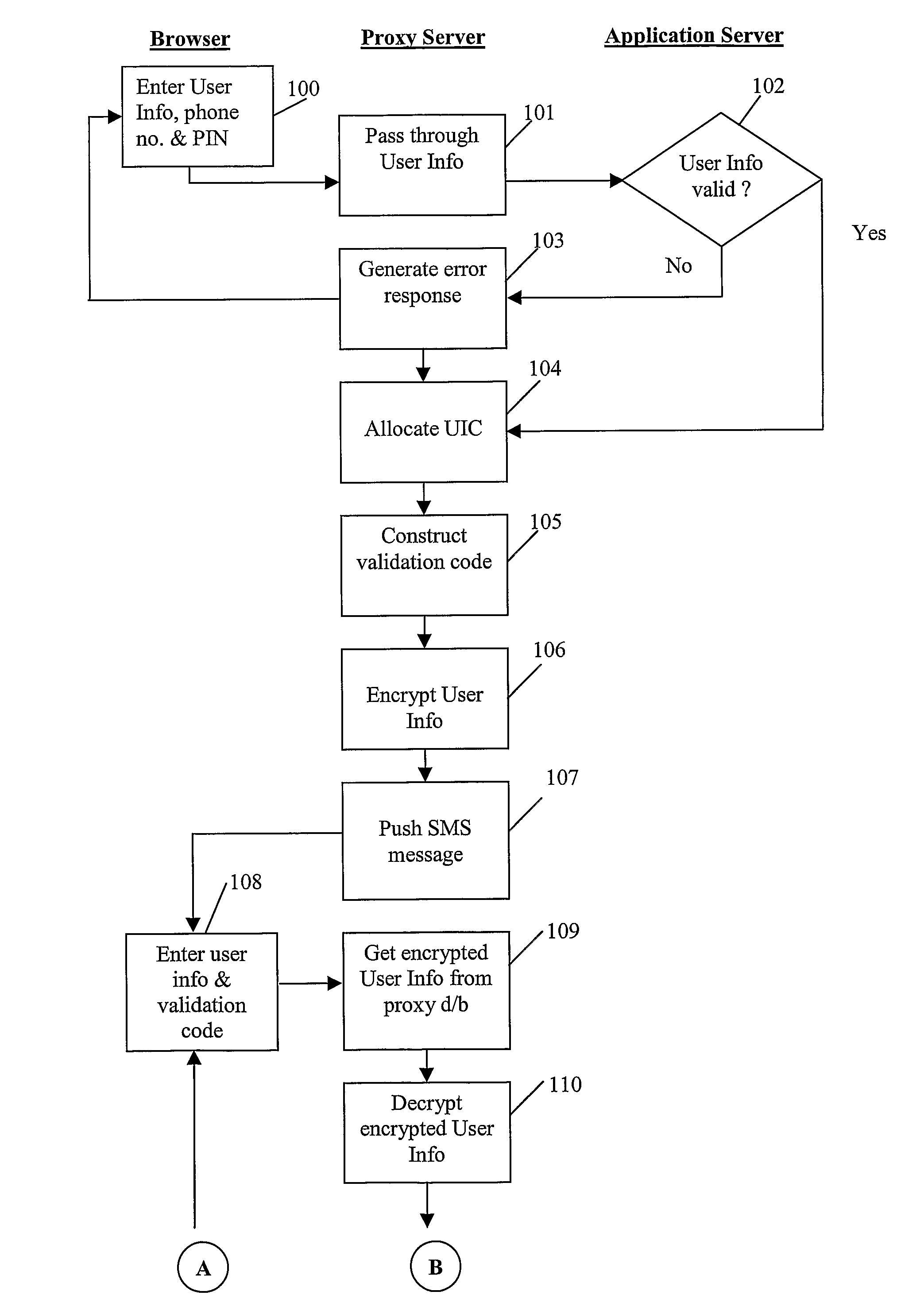
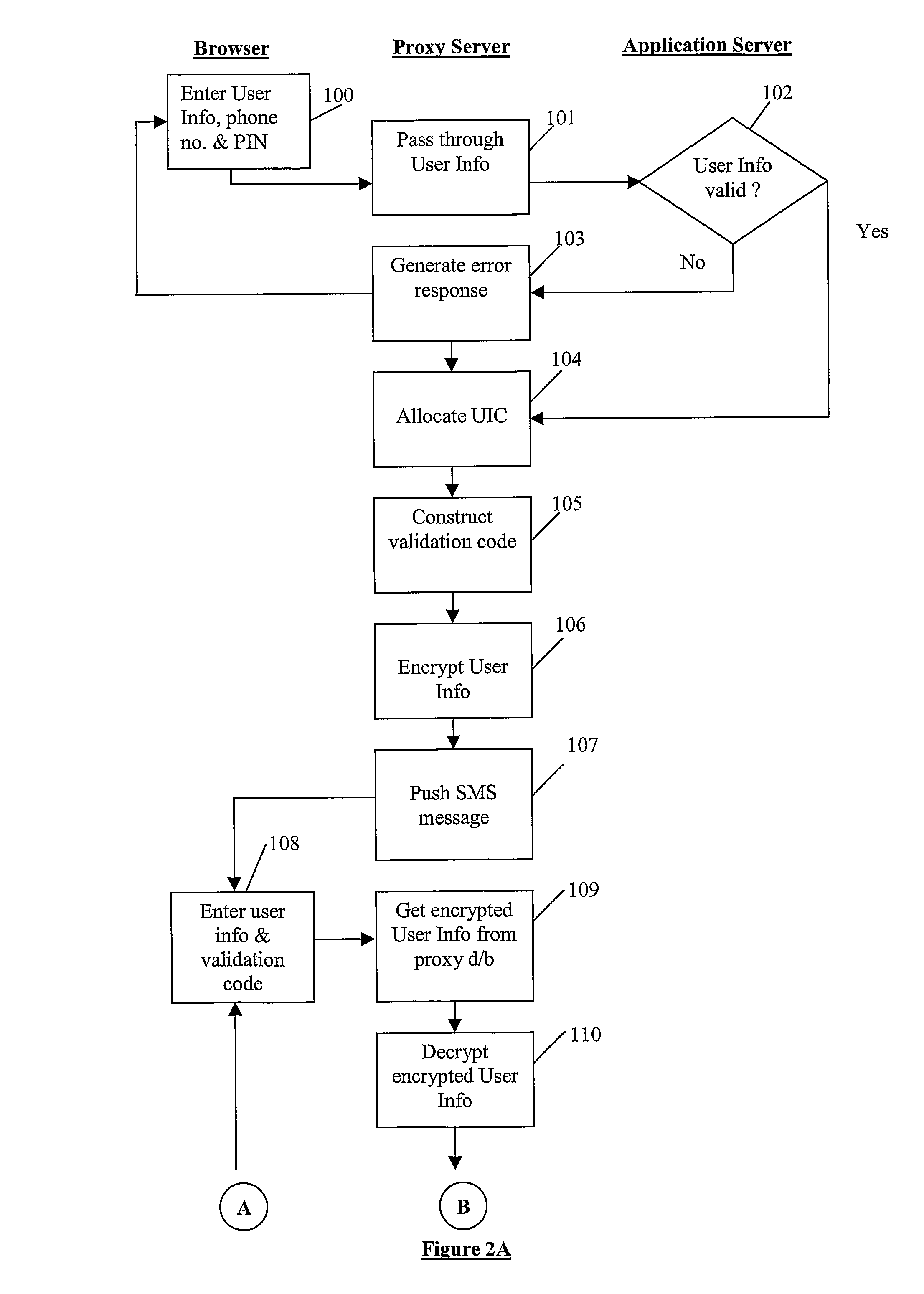
Online Commercial Transaction System and Method of Operation Thereof
ActiveUS20080301057A1Reduce disadvantagesUser identity/authority verificationDigital data authenticationApplication serverLogin Name
A system for conducting commercial transactions comprises an application server that hosts a software application that can be accessed by users to conduct commercial transactions thereon, an application user database of authorised users capable of accessing the application server, each authorised user in the application user database being uniquely identifiable by means of corresponding login name and password, and a proxy server communicable with the application server and accessible by a plurality of registered users from respective mobile phones The proxy server provides each one of the plurality of registered users with access to the application server from that user's respective mobile phone. A proxy database is associated with the proxy server, the proxy database containing details of authorised users in the application user database who are also registered to access the application server through the proxy server from their respective mobile phones. Each registered user in the proxy database is uniquely identifiable by means of a corresponding user identification code, the proxy database also providing, for each registered user, a mapping of that user's user identification code and the user's corresponding user information contained in the application user database. The proxy database stores each registered user's corresponding user information in encrypted format, and the system includes a encryption engine capable of encrypting any data passed between the proxy server and the mobile phone of each registered user. The proxy database also stores an active encryption key for each registered user, the active encryption key being used by the encryption engine to encrypt and decrypt data passed between the proxy server and the user's mobile access terminal. The encryption engine is dynamic, using a different encryption key during each session in which the user accesses the application server from his respective mobile phone, the encryption engine generating, during each session, a further encryption key for the user and transferring the further encryption key to the user's mobile phone for storage therein.
Owner:CORK GROUP TRADING
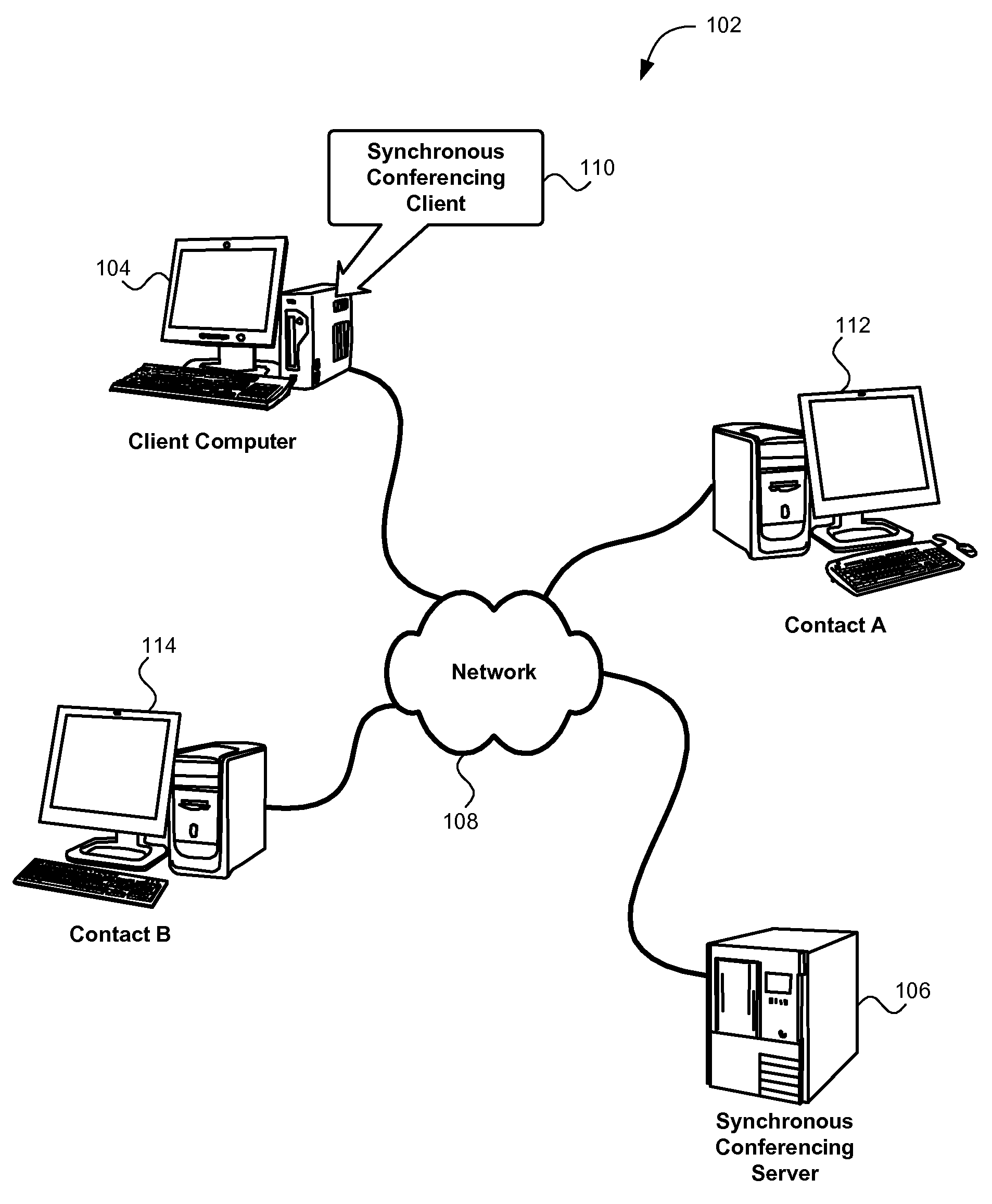
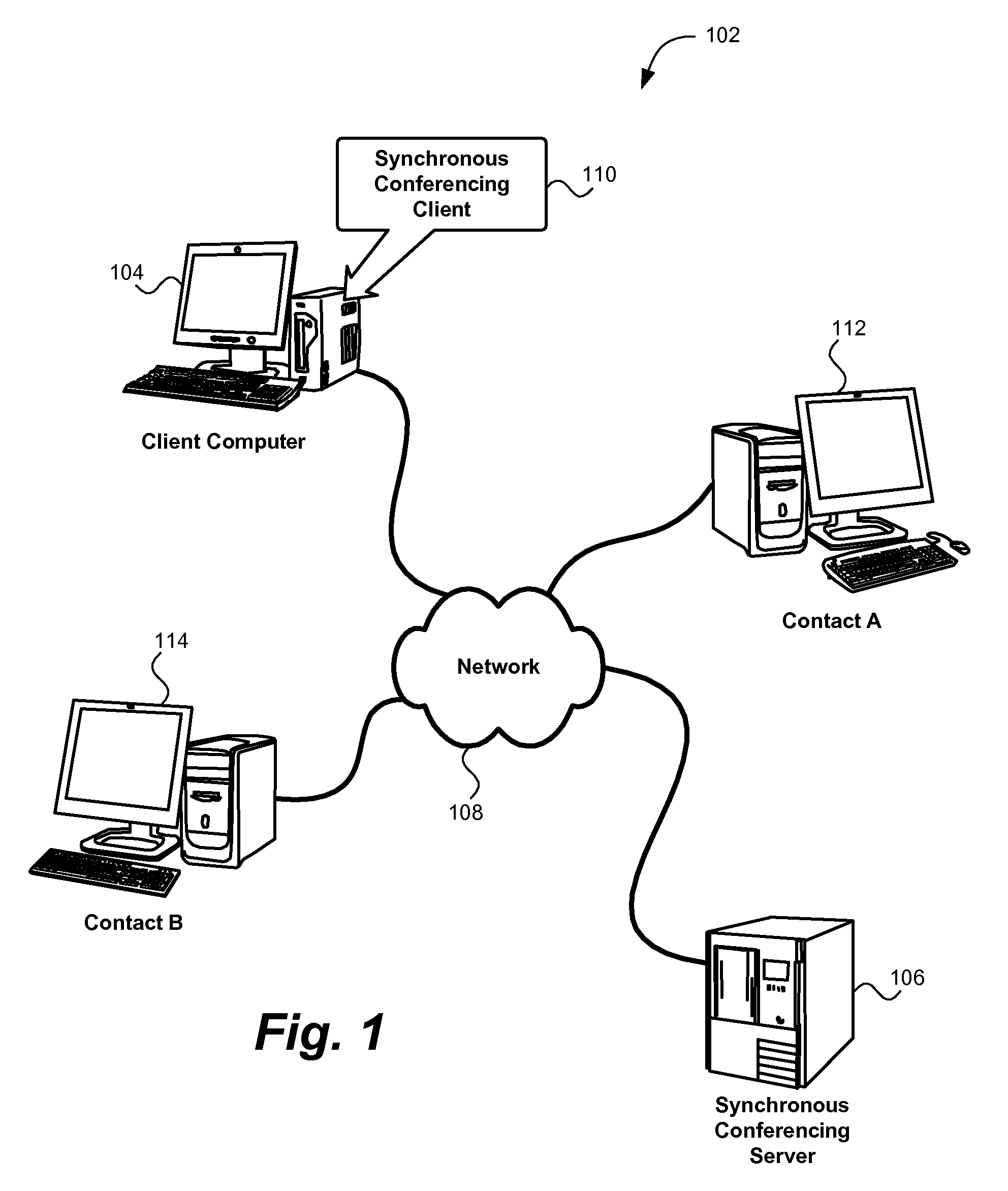
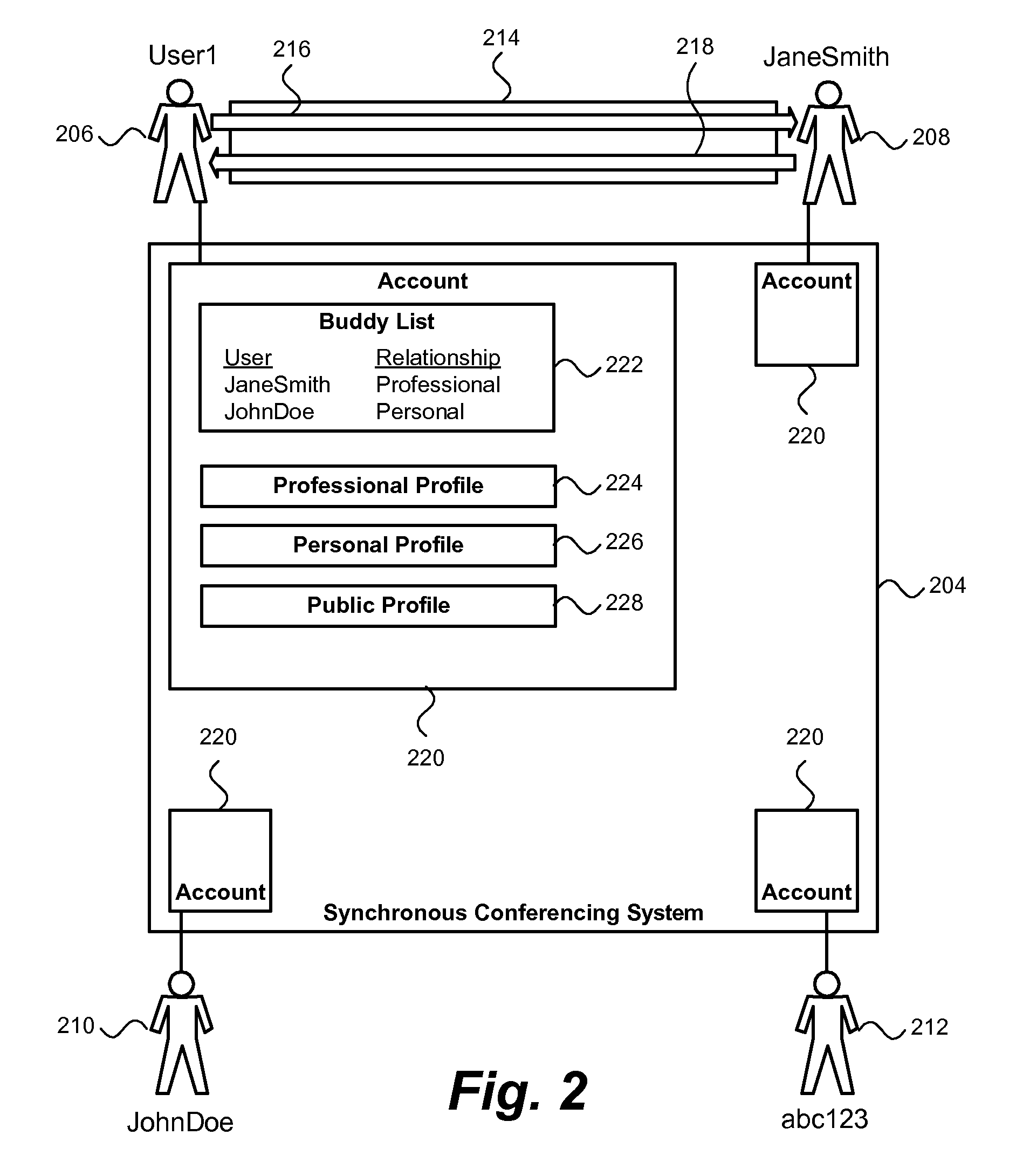
Multiple profiles for a user in a synchronous conferencing environment
ActiveUS20090177974A1Data switching networksInput/output processes for data processingSynchronous conferencingData field
Owner:HCL TECH LTD
Image processing apparatus, information transmission method and image processing system
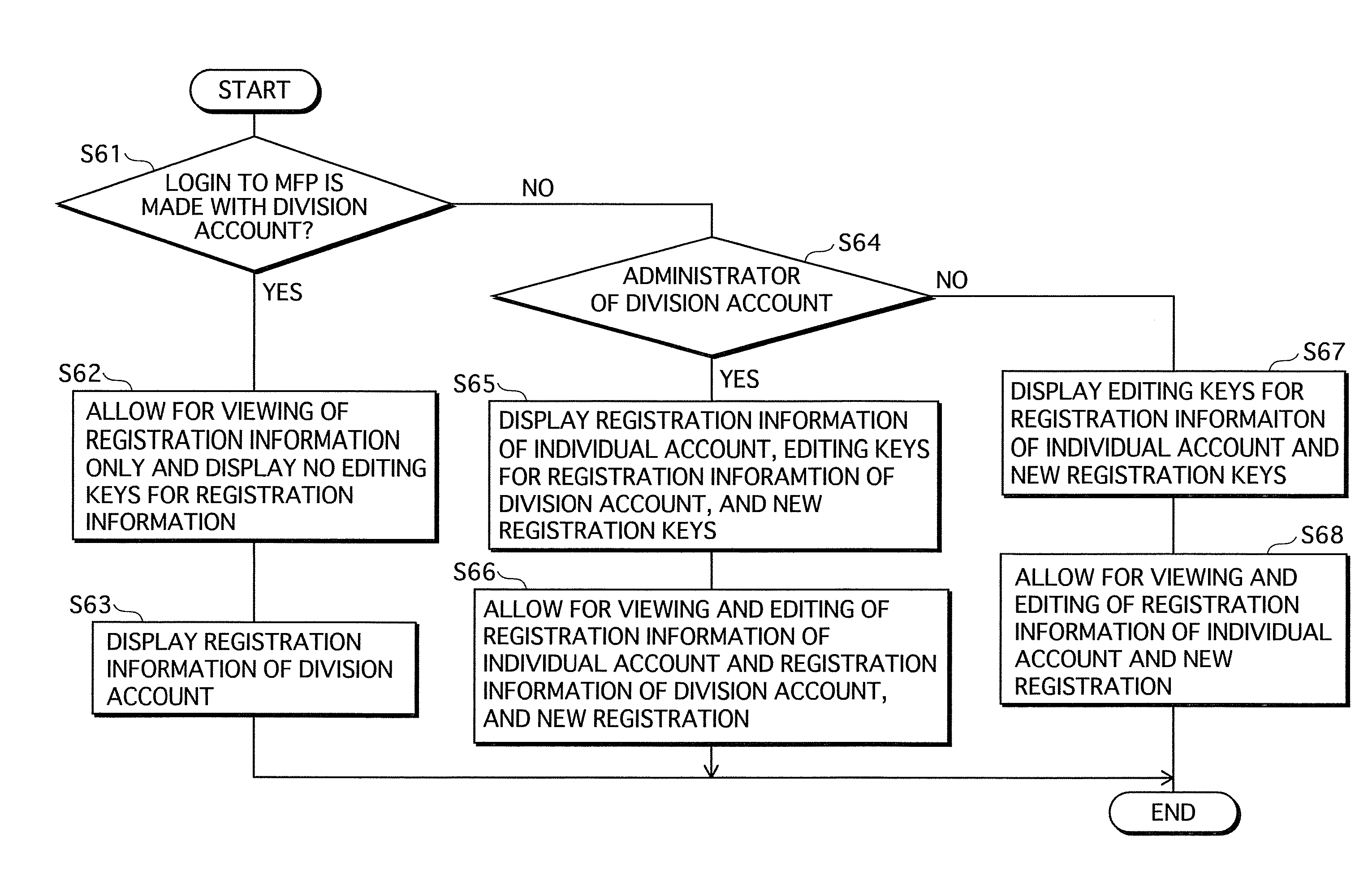
ActiveUS20080074693A1Trouble in key operationReduce troubleDigital data information retrievalDigital computer detailsInformation transmissionImaging processing
The present invention provides an image processing apparatus that reduces the troubles of key operations, while ensuring the security, when access is made to a web server. The image processing apparatus comprises: (a) an identification unit operable to identify a login name of a user of the image processing apparatus; (b) a web server management table in which, with respect to each login name, location information indicating a location of a web server is associated with transmission information to be transmitted to the web server; and (c) a transmission unit operable to transmit the transmission information to the web server, the location of which is indicated by the location information pertaining to the identified login name in reference to the web server management table.
Owner:KONICA MINOLTA BUSINESS TECH INC
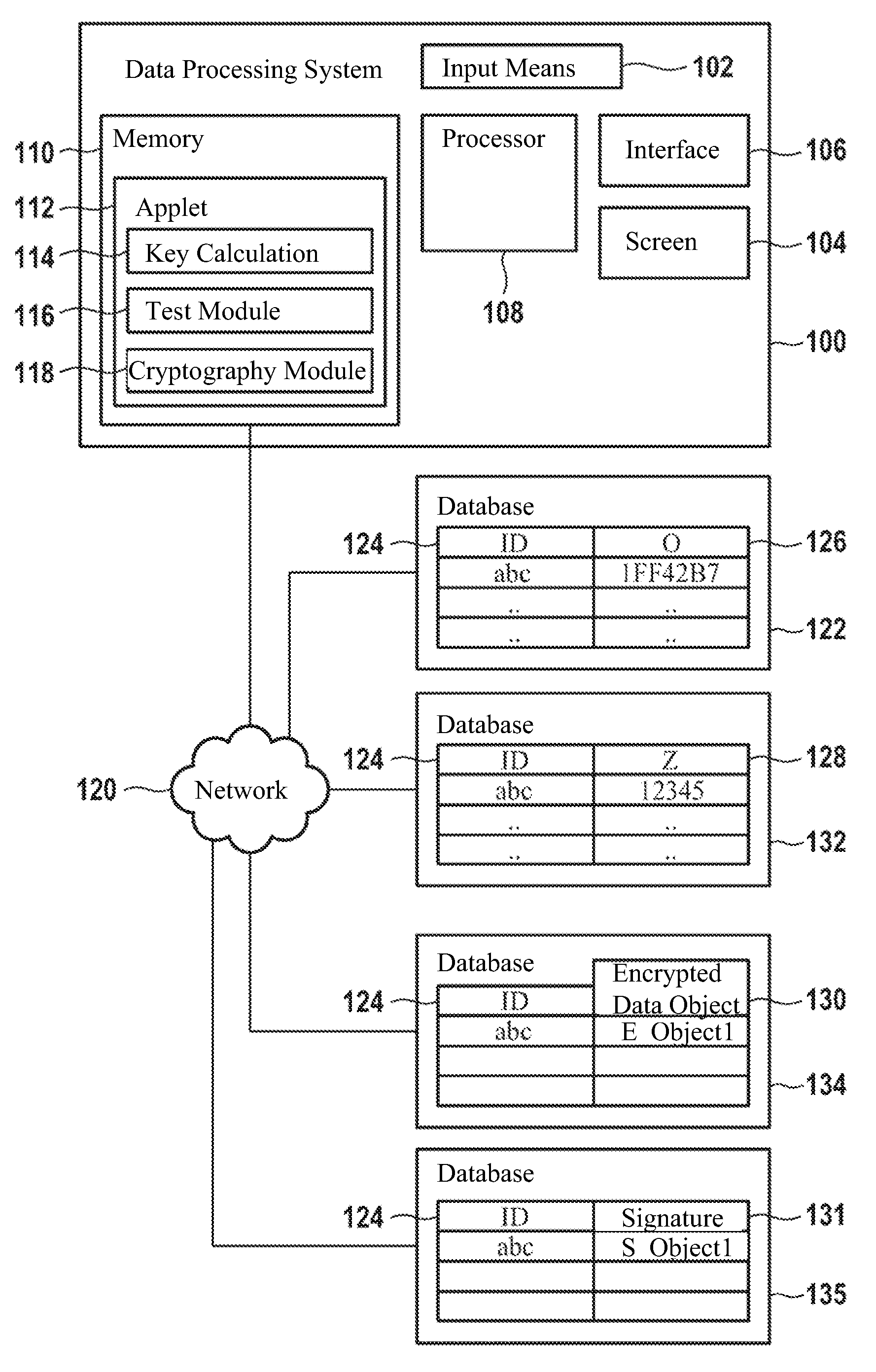
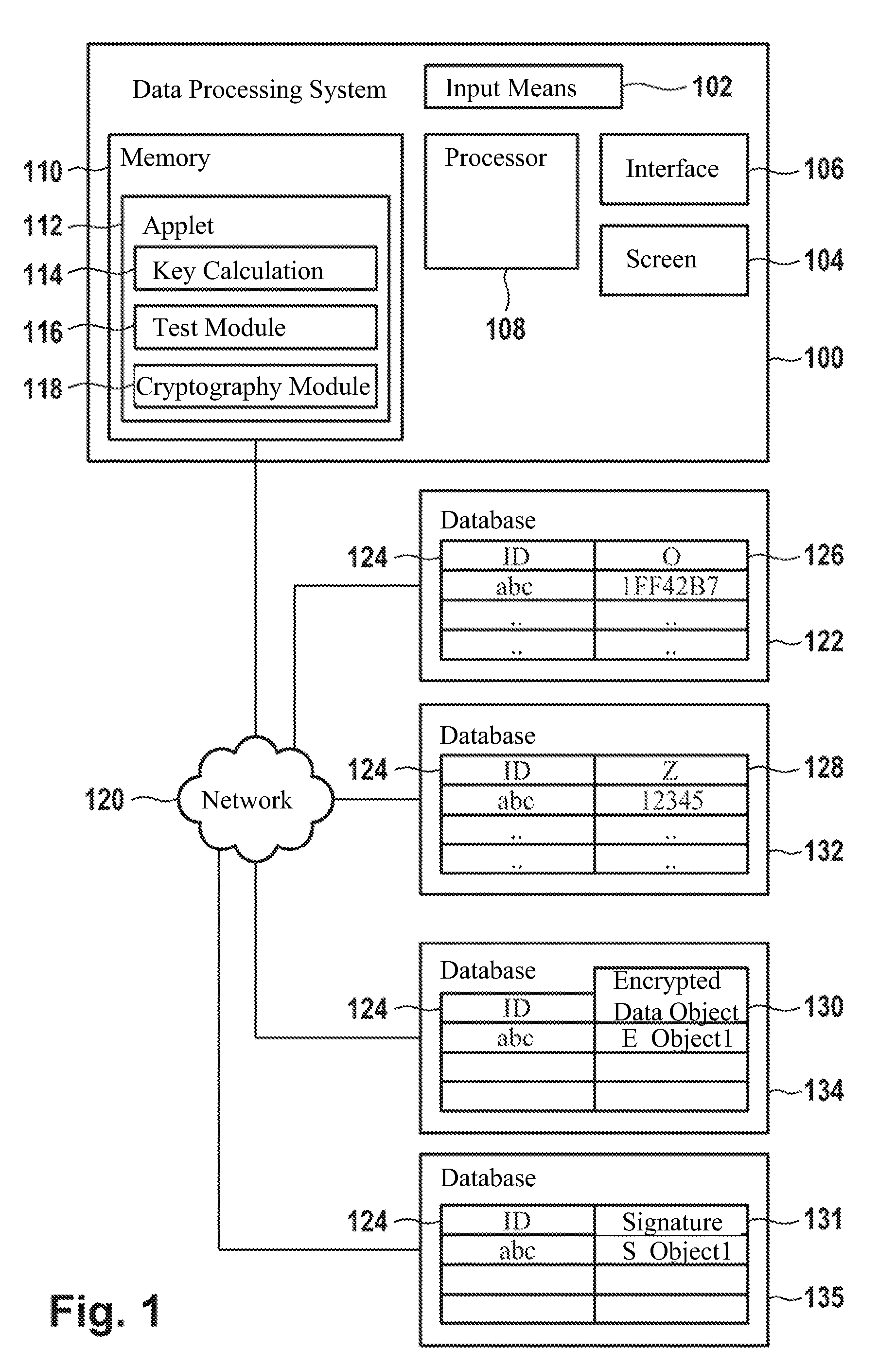
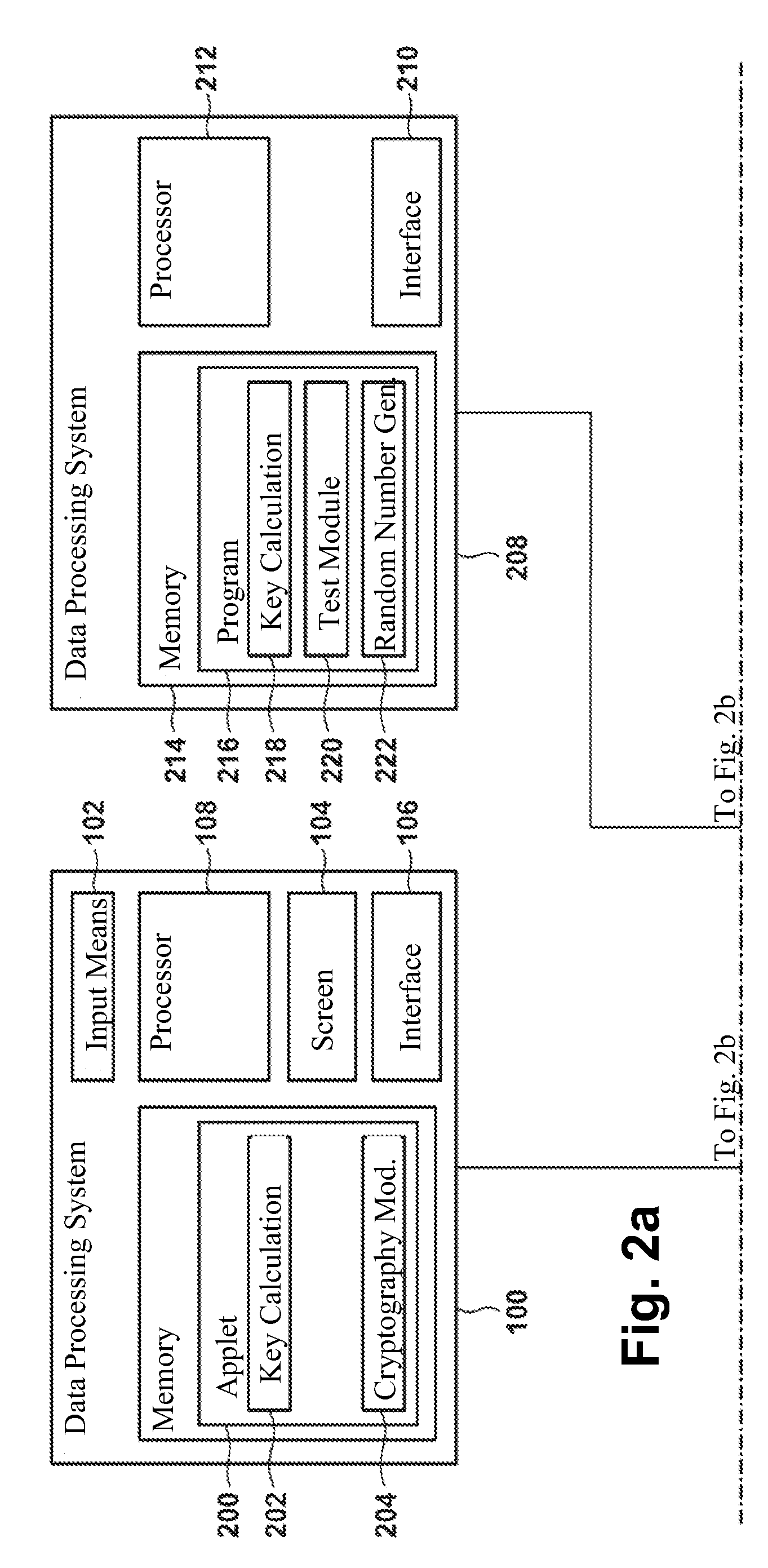
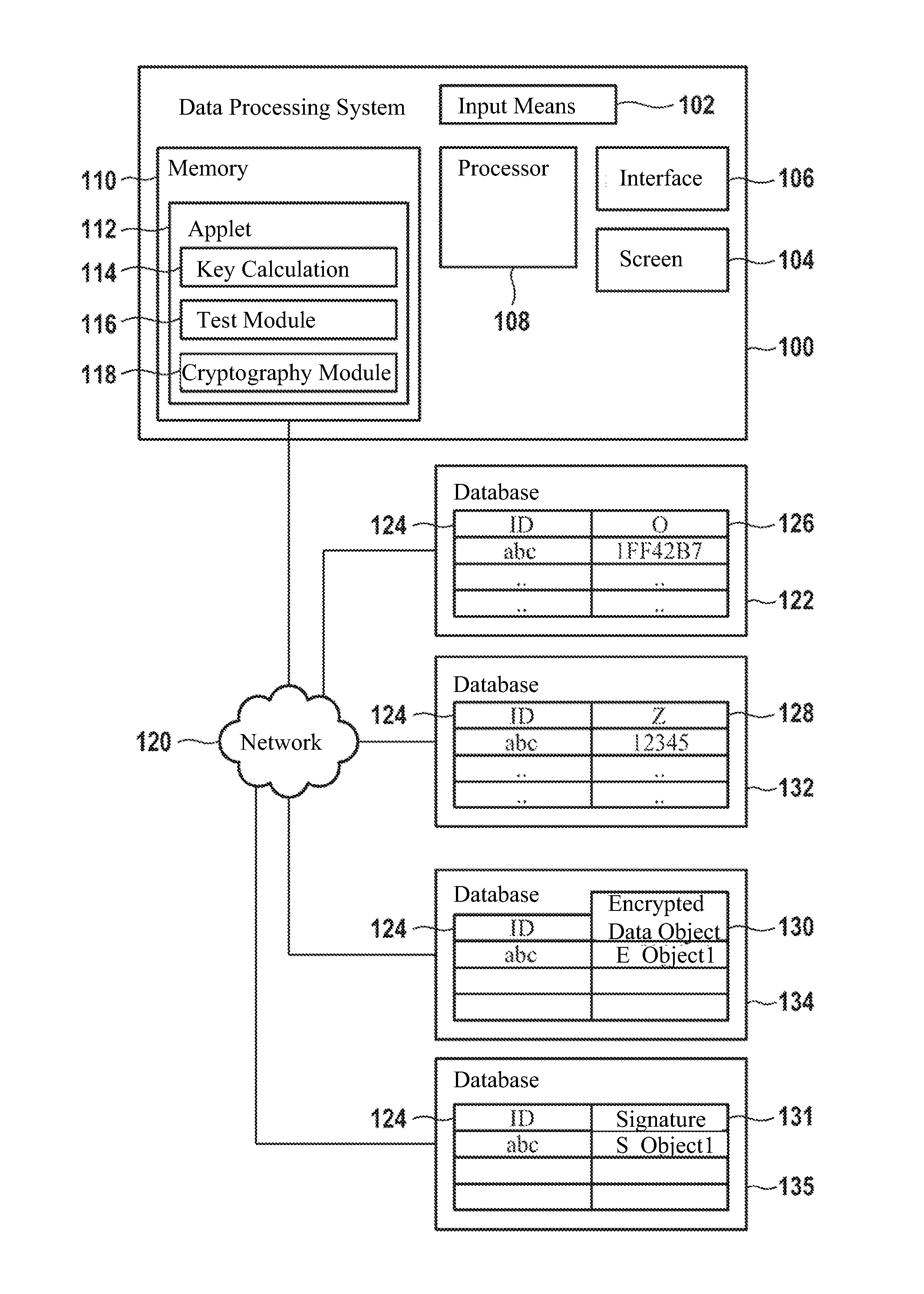
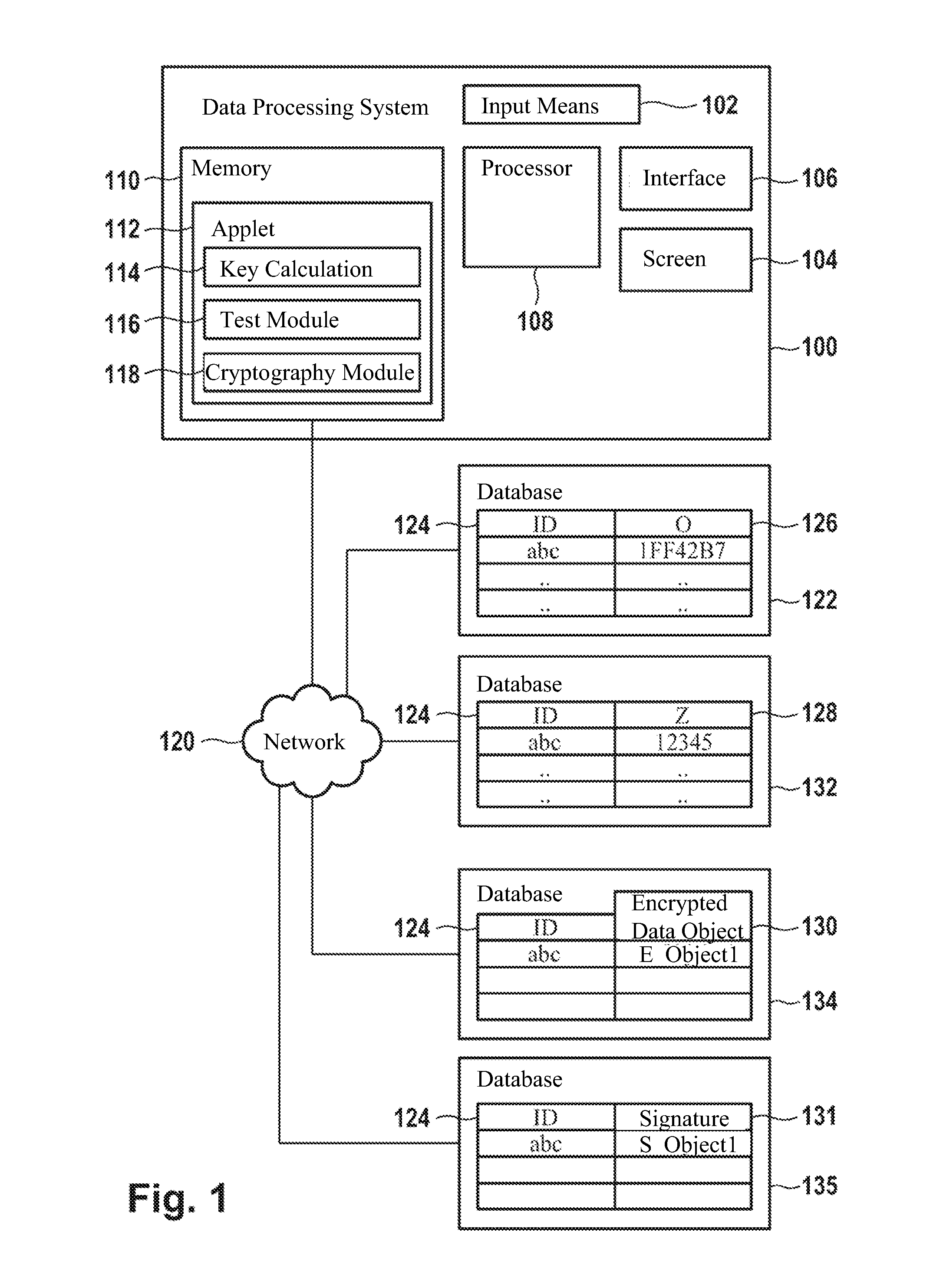
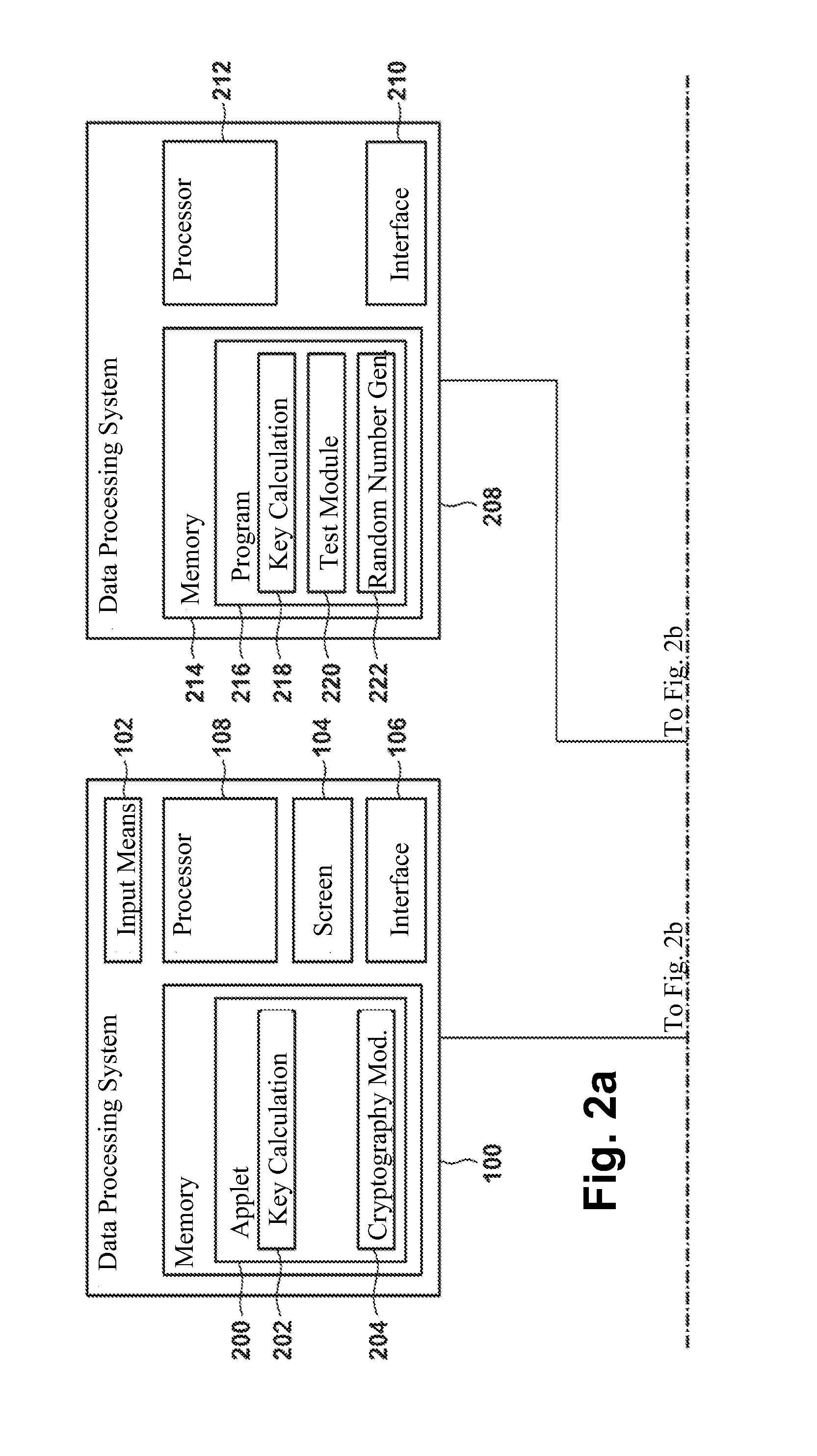
Method for generating an asymmetric cryptographic key pair and its application
The invention pertains to a method, computer readable medium, and data processing system for generation of an asymmetric cryptographic key pair including reception of an arbitrarily selectable login name, calculation of a first data object key, whereby a random value and the login name are included in the calculation, and calculation of a second data object key from the first data object key, whereby the first and second data object keys form the asymmetric cryptographic key pair.
Owner:COMPUGRP MEDICAL SE
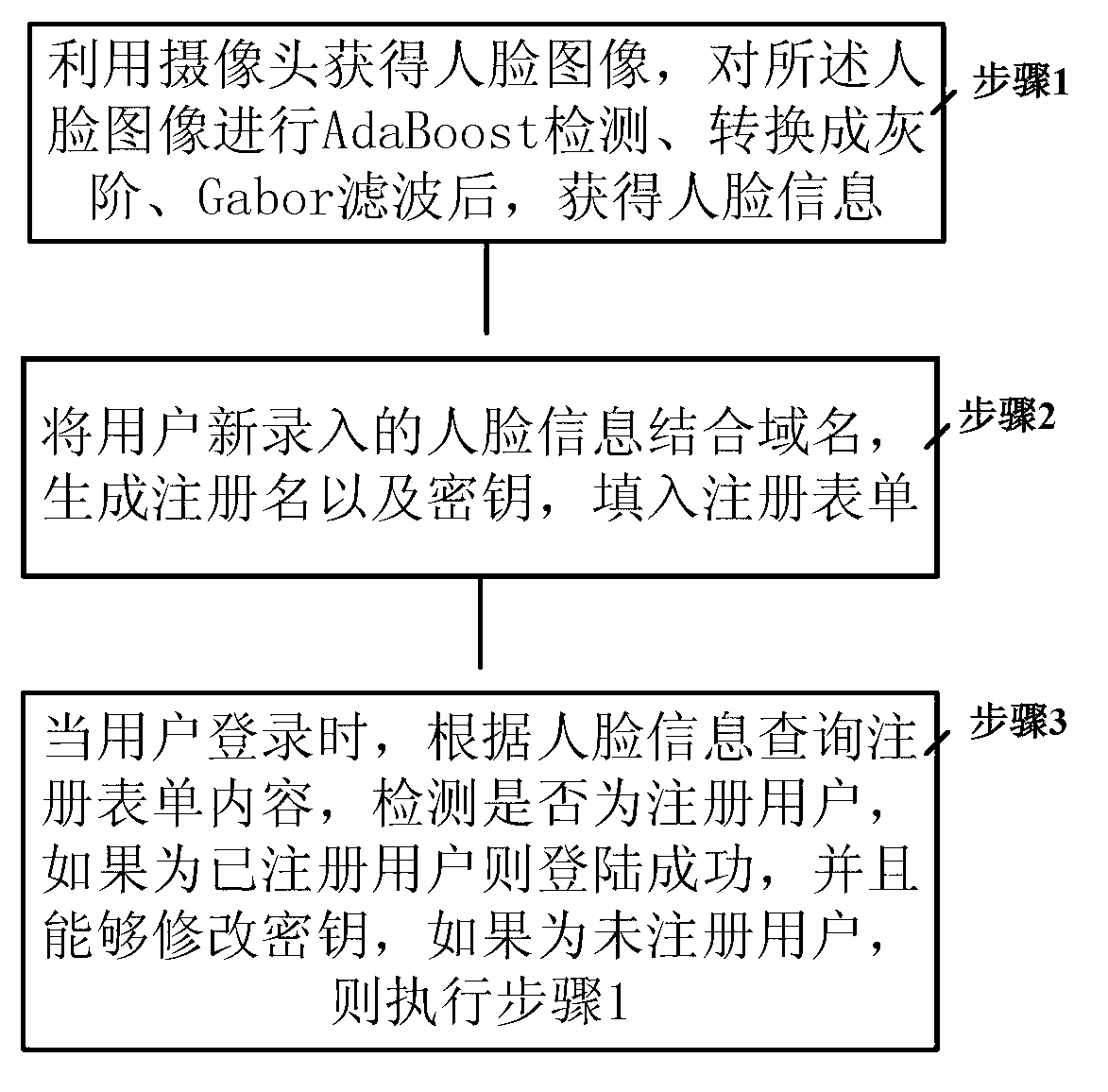
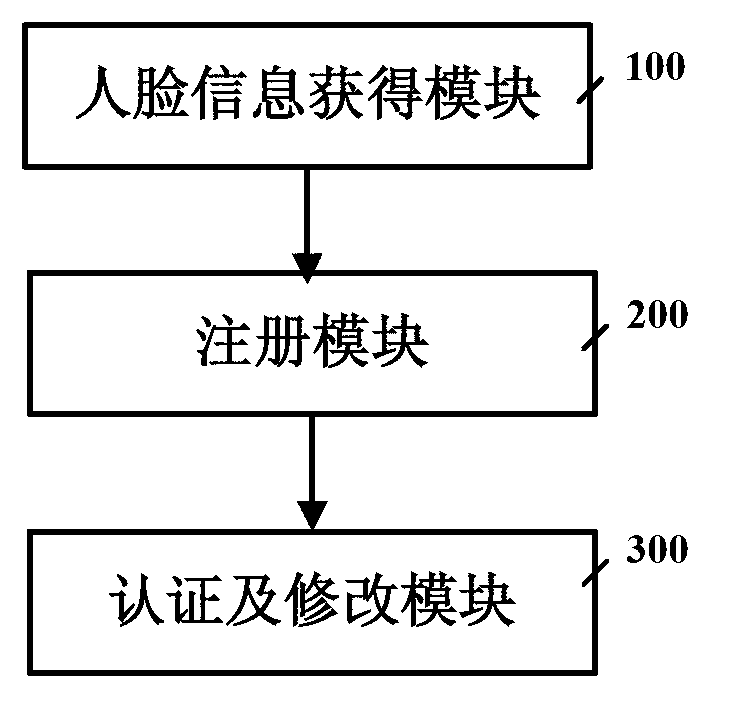
User registration authentication method and system based on facial features
The invention provides a user registration authentication method and a system based on facial features. The user registration authentication method is characterized by comprising the following steps: (1) obtaining a facial picture through a camera, conducting AdaBoost detection, gray level conversion and Gabor filtering to the facial picture, and obtaining facial information, (2) generating a login name and a secret key through combination of the new facial information input by a user and a realm name, and filling the login name and the secret key into a login form, and (3) when the user logs in, requiring content of the login form according the facial information, detecting whether the user is a registered user, if the user is the registered user, logging in successfully, modifying the secret key, and if the user is a unregistered user, conducting the step (1). According to the user registration authentication method and the system based on the facial features, the facial information and a secret system are combined, the process of authentication identification is enabled to be guaranteed, and meanwhile convenience is brought to use.
Owner:青岛爱维互动信息技术有限公司
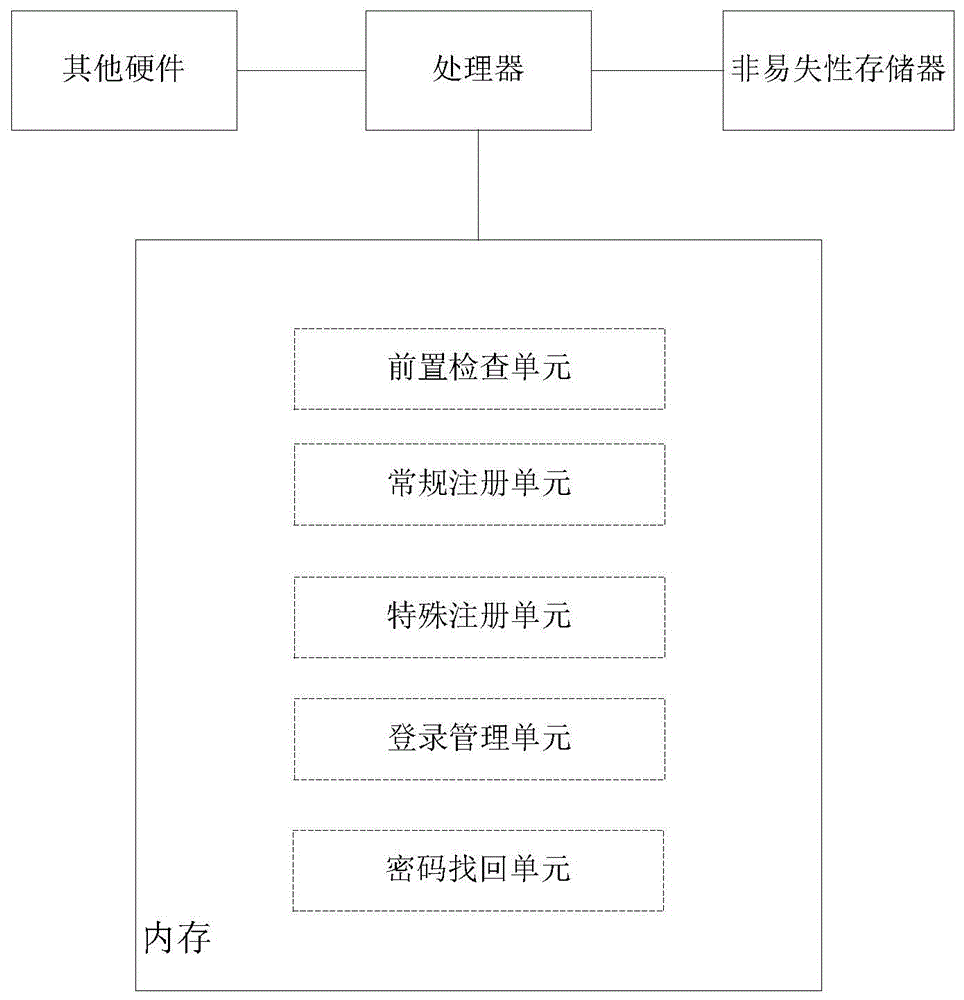
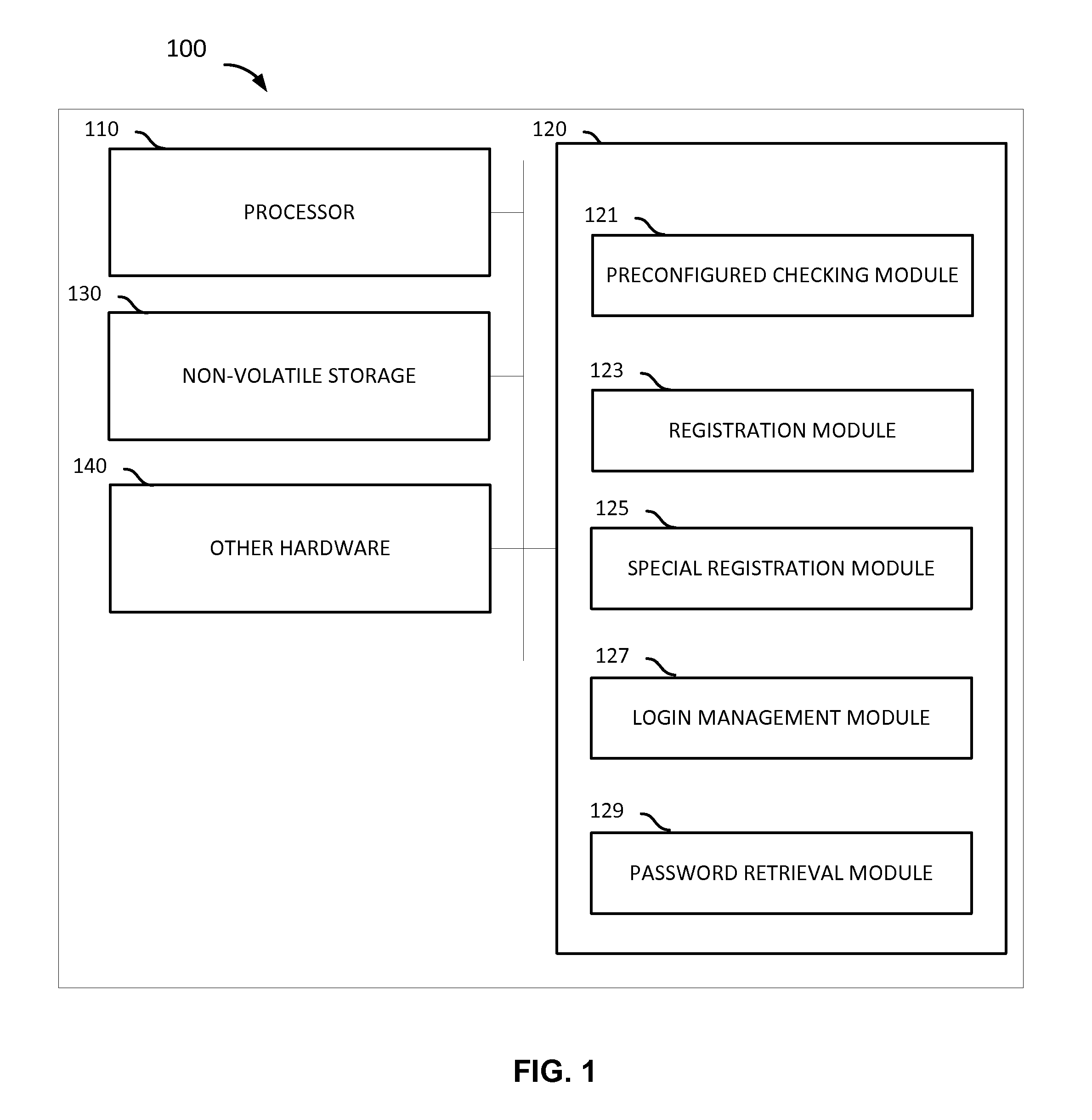
User account management method and device
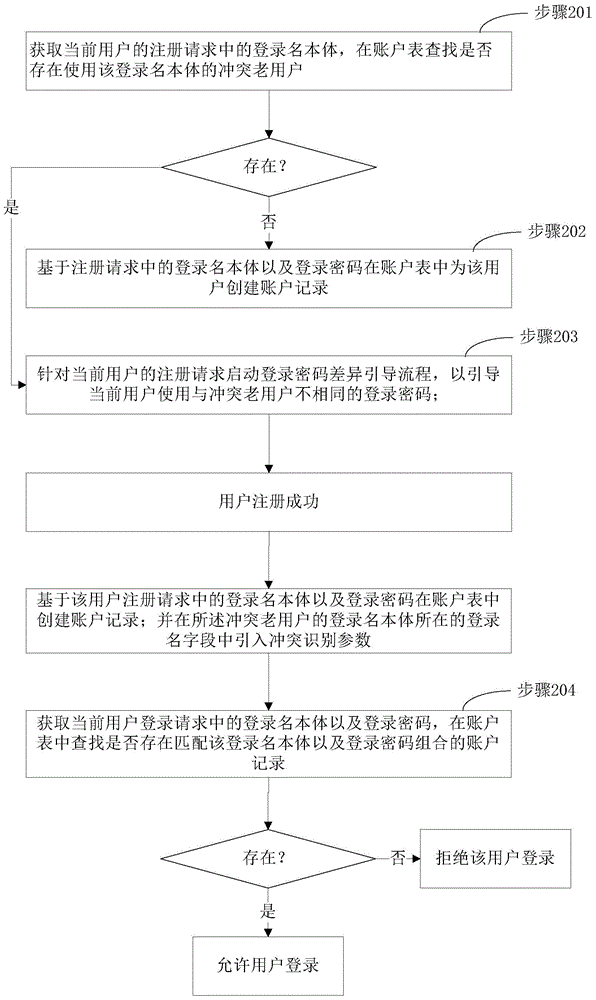
ActiveCN105101196ASolve the decline of experienceHigh cost of solutionDigital data authenticationTransmissionLogin NameComputer science
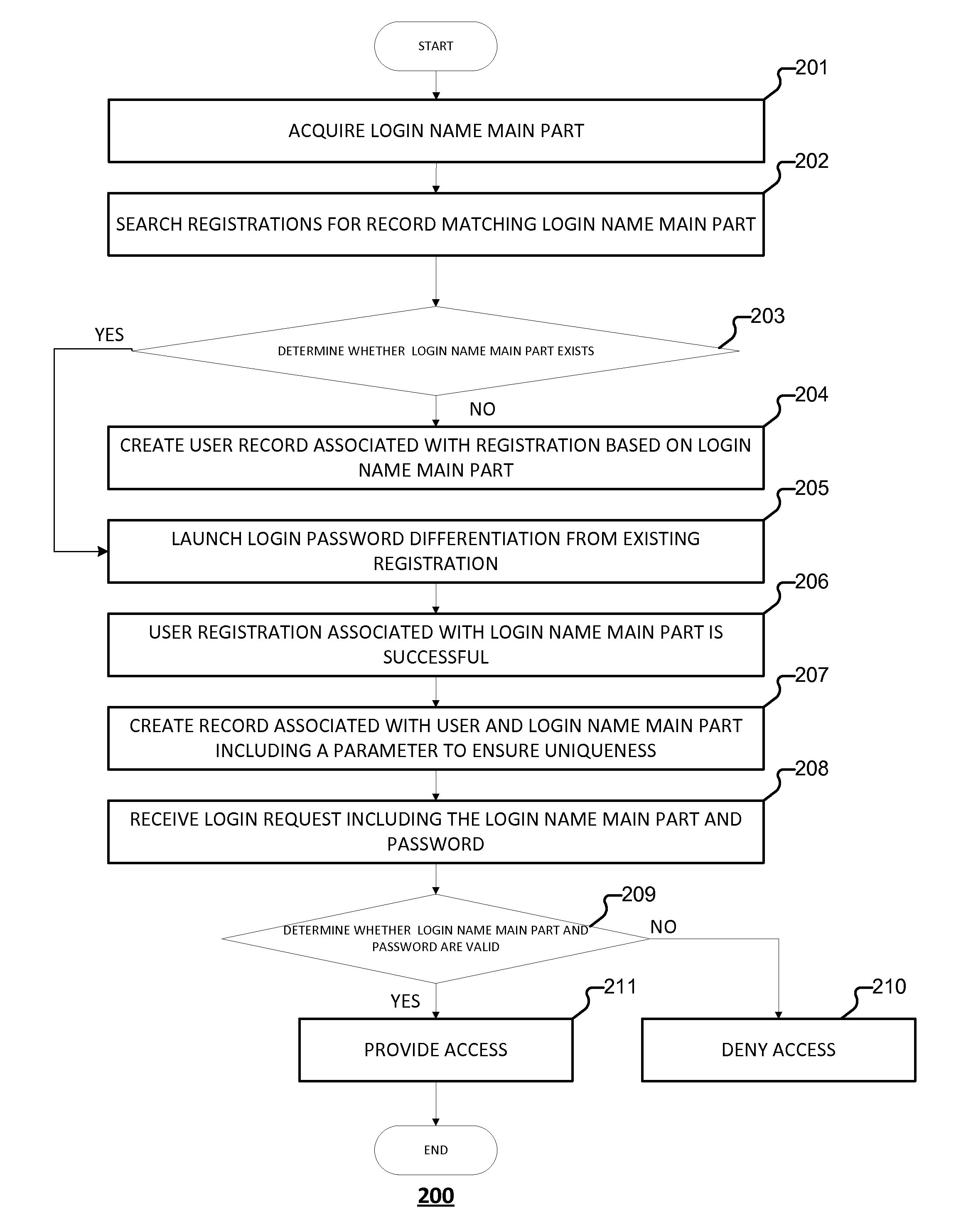
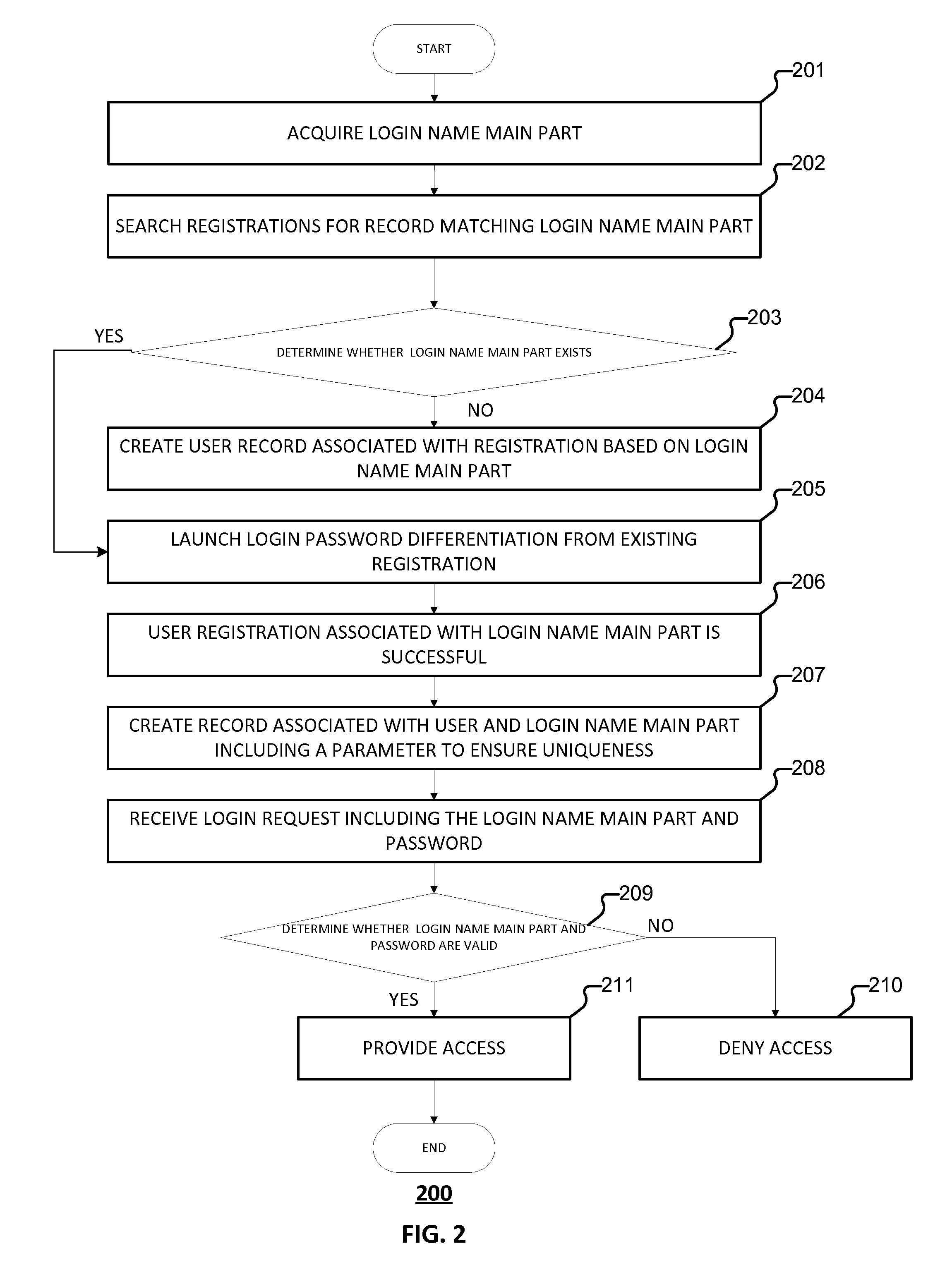
Embodiments of the present application relate to a method and system for managing user accounts. The method includes receiving a registration request from a current user, wherein the registration request comprises a login name main part, determining, in a database, whether a conflicting old user exists, wherein a conflicting old user corresponds to another user that has a conflicting login name main part that is the same as the login name main part received in connection with the registration request, in the event that a conflicting old user exists, executing a login password differentiation process that requires a user to register a different login password that is different from a login password associated with the conflicting old user, and storing the different login password to the database in connection with a registration of the current user.
Owner:ADVANCED NEW TECH CO LTD
Method, apparatus, and system for managing user accounts
ActiveUS20150324579A1Data augmentationDigital data processing detailsMultiple digital computer combinationsLogin NameComputer science
Embodiments of the present application relate to a method and system for managing user accounts. The method includes receiving a registration request from a current user, wherein the registration request comprises a login name main part, determining, in a database, whether a conflicting old user exists, wherein a conflicting old user corresponds to another user that has a conflicting login name main part that is the same as the login name main part received in connection with the registration request, in the event that a conflicting old user exists, executing a login password differentiation process that requires a user to register a different login password that is different from a login password associated with the conflicting old user, and storing the different login password to the database in connection with a registration of the current user.
Owner:ADVANCED NEW TECH CO LTD
Safety login method and system
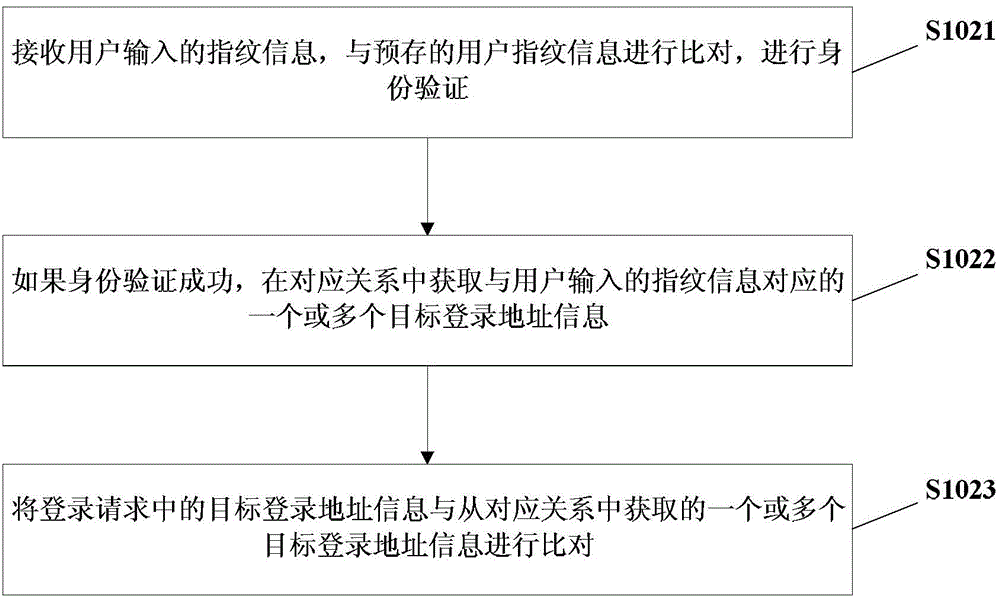
The invention discloses a safety login method and system. The safety login method comprises the steps of prestoring user's fingerprint information and establishing a corresponding relation between the user's fingerprint information and target login address information, a login name and passwords; receiving a login request input by a user and including fingerprint information and target login address information, and comparing the fingerprint information and the target login address information with the user's fingerprint information and the target login address information in the corresponding relation; if comparison is successful, acquiring the login name and the passwords corresponding to the fingerprint information and the target login address information from the corresponding relation, and submitting the login name and the passwords to a target login address to perform automatic login.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
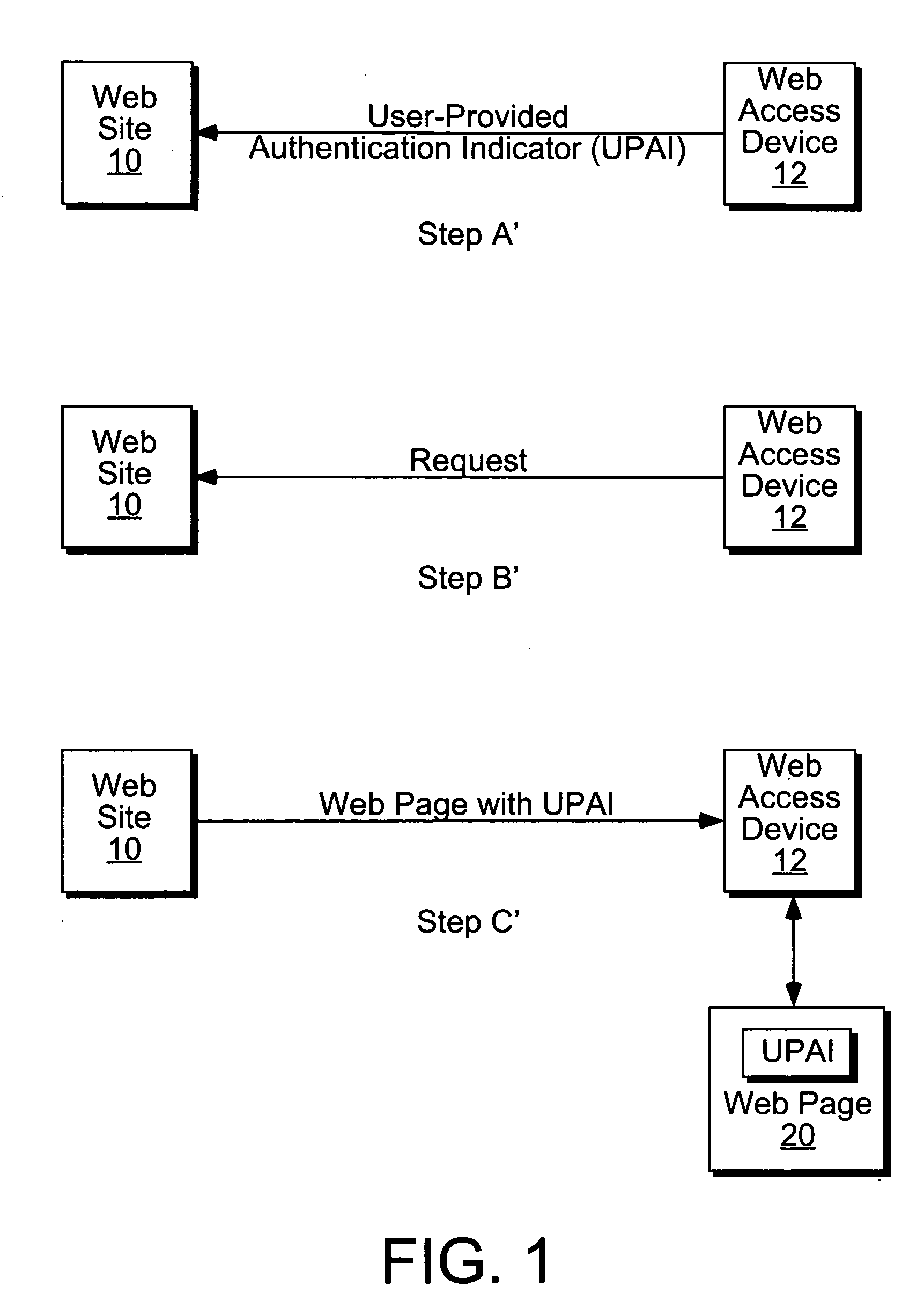
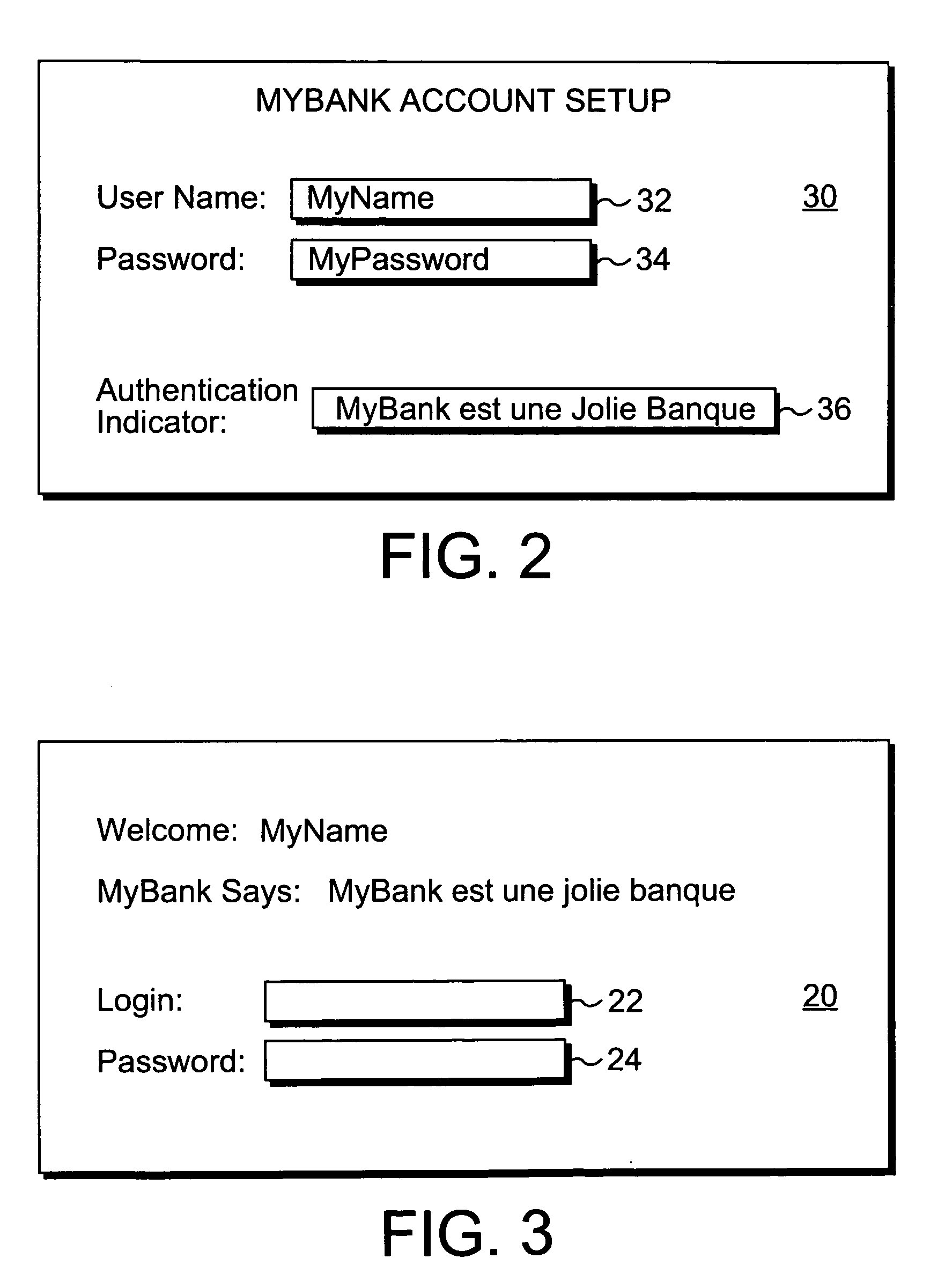
Authenticating a web site with user-provided indicators
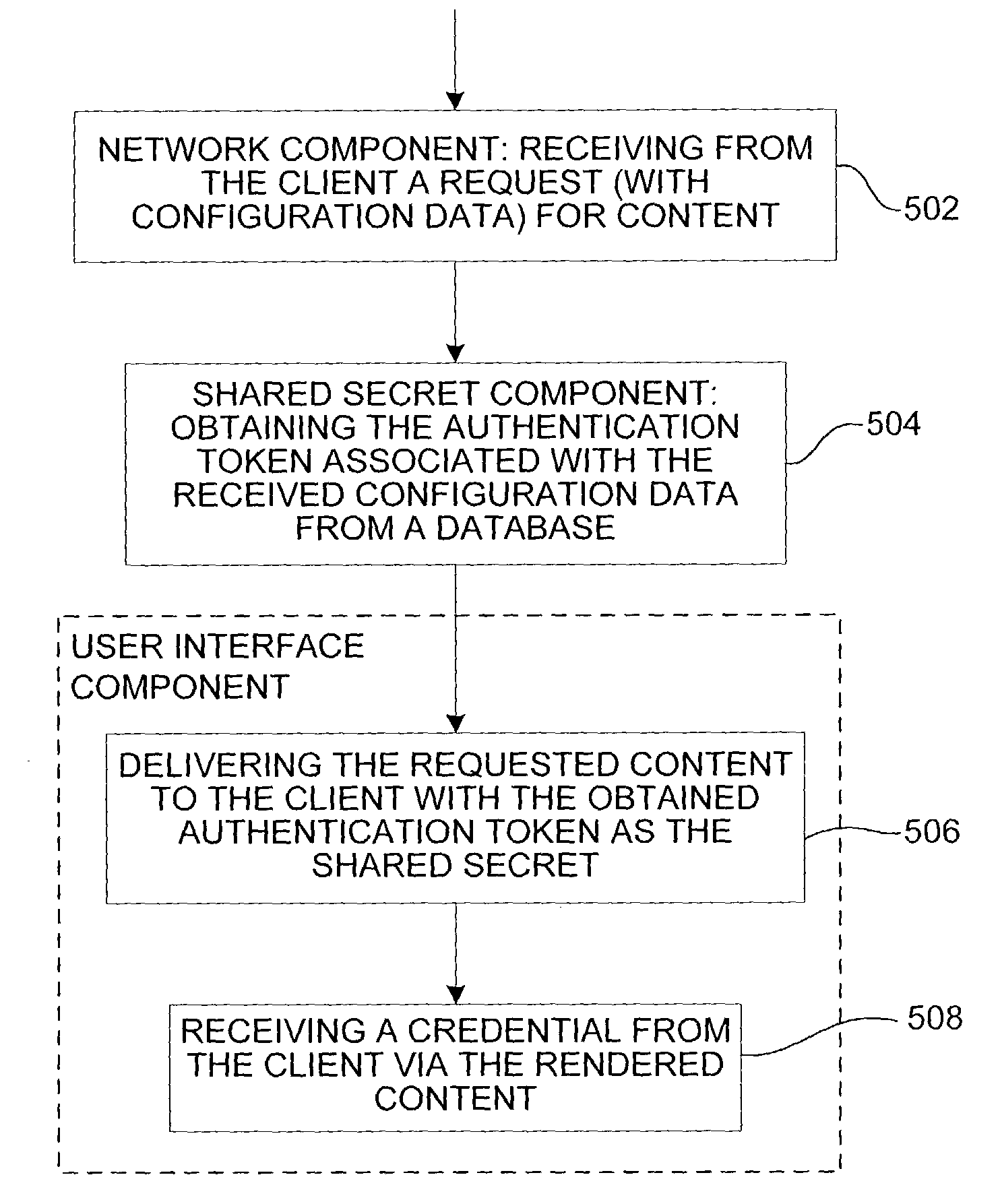
InactiveUS20050228782A1Digital data processing detailsDigital data authenticationWeb siteUser verification
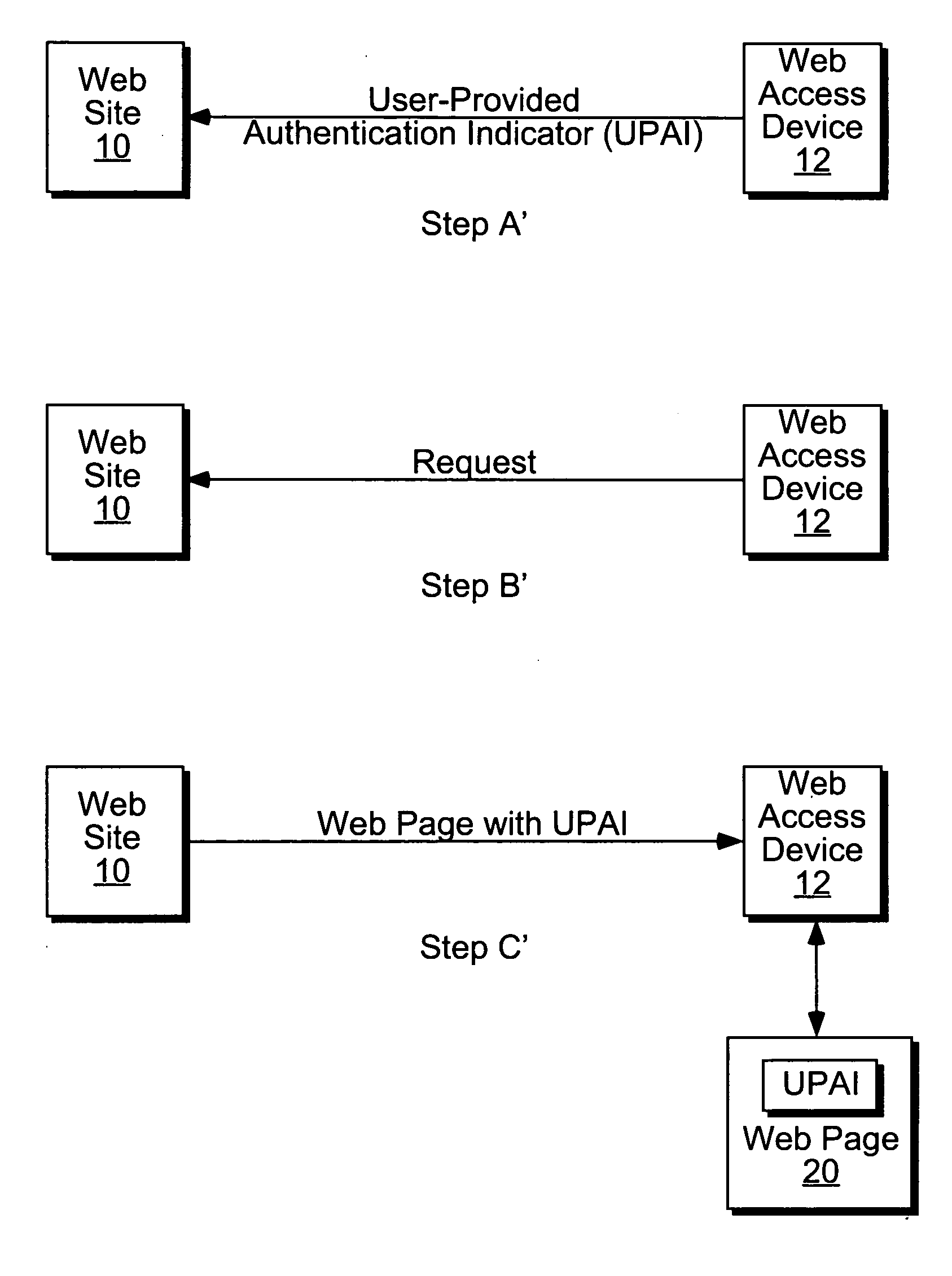
Techniques for authenticating a web site that protect a user from a forged / spoofed web site. A web site according to the present techniques obtains from the user an indicator to be used in authenticating the web site to the user. In response to a request to access the web site, the web site generates a web page that includes the indicator. Recognition of the indicator provides the user with assurance of the authenticity of the web page before entering any personal information, e.g. login name, password, etc. into a web site.
Owner:ASTAV INC
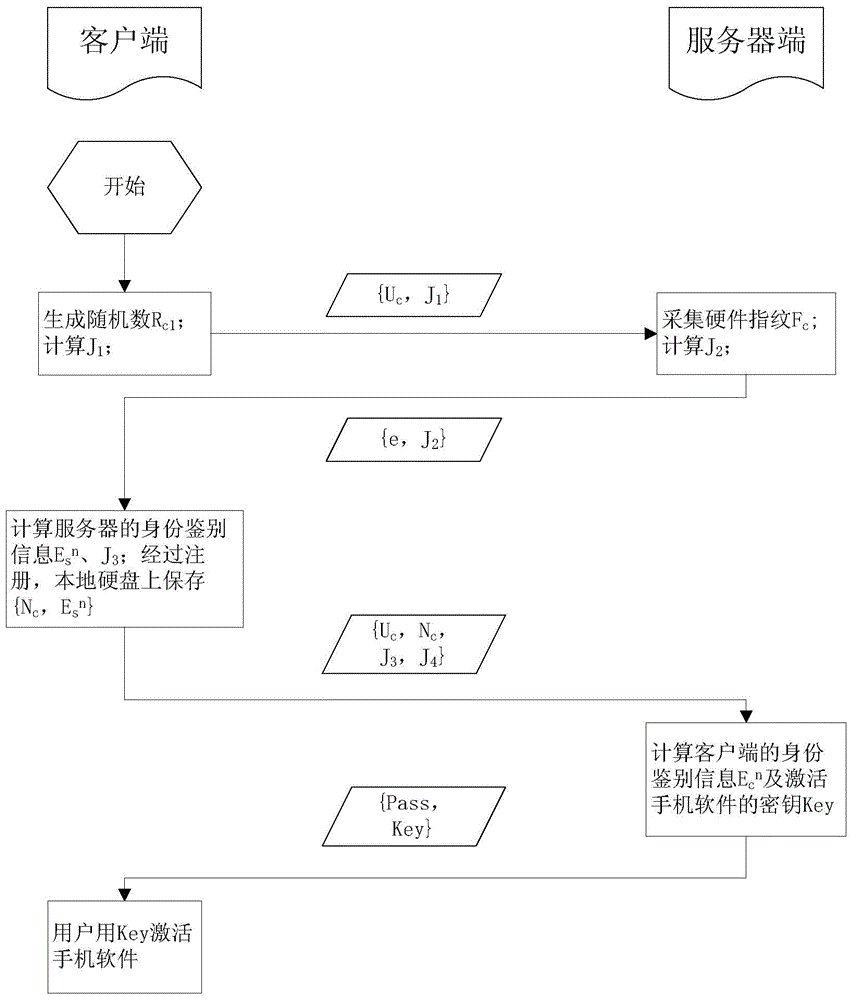
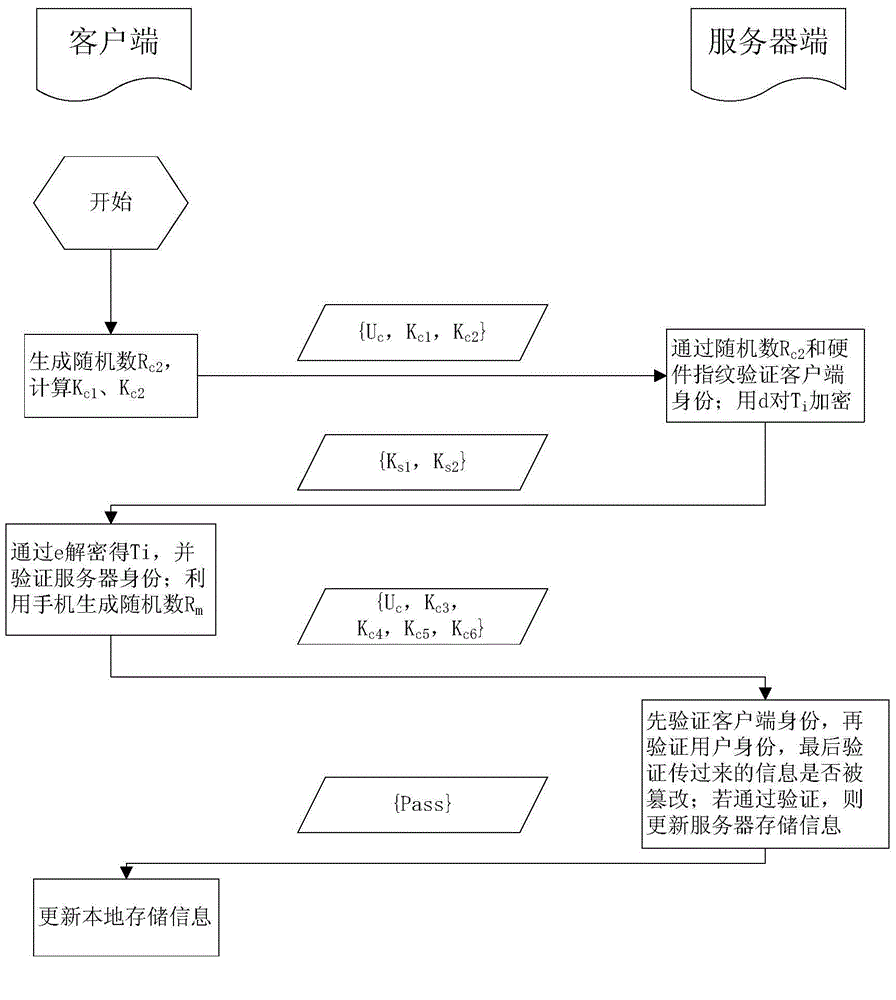
Multi-factor identity authentication method and system
ActiveCN104660605AEasy to useDefense against replay attacksUser identity/authority verificationValidation methodsClient-side
The invention discloses a multi-factor identity authentication method and system. The multi-factor identity authentication method comprises a registration phase and an authentication phase, wherein in the registration phase, a current user is set as C, and registration is performed through a user login name and a login password; the authentication phase comprises bidirectional authentication and login association of a client and a server side: the server side verifies client information in combination of a random number and hardware fingerprint, the client verifies the server side through a public key returned by a server during registration, and the server side performs login association of current login and next login. The non-hardware multi-factor identity authentication method can meet the requirements for identity authentication and information safety, integrity and non-repudiation during login of the identity authentication system; hardware equipment is not required, and the method is convenient to implement.
Owner:BEIJING ANPRO INFORMATION TECH
User and device authentication for media services
A user obtains access to particular services levels associated with media content. A user and devices associated with the user may be authenticated to access content at a particular service level such as a particular quality level, content level, resolution, limited viewing, unlimited simultaneous viewing, etc. When the user is authenticated at a device, content at an appropriate service level is selected and provided to the device. Authenticating the user at a device such as a set top box may involve receiving a manually entered login and password, a passcode transmitted from a mobile device, face detection, a mobile device authorization code sent using infrared or radio frequency transmission, or other mechanisms identifying that the user or the mobile device is in the vicinity or is periodically in the vicinity of the set top box.
Owner:TIVO CORP
Safety control method and safety control system for information in production procedures
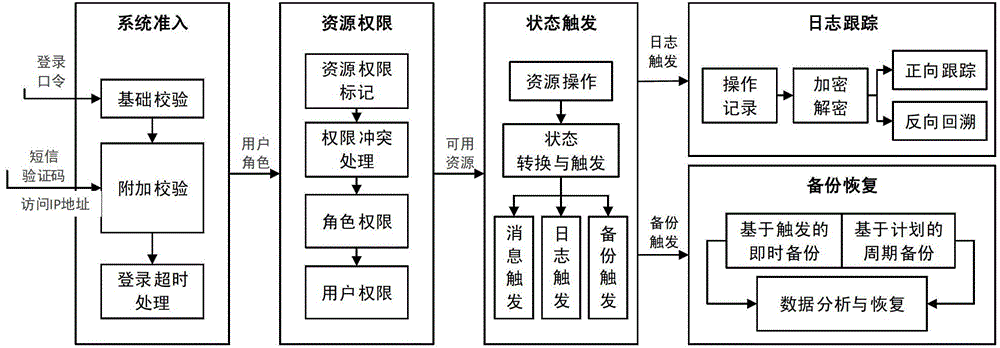
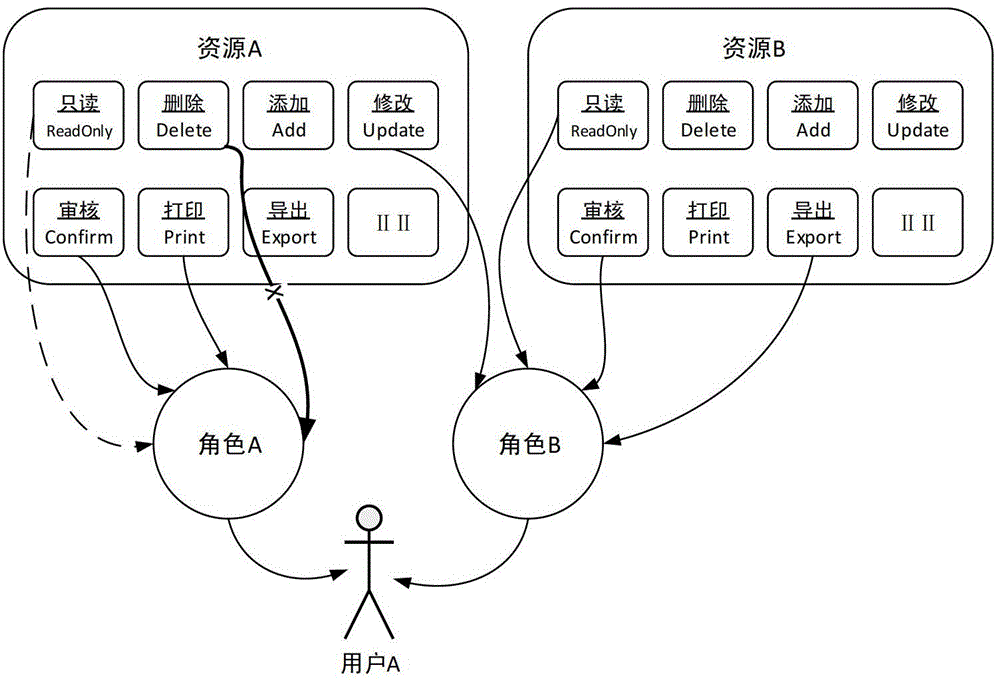
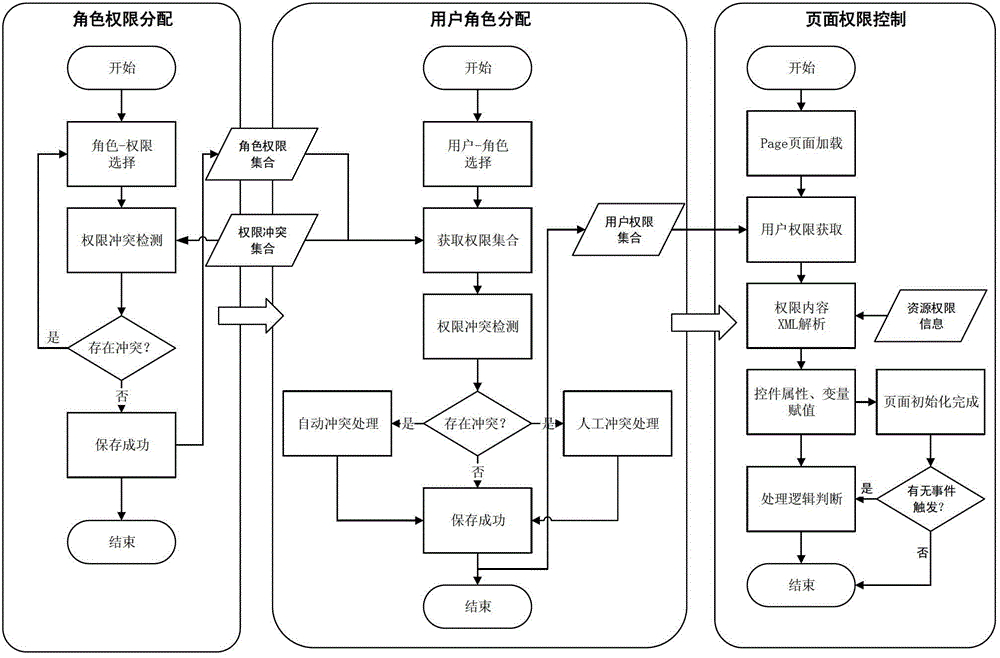
ActiveCN104376237AImprove completenessImplementation-definedDigital data authenticationSafety controlStructure of Management Information
The invention relates to a safety control method for sensitive key information in production procedures. The safety control method includes steps of fundamentally checking personnel login names and passwords and implementing additional checking by the aid of access addresses and check codes of short messages; acquiring resource authority sets of login users according to configuration information of the users, roles and authority, parsing resource authority storage structures and controlling user operation authority; triggering messages, log and backups according to configuration information of process states in user resource operation procedures. The safety control method has the advantages that the method runs through all procedures of operation links such as inputting, storing, publishing, querying, maintaining and exception handling for the sensitive key information, accordingly, safety incidents can be prevented, important operation can be tracked, information data can be recovered, the method is high in configuration and flexibility, and comprehensive and reliable safety guarantee can be provided for information management and application.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
System and method for providing virtual online engineering of a production environment
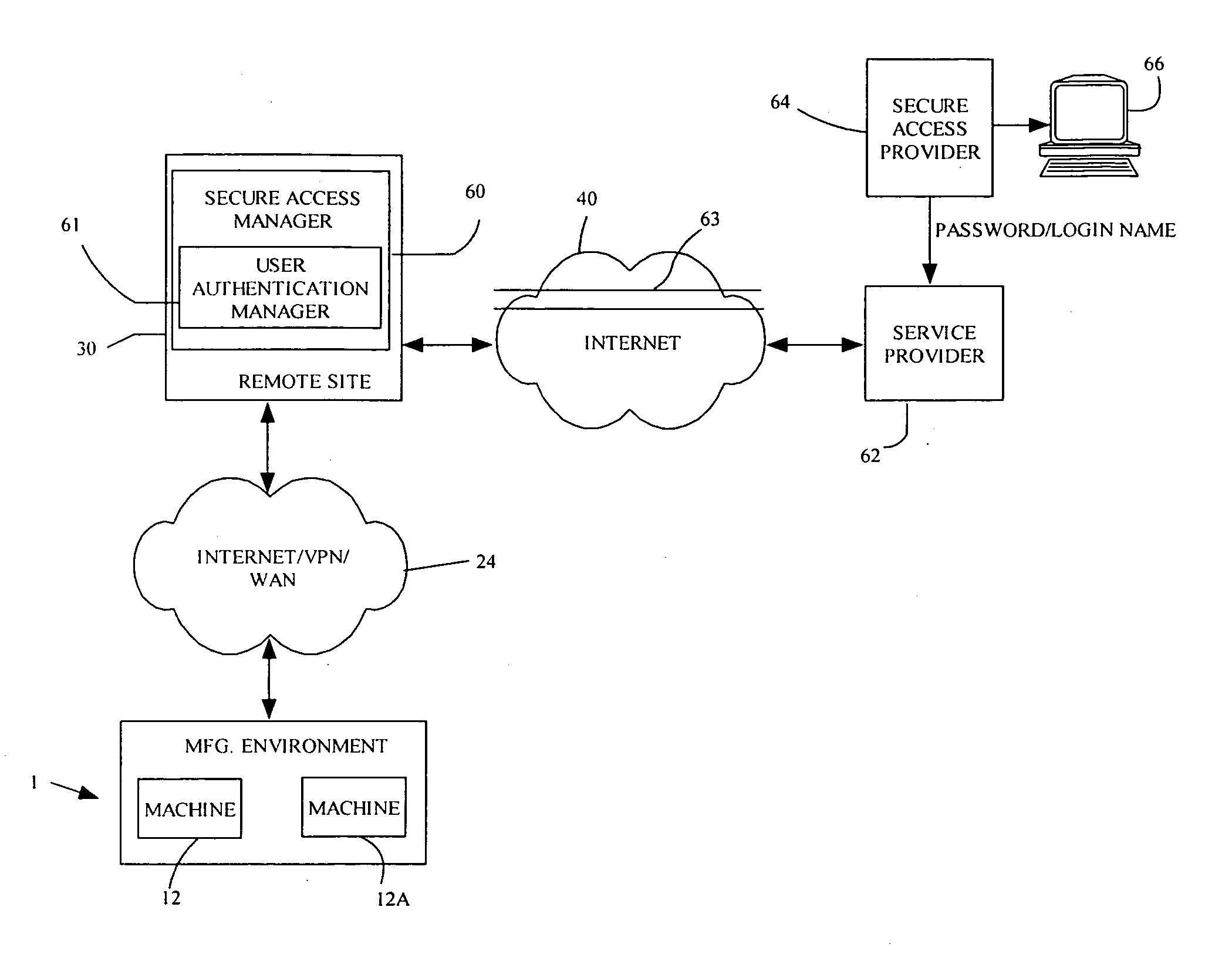
InactiveUS20060089977A1Programme controlMultiple digital computer combinationsData streamService provision
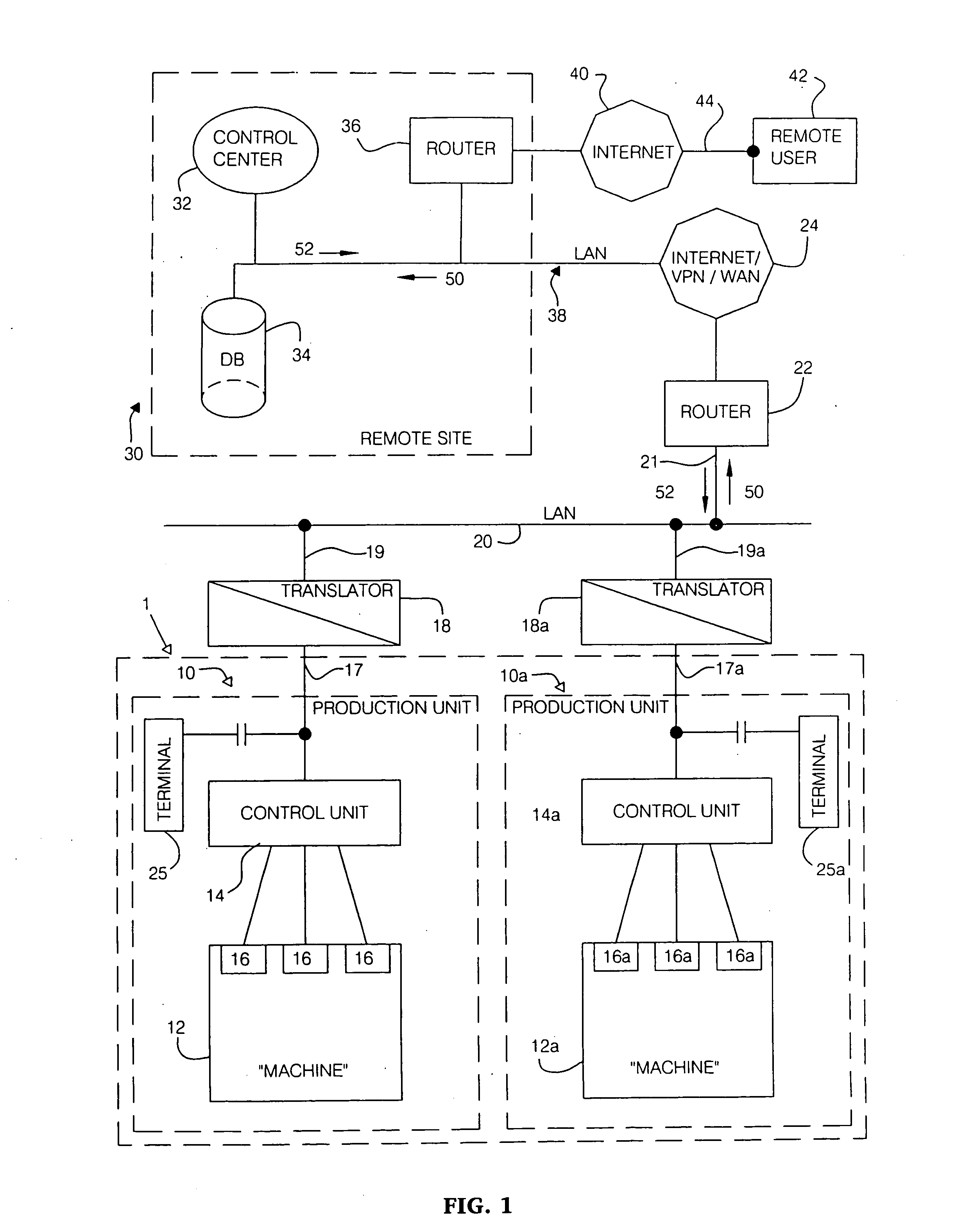
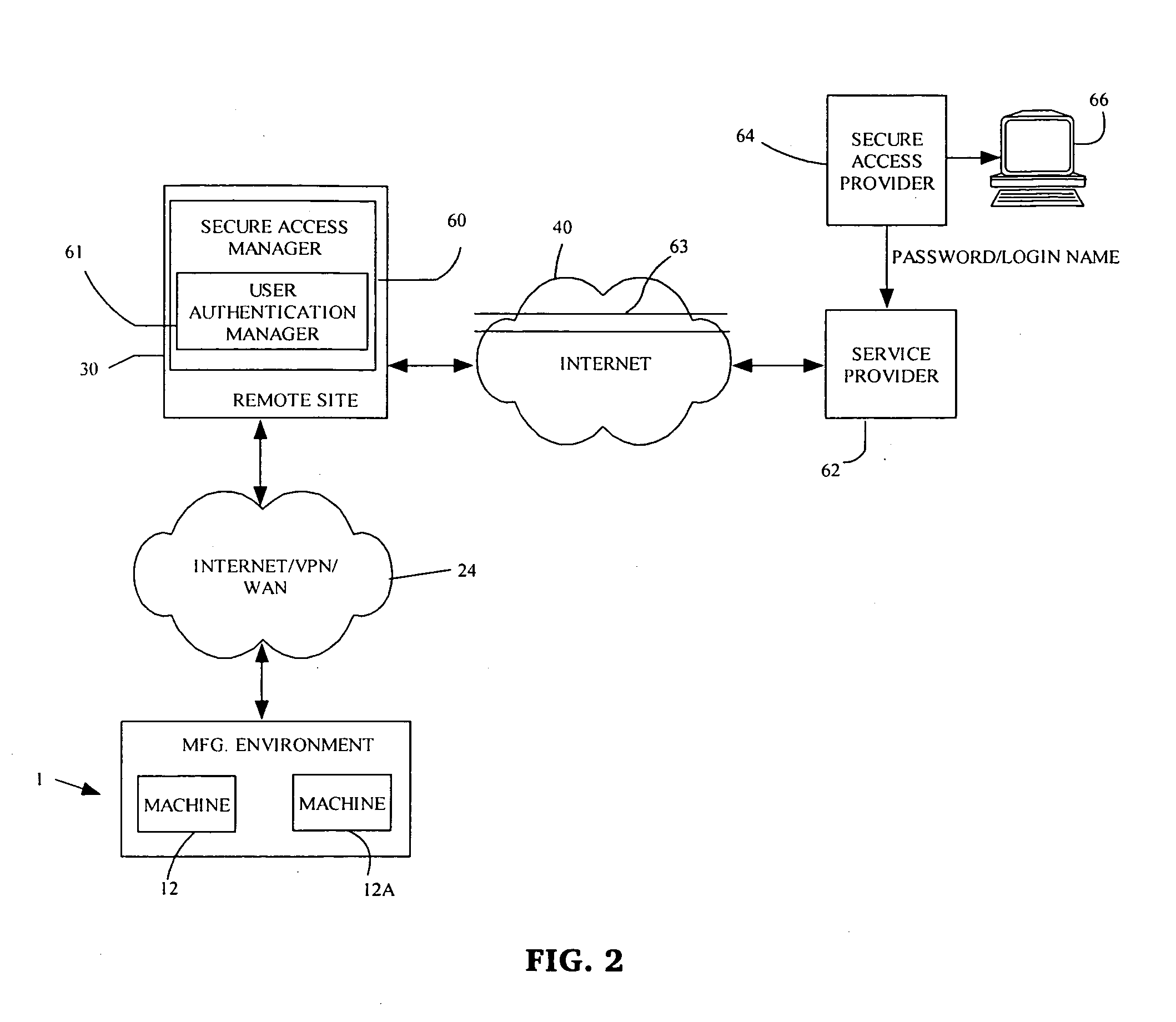
A system and method of provide real-time monitoring and control of a production environment. Manufacturing equipment having proprietary or non-standard digital interfaces provide a plurality of data streams having incompatible communication protocols that are converted to a common communication protocol by a translator and aggregated on a local area network. The resulting aggregated data stream is transmitted across an open network such as the internet or via a wide area network to a remote network. Virtual remote engineering of the production environment is possible from the remote network through monitoring, analysis and control of the production environment. A service provider may be given secure access to the remote network over the Internet by providing the service provider with a password and / or a login name.
Owner:CRAMER SPENCER +4
Payment method and system based on network
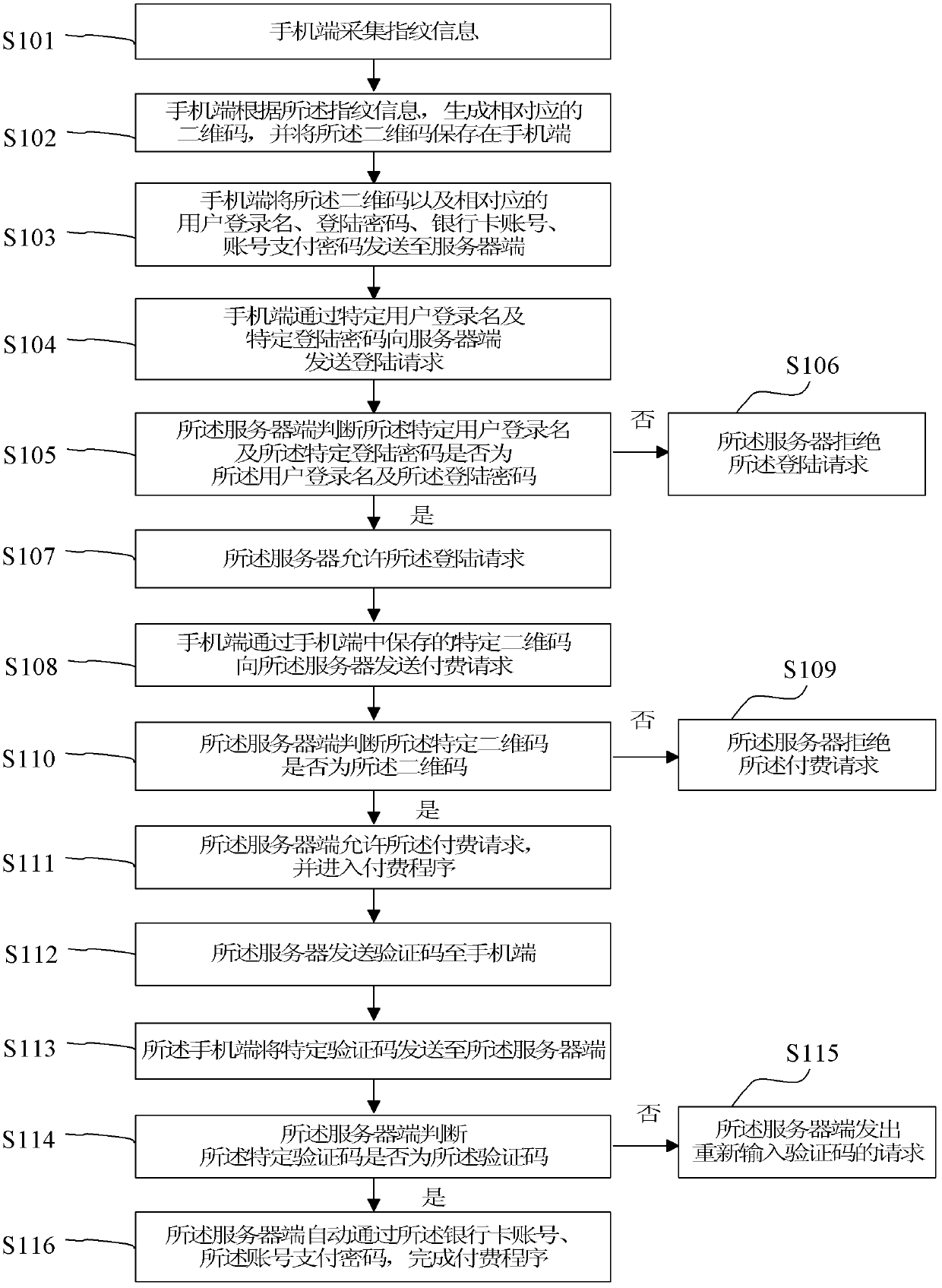
The invention provides payment method and system based on a network. The payment method based on the network comprises the steps that S1, human body biological characteristic information is collected; S2, a corresponding two-dimensional code is generated according to the human body biological characteristic information; S3, the two-dimensional code, corresponding user login name, login password, bank card account number and account number payment password are sent to a server through the network; S4, with the user login name and the login password, accessing the server through the network is carried out; S5, with the two-dimensional code, coming into a payment application through the network is carried out; and S6, the server automatically completes the payment application through the bank card account number and the account number payment password. According to the invention, provided payment method and system can simplify an online payment process, and have the advantages of flexible and convenient use and great reliability and confidentiality.
Owner:SHANGHAI WINGTECH ELECTRONICS TECH
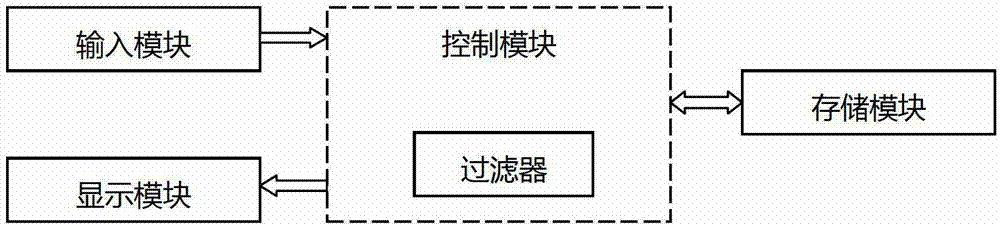
User multi-code management system and method
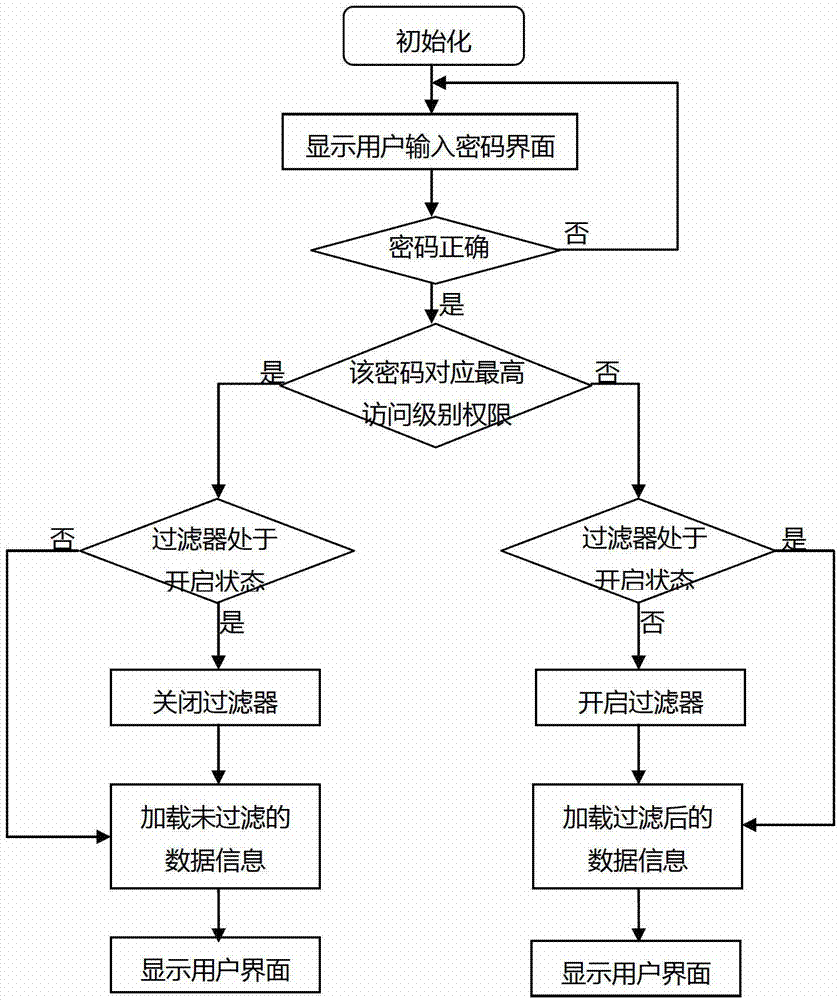
InactiveCN103049685AEnsure safetyDigital data protectionDigital data authenticationUser inputHuman–computer interaction
The invention discloses a user multi-code management system. The user multi-code management system comprises a display module, a control module, a storage module and an input module. The invention also discloses a user multi-code management method. The user multi-code management method comprises the following steps of; (1) displaying a user input code interface; (2) acquiring user input information, and judging whether the input information is matched with a certain code prestored in a database or not; (3) filtering the database according to preset user access authority which corresponds to the code matched with the input information through a filter; and (4) displaying an individual interface which corresponds to the code matched with the input information. For the user multi-code management system disclosed by the invention, the login name and code corresponding mode in the prior art can be saved, only the user input code interface is displayed in the display module, and the user access authority is preset for each code, thereby entering the individual interface which corresponds to the code by only directly inputting the code in the logging process and further ensuring the user information safety.
Owner:TIANJIN SAMSUNG OPTO ELECTRONICS +1
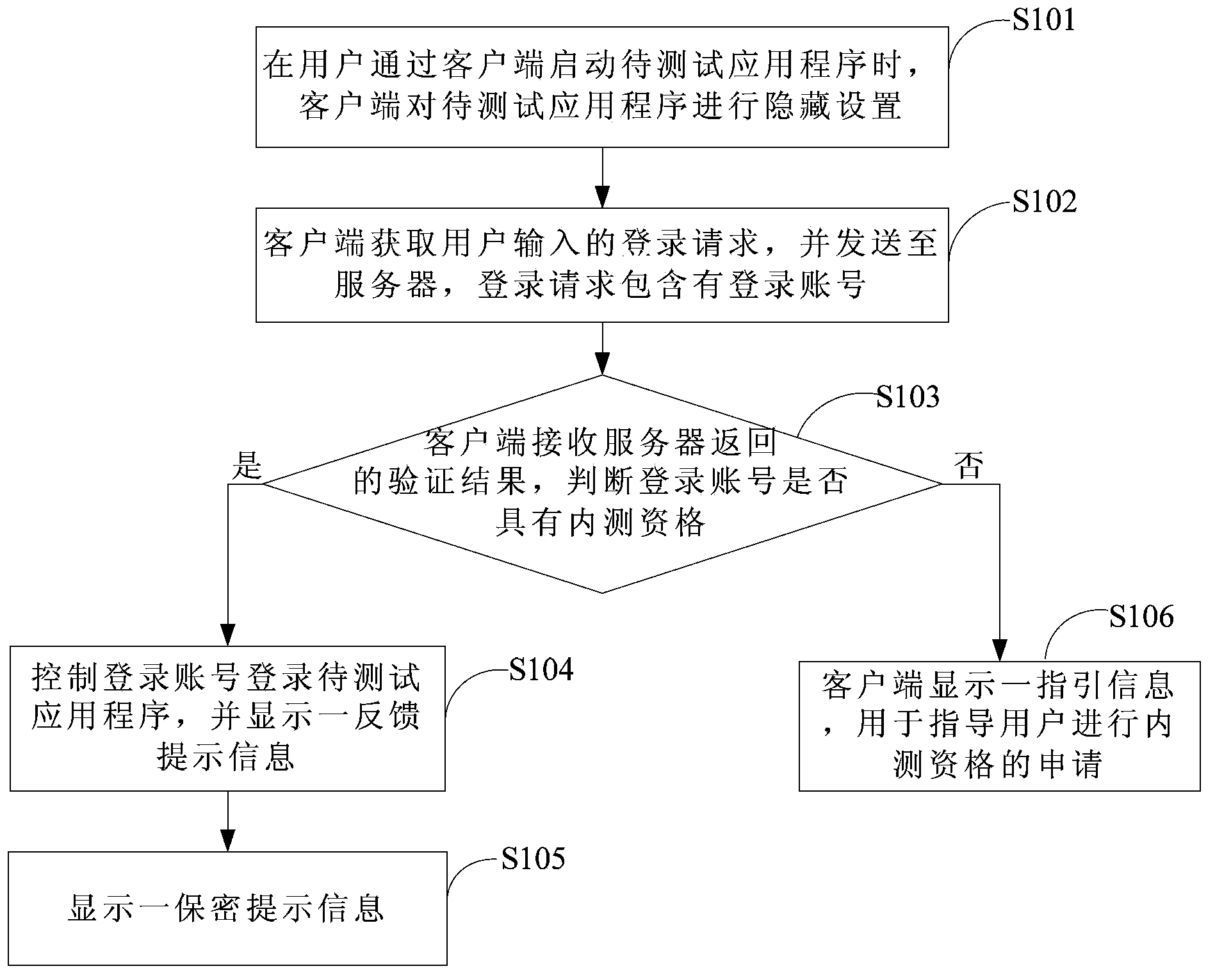
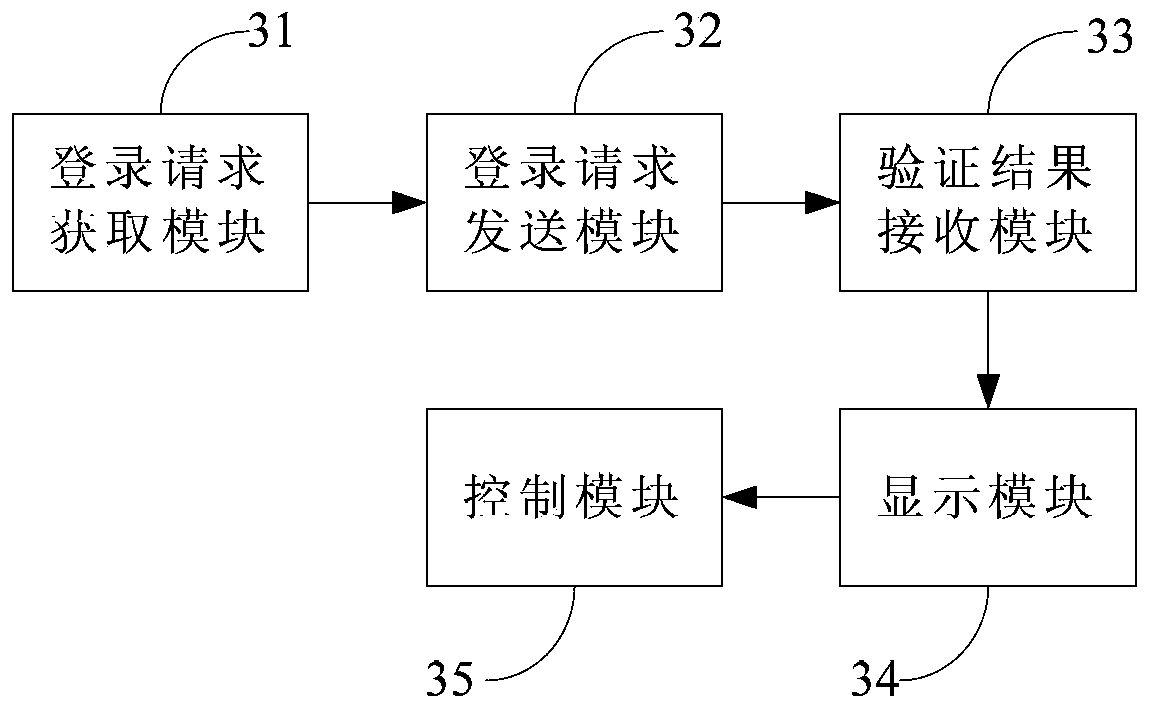
Internal test method of application program, client and server
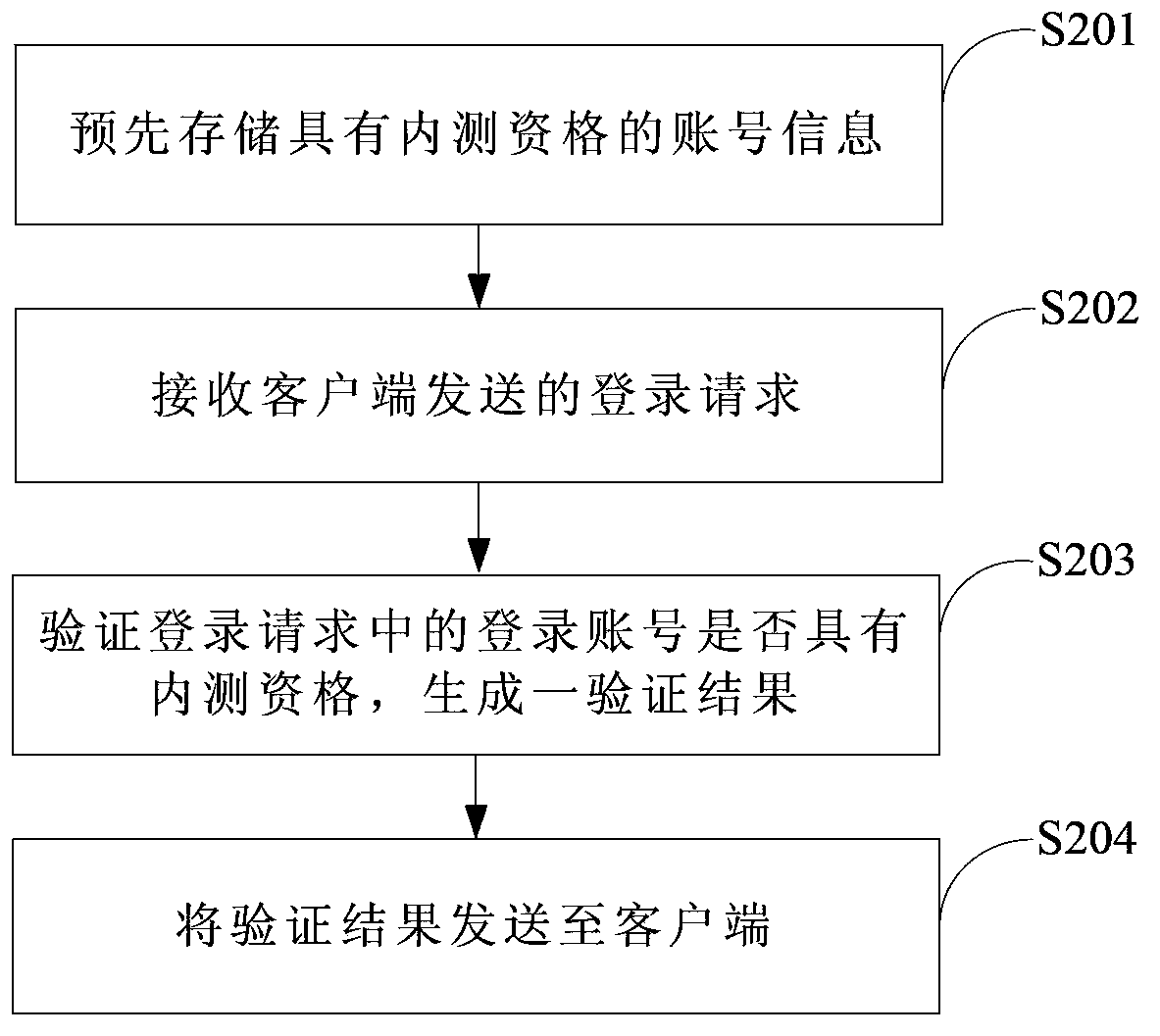
The invention provides an internal test method of an application program, a client and a server. The internal test method of the application program comprises the steps that: the client obtains a login request which is used for starting the application program to be tested; the client sends the obtained login request to the server, wherein the login request includes a login name; the client receives the verifying result fed back by the server; if the verifying result is that the login name is qualified for internal test, the client controls the login name to log in the application program to be tested, and displays a feedback prompt message for promoting the user to feed back experience information of the internal test.
Owner:GUANGZHOU KUGOU TECH
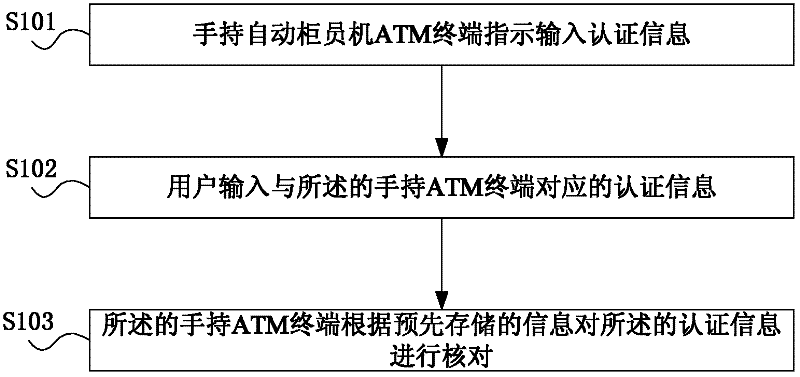
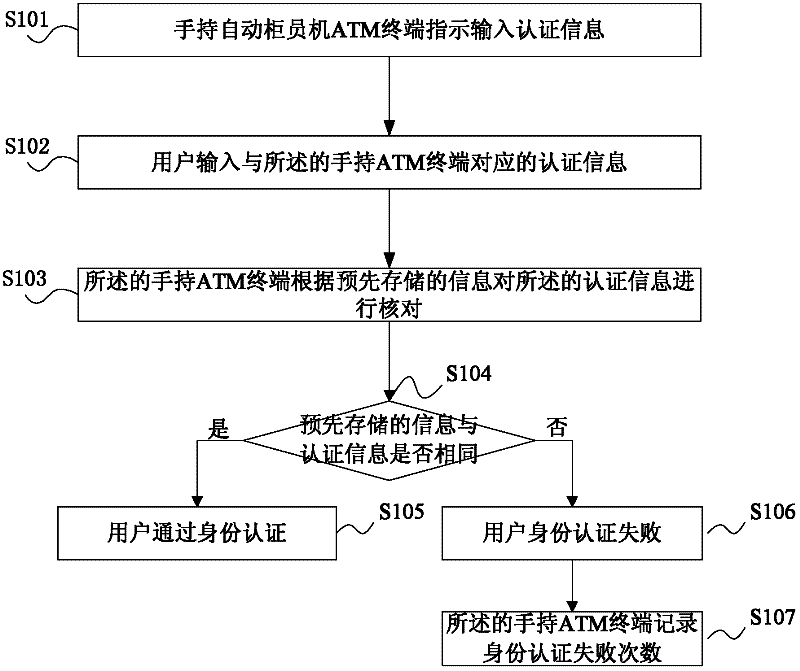
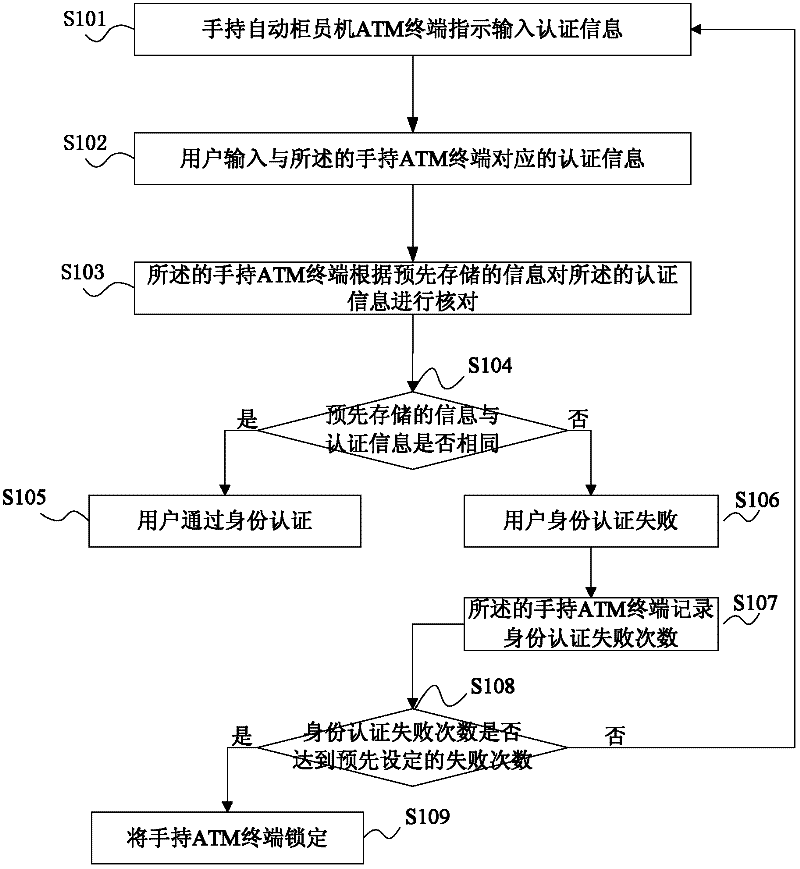
Identity authentication method, handheld ATM (automated teller machine) terminal and system
InactiveCN102411814AImprove experienceAvoid security risksComplete banking machinesUser inputComputer terminal
The embodiment of the invention provides an identity authentication method, a handheld ATM (automated teller machine) terminal and a system. The terminal comprises a keyboard, a display screen, a card reader, an identity authentication module, a service module and a master module, wherein the keyboard is used for collecting instructions input by users, and the instructions comprise authentication information; the display screen is used for displaying the instructions input by the users and service information of the service module, and the identity authentication module is used for performing the identity authentication of the users according to the collected authentication information; and the card reader is used for reading card numbers or account information of the users after the identity of the users is authenticated, and the service module is used for performing service operation according to the instructions of the users, and the card numbers or account information. By checking the authentication information input by the users and the pre-stored information, the security risk problem of e-banking channel service by using a login name and a static login password is solved, and the user experience is improved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Method for generating an asymmetric cryptographic key pair and its application
ActiveUS20110185177A1Avoid decryptionUser identity/authority verificationData processing systemLogin Name
The invention pertains to a method, computer readable medium, and data processing system for generation of an asymmetric cryptographic key pair including reception of an arbitrarily selectable login name, calculation of a first data object key, whereby a random value and the login name are included in the calculation, and calculation of a second data object key from the first data object key, whereby the first and second data object keys form the asymmetric cryptographic key pair.
Owner:COMPUGRP MEDICAL SE
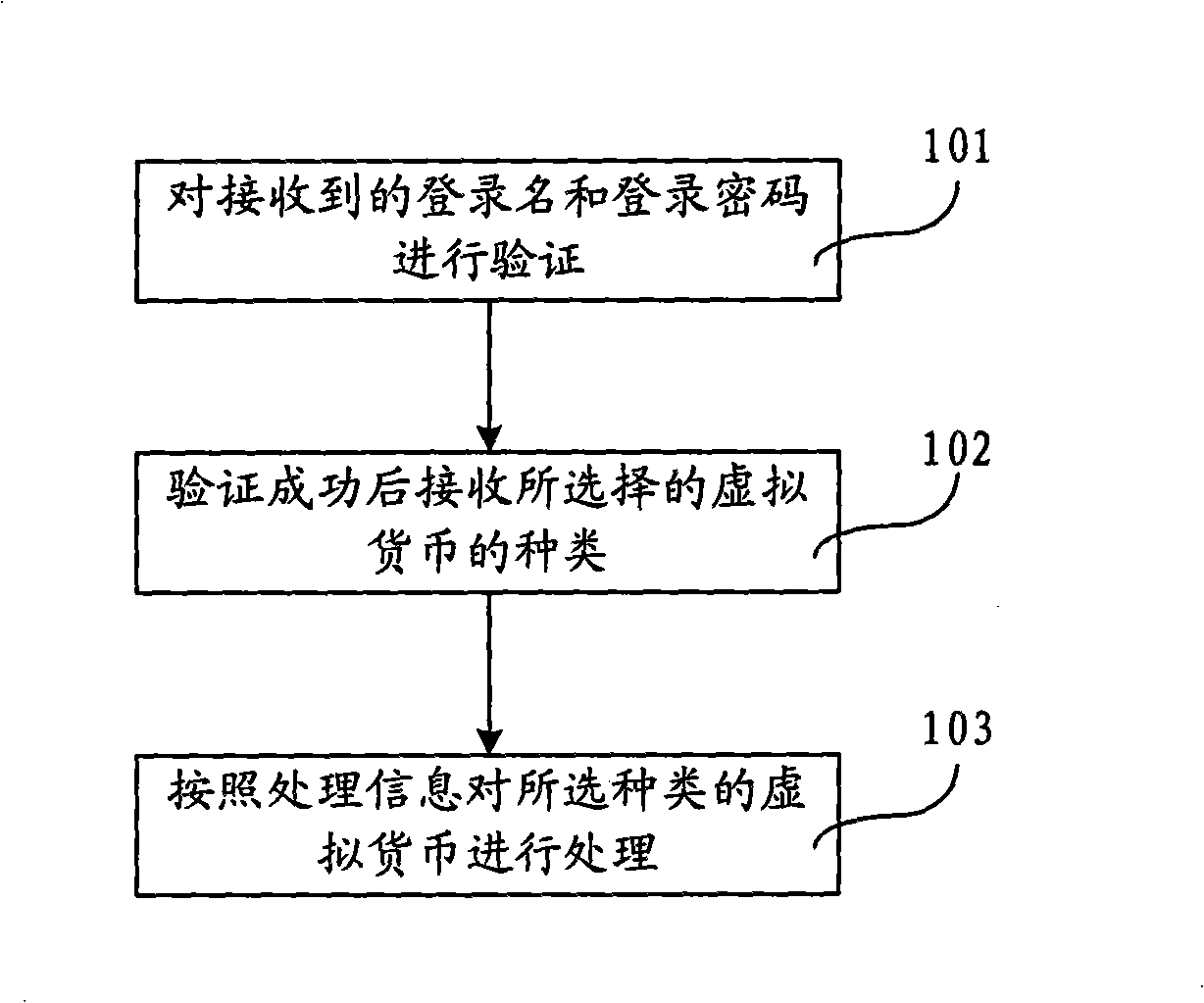
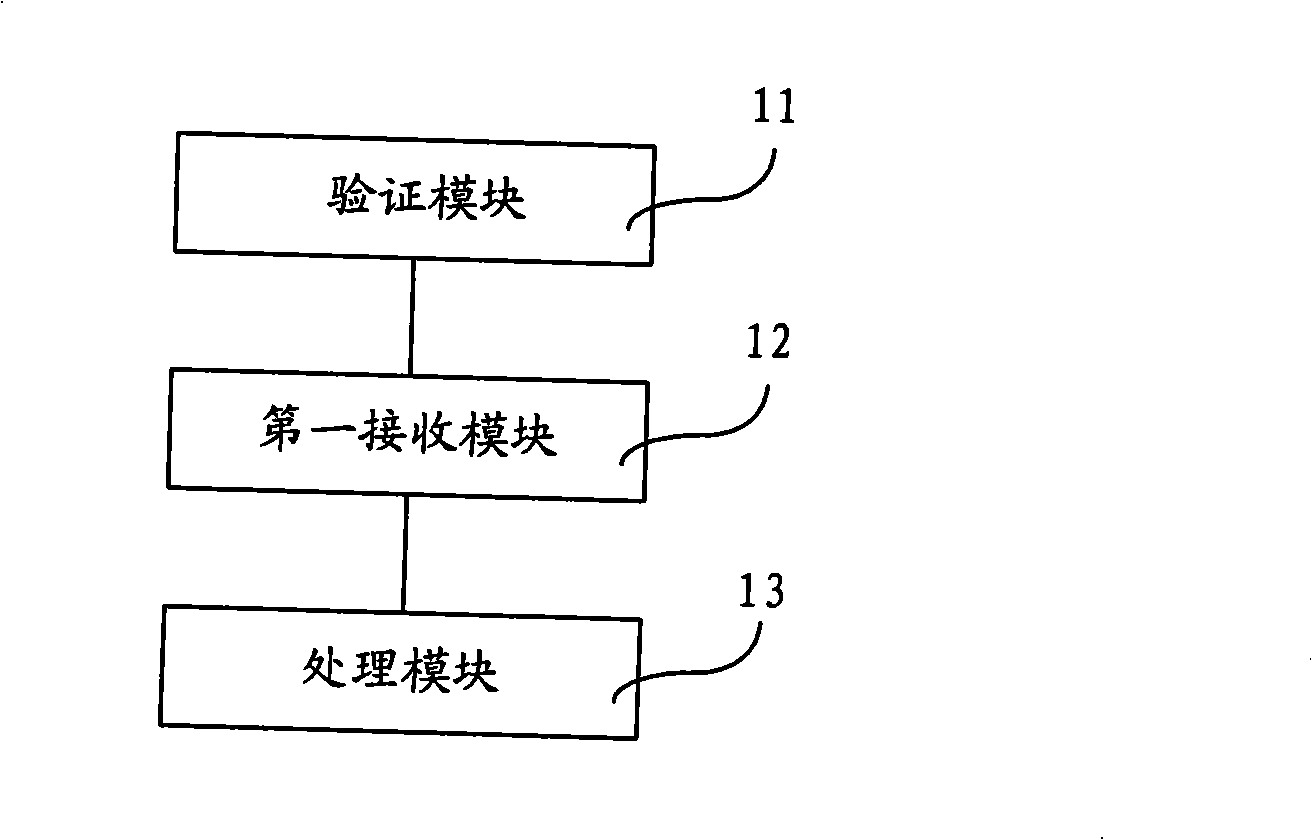
Method and system for processing electric currency information
The invention provides a processing method of electronic currency information, and a system thereof. The processing method of the electronic currency information comprises that: the received login name and login password are first verified; after the successful verification, the types of selected virtual currency are received; the virtual currency of the selected type is processed according to processing information. The processing system of the electronic currency information comprises a verification module which is used for the verification of the received login name and login password, a first receiving module used for receiving the selected type of the virtual currency after the verification passes, a processing module which is used for the processing of the virtual currency of the selected type according to the processing information. The processing method and the processing system of the electronic currency information provided by the embodiment of the invention provide various virtual currency types for the choice of users, thus offering diversified selections to the users, and have complete and powerful design functions.
Owner:中国网通集团宽带业务应用国家工程实验室有限公司
Information sharing method, device and system
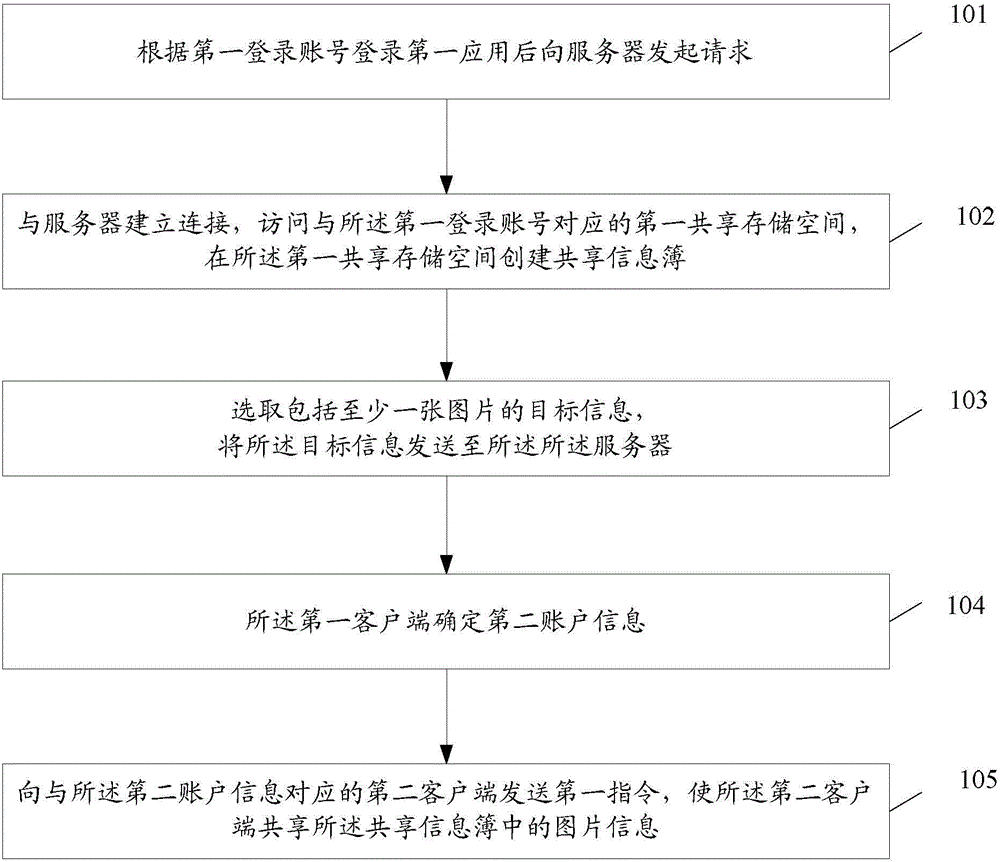
ActiveCN104980334AQuick shareImprove user experienceData switching networksSpecial data processing applicationsObjective informationLogin Name
The invention discloses an information-sharing method, an information-sharing device and an information-sharing system, wherein the method comprises the steps as follows: a first client initiates a request to a server after logging in a first application according to a first login name; establishes a connection with the server after receiving a response of the server to the request, accesses a first sharing storage space corresponding to the first login name, establishes a sharing information book in the first sharing storage space; selects target information, transmits the target information to the server; determines second account information, and transmits a first instruction to a second client corresponding to the second account information so that the second client could share picture information in the sharing information book.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Data access authority identification method and device
ActiveCN106384057AEnsure safetyEasy to manageDigital data protectionSpecial data processing applicationsData accessData management
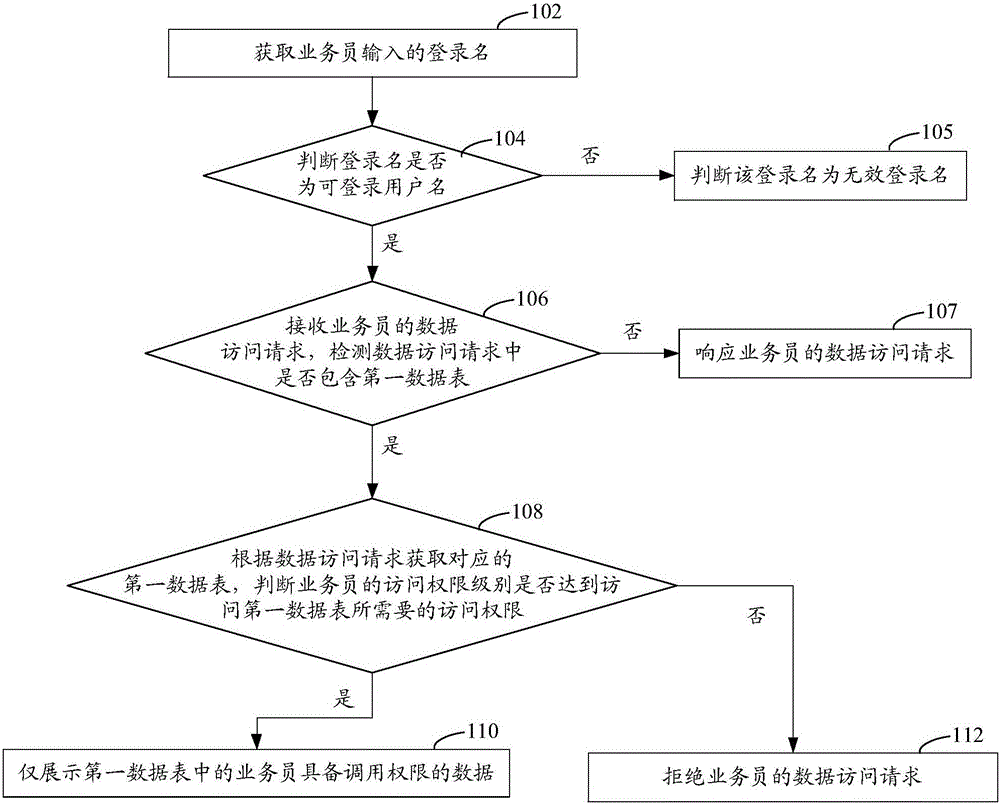
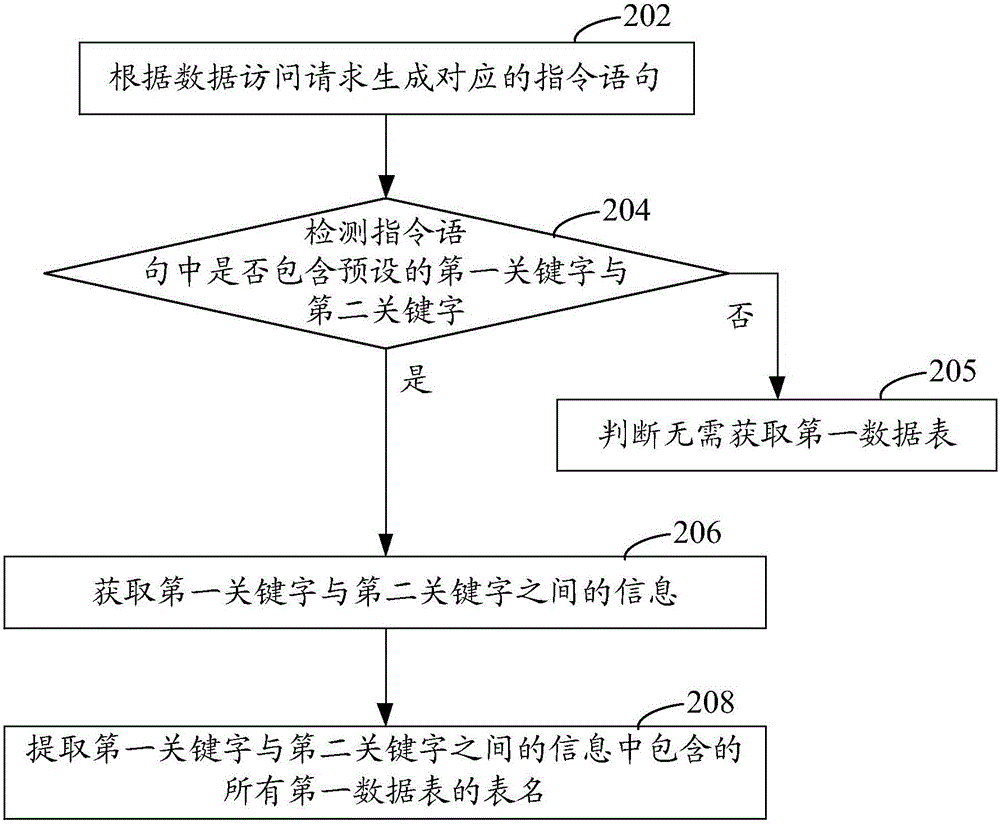
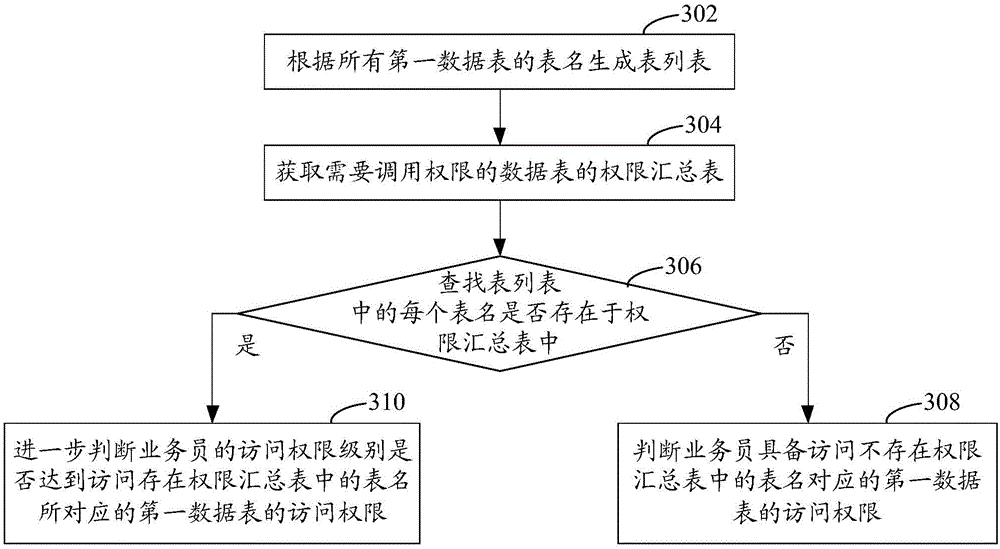
The invention relates to a data access authority identification method comprising the following steps: obtaining a clerk inputted login name, and determining whether the login name is a registered user name or not; if yes, obtaining an access authority level corresponding to the login name; receiving a clerk data access request, and detecting whether the data access request contains a first data sheet or not; if yes, obtaining the first data sheet corresponding to the data access request; determining whether the clerk access authority level has reached the access authority for accessing the first data sheet or not; if yes, only displaying the data, to which the clerk has the access authority, from the first data sheet. The data access authority identification method allows various data items to be stored in the same data sheet, thus saving storage space, reducing resource occupation, and data management is more convenient; in addition, the invention also provides a data access authority identification device.
Owner:PING AN TECH (SHENZHEN) CO LTD
Multi-point login communication method, multi-point login communication device, multi-point login communication system and user terminal
InactiveCN103825865AMulti-sign-on implementationSolve the problem that is not convenient for users to operateData switching networksTelecommunicationsCommunications system
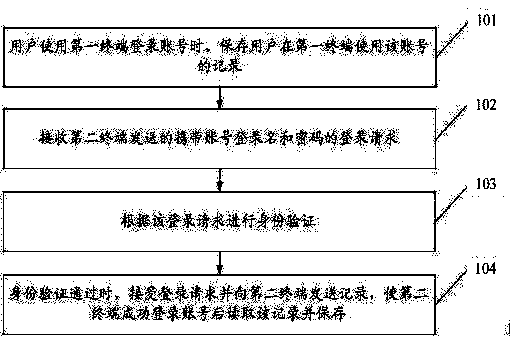
The invention discloses a multi-point login communication method, a multi-point login communication device, a multi-point login communication system and a user terminal, and relates to the field of communication. The invention aims to solve the problem that IM records cannot be shared on different terminals to make operation by users inconvenient in the prior art. The technical scheme disclosed by the invention comprises the following steps: when a user uses a first terminal to log in an account, a record in which the user uses the account on the first terminal is stored; a login request sent by a second terminal and carrying a login name and a password of the account is received; identity authentication is carried out according to the login request; and after identity authentication, the login request is received, and the record is sent to the second terminal to enable the second terminal to read and store the record after successfully logging in the account. The scheme can be applied to an instant messaging system and the like.
Owner:ZHENJIANG GOLDNT SOFTWARE CORP
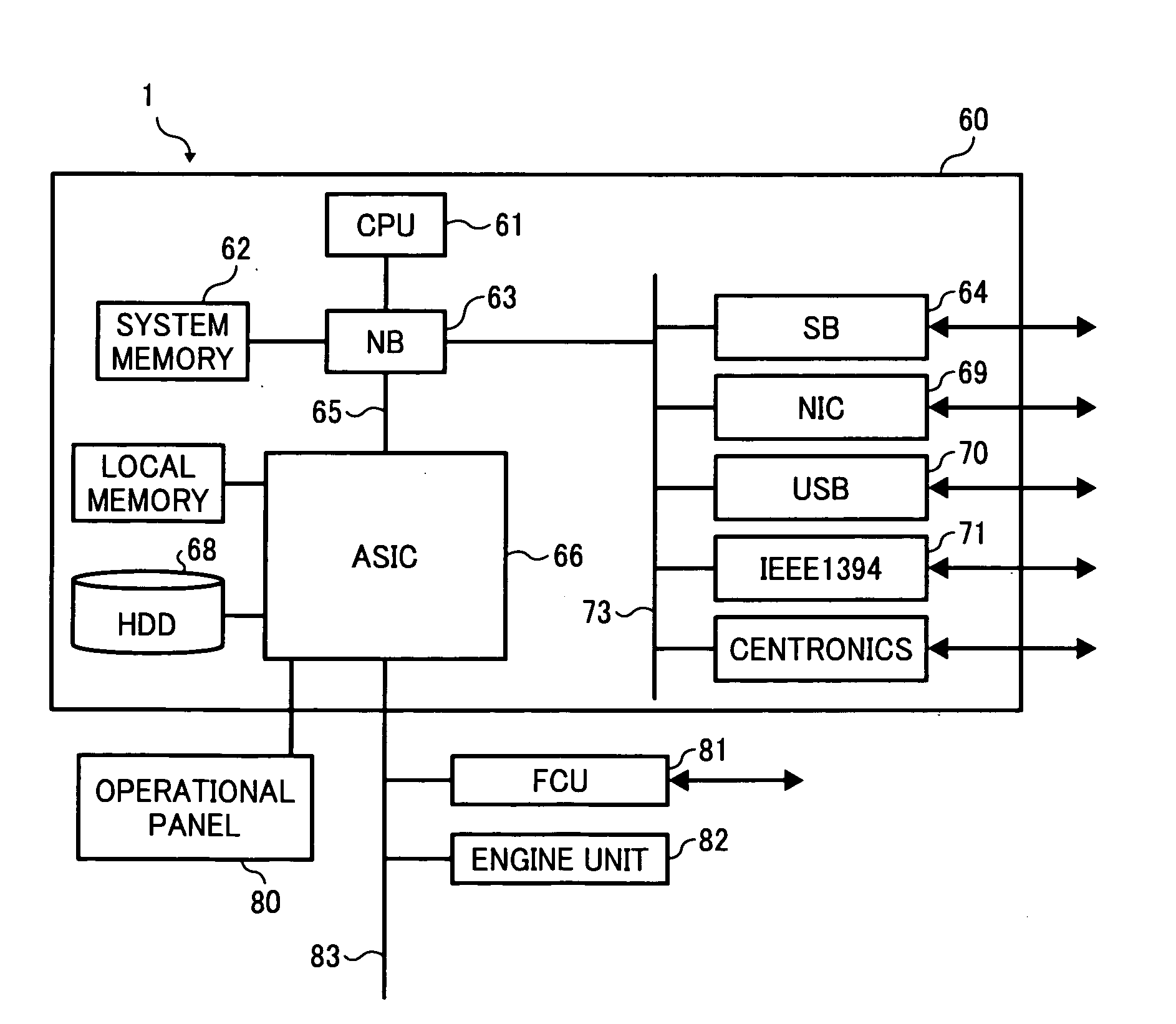
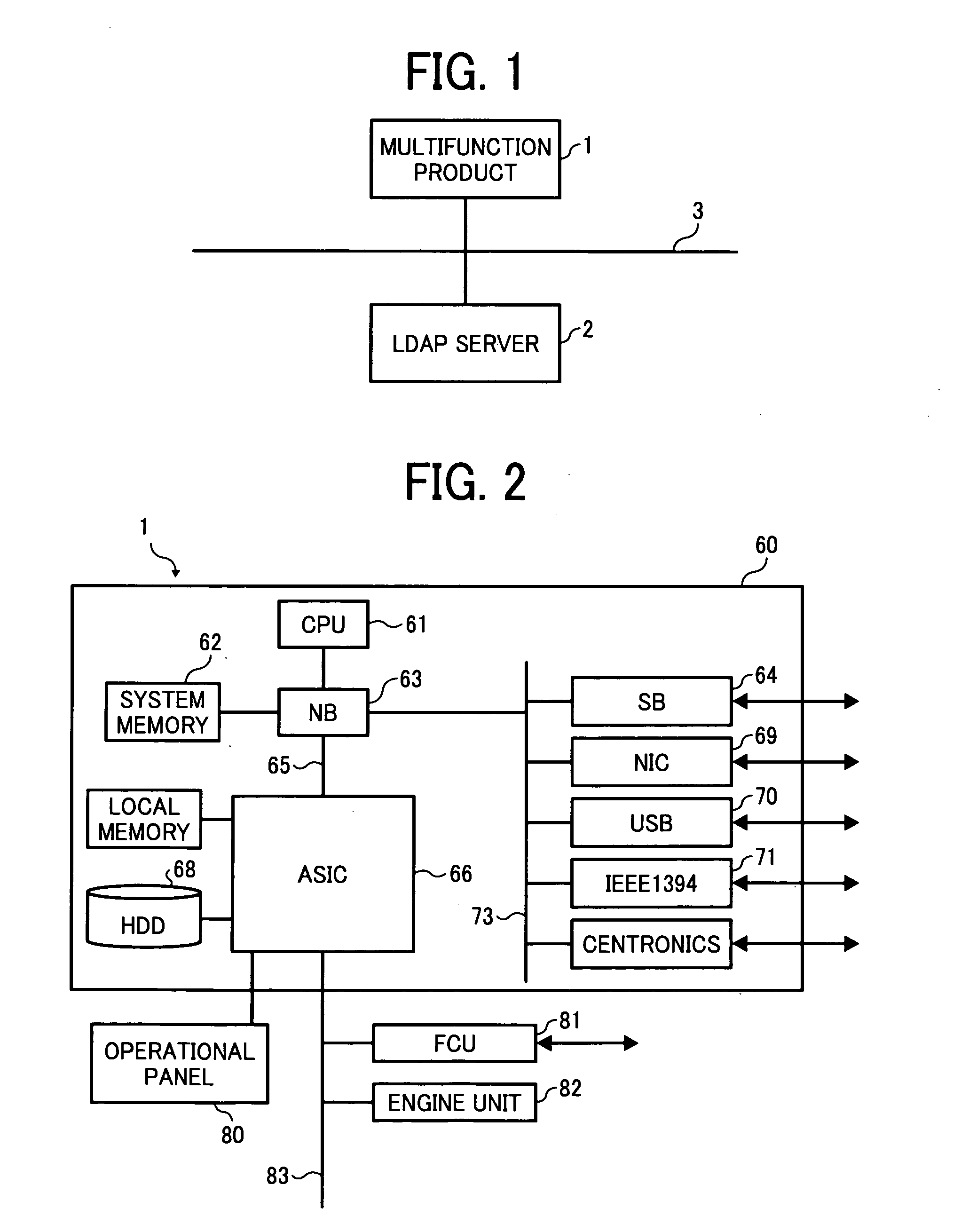
Information processing apparatus and information processing method
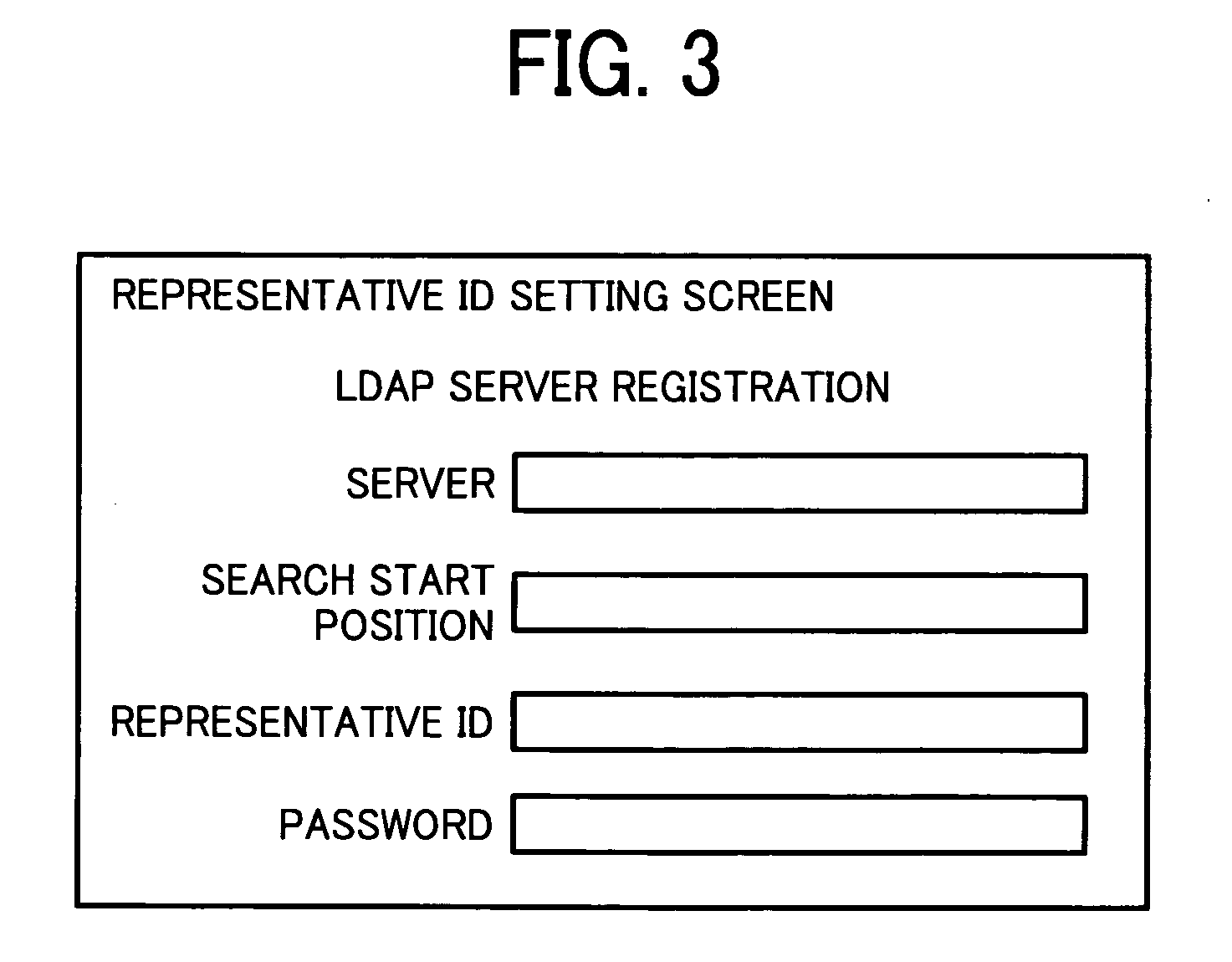
InactiveUS20080307510A1Solve problemsDigital data processing detailsMultiple digital computer combinationsInformation processingLogin Name
A multifunction product, when receiving input of login name and password, requests an LDAP server to perform authentication by using a pre-set representative ID. If the authentication is successful, the multifunction product requests the LDAP server to search for user information (DN) with the use of the login name, and after acquiring the DN, requests the LDAP server to perform authentication with the use of the DN. If the authentication processing is successful, the multifunction product permits a search for user information stored in the LDAP server.
Owner:RICOH KK
Secure single sign-on for a group of wrapped applications on a computing device and runtime credential sharing
ActiveUS9473485B2Key distribution for secure communicationDigital data protectionArray data structureUser input
A mobile device user is able to execute an app in a federation of wrapped apps without having to login to that app provided that the user has already logged into another app in that federation. The federation of apps on the device uses multi-app authentication to enable the user to start subsequent apps after explicitly entering login credentials for another app in that federation. This feature is loosely referred to as single sign-on for apps in the federation. The multi-app authentication is implemented by giving the second app a chance to prove two facts. One that it knows where in the operating system keychain a login ticket is stored and two, what the hash value of a random byte array is. By showing these facts, the logged-into app can safely provide login credentials to subsequent app without the user having to enter a login name or password.
Owner:BLUE CEDAR NETWORKS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com