Safety login method and system
A technology for secure login and automatic login, applied in transmission systems, electrical components, etc., can solve problems such as forgetting, insecure user names and passwords, and achieve the effect of improving the level of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0053] Figure 5 A flow chart of writing information for a user in a specific embodiment of the present invention. Figure 6 It is a flow chart of user security login in a specific embodiment of the present invention.
[0054] Such as Figure 5 As shown, in step S501, the user first needs to enter information and send a request for writing information.
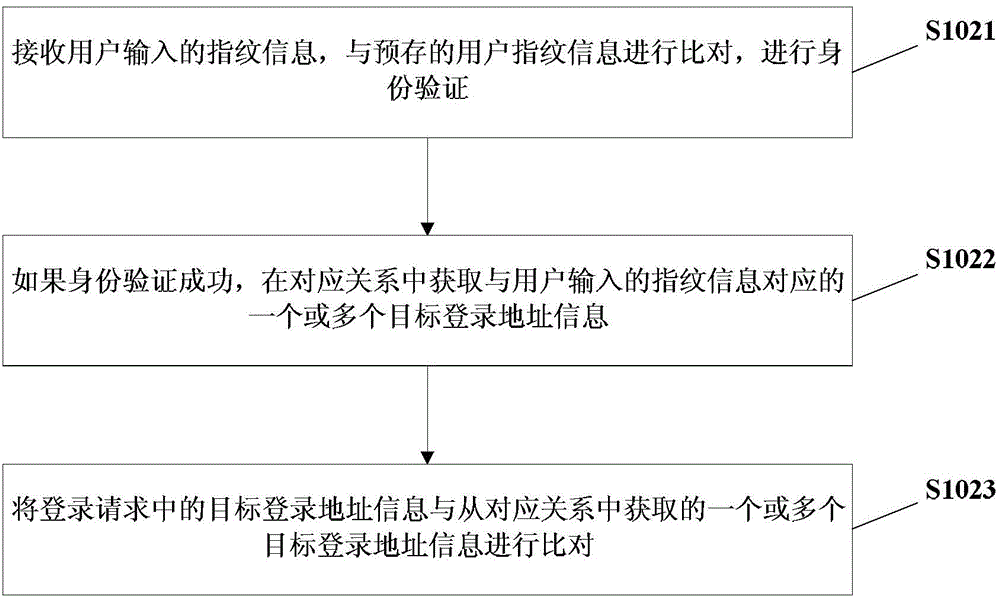
[0055] Step S502, collect the user's fingerprint, compare it with the pre-stored fingerprint information, and verify the user's identity; if the verification is successful, execute step S503; if the verification fails, end the operation.
[0056] Step S503, the user inputs target login address information, user name and password;
[0057] Among them, in this step, there is a corresponding relationship between the user fingerprint, target login address information, user name, and password: the user identity can be confirmed according to the user fingerprint, and the user identity can correspondingly input one or more target ...
Embodiment 2
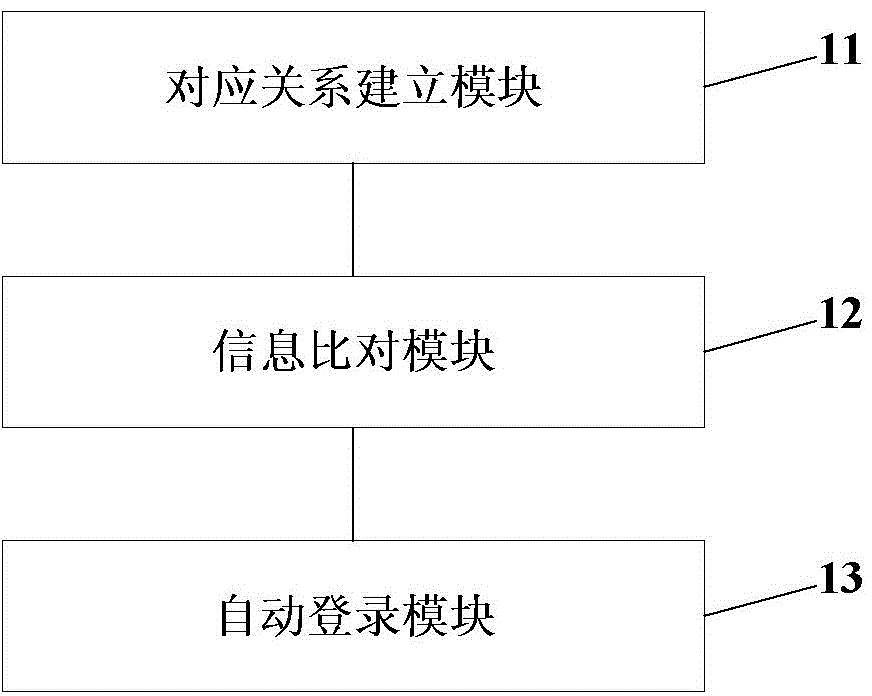
[0066] According to the secure login method and system of the present invention, it can be implemented in combination with a set of hardware devices in practical applications, specifically as Figure 7 and Figure 8 shown.
[0067] Figure 7 Shown is a schematic structural diagram of a security login device according to a specific embodiment of the present invention. The security device can realize the functions of the aforementioned security login method and system, such as Figure 7 As shown, the security login device 3 includes: a fingerprint extractor 31, a digital signal processor (Digital Signal Processing, DSP) 32, a first memory 33, a second memory 34, a read-write switch 35, a login controller 36, a crystal oscillator 37, Data interface 38, first data address bus 39; Wherein,
[0068] in achieving the aforementioned Figure 5 In the step S501 of recording information, the login controller 36 in the security login device 3 can be used when a request for writing inf...
Embodiment 3
[0099] combined with the aforementioned Figure 7 and Figure 8 Said embodiment, the present invention also proposes a more specific security login device; Figure 7 As shown, the security login device 3 includes: a fingerprint extractor 31, a digital signal processor (Digital Signal Processing, DSP) 32, a first memory 33, a second memory 34, a read-write switch 35, a login controller 36, a crystal oscillator 37, Data interface 38, first data address bus 39; Wherein,
[0100] The fingerprint extractor 31 can be a solid capacitive sensor, such as Fujitsu MBF200, with a resolution of 508DPI, a single image size (bytes) of 76K, and an antistatic index of ±10kV. The fingerprint sensor can also be a semiconductor sensor, using a sliding SWIPE chip, and the resolution needs to be above 500DPI. The fingerprint sensor is connected with data pins D0-D7, address pins A0-A2, read signal RD, and write signal WD of the data signal processor DSP-TMS320VC35 for collecting fingerprint data...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com