User multi-code management system and method
A management system and multi-password technology, applied in the field of encryption and decryption, can solve the problems that the login name is not hidden and cannot be seen at will, so as to achieve the effect of ensuring the security of user information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
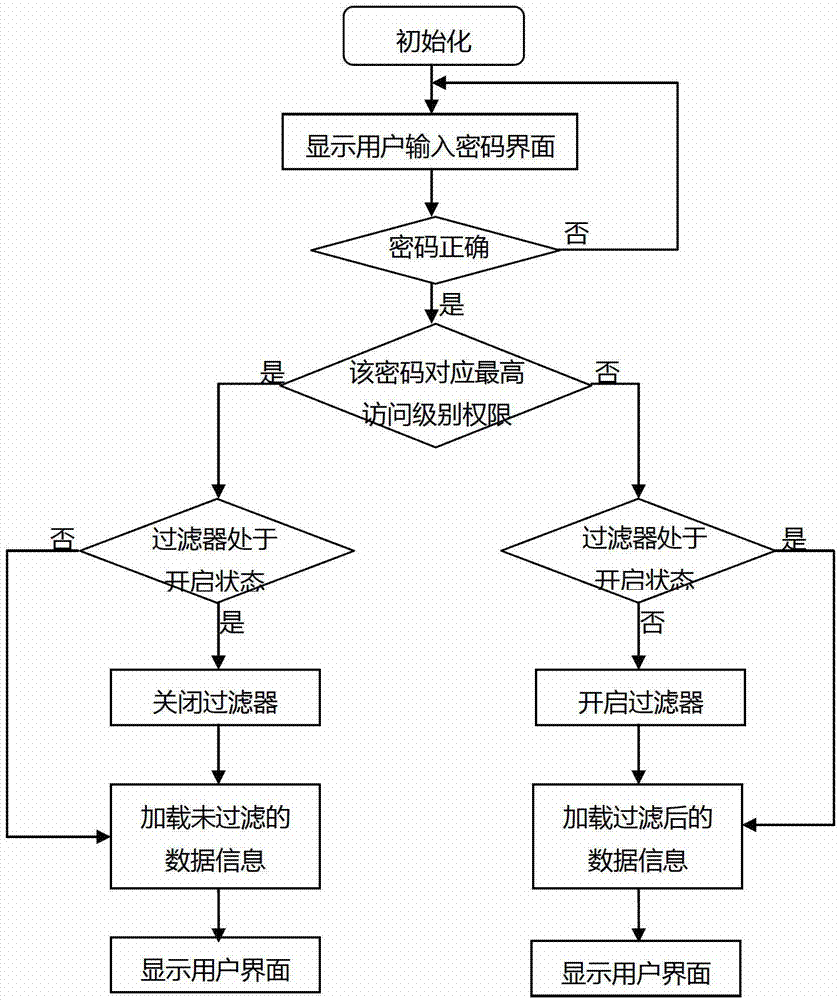
[0027] In order to enable those skilled in the art to better understand the technical solutions of the present invention, the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
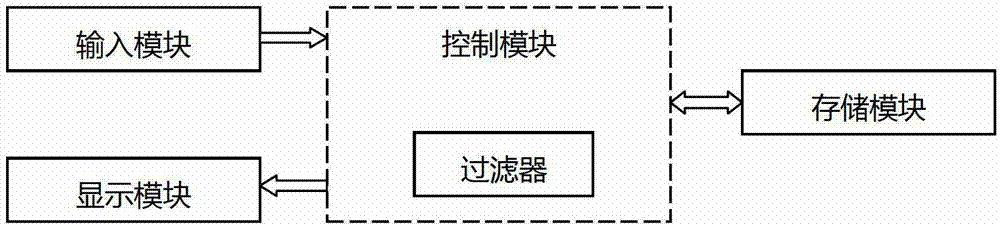
[0028] like figure 1 As shown, the present invention also relates to a user multi-password management system, including a display module, a control module, an input module and a storage module.
[0029] The display module is connected with the control module, and is used for displaying the user input password interface, and displaying the corresponding user interface according to the instruction sent by the control module. Since the user multi-password management system of the present invention can be used in user login systems such as computers, networks, and mobile terminals, the display module can be a computer or mobile terminal display, a touch screen or a liquid crystal display, or It's an LED display.
[0030] The control...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com