Patents
Literature
46 results about "Heuristic analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
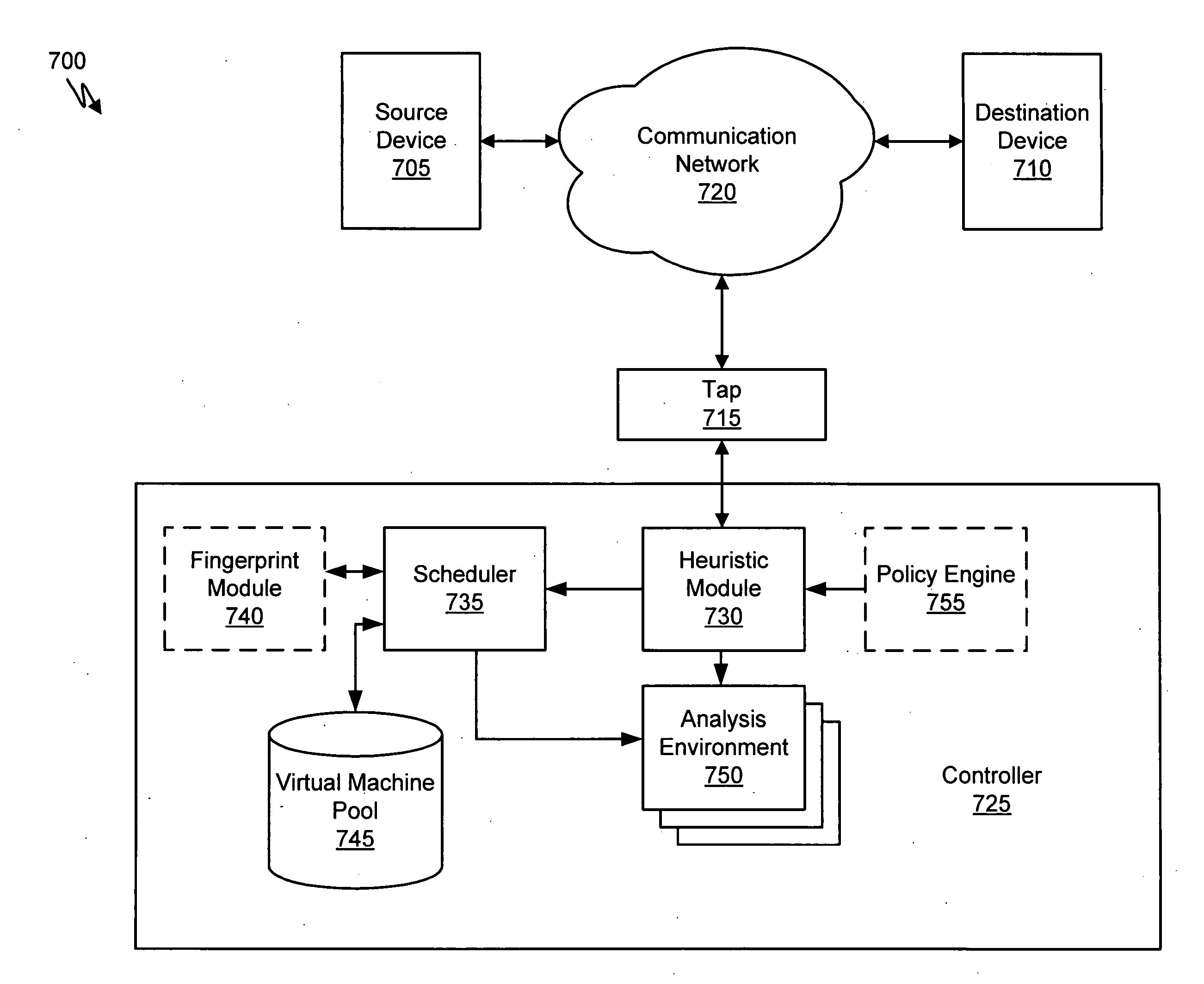
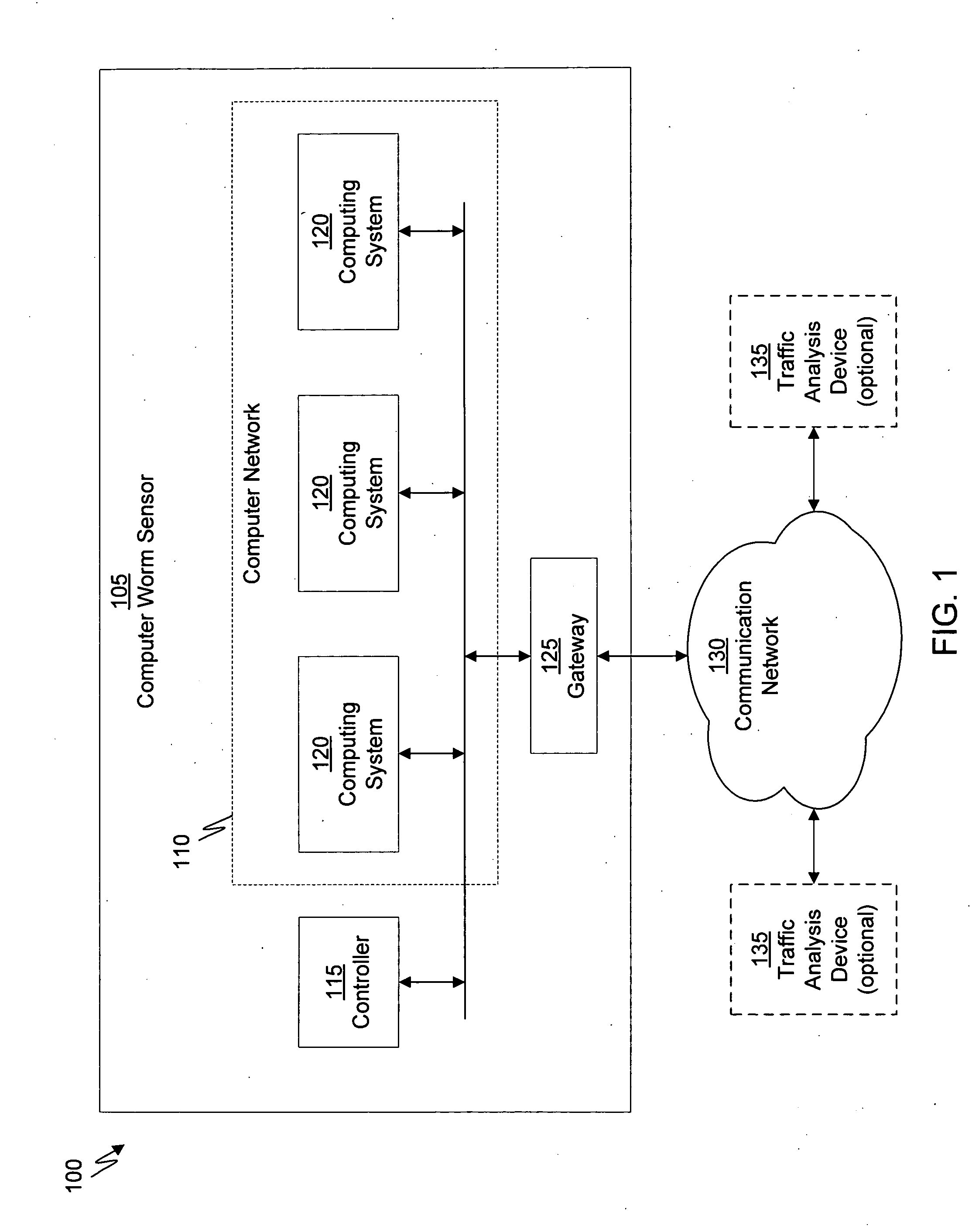
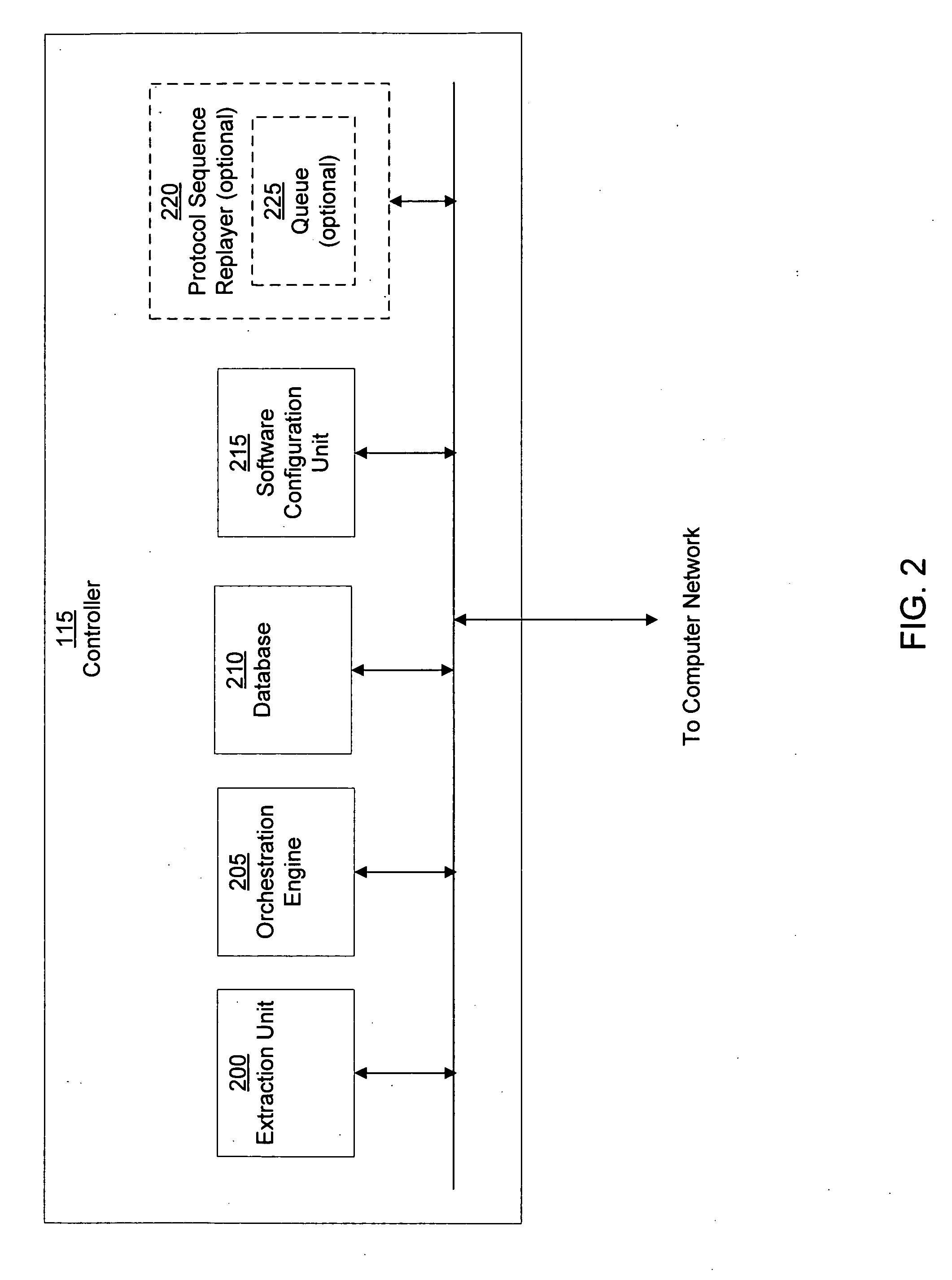
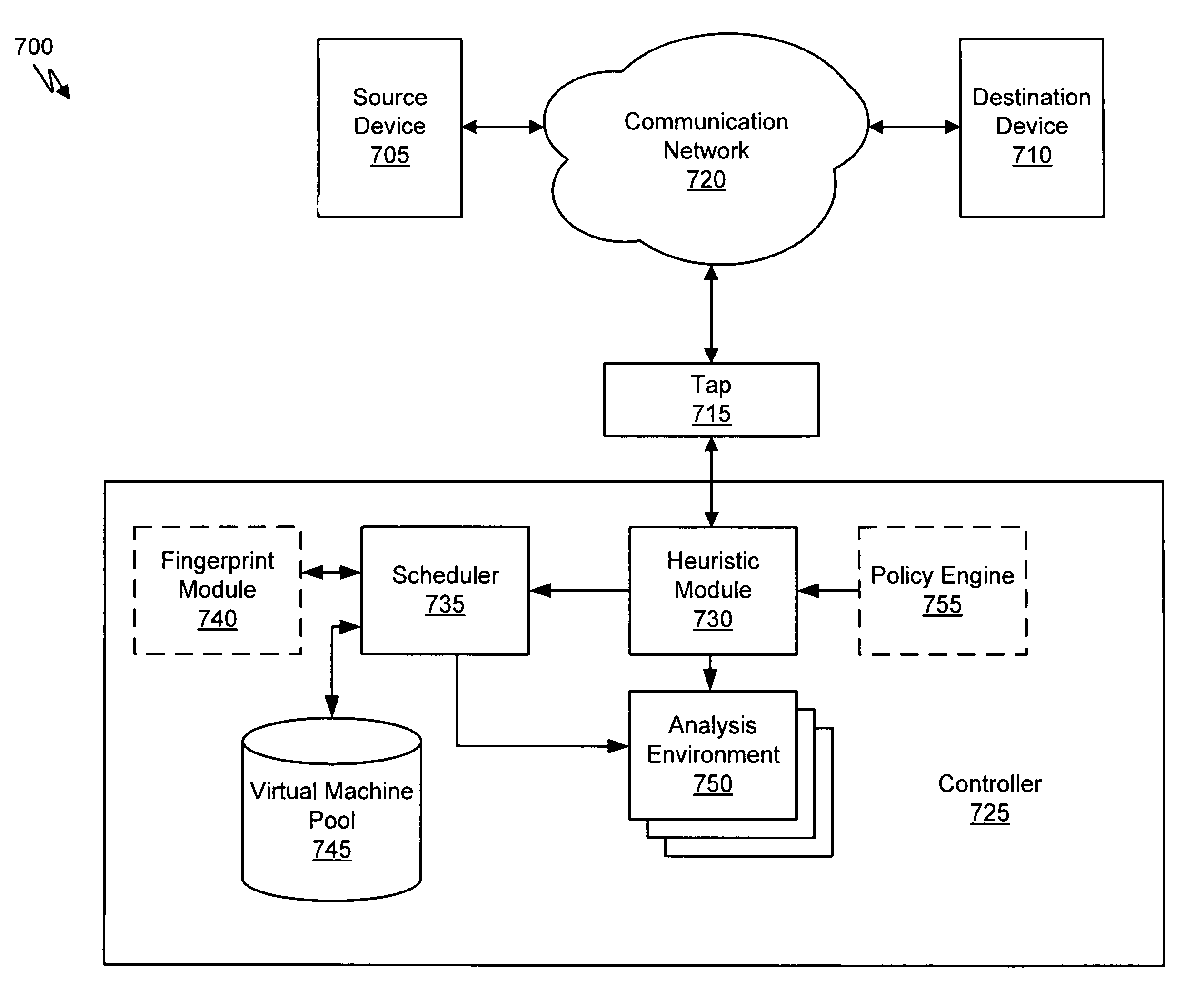
Heuristic based capture with replay to virtual machine
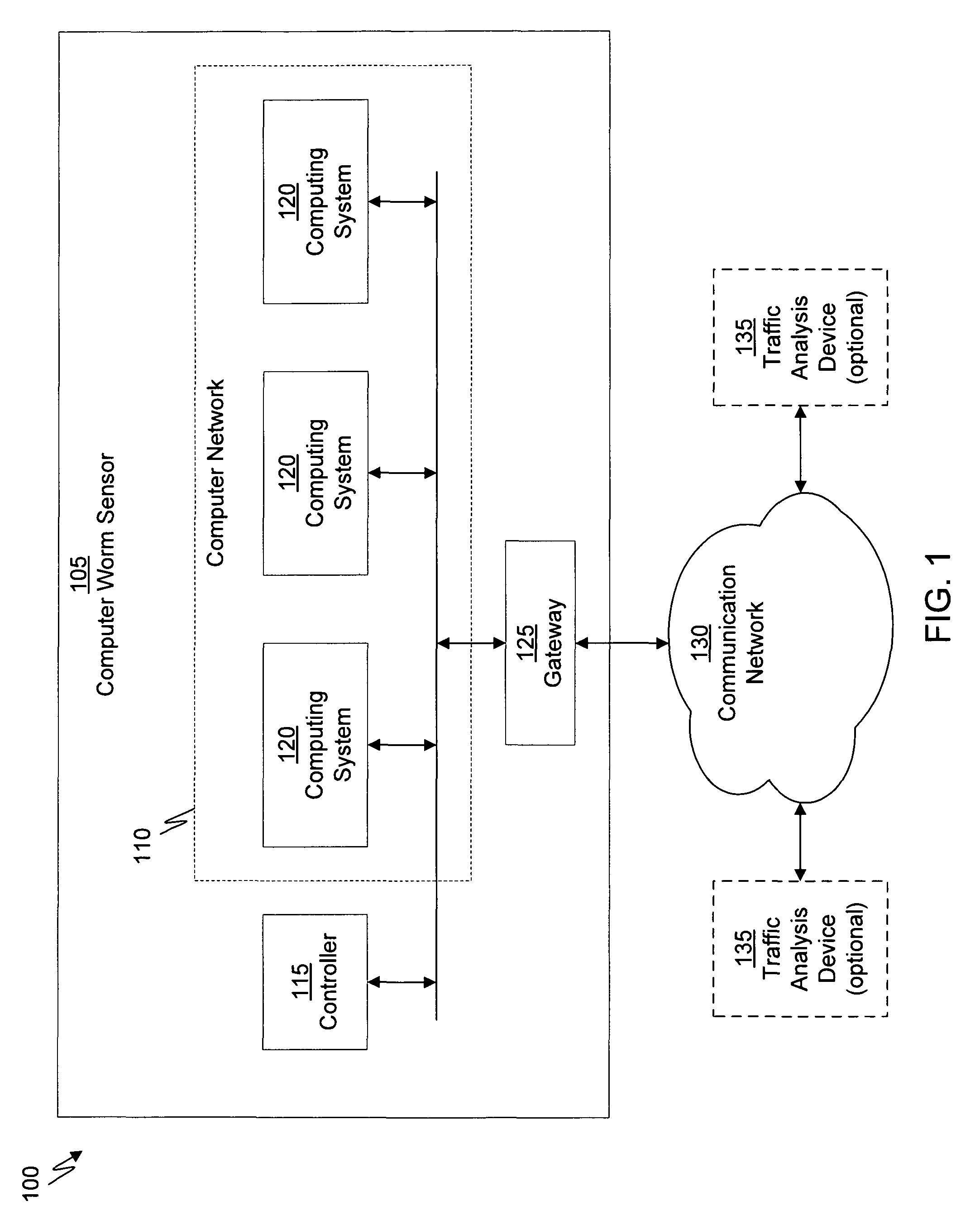
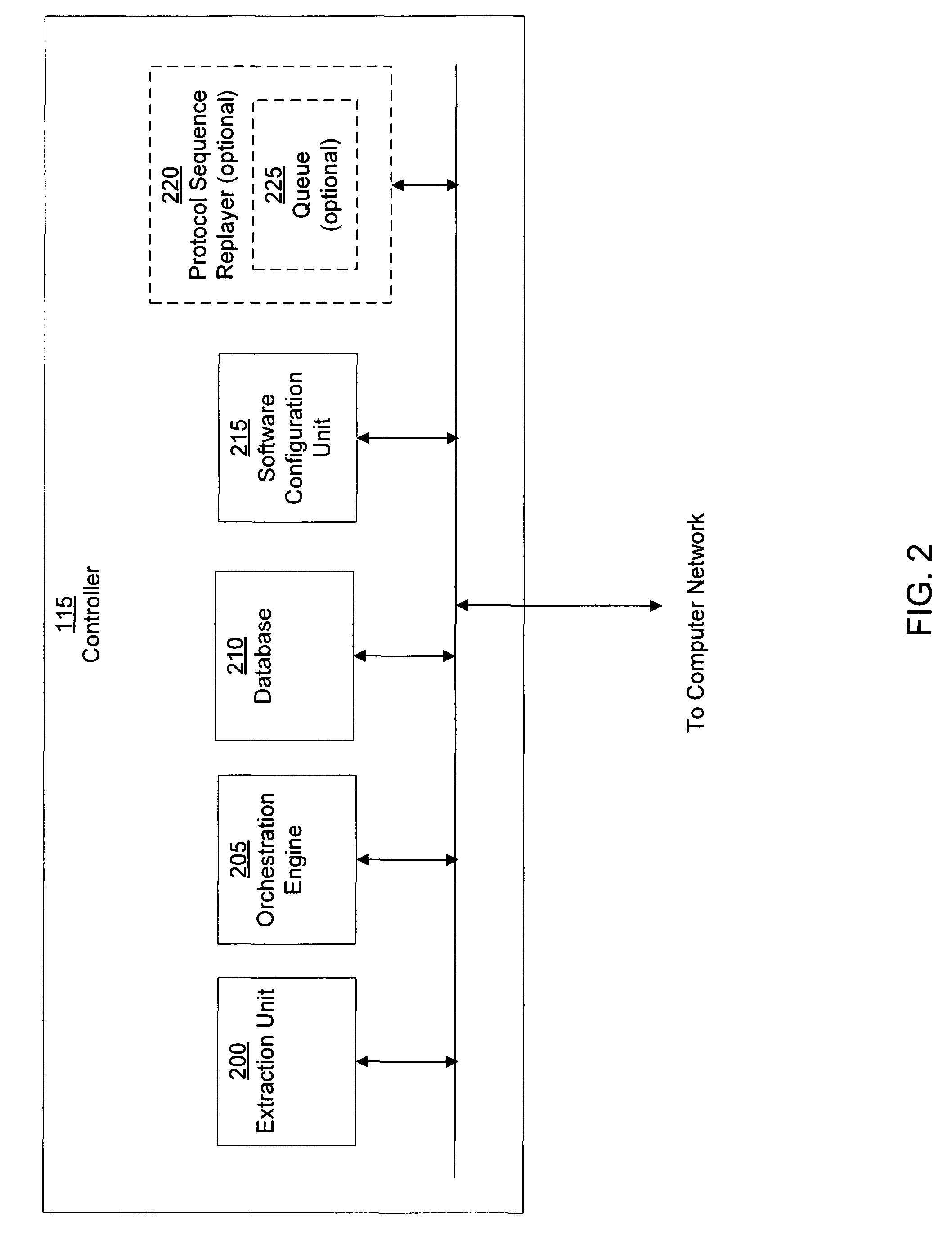
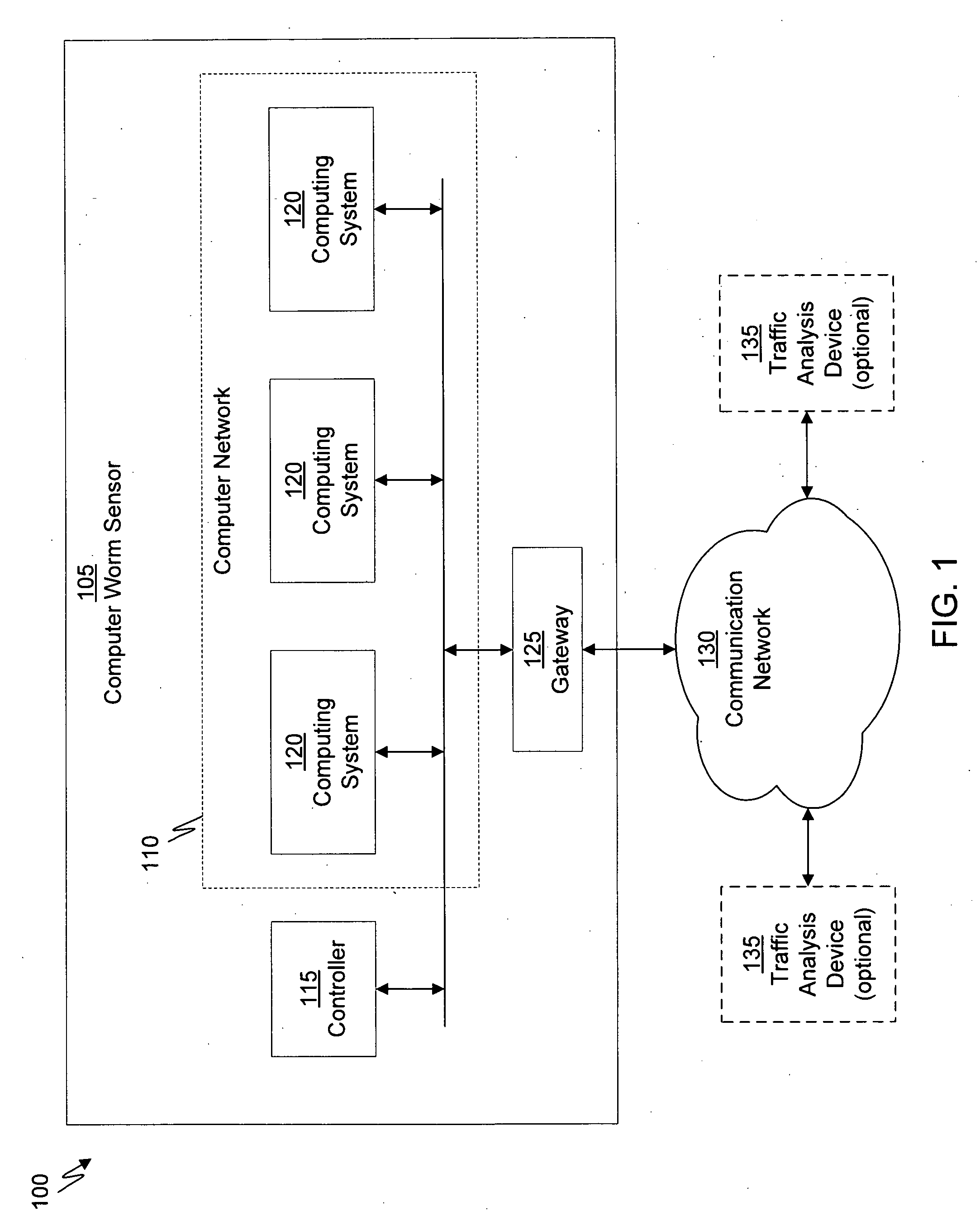
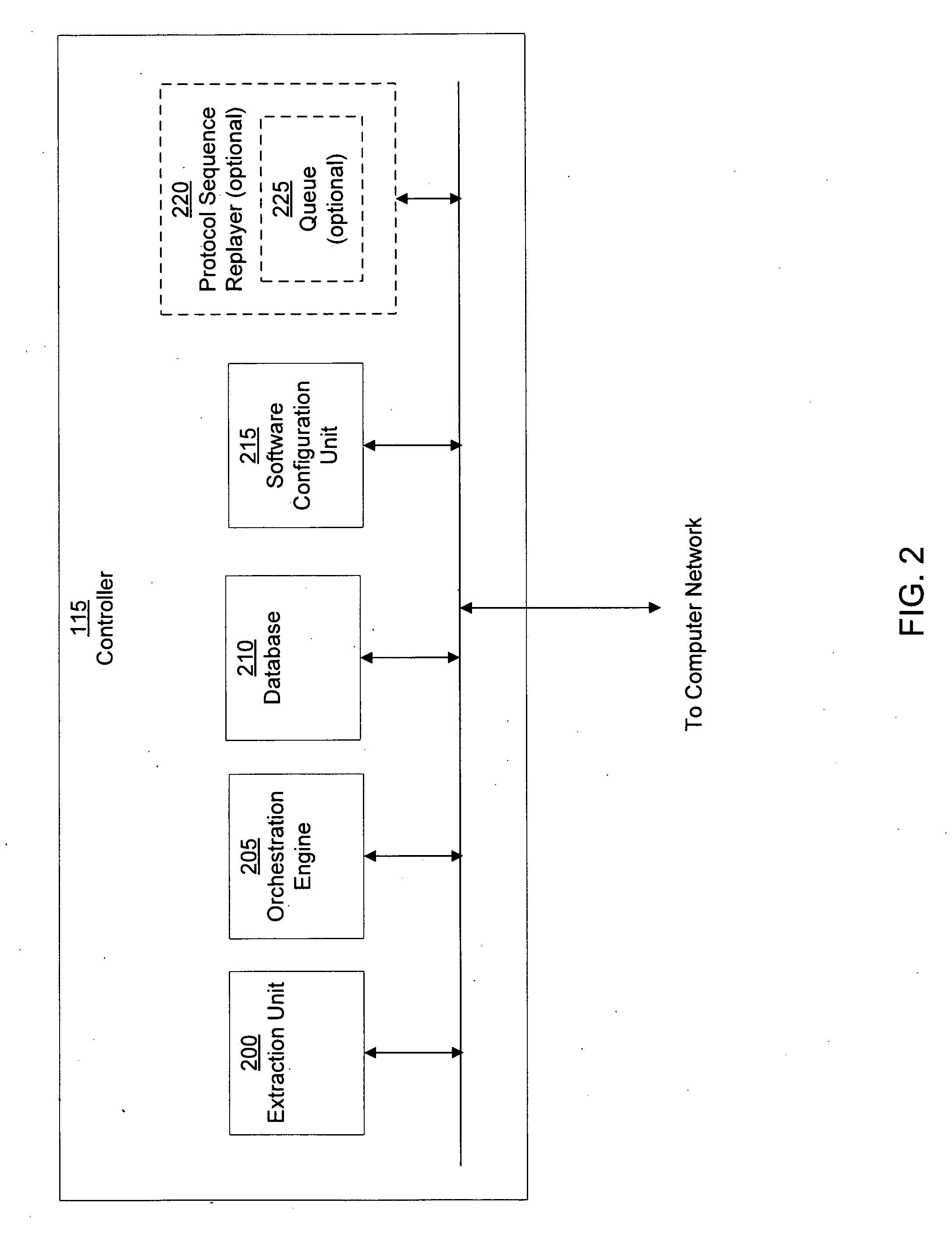
A suspicious activity capture system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is coupled to the tap and is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to flag the network data as suspicious, and simulate transmission of the network data to a destination device.
Owner:FIREEYE SECURITY HLDG US LLC
Dynamic signature creation and enforcement
Owner:FIREEYE SECURITY HLDG US LLC
Dynamic signature creation and enforcement
ActiveUS20120331553A1Memory loss protectionDigital data processing detailsNetwork dataDigital device
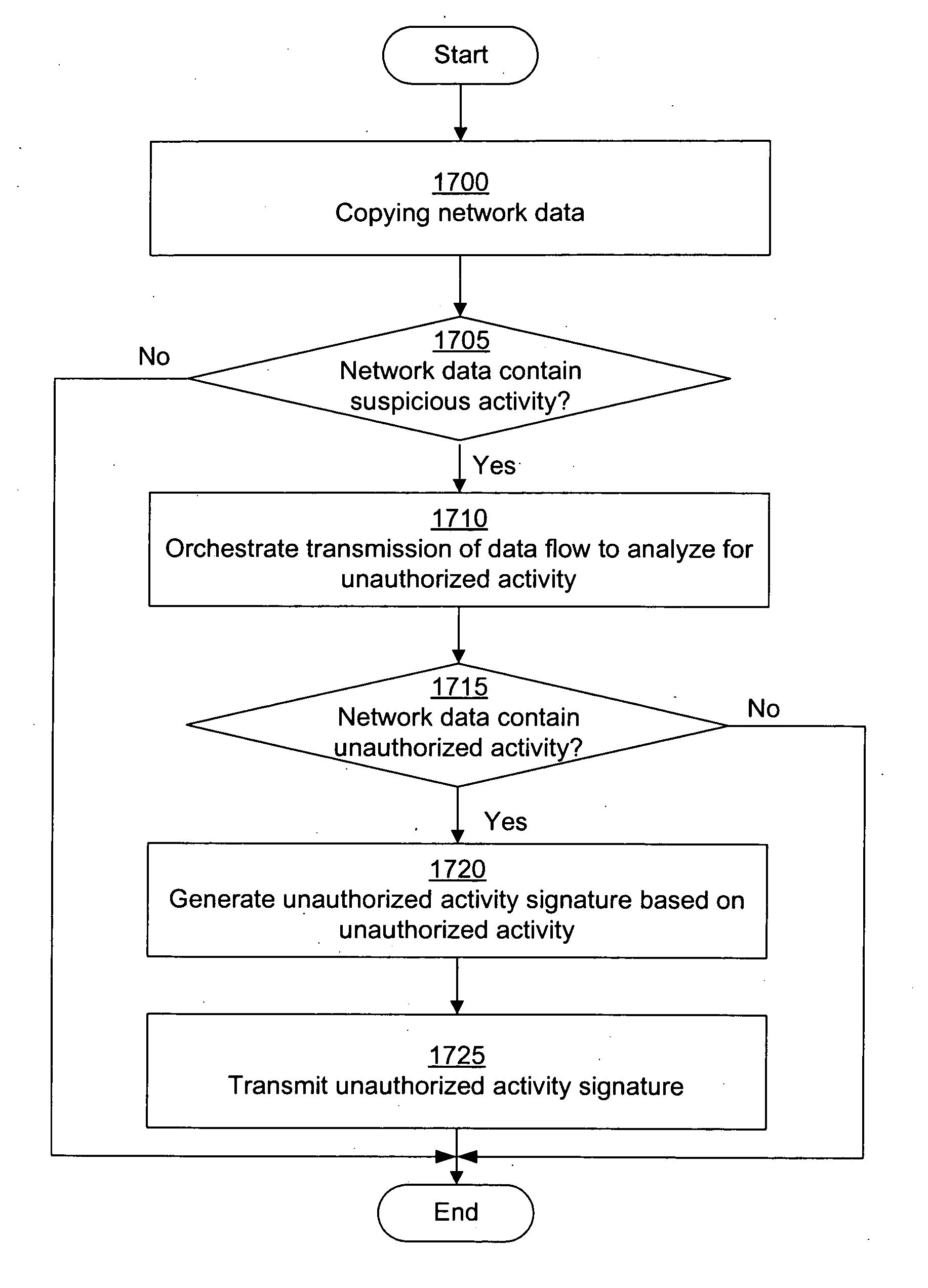
A dynamic signature creation and enforcement system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to determine if the network data is suspicious, flag the network data as suspicious based on the heuristic determination, simulate transmission of the network data to a destination device to identify unauthorized activity, generate an unauthorized activity signature based on the identification, and transmit the unauthorized activity signature to a digital device configured to enforce the unauthorized activity signature.
Owner:FIREEYE SECURITY HLDG US LLC
System and method for computer virus detection utilizing heuristic analysis
ActiveUS7231667B2Memory loss protectionUnauthorized memory use protectionChronological timeComputer engineering
A computer virus detection method includes compiling a list of heuristic events and a chronological order in which they occur, comparing the list of heuristic events and the chronological order with a defined list of heuristic events occurring in a defined chronological order and determining whether a computer virus is present based on a result of the comparing.
Owner:COMP ASSOC THINK INC
Distributed systems and methods for automatically detecting unknown bots and botnets
ActiveUS9430646B1Error detection/correctionPlatform integrity maintainanceOutbound communicationCommand and control
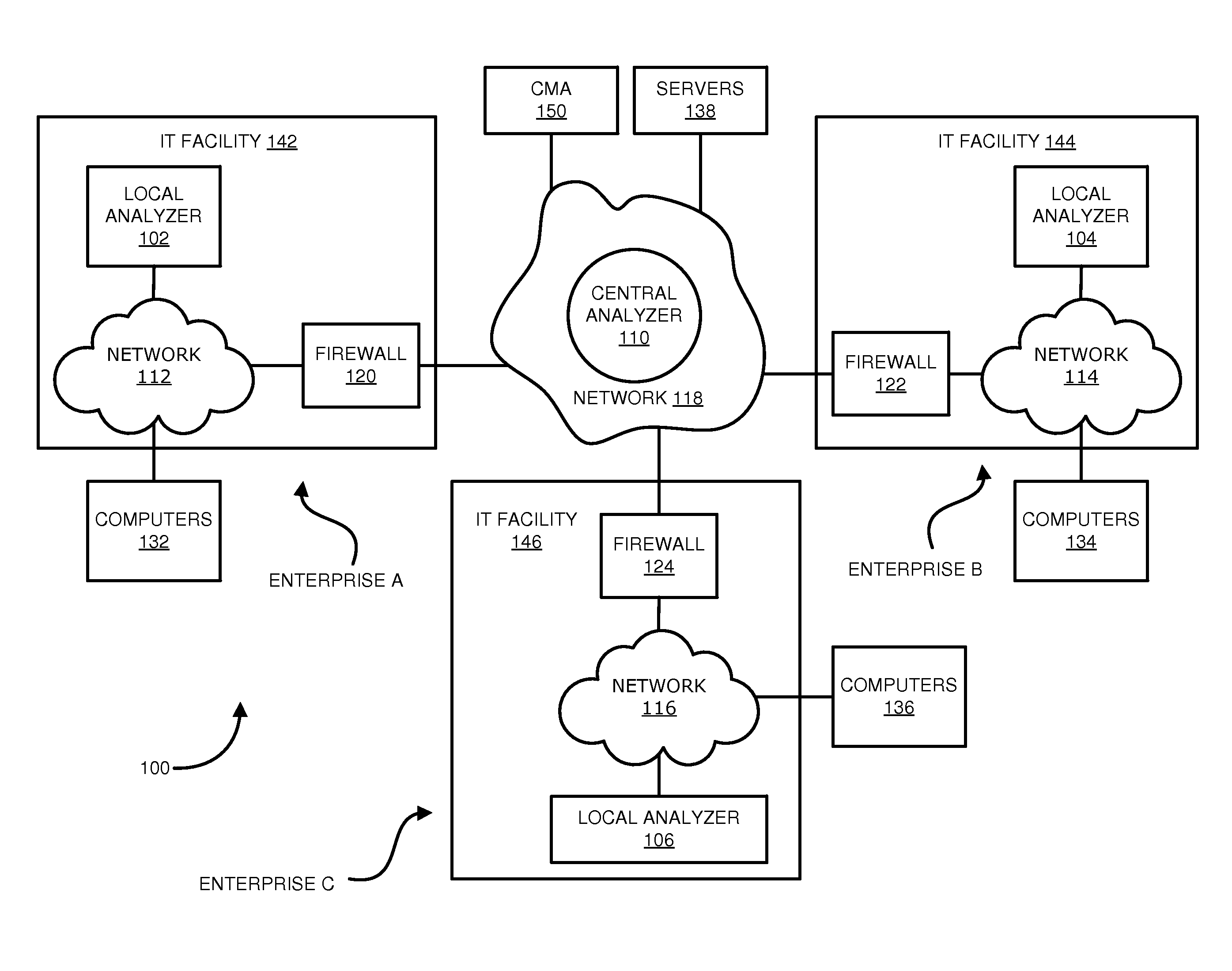
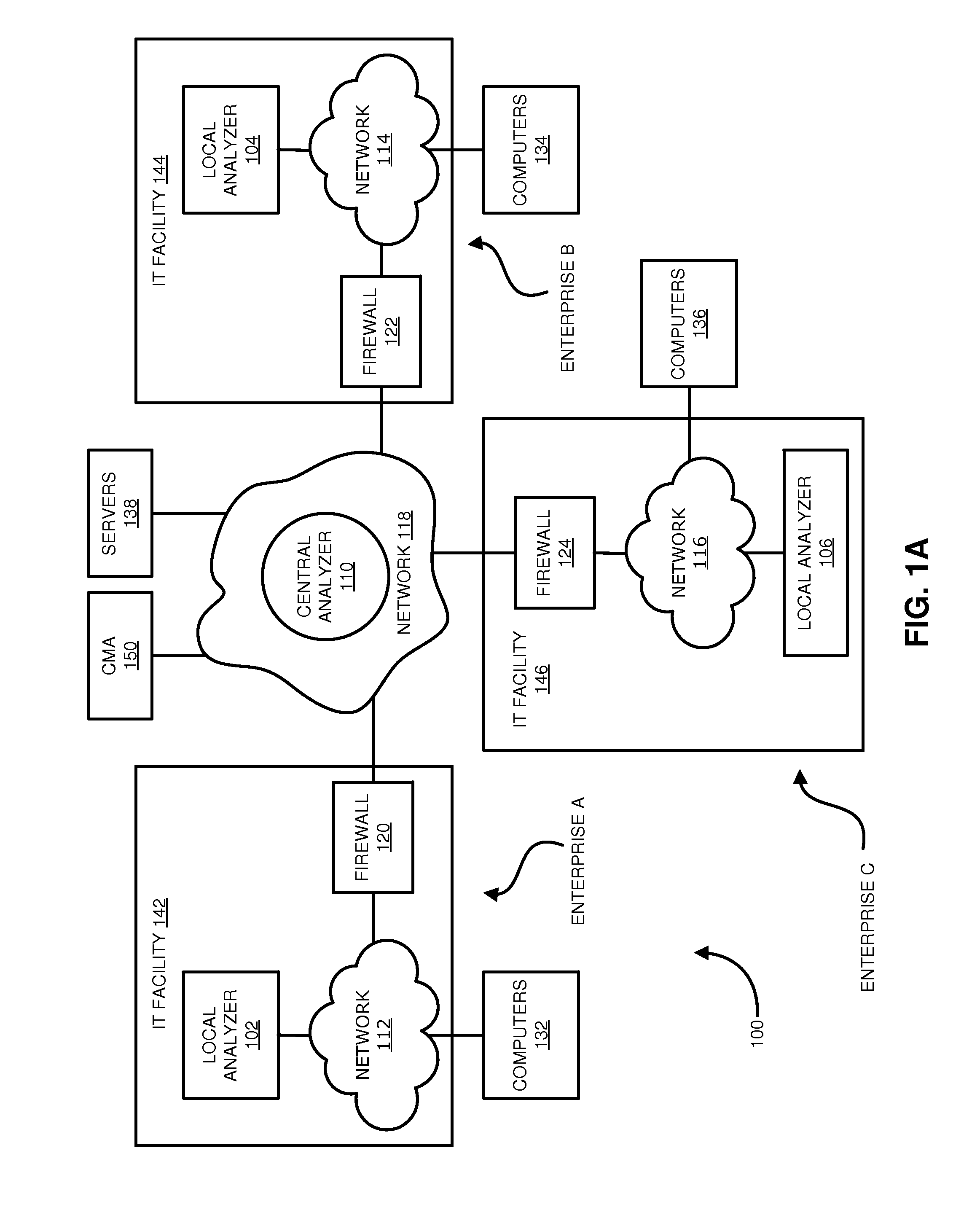
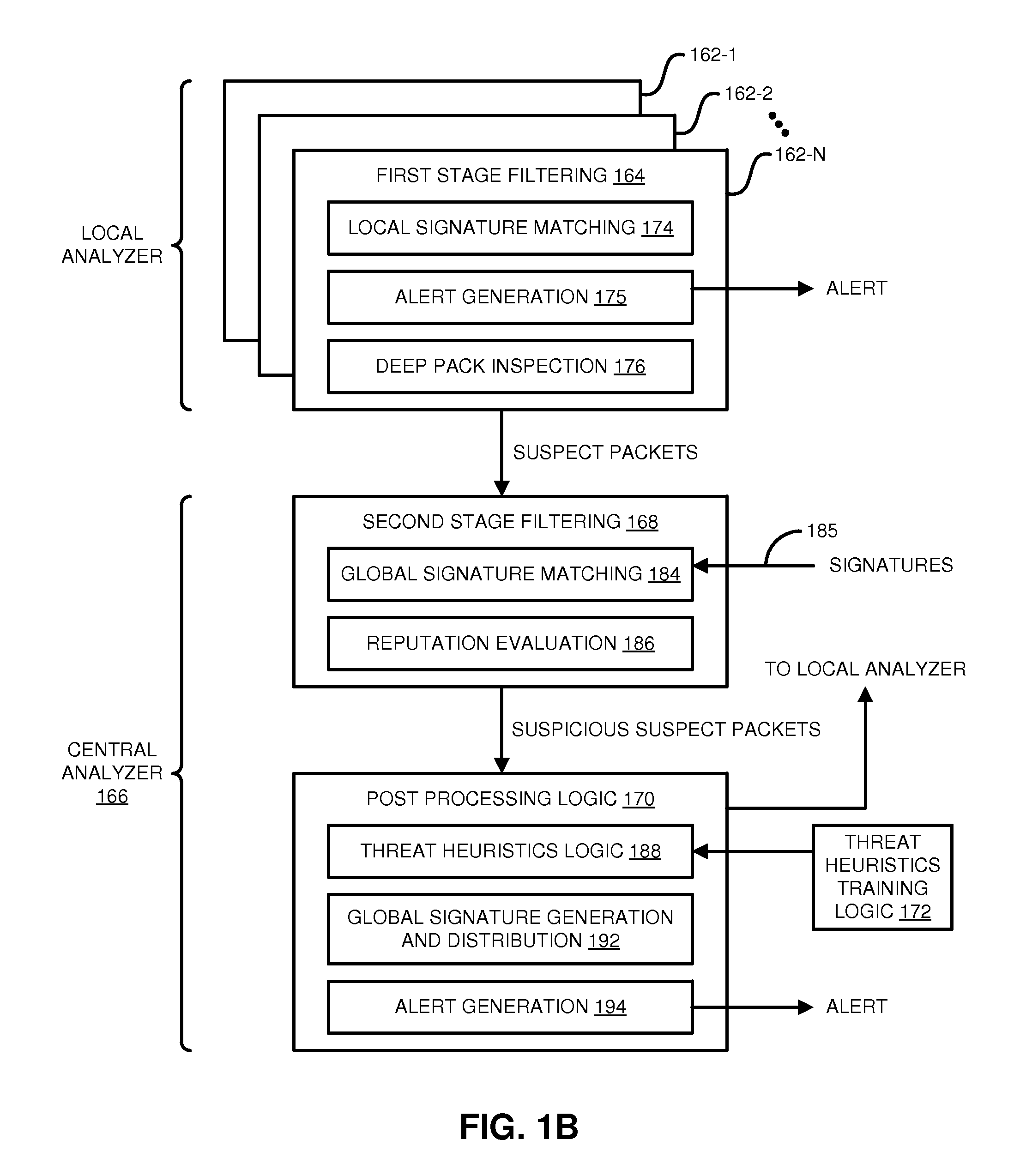
Techniques may automatically detect bots or botnets running in a computer or other digital device by detecting command and control communications, called “call-backs,” from malicious code that has previously gained entry into the digital device. Callbacks are detected using a distributed approach employing one or more local analyzers and a central analyzer. The local analyzers capture packets of outbound communications, generate header signatures, and analyze the captured packets using various techniques. The techniques may include packet header signature matching against verified callback signatures, deep packet inspection. The central analyzer receives the header signatures and related header information from the local analyzers, may perform further analysis (for example, on-line host reputation analysis); determines using a heuristics analysis whether the signatures correspond to callbacks; and generally coordinates among the local analyzers.
Owner:FIREEYE SECURITY HLDG US LLC
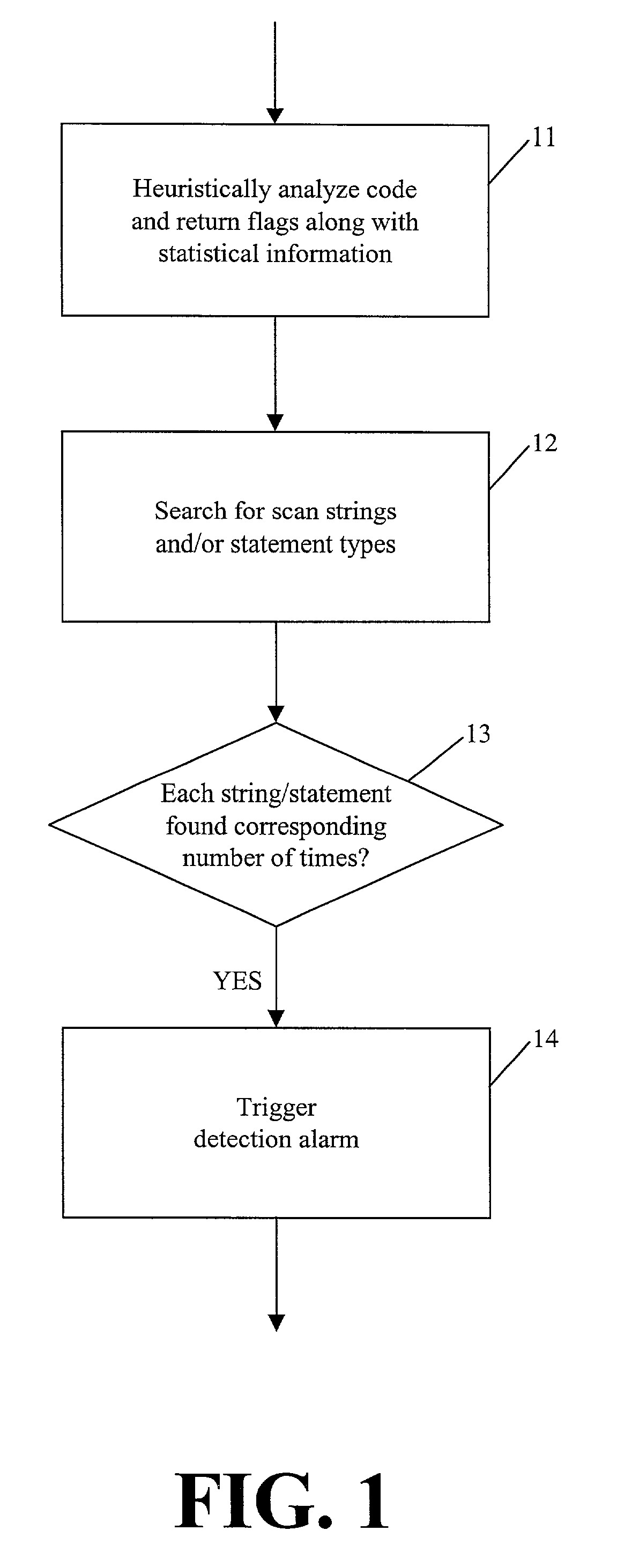
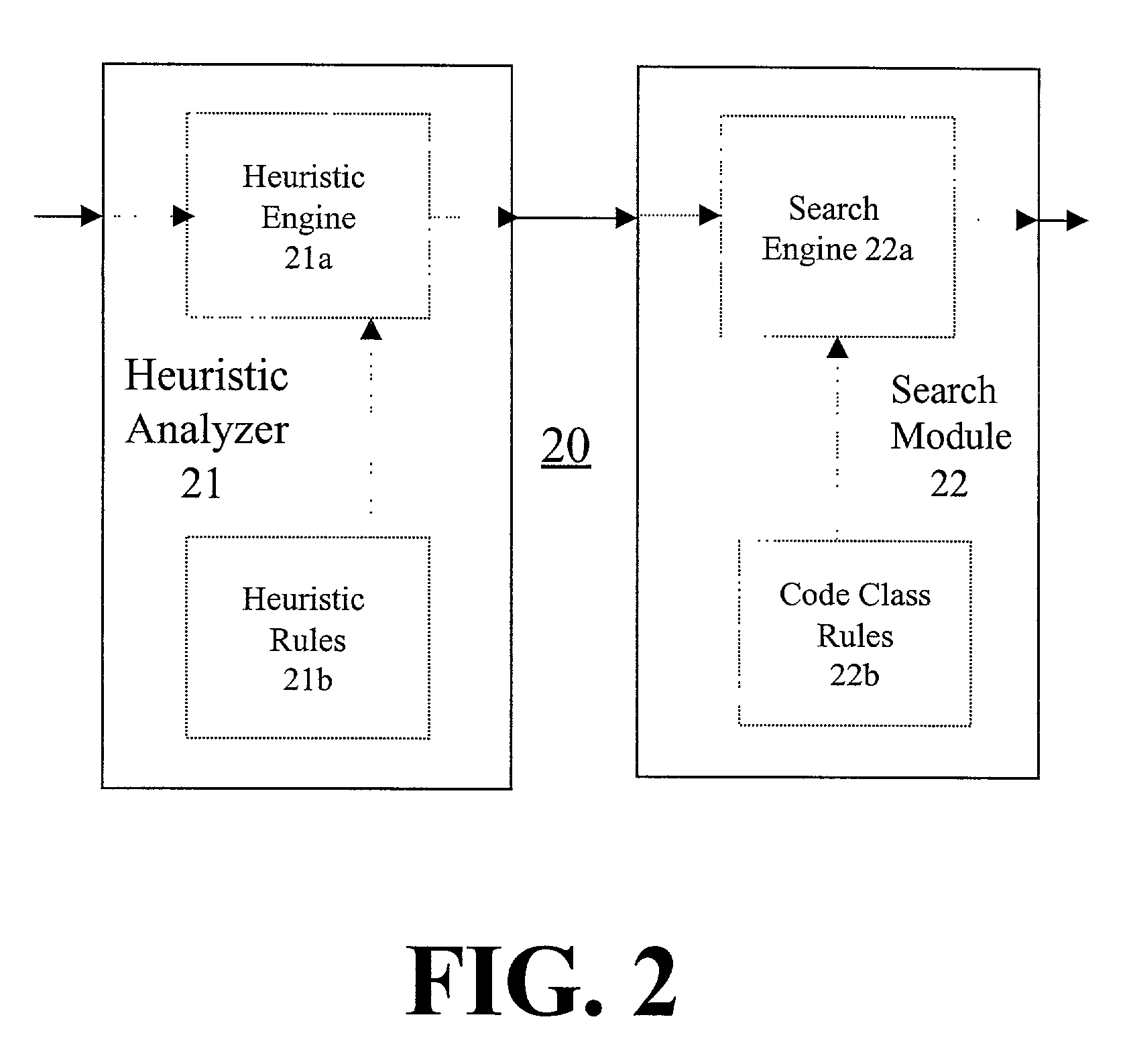
Detection of a class of viral code
InactiveUS7069589B2Memory loss protectionDigital data processing detailsTheoretical computer scienceSubject specific
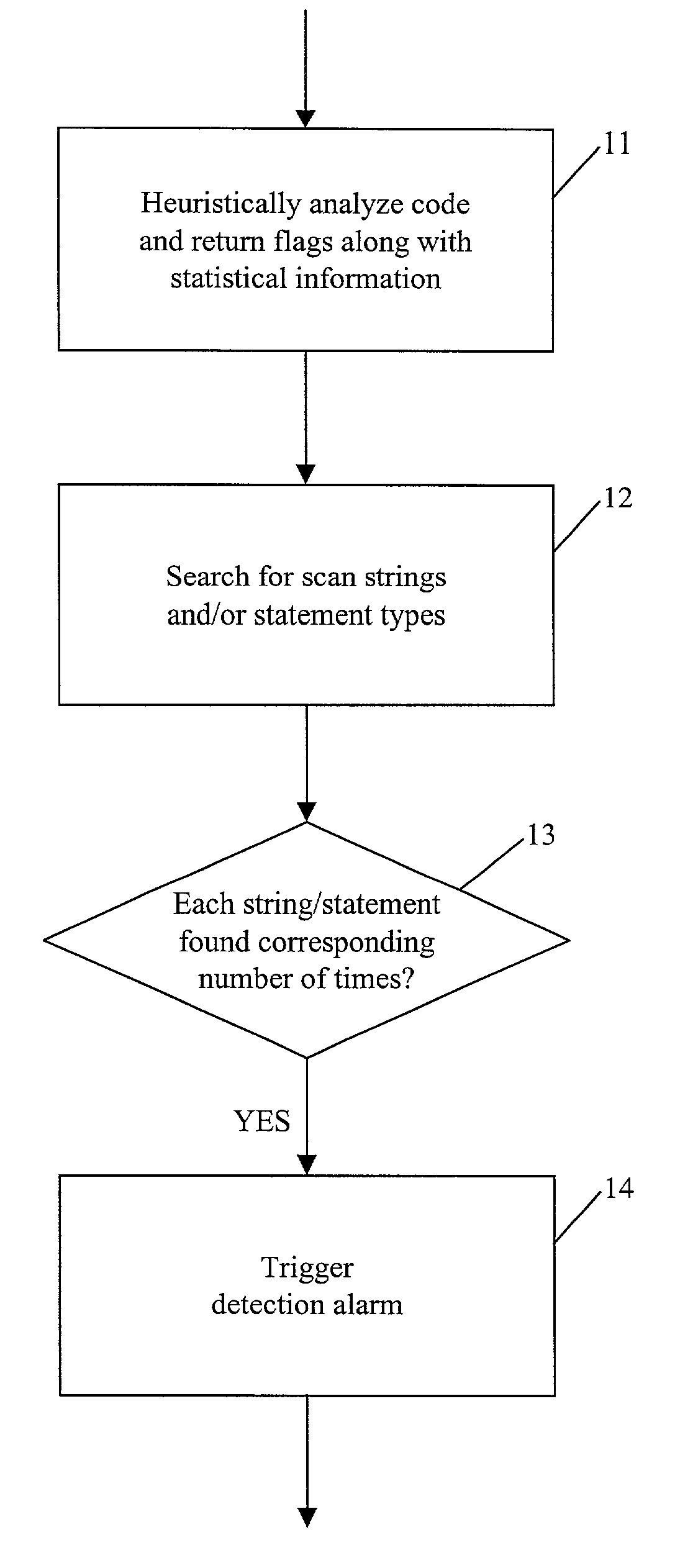
A method and apparatus for detecting a class of viral code are provided. The apparatus comprises an heuristic analyzer and a search component. The heuristic analyzer heuristically analyzes a subject file and generates a set of flags along with statistical information. The search component uses the set of flags with statistical information to perform a search for a scan string and / or a statement type in the subject file. A positive detection alarm is triggered if the scan string and / or statement type is found at least a corresponding predetermined number of times. The heuristic analyzer may be rule-based and comprise an heuristic engine and heuristic rules. The search component also may be rule-based and comprise a search engine and viral code class rules.
Owner:COMP ASSOC THINK INC
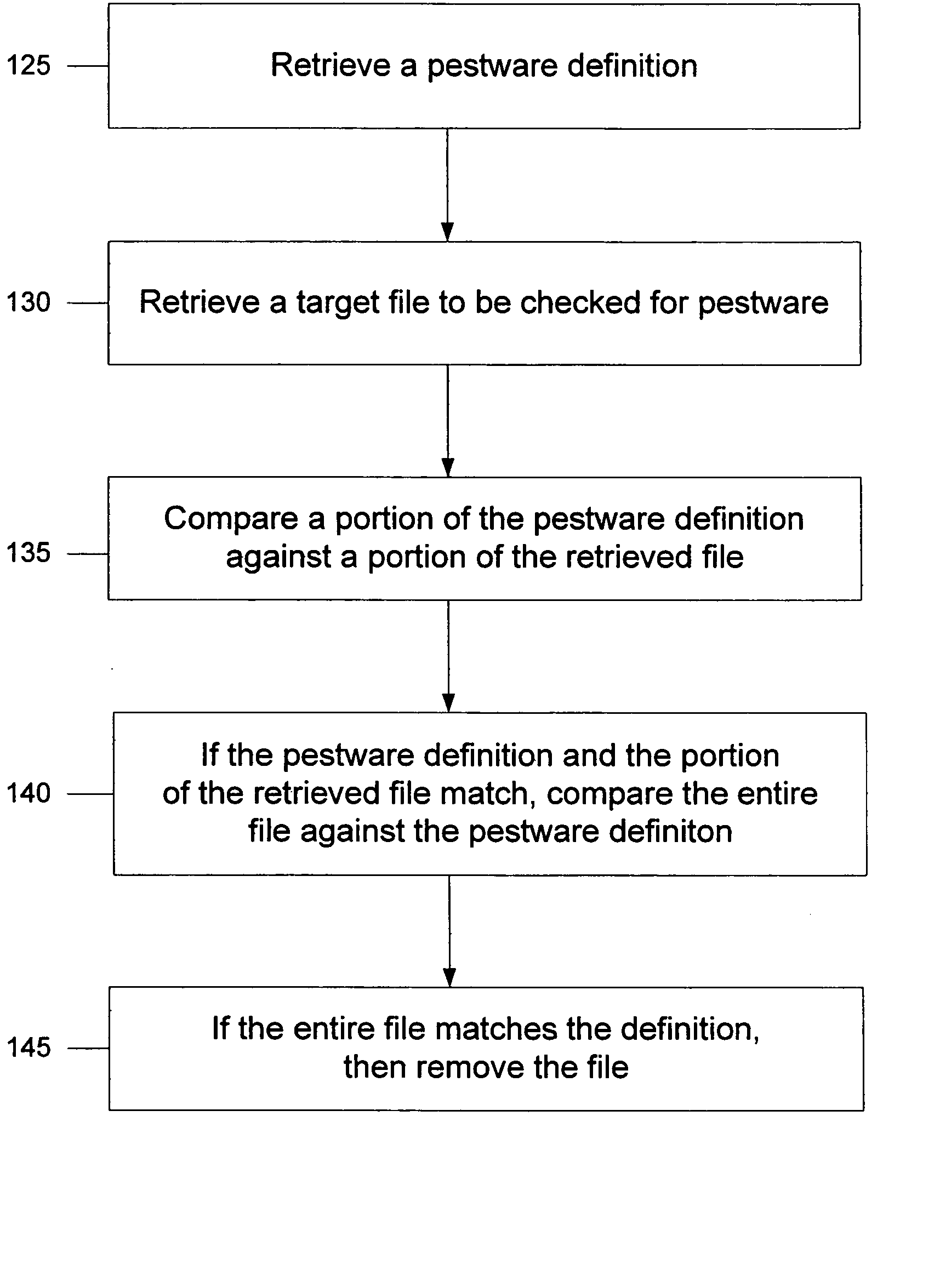
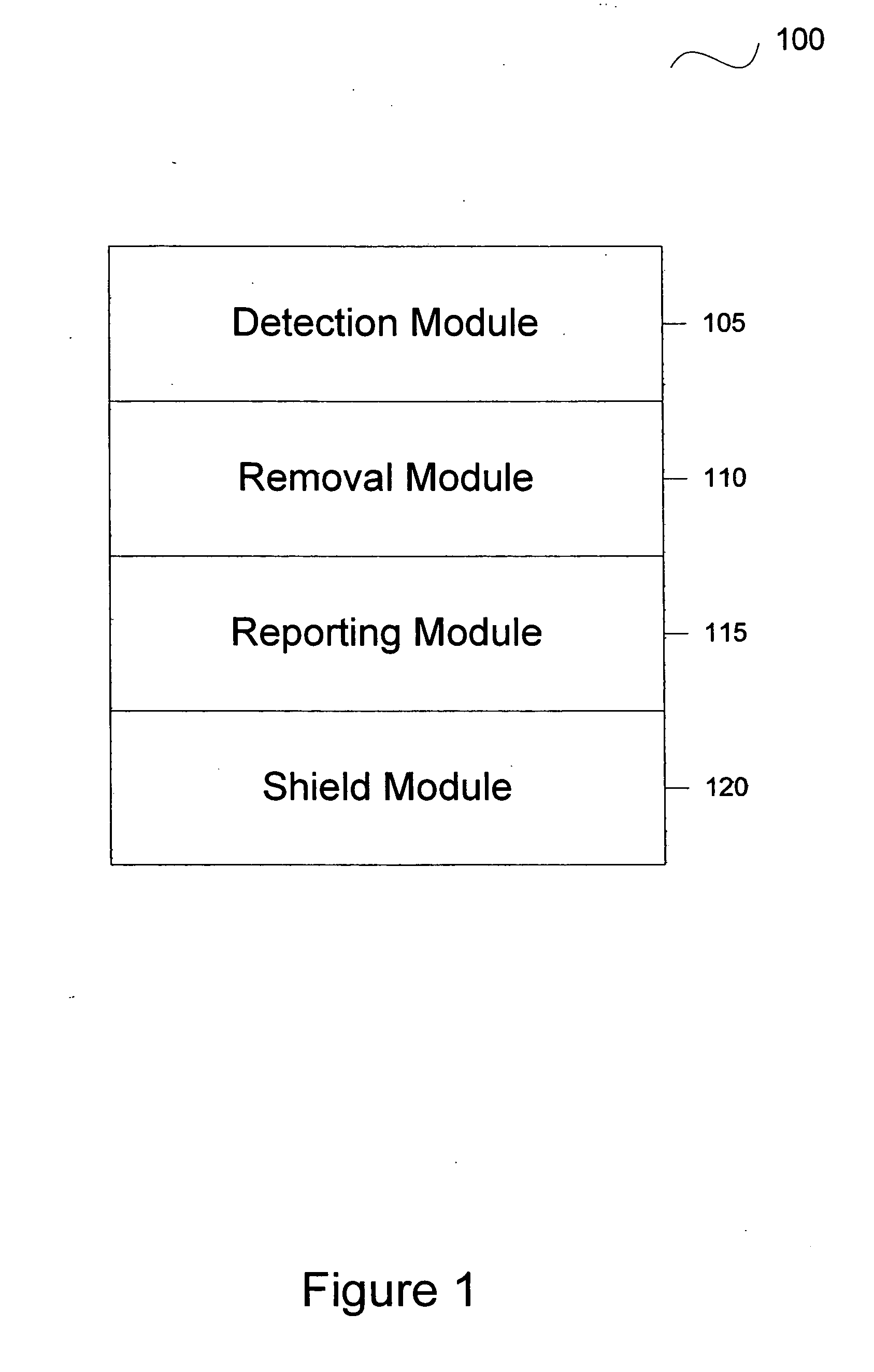
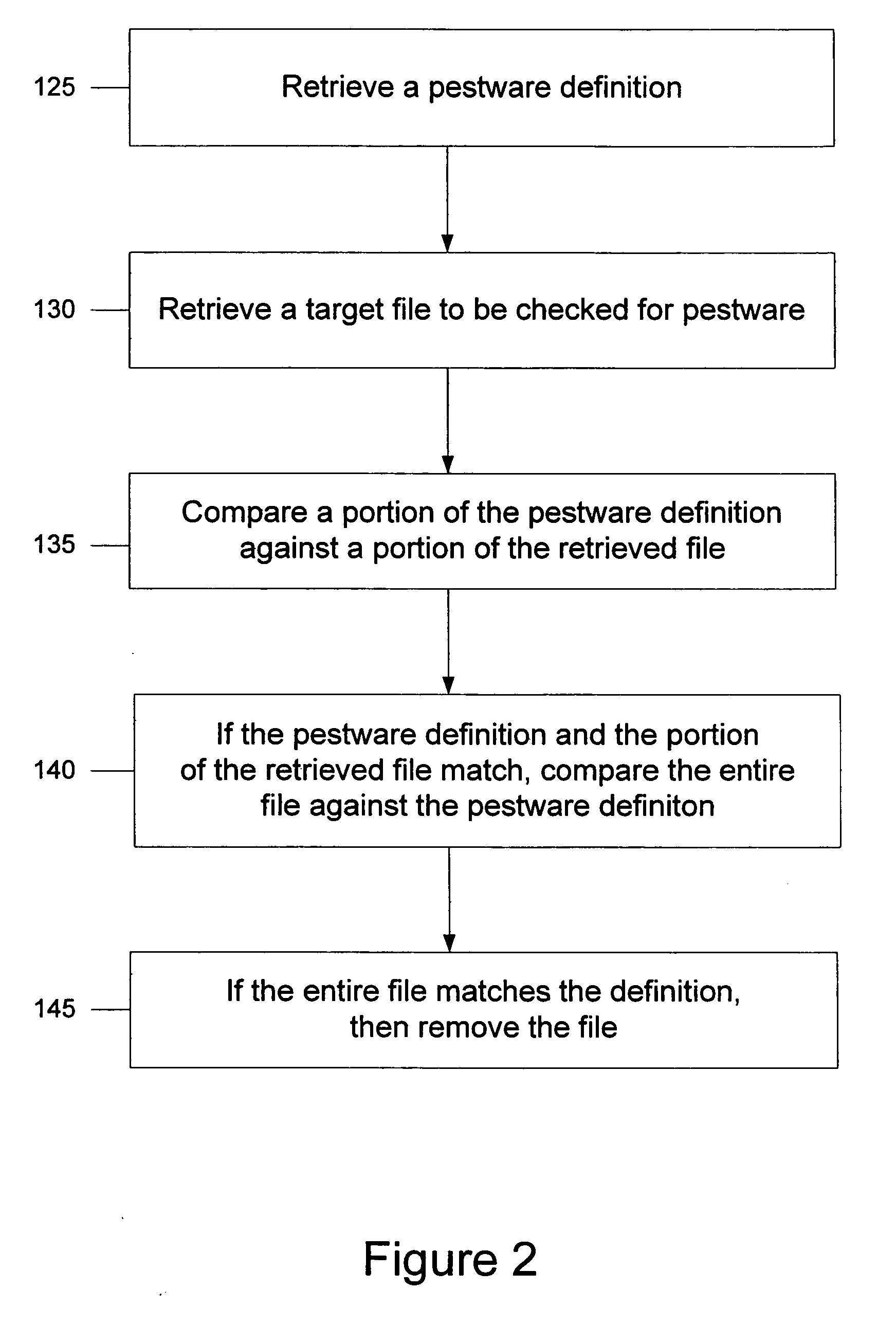
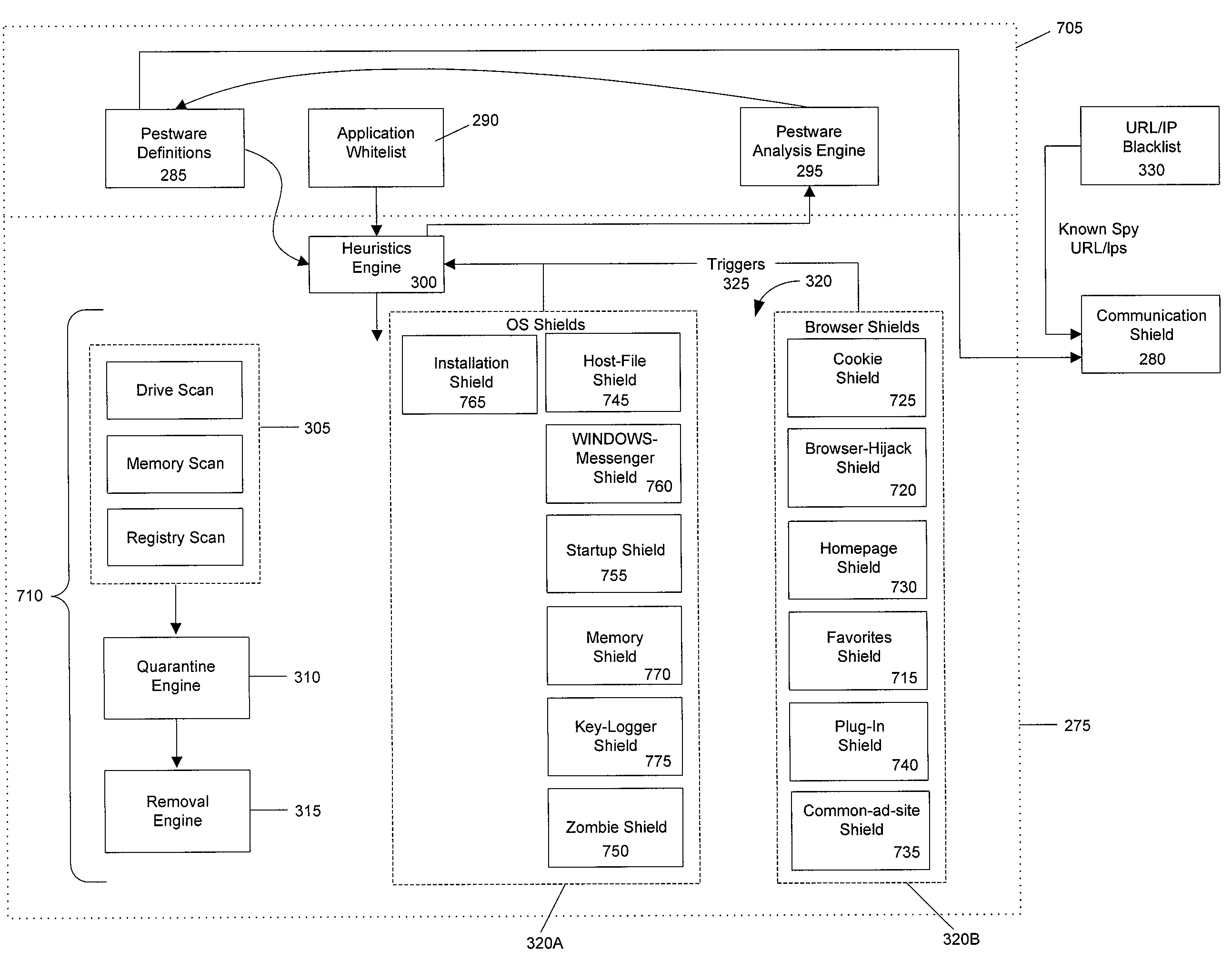
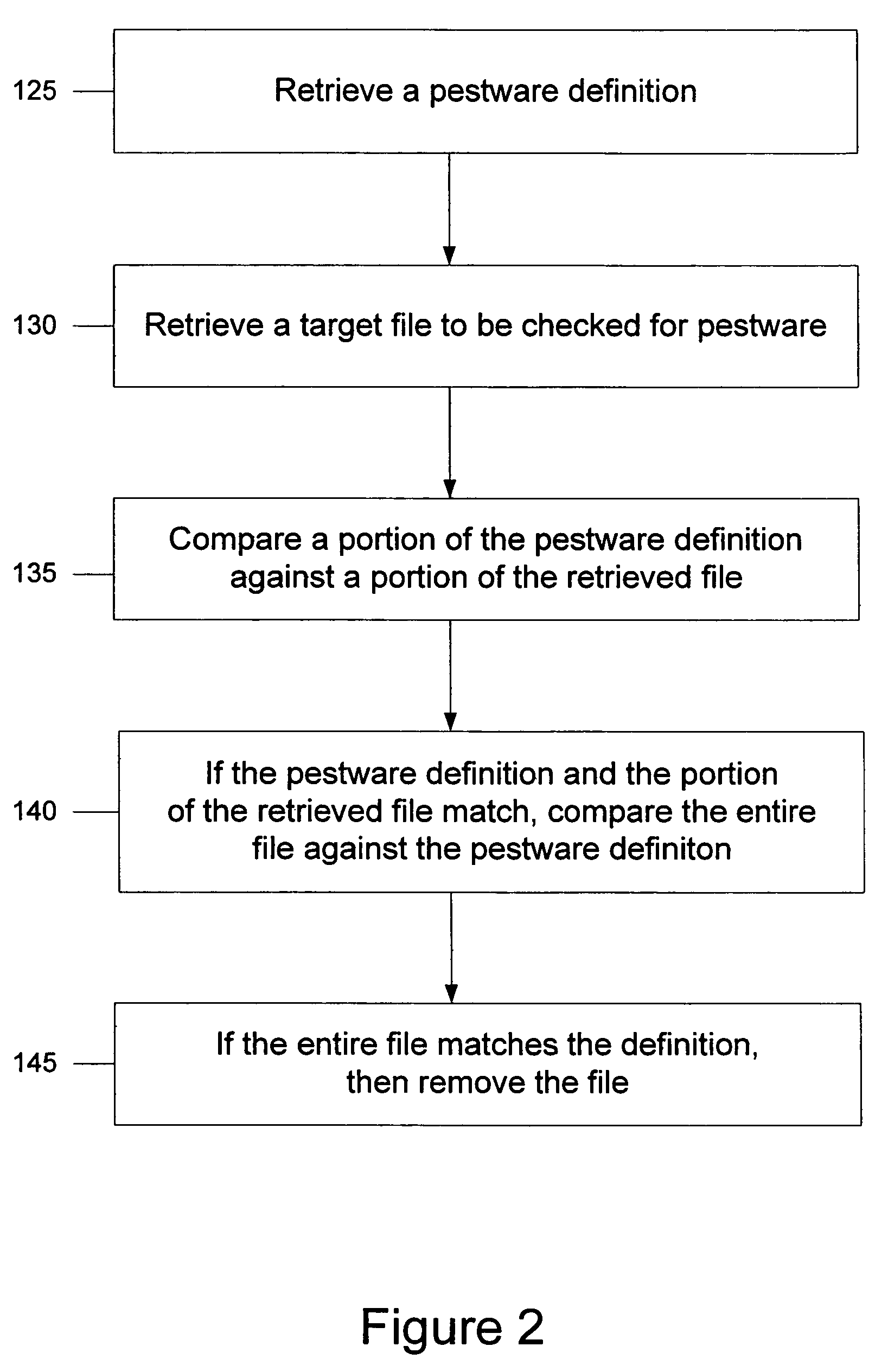
System and method for heuristic analysis to identify pestware
Systems for preventing pestware activity are described. One embodiment a heuristic engine configured to identify repeat pestware activity and configured to block the repeat pestware activity; an operating system pestware shield in communication with the heuristic engine, the operating system pestware shield configured to detect pestware activity and report the pestware activity to the heuristic engine; and a browser pestware shield in communication with the heuristic engine, the browser pestware shield configured to detect pestware activity and report the pestware activity to the heuristic engine.
Owner:OPEN TEXT CORPORATION
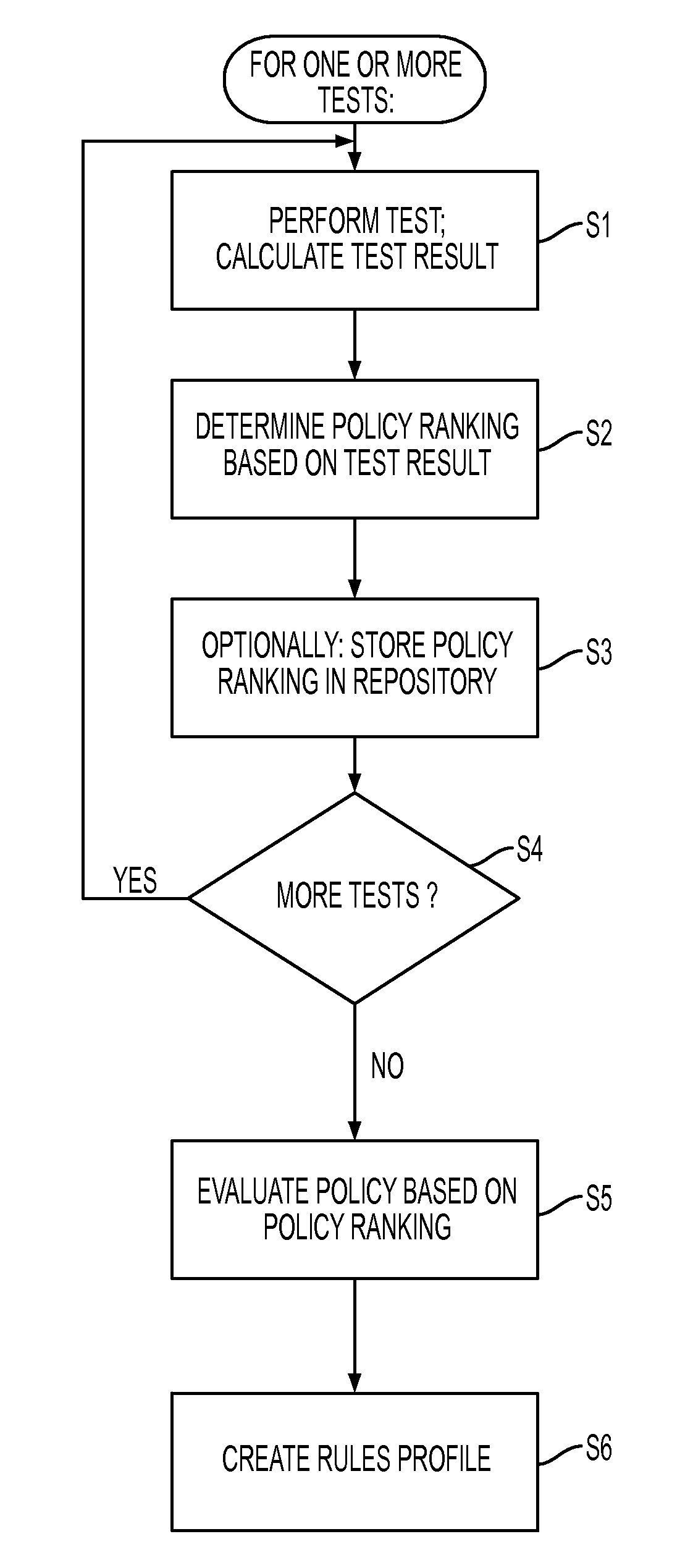
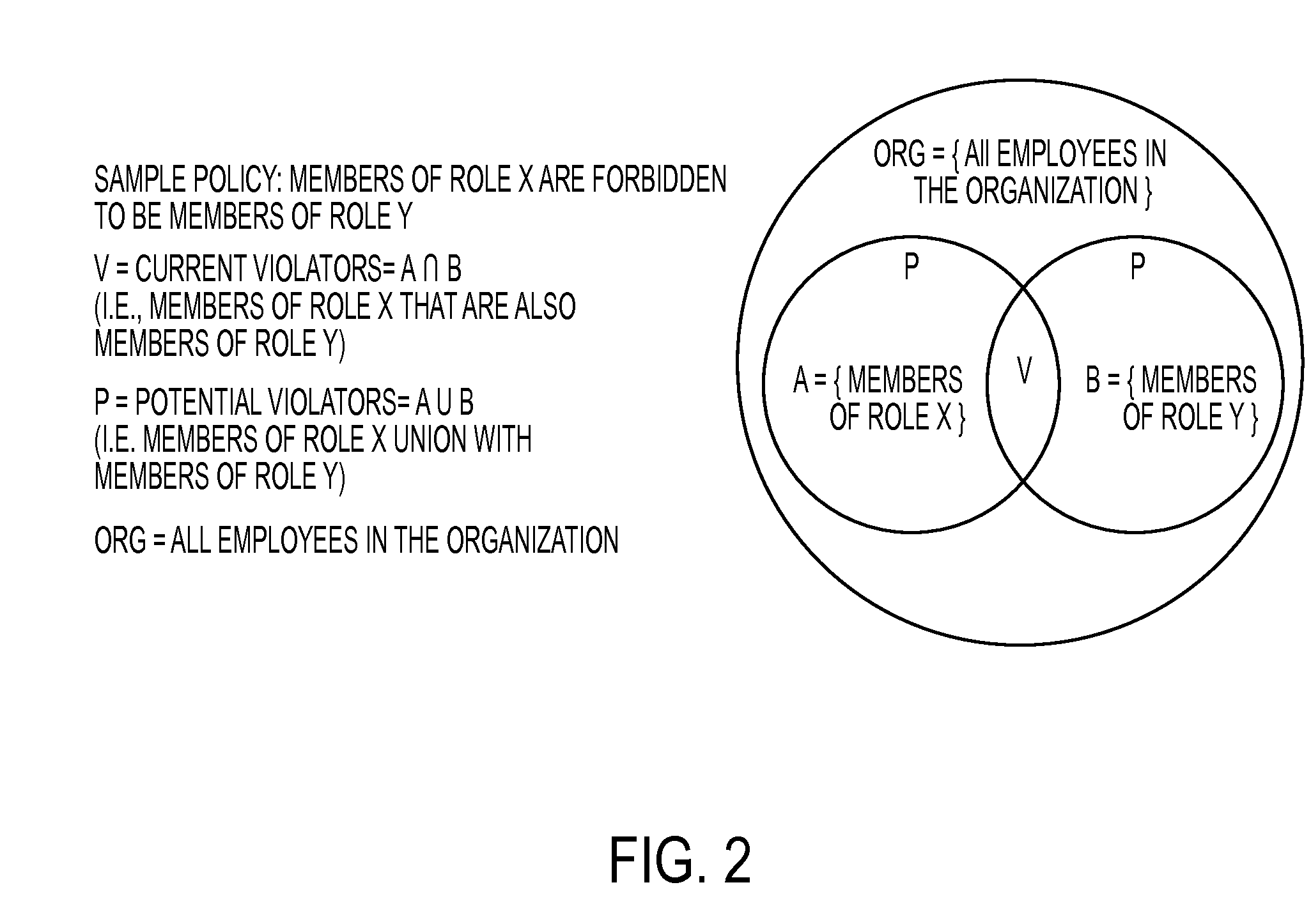
Heuristic policy analysis
A system and method using statistical analysis for the process of analyzing and generating organizational policies is presented. This inventive method comprises, for one or more tests, using a test to calculate a test result for the policy based on current violator entities and potential violator entities, and determining a policy ranking for the policy based on the test result of the test, and evaluating the policy based on the policy rankings determined from the tests. The method can also comprise creating a repository comprising the policy rankings for the plurality of policies. The repository can be used to trend, benchmark, alert and improve the policies. The method can also comprise creating a rule profile for the one policy comprising the one policy, the current violator entities of the policy, the potential violator entities of the policy, the test results and the policy rankings from the tests.
Owner:CA TECH INC
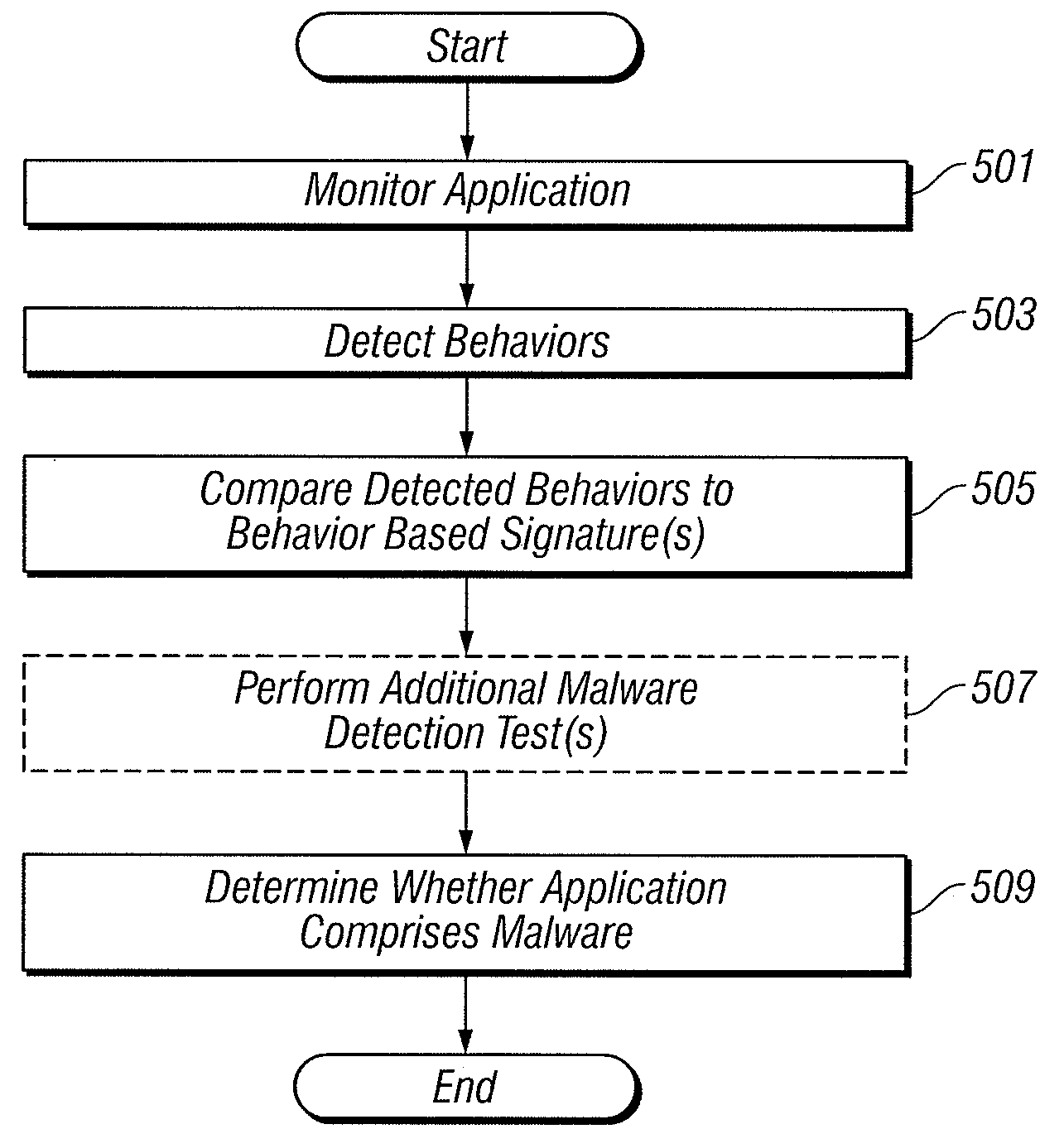
Behavior based signatures
Behavior based signatures for identifying applications are generated. An application is monitored as it runs. Specific behaviors concerning the execution of the application are detected, and a behavior based signature representing detected behaviors is created, such that the behavior based signature can be used subsequently to identify instances of the application. Behavior based signatures identifying known malicious and / or non-malicious applications can be used to determine whether other applications comprise malware. To do so, a running application is monitored, and specific behaviors concerning the execution of the application are detected. The detected behaviors are compared to one or more behavior based signatures. Responsive to whether the detected behaviors match, a behavior based signature, it can be determined whether the application comprises malware. An additional malware detection test, such as a heuristic analysis, can also be performed and used in determining whether the application comprises malware.
Owner:CA TECH INC
Automated latent star schema discovery tool
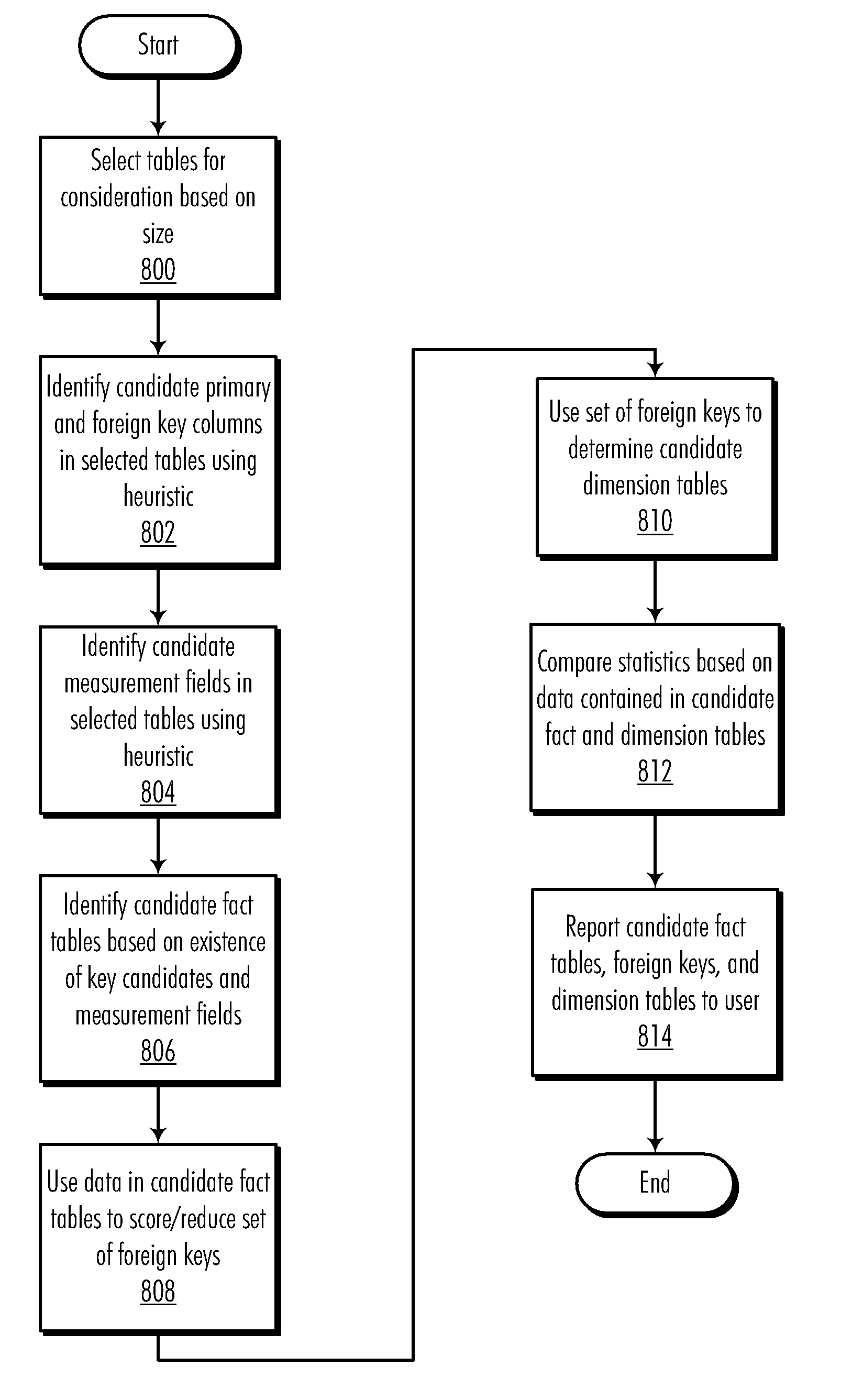
InactiveUS7856416B2Digital data processing detailsMulti-dimensional databasesStar schemaData processing system
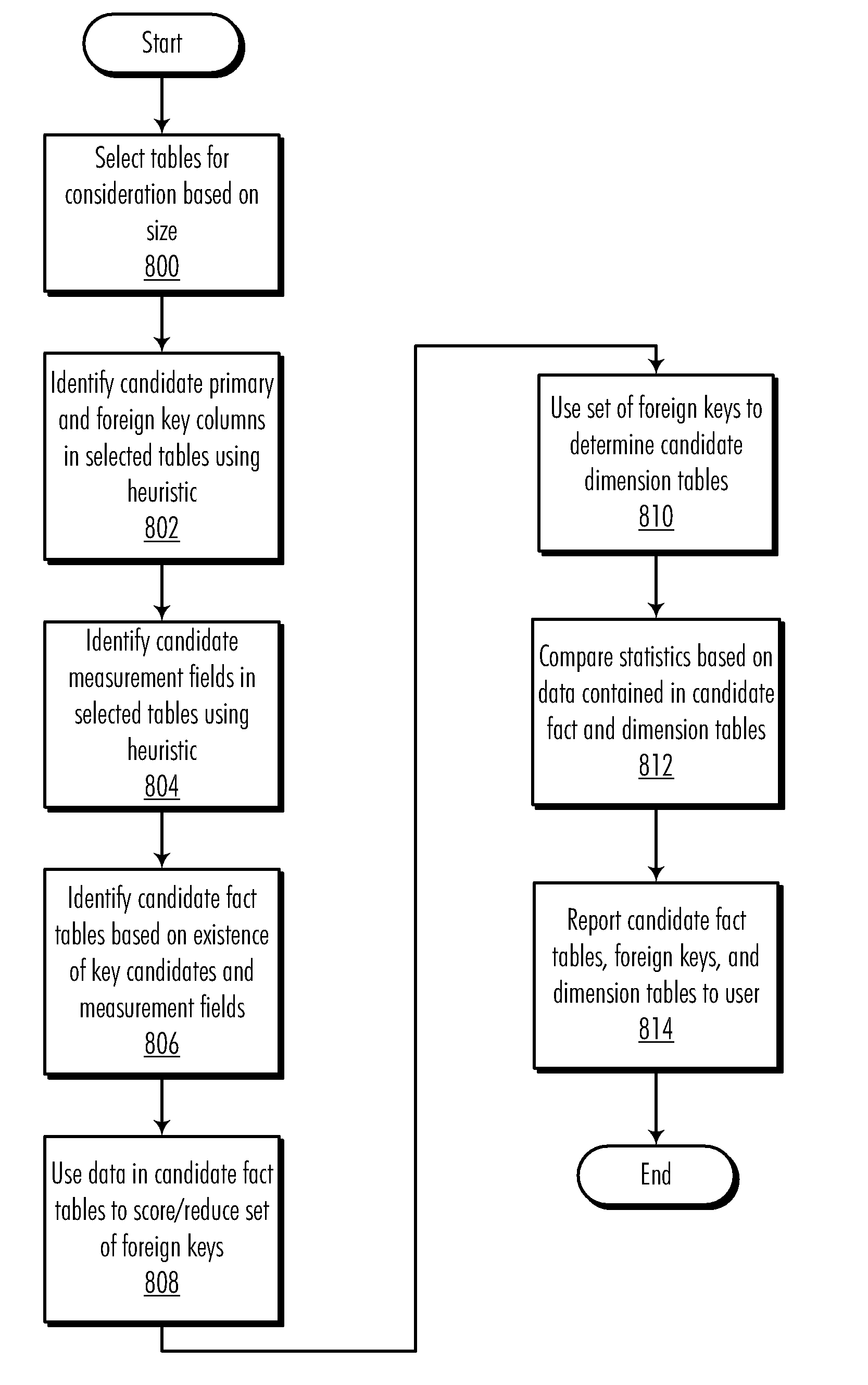
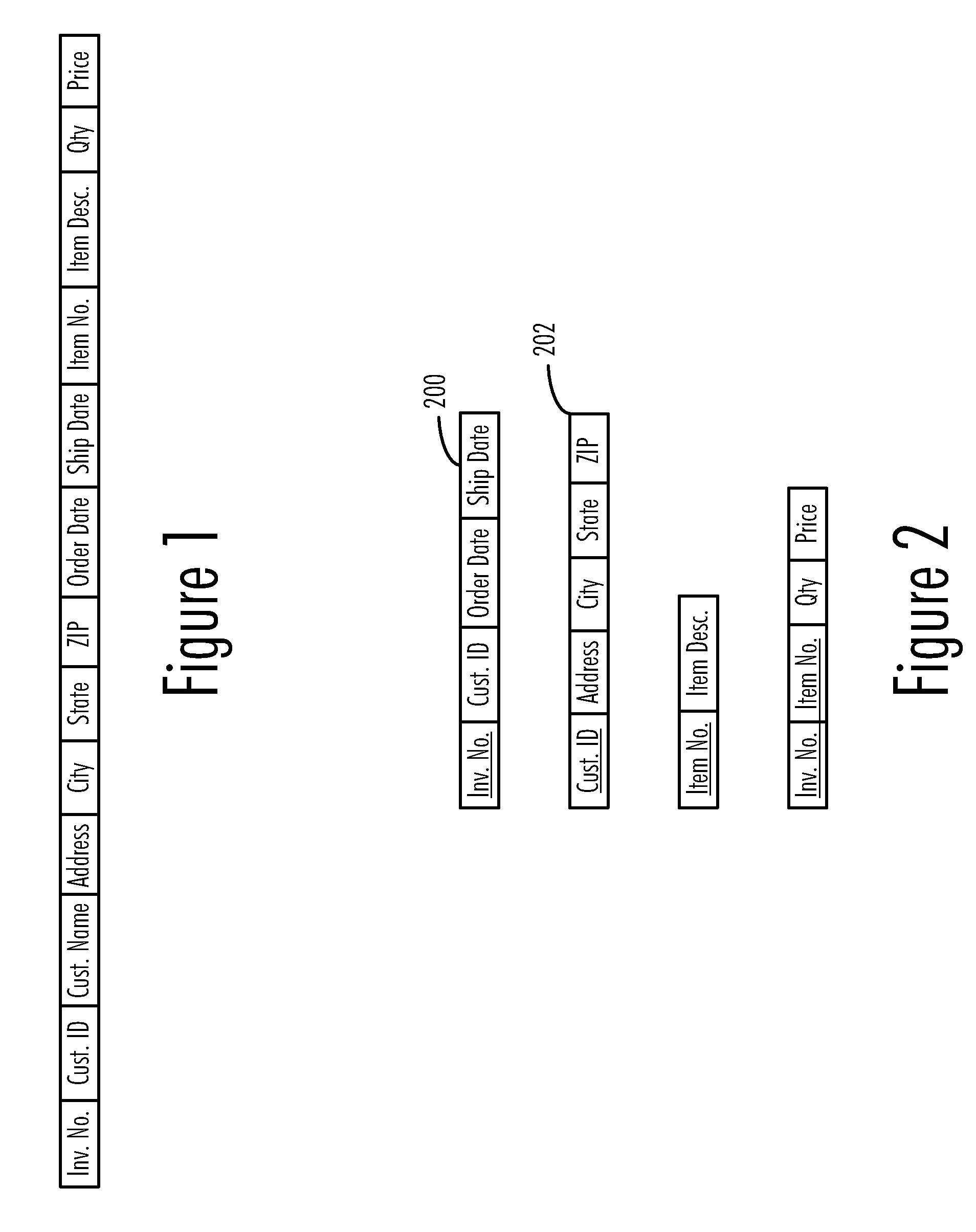
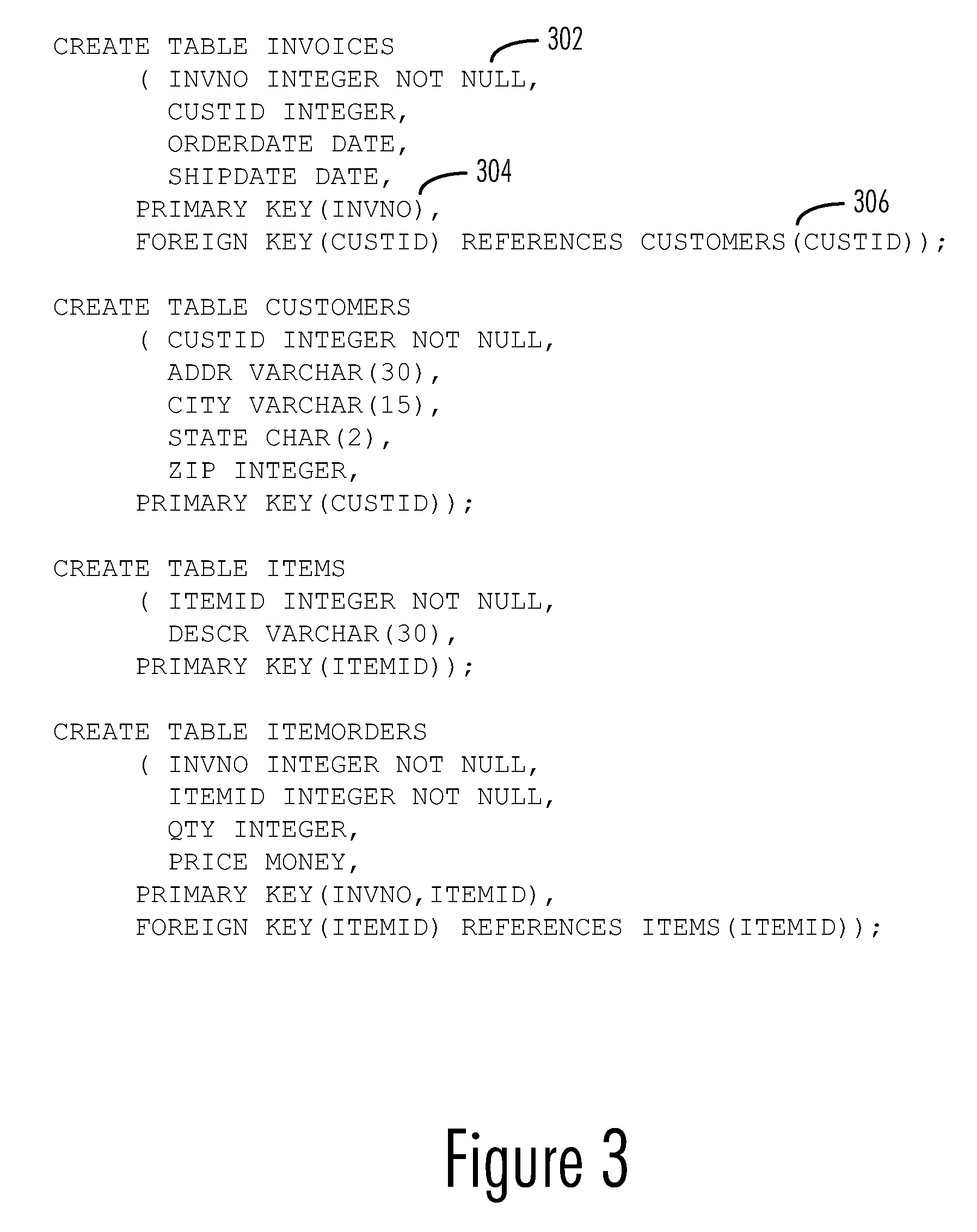
A method, computer program product, and data processing system for computer-aided design of multidimensional data warehouse schemas are disclosed. A preferred embodiment of the present invention provides a software tool for identifying a latent star schema structure within an existing database. This software tool performs a heuristic analysis of the existing database schema to locate potential keys and measurement fields. Database tables within the existing schema are scored heuristically as to their suitability as fact tables based on the key candidates and measurement fields. For each fact table, other tables from the existing schema are identified as possible dimension tables. Data from the database is then used to test the suitability of the fact tables and dimension tables. The identified fact tables and their associated dimension tables are then reported to the user to reveal a basic star schema structure, which can be used as a basis for further design.
Owner:LINKEDIN
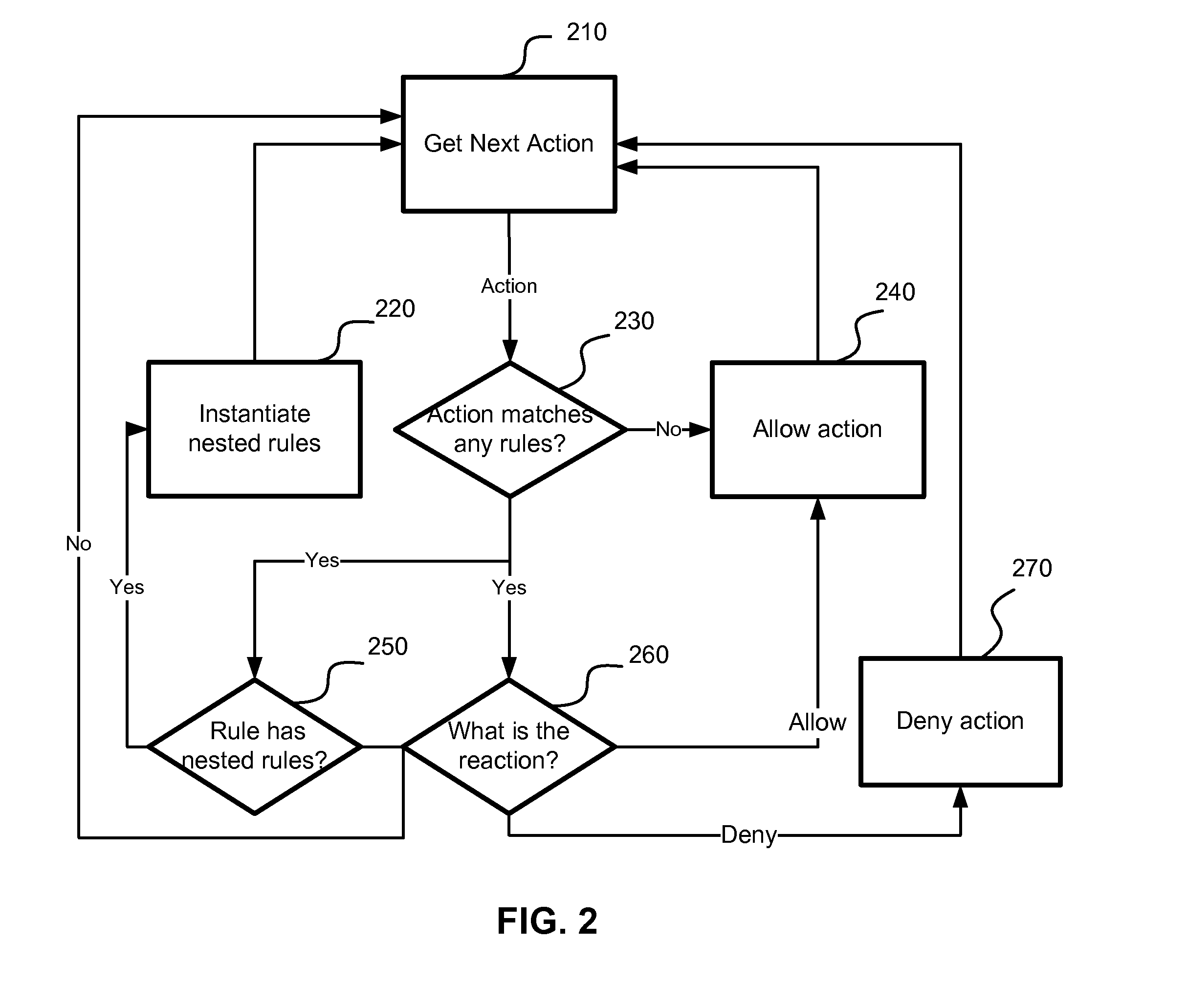
Application of nested behavioral rules for anti-malware processing
InactiveUS8850579B1Save system resourcesLarge actionMemory loss protectionError detection/correctionRequest - actionTheoretical computer science
A system, method and computer program product for implementing dynamic behavior rules for malware detection. A method of heuristic analysis of computer program execution is used. A behavior of a computer program is monitored, analyzed and blocked in runtime. Actions performed or triggered by each executable component are compared against a set of behavioral rules. The behavioral rules determine wherever the requested action is allowed or blocked, and which new behavioral rules are needed to be applied to future actions. Executed actions (allowed or blocked) introduce new dynamic behavioral rules to the computer system, which in turn can apply these rules for analyzing behavior of subsequent components executed on the computer system.
Owner:SAFE N SEC
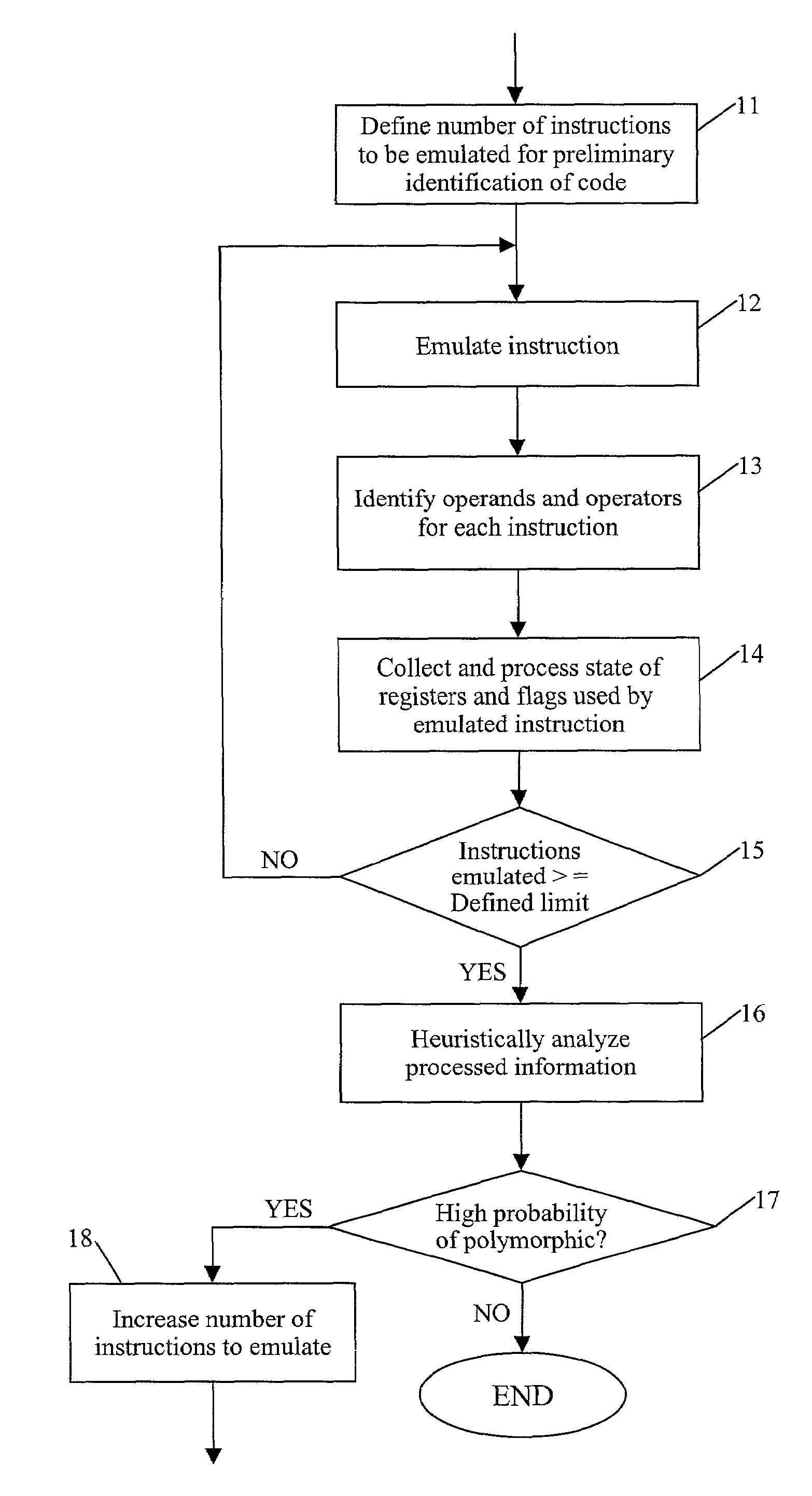
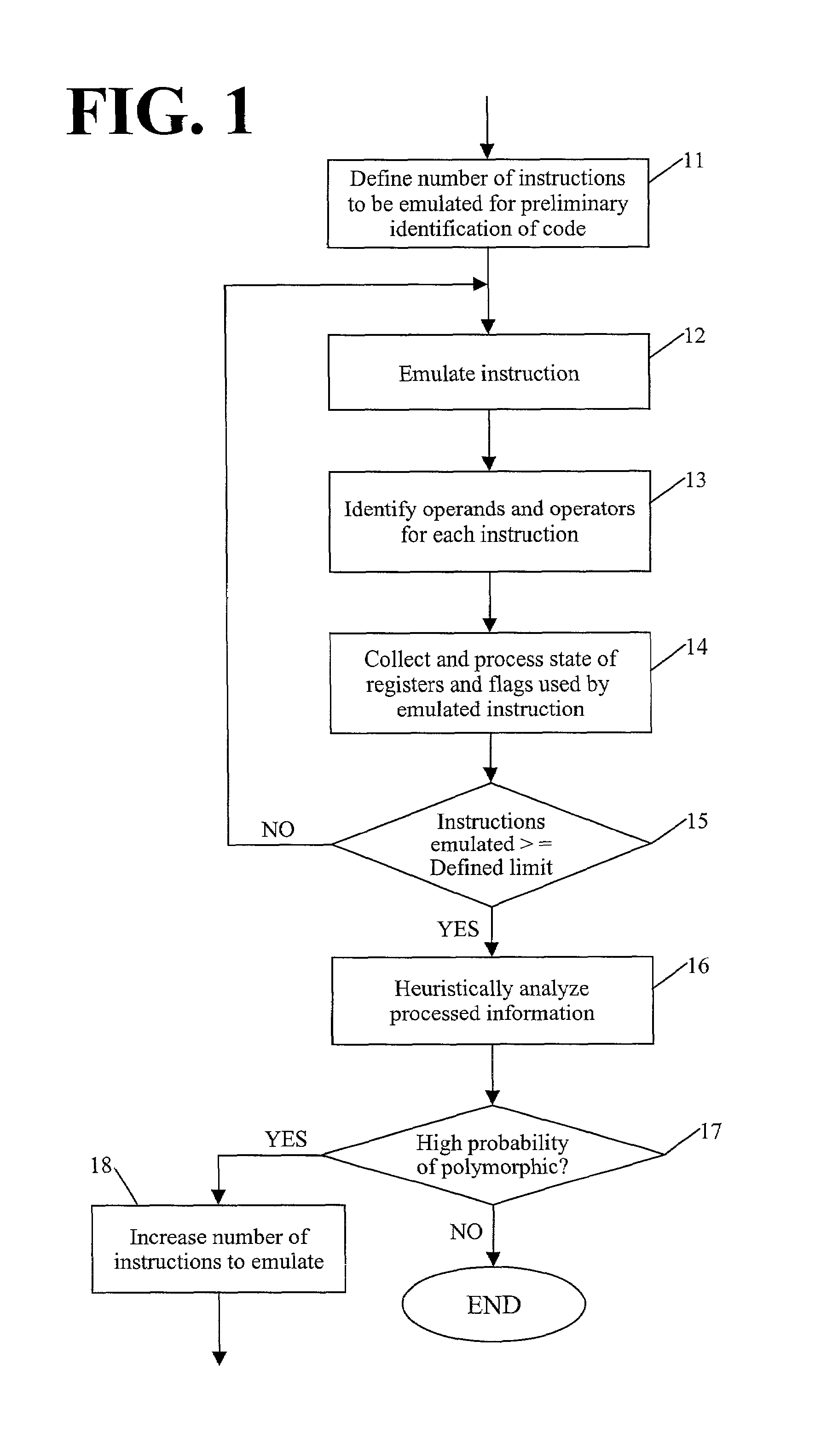
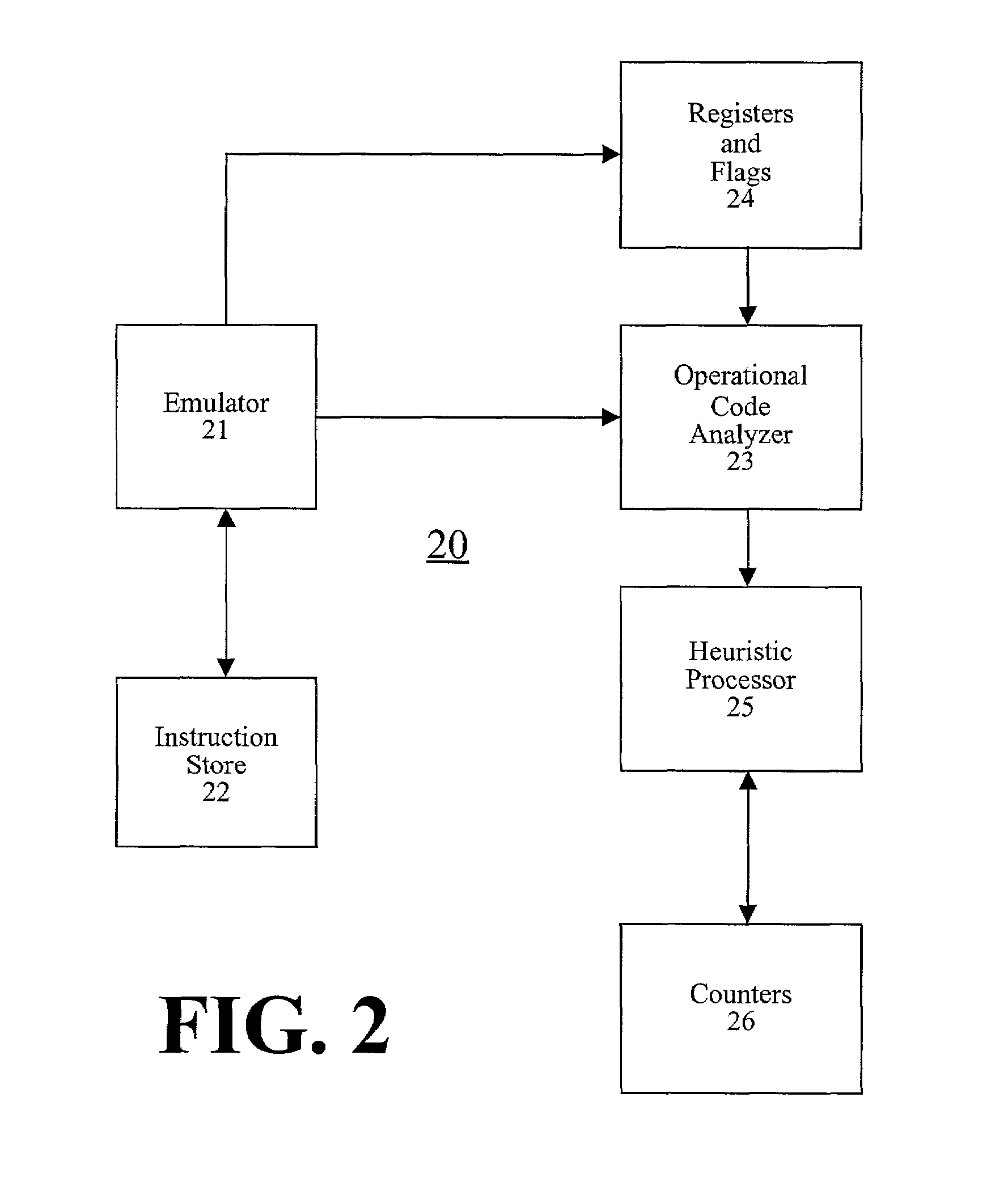
Detection of polymorphic virus code using dataflow analysis
A method and apparatus for detecting polymorphic viral code in a computer program is provided. The apparatus comprises an emulator, an operational code analyzer and an heuristic analyzer. The emulator emulates a selected number of instructions of the computer program. The operational code analyzer collects and stores information corresponding to operands and operators used in the instructions and the state of registers / flags after each emulated instruction execution. The heuristic analyzer determines a probability that the computer program contains viral code based on an heuristic analysis of register / flag state information supplied by the operational code analyzer.
Owner:COMP ASSOC THINK INC
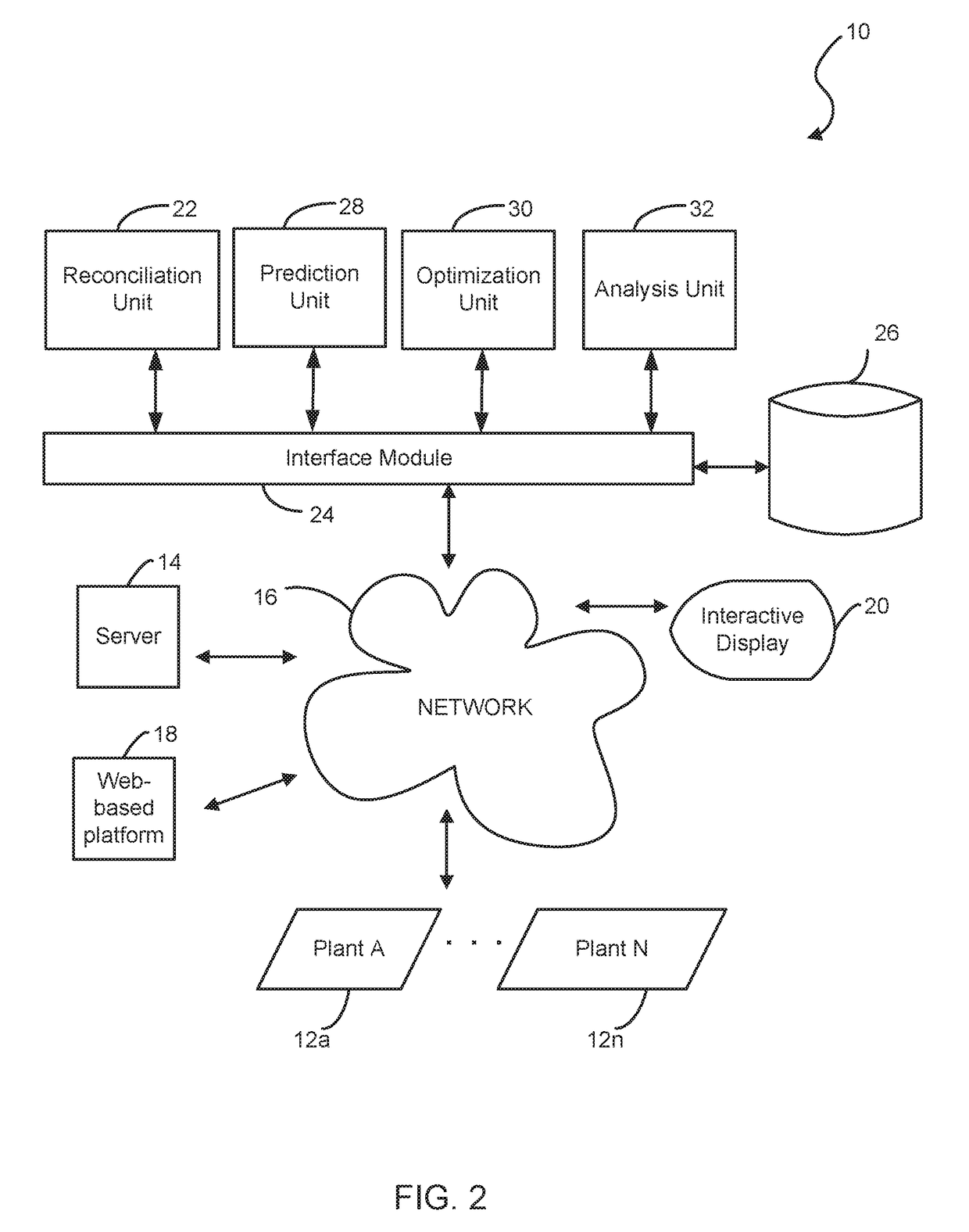
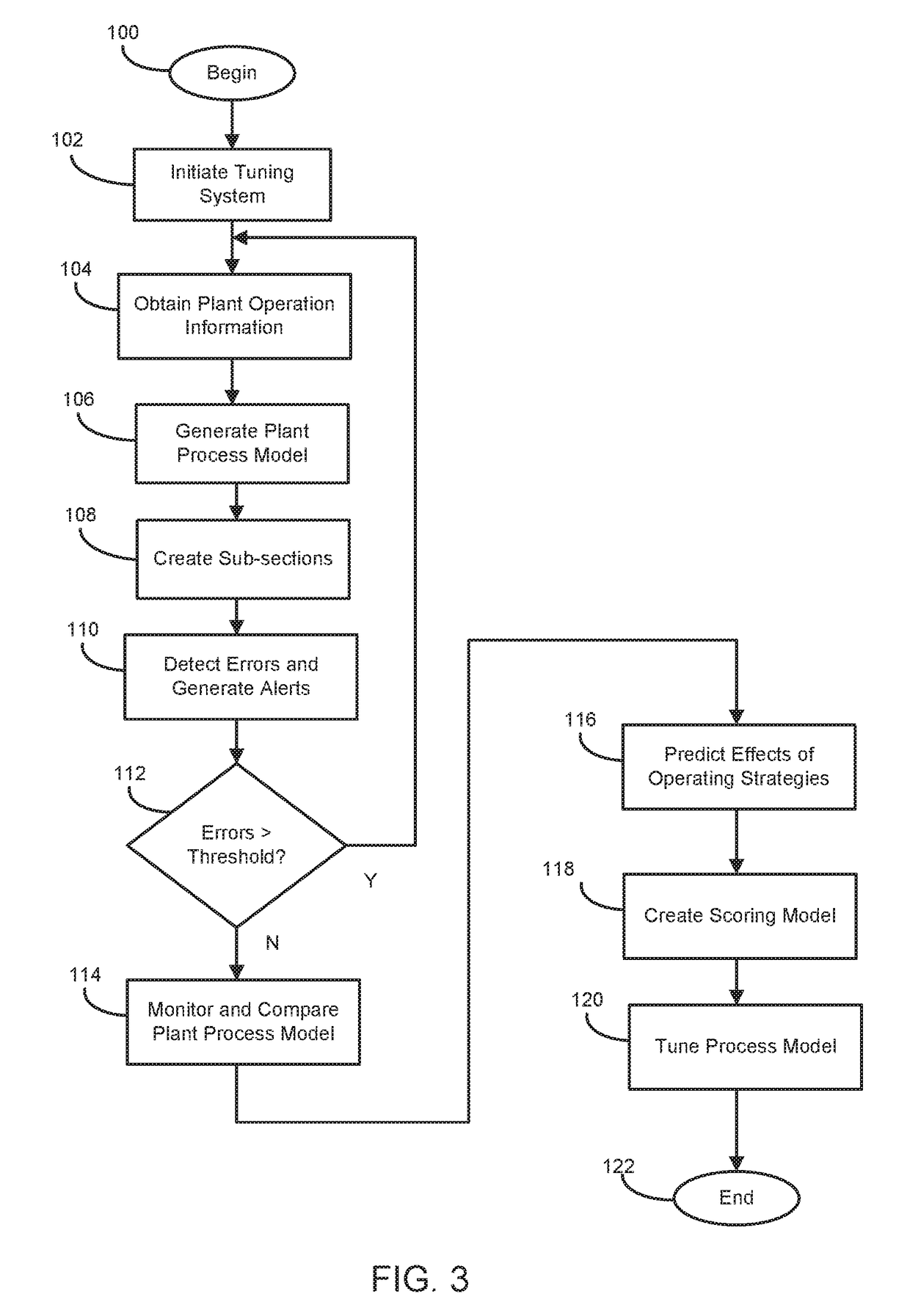
System and method for tuning process models
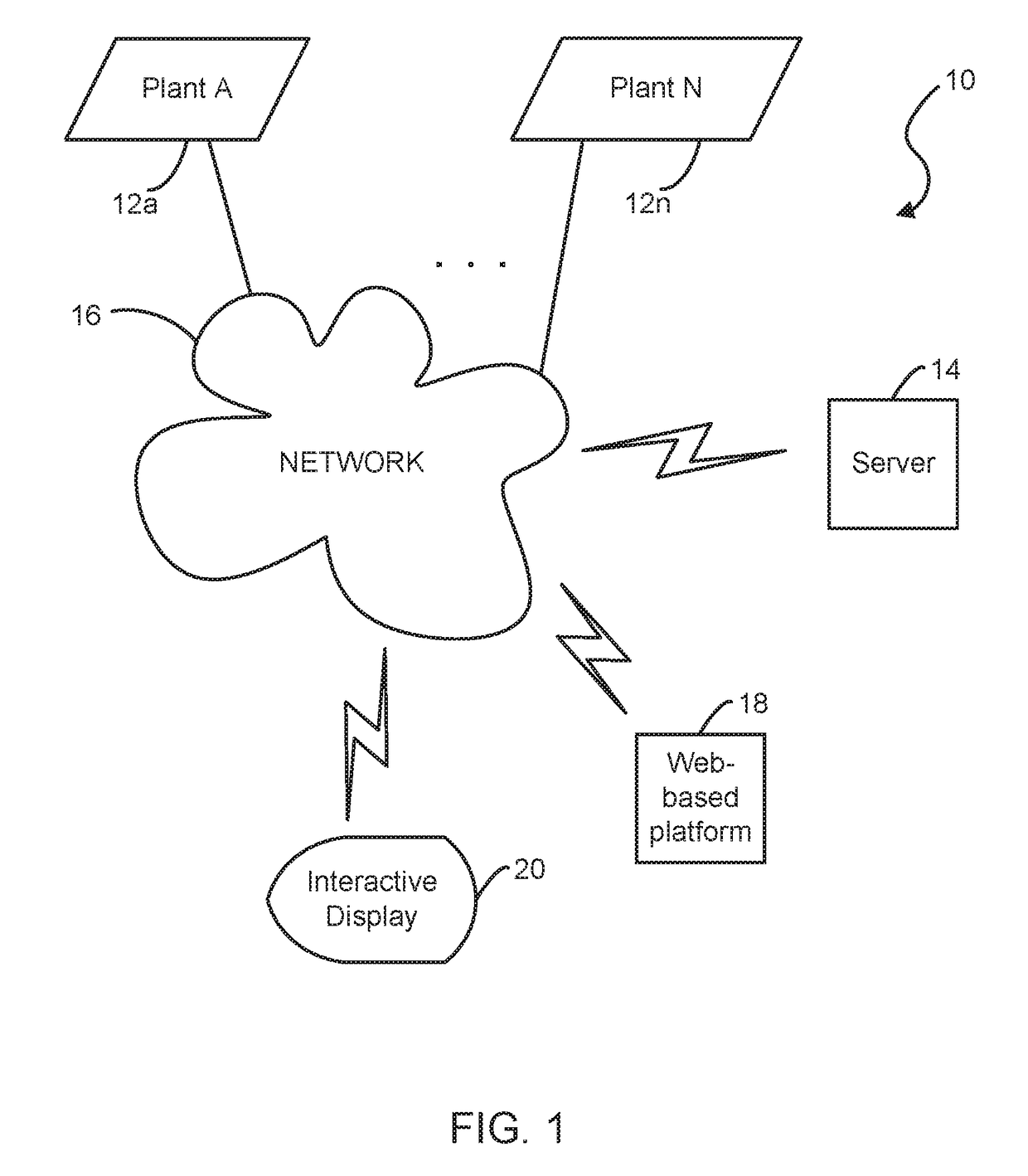
ActiveUS20160291584A1Bridging the gapMaximum process performanceDigital computer detailsTotal factory controlDisplay deviceComputerized system
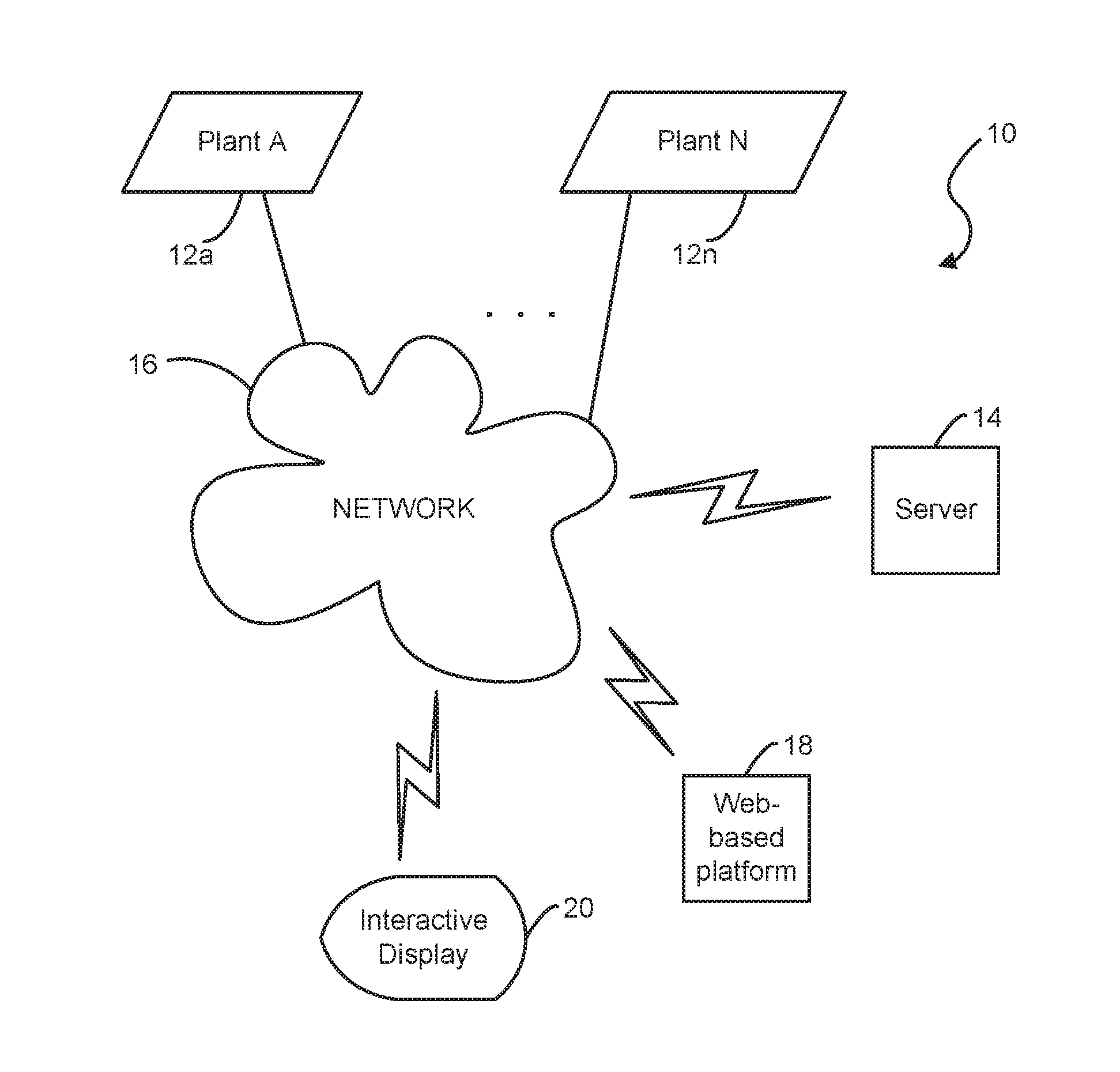
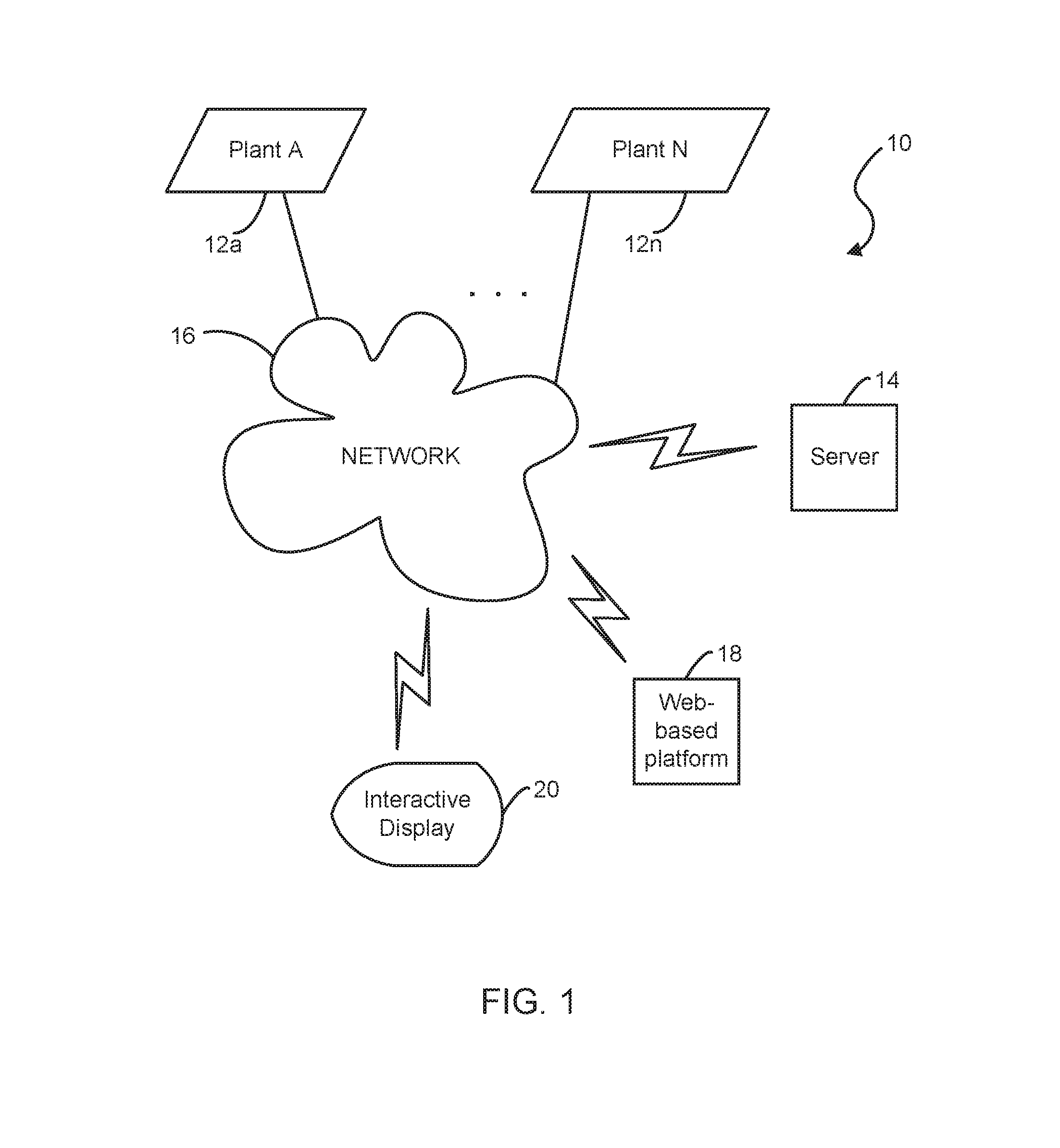
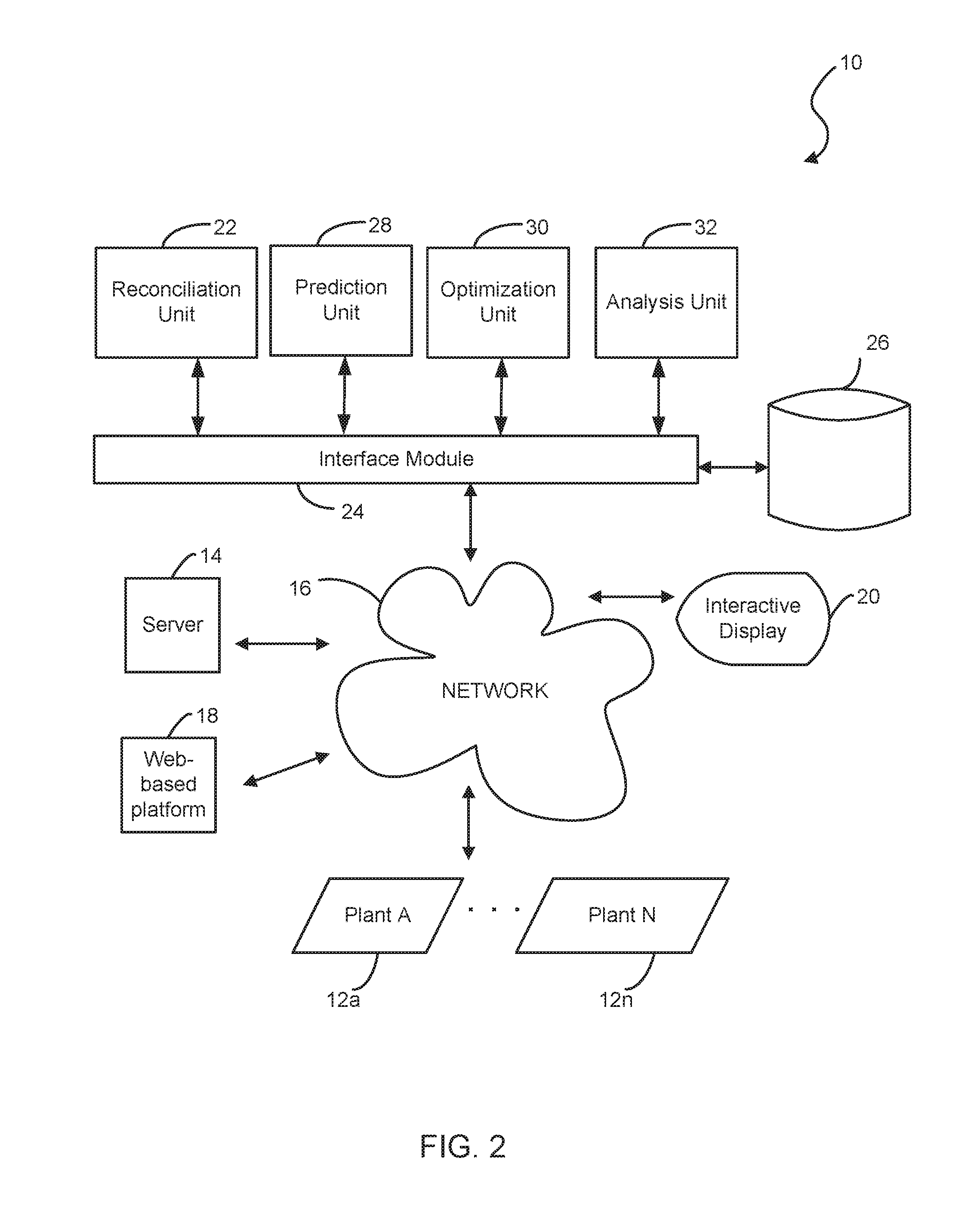
A tuning system for improving operation of a plant. A server is coupled to the tuning system for communicating with the plant via a communication network. A computer system has a web-based platform for receiving and sending plant data related to the operation of the plant over the network. A display device interactively displays the plant data. A reconciliation unit is configured for reconciling actual measured data from the plant in comparison with a performance process model result from a simulation engine based on a set of predetermined reference or set points. The reconciliation unit performs a heuristic analysis against the actual measured data and the performance process model result using a set of predetermined threshold values.
Owner:UOP LLC
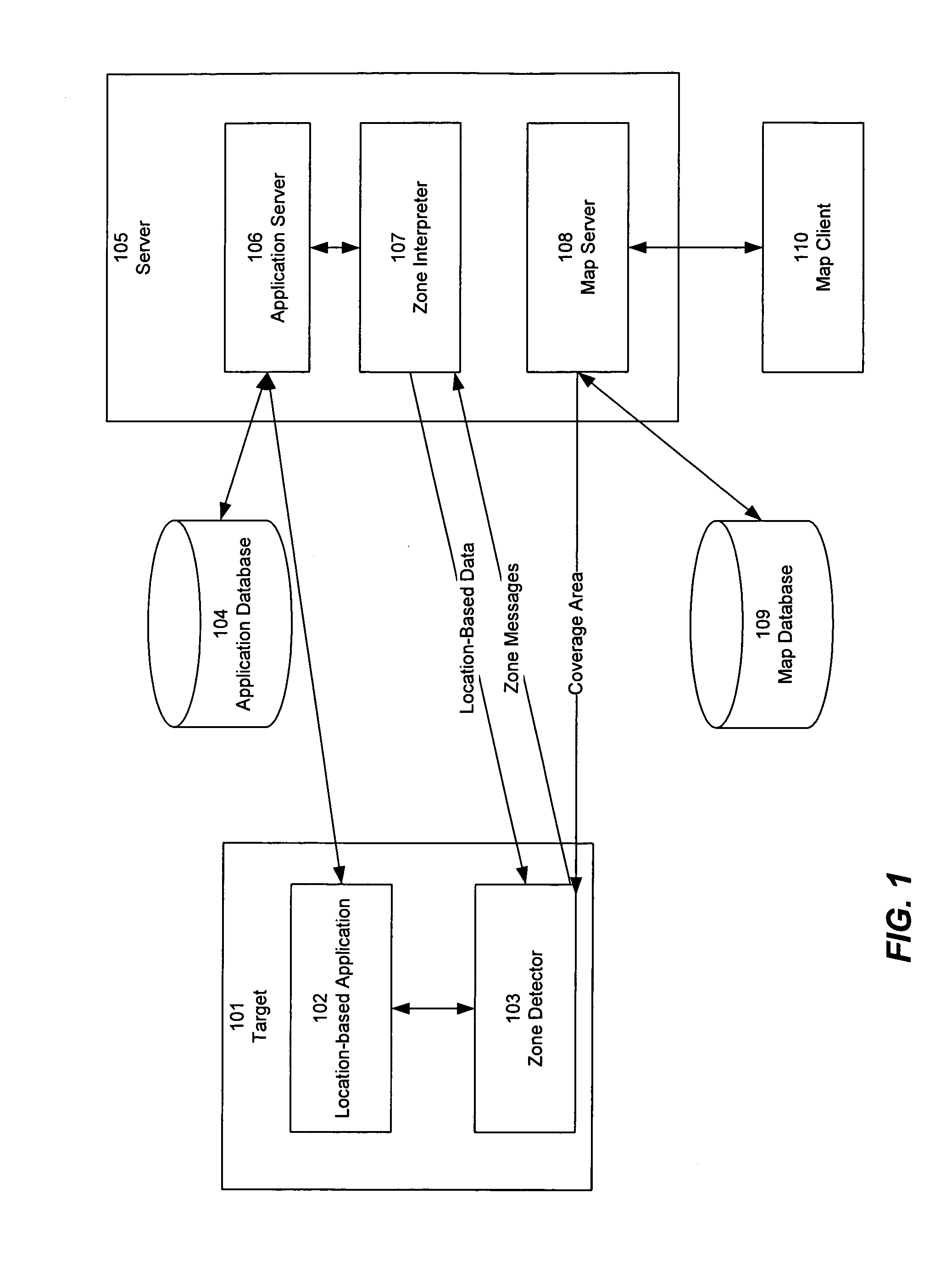
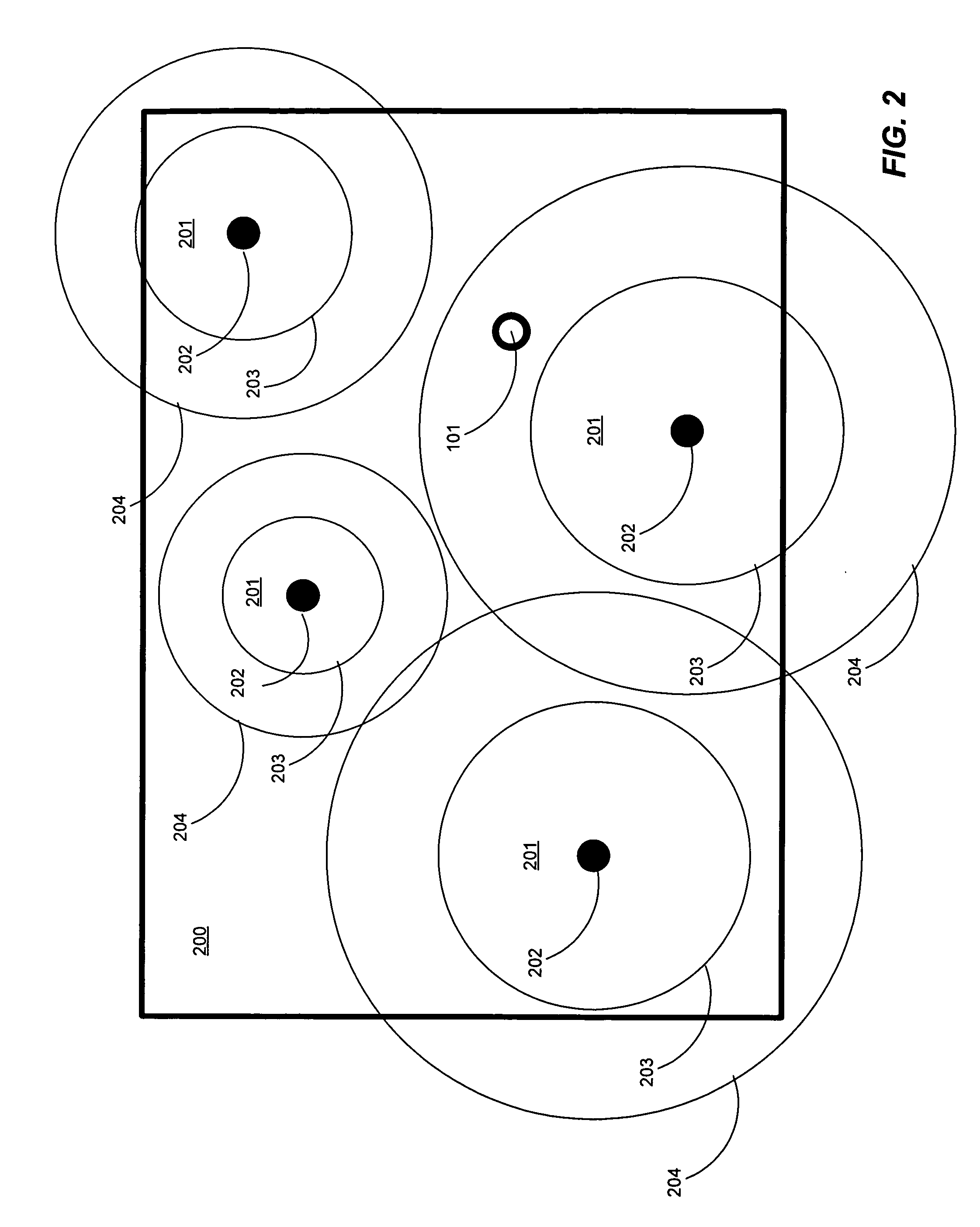
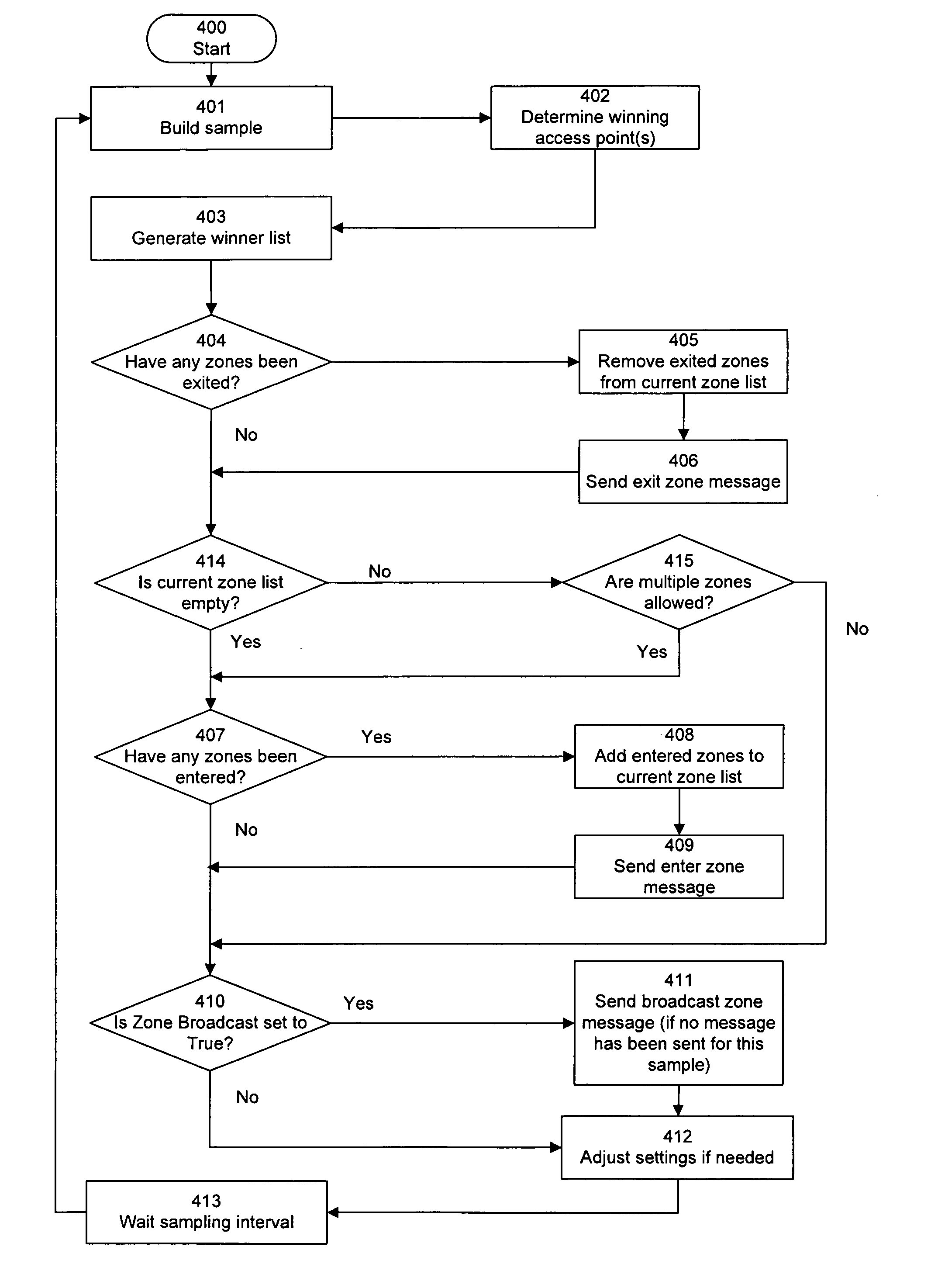
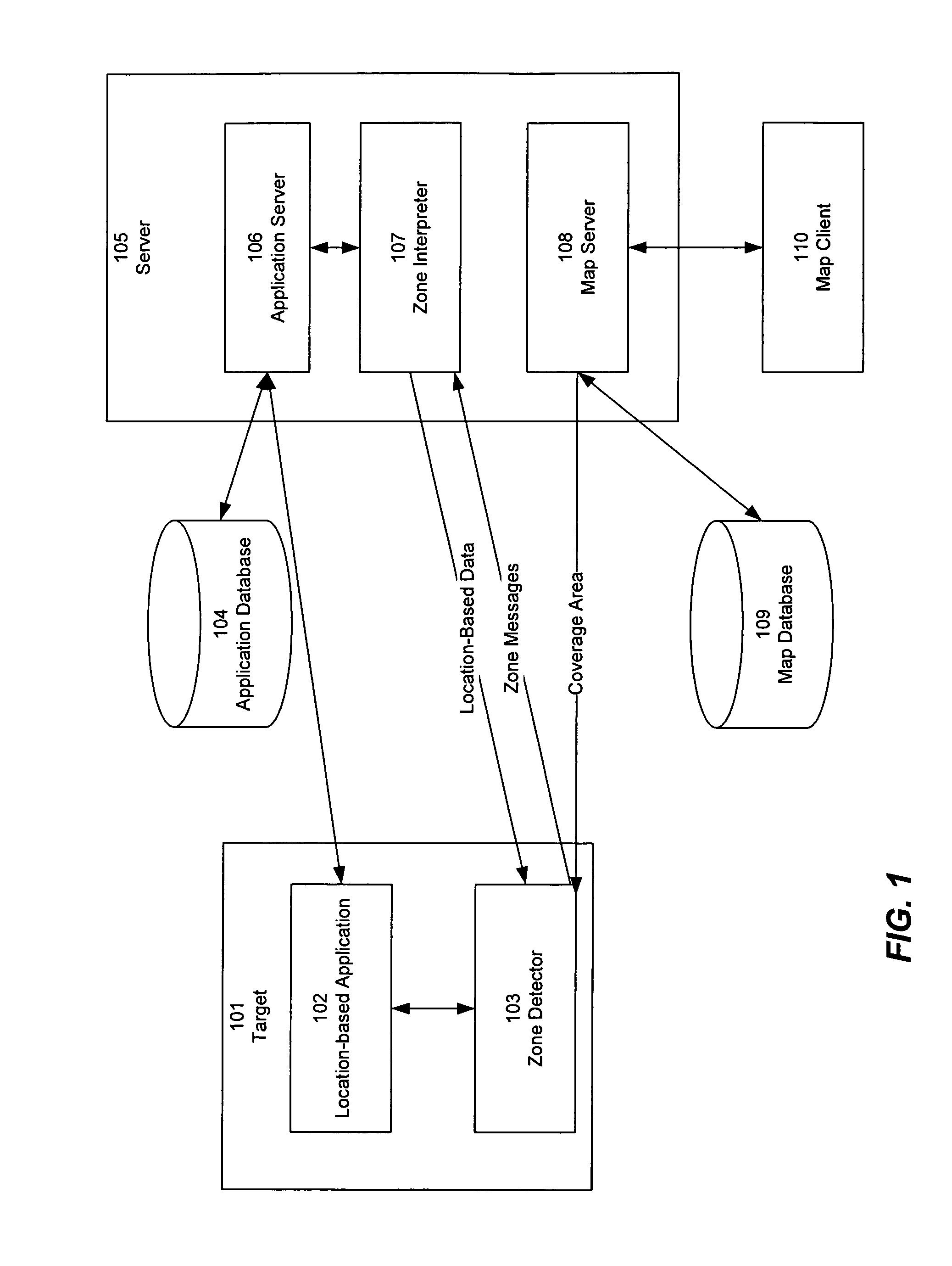
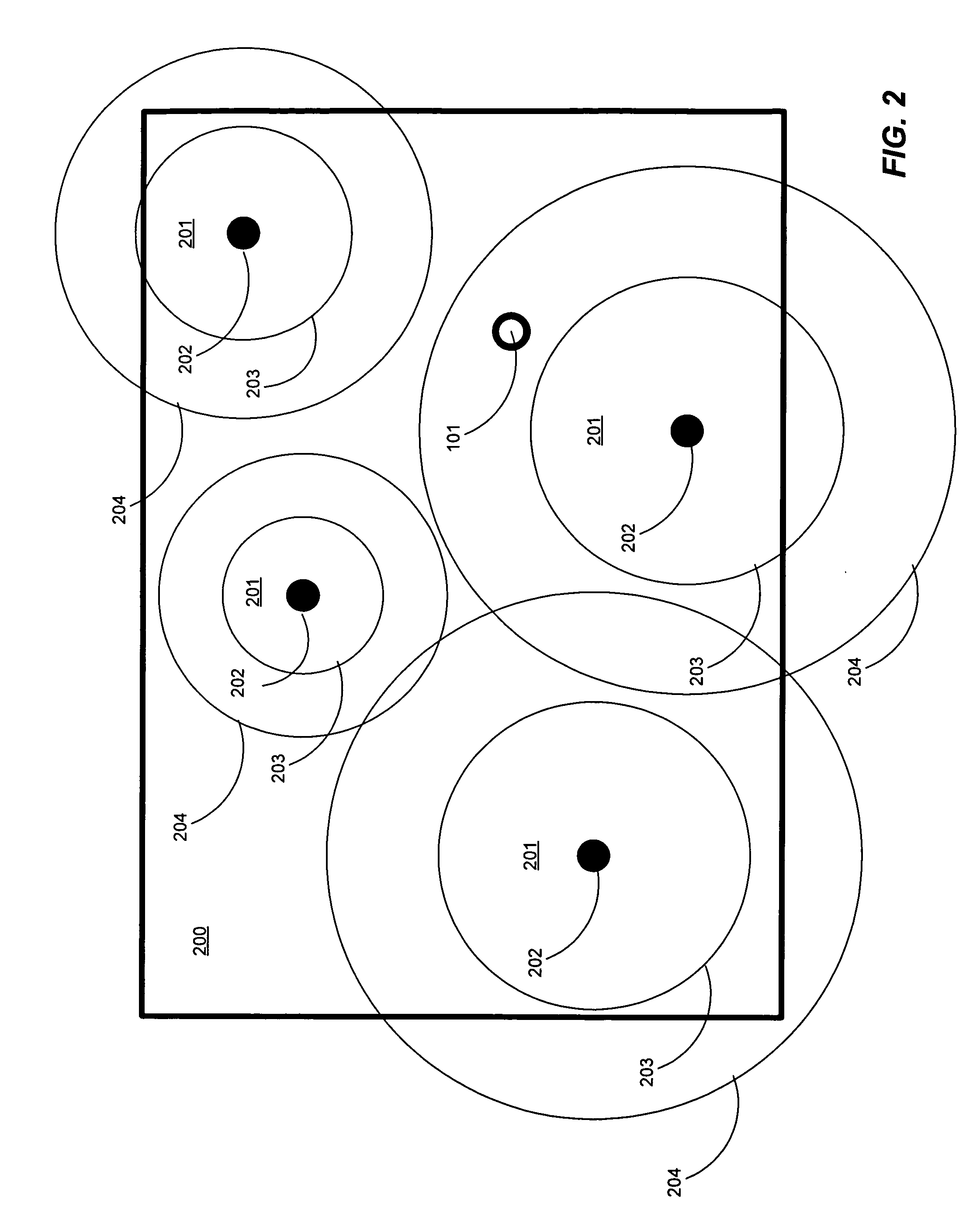
Configurable zone-based location detection
InactiveUS20080225810A1Reduce morbidityStrong configurabilityError preventionFrequency-division multiplex detailsWi-FiLocation detection
An improved technique provides location detection using wireless net-works such as Wi-Fi networks in a flexible, configurable manner that allows for variations in the environment and tracks target movement accurately in such an environment. Zones of different relative sizes and sensitivities can be defined, so as to vary the degree of resolution for different parts of the area being detected. Mechanisms are provided to take into account fluctuations in signal strength, and reduce the incidence of false positives resulting from incorrectly detecting zone or location changes due to fluctuations of signal strength. In addition, detection time can be configured for zone entry and / or exit. Self-adjustment based on heuristic analysis can also be implemented. Data can be sent or received based on the physical location as determined by the zone.
Owner:BUCHWALD JON
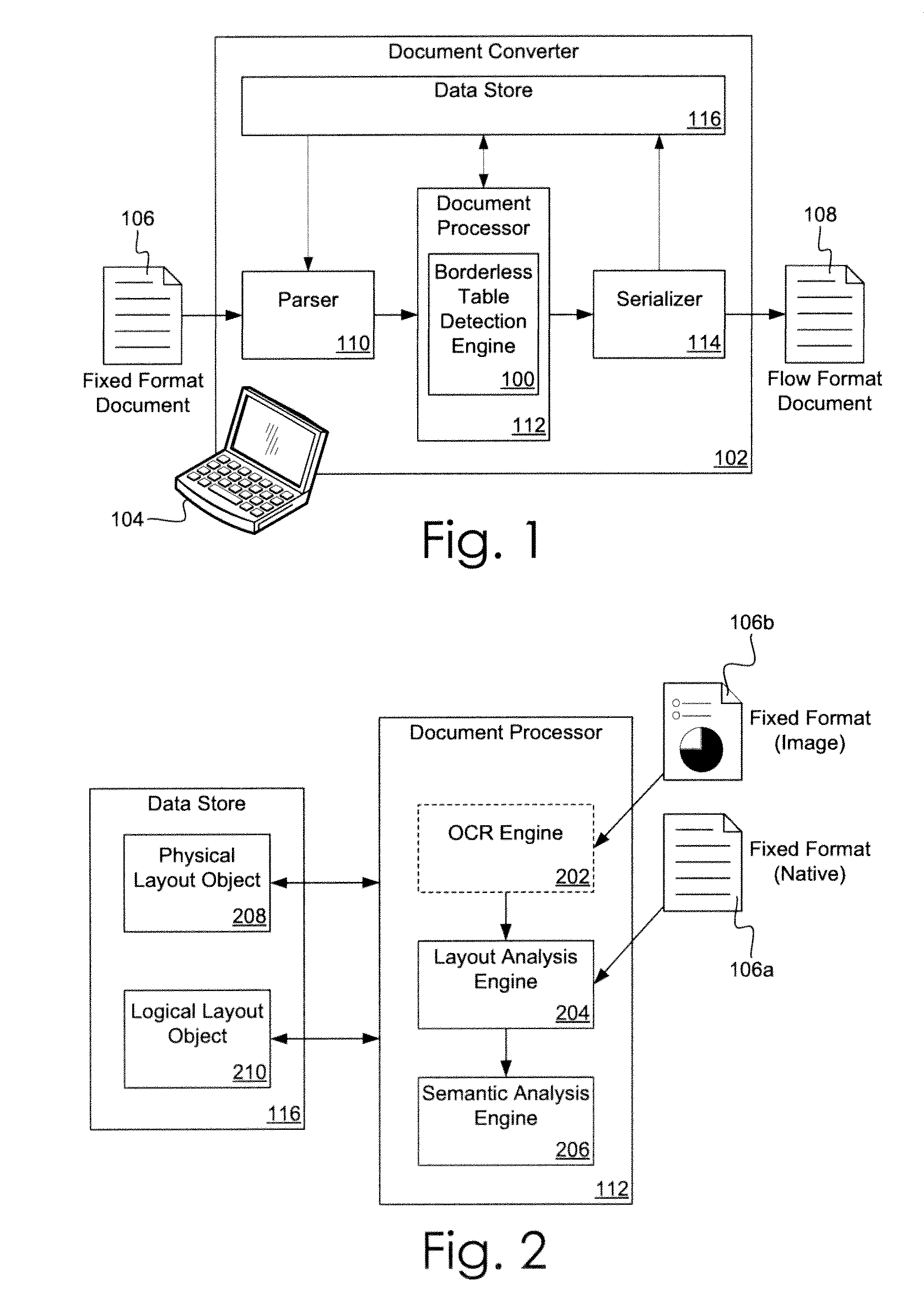
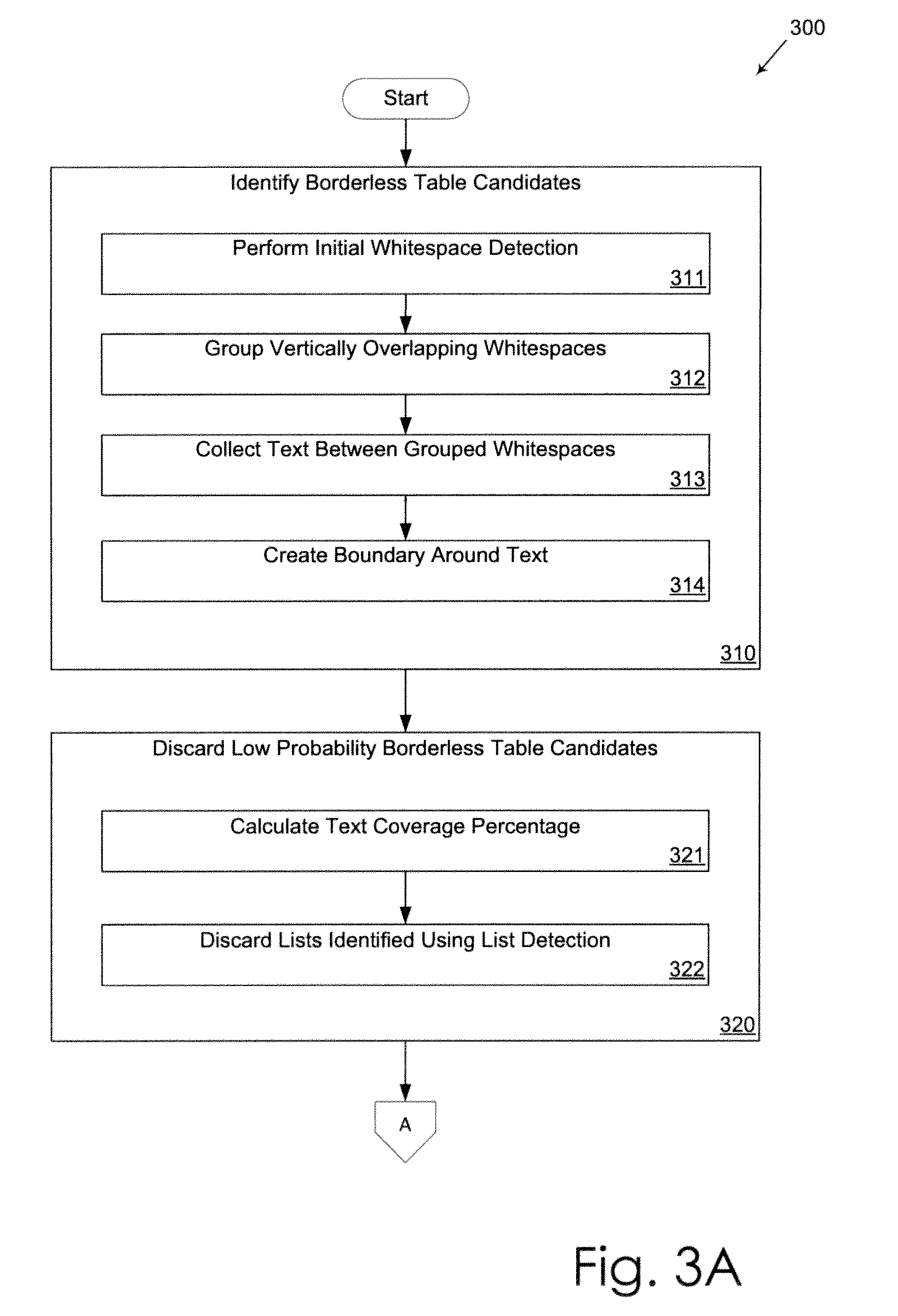
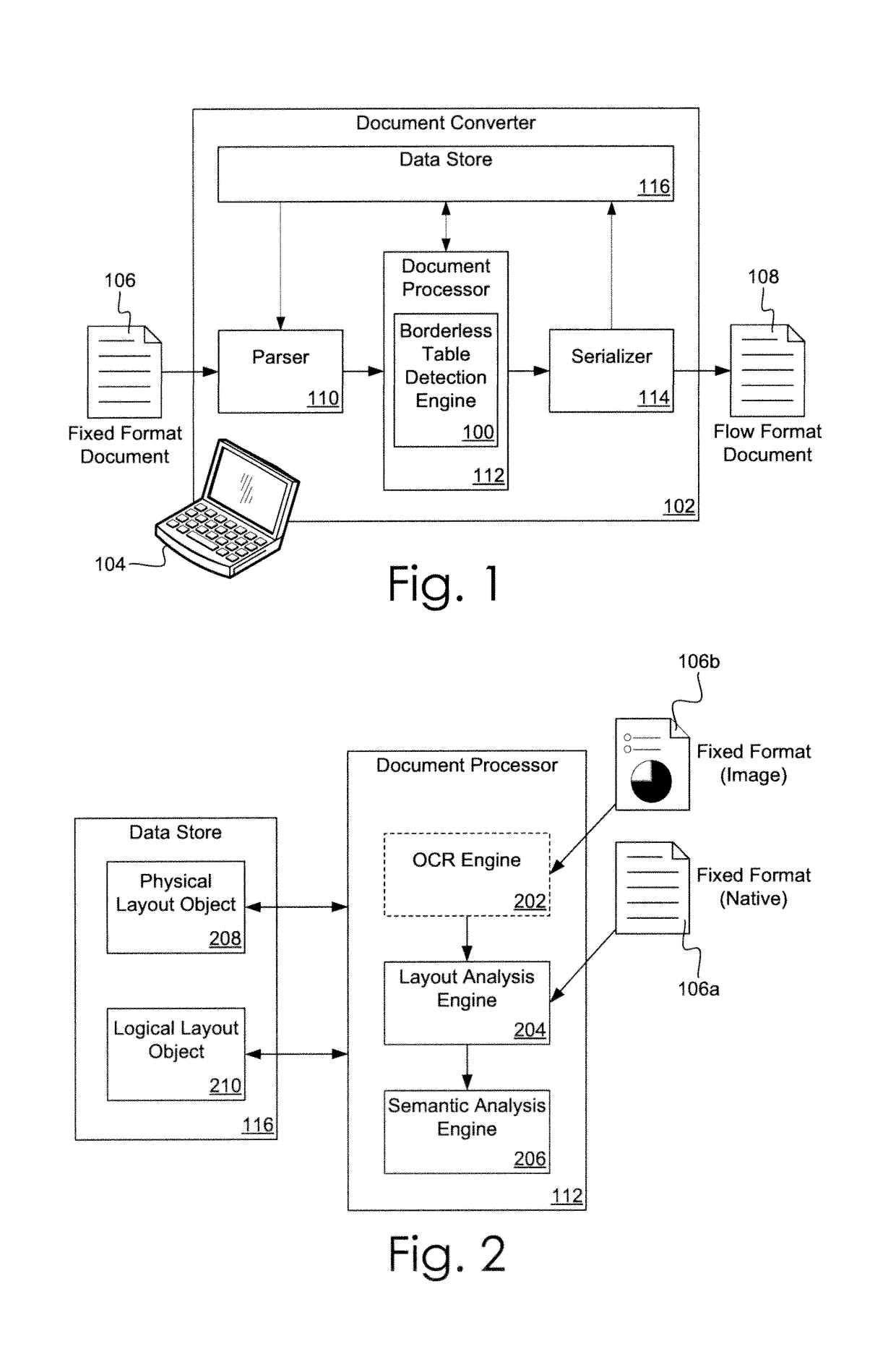
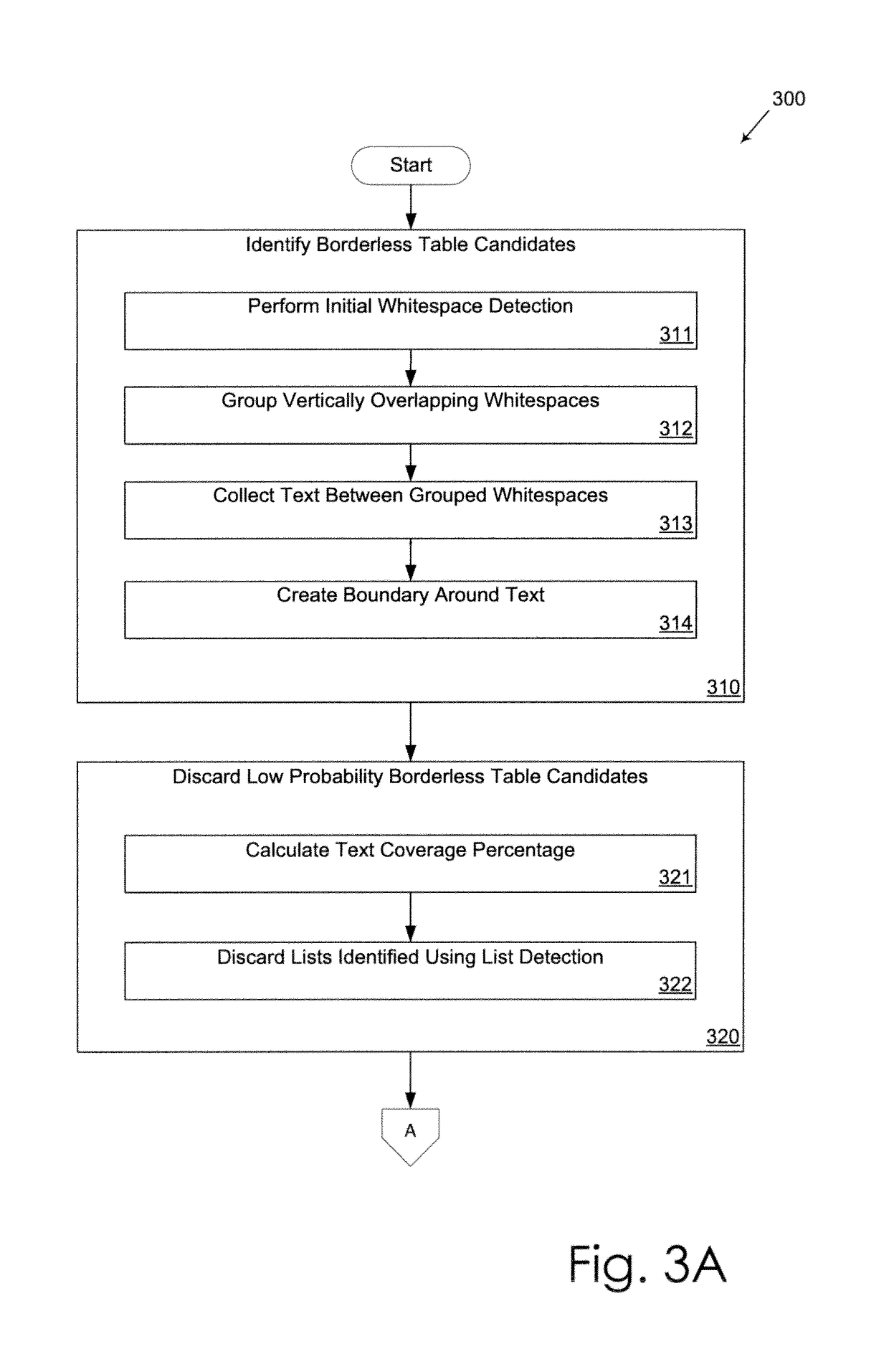
Borderless Table Detection Engine
ActiveUS20130191715A1Small widthNatural language data processingSpecial data processing applicationsDocumentationHeuristic analysis
A borderless table detection engine and associated method for identifying borderless tables appearing in data extracted from a fixed format document. Due to the lack of visible borders, reliable automated detection of a borderless table is difficult. The borderless table detection engine uses whitespace, rather than content, to detect borderless table candidates. Applying heuristic analysis, the borderless table detection engine discards borderless table candidates with a layout that lacks sufficient characteristics of a table and is unlikely to be a valid borderless table.
Owner:MICROSOFT TECH LICENSING LLC
System and method for heuristic analysis to identify pestware
Systems for preventing pestware activity are described. One embodiment a heuristic engine configured to identify repeat pestware activity and configured to block the repeat pestware activity; an operating system pestware shield in communication with the heuristic engine, the operating system pestware shield configured to detect pestware activity and report the pestware activity to the heuristic engine; and a browser pestware shield in communication with the heuristic engine, the browser pestware shield configured to detect pestware activity and report the pestware activity to the heuristic engine.
Owner:OPEN TEXT CORPORATION
Automated Latent Star Schema Discovery Tool
InactiveUS20090265335A1Multi-dimensional databasesSpecial data processing applicationsData processing systemStar schema
A method, computer program product, and data processing system for computer-aided design of multidimensional data warehouse schemas are disclosed. A preferred embodiment of the present invention provides a software tool for identifying a latent star schema structure within an existing database. This software tool performs a heuristic analysis of the existing database schema to locate potential keys and measurement fields. Database tables within the existing schema are scored heuristically as to their suitability as fact tables based on the key candidates and measurement fields. For each fact table, other tables from the existing schema are identified as possible dimension tables. Data from the database is then used to test the suitability of the fact tables and dimension tables. The identified fact tables and their associated dimension tables are then reported to the user to reveal a basic star schema structure, which can be used as a basis for further design.
Owner:LINKEDIN
Tuning system and method for improving operation of a chemical plant with a furnace
ActiveUS10180680B2Operation efficiency can be improvedEasy to operateDigital computer detailsTotal factory controlDisplay deviceComputerized system
A tuning system for improving operation of a plant. A server is coupled to the tuning system for communicating with the plant via a communication network. A computer system has a web-based platform for receiving and sending plant data related to the operation of the plant over the network. A display device interactively displays the plant data. A reconciliation unit is configured for reconciling actual measured data from the plant in comparison with a performance process model result from a simulation engine based on a set of predetermined reference or set points. The reconciliation unit performs a heuristic analysis against the actual measured data and the performance process model result using a set of predetermined threshold values.
Owner:UOP LLC
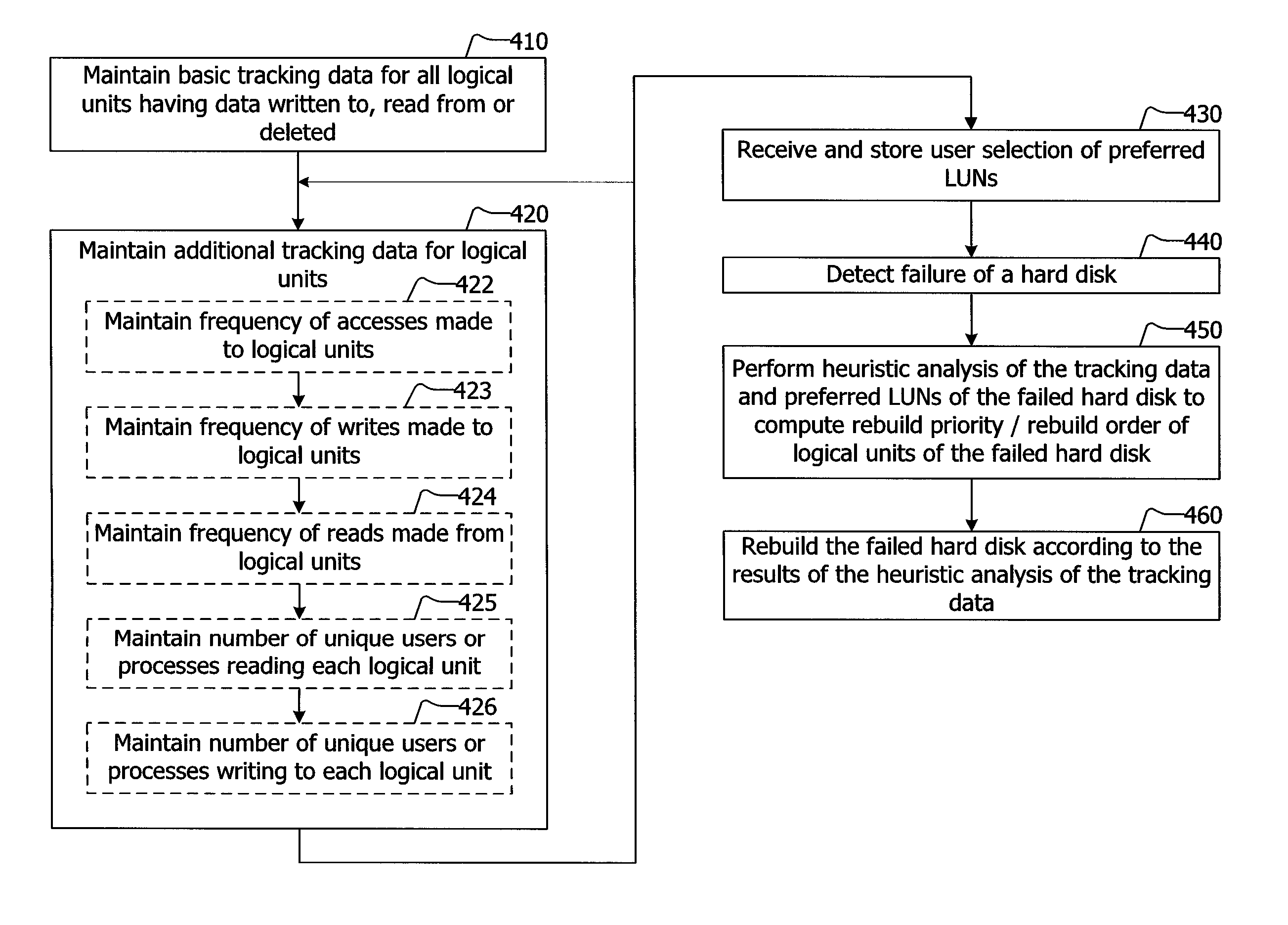
Prioritized Rebuilding of a Storage Device
Rebuilding a storage device after failure of a storage device is disclosed. The method is particularly useful for RAID groups of hard disks. The method may also apply to other storage media arranged as a group. The method includes rebuilding a hard disk in a non-linear fashion according to a heuristic analysis of logical units of the failed hard disk. The method may be implemented in hardware, firmware, software, or a combination thereof.
Owner:DATADIRECT NETWORKS
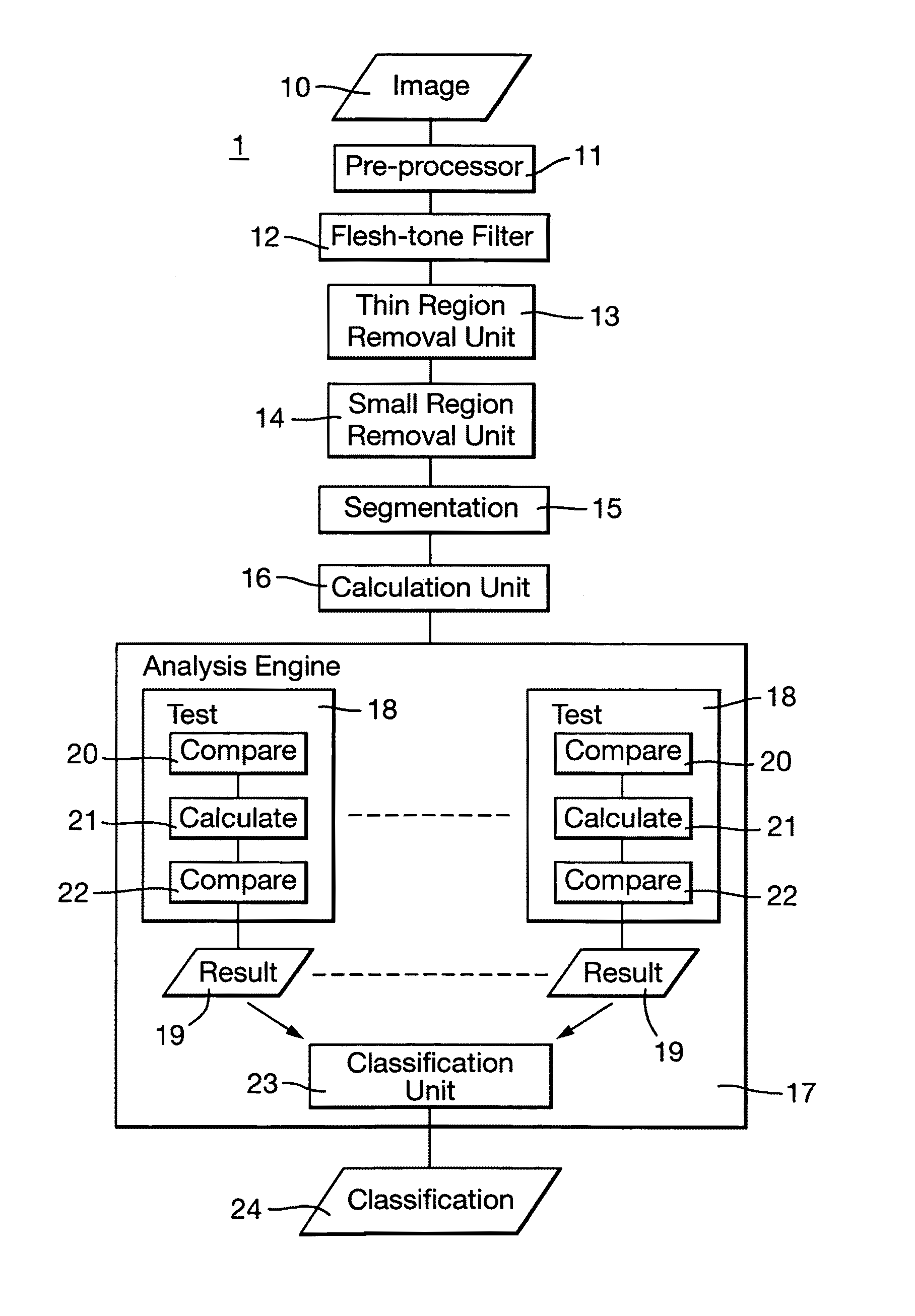
Scanning images for pornography
ActiveUS20090123064A1Improve abilitiesImprove performanceBiometric pattern recognitionSkin colorComputer science
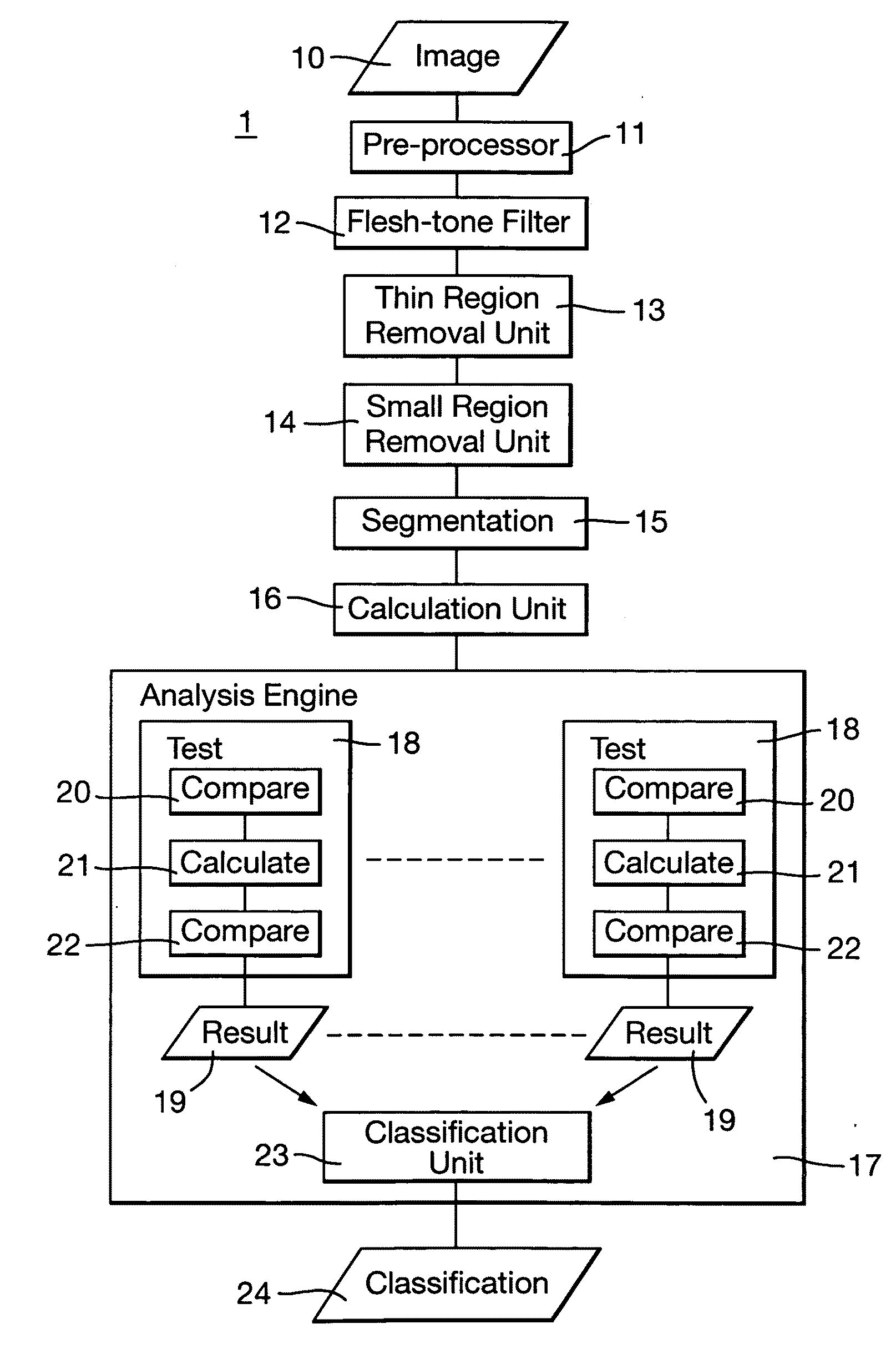
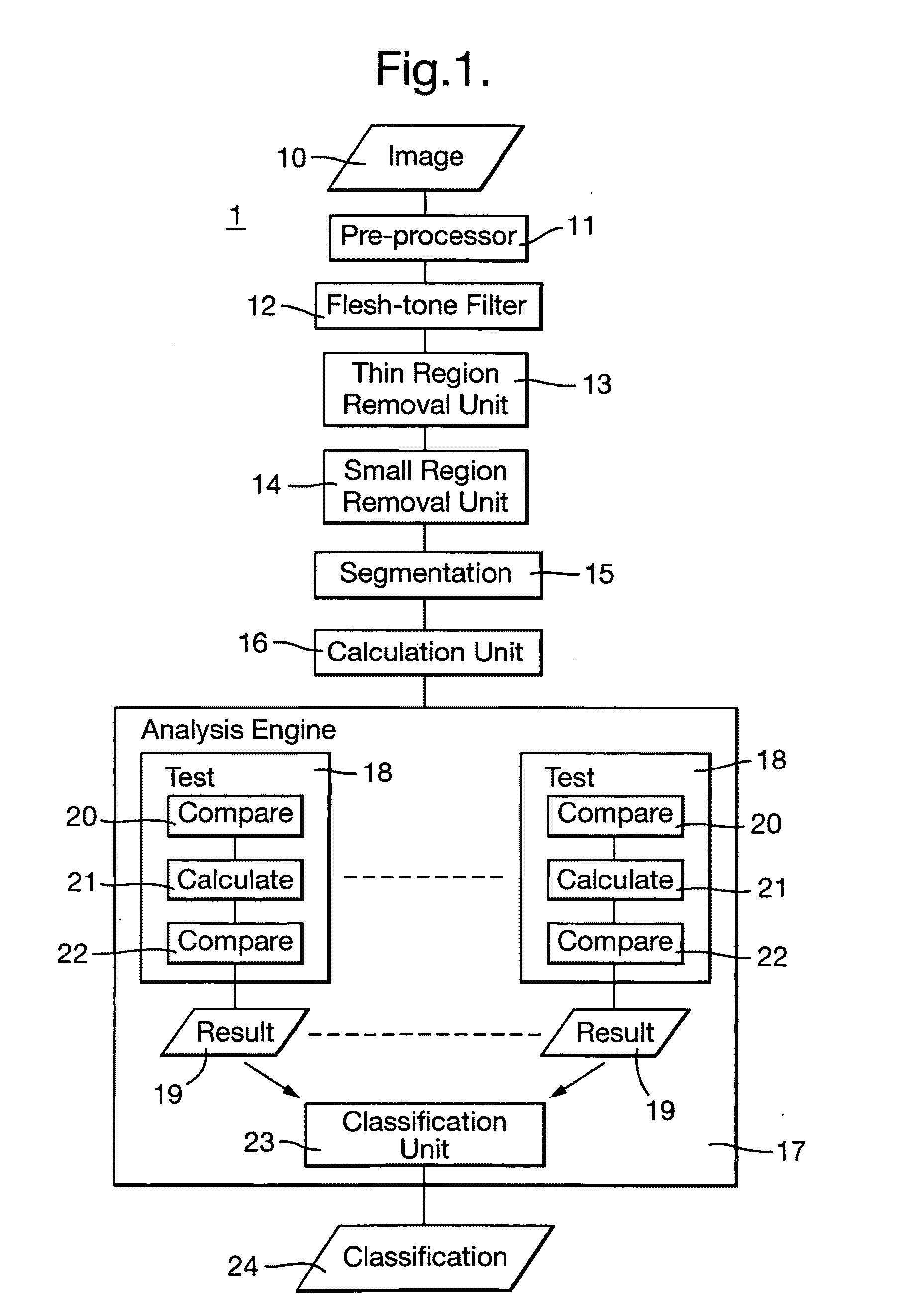
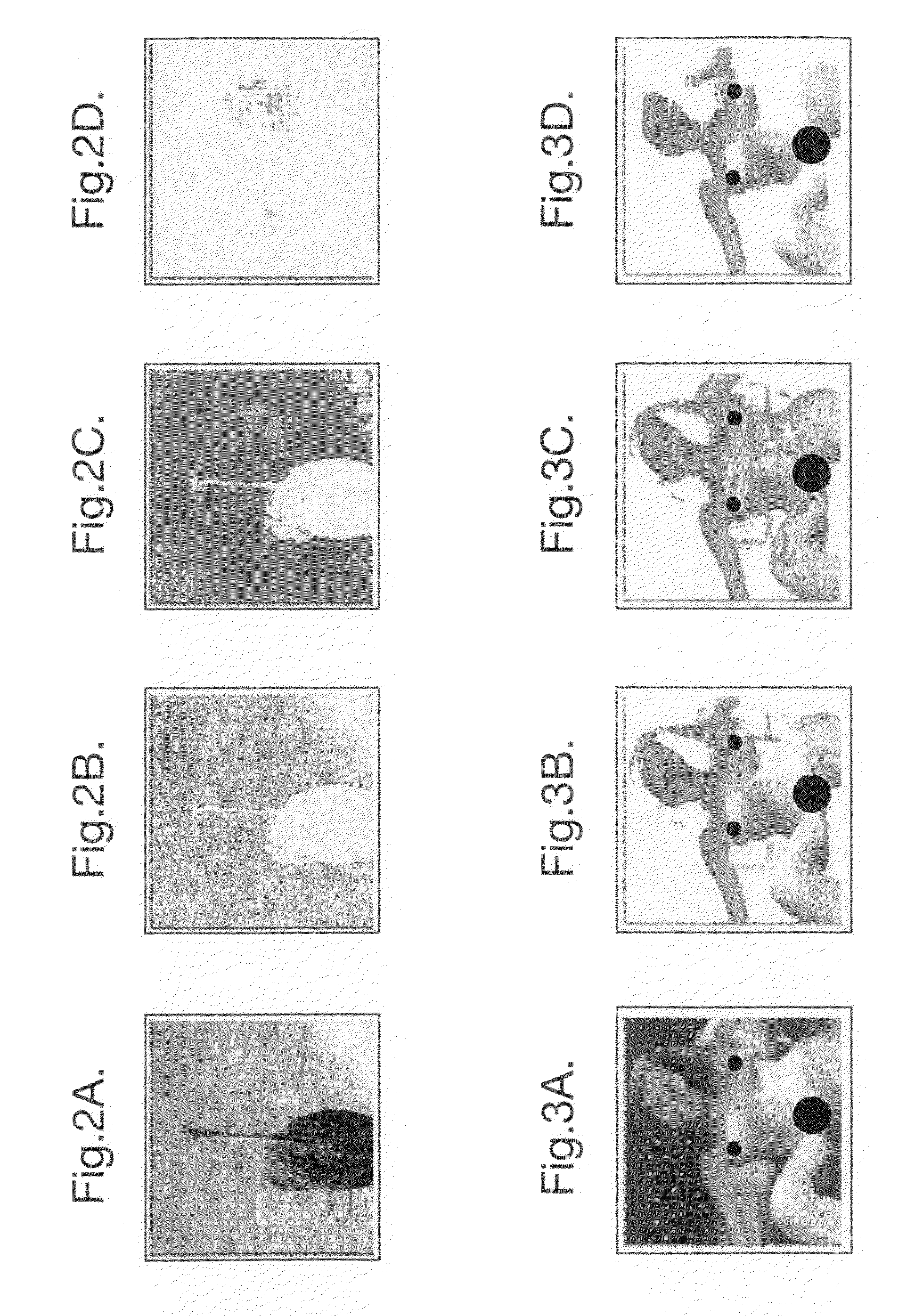
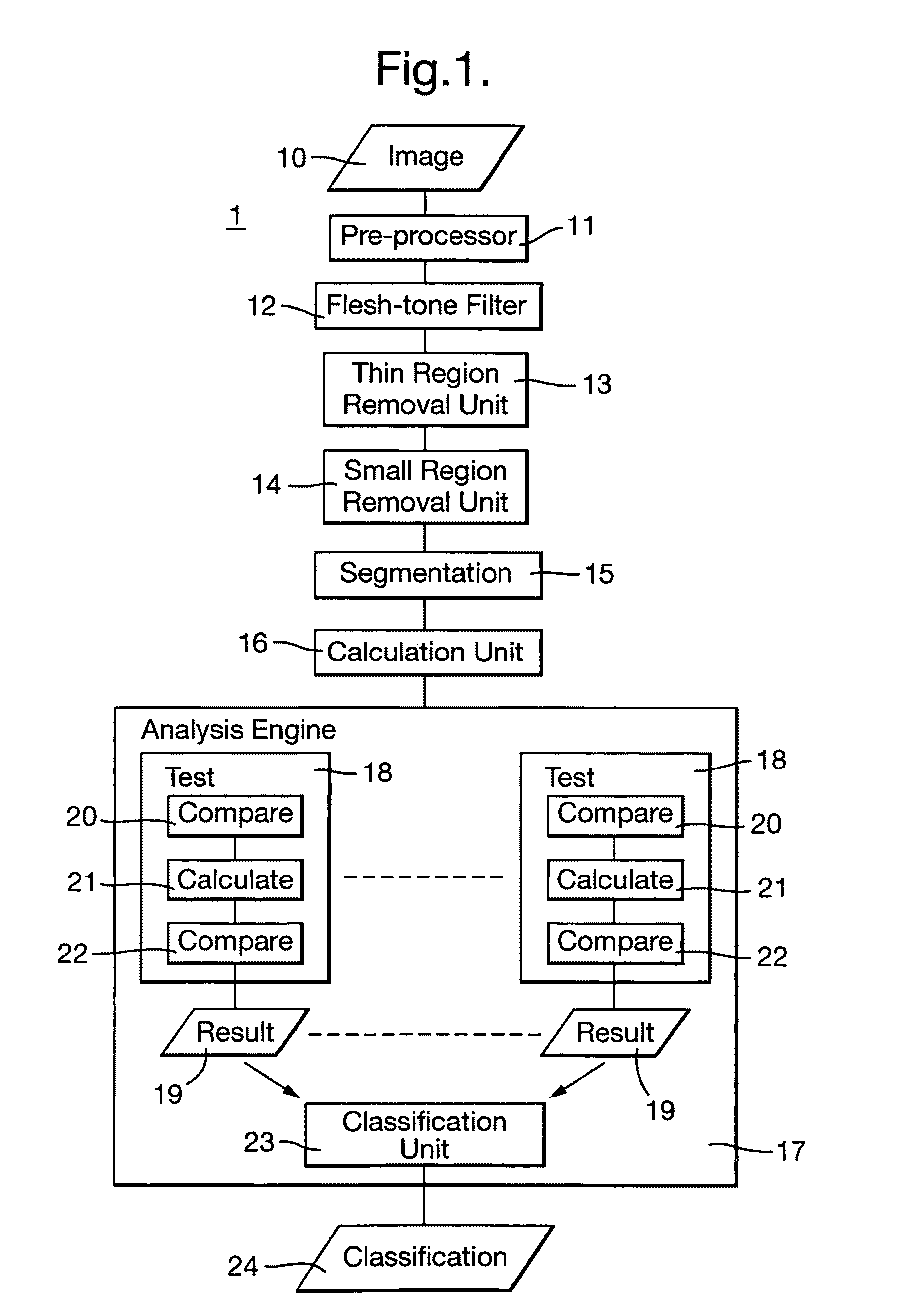
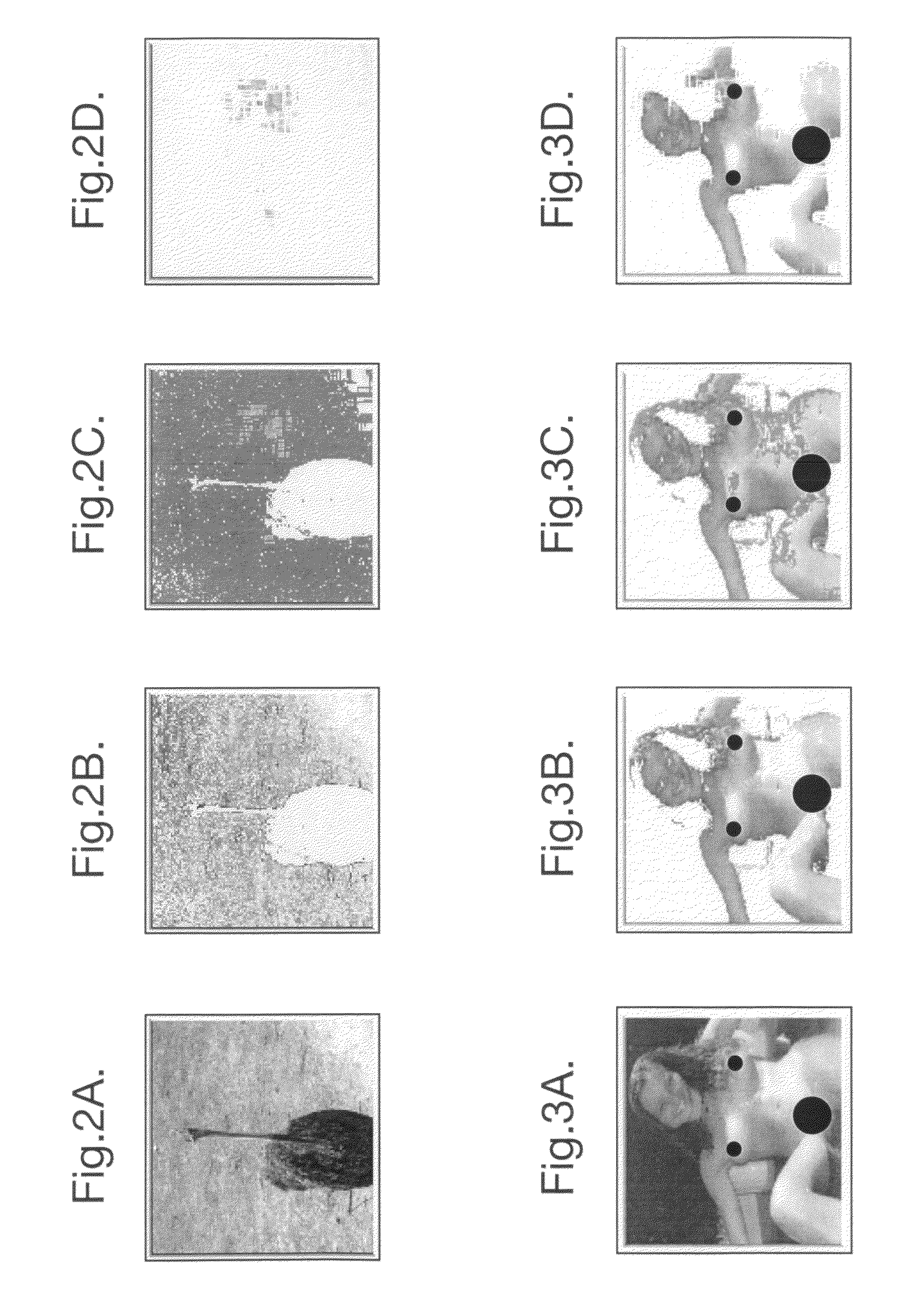
Heuristic analysis of image is performed to detect pornographic content. Pixels of an image representing a flesh-tone are identified. A heuristic analysis of the image is performed to classify the image as being pornographic or not. The analysis uses measures of a set of predetermined characteristics of the identified pixels as a heuristic to indicate a likelihood that the identified pixels contain pornographic content or not. Particular characteristics used are: the thickness of a region of identified pixels; the area of regions of adjacent identified pixels; the flatness of regions of adjacent identified pixels; the distance of pixels from the centre of the image; the degree of texture of regions adjacent identified pixels; the likelihood of the identified pixels being flesh-tone, and the area of the identified pixels. The heuristic analysis is layered, comprising a plurality of tests, each test using the set of predetermined characteristics with differing degrees of significance attributed to each characteristic.
Owner:CA TECH INC
Configurable zone-based location detection
InactiveUS8165034B2Accurate trackingError preventionFrequency-division multiplex detailsWi-FiLocation detection
An improved technique provides location detection using wireless net-works such as Wi-Fi networks in a flexible, configurable manner that allows for variations in the environment and tracks target movement accurately in such an environment. Zones of different relative sizes and sensitivities can be defined, so as to vary the degree of resolution for different parts of the area being detected. Mechanisms are provided to take into account fluctuations in signal strength, and reduce the incidence of false positives resulting from incorrectly detecting zone or location changes due to fluctuations of signal strength. In addition, detection time can be configured for zone entry and / or exit. Self-adjustment based on heuristic analysis can also be implemented. Data can be sent or received based on the physical location as determined by the zone.
Owner:BUCHWALD JON
Scanning images for pornography
ActiveUS8358846B2Improve abilitiesImprove performanceBiometric pattern recognitionSkin colorHeuristic analysis
Heuristic analysis of image is performed to detect pornographic content. Pixels of an image representing a flesh-tone are identified. A heuristic analysis of the image is performed to classify the image as being pornographic or not. The analysis uses measures of a set of predetermined characteristics of the identified pixels as a heuristic to indicate a likelihood that the identified pixels contain pornographic content or not. Particular characteristics used are: the thickness of a region of identified pixels; the area of regions of adjacent identified pixels; the flatness of regions of adjacent identified pixels; the distance of pixels from the center of the image; the degree of texture of regions adjacent identified pixels; the likelihood of the identified pixels being flesh-tone, and the area of the identified pixels. The heuristic analysis is layered, comprising a plurality of tests, each test using the set of predetermined characteristics with differing degrees of significance attributed to each characteristic.
Owner:CA TECH INC
Prioritized rebuilding of a storage device
Rebuilding a storage device after failure of a storage device is disclosed. The method is particularly useful for RAID groups of hard disks. The method may also apply to other storage media arranged as a group. The method includes rebuilding a hard disk in a non-linear fashion according to a heuristic analysis of logical units of the failed hard disk. The method may be implemented in hardware, firmware, software, or a combination thereof.
Owner:DATADIRECT NETWORKS
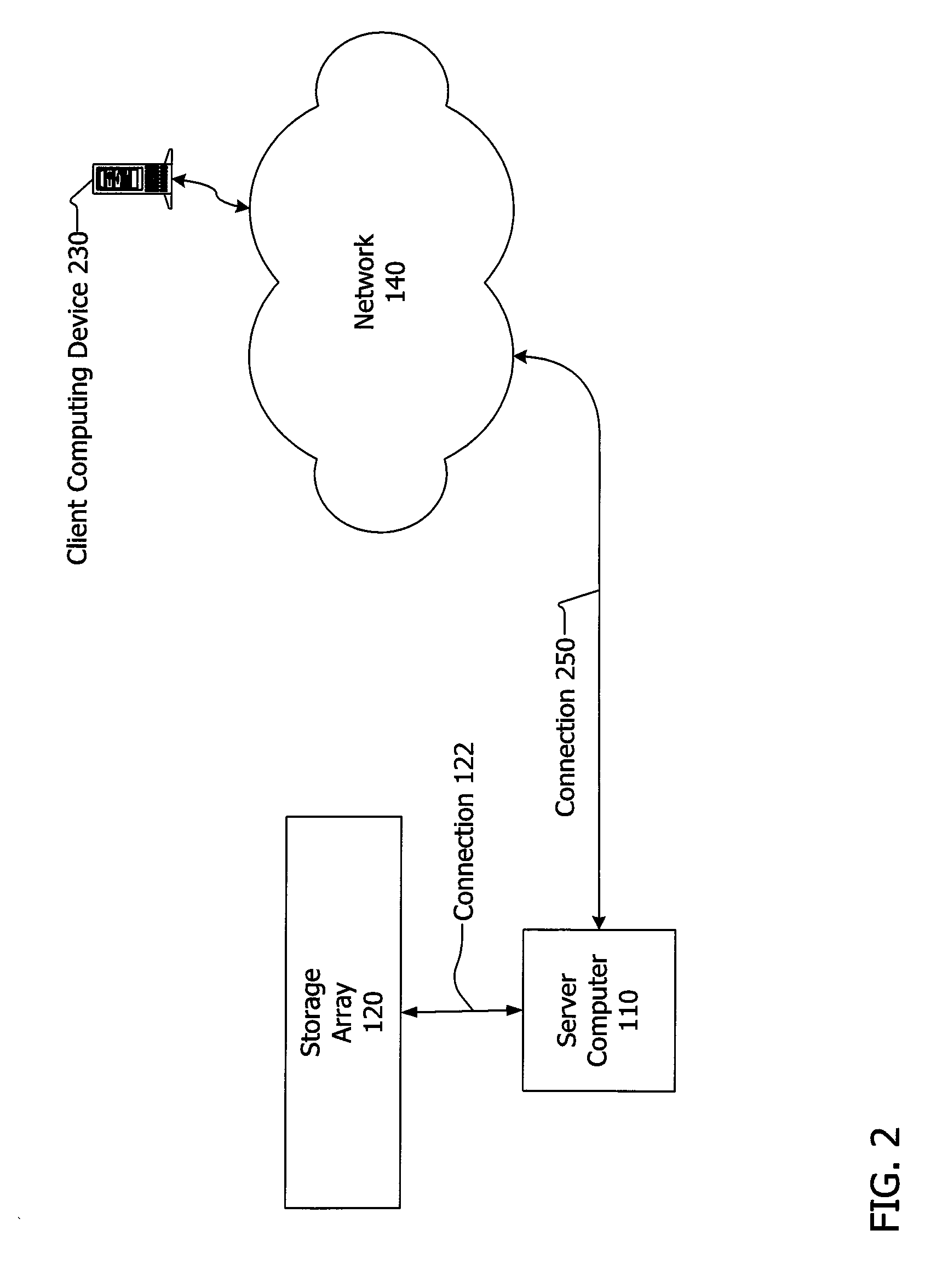
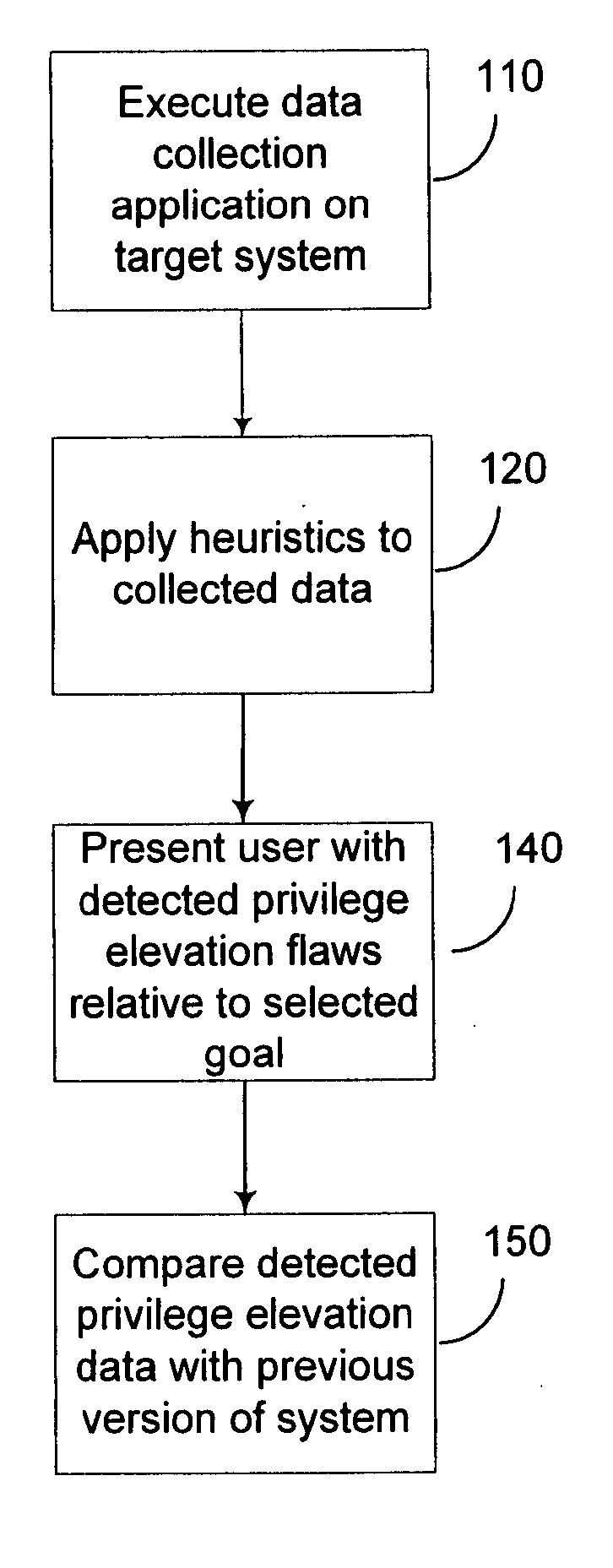
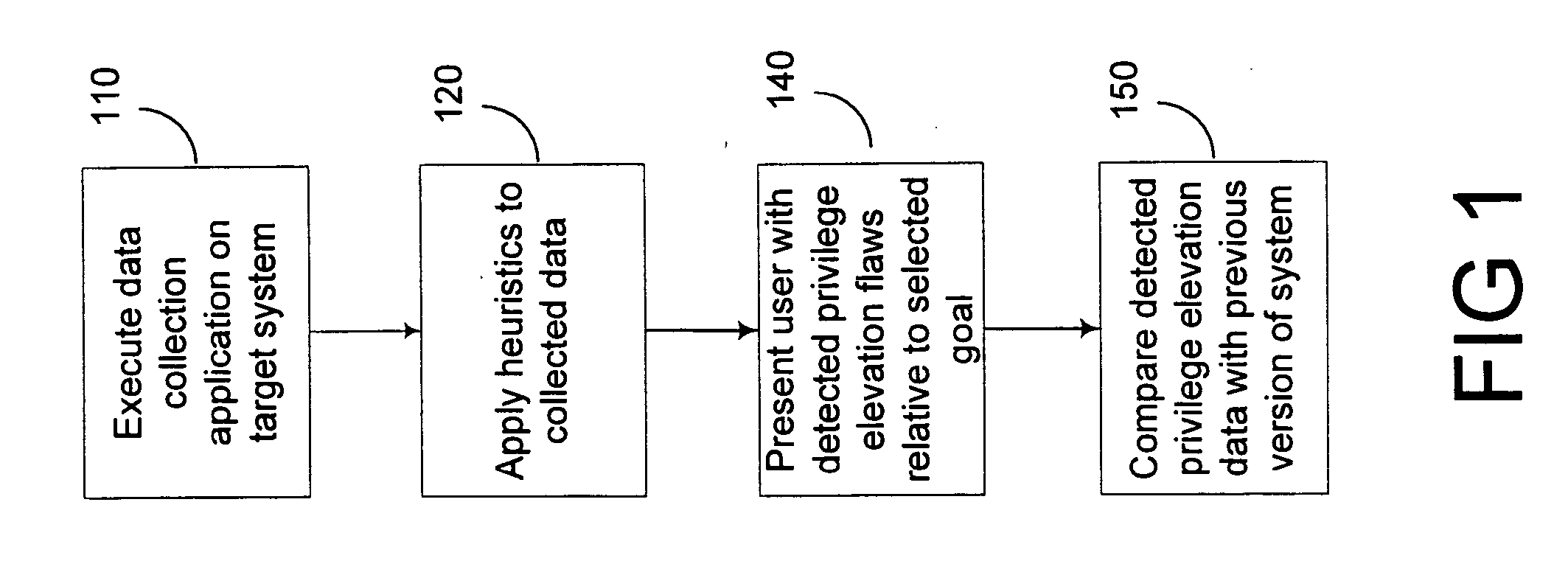
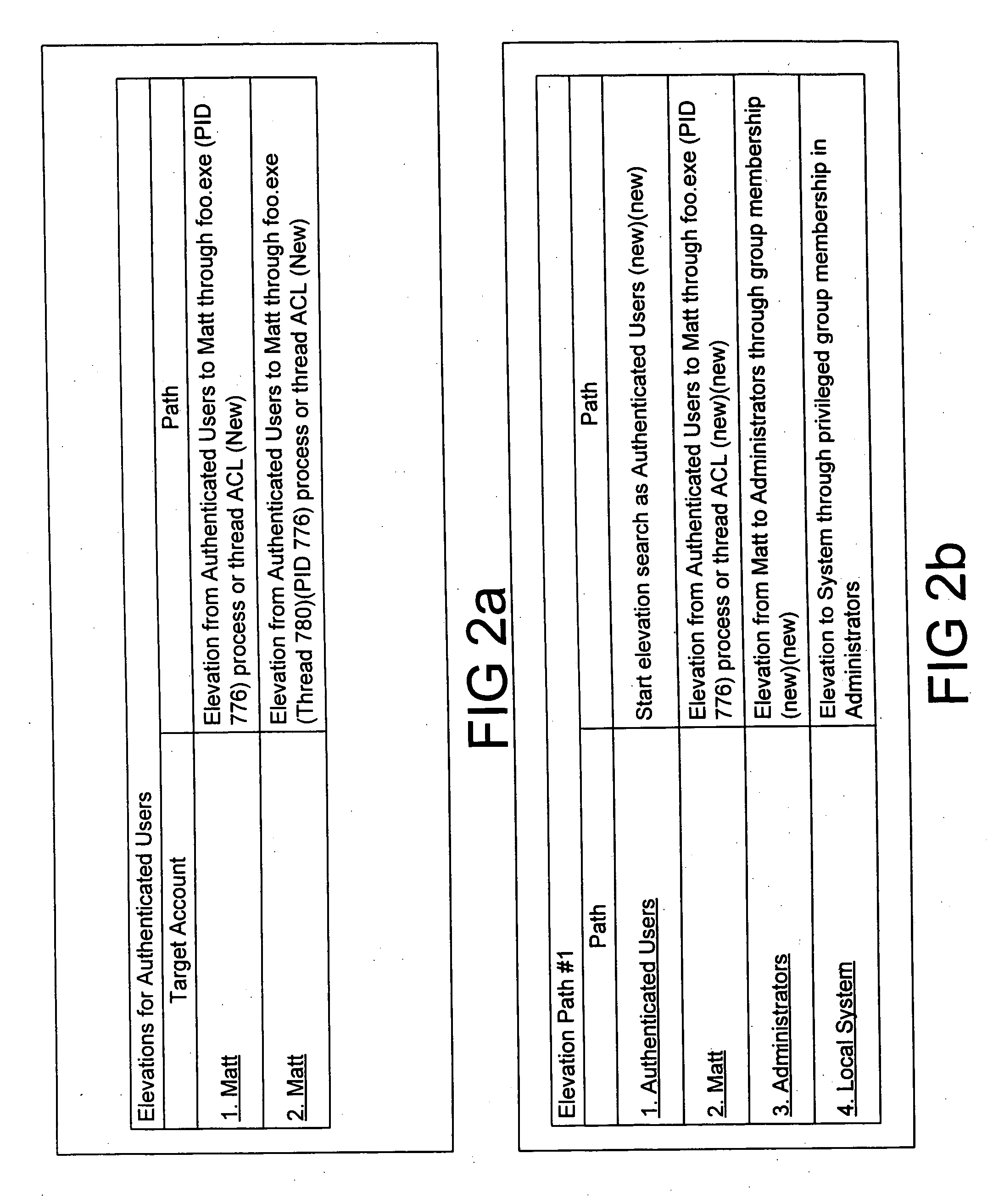
Expert system analysis and graphical display of privilege elevation pathways in a computing environment
A data collection application is executed on a target system. Various data indicative of privilege elevation pathways is collected, including user account data, file permission data, and system registry data. The collected data is analyzed according to heuristics. System accounts are displayed on a graph as nodes. Detected privilege elevations between the accounts are displayed as edges between their corresponding accounts. A user may customize the displayed graph to focus on particular goal accounts, and categories of privilege elevations.
Owner:MICROSOFT TECH LICENSING LLC
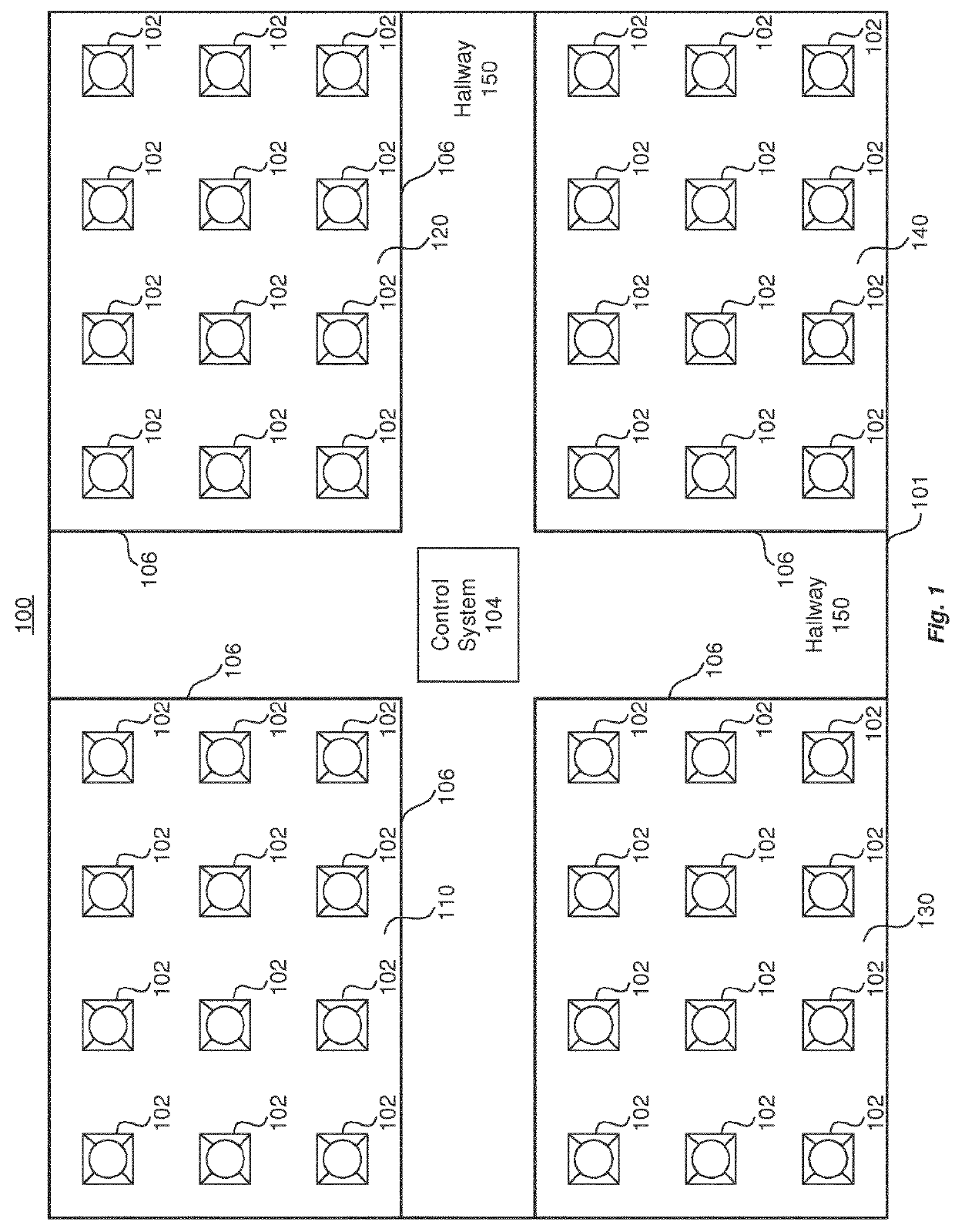
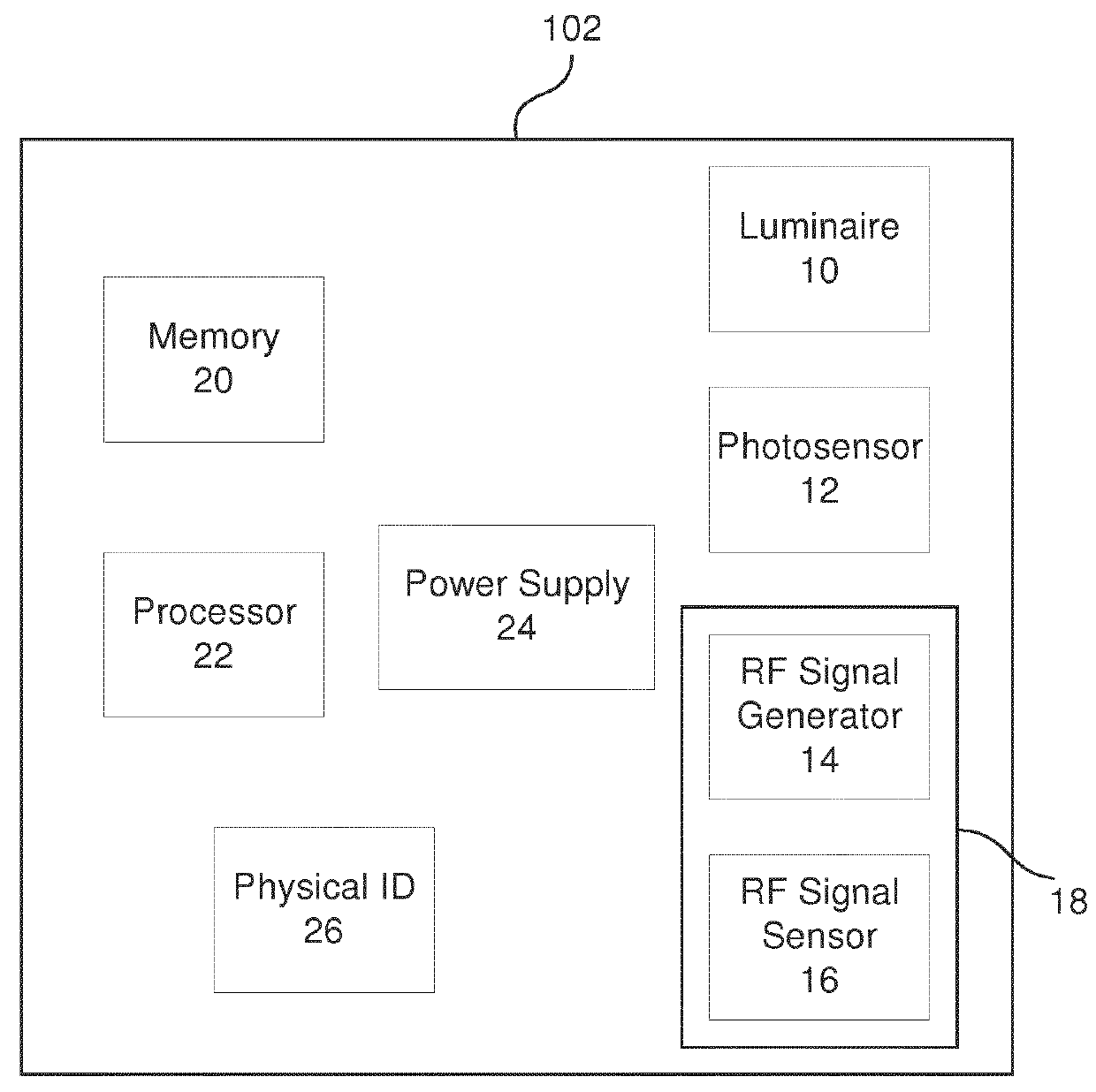
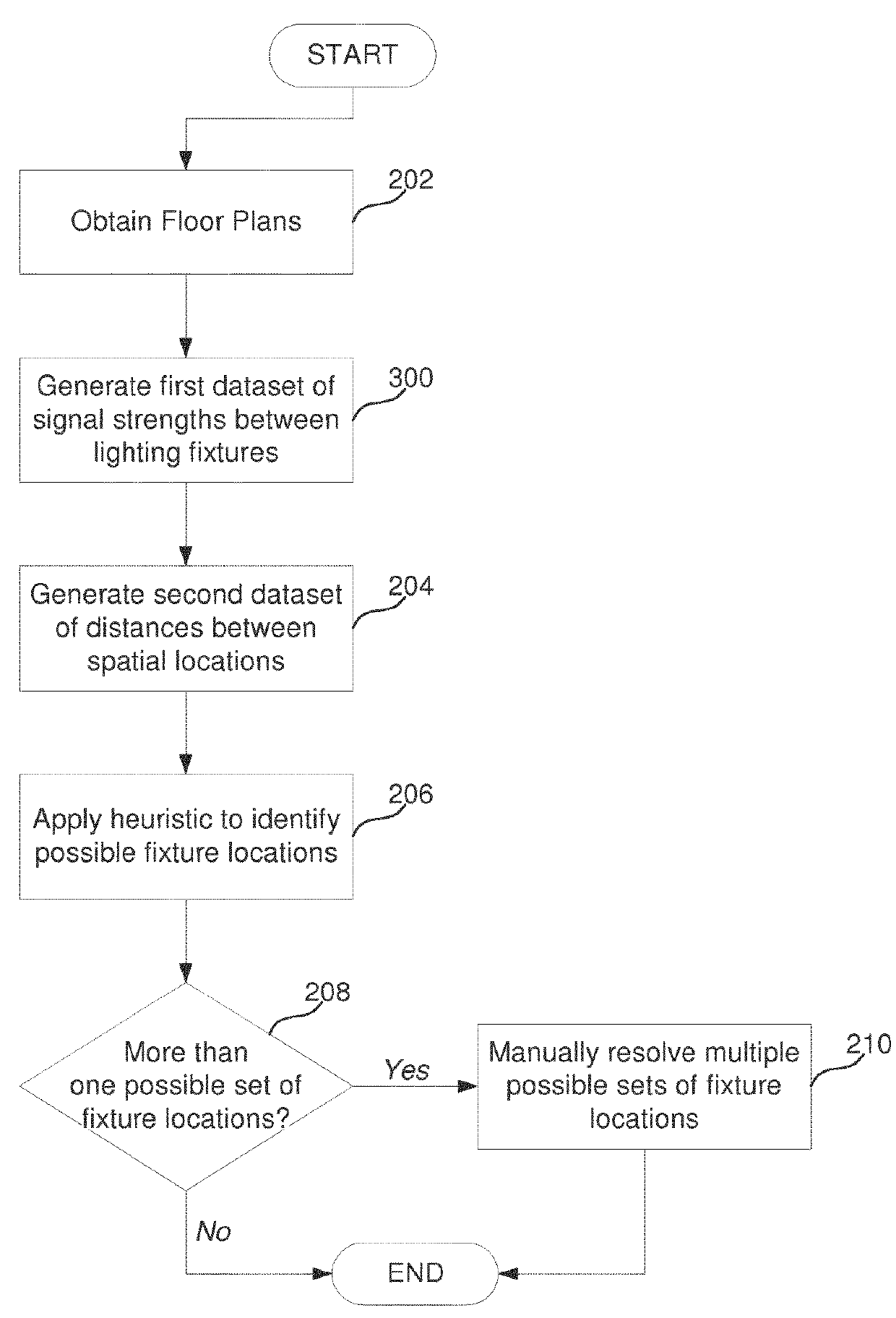
Systems and methods for automatic lighting fixture location mapping
ActiveUS20180270933A1Electric light circuit arrangementData switching networksControl systemFloor plan
Lighting systems and methods for lighting fixture location mapping, for example, using a combination of photo sensing and / or other type of signaling, such as radiofrequency (RF) signaling is provided. The lighting systems may map a plurality of lighting fixtures to a plurality of spatial locations in a floor plan using the signal generating capabilities and sensors that are located within each of the lighting fixtures. The commissioning of the lighting fixtures may be automatically determined using a control system without significant manual intervention. In particular, the lighting fixtures may be mapped to their respective spatial locations by applying a heuristic analysis of strength of signals emitted and received between light fixtures and distances as provided in a building plan between spatial locations to which the light fixtures may be correlated.
Owner:SIGNIFY HLDG BV
Borderless table detection engine
ActiveUS9990347B2Natural language data processingSpecial data processing applicationsProgramming languageCorrelation method
A borderless table detection engine and associated method for identifying borderless tables appearing in data extracted from a fixed format document. Due to the lack of visible borders, reliable automated detection of a borderless table is difficult. The borderless table detection engine uses whitespace, rather than content, to detect borderless table candidates. Applying heuristic analysis, the borderless table detection engine discards borderless table candidates with a layout that lacks sufficient characteristics of a table and is unlikely to be a valid borderless table.
Owner:MICROSOFT TECH LICENSING LLC
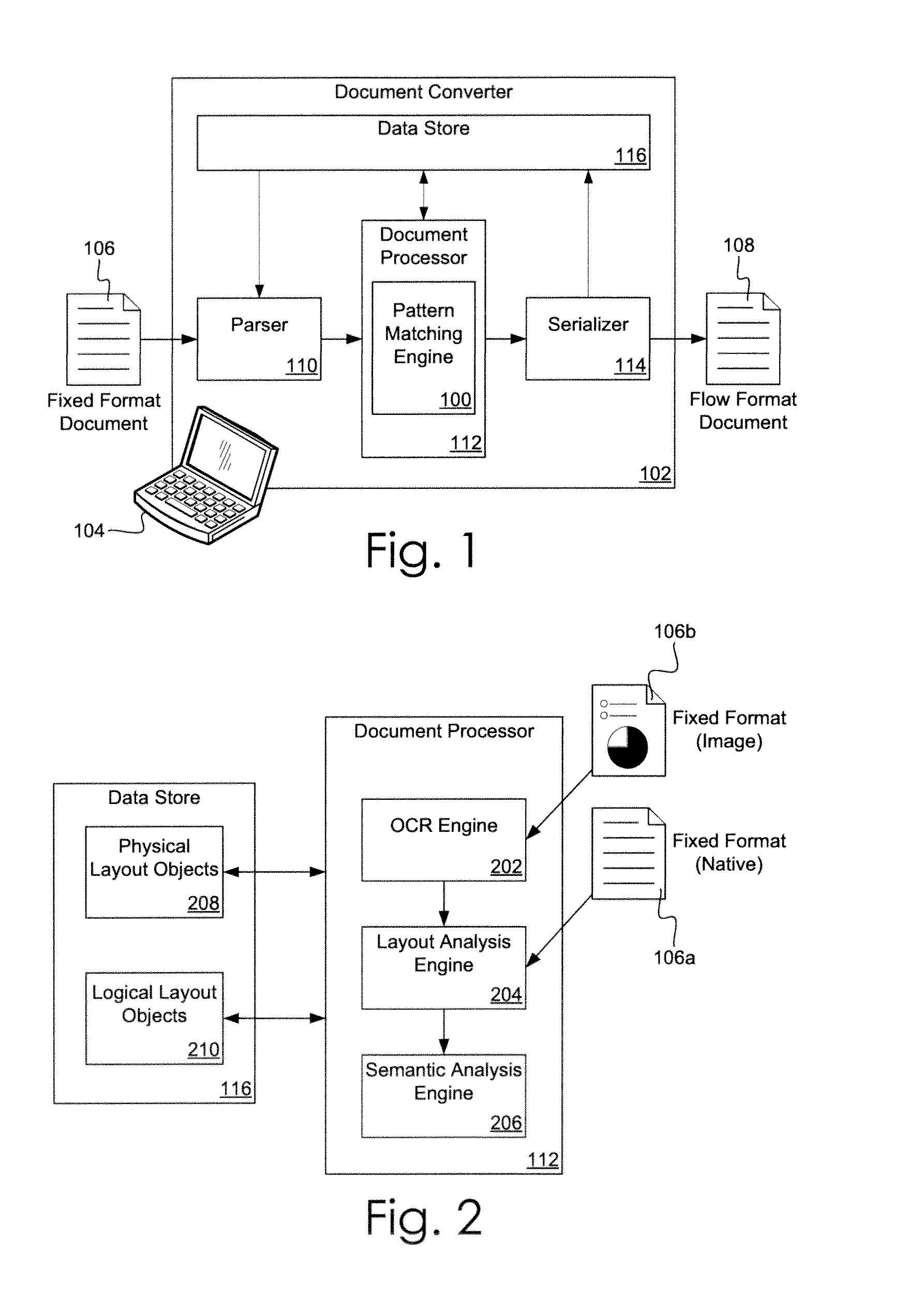
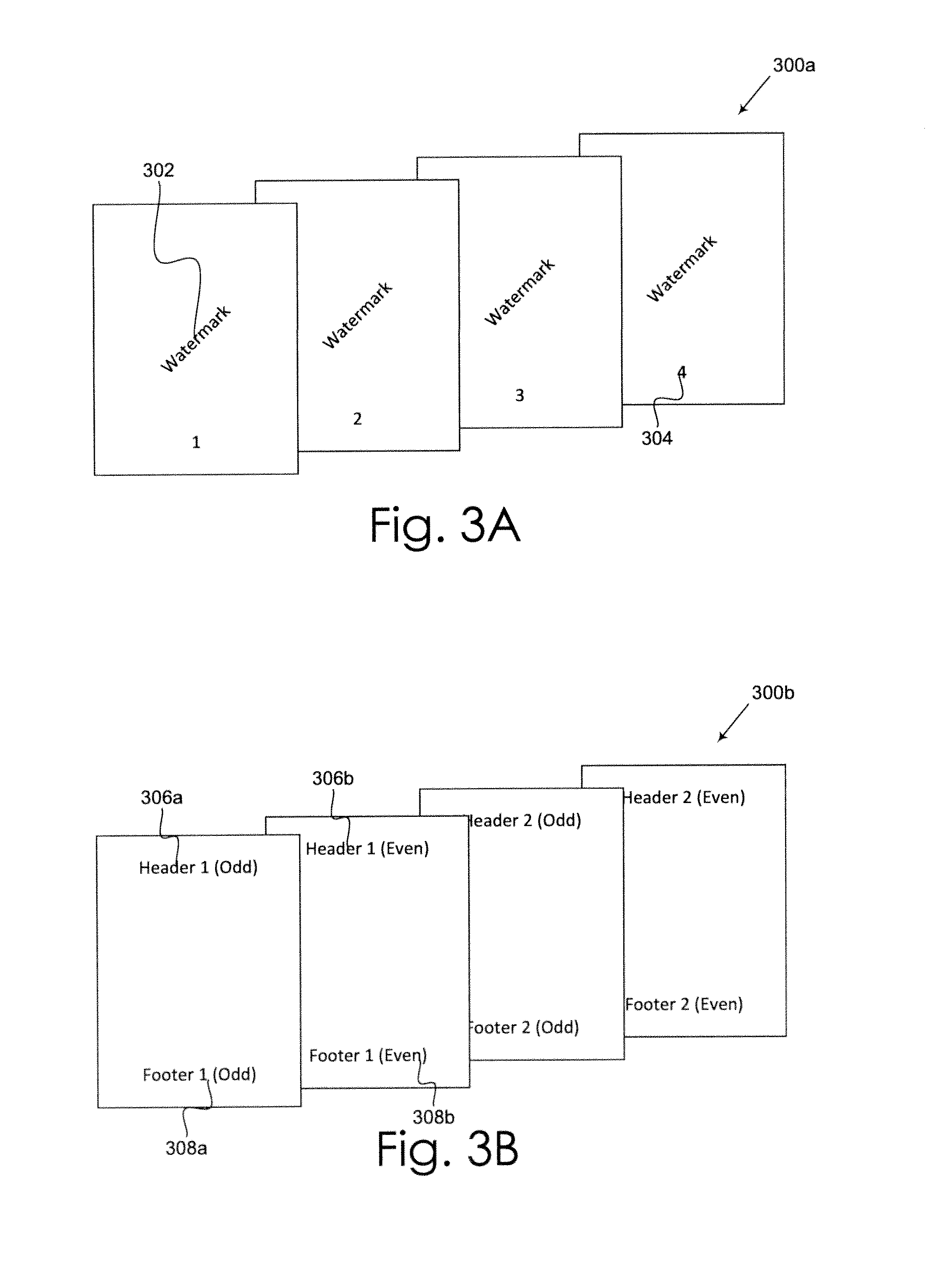
Pattern Matching Engine
InactiveUS20130191366A1Well formedDigital data processing detailsCharacter and pattern recognitionPattern matchingRepeat pattern
A pattern matching engine and associated method for detecting one or more of headers, footers, watermarks, page numbering, page colors, and page borders appearing in a fixed format document. The pattern matching engine performs pattern matching across pages of the fixed format document to identify repeating patterns. Using heuristic analysis, repeating patterns meeting selected criteria are classified as headers, footers, or watermarks. Filtering removes repeating patterns unlikely to represent headers, footers, or watermarks. The information produced by the pattern matching engine allows the repeating elements to be properly reconstructed as flowable elements when converting a fixed format document into a flow format document.
Owner:MICROSOFT TECH LICENSING LLC
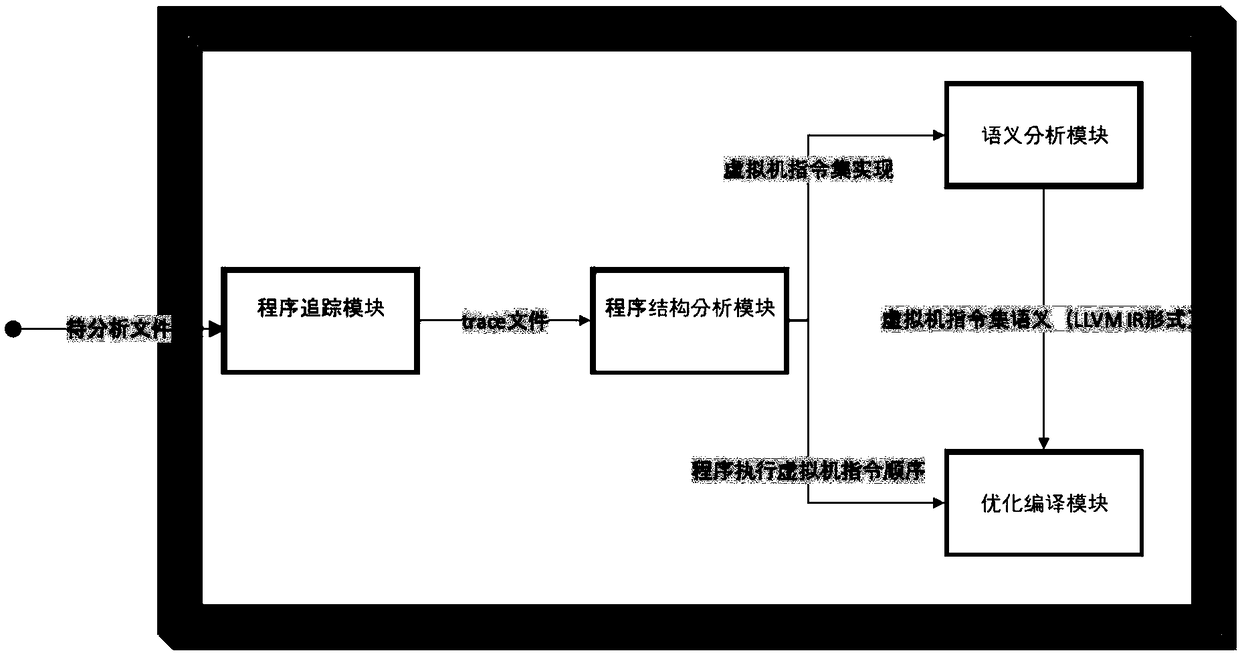
Anti-obfuscation system and method for software virtual machine protection
ActiveCN109145534AReduced number of code instructions to executeReduce the number of instructionsProgram/content distribution protectionSoftware simulation/interpretation/emulationObfuscationReverse analysis
The invention relates to an anti-confusion system and a method for software virtual machine protection. After a program is traced and a tracing file is obtained, a heuristic analysis strategy is adopted to analyze a trace file to obtain a software virtual machine instruction set; then the semantics is extracted from the instruction set of the virtual machine; finally, anti-obfuscation is realizedby rewriting and optimizing compilation. The invention aims at the program protected by the commercial software virtual machine vmprotect, the instructions executed by the optimized program are reduced by 2 / 3 on average, and the program is easy to be modified, thus overcoming the defect of the prior software virtual machine reverse analysis method.
Owner:SHANGHAI JIAO TONG UNIV
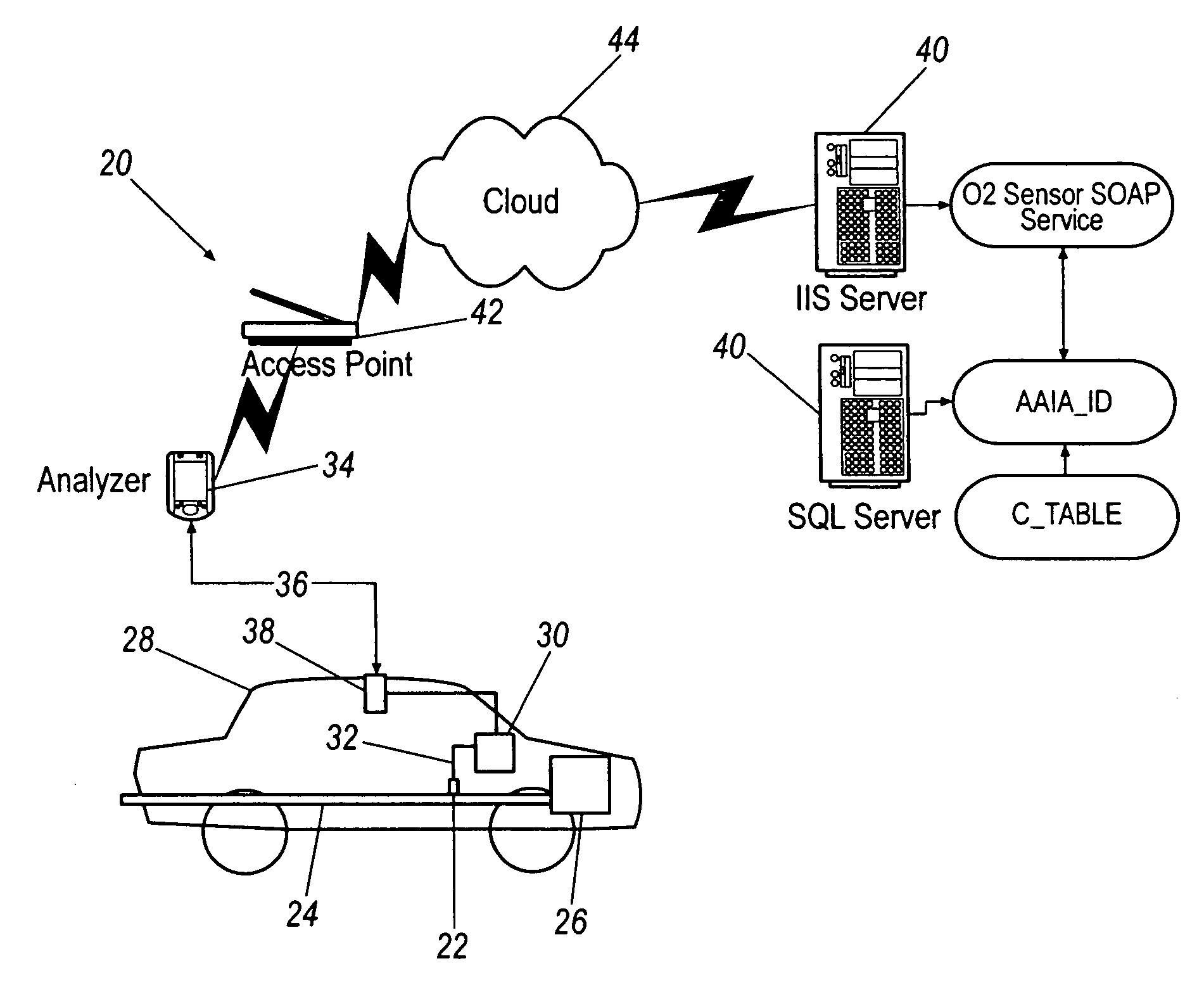
Diagnostic tool for sensing oxygen sensor heater operation
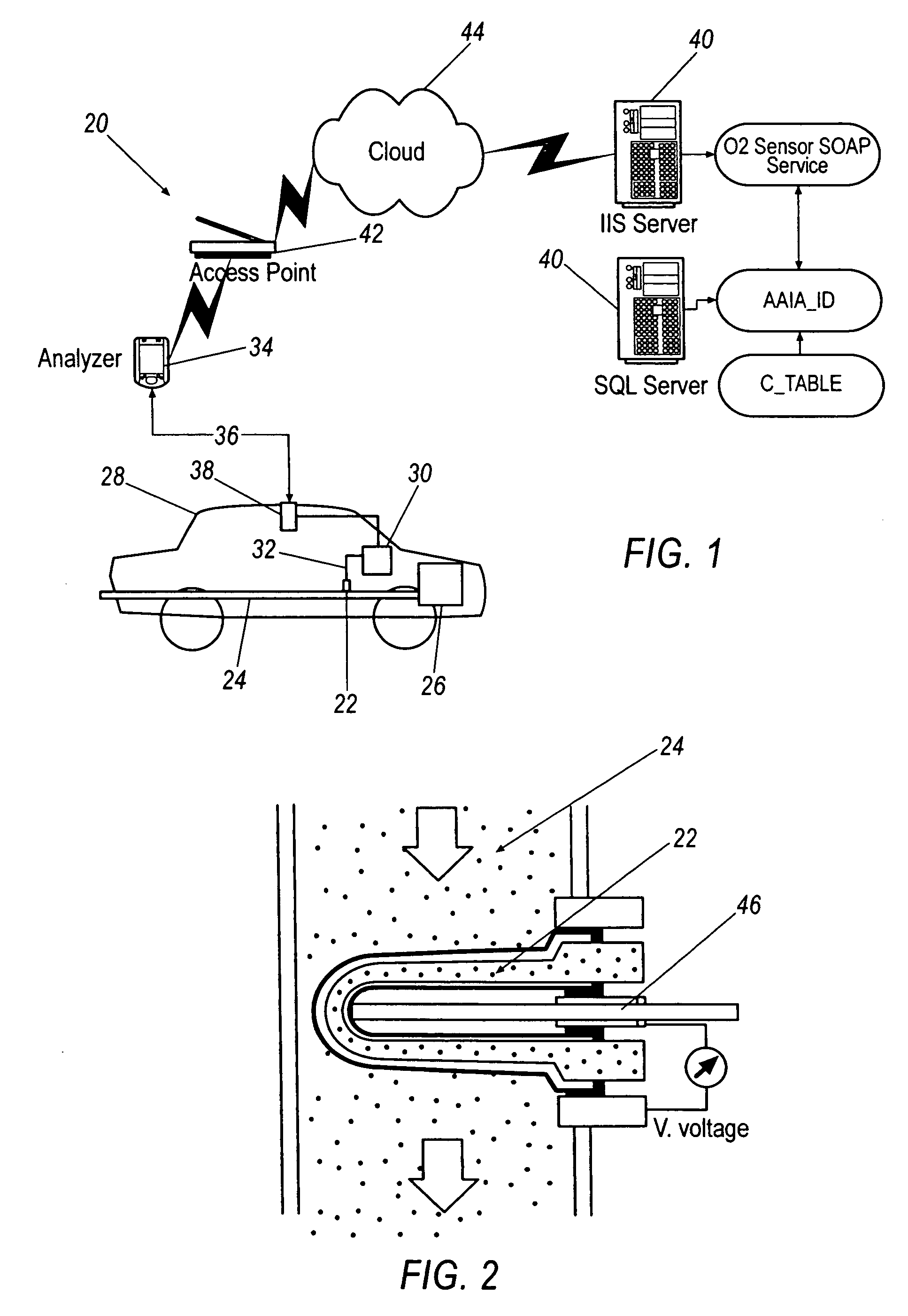
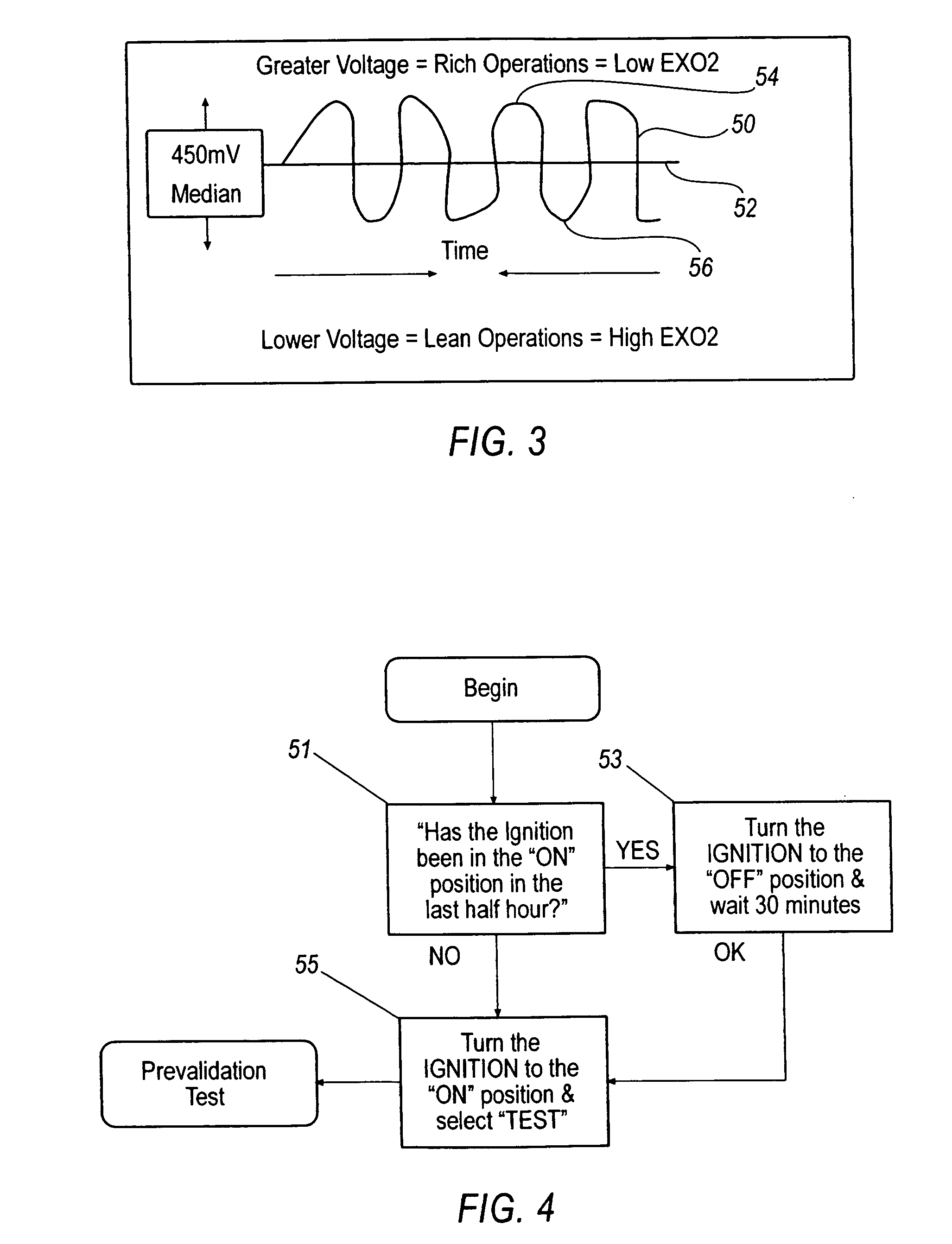
ActiveUS20060247842A1Analogue computers for vehiclesInternal-combustion engine testingTelecommunications linkOxygen sensor
A diagnostic testing system for a vehicle comprising an oxygen sensor having a heating element for heating the oxygen sensor to its minimum operational temperature, an analyzer having a user interface, a communications link between the analyzer and the vehicle to obtain data from the oxygen sensor, and a diagnostic heuristic analyzing the data and confirming proper operation of the heating element, the diagnostic heuristic being adapted to generate an output and transmit the output to the user interface, the output including the results generated by analysis of the data by the diagnostic heuristic.
Owner:DELPHI TECH IP LTD
System and method for configuration of an ensemble solver
ActiveUS9684865B1Efficiently exploreRisk minimizationEnsemble learningKnowledge representationAlgorithmSolver
In a system for enabling configuration of an ensemble of several solvers, such that the ensemble can efficiently solve a constraint problem, for each one of several candidate configurations, an array of scores is computed. The array corresponds to a statistical parameter related to a problem solution, and the computation is based on, at least in part, a set of features associated with the problem. One candidate configuration is assigned to a solver, and based on the array of scores associated with that candidate configuration the same or a different candidate configuration is assigned to a another solver. A system for dynamically reconfiguring an ensemble of solvers obtains runtime data from several solvers, and a new configuration is determined by applying a machine learning and / or heuristic analysis procedure to the runtime data. The configuration of a solver may be updated according to the new configuration while that solver is running.
Owner:QUALCOMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com