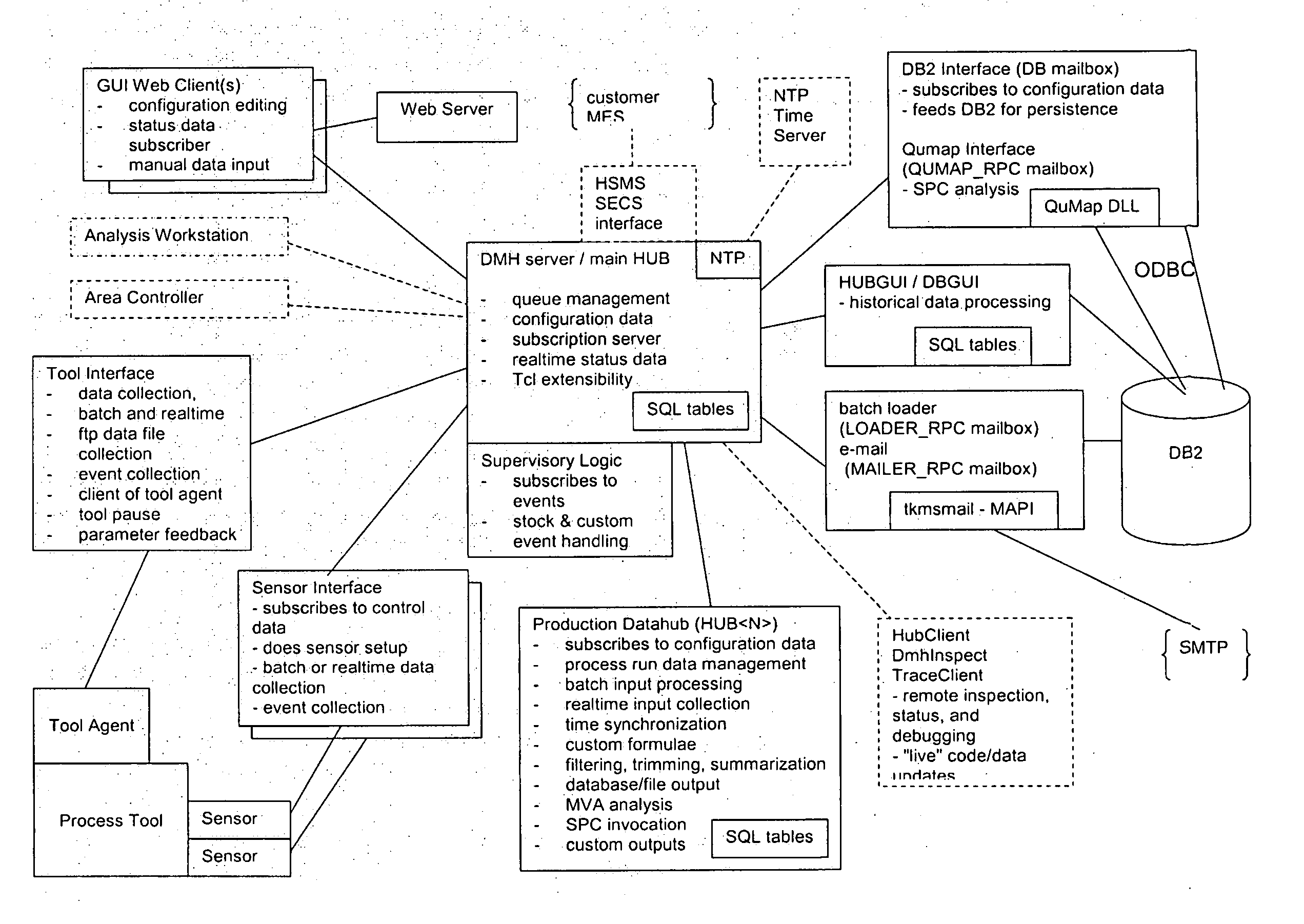
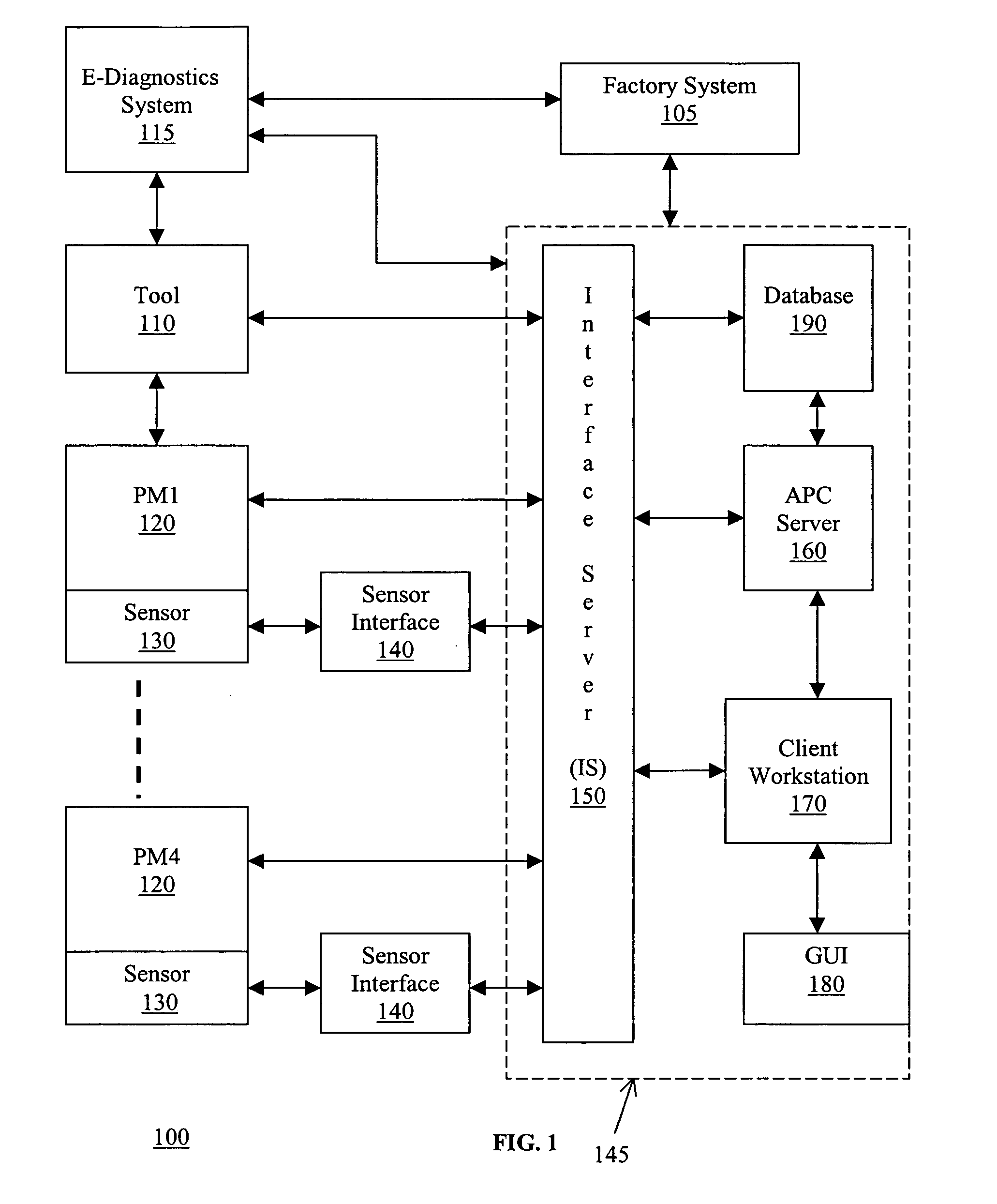
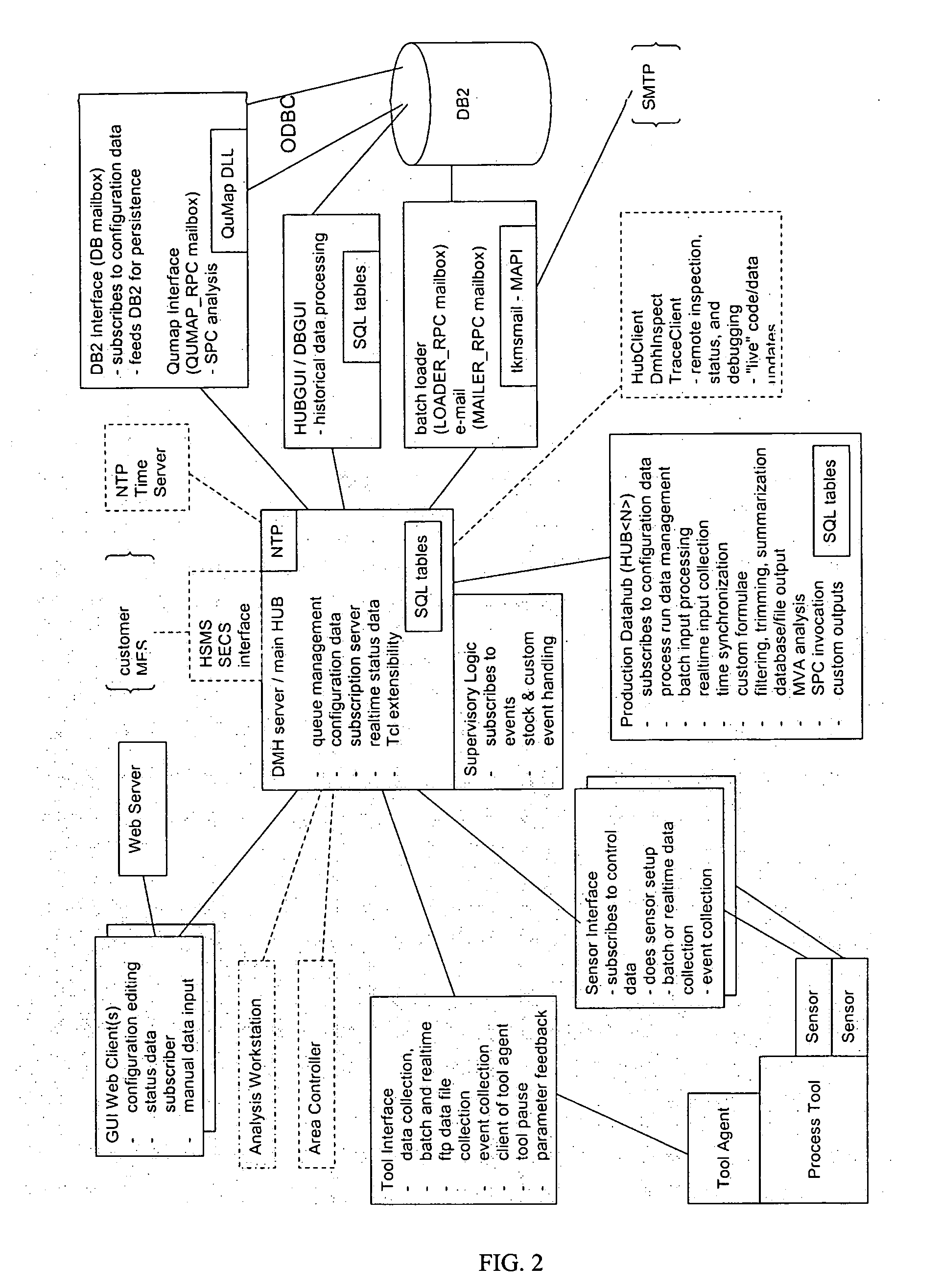
Patents
Literature
193 results about "Trace file" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
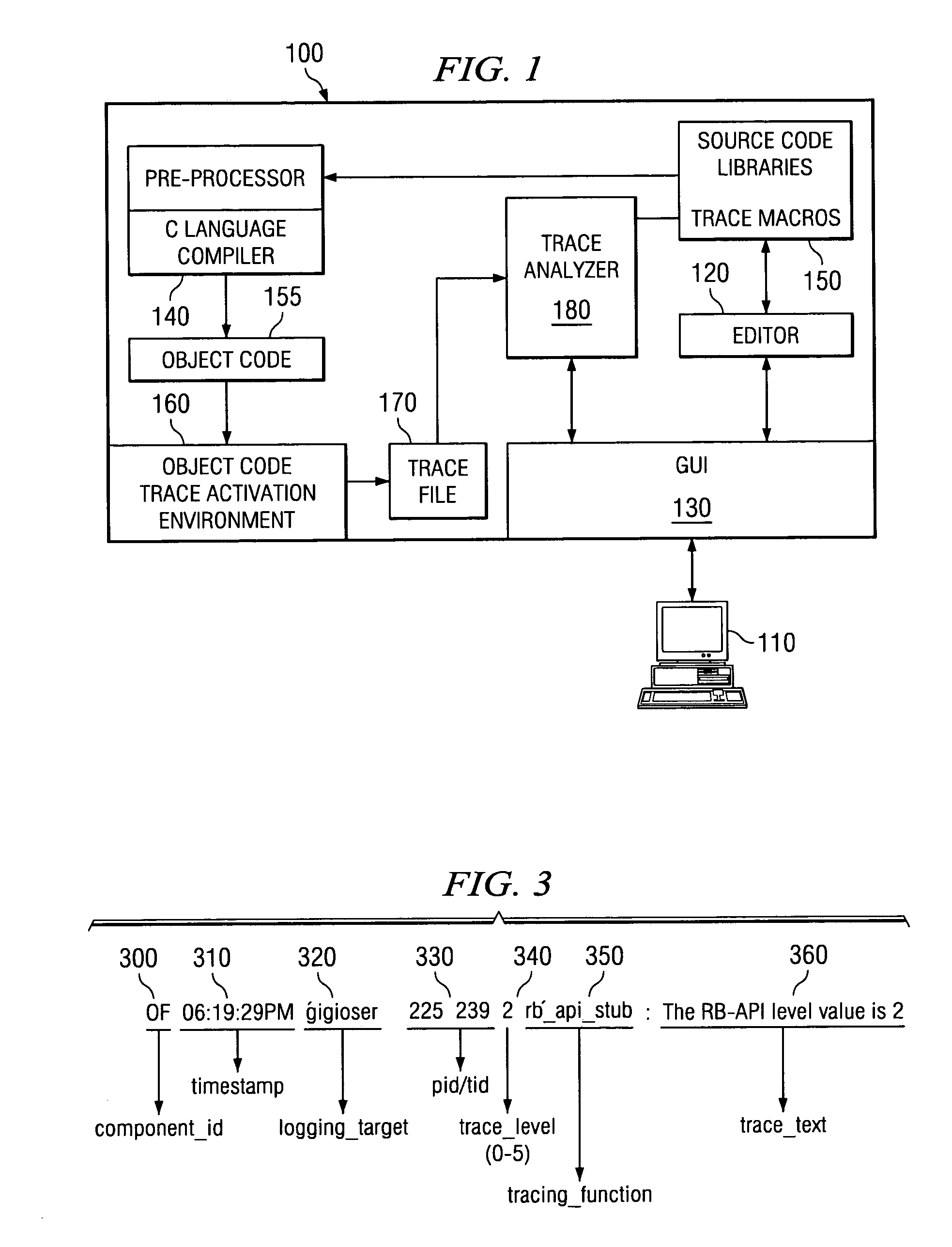
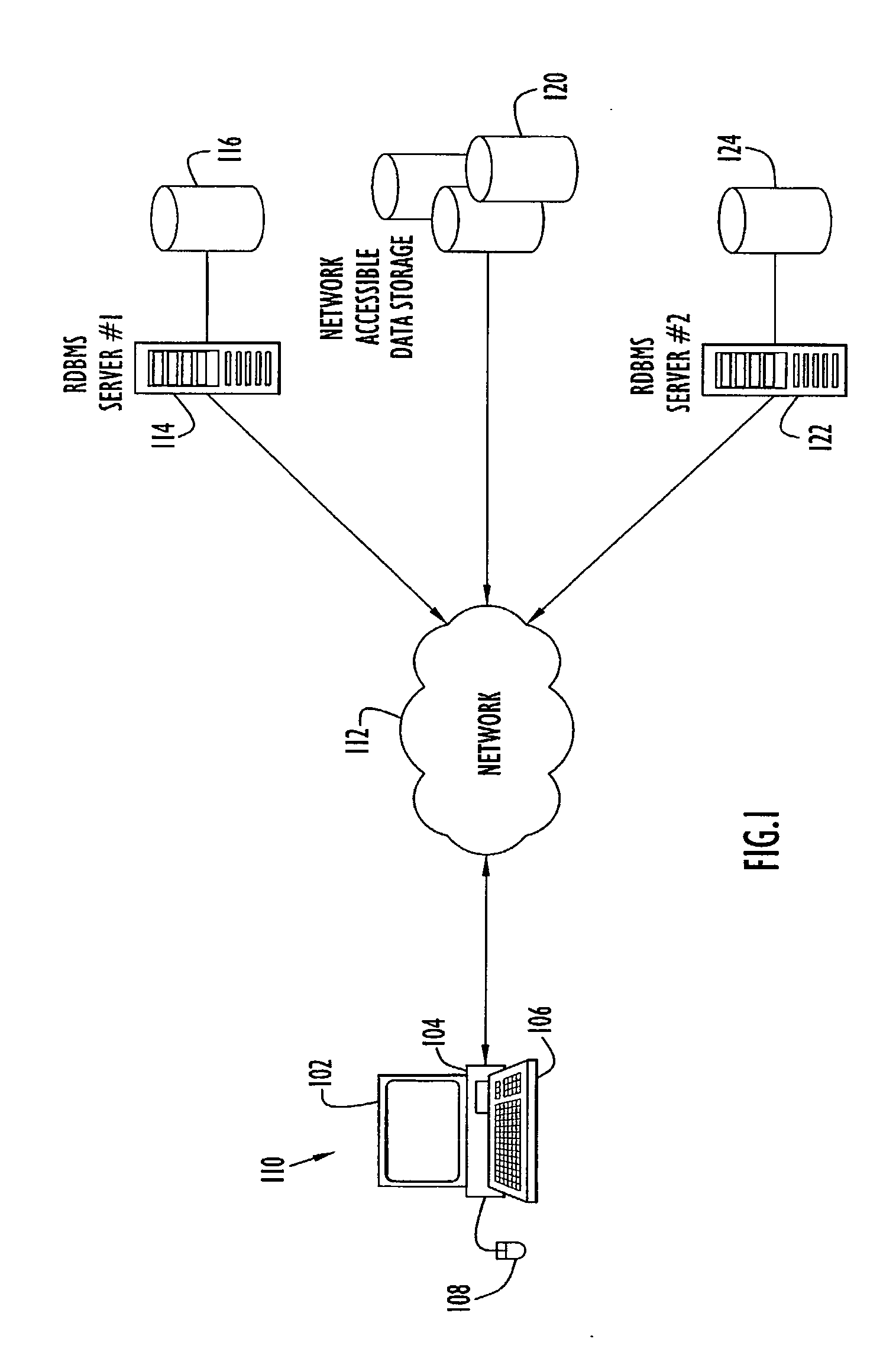
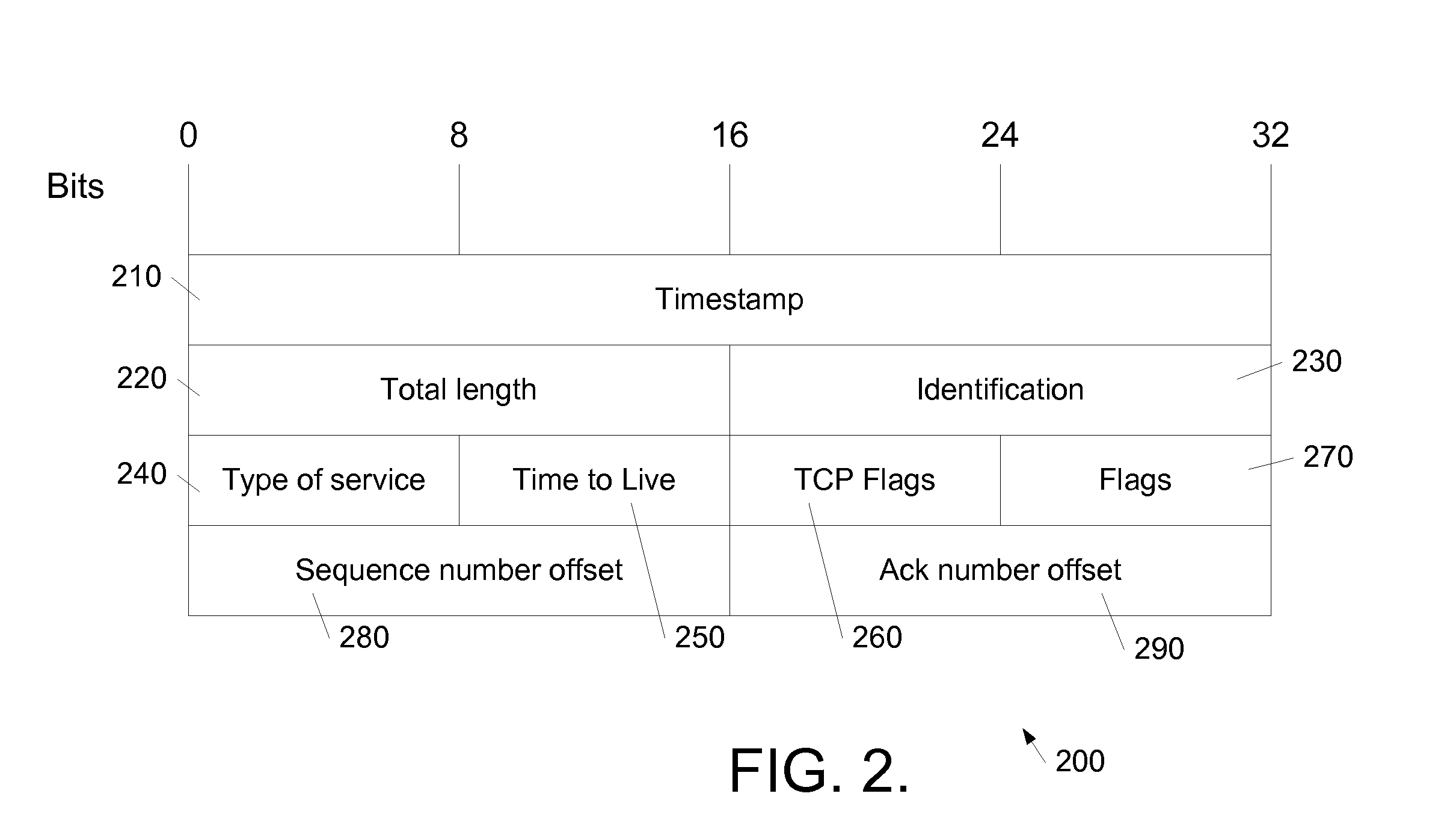
Trace File are trace (or dump) file that Oracle Database creates to help you diagnose and resolve operating problems. Each server and background process writes to a trace file. When a process detects an internal error, it writes information about the error to its trace file.
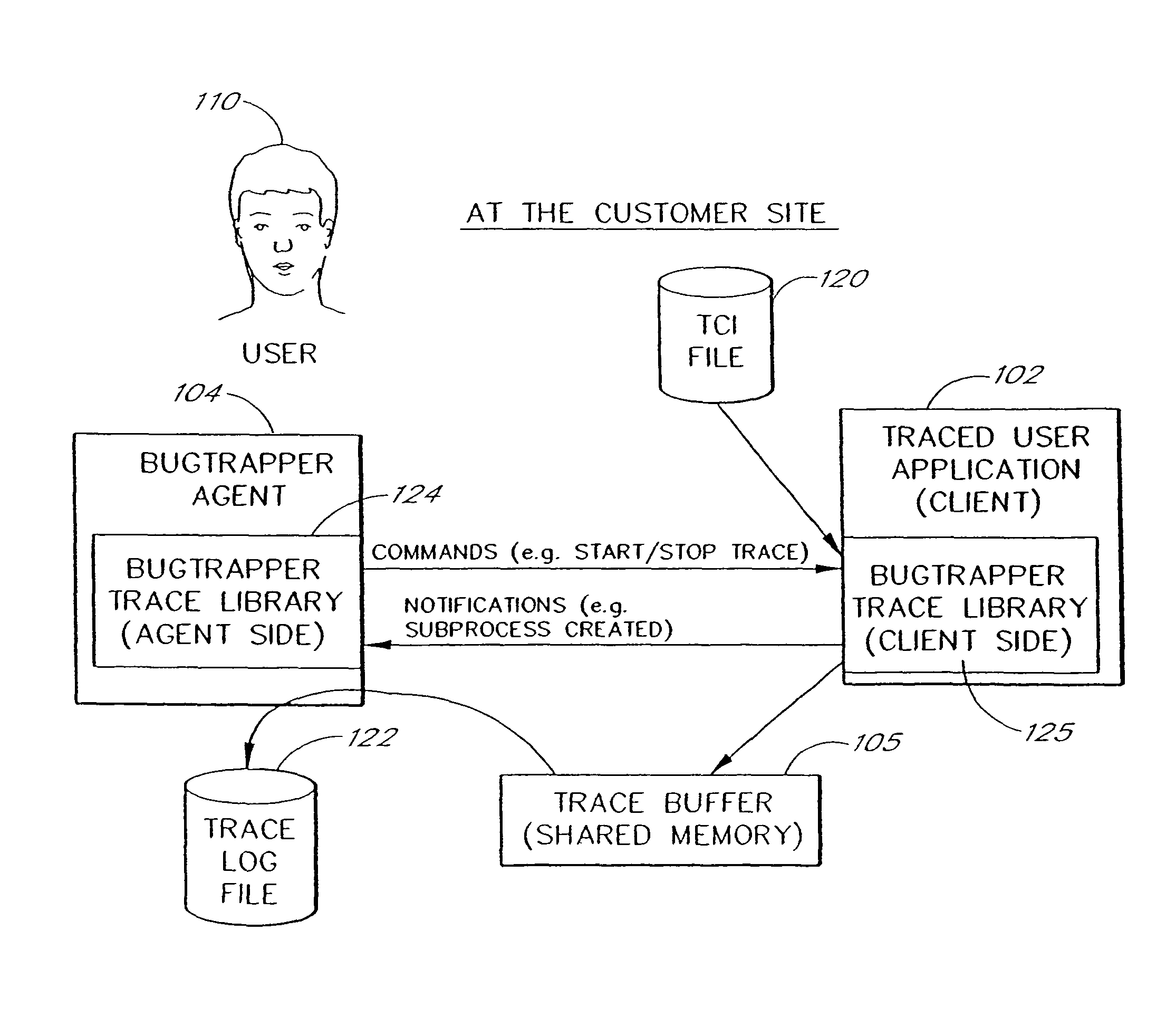
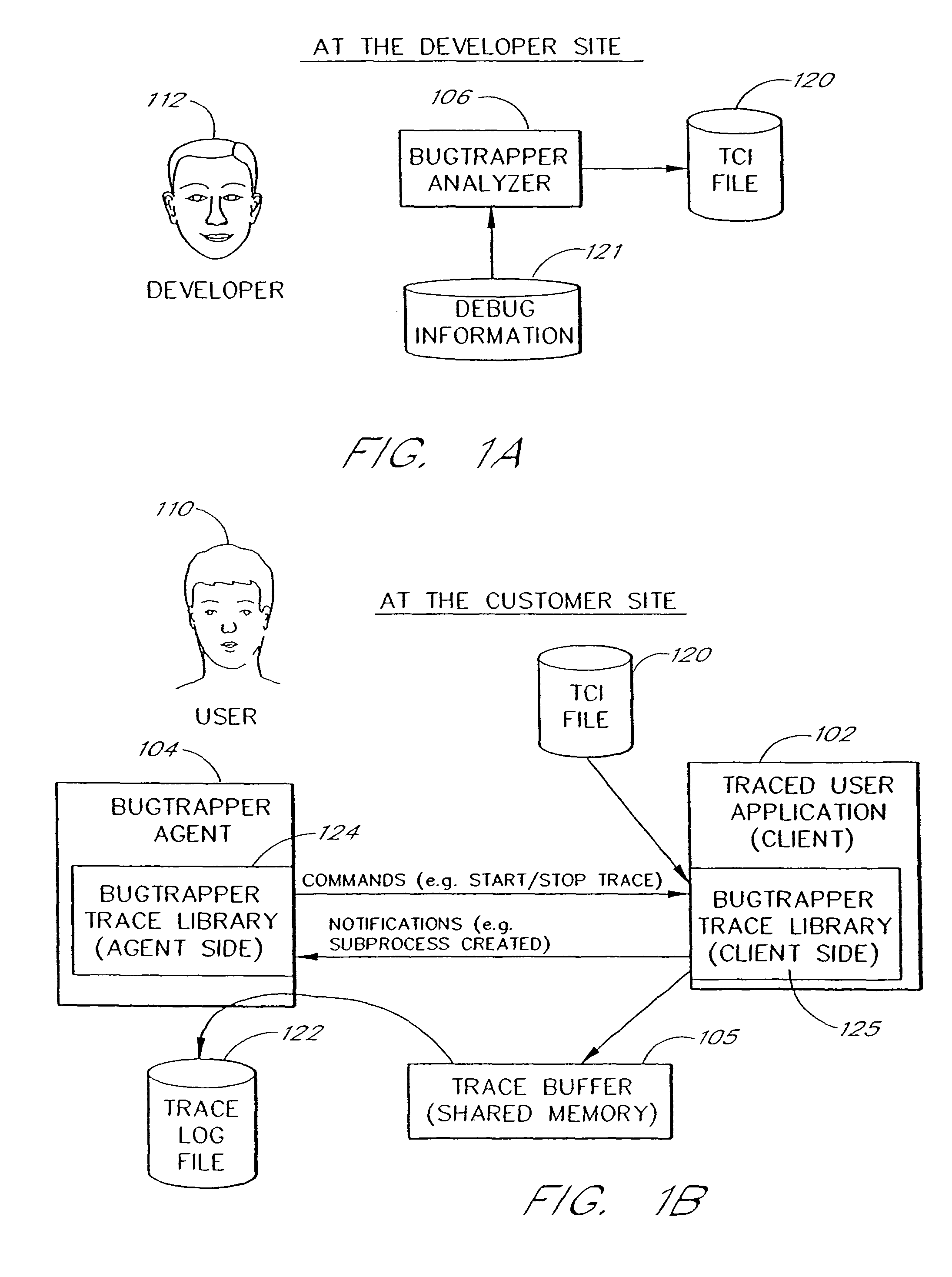
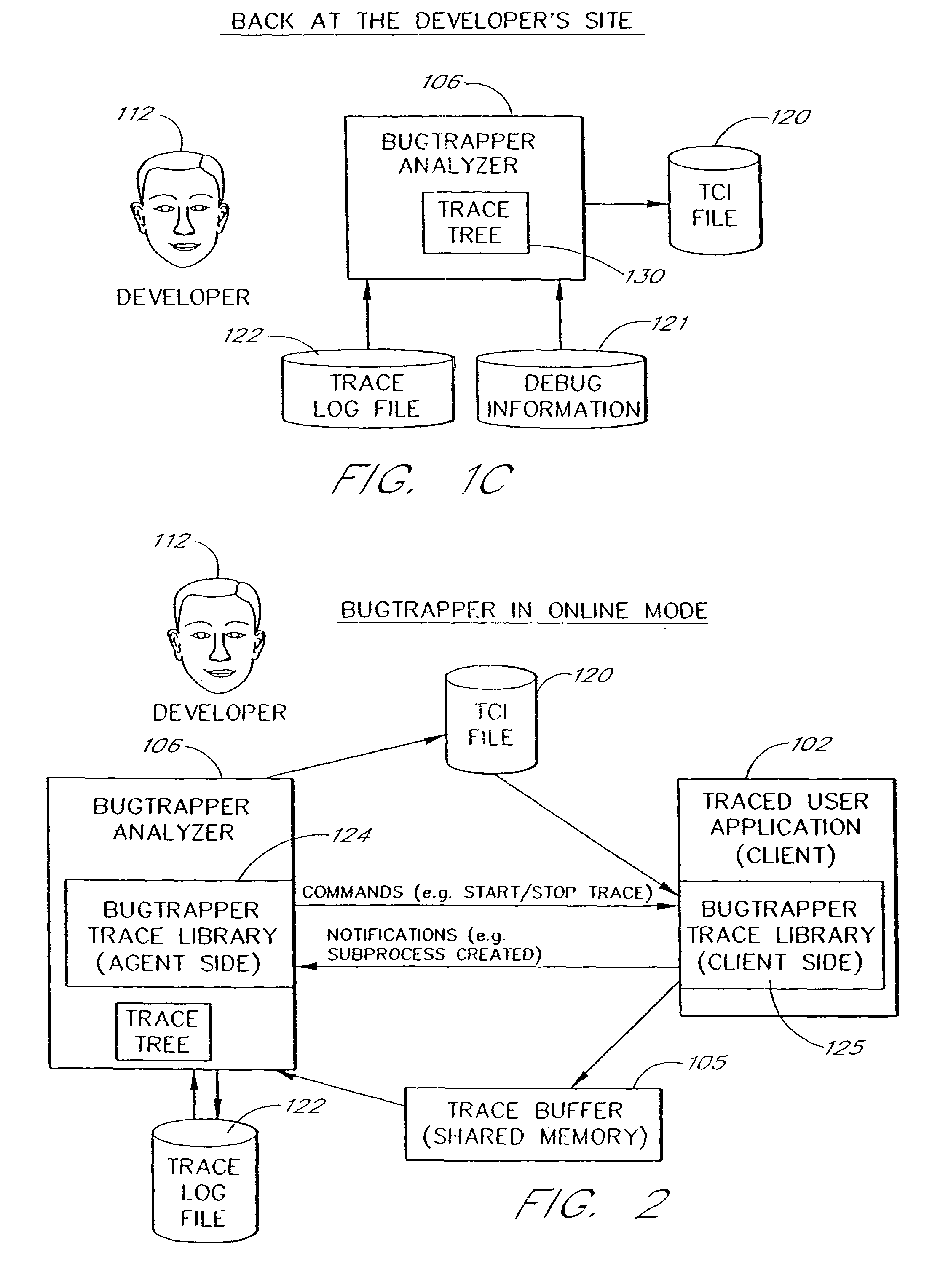
System and method for conditional tracing of computer programs
ActiveUS20060242627A1Small sizeRaise the possibilityError detection/correctionSpecific program execution arrangementsSource code fileTrace file
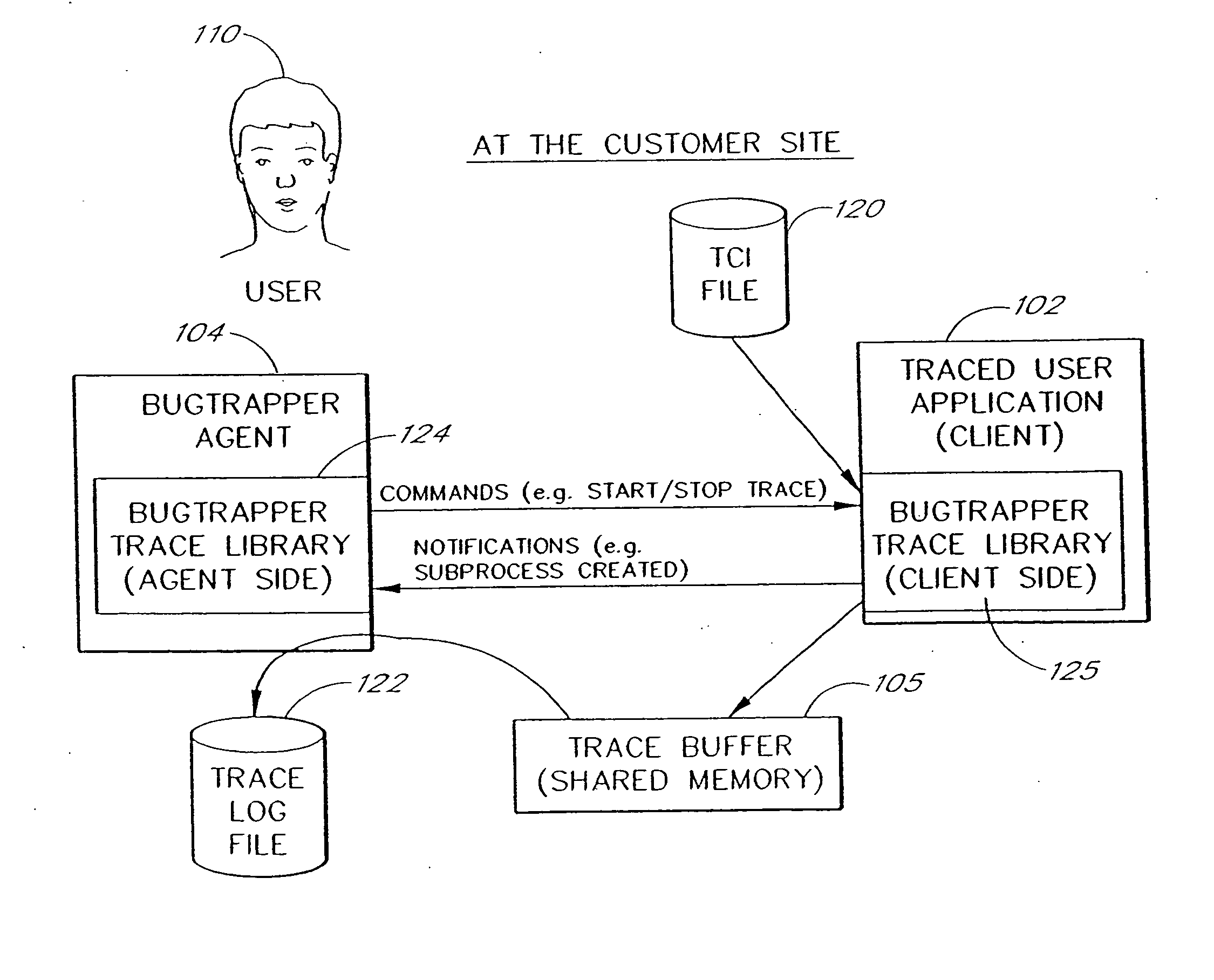
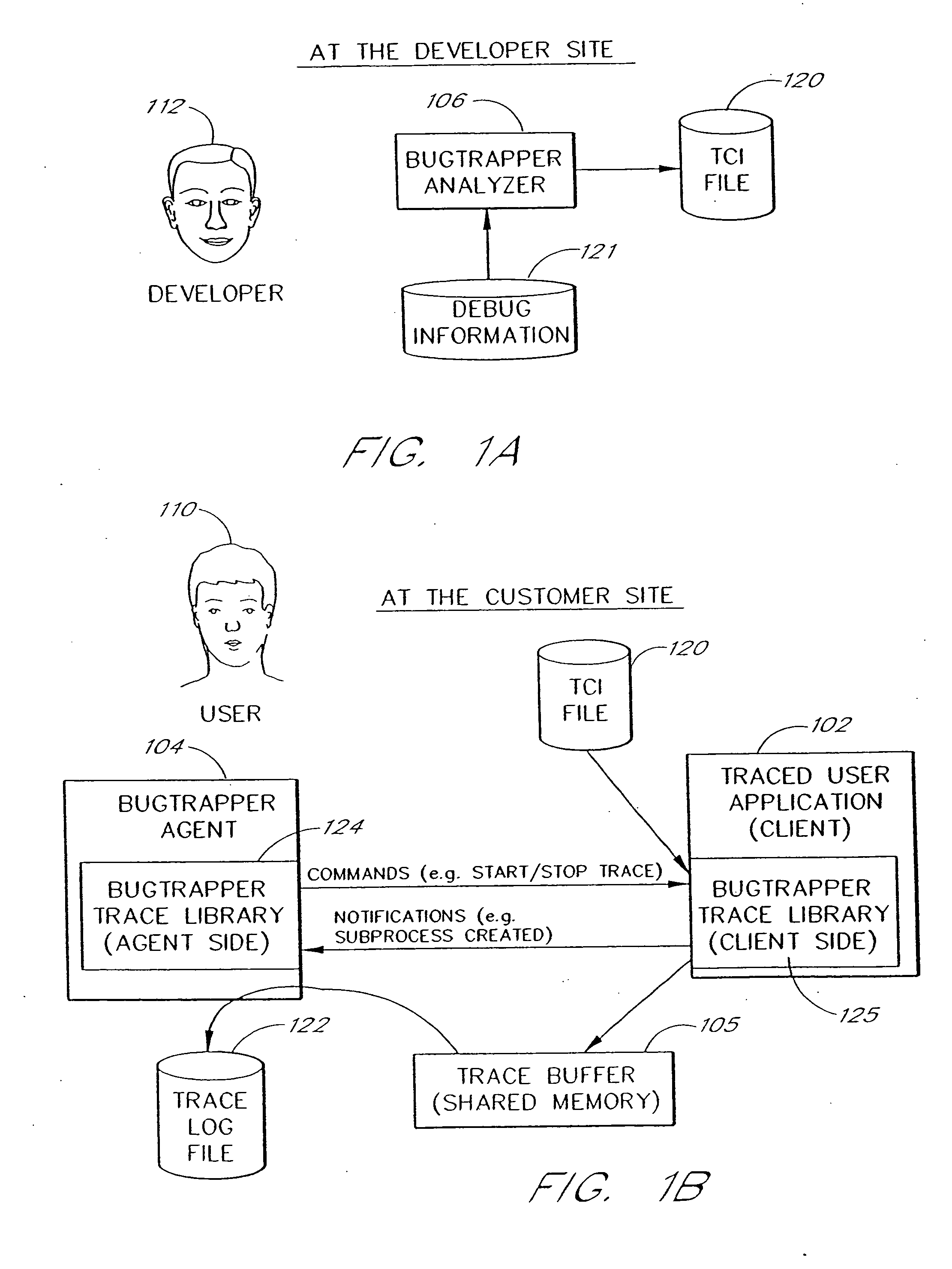
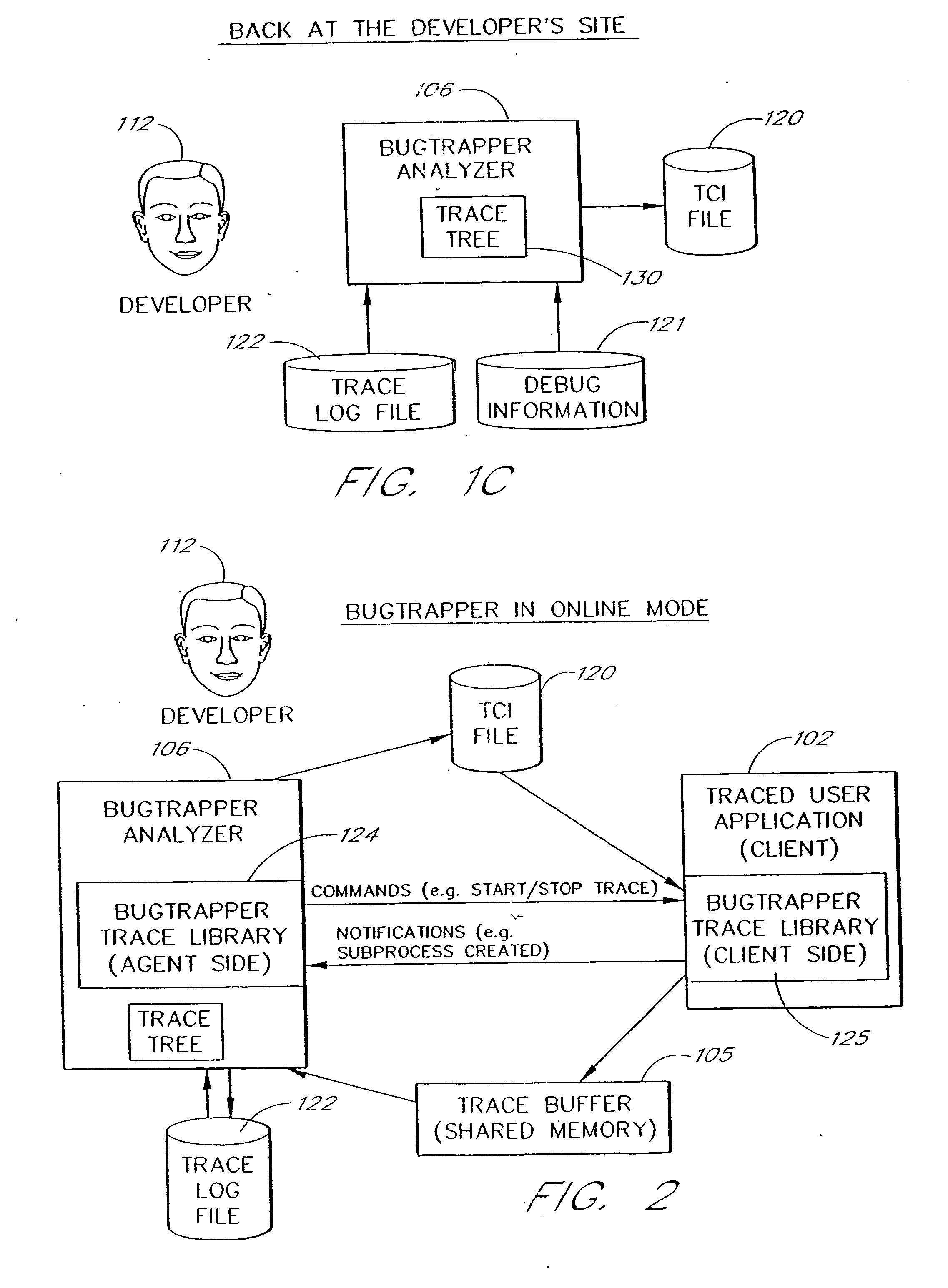
A software system is disclosed which facilitates the process of tracing the execution paths of a program, called the client. The tracing is performed without requiring modifications to the executable or source code files of the client. Trace data collected during the tracing operation is collected according to instructions in a trace options file. At run time, the tracing library attaches to the memory image of the client. The tracing library is configured to monitor execution of the client and to collect trace data, based on selections in the trace options file. Conditional tracing, through the use of triggers and actions taken in response to the triggers, allows the developer to control the tracing operation. The triggers can be conditional triggers in which the corresponding action is taken only if a conditional expression is satisfied. The system can trace multiple threads and multiple processes. The tracing system provides a remote mode and an online mode. In remote mode, the developer sends the trace control information (which can include triggers and corresponding actions) to a remote user site together with a small executable image called the agent that enables a remote customer, to generate a trace file that represents execution of the client application at the remote site. In online mode, the developer can generate trace options (including triggers and corresponding actions), run and trace the client, and display the trace results in near real-time on the display screen during execution of the client program.
Owner:BMC SOFTWARE ISRAEL LTD
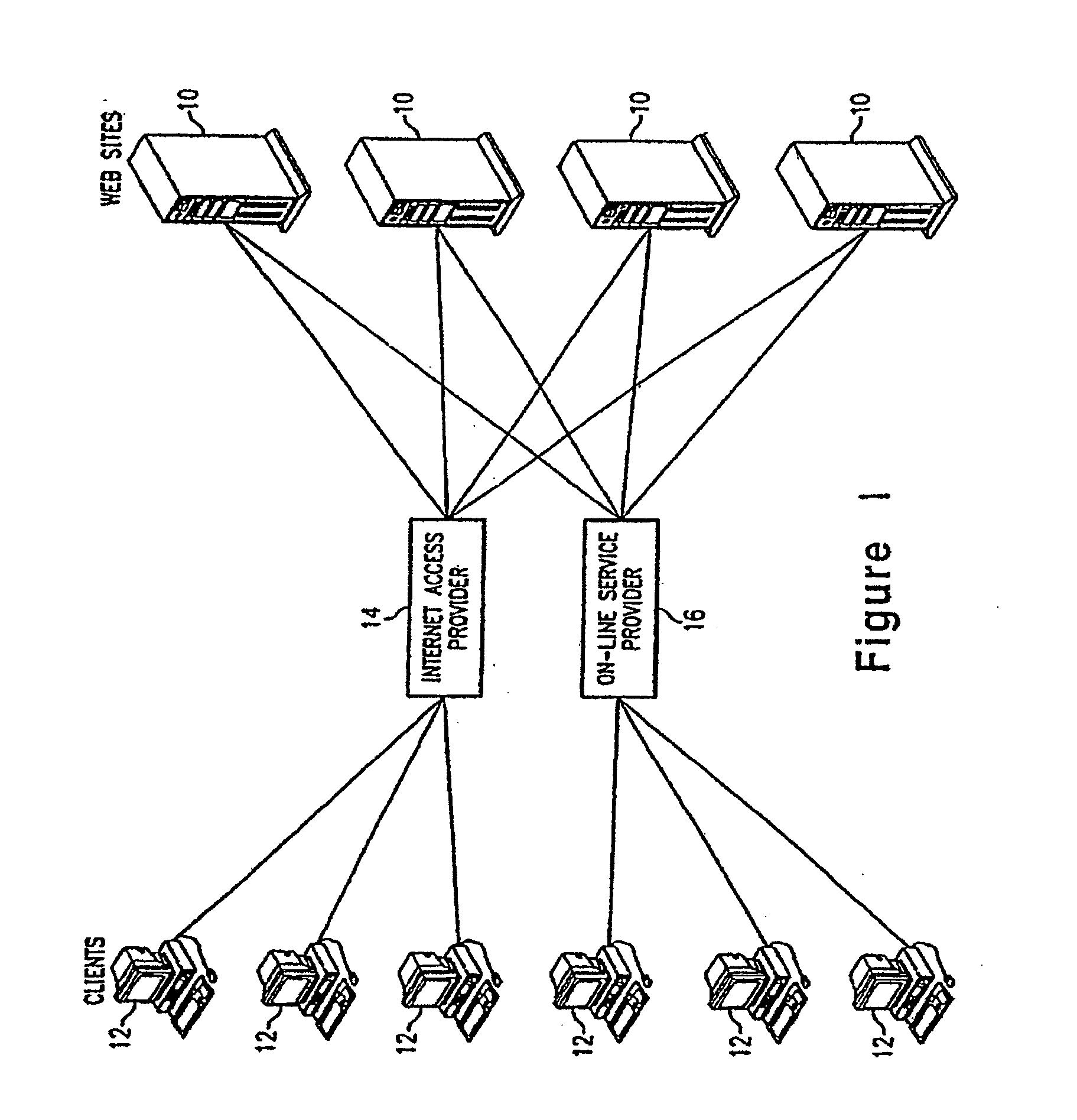
Method and apparatus for tracking client interaction with a network resource
InactiveUS20080086559A1Digital data information retrievalDigital computer detailsTrace fileClient-side
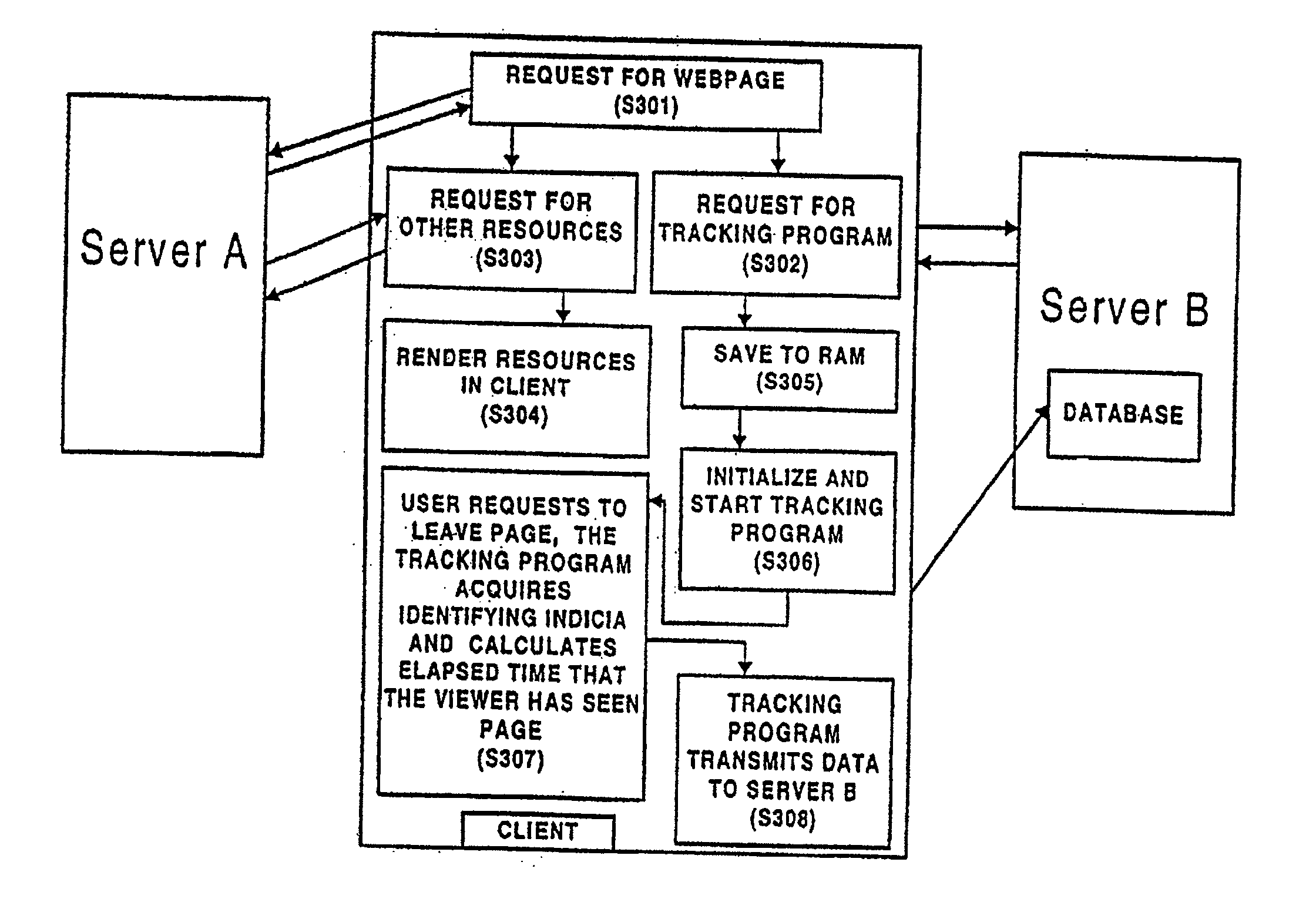
A method for monitoring client interaction with a resource downloaded from a server in a computer network includes the steps of using a client to specify an address of a resource located on a first server, downloading a file corresponding to the resource from the first server in response to specification of the address, using the client to specify an address of a first executable program located on a second server, the address of the first executable program being embedded in the file downloaded from the first server, the first executable program including a software timer for monitoring the amount of time the client spends interacting with and displaying the file downloaded from the first server, downloading the first executable program from the second server to run on the client so as to determine the amount of time the client interacts with the file downloaded from the first server, using a server to acquire client identifying indicia from the client, and uploading the amount of time determined by the first executable program to a third server. The first executable program may also monitor time, keyboard events, mouse events, and the like, in order to track choices and selections made by a user in the file, and may execute upon the occurrence of a predetermined event, as well as monitoring or determining the amount of information downloaded by the client. The monitored information and client identifying indicia is stored on a database in a server for use in analysis and for automatically serving out files assembled according to user interests and preferences.
Owner:DAVIS OWEN +1
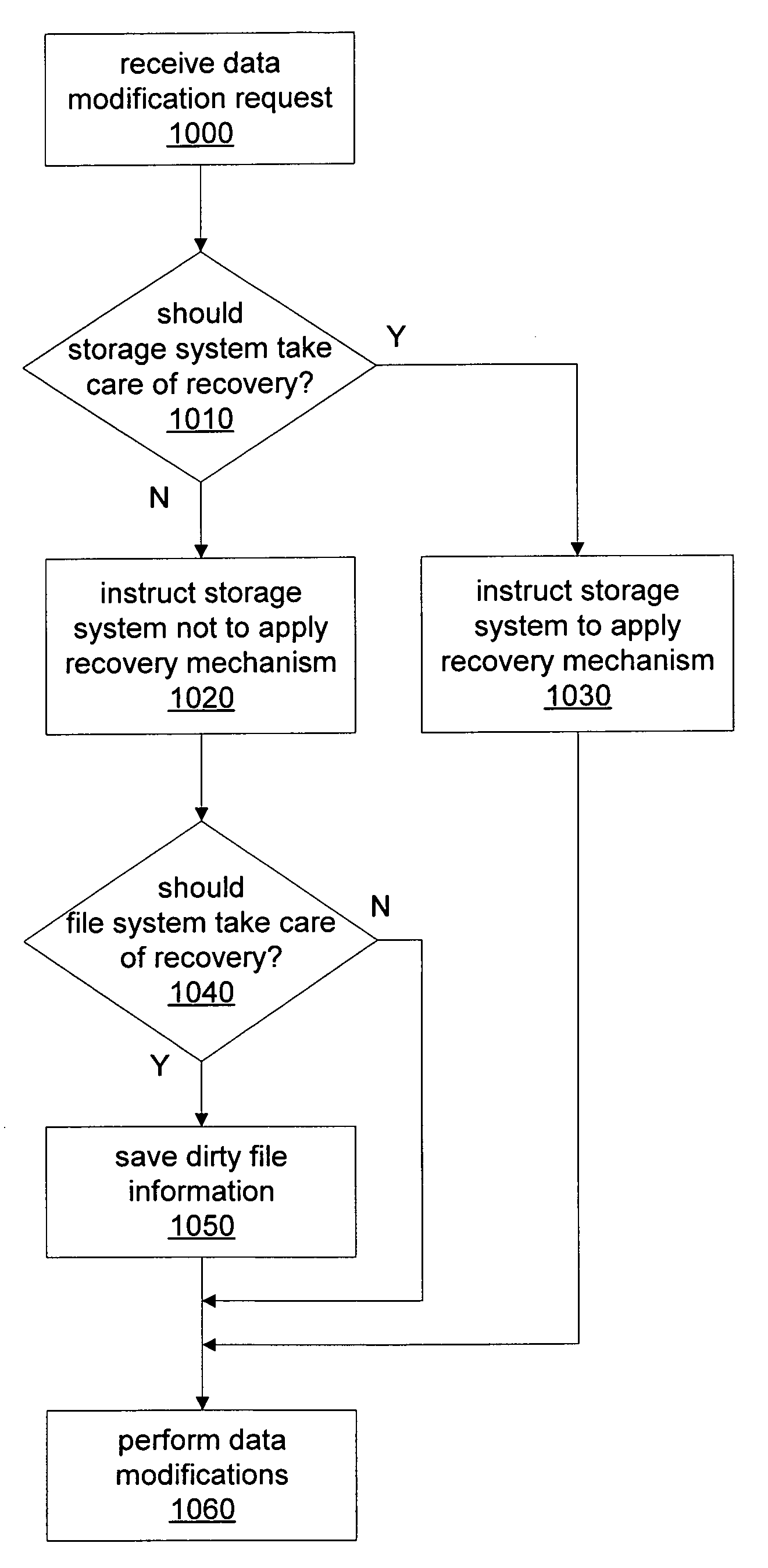
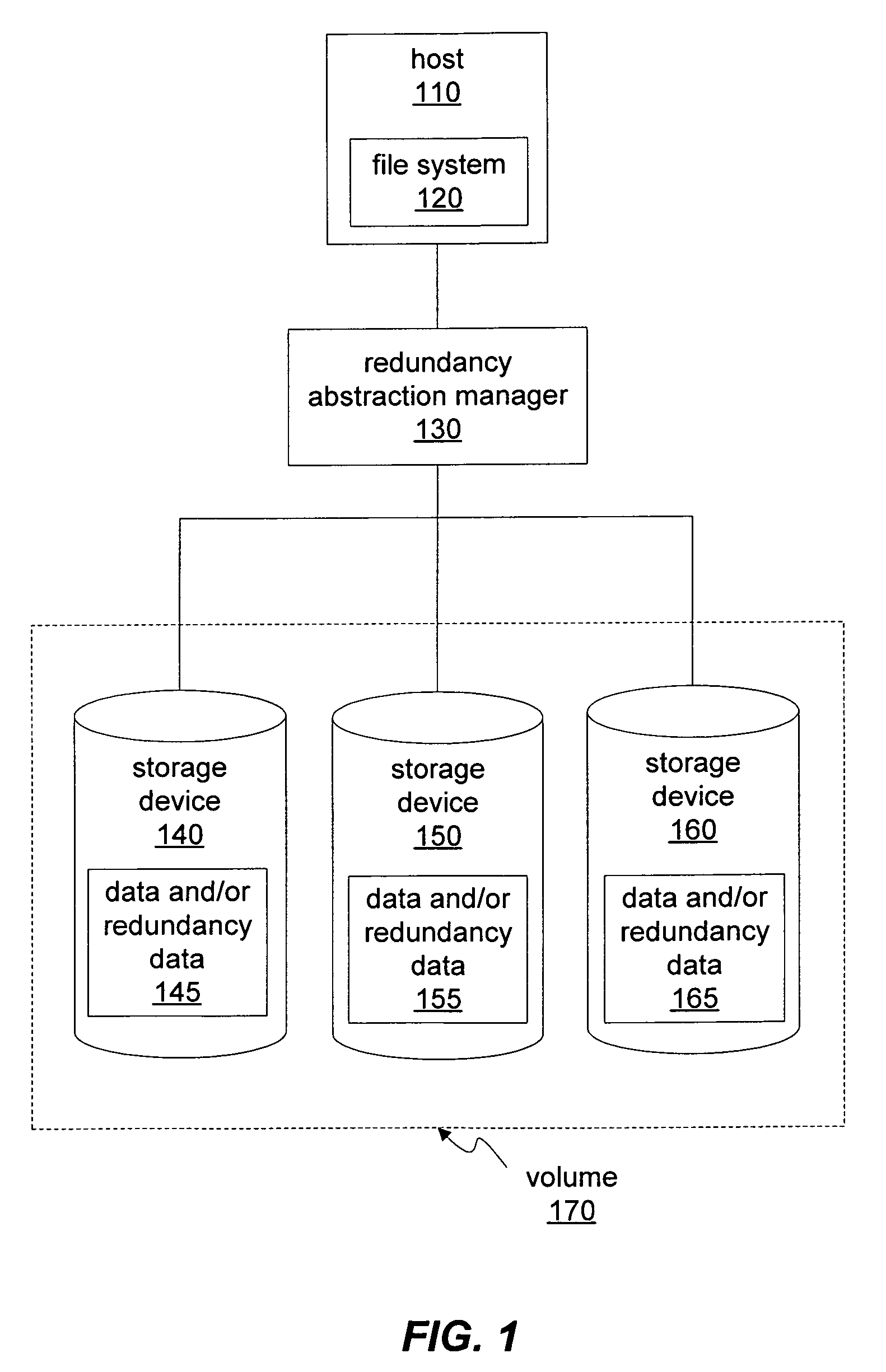
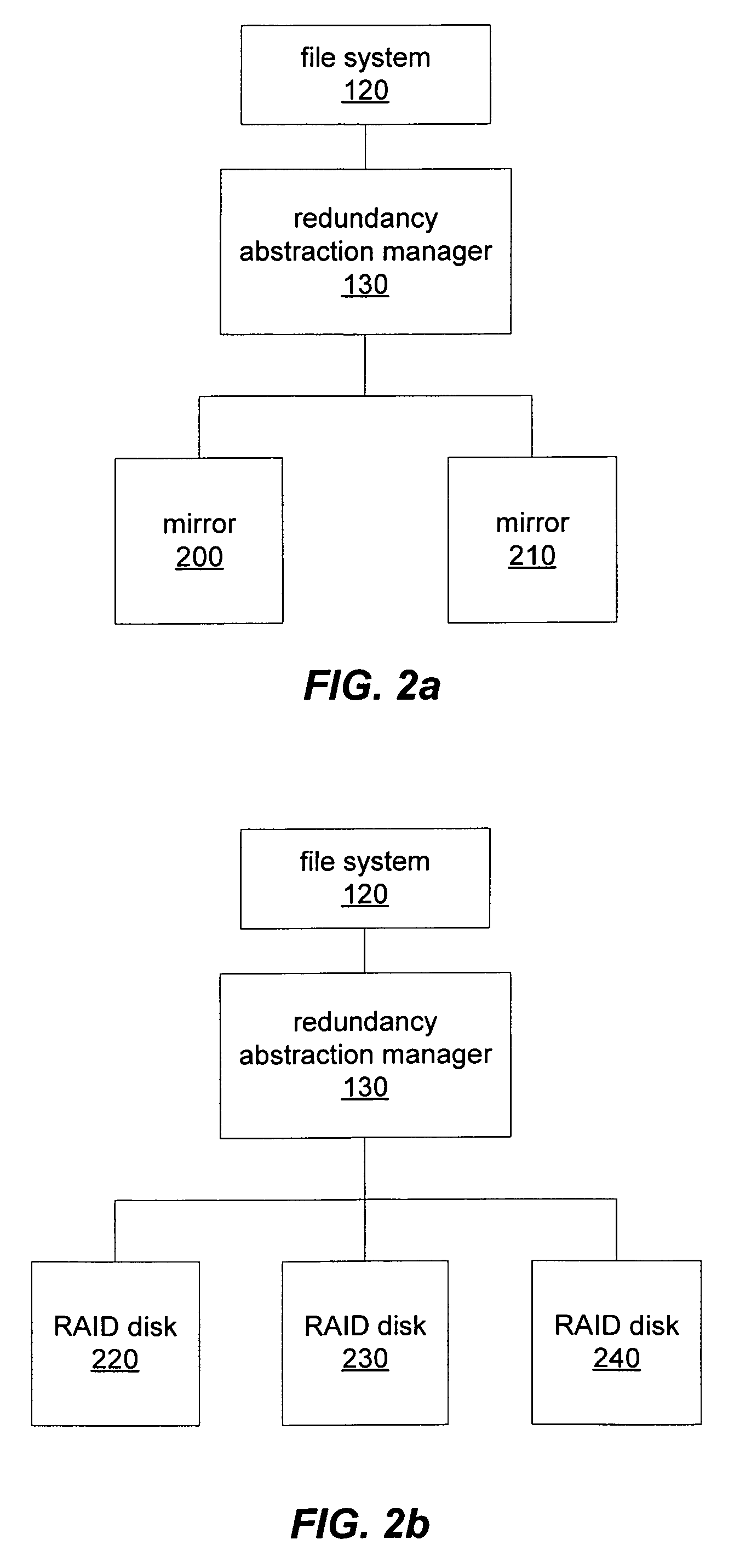
System and method for redundant storage consistency recovery
ActiveUS7415488B1Reduce amountDigital data processing detailsSpecial data processing applicationsFile systemTrace file
A file system may selectively perform redundancy consistency recovery and synchronization of mirrors and may store dirty file information in a log or journal that indicates the modification of a file. A file system may update saved dirty file information to indicate successful modification of data across mirrors and may keep track of redundancy consistency recovery information on a file-by-file basis or may track the redundancy consistency of portions of files. A file system may also instruct an underlying storage system not to track data modifications, possibly selectively for each I / O request. During synchronization the file system may synchronize its log and use saved dirty file information to determine files to be synchronized. A file system may selectively use file system logging for individual data modification requests and may expose an API allowing applications to specify a redundancy consistency mechanism.
Owner:SYMANTEC OPERATING CORP
System and method for conditional tracing of computer programs
ActiveUS8312435B2Easy to identifyImprove isolationError detection/correctionSpecific program execution arrangementsSource code fileSoftware system
A software system is disclosed which facilitates the process of tracing the execution paths of a program, called the client. The tracing is performed without requiring modifications to the executable or source code files of the client. Trace data collected during the tracing operation is collected according to instructions in a trace options file. At run time, the tracing library attaches to the memory image of the client. The tracing library is configured to monitor execution of the client and to collect trace data, based on selections in the trace options file. Conditional tracing, through the use of triggers and actions taken in response to the triggers, allows the developer to control the tracing operation. The triggers can be conditional triggers in which the corresponding action is taken only if a conditional expression is satisfied. The system can trace multiple threads and multiple processes. The tracing system provides a remote mode and an online mode. In remote mode, the developer sends the trace control information (which can include triggers and corresponding actions) to a remote user site together with a small executable image called the agent that enables a remote customer, to generate a trace file that represents execution of the client application at the remote site. In online mode, the developer can generate trace options (including triggers and corresponding actions), run and trace the client, and display the trace results in near real-time on the display screen during execution of the client program.
Owner:BMC SOFTWARE ISRAEL LTD
Method for processing data based on the data context
A method for managing data in a semiconductor processing environment. Raw data is collected during a process. Also, trace file data and process log file data are received. The raw data is synchronized with the trace file data and process log file data to create wafer data summary data is calculated from the raw data and a file is created containing the wafer data and the summary data.
Owner:TOKYO ELECTRON LTD
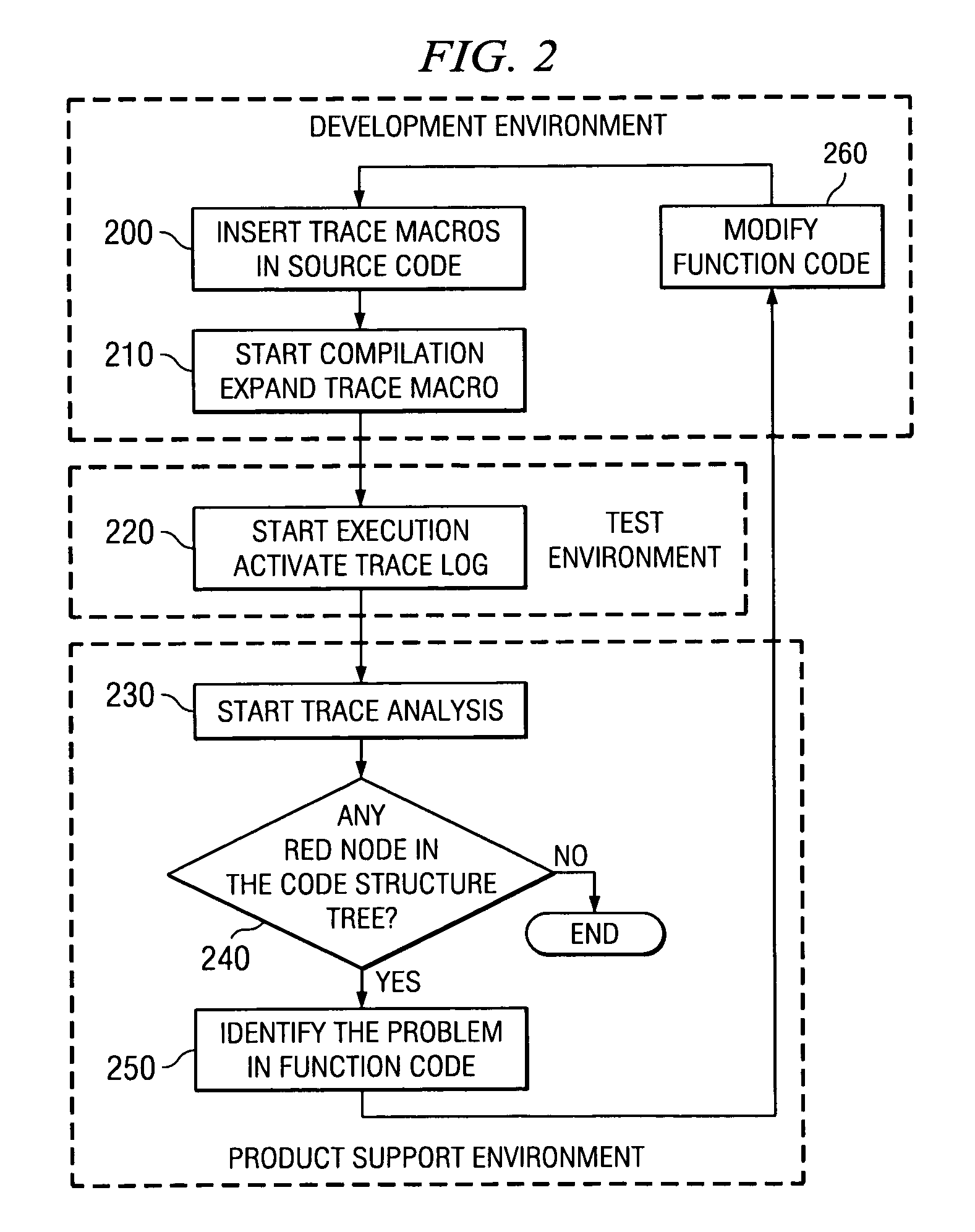
Method and system for tracing and displaying execution of nested functions
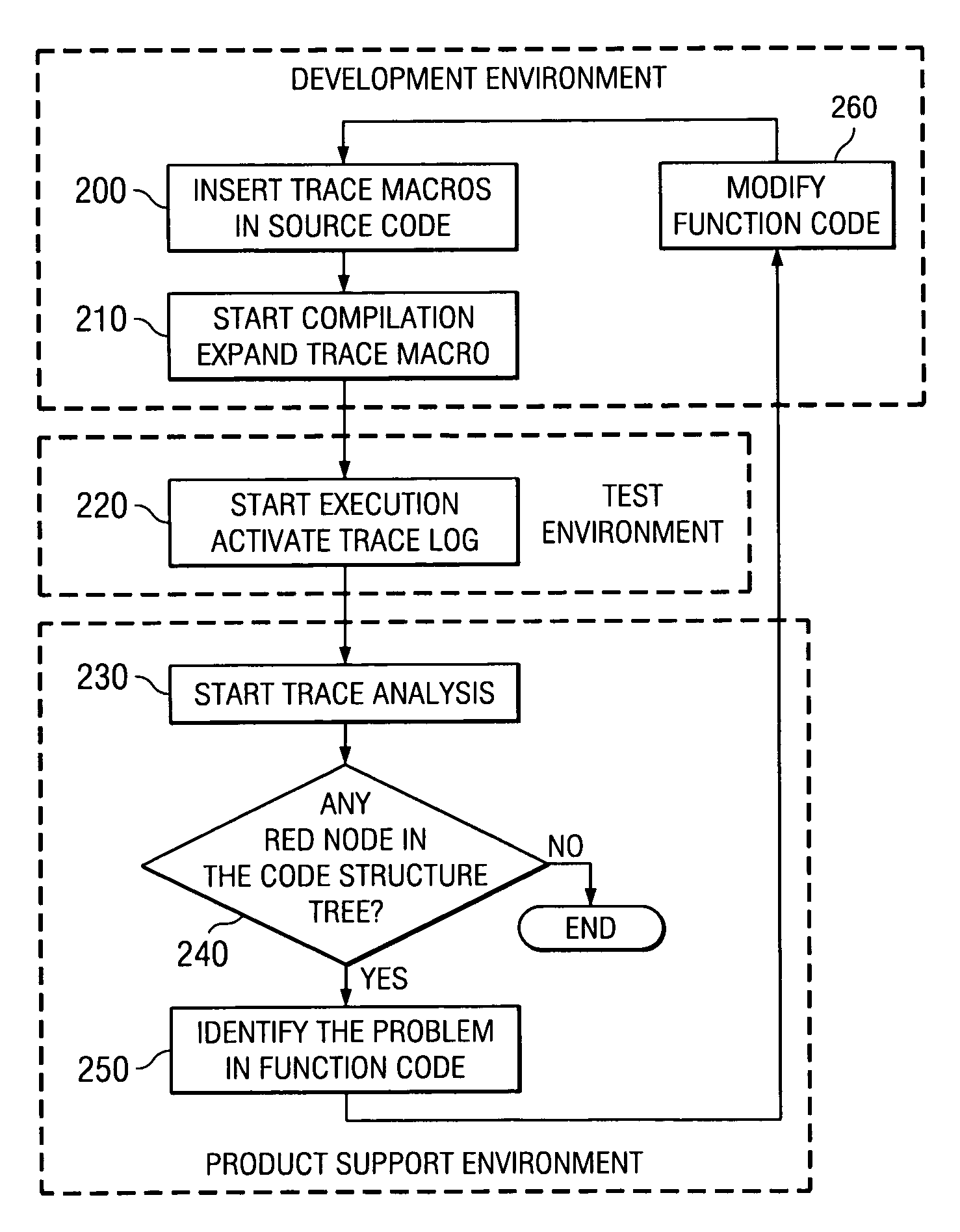
InactiveUS7120901B2Improve productivityMinimize timeSoftware testing/debuggingSpecific program execution arrangementsGraphicsGraphical user interface
A method and system for tracing the failing or successful execution of nested functions coded with return codes in a thread during its execution. The method comprises an ENTRY and EXIT trace macro to mark the beginning and the end of execution of the function, a TRACE macro to record messages and program variable values, and a QUIT macro marking the failing execution of the corresponding function. Using a Graphical User Interface, an interactive trace analyzer reads the trace file and displays the tree structure of the nested functions and marks, by using different colors, the success or failure of each of them. The trace analyzer utilities help the user to quickly identify the error in the source code corresponding to a function with a failing execution.
Owner:IBM CORP
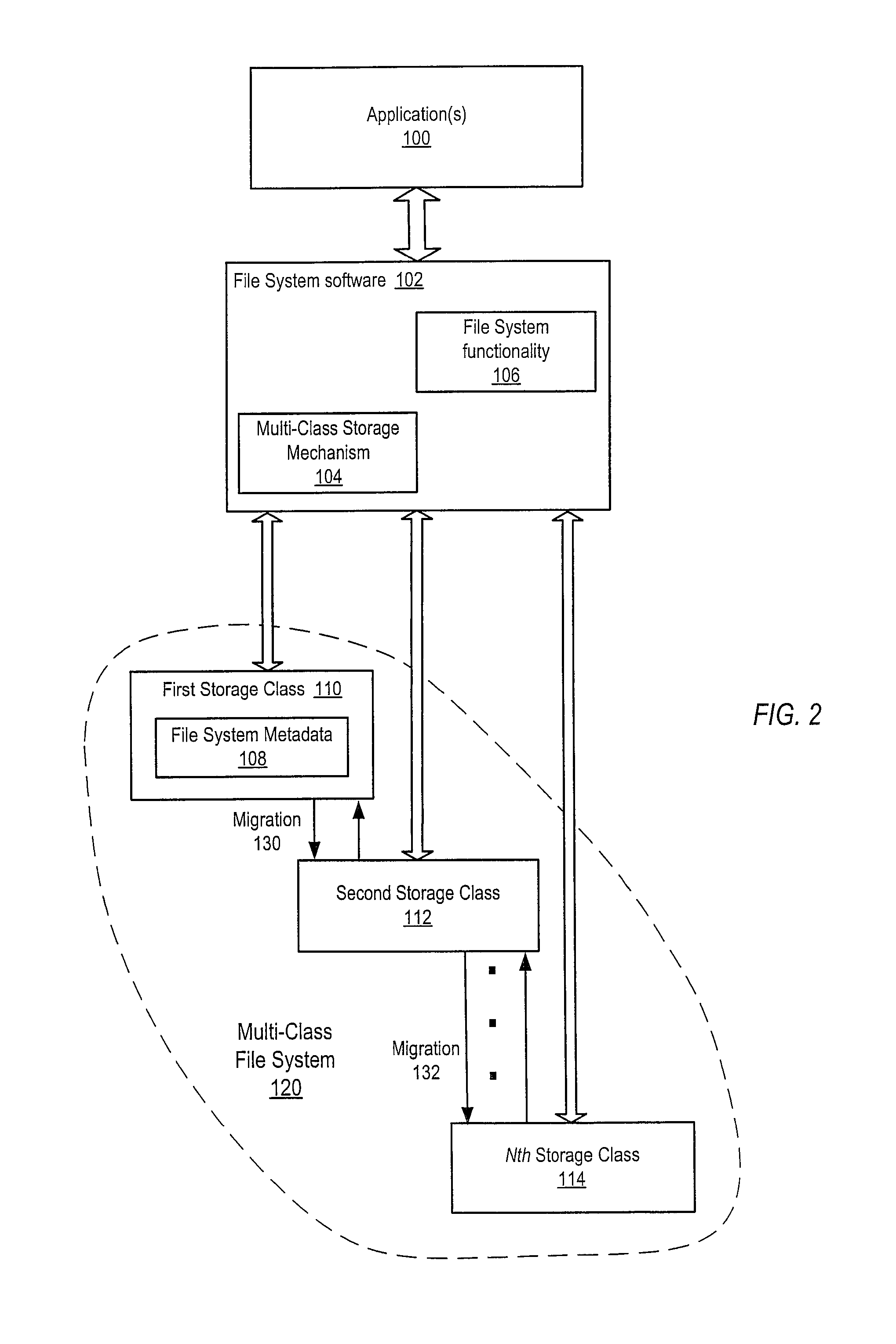
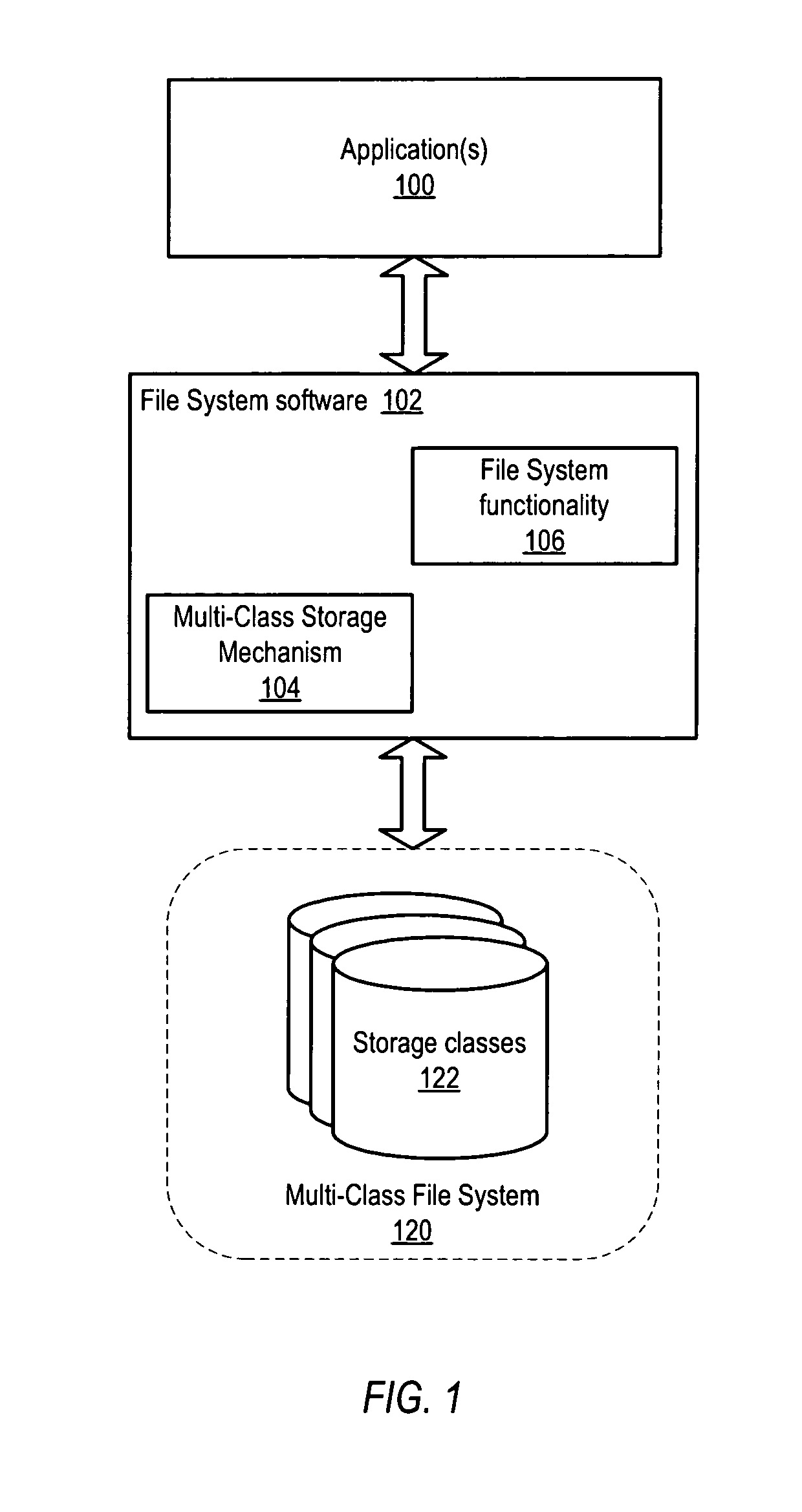
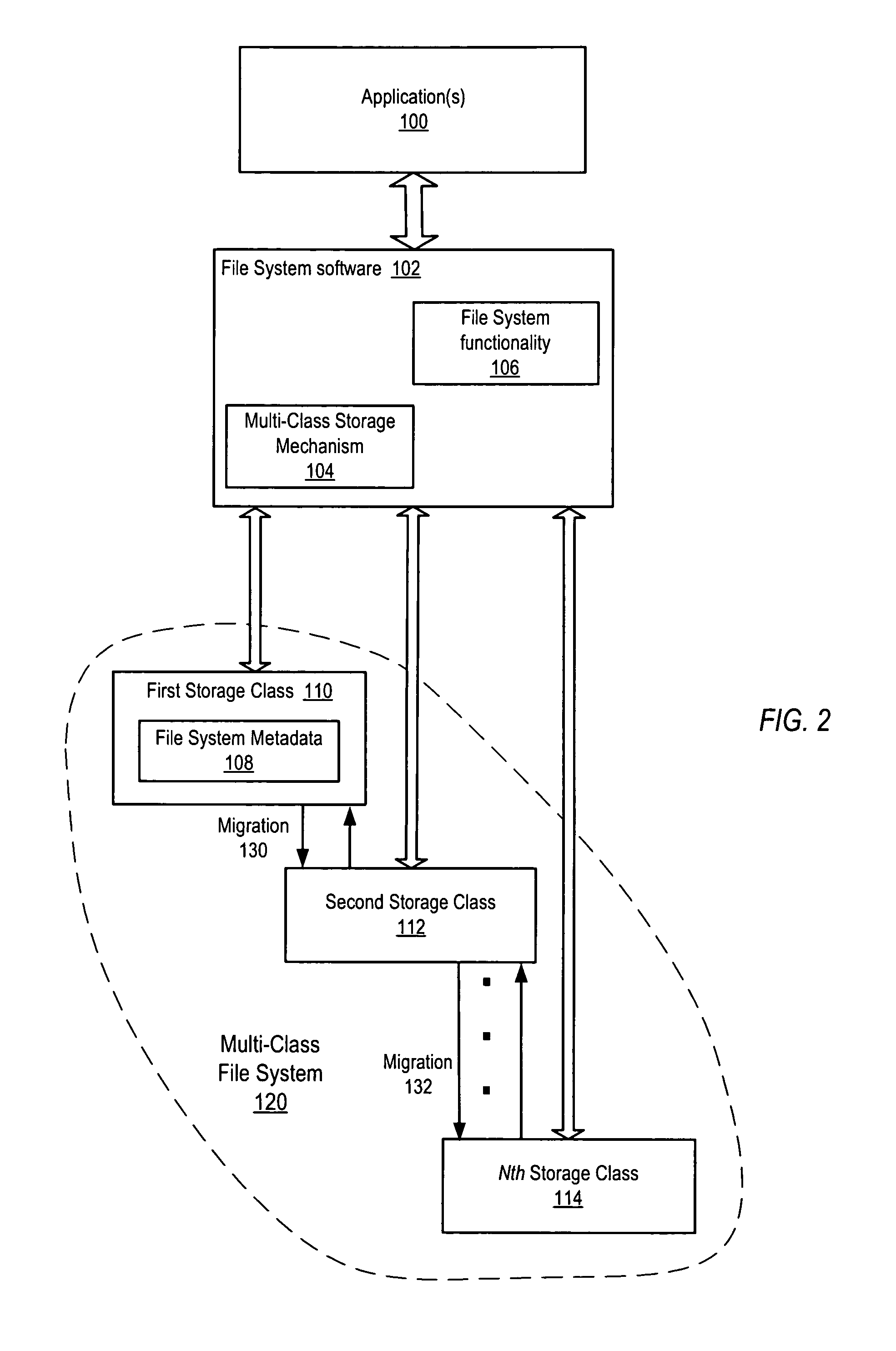
Dynamic storage mechanism
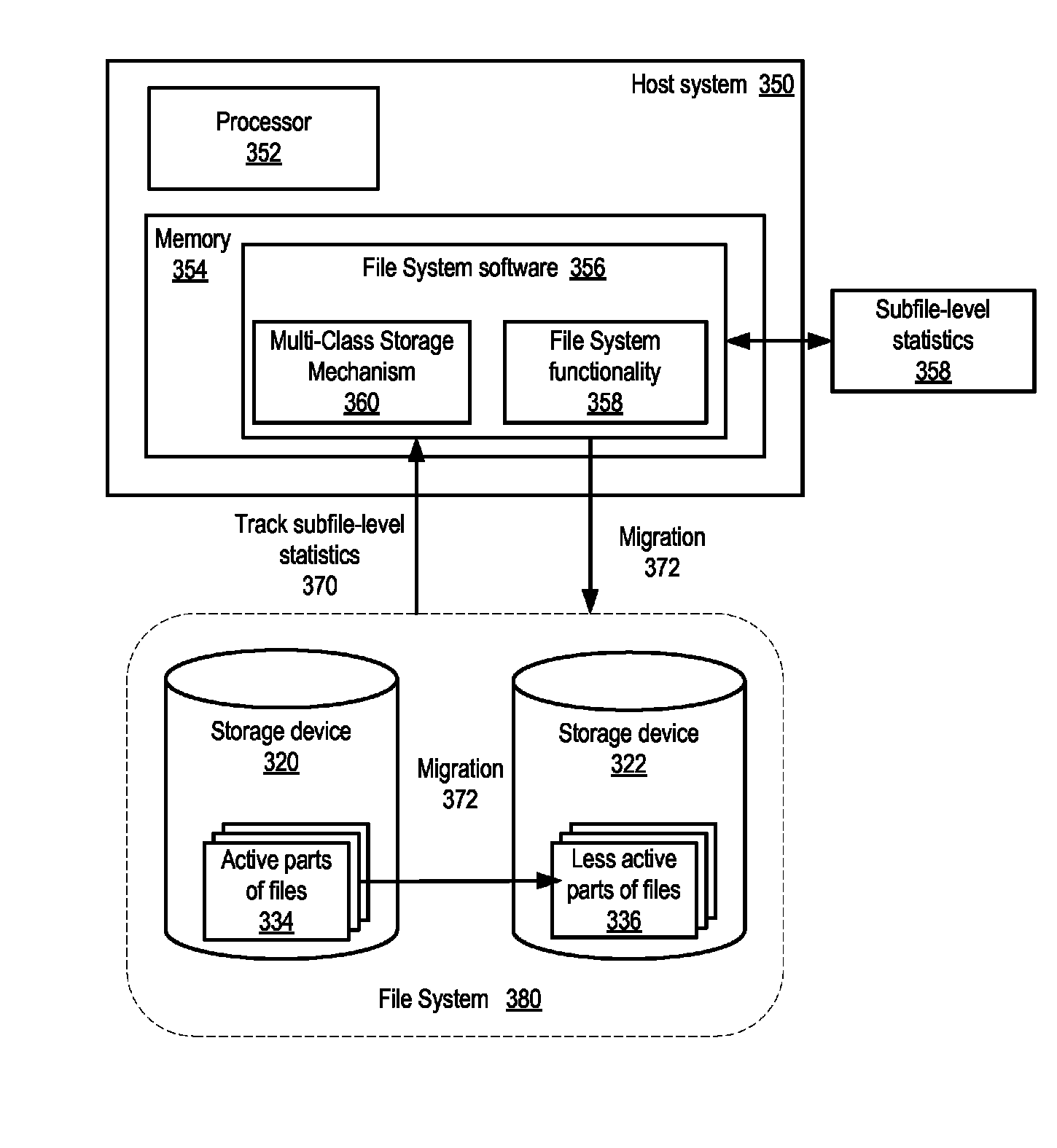
ActiveUS8280853B1Reduce storage costs without compromising performanceLess expensiveDigital data information retrievalDigital data processing detailsTimestampTrace file
System and method for tracking statistics at the subfile level and transparently placing or migrating inactive or less active blocks of data to other storage devices. Embodiments may provide mechanisms to track statistics at the subfile level of files including, but not limited to, database files, and to transparently place or migrate inactive or less active blocks of data of the files from higher-performing, typically more expensive, storage to lower-performing, typically less expensive, storage, while placing or migrating active blocks of data of the files to higher-performing storage, based on the subfile-level statistics rather than on file-level timestamps. In some embodiments, knowledge of file structure (e.g., database file structure), for example knowledge of database partitions with header blocks and data blocks in databases using data partitioning, may be used to separate more active and less active blocks of data of files onto storage with different performance and / or other characteristics.
Owner:VERITAS TECH
Apparatus and method for cataloging symbolic data for use in performance analysis of computer programs
InactiveUS6988263B1Hardware monitoringSoftware testing/debuggingTrace fileTheoretical computer science
An apparatus and method for cataloging symbolic data for use in performance analysis of computer programs is provided. The apparatus and method stores symbolic data for loaded modules during or shortly after a performance trace and utilizes the stored symbolic data when performing a performance analysis at a later time. A merged symbol file is generated for a computer program, or application, under trace. The merged symbol file contains information useful in performing symbolic resolution of address information in trace files for each instance of a module. During post processing of the trace information generated by a performance trace of a computer program, symbolic information stored in the merged symbol file is compared to the trace information stored in the trace file. The correct symbolic information in the merged symbol file for loaded modules is identified based a number of validating criteria. The correct symbolic information for the loaded modules may then be stored as an indexed database that is used to resolve address information into corresponding symbolic information when providing the trace information to a display for use by a user.
Owner:IBM CORP
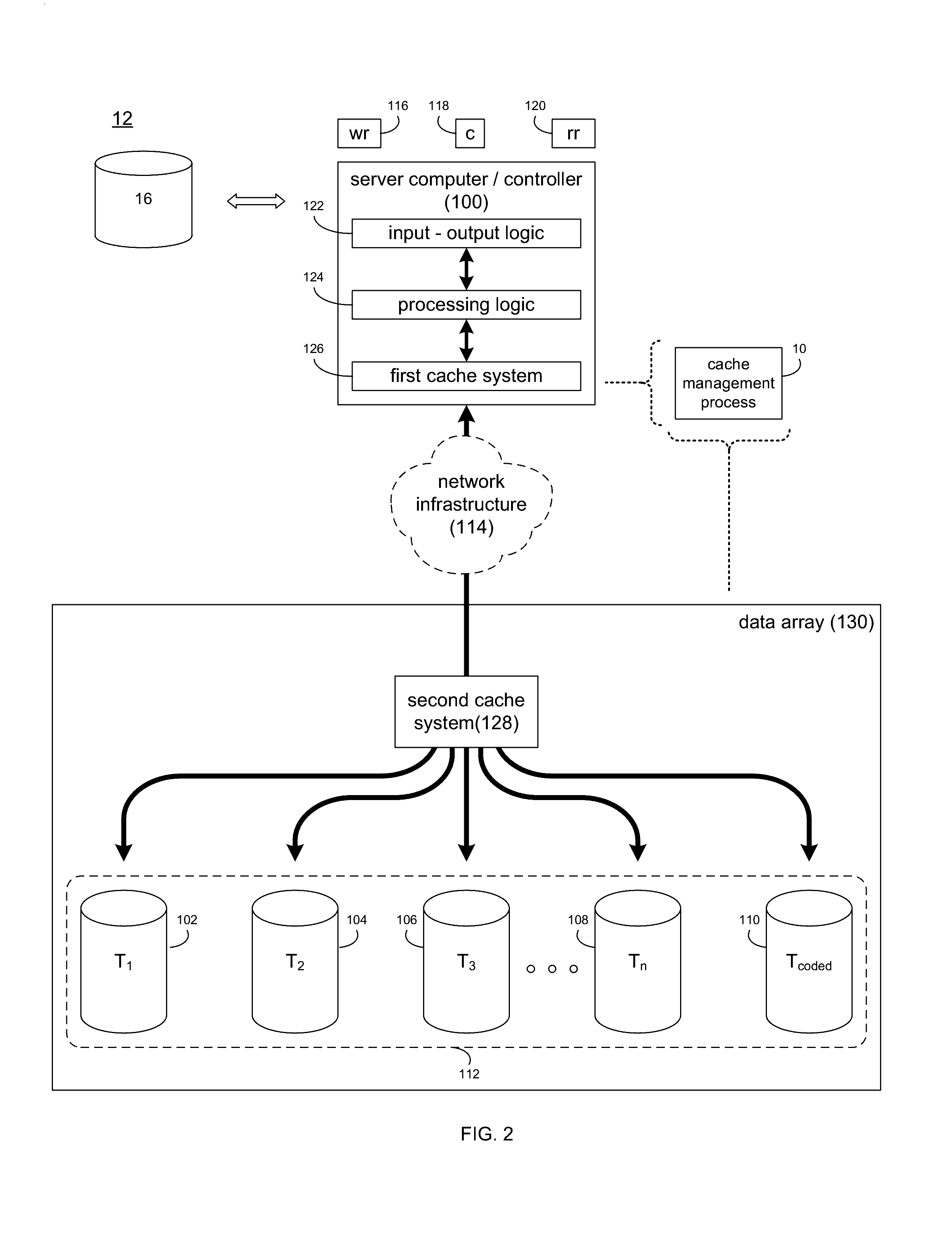
System and method for cache management
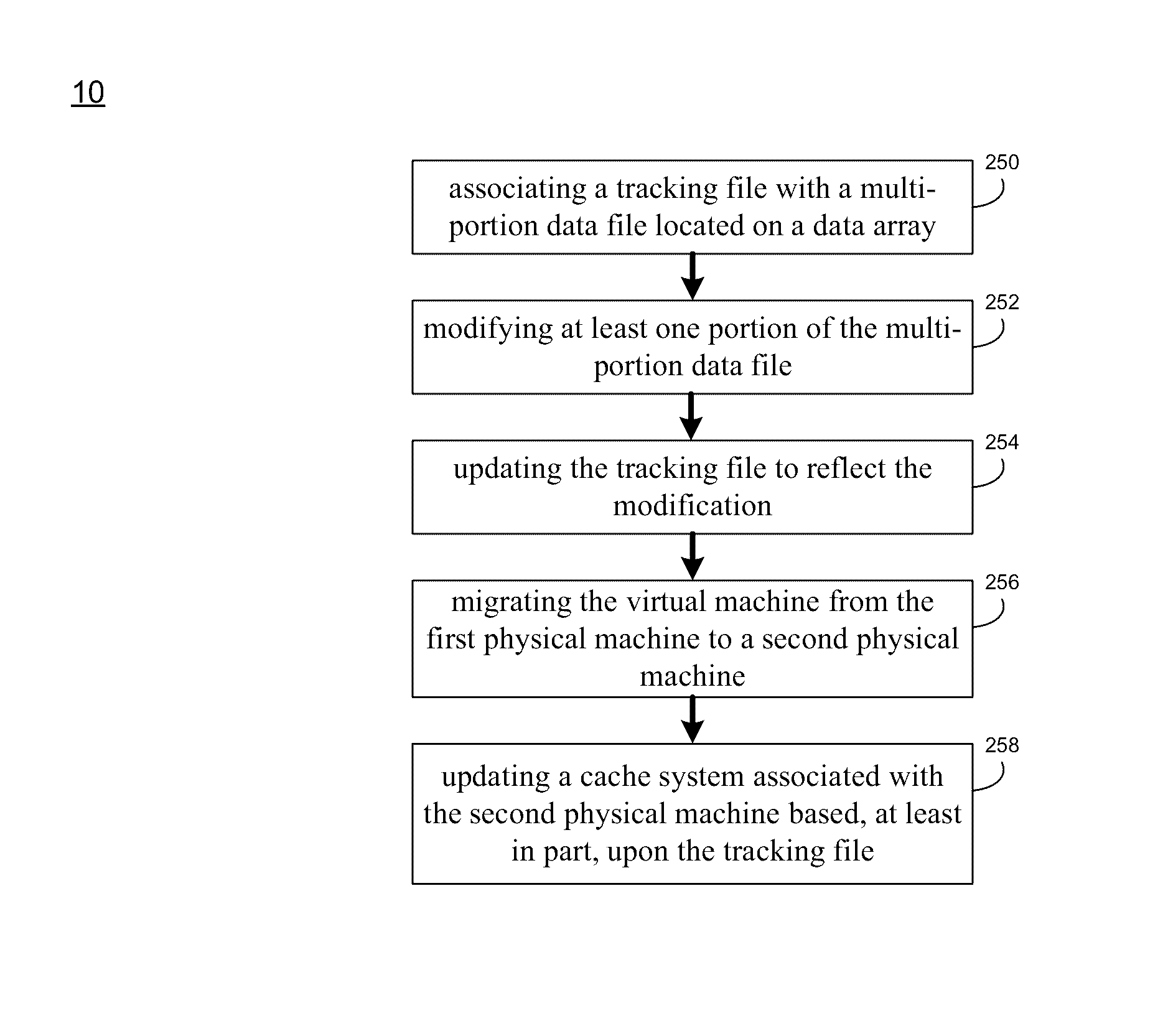
ActiveUS9507732B1Memory architecture accessing/allocationError detection/correctionTrace fileData file
A method, computer program product, and computing system for associating a tracking file with a multi-portion data file located on a data array. The tracking file is configured to monitor the status of each portion of the multi-portion data file. At least one portion of the multi-portion data file is modified via a virtual machine executed on a first physical machine. The tracking file is updated to reflect the modification of the at least one portion of the multi-portion data file.
Owner:EMC IP HLDG CO LLC
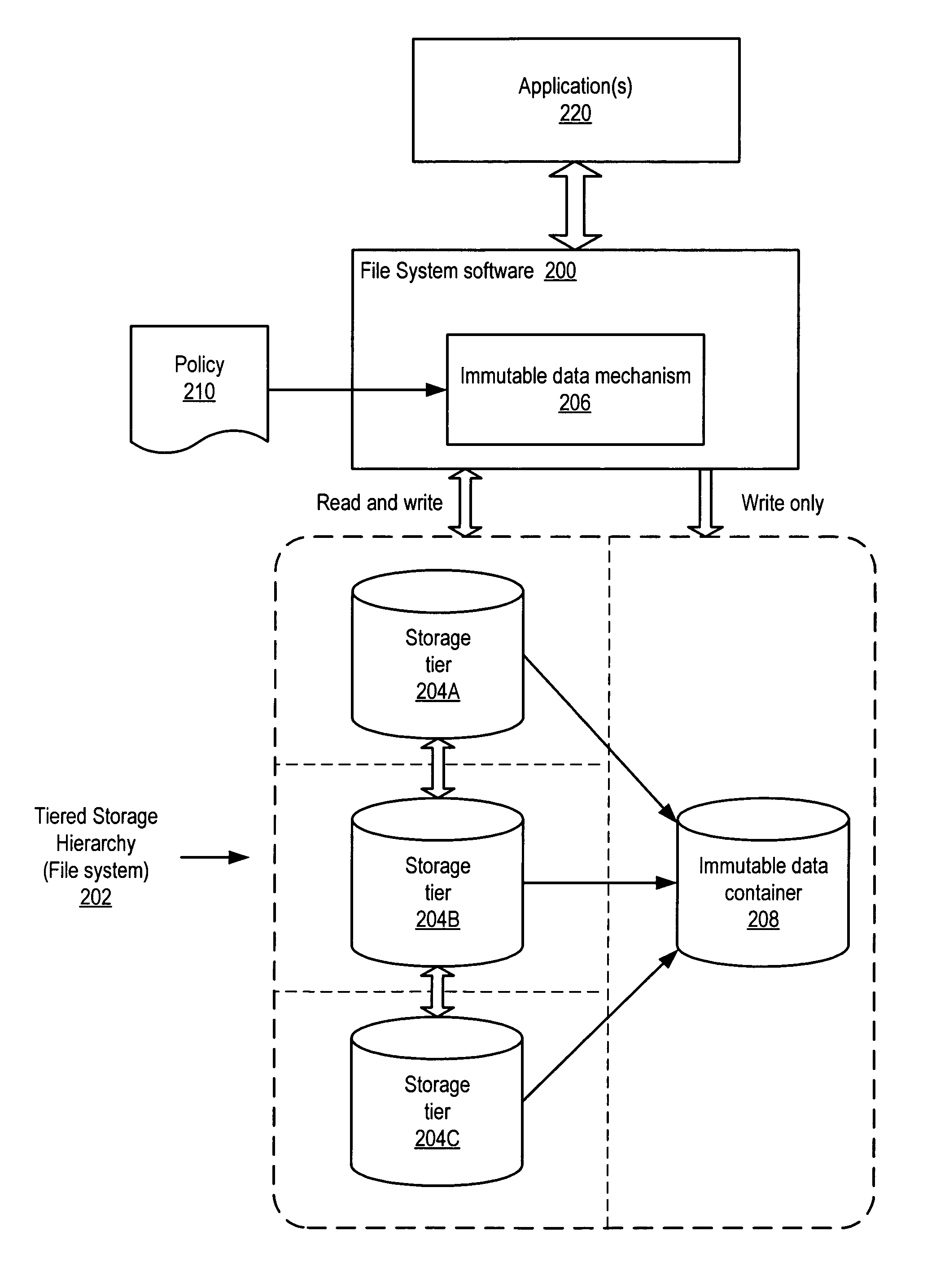
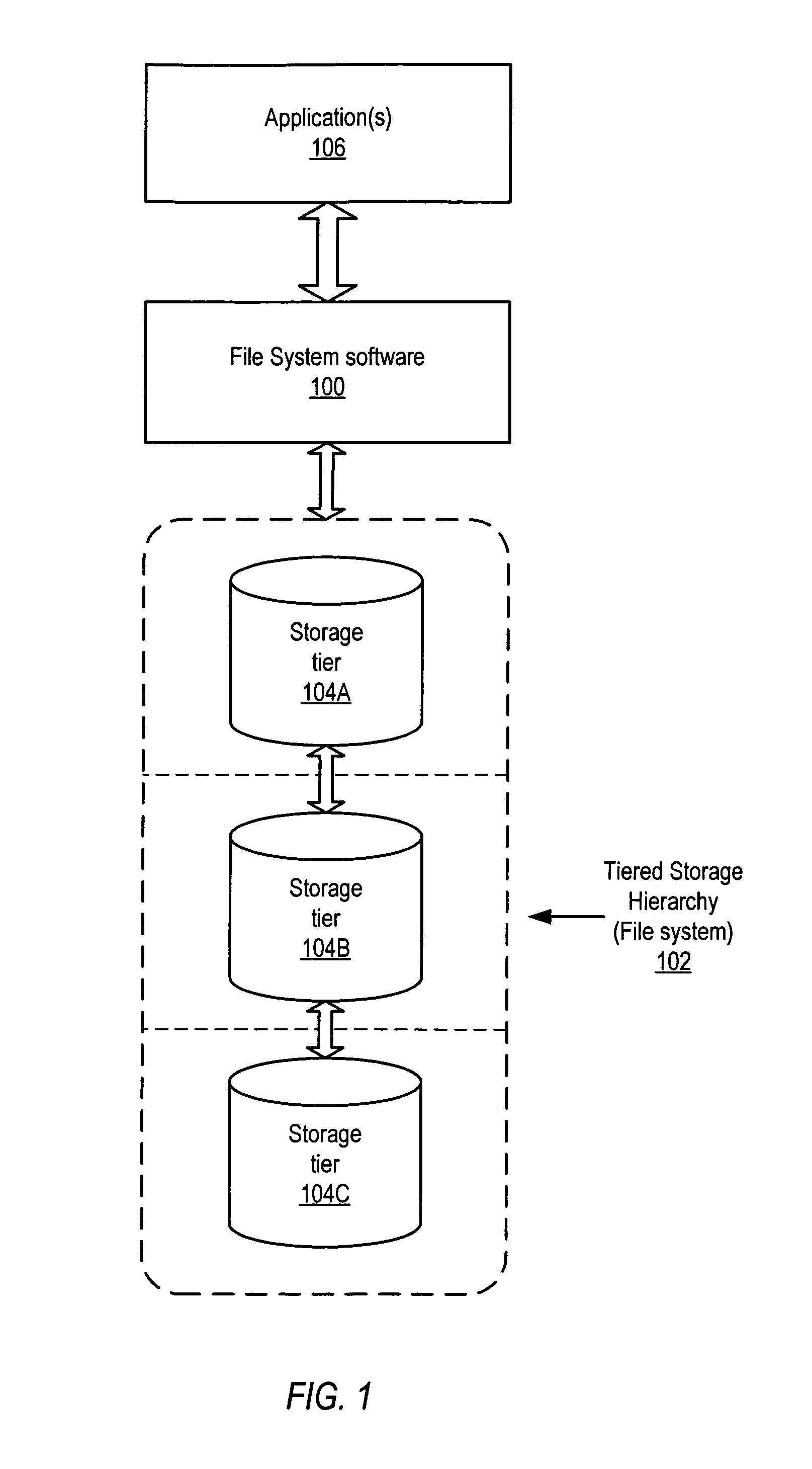
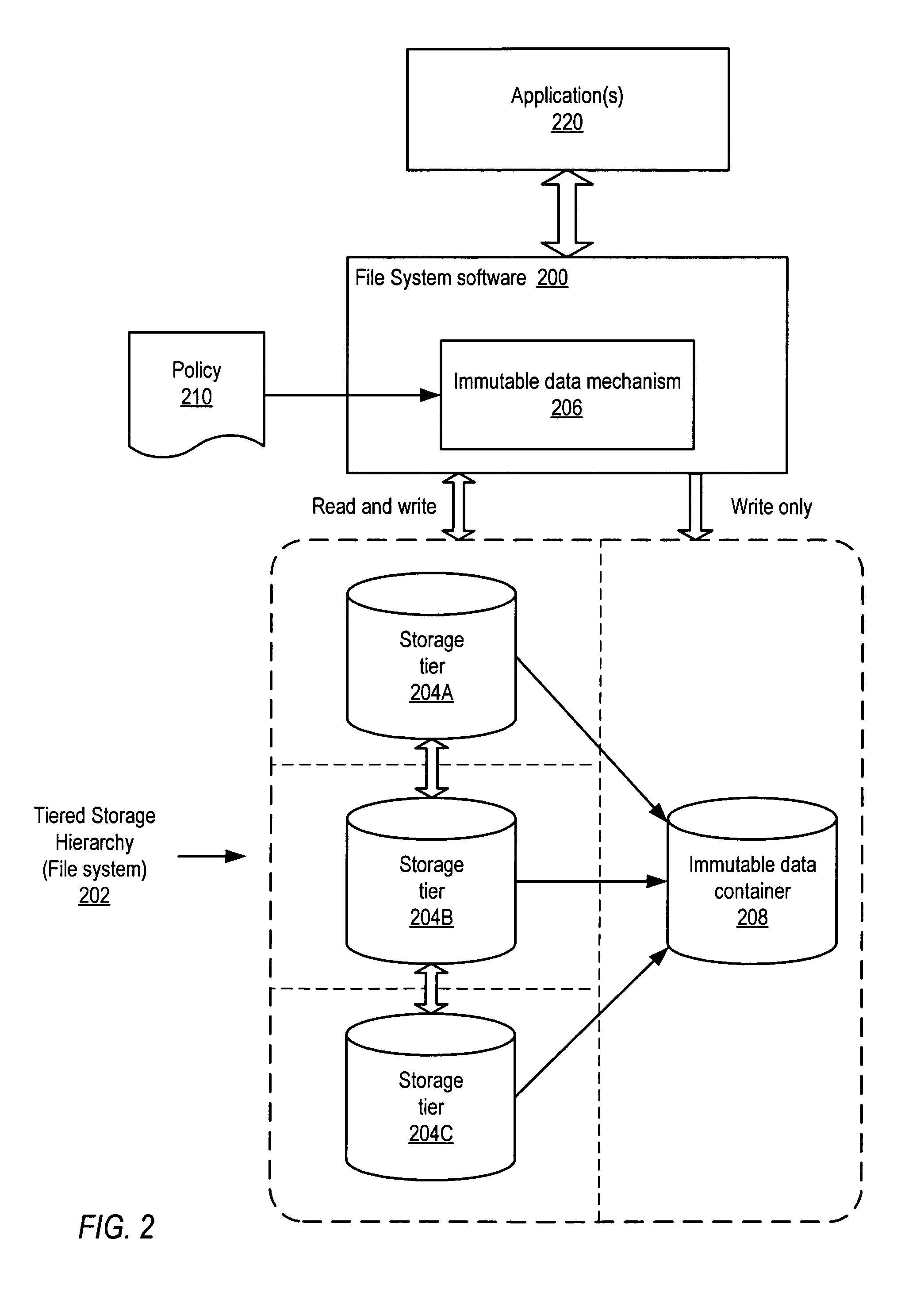
Immutable data containers in tiered storage hierarchies
ActiveUS8055622B1Digital data information retrievalDigital data processing detailsTrace fileFile system
System and method for providing immutable data containers in tiered storage hierarchies. Embodiments may allow fulfillment of regulatory requirements for retaining certain data through management of a user-defined policy. The policy may specify what data in the file system needs to be stored as immutable data to the immutable data container in the file system. File system data may be tracked, and data specified by the policy may be transparently and automatically stored to the immutable data container within the file system. Updates to the data specified by the policy may also be stored to the immutable data container. This may be performed without overwriting or modifying the earlier version(s) of the data stored to the immutable data container, and thus every version of the data specified by the policy may be stored to and, if necessary, reconstructed from the immutable data container.
Owner:SYMANTEC OPERATING CORP
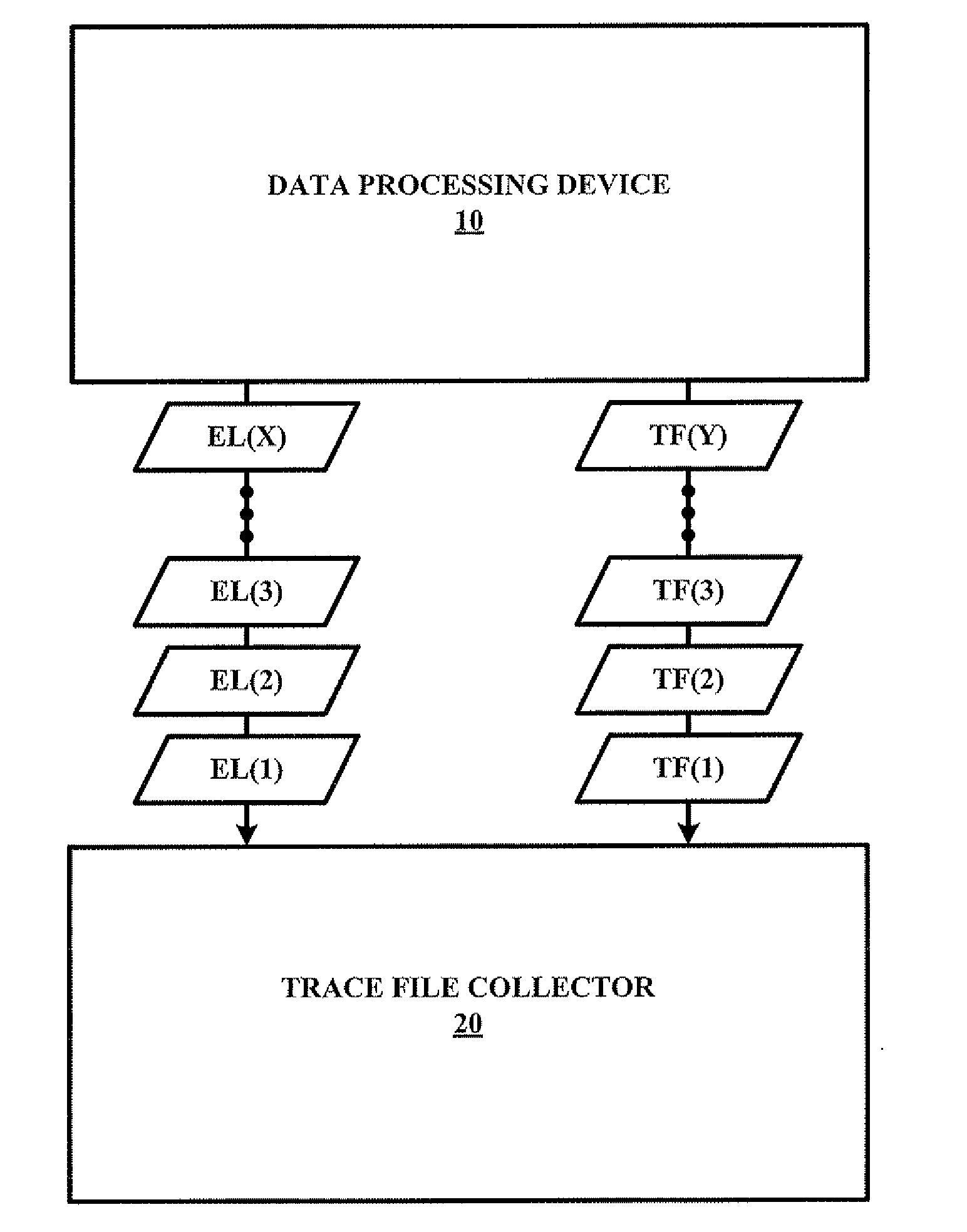
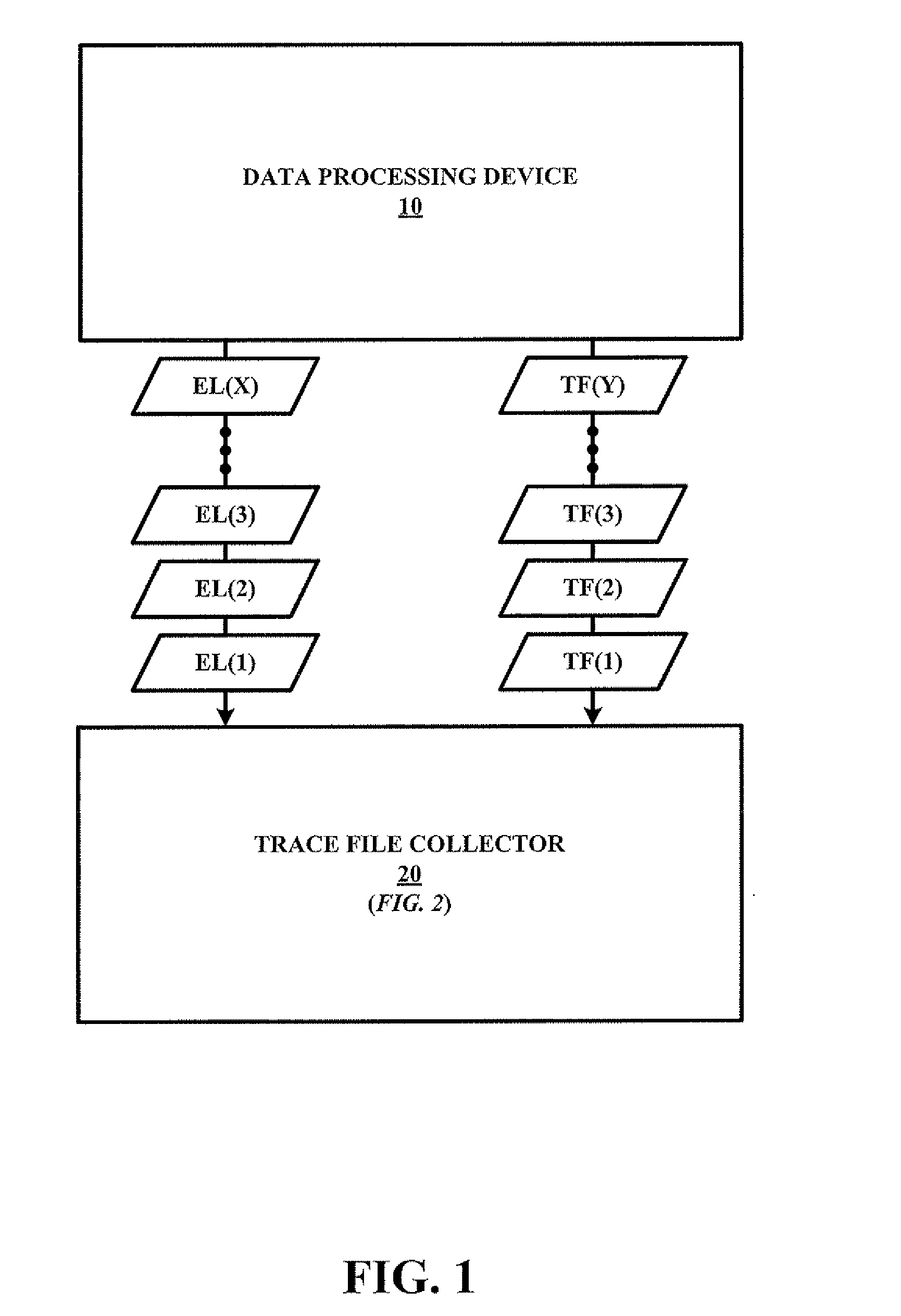
Method and System for a Soft Error Collection of Trace Files
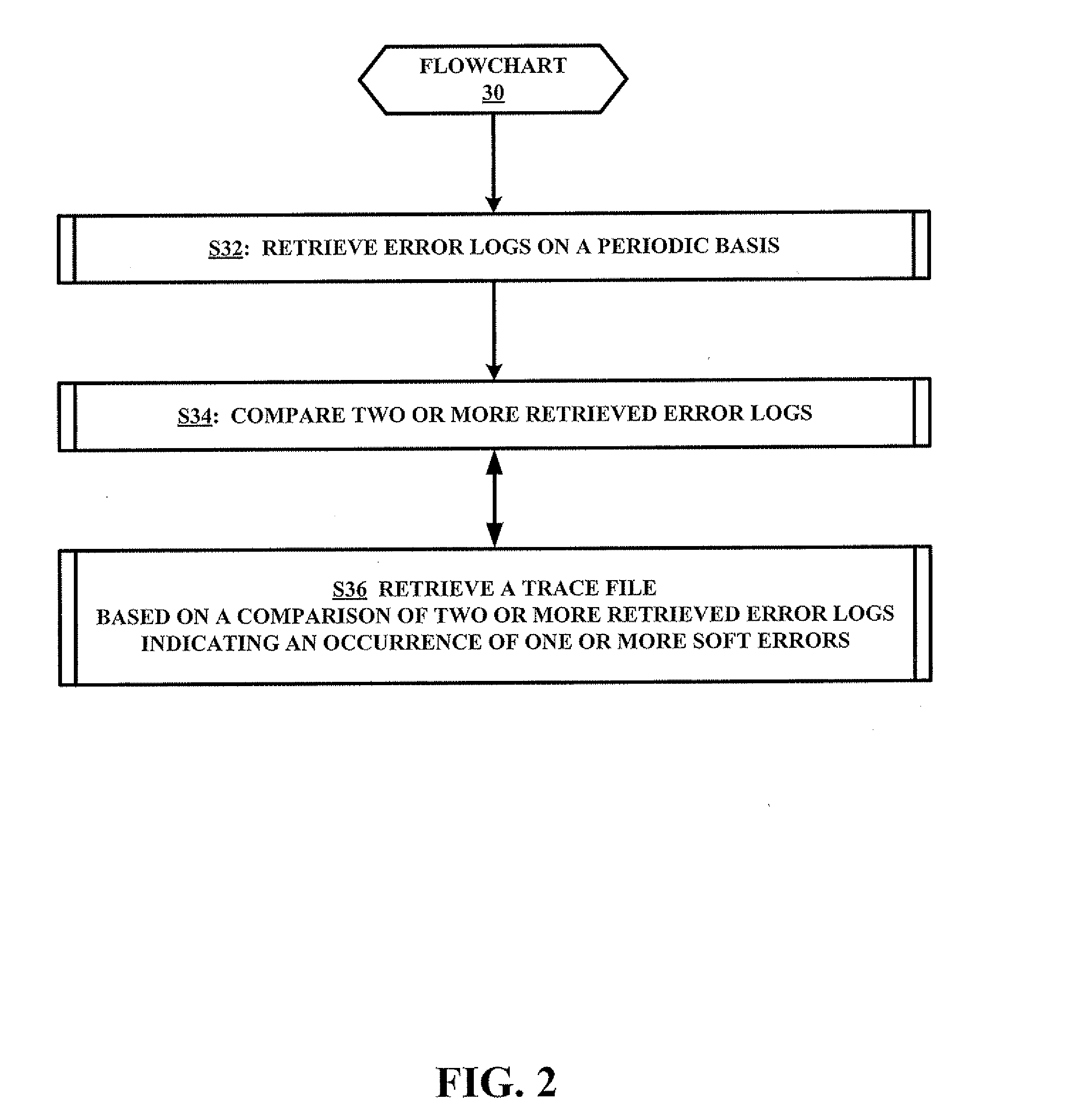
InactiveUS20080086515A1Error detection/correctionSpecial data processing applicationsComputer hardwareCollection system
A trace file collection system for implementing a trace file collection method for a soft error collection of one or more trace files associated with a data processing device. The method involves a periodic retrieval of an error log from the data processing device, a comparison of two or more retrieved error logs, and a retrieval of the trace file(s) from the data processing device based on the comparison of the two or more retrieved error logs indicating an occurrence of one or more soft errors within the data processing device.
Owner:IBM CORP
Method for processing data based on the data context
A method for managing collected data in a semiconductor processing environment. The collected data can include: raw data collected during a process, trace file data received during a process, and process log file data received during a process. The raw data is synchronized with the trace file data and process log file data to create wafer data and summary data, and a file is created containing the wafer data and the summary data.
Owner:TOKYO ELECTRON LTD
Method and System for Diagnosing an Application
InactiveUS20080215922A1Easy to detectOptimizing log mechanismError detection/correctionApplication serverTrace file
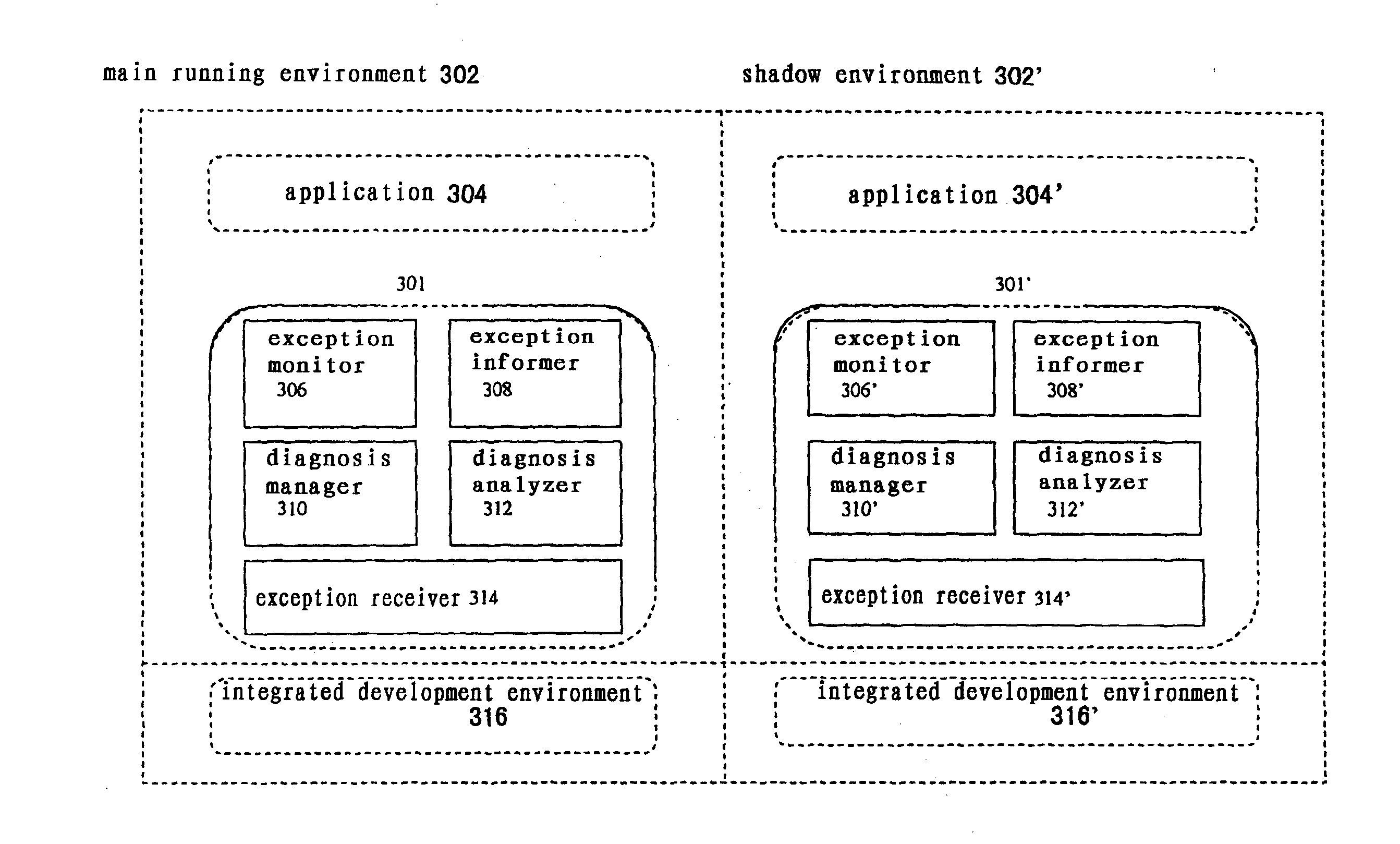
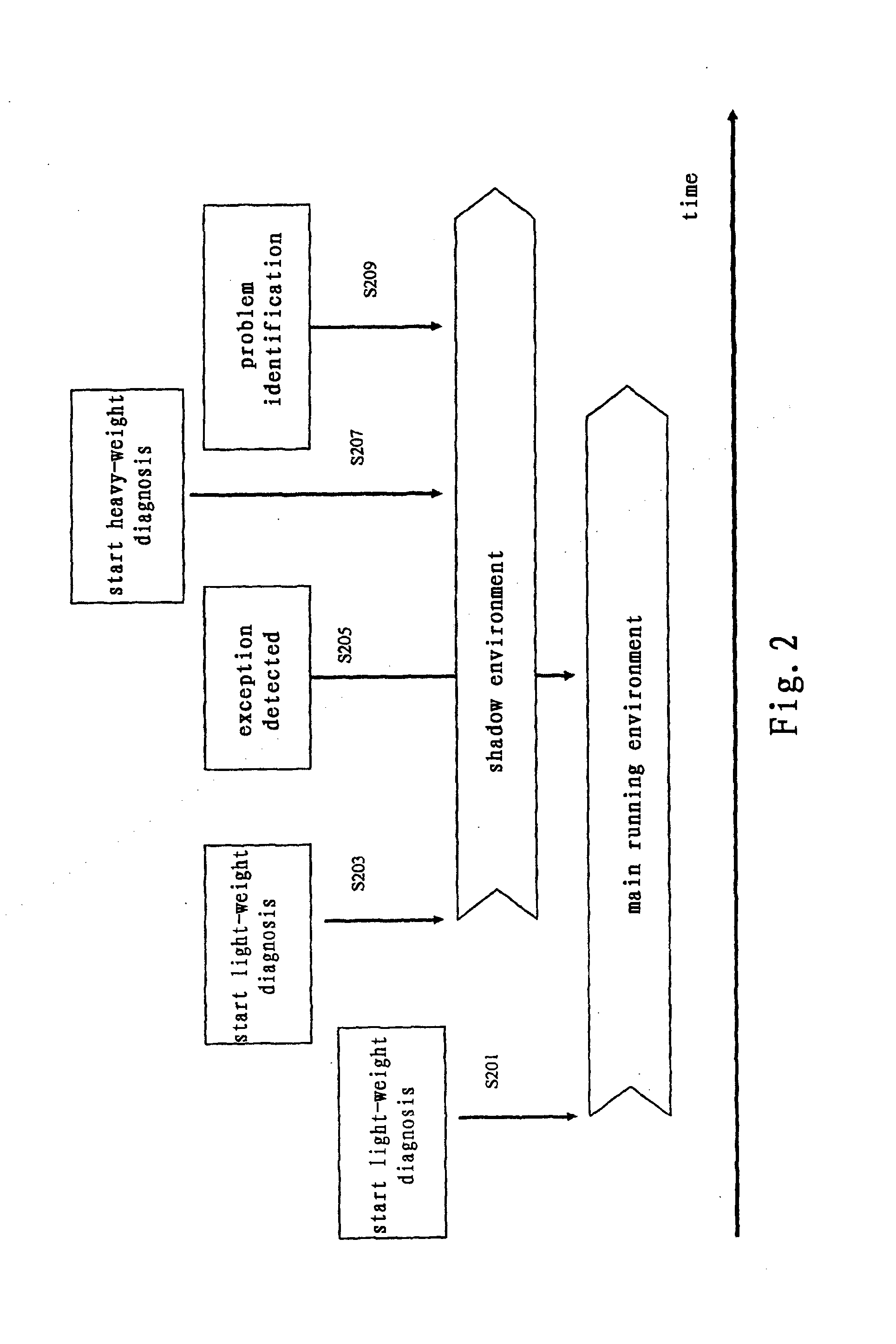
A system, method and program enabling users to diagnose applications easily without affecting the operating performance of the application server, optimizing the log mechanism based on the integrated development environment. The method includes running the application in a main running environment and at least one shadow environment, the shadow environment obtained by duplicating the main running environment; and the main running environment interacting with the shadow environment with respect to the fault of the application. The method includes performing the steps of the main running environment: monitoring the exceptions in the system and sending system exception information to the shadow environment in the event of finding exceptions in the system. The shadow environment: receives the system exception information, opens diagnostic log / trace functions to obtain diagnosis log / trace files related to the system exceptions, and analyzes the diagnosis result based on the obtained diagnosis log / trace files.
Owner:IBM CORP
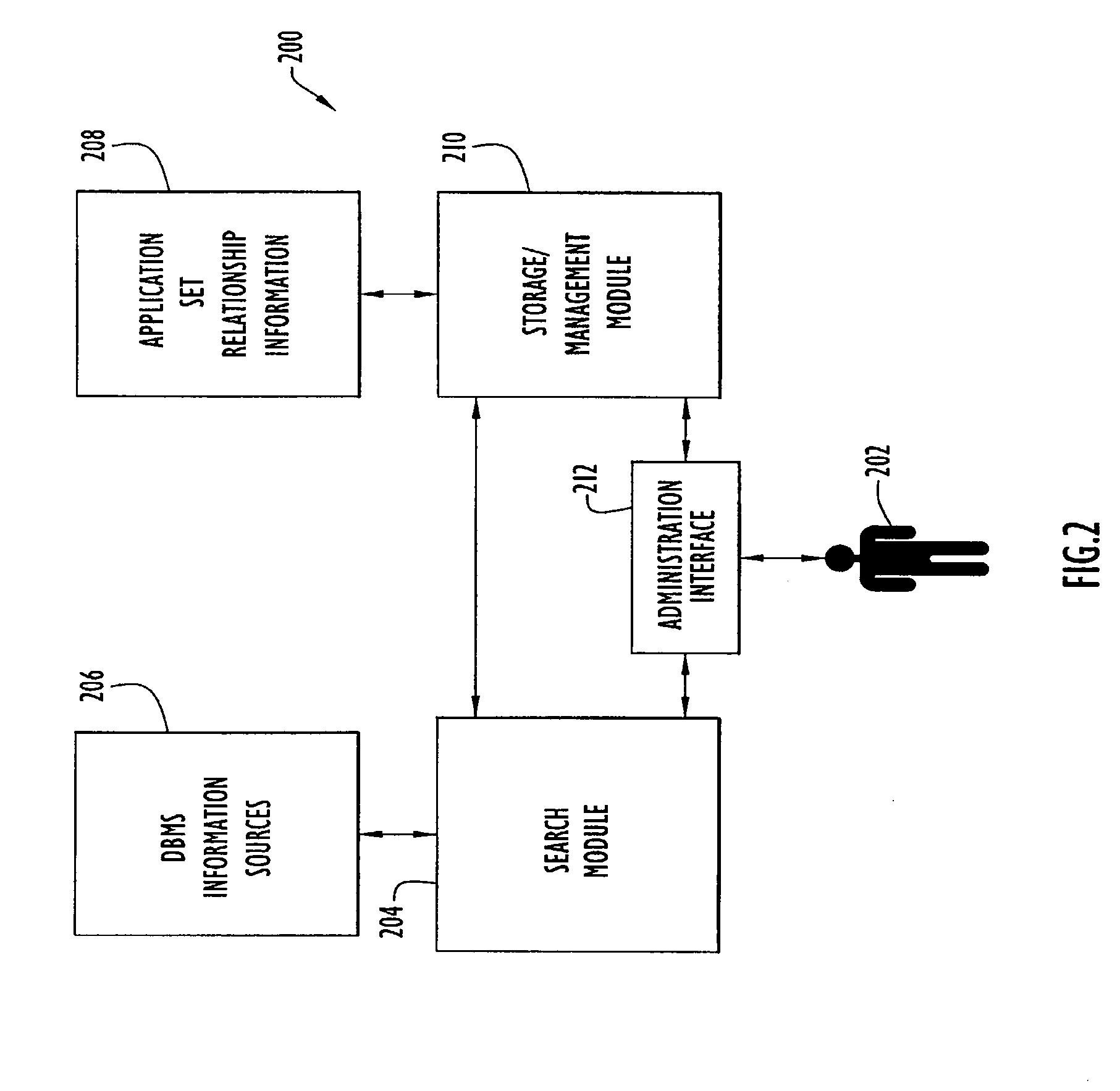
Method and apparatus for recording and managing data object relatonship data
ActiveUS20080016026A1Data processing applicationsDigital data processing detailsInformation repositoryTrace file
The invention relates to a method and apparatus for recording and maintaining stored information system object relationship information. Information contained within a stored information system (including system catalogs, referential constraints, triggers, table hierarchies, column references, indexes, stored program packages, system catalogs, stored procedures, stored queries, log / trace files of dynamically executed code, etc.) are searched to identify dependency relationships between objects. This object relationship information is stored and maintained in an information base. Information within the information based may be organized based upon subsets of objects that support a common application, service, or capability. Object relationship data is used to facilitate stored information system administration activities such as generating / restoring from archives, physically / logically segmenting data objects, replicating data objects; optimizing the distribution of data in distributed data system; and estimating operational capacity.
Owner:SERVICENOW INC
Lightweight indexing for fast retrieval of data from a flow-level compressed packet trace
The present invention describes methods, systems, and data structures to create and search index records within a trace of a packet-based communications link that has been compressed by organizing the data packets according to which flow they belong. Index points are inserted within the compressed flow trace file to create frames and index records are created and saved for each index point. Consequently, searching for a particular data packet does not require sequentially reading the compressed flow trace file, but rather locating the appropriate index record and its corresponding frame in the compressed flow trace file.
Owner:T MOBILE INNOVATIONS LLC
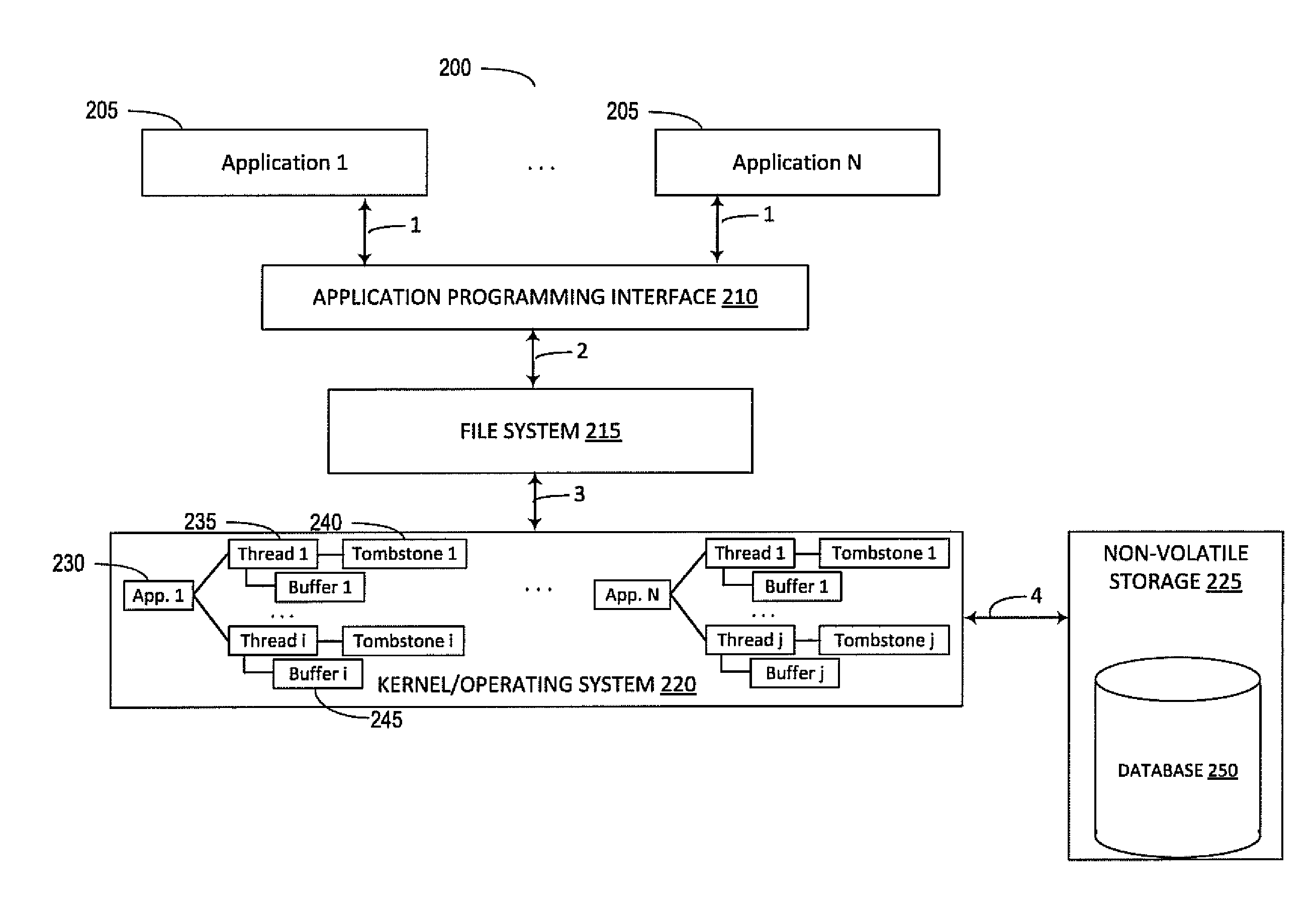
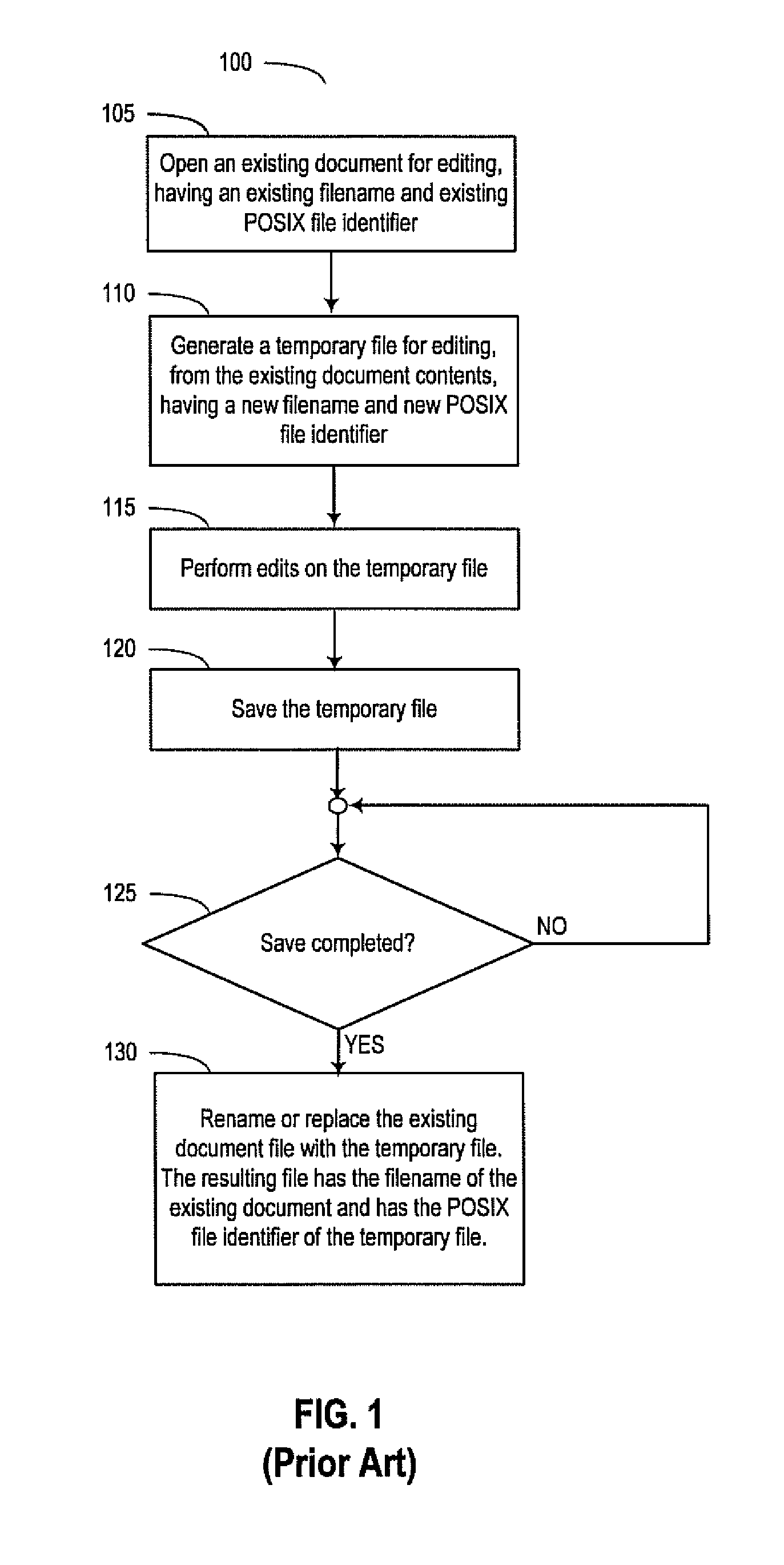
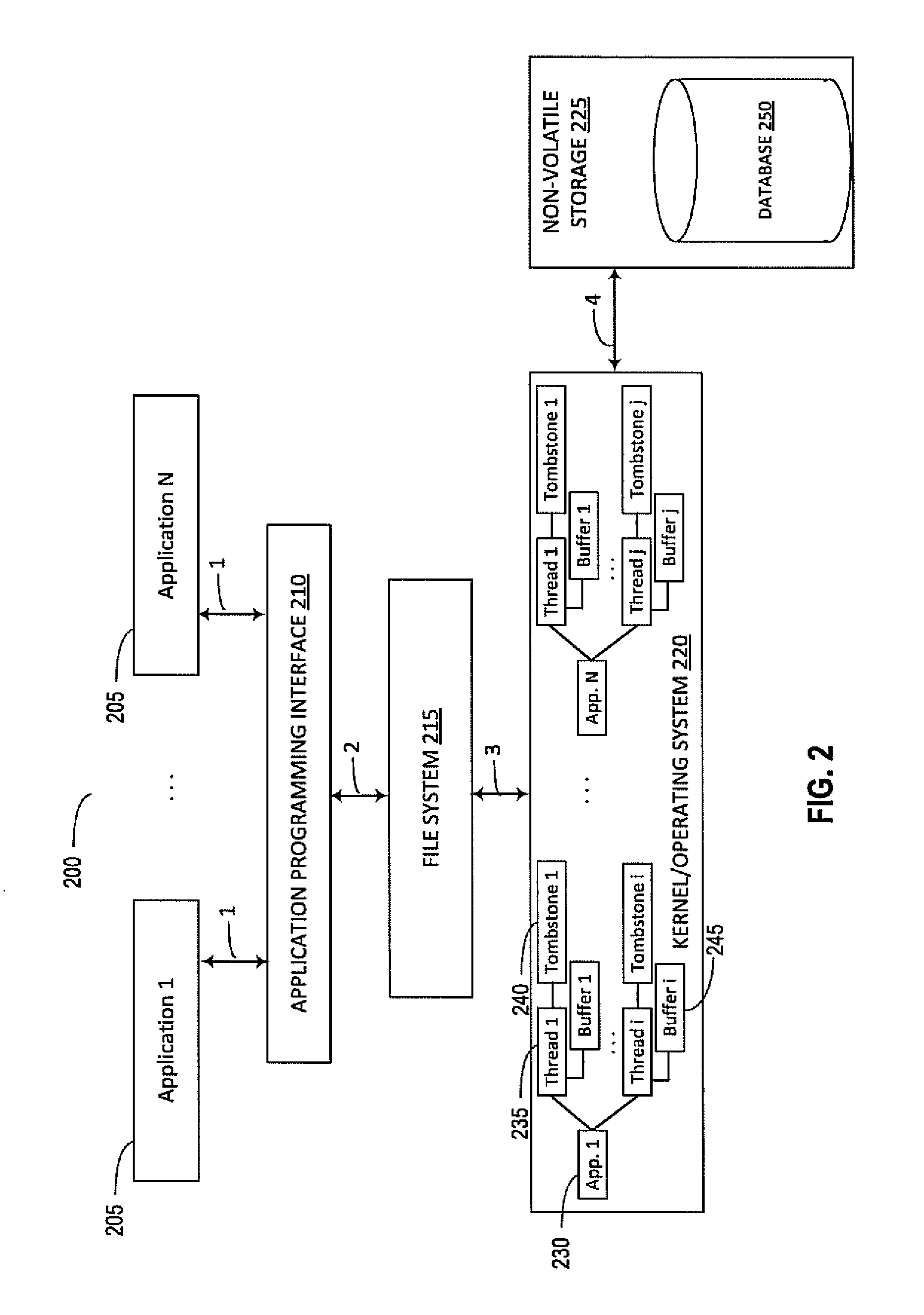
Document tracking for safe save operations
ActiveUS20150347440A1Operational securityDigital data information retrievalRedundant operation error correctionOperational systemFlash file system
Systems and methods are disclosed that track a document within a file system using document identifier (DOCID) that is preserved during safe save operations. The DOCID can be a universally unique identifier (UUID). The DOCID can be generated on a local file system or generated during a synchronization process with a remote synchronization service. Applications can opt in to document tracking. The kernel of the operating system can monitor file system operations on a per-application and per-thread basis and determine when a processing thread is about to perform a safe save. When a sequence of file system operations indicates that a safe save is to be performed, the kernel can generate and store a tombstone record that includes the DOCID and other metadata of the tracked document and pass the DOCID and metadata to the newly saved document.
Owner:APPLE INC
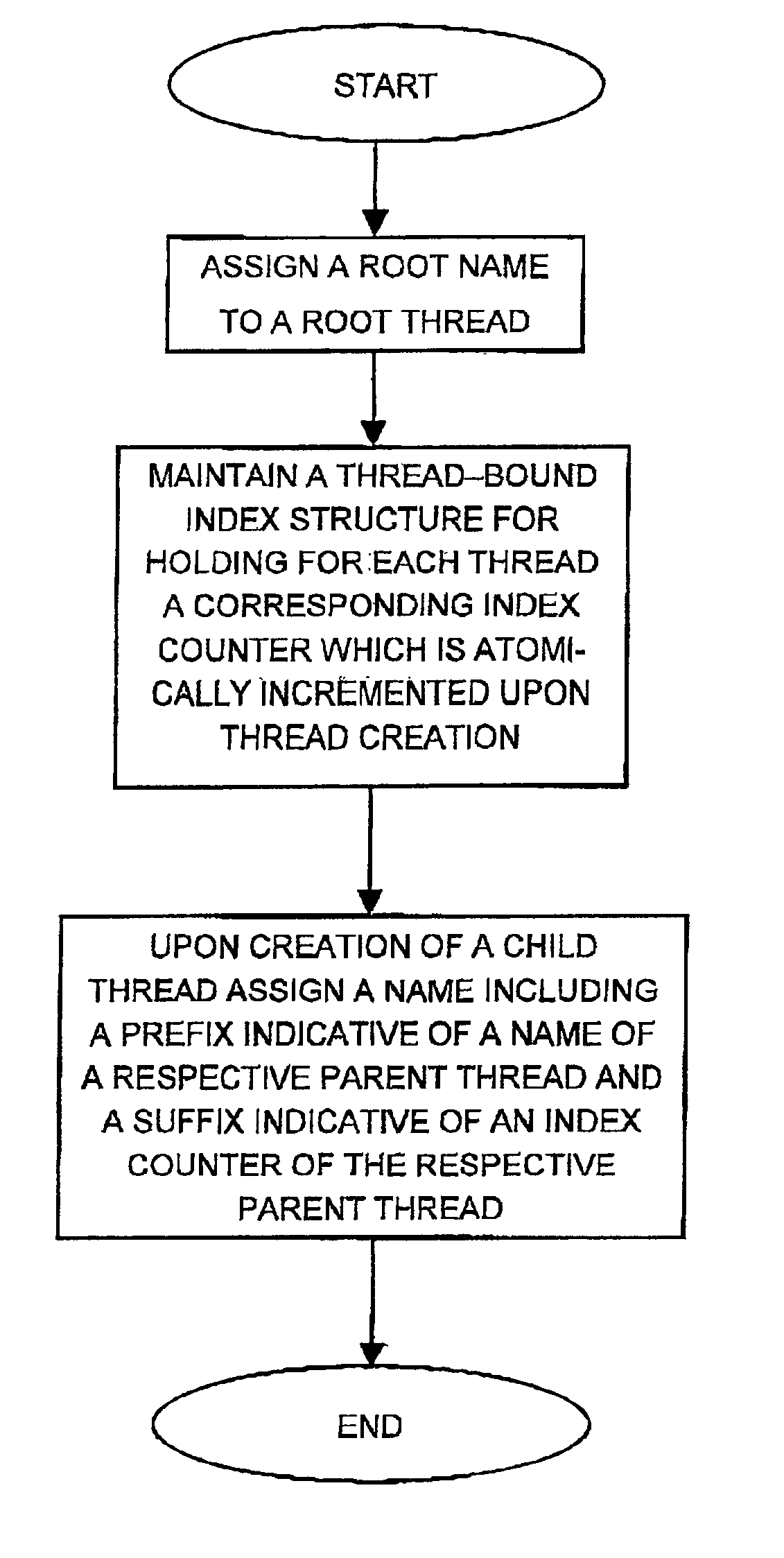
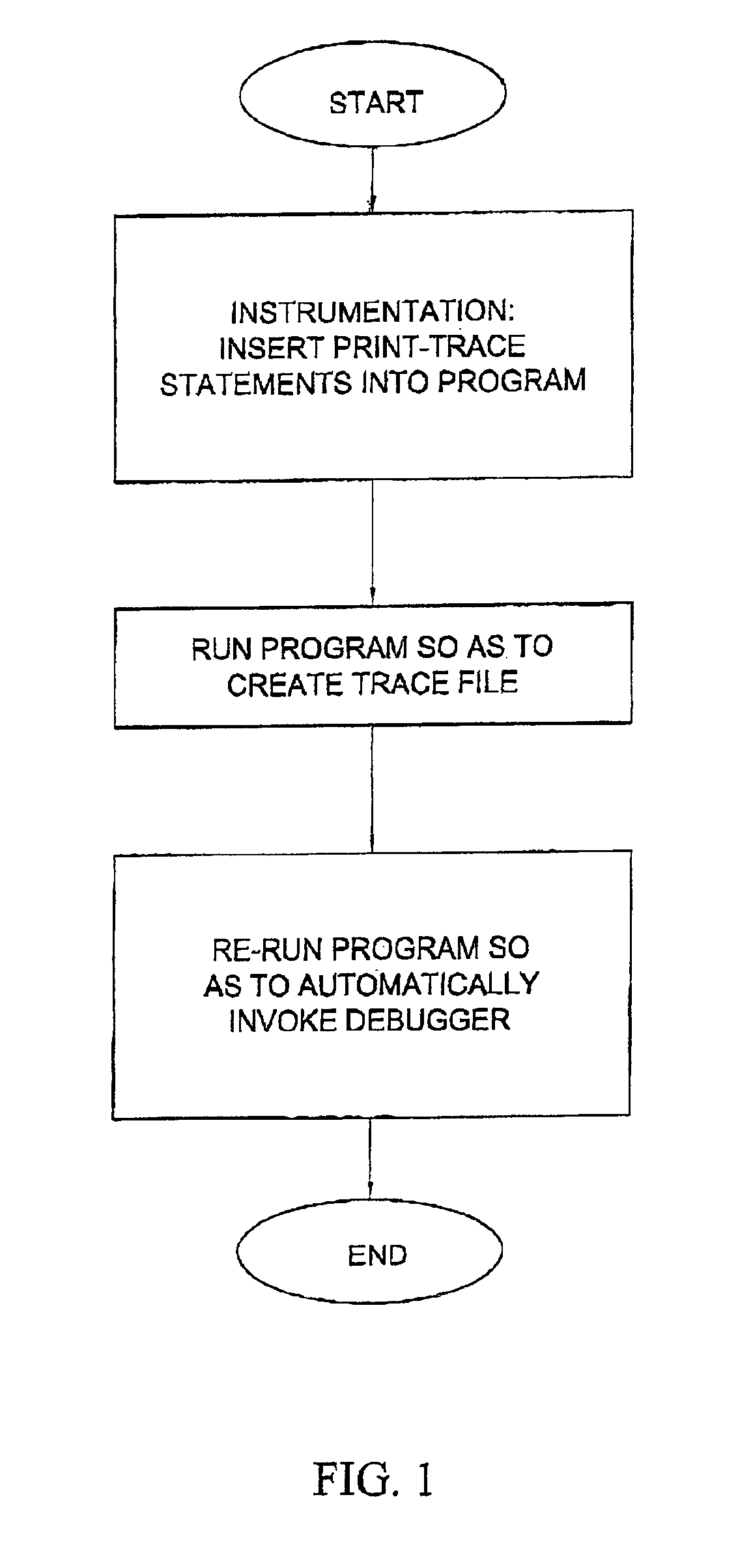
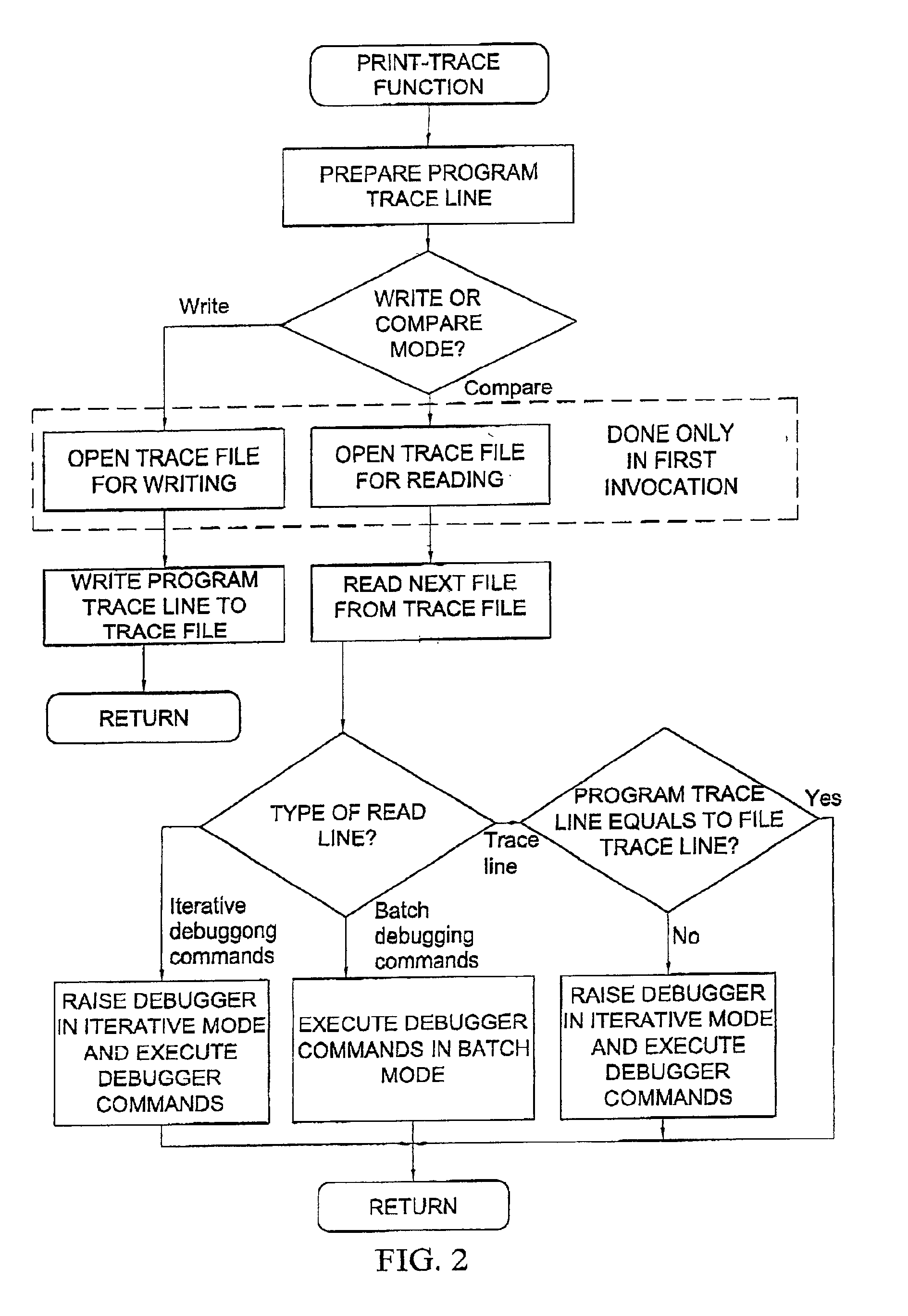
Computer-implemented method and system for automatically invoking a predetermined debugger command at a desired location of a single thread of a program
InactiveUS6978444B1Difficult to implementCompromise integrityError detection/correctionSpecific program execution arrangementsTrace fileProgram Thread
A computer-implemented method and system for automatically invoking a predetermined debugger command at a desired location of a single thread of a program containing at least one thread. At the desired location of the program thread, there is embedded a utility which reads a trace file in which the predetermined debugger command has been previously embedded. Upon re-running the program, the trace file is read and upon reaching the predetermined debugger command, the debugger attaches itself to the running process and executes the process from its current program counter. The debugger is invoked only if there is a discrepancy between successive runs of the program.
Owner:IBM CORP
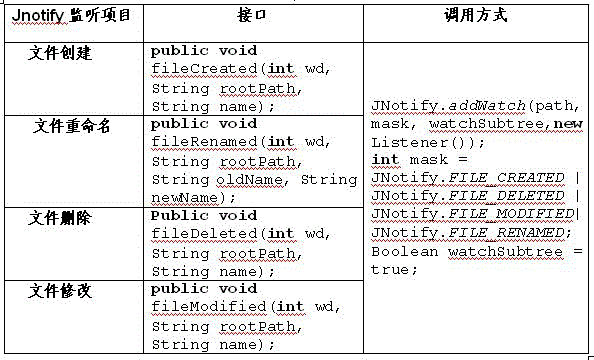
Electronic system, components and method for tracking files
InactiveUS7079044B1Easily and accurately identifyOvercome problemsHand manipulated computer devicesCo-operative working arrangementsElectronic systemsTrace file
A file tracking system including a processor, which maintains and interfaces with a database, a plurality of file folder retainers, and a plurality of file folders. The file tracking system actively maintains and updates the database, which includes file information, file location, and unique file address for the plurality of files, by providing interactive communication between the processor, the folder retainers, and the file folders. Each file folder may include an indicator light, such as an LED, which a user may cause to blink when trying to locate the file folder at a location accessed from the database.
Owner:STEELCASE DEV INC
Snapshoot management method and device
ActiveCN104714755AEasy to manageInput/output to record carriersSoftware simulation/interpretation/emulationTrace fileFile system
The invention discloses a snapshoot management method and device. The snapshoot management method includes the steps that a server receives a snapshoot identification request from a client side, wherein a snapshoot identification is used for identifying a snapshoot generated by a client side file system; a latest snapshoot number of the whole file system is generated and fed back to the client side as the snapshoot identification, and a file descriptor structure of the file system is updated; a track file corresponding to the snapshoot generated by the file system is built and used for tracking files and recording the change information of the file system after the snapshoot is generated. In this way, the snapshoot management method and device can realize any catalogue snapshoot for the distribution type file system without a file layout or an overall file descriptor structure table.
Owner:XFUSION DIGITAL TECH CO LTD
Providing a visual representation of a sub-set of a visual program
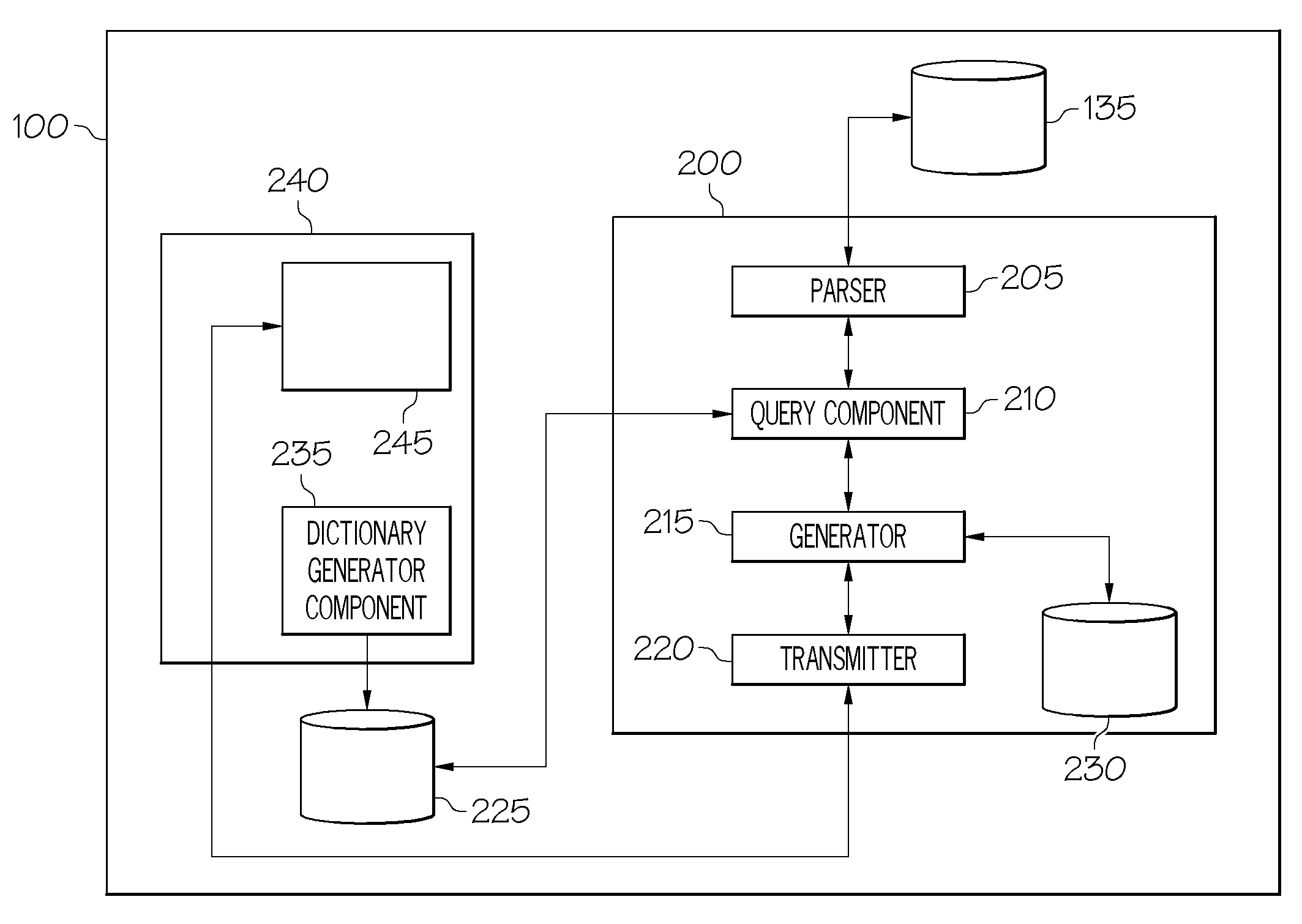
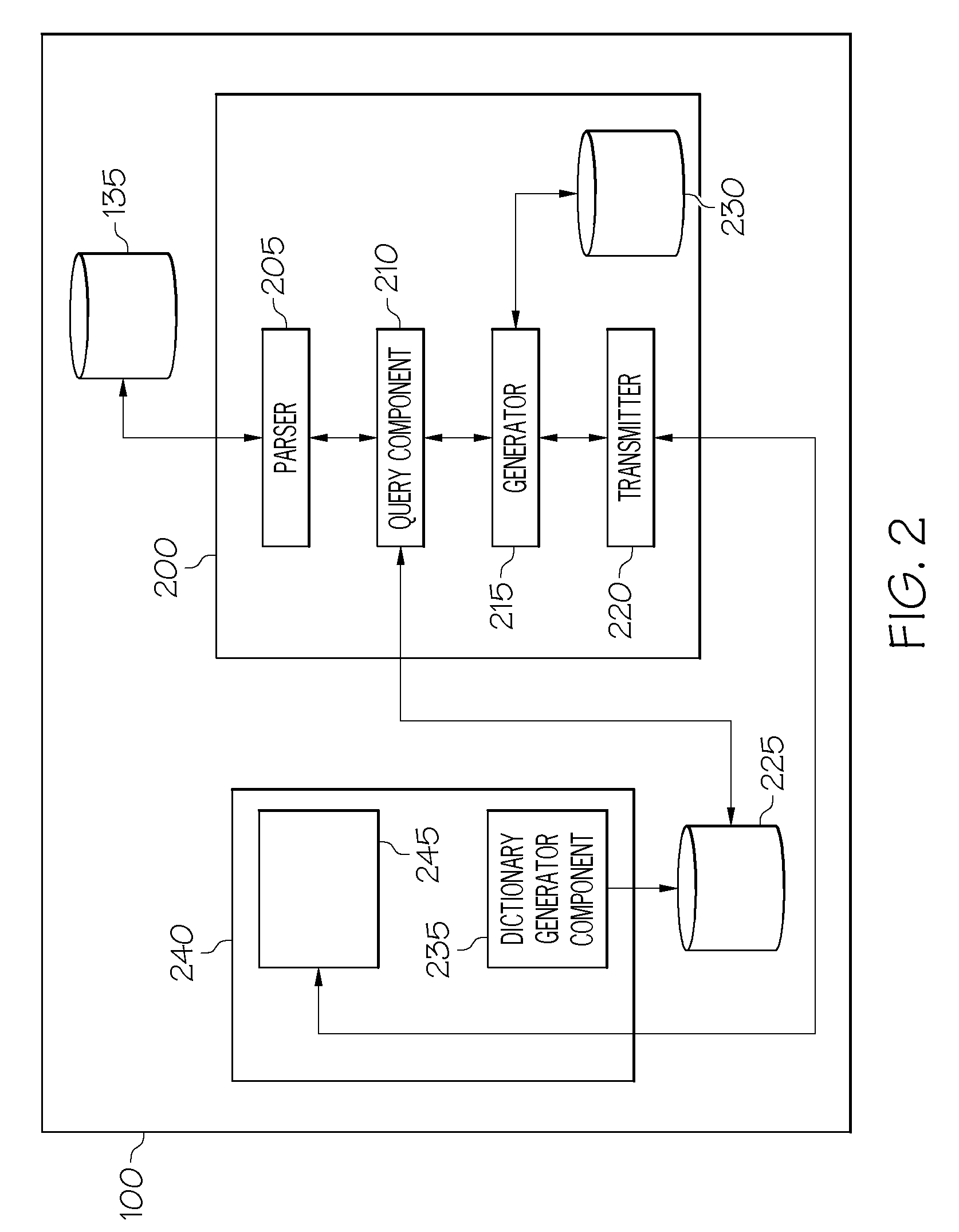
InactiveUS20080059436A1Requires minimizationError detection/correctionVisual/graphical programmingTrace fileEvent data
To provide a visual representation of a sub-set of a visual program generated using a visual programming tool, wherein a trace operation is executed against the visual program and resulting trace data is stored in a trace file, an apparatus includes a parser for parsing the trace file to obtain the trace data, and a generator for using event data associated with an event and associated component data associated with a component of the visual program to generate render data. The event data and the component data are associated with the trace data.
Owner:IBM CORP
Dynamic storage mechanism
InactiveUS8825591B1Reduce storage costs without compromising performanceLess expensiveDigital data information retrievalDigital data processing detailsTimestampTrace file
System and method for tracking statistics at the subfile level and transparently placing or migrating inactive or less active blocks of data to other storage devices. Embodiments may provide mechanisms to track statistics at the subfile level of files including, but not limited to, database files, and to transparently place or migrate inactive or less active blocks of data of the files from higher-performing, typically more expensive, storage to lower-performing, typically less expensive, storage, while placing or migrating active blocks of data of the files to higher-performing storage, based on the subfile-level statistics rather than on file-level timestamps. In some embodiments, knowledge of file structure (e.g., database file structure), for example knowledge of database partitions with header blocks and data blocks in databases using data partitioning, may be used to separate more active and less active blocks of data of files onto storage with different performance and / or other characteristics.
Owner:SYMANTEC OPERATING CORP
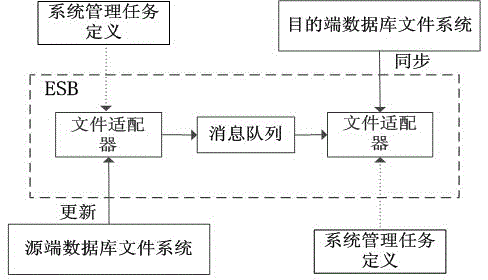
Remote file synchronizing method realized based on distributed enterprise service bus
ActiveCN102624871AImprove efficiencyImprove performanceTransmissionSpecial data processing applicationsFile systemBusiness enterprise
The invention discloses a remote file synchronizing method which is realized based on a distributed enterprise service bus. The method can start real-time monitoring of a heterogeneous system in the distributed enterprise service bus to track the dynamic change of a file system, obtains increment information through difference calculation, and then sends to a destination end to complete new file reconstruction. The method disclosed by the invention adopts efficient file discovery, difference calculation and reconstruction polices, so as to greatly reduce the time and transmission quantity for file remote synchronization.
Owner:杭州铭唐信息科技有限公司
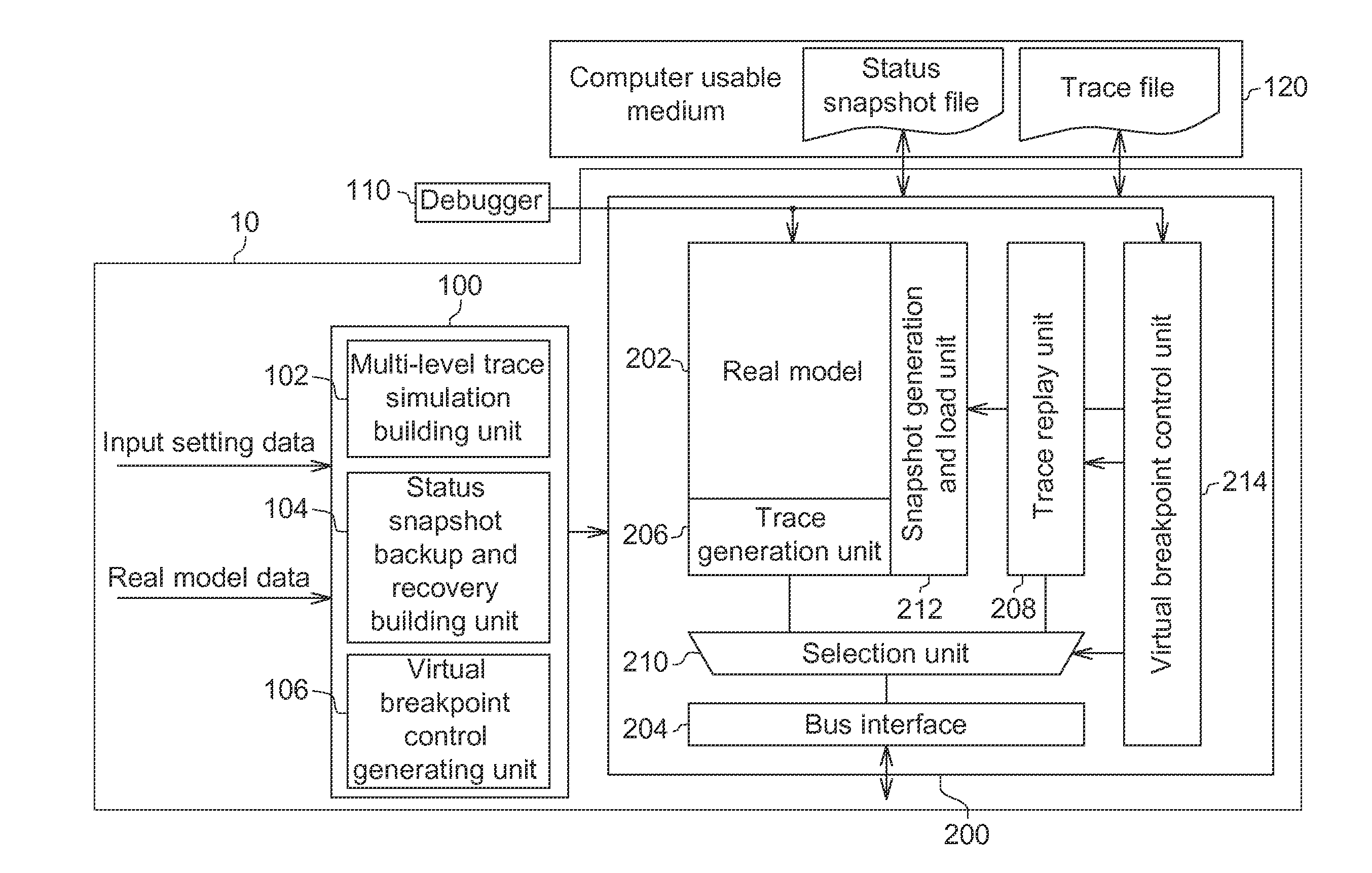
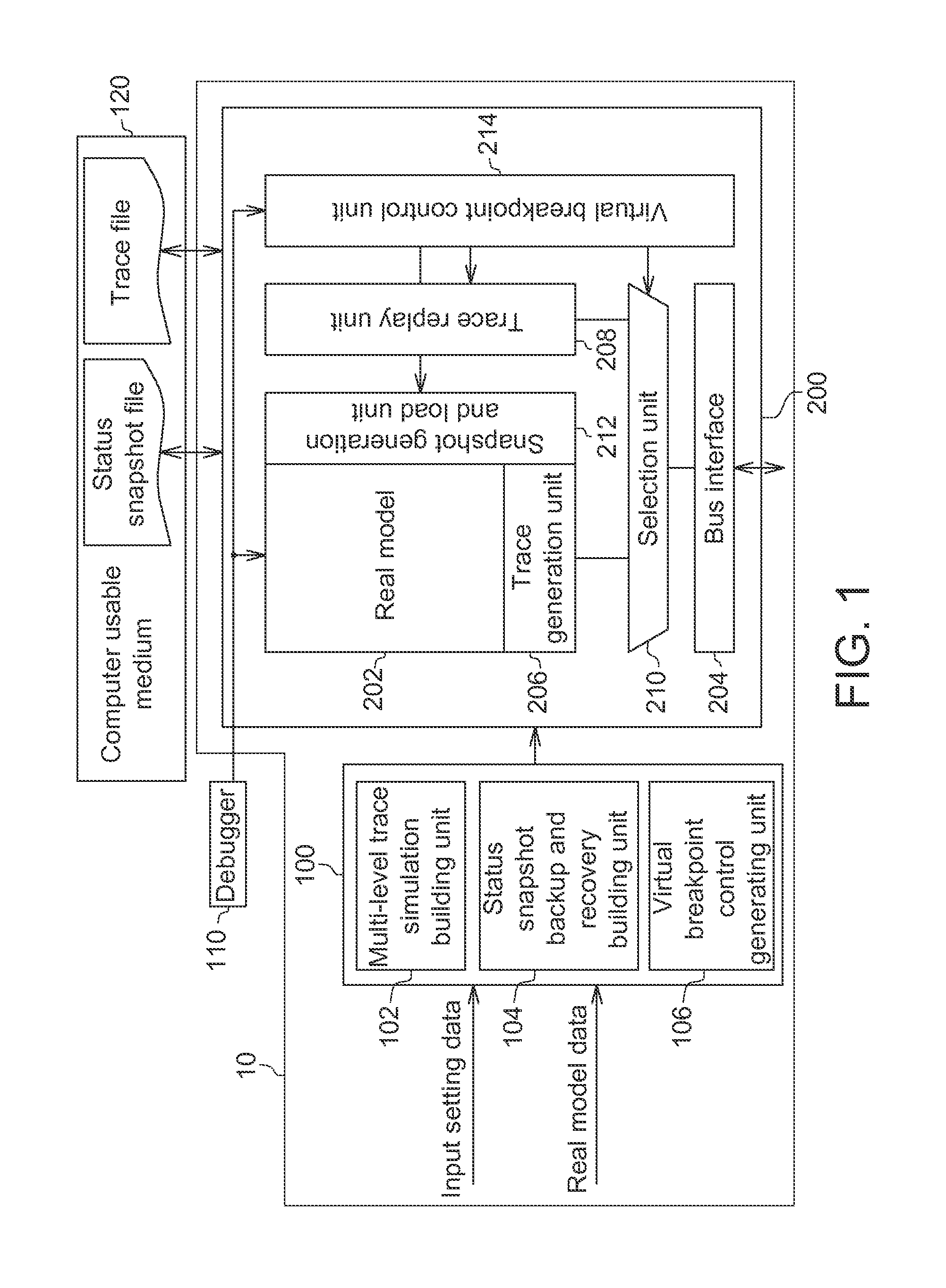
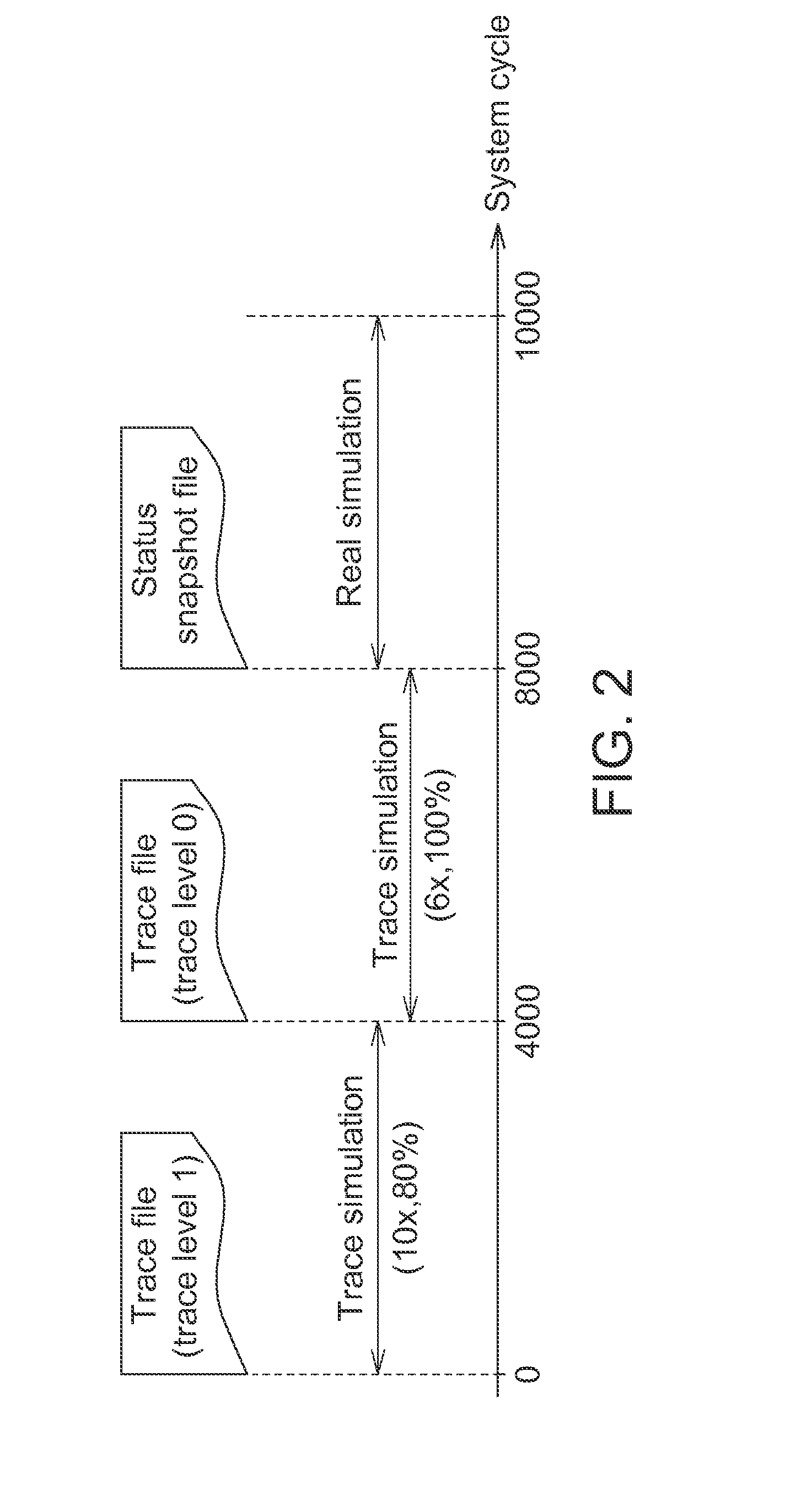
Hybrid Simulation System and Method
A hybrid simulation model includes a real model, a bus interface and an acceleration model. The real model simulates a group of instructions. The acceleration model includes a trace generation unit, a trace replay unit, a selection unit, a snapshot generation and load unit and a virtual breakpoint control unit. The trace generation unit records at least one trace file of the real model in a first simulation. The trace replay unit reads and accordingly accesses the at least one trace file. The selection unit dynamically switches to perform a real simulation or a trace simulation. The snapshot generation and load unit generates at least one status snapshot file and loads the at least one status snapshot file to the real model in repeated simulations. The virtual breakpoint control unit controls the selection unit to switch between the trace simulation and the real simulation according to a virtual breakpoint.
Owner:IND TECH RES INST
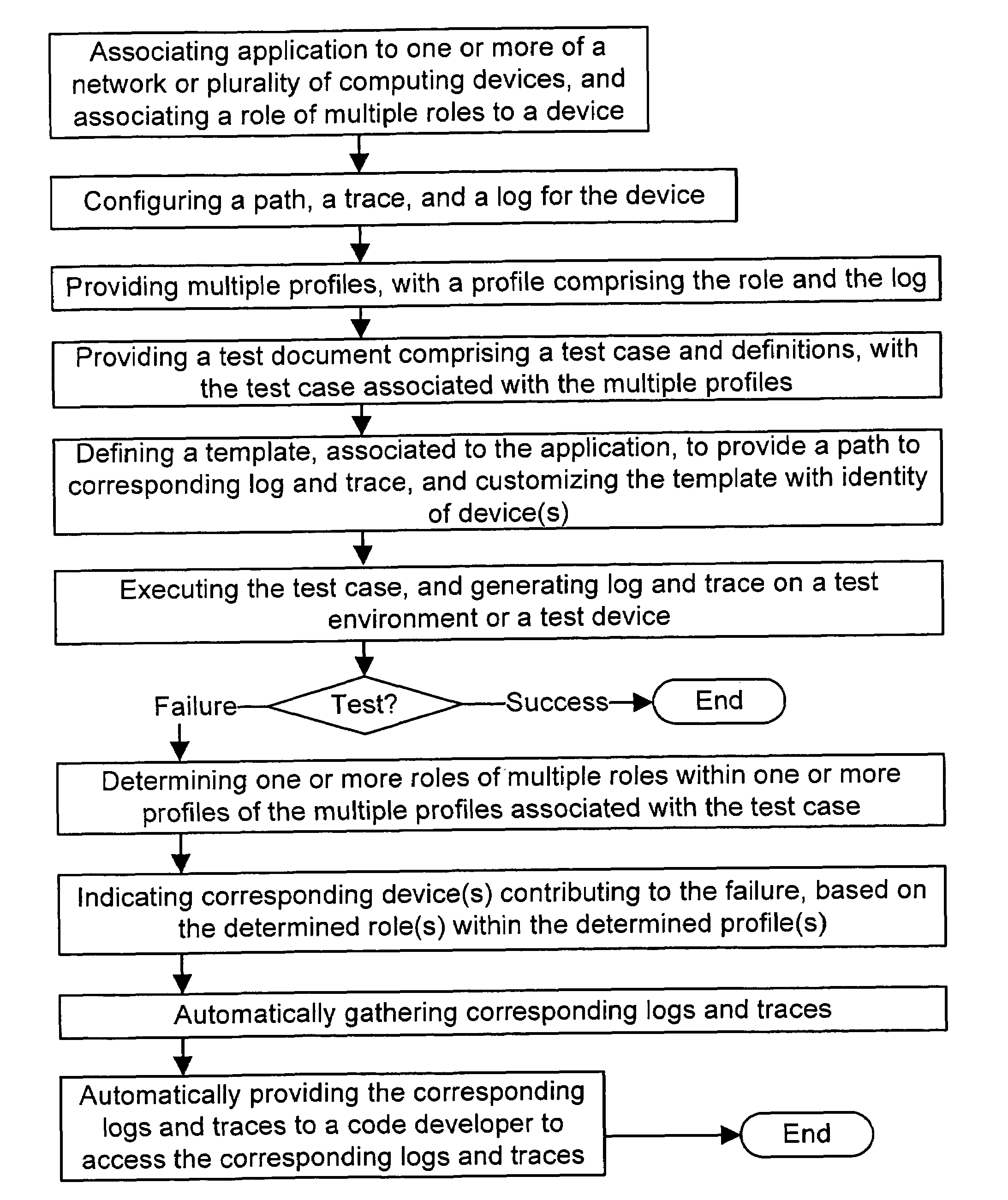
Method and system for associating logs and traces to test cases
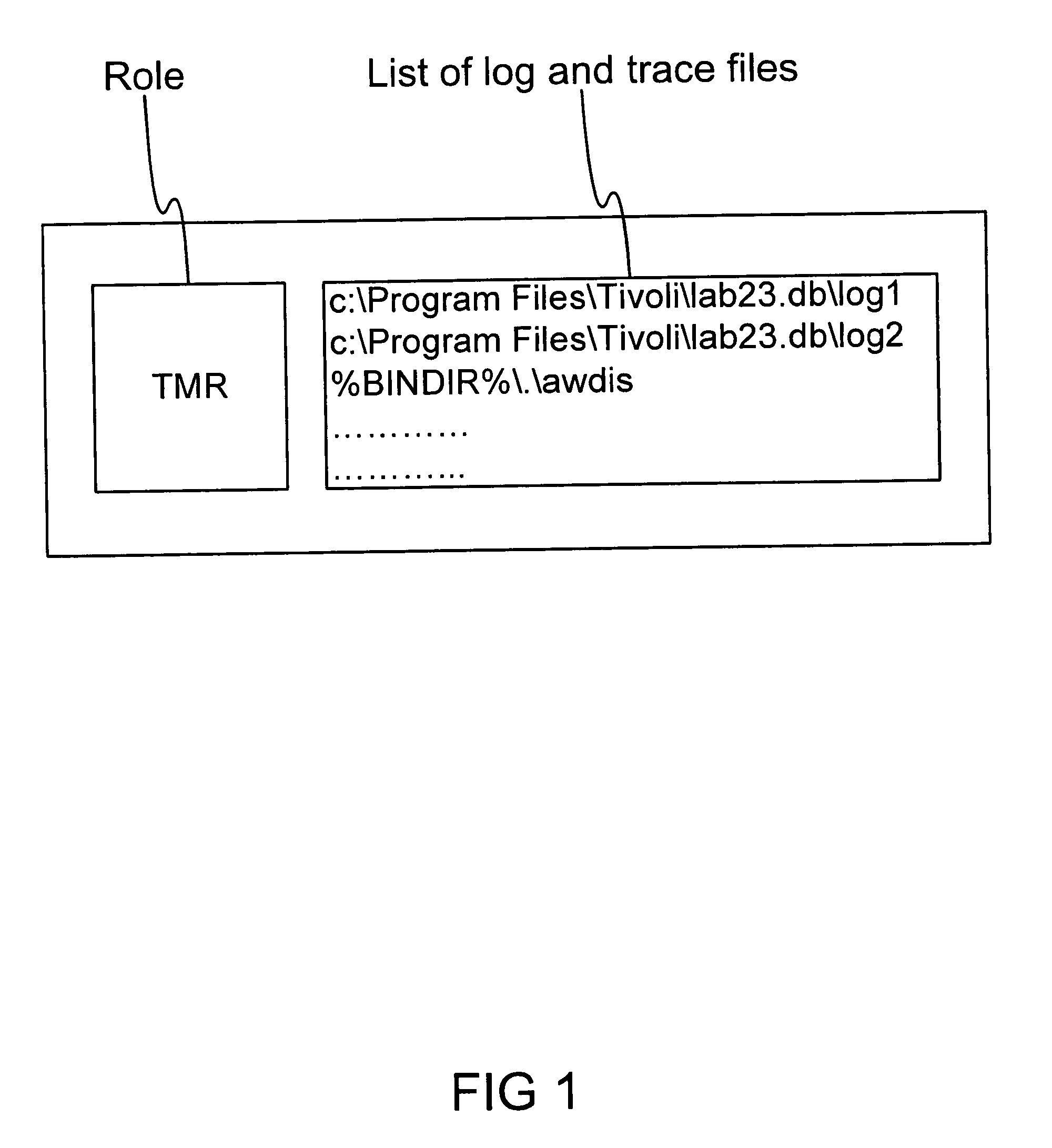
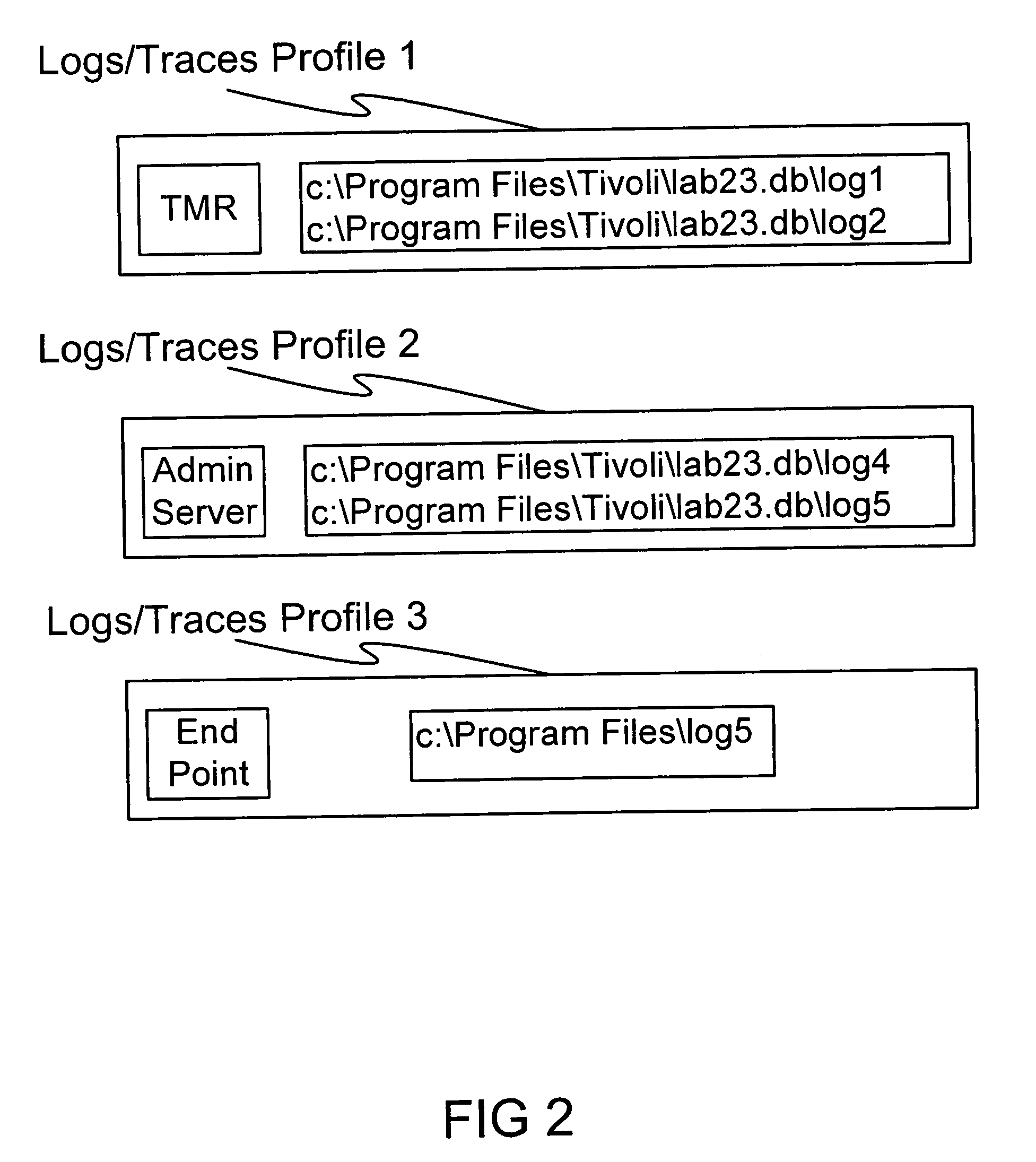
InactiveUS7512933B1Problem be fixError detection/correctionSpecific program execution arrangementsTest designDocumentation procedure
One of the examples is to define and use the concept of “Logs / Traces Profile” and “System Logs / Traces Profile” (including a role and the log and trace file locations), and incorporate them within the test design document. Each test design document can be associated to each test case to highlight which logs and traces need to be collected during its execution. In this way, the testers will know which logs and traces to provide to the code developers, when addressing an issue. In this way, developer can investigate the bug, understand them, and be able to fix the problem, especially due to timing, synchronization, and concurrency.
Owner:IBM CORP
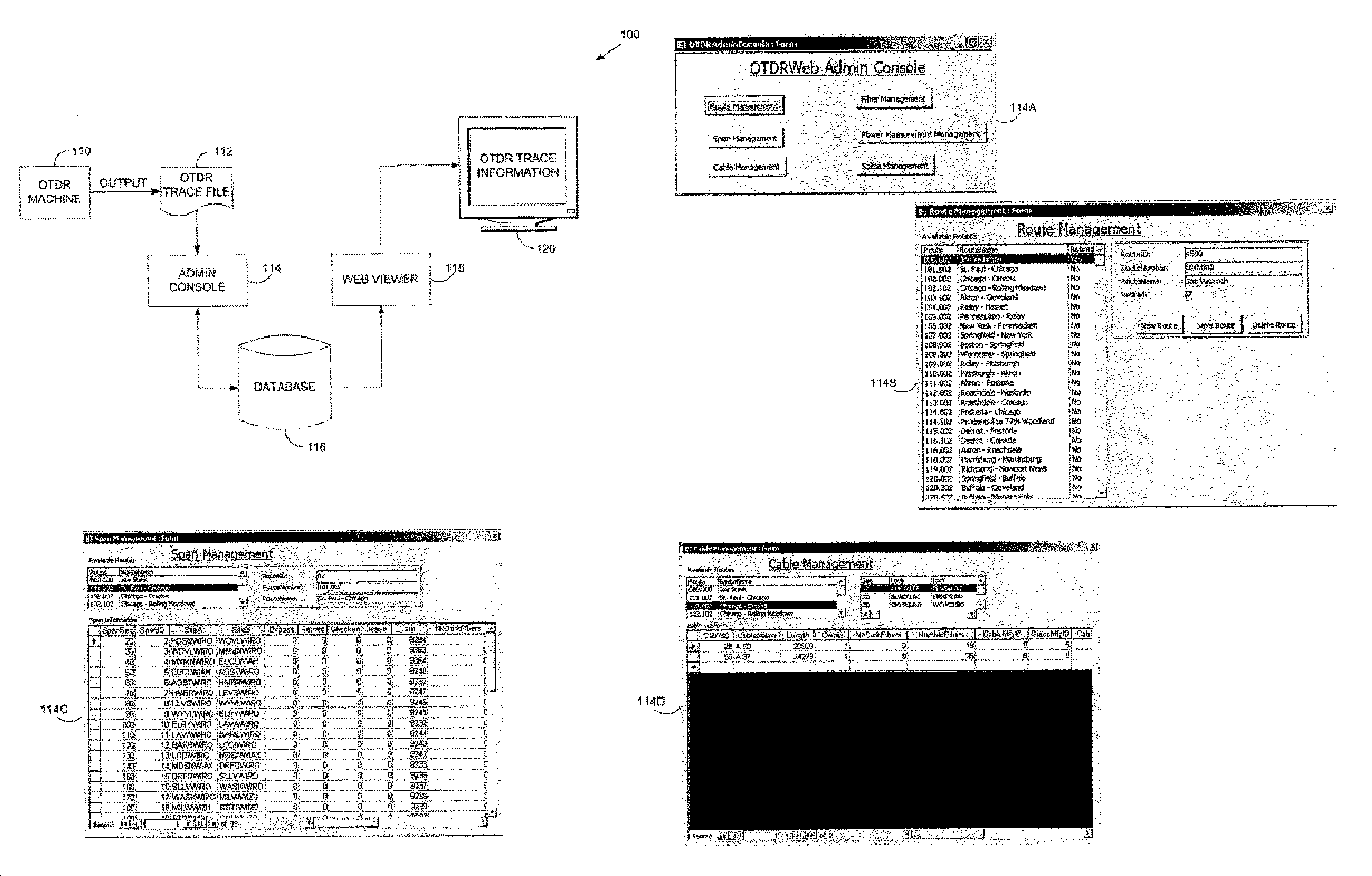
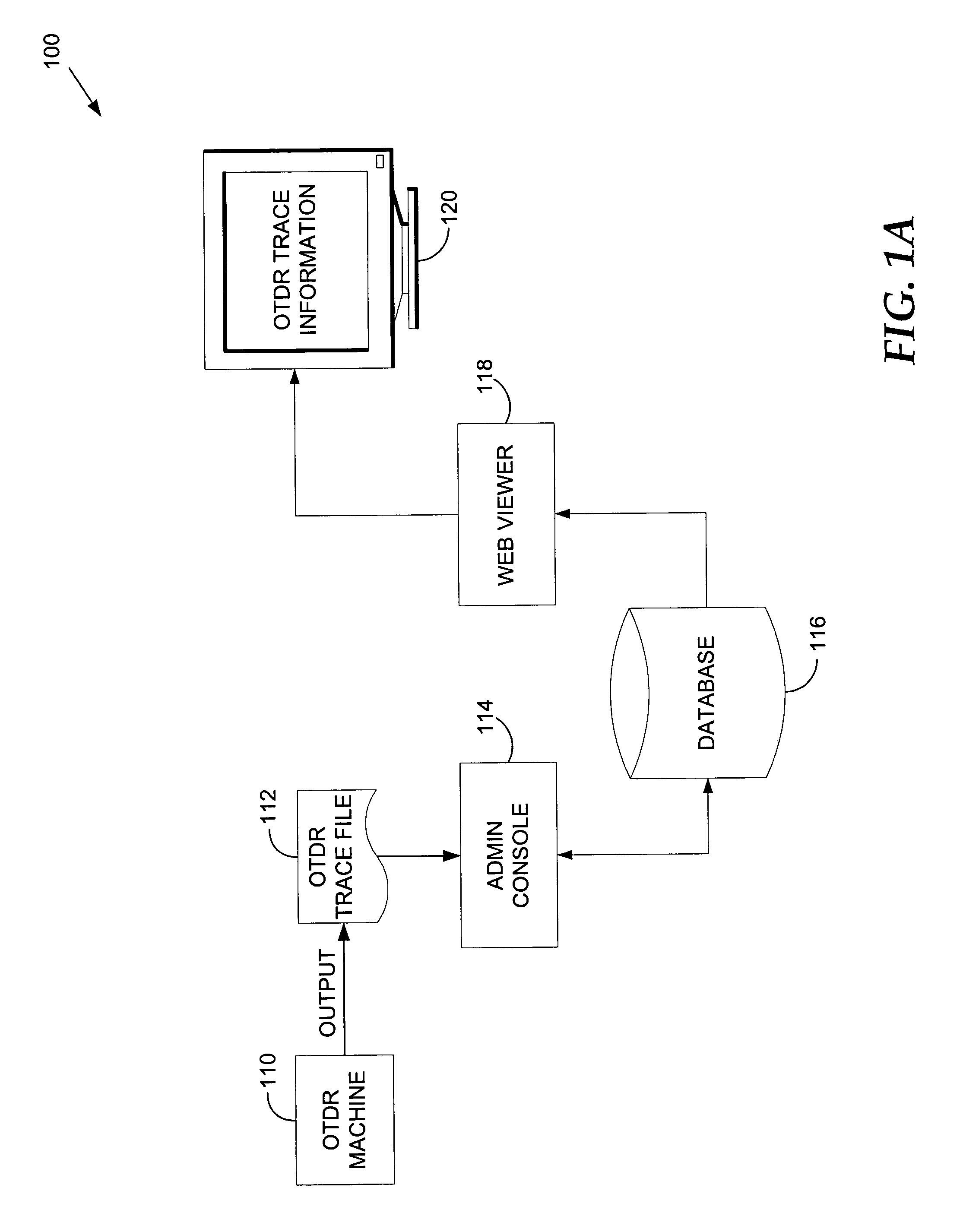
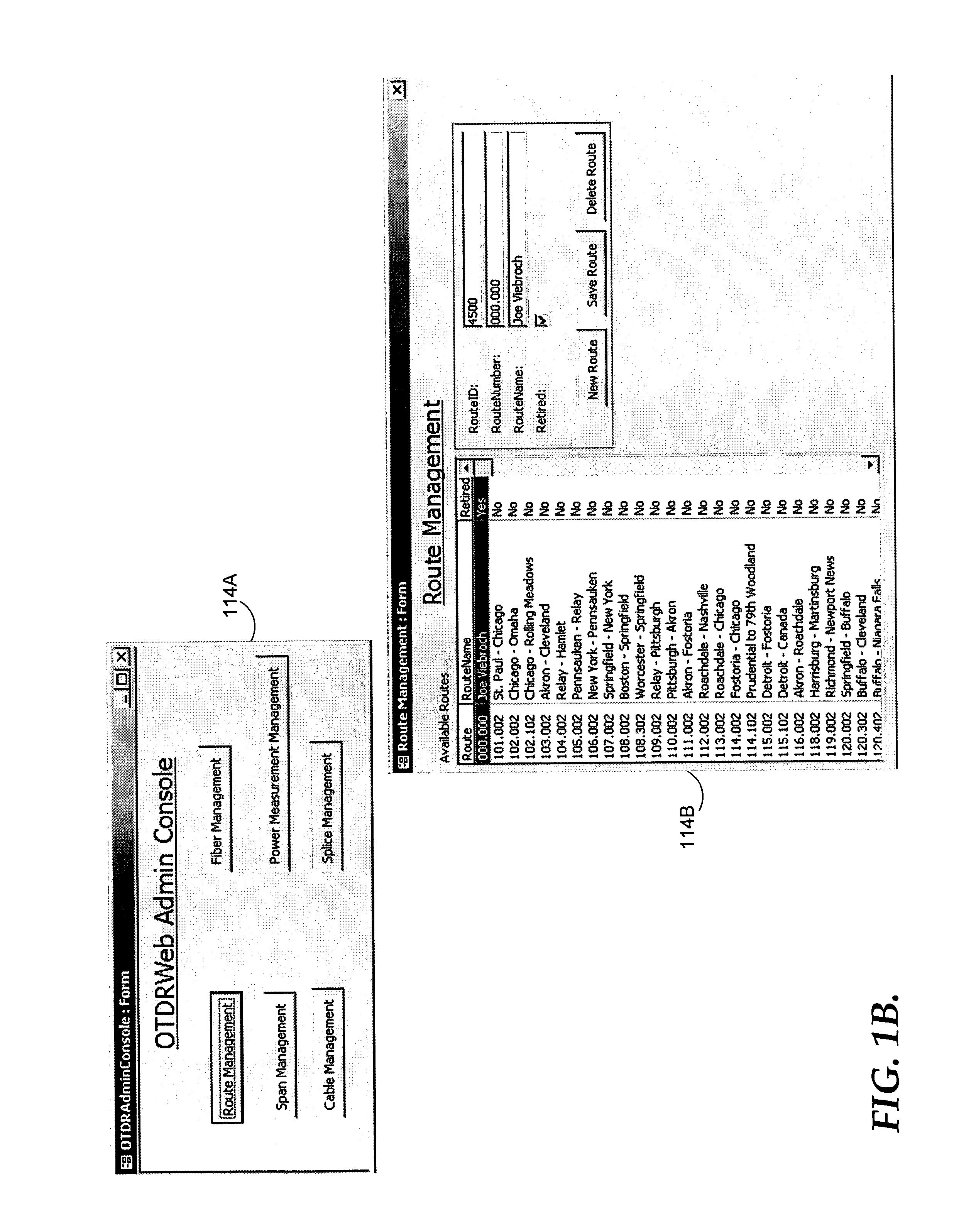
Optical time domain reflectometer (OTDR) data storage and retrieval
ActiveUS7136156B1Material analysis by optical meansReflectometers detecting back-scattered light in time-domainTime domainTrace file
A method, system, and medium are provided for Optical Time Domain Reflectometer (OTDR) Data storage and retrieval in a networking environment. The method includes receiving an OTDR trace file in its native format that includes OTDR information, storing the trace file, receiving a request to present the OTDR information in a browser or some other interface, identifying a viewer that can render the OTDR information, and communicating the OTDR information to the browser. The system includes a user interface that facilitates uploading an OTDR trace file in its native format, a storage device for receiving the trace file, and a viewer that can render the data within the OTDR trace file.
Owner:T MOBILE INNOVATIONS LLC
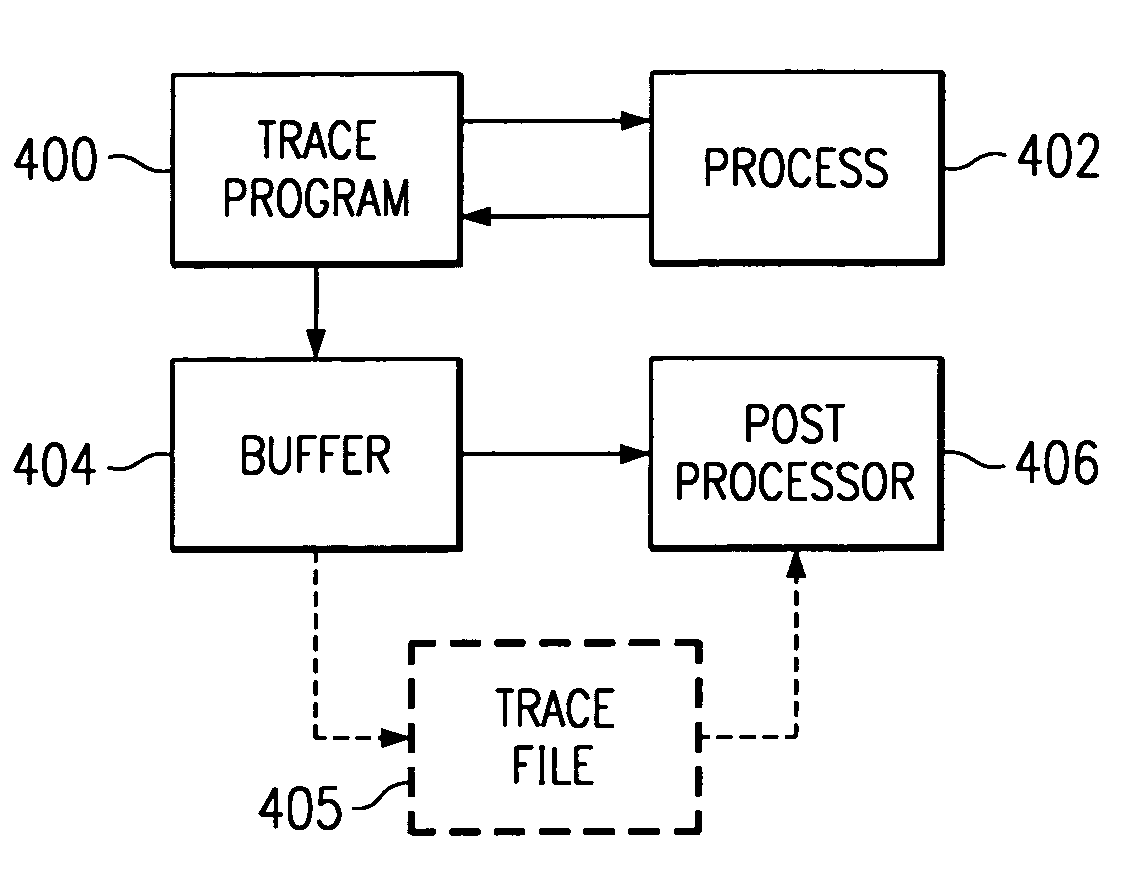
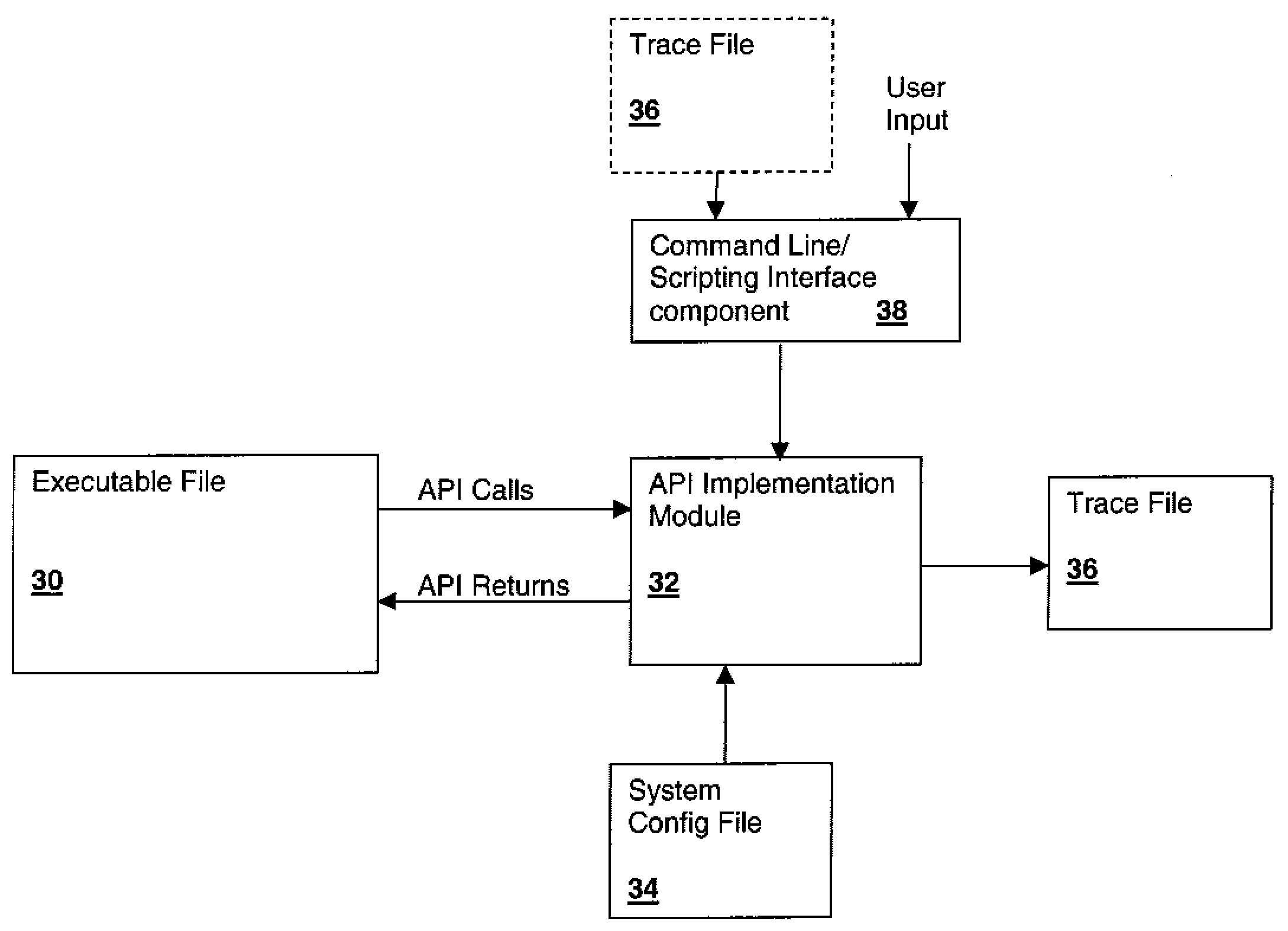
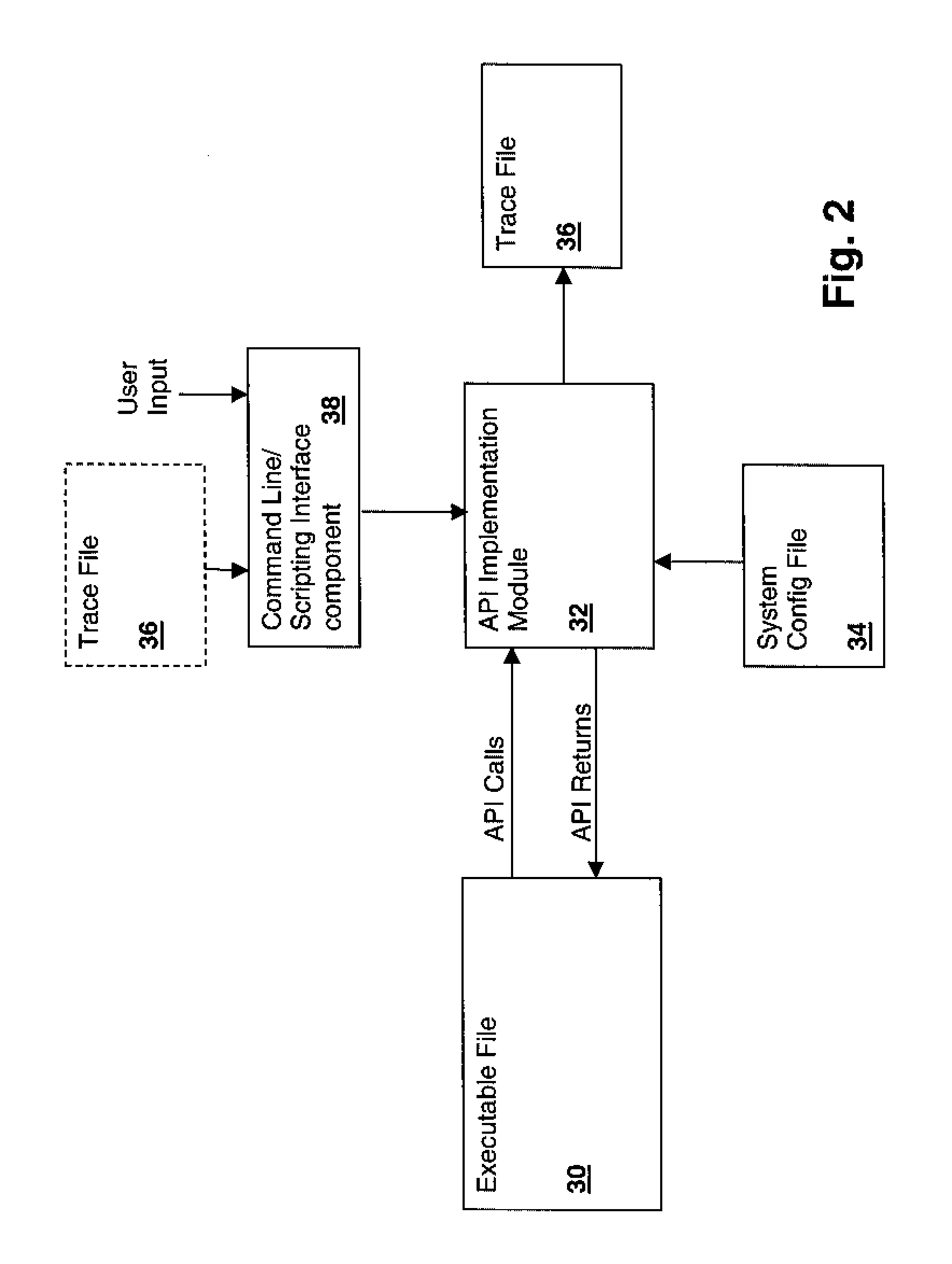
Executable High-Level Trace File Generation System and Method
ActiveUS20090013312A1Easy to understandError detection/correctionSpecific program execution arrangementsCommand-line interfaceTrace file
An executable high-level trace file generation system and method provide reduced debugging effort and time, particularly on initial startup of new or modified hardware. An executable program invokes high-level application programming interfaces (APIs), to perform various tasks. Instructions within the APIs generate a trace file documenting the invoked sequence of APIs by writing a line to a trace file that documents the API and input parameters received by the API. Upon completion of execution of the API, the return value may be documented as a comment line in the trace file. The resulting trace file is then re-executable as a script and may be edited to alter the sequence of APIs invoked and / or the arguments provided. The script interpreter may be a command line interface through which the APIs are invoked, and trace files may be similarly generated that document sequences of manually entered commands.
Owner:IBM CORP
Apparatus and method for detecting software error
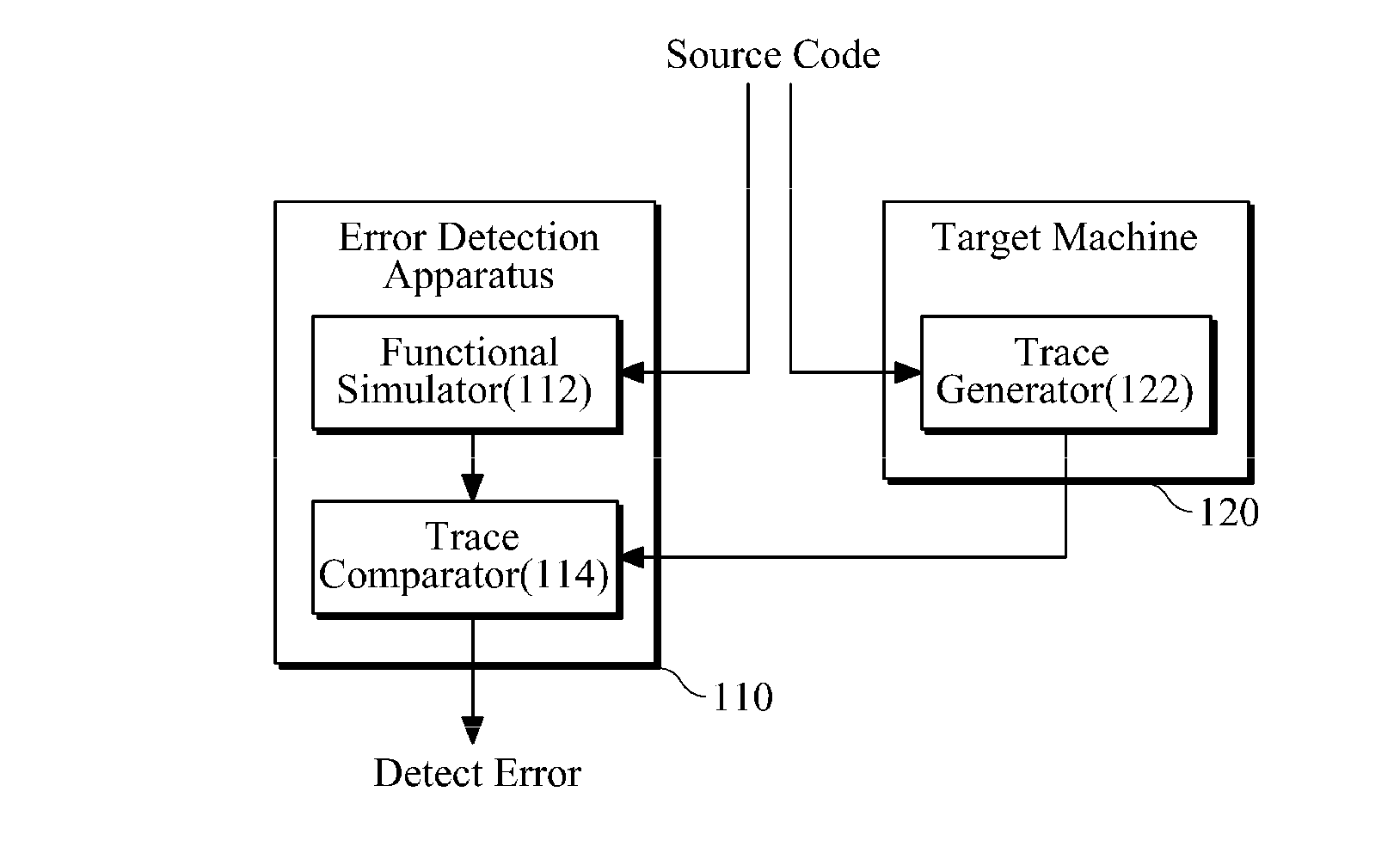
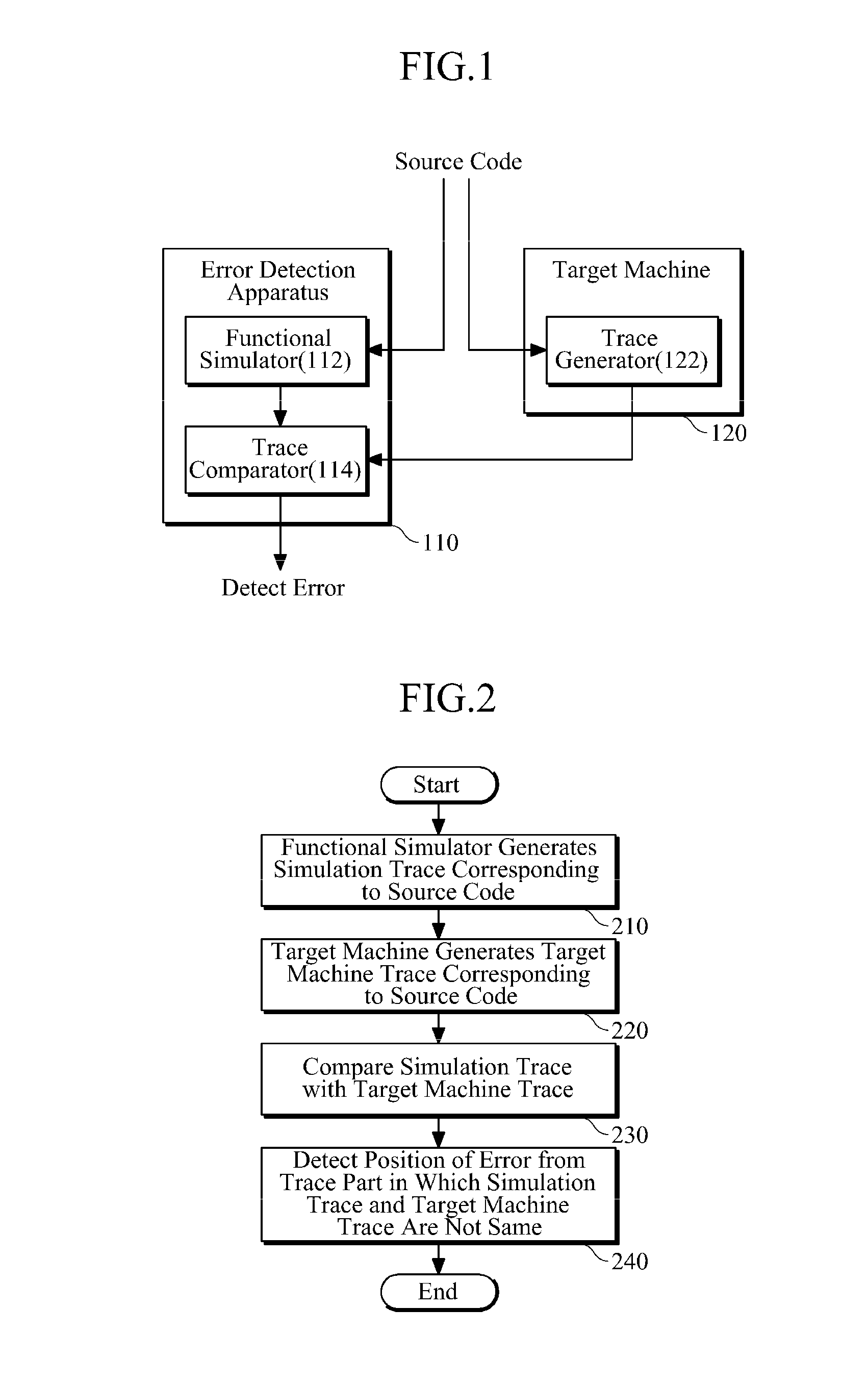
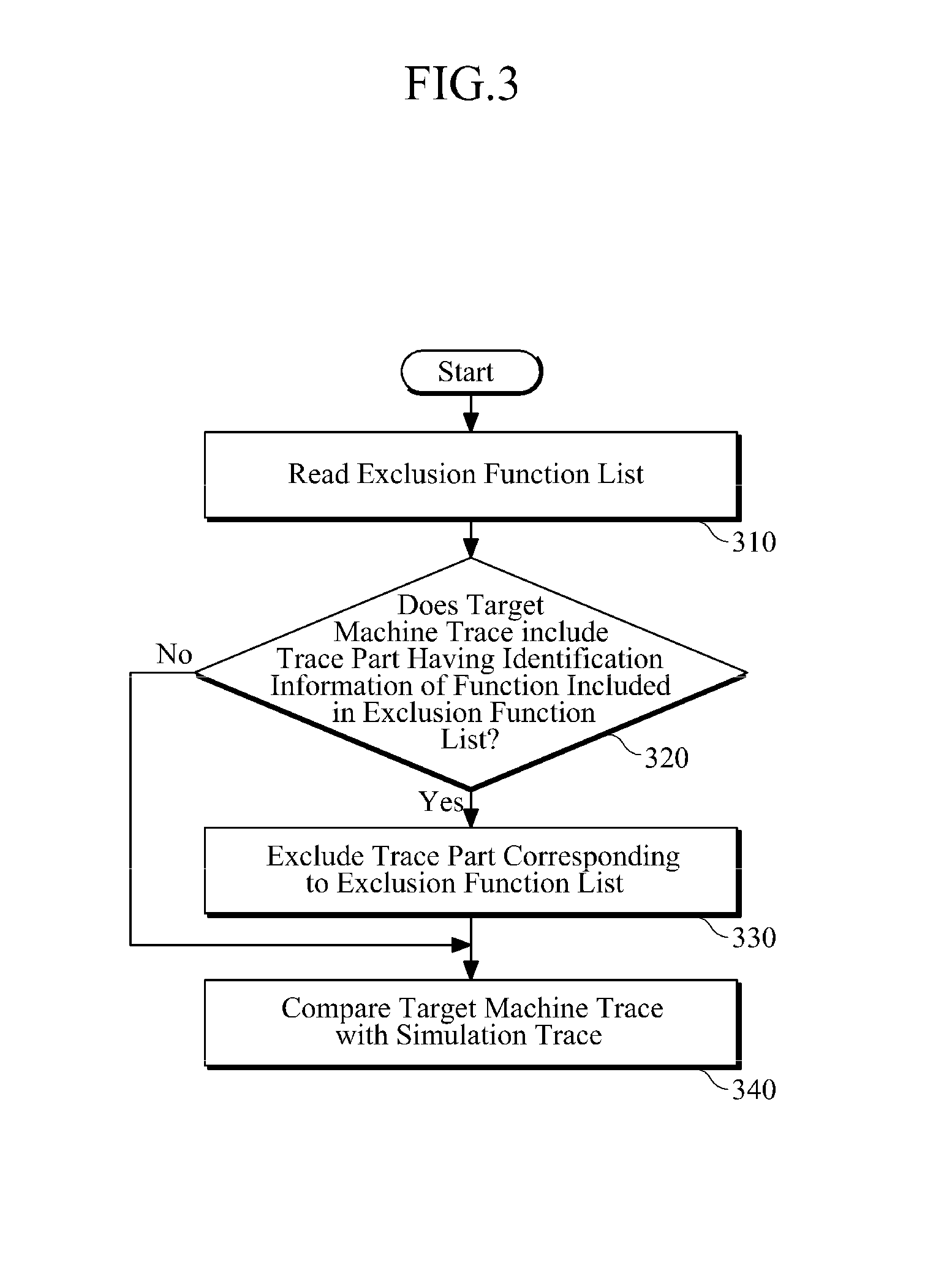
An apparatus and method for detecting software error are provided. Trace files are respectively generated by a target machine and a functional simulator that imitates the target machine and performs the same operation as the target machine. Each of the trace files may include at least one of a data-flow-type trace including execution information about one or more instructions and a control-flow-type trace representing information about a part in which a change in address indicating the position of an instruction is a predetermined threshold value or more when the instruction is executed. By comparing the generated trace files, software error may be detected.
Owner:SAMSUNG ELECTRONICS CO LTD
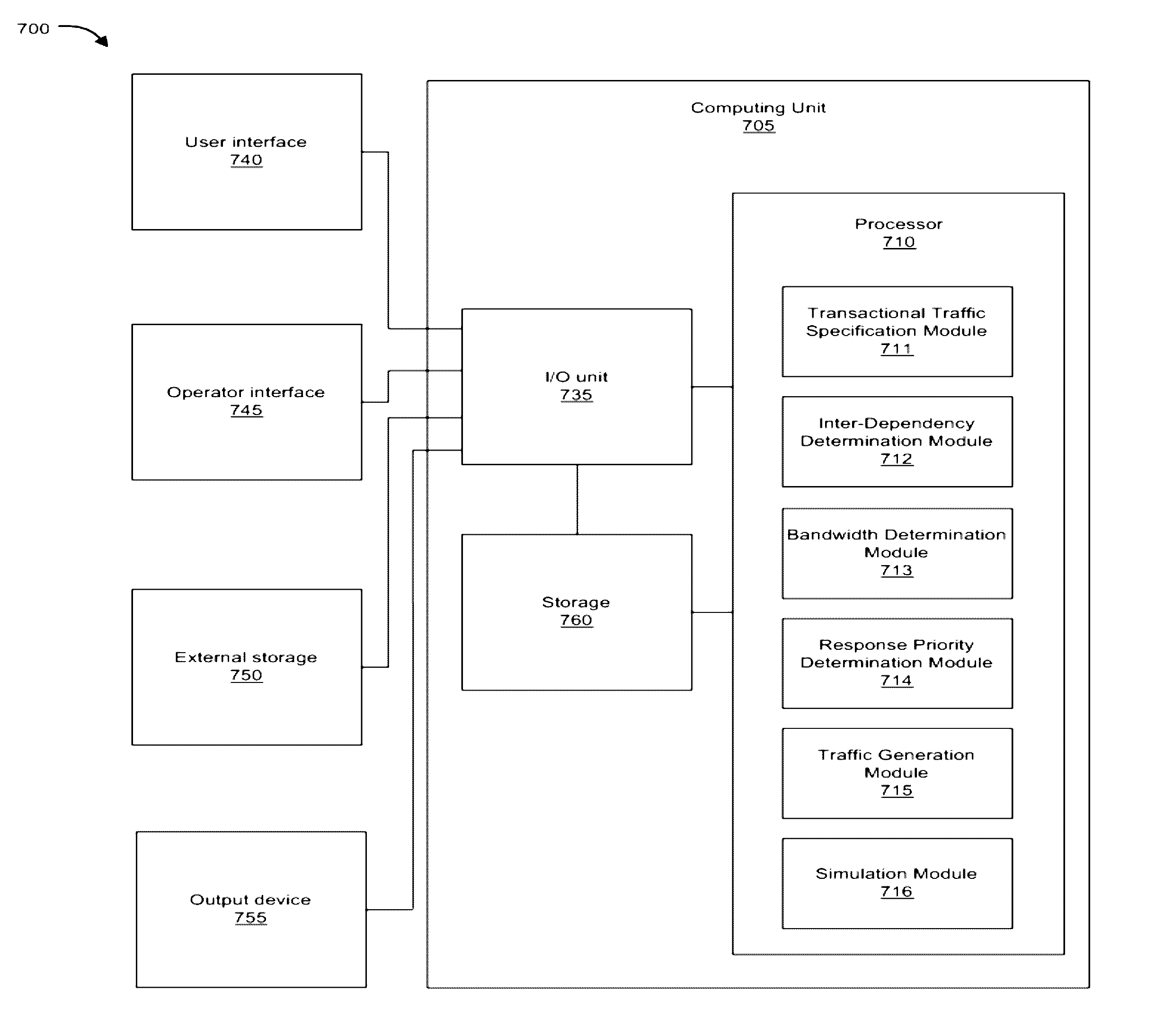
Transactional traffic specification for network-on-chip design
Example implementations described herein are directed to a consolidated specification with information to generate and optimize the NoC. The consolidated specification can also facilitate the generation of traffic trace files. Based on the trace files, performance simulation where packets are injected in the NoC can be conducted. The consolidated specification can include parameters for bandwidth, traffic, jitter, dependency information, and attribute information depending on the desired implementation.
Owner:INTEL CORP
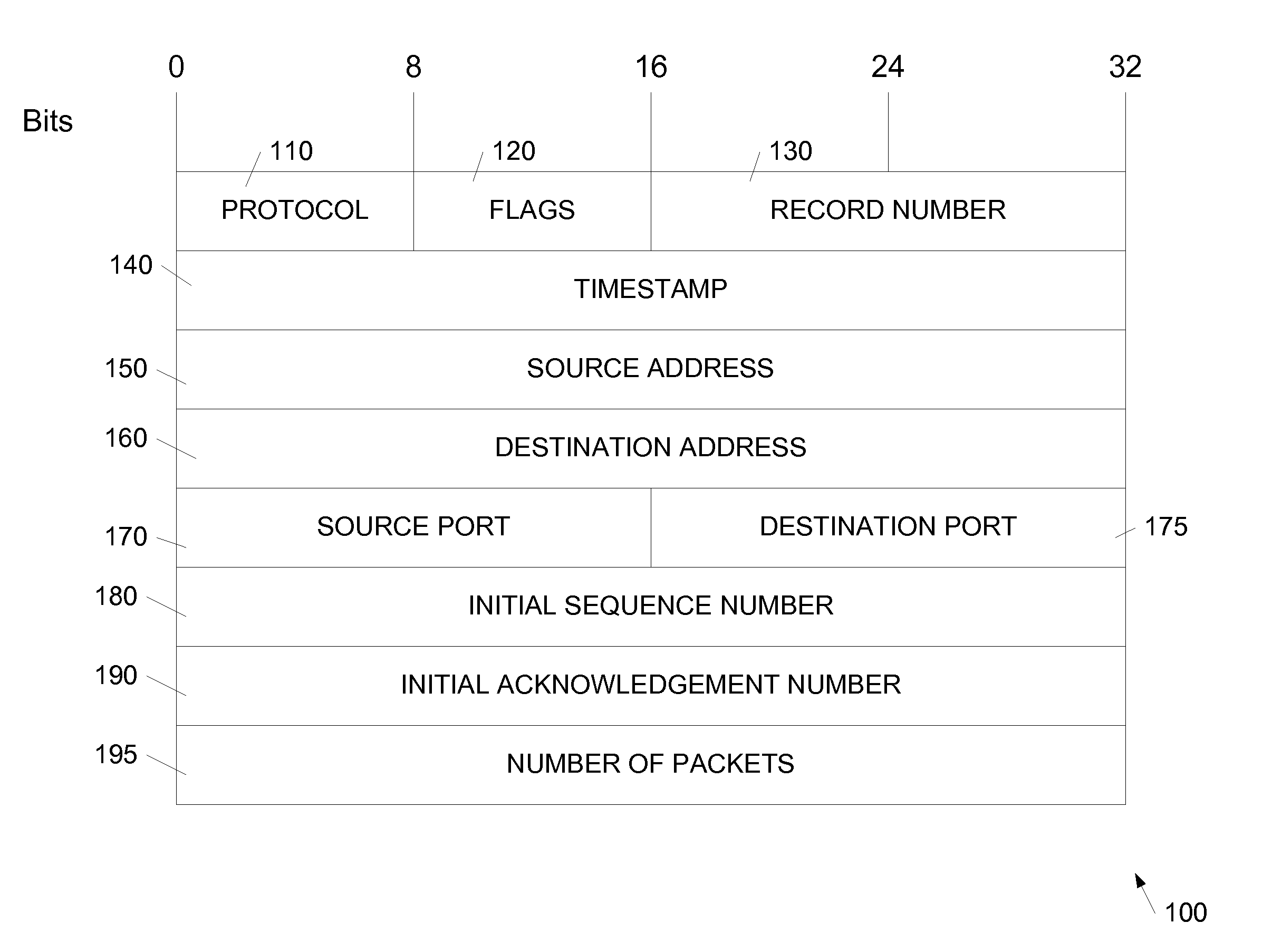
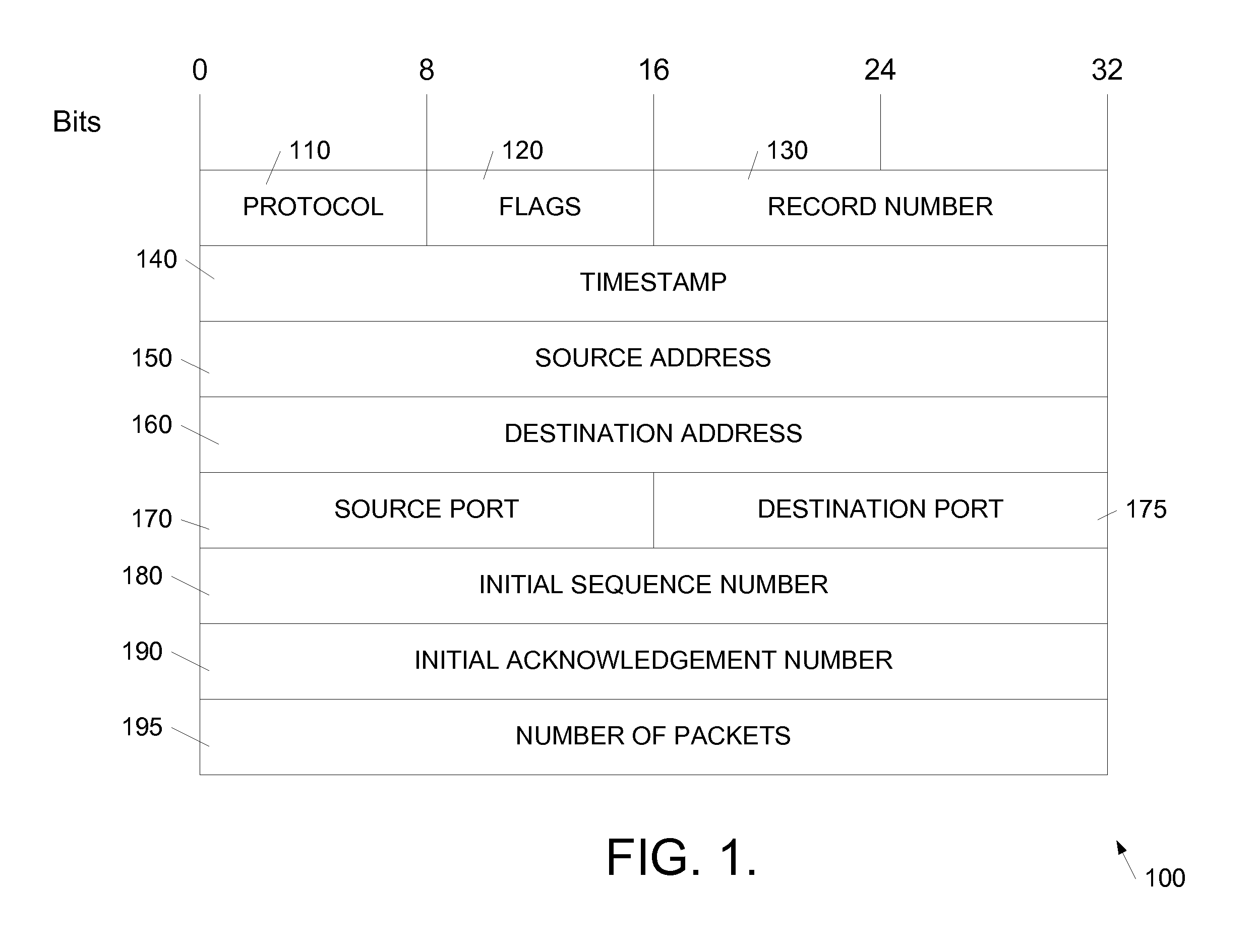
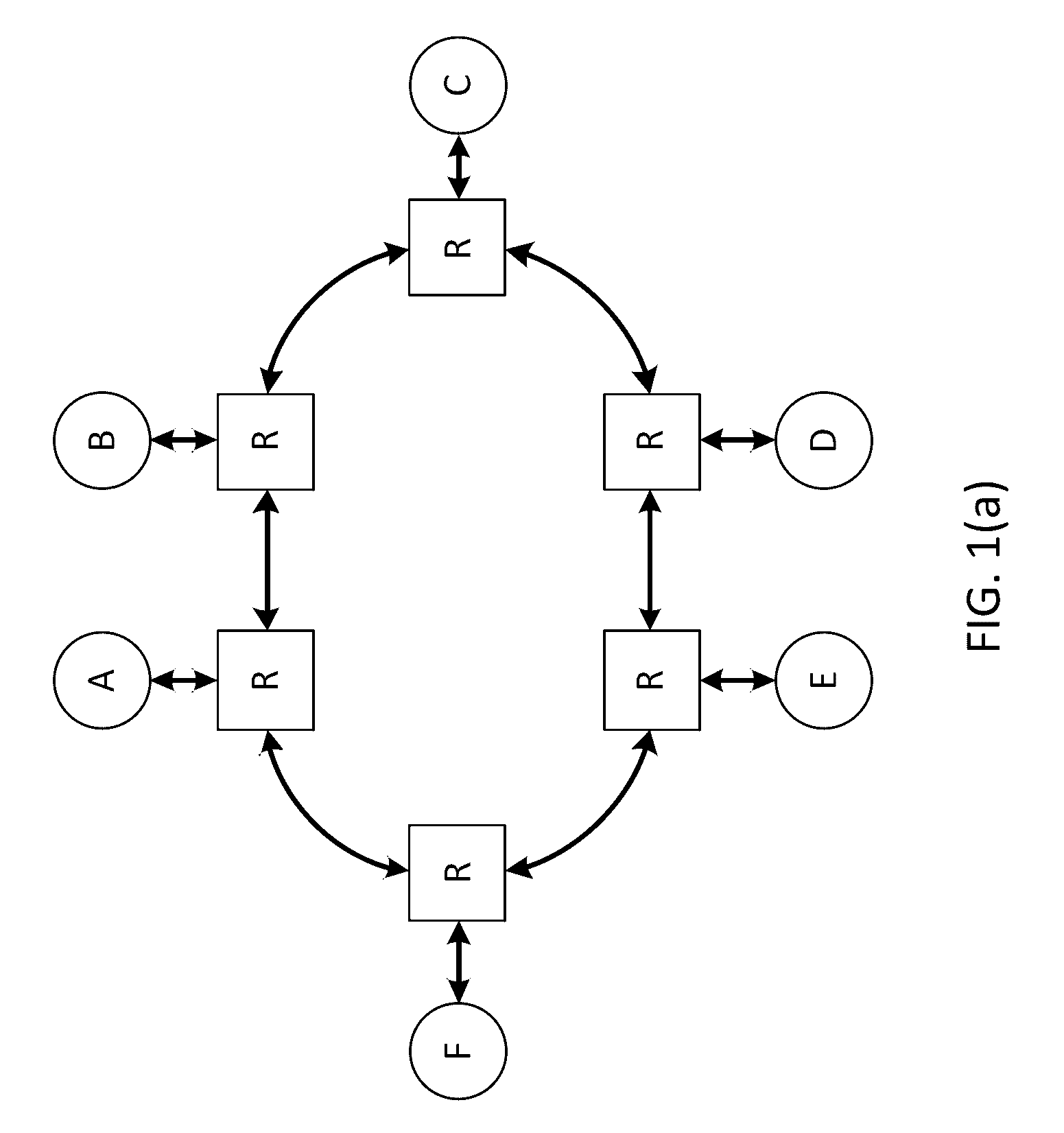
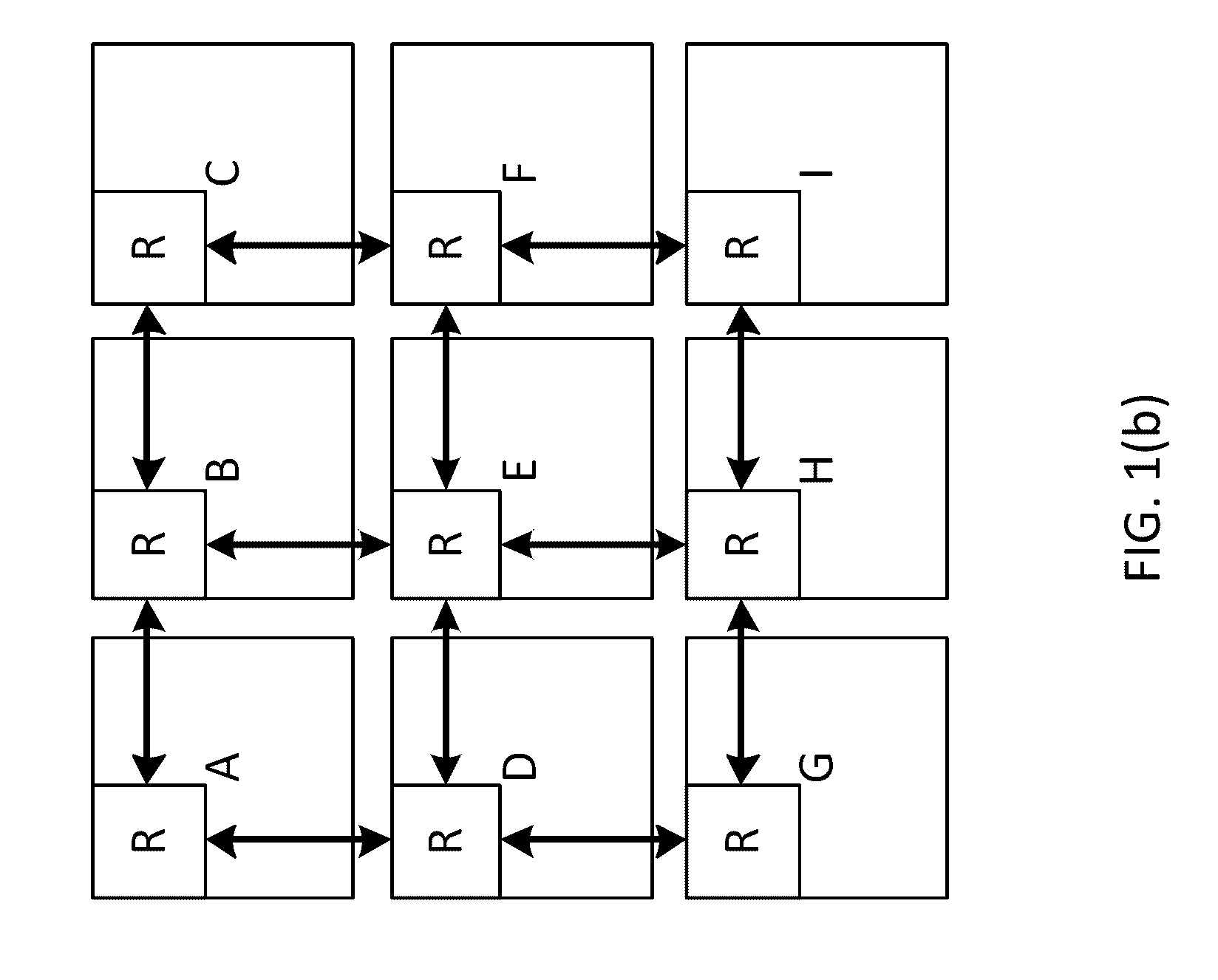
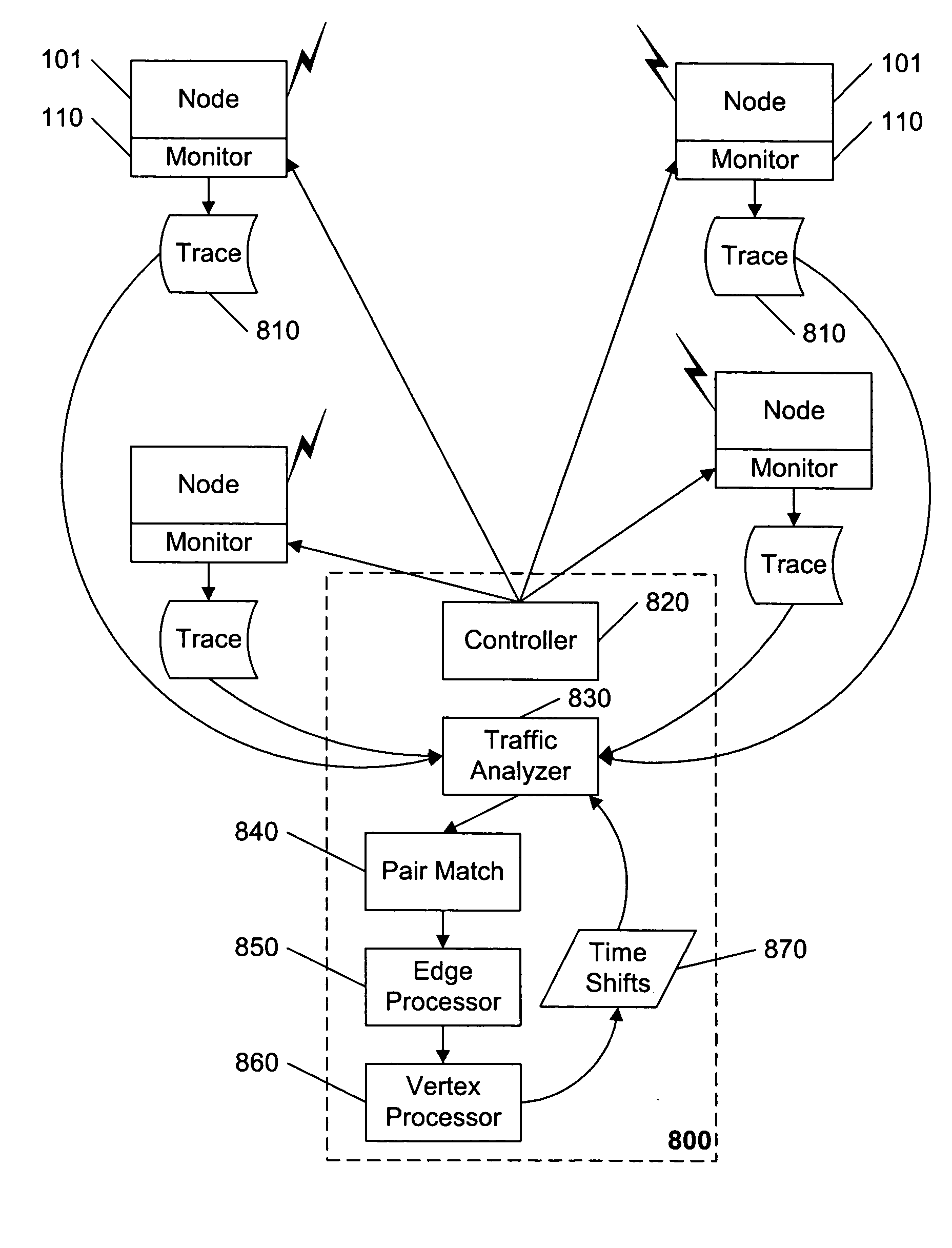
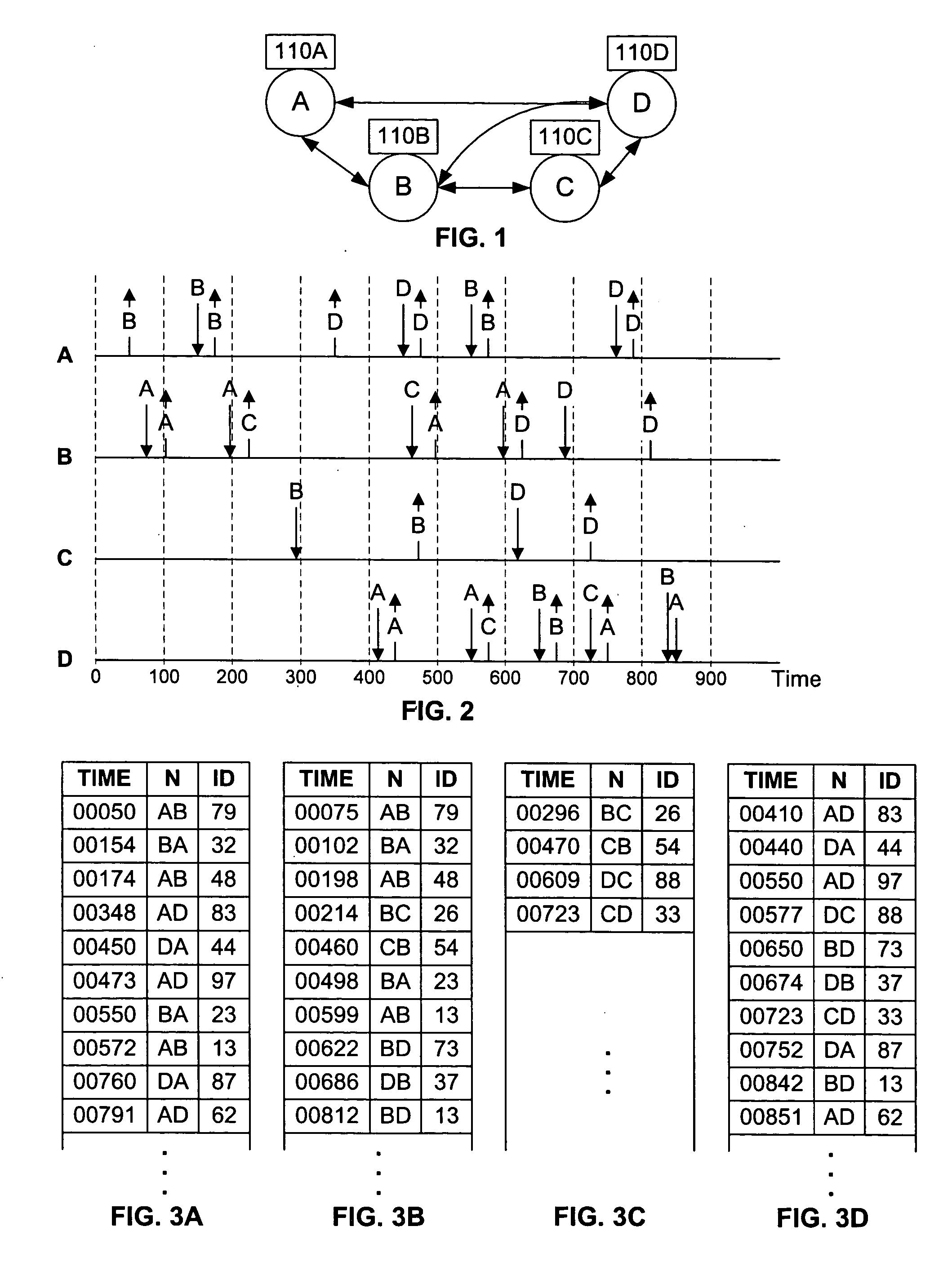
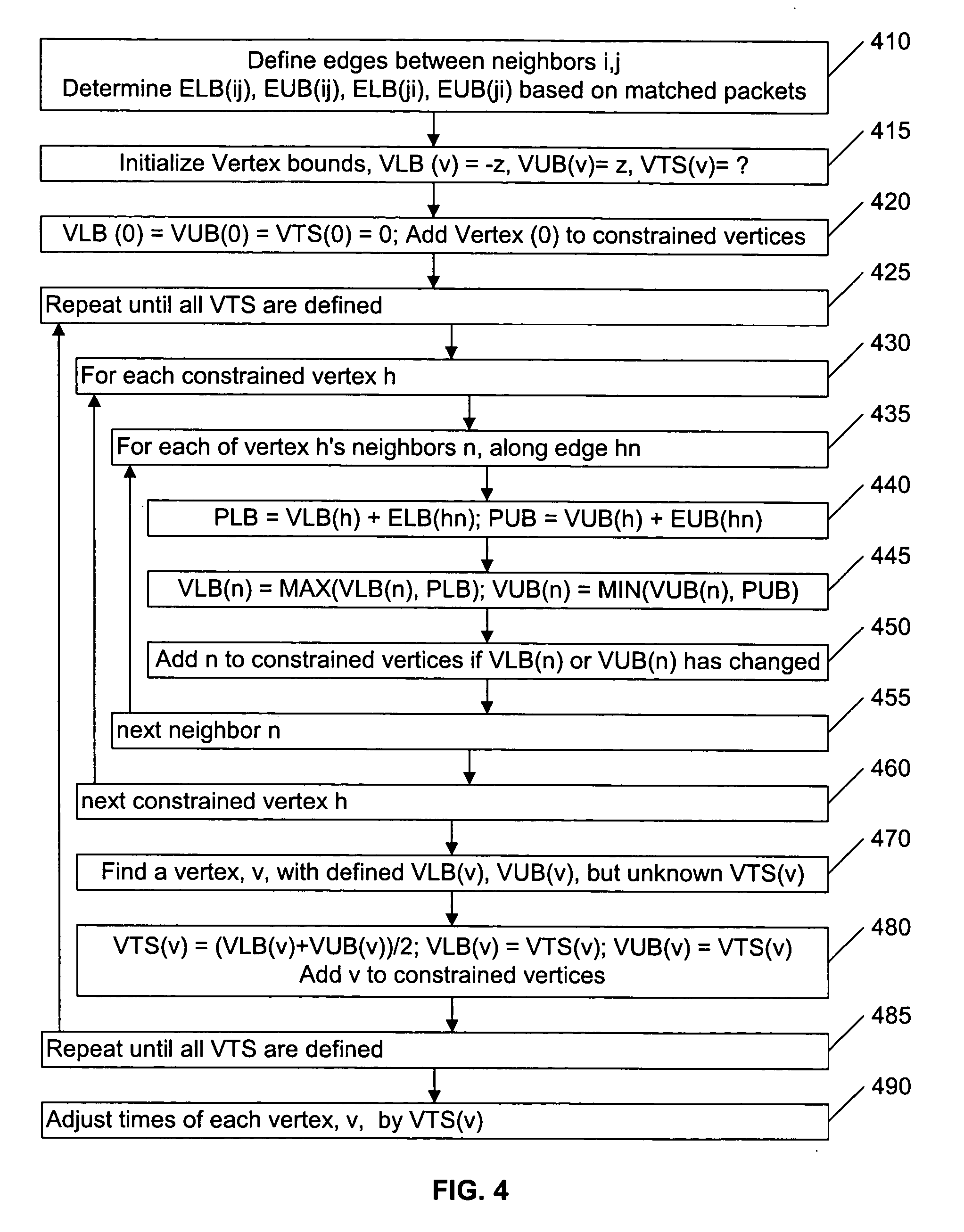
Synchronizing packet traces
A system and method for determining a common time base among nodes in a network by iteratively propagating timing constraints among the nodes, and determining a time-shift to apply to the time base of each node that conforms to these constraints. “Trace” files record the time of transmission or reception of packets at each node, based on the time base at the node. A fundamental constraint in a common time-based system is that the time of reception of a packet at a destination node cannot be prior to the time of transmission of the packet from a source node. A further constraint in a common time-based system is that the time of reacting to an event cannot be prior to the time of the event. By concurrently tracing traffic among multiple nodes in a network and subsequently processing the trace files to assure that each packet's transmission occurs prior to its reception, and that each reaction packet occurs after its corresponding causal packet, a correspondence between each node's time base and the common time base can be determined.
Owner:RIVERBED TECH LLC
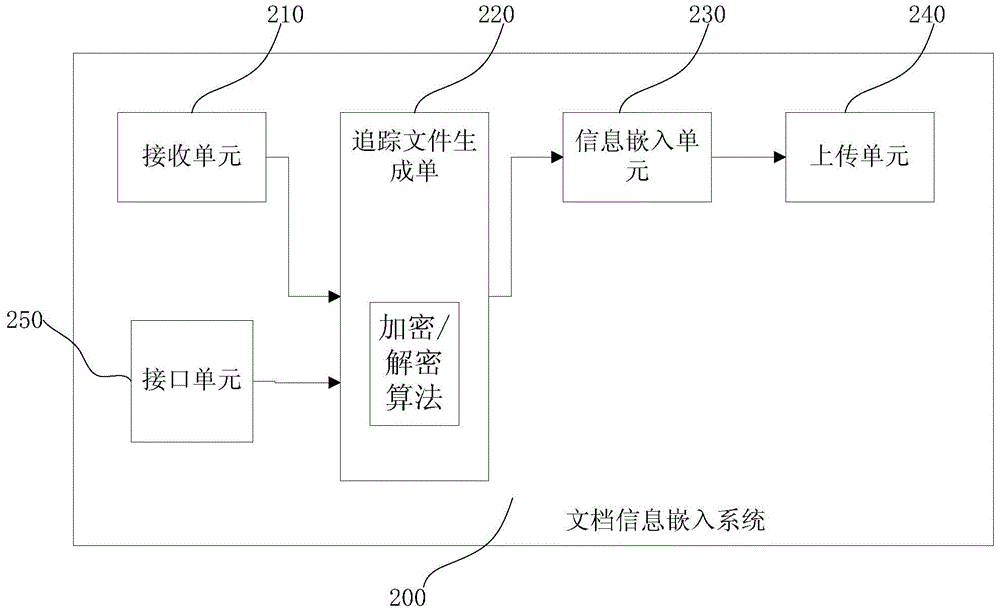
Document information embedding and tracking methods and systems and proxy service equipment
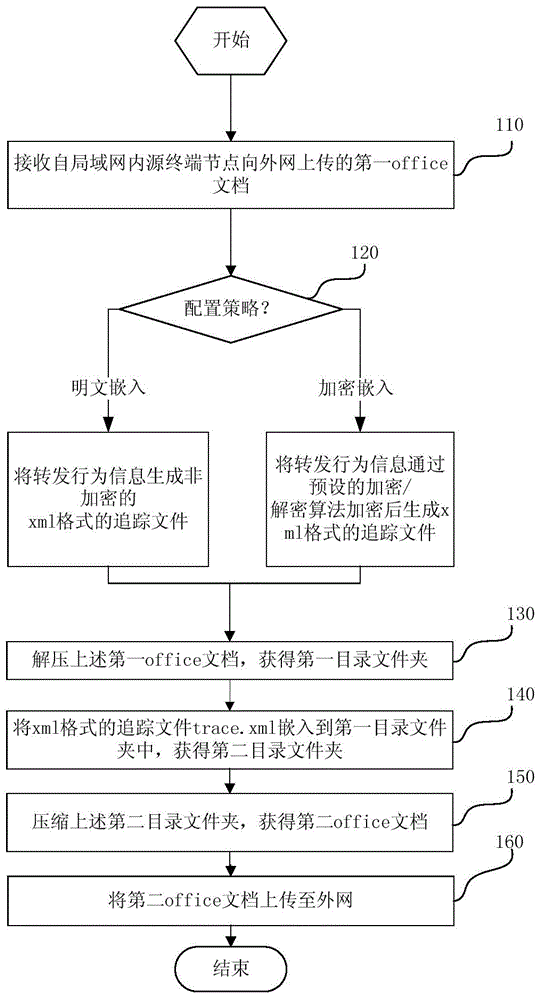
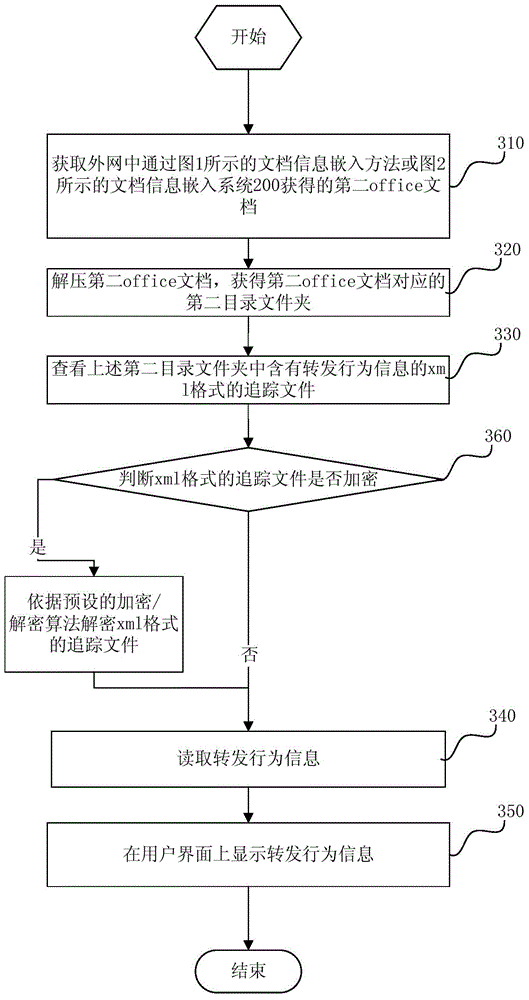
ActiveCN104657637AResolve persistent storageSolve operational problemsProgram/content distribution protectionDocumentation procedureDocument preparation
The invention provides document information embedding and tracking methods and systems and proxy service equipment. The document information embedding method comprises the following steps: receiving a first office document uploaded from a source terminal node in a local area network to an extranet; generating a trace file in an xml (extensive markup language) format from forward behavior information according to a configuration strategy, wherein the forward behavior information comprises at least source terminal node login information, an IP (Internet Protocol) address of the source terminal node and office document upload time; embedding the tracking file in the xml format into the first office document to obtain a second office document for uploading. After information leakage, related information generated by a secret leakage behavior can be acquired by examining or decoding operator information in the leaked Office document.
Owner:SANGFOR TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com