Document information embedding and tracking methods and systems and proxy service equipment
A document information and document technology, applied in the field of system and agency service equipment, can solve the unfavorable long-term preservation of audit information, difficulties and other problems, and achieve the effect of solving the problem of easy operability and long-term preservation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
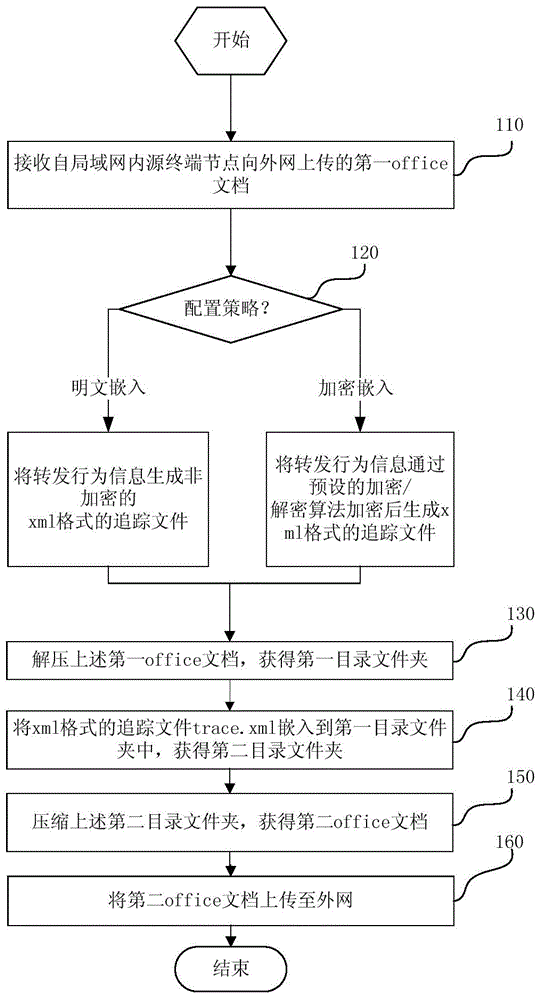
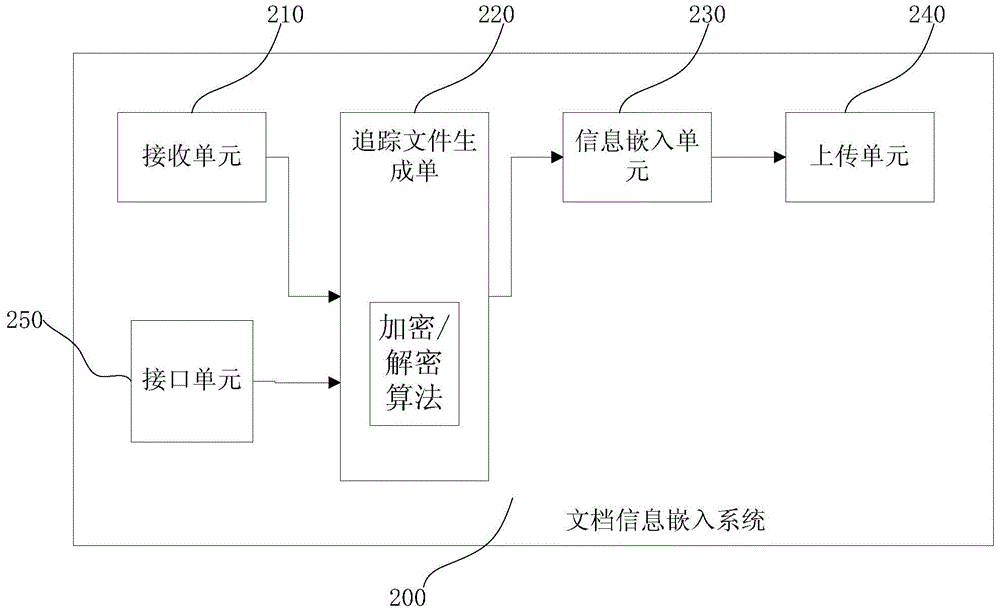
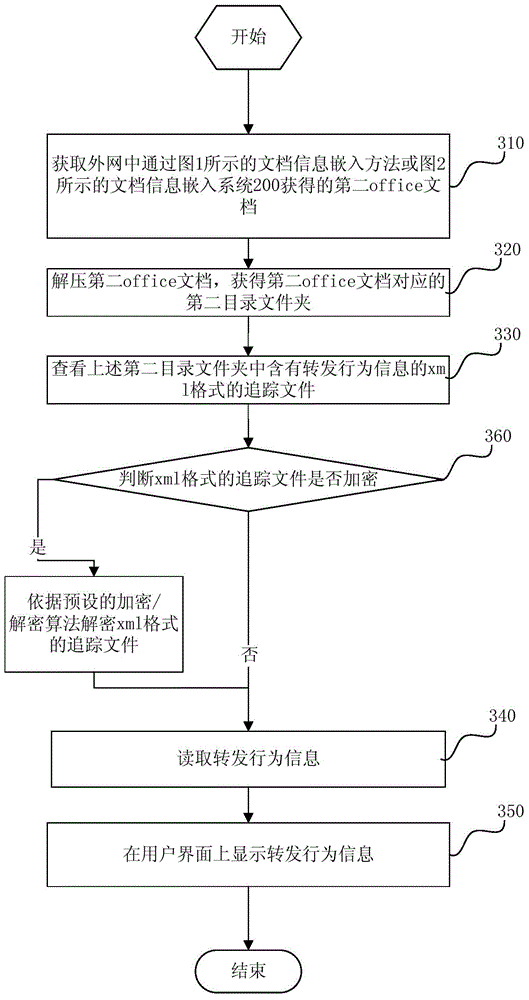
[0046] Based on the unique Open XML feature of Microsoft Office documents 2007 and later versions, the present invention can embed information embedded in office documents in the proxy server, track new methods and systems under the condition that the client PC does not install specific software. The function is to embed files related to the leaker in the original structure of office documents uploaded to the external network through the switch. The forwarding behavior information related to the leak includes the user name logged in at the source terminal node and the IP of the source terminal node. Address, time of leak and other information. When the relevant organization discovers that the document has leaked, it can obtain relevant information generated by the leak by viewing or decrypting the forwarding behavior information embedded in the leaked office document, making it possible to trace the specific leaker. And in the present invention, by embedding the leaking behavi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com