http flow defense method and system for resisting DDoS attack
A defense system and flow technology, applied in the transmission system, electrical components, etc., can solve the problems of inability to distinguish between normal clients and illegal attacker traffic, incompleteness, and many restrictions, so as to improve recognition and performance processing capabilities, and general strong effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
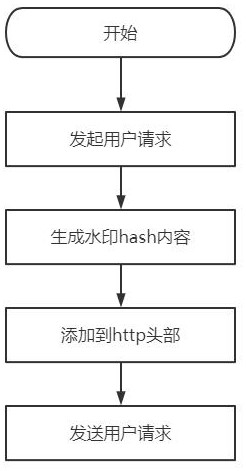
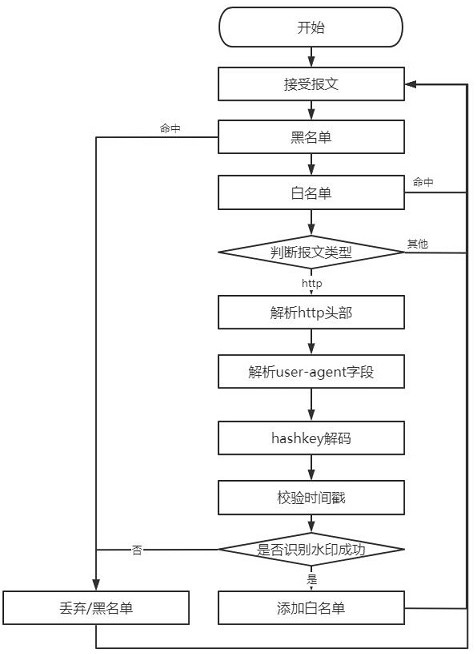
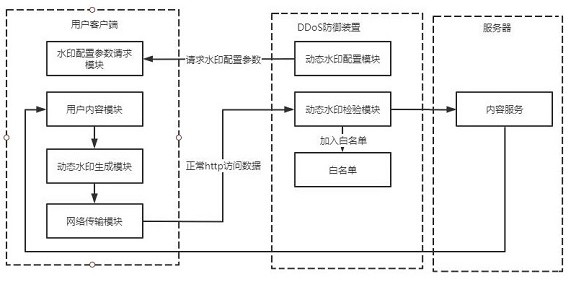
[0044] This embodiment proposes an anti-DDoS attack http traffic defense method, based on the anti-DDoS attack http traffic defense system, such as figure 1 , image 3 As shown, the method first performs watermark configuration on the head of the http access request sent by the user content module through the dynamic watermark generation module, and then normally sends the http access request, and the watermark of the head of the http access request is checked by the dynamic watermark inspection module Analyze the watermark field; finally, manage the IP corresponding to the http access request according to the result of the analysis;
[0045] Before watermark configuration, the watermark configuration parameter request module requests watermark configuration parameters from the dynamic watermark configuration module through an encrypted channel, and then the dynamic watermark configuration module sends the watermark configuration parameters to the watermark configuration param...
Embodiment 2
[0048] In this embodiment, on the basis of the above-mentioned embodiment 1, in order to better realize the present invention, further, the watermark hash content is configured in the user-agent field of the header of the http access request.
[0049] Working principle: Based on the design of the generation and verification mechanism of the watermark information added to the HTTP header, including but not limited to the user-agent field, it protects other common or custom fields of the HTTP header with similar mechanisms. The user-agent field is read-only for the server and does not affect the parsing and use of the server. You can also add parameters to other header field parameters or custom parameters, and then obtain the encrypted string watermark hash content. For example, by reading user-agent=Mozilla / 5.0 (Windows NT 10.0; Win64; x64) hash-AF11SD22SSDLKJJ, the result of obtaining the watermark hash2 content after analyzing the keyword hash is AF11SD22SSDLKJJ.
[0050] Ot...
Embodiment 3
[0052] In this embodiment, on the basis of any one of the foregoing embodiments 1-2, in order to better realize the present invention, further, the watermark hash content includes the second-level timestamp parameter Timestamp, source sip, source port sport, key key, time range conf_time, configured encryption method alg;
[0053] The generating formula for generating the watermark hash content is hash=f(timestamp / conf_time, sip, sport, key, alg);
[0054] The f() function is used to control through the alg parameter, and the input parameters are calculated to obtain the watermark hash content, and the operation is quickly completed through binary AND or NOT.
[0055] Working principle: The f operation is performed here to solve the problem of inaccurate watermark caused by message transmission on the network.
[0056] Other parts of this embodiment are the same as those of any one of Embodiments 1-2 above, so details are not repeated here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com