Distributed intrusion detection method and system for ad hoc network
An intrusion detection and self-organizing network technology, applied in the field of network security, can solve problems such as complex data types, limitations in processing and detection capabilities, and decision-making errors, achieve accurate intrusion detection, avoid malicious interference, and ensure authenticity and reliability. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be further described in detail below through specific embodiments in conjunction with the accompanying drawings.
[0033] Blockchain (Blockchain) technology, as a decentralized distributed ledger technology, has a traceable, non-tamperable and timed data structure, and its distributed consensus maintains trust among multiple parties.
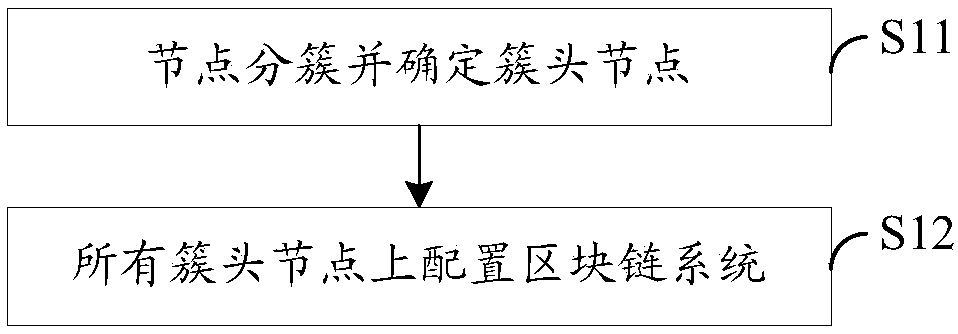
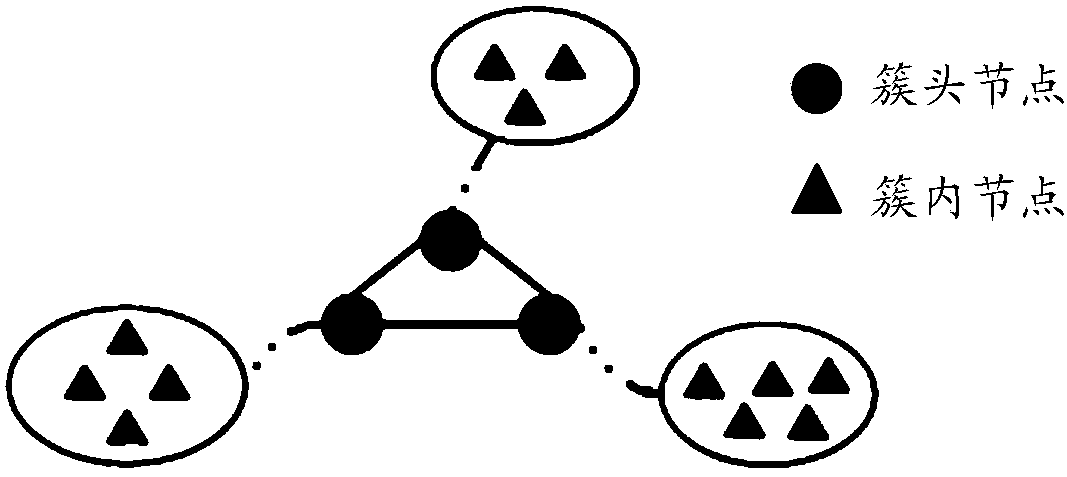
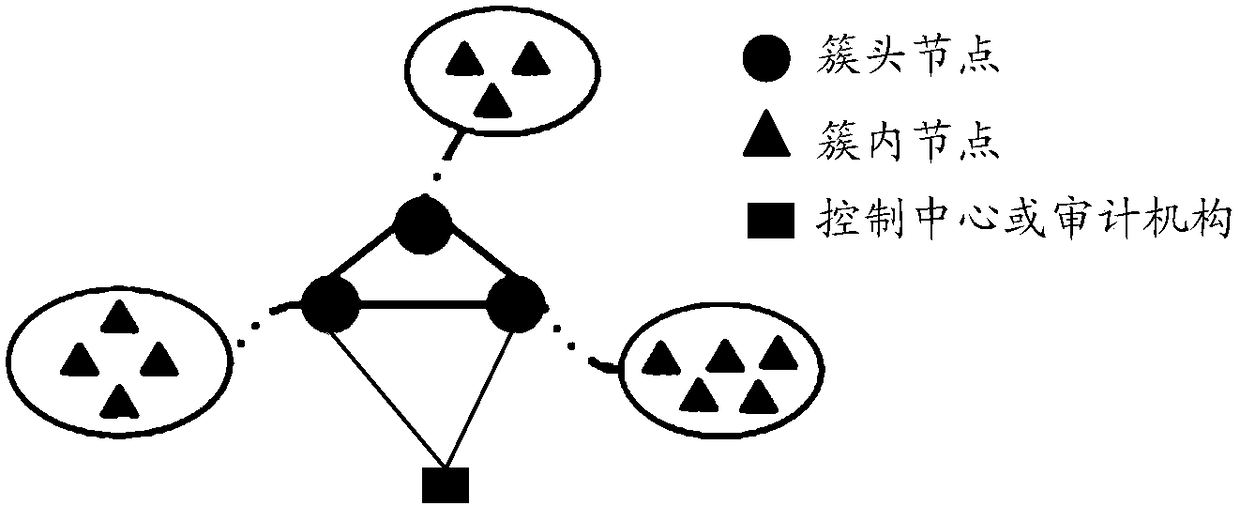
[0034] In the embodiment of the present invention, multiple nodes in the ad hoc network are divided into at least one cluster, and then the cluster head node of each cluster is selected as an agent for intrusion detection, and then the block chain system is configured on all the cluster head nodes, Form a blockchain network; when the log of a node is updated, the node sends a transaction request to the cluster head node of the cluster to which it belongs to request the blockchain system to verify and record, and the cluster head node receives the transaction request sent by the requesting node containing the The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com