An abnormal intrusion detection method for Internet of Vehicles based on the difference of traffic flow density
A technology of traffic flow density and intrusion detection, applied in the transmission system, electrical components, etc., can solve the problems of vehicle security loopholes, low classification accuracy, and time-consuming, etc., and achieve the goal of adapting to the moving speed, ensuring high efficiency, and ensuring integrity Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be described in detail below in conjunction with the accompanying drawings and examples.
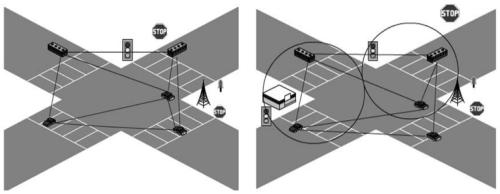
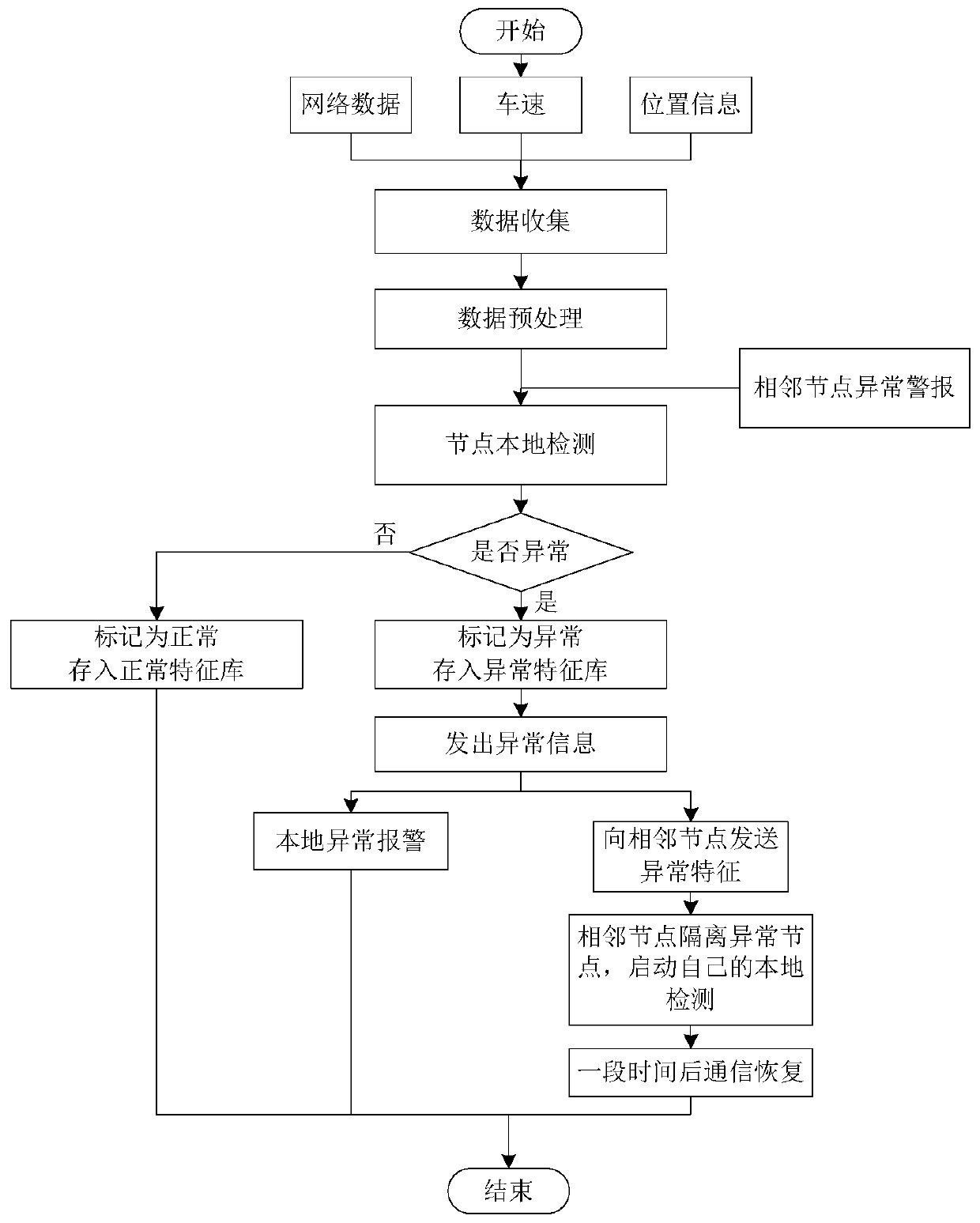
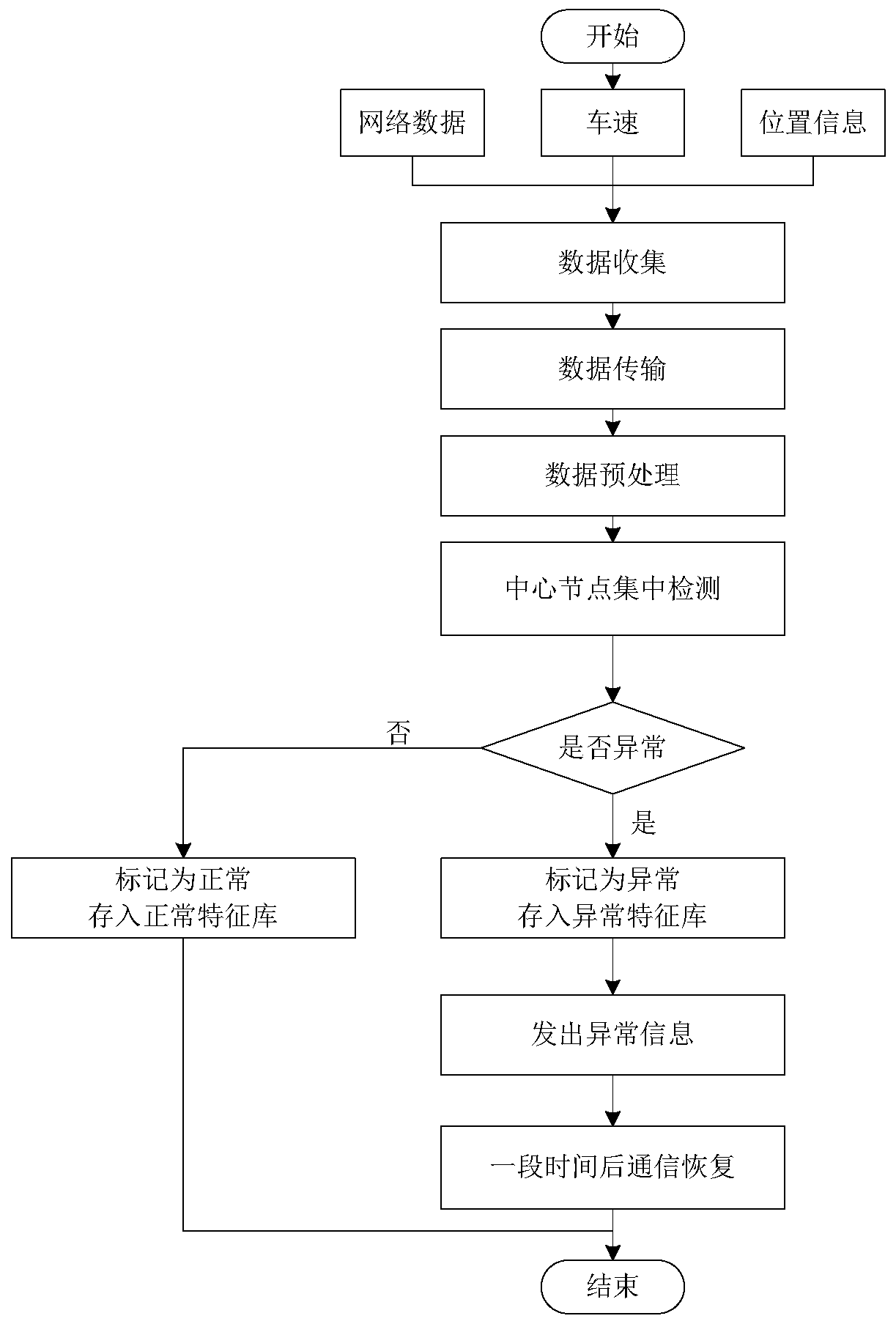
[0033] Such as figure 1 As shown, it is a traffic scene diagram of the application of the intrusion detection system of the present invention. The scene is divided into two types corresponding to the application of the two intrusion detection mechanisms. The traffic scene includes the vehicle ad hoc network and the vehicle and roadside base station. The internet. Each vehicle is equipped with an on-board unit for information collection and local detection, and the dedicated communication unit of each roadside base station is connected to a computer for centralized detection. In the method of the present invention, network data packets and basic traffic information, including vehicle speed, position, etc., are obtained in real time through the vehicle-mounted unit and the roadside base station on each vehicle in the network. Then anomaly intrusion detec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com