Zombie machine detection method based on alarm association
A detection method and alarm technology, applied in the field of the Internet of Things, can solve problems such as time-consuming, tedious, and difficult updates, and achieve the effect of reducing bad consequences and reducing false alarm rates
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
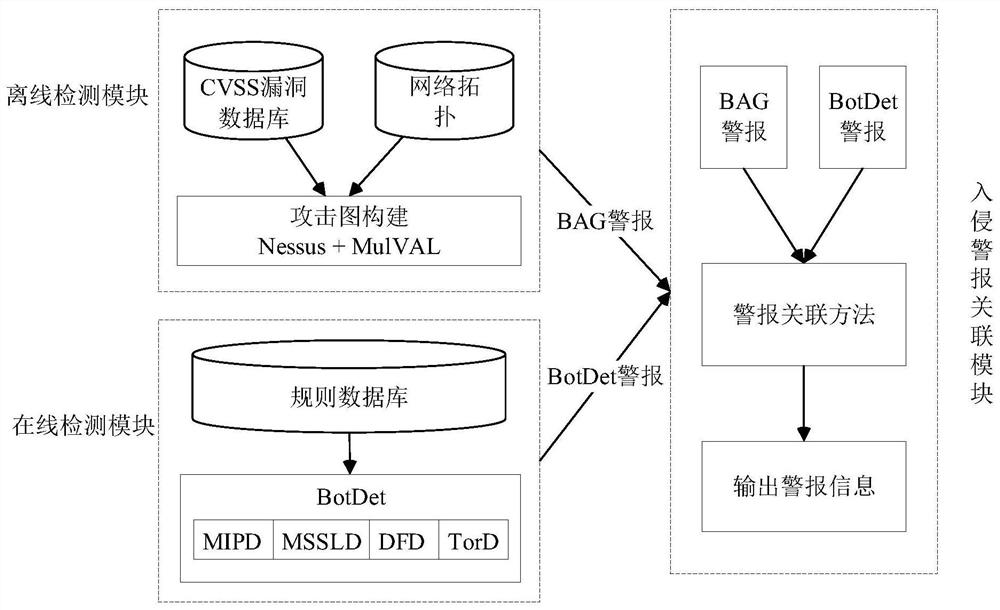
[0045] Such as figure 1 As shown, a zombie machine detection method based on alarm correlation includes the following modules: an online intrusion detection module, an offline intrusion detection module and an intrusion alarm correlation module, wherein:
[0046] The online intrusion detection module uses existing technical solutions to detect real-time network traffic;
[0047] The offline intrusion detection module uses the improved attack graph technology to evaluate the security status of the virtual machine;
[0048] The intrusion detection alarm association module includes alarm aggregation and alarm verification, which is used to associate the alarms of the online intrusion detection module with the results of the offline intrusion detection module, finally judge whether an intrusion occurs, and output alarm information.
[0049] The above-mentioned online intrusion detection module uses existing technical solutions to detect real-time network traffic; the online intru...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com