Data merging mechanism for large distributive intrusion inspecting system
An intrusion detection system and real-time data technology, applied in the field of network security, can solve problems such as technical means that are difficult to prevent and economic losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
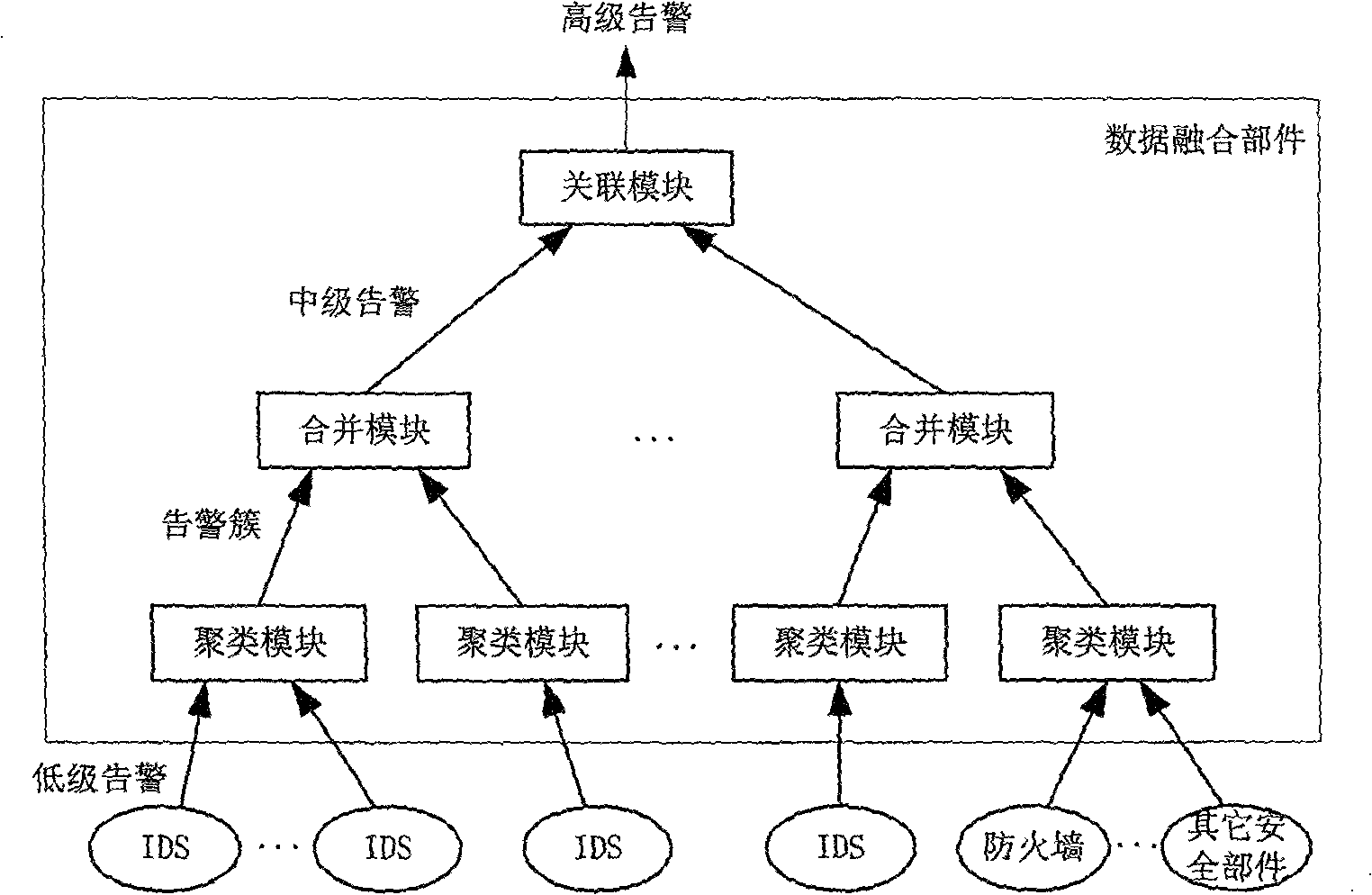
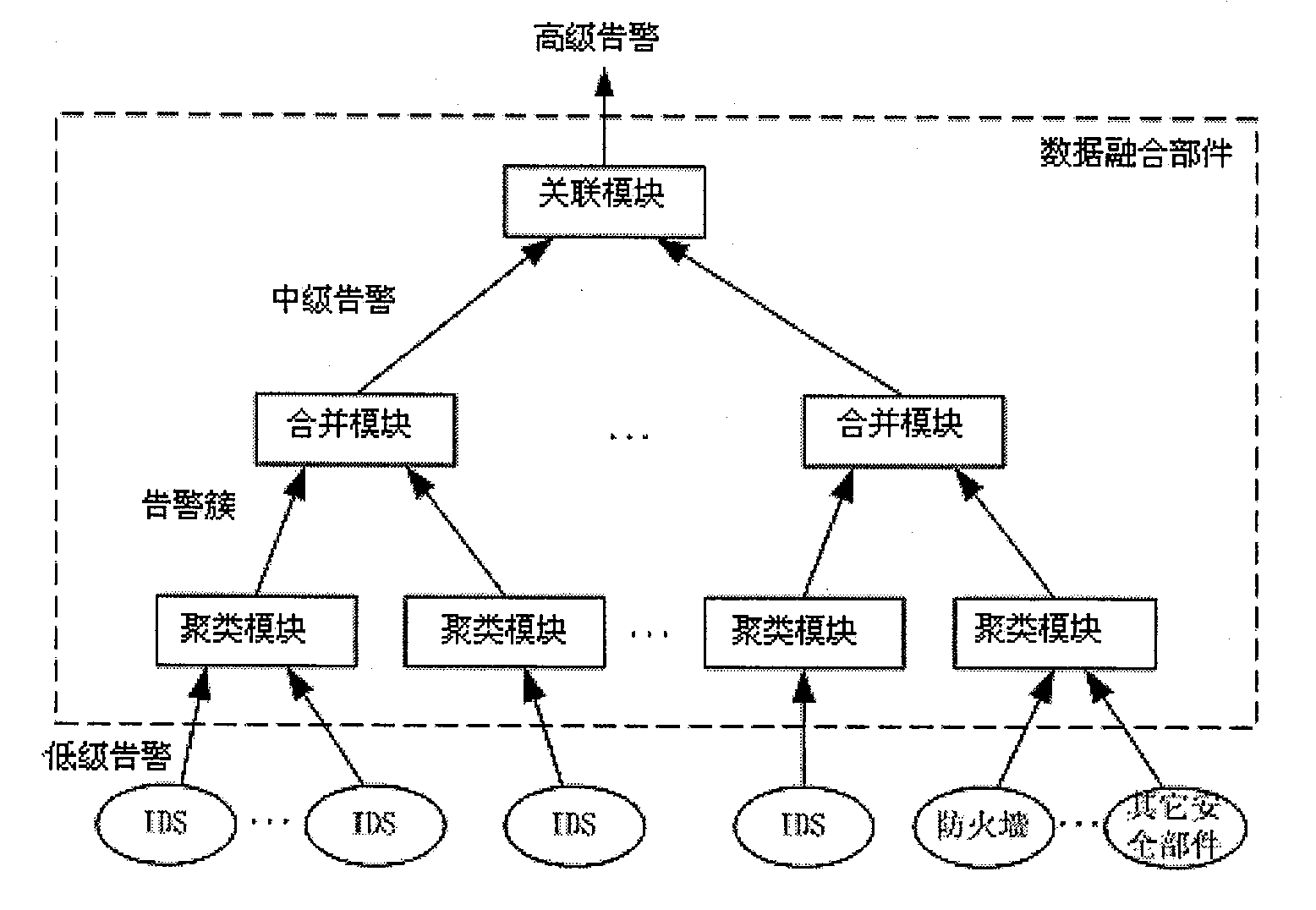
[0098] The data fusion method proposed by the invention has good expansibility, is very suitable for the characteristics of a large-scale distributed intrusion detection system, and can adopt different numbers of data fusion modules for different system scales.
[0099] 1) Small network
[0100] For a smaller network environment, such as an enterprise network with less than 100 computers, use the following figure 1 A data fusion component as shown will suffice.
[0101] 2) Large network
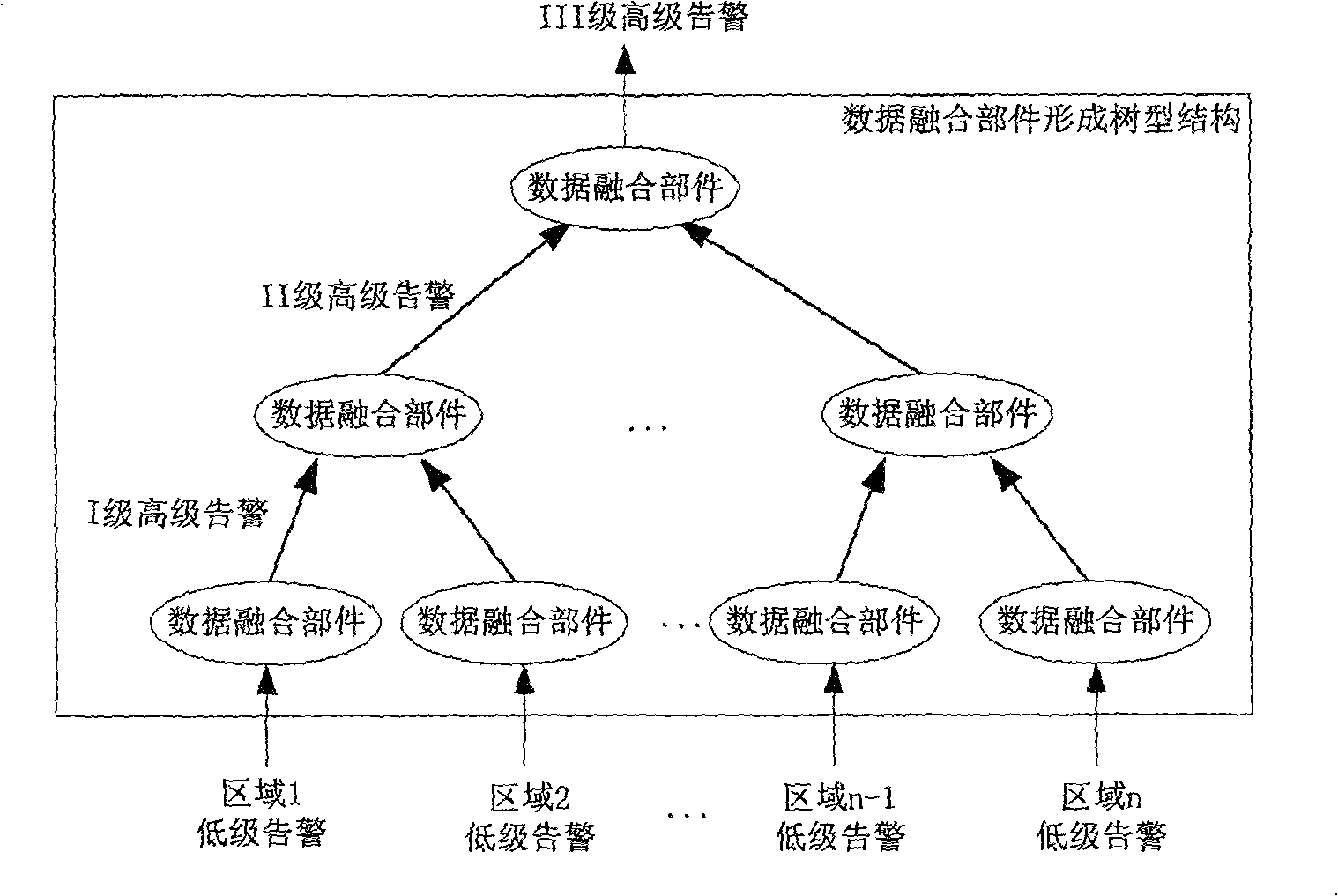
[0102] For a large-scale distributed network environment, such as the China Education Network, which has millions of computers, some preparatory work is required to deploy the data fusion module: Step 1: Divide the network by domain: use network security authorization Based on the principle of regionalization, a large network is divided into multiple security domains, and a data fusion module is placed in each domain; the second step is to choose an appropriate way to organize these data fu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com