Distributed intrusion detection method, device and system
An intrusion detection and distributed technology, applied in the field of network communication, can solve problems such as large data traffic affecting network performance, and achieve the effect of reducing data traffic, ensuring reliability, and reducing impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
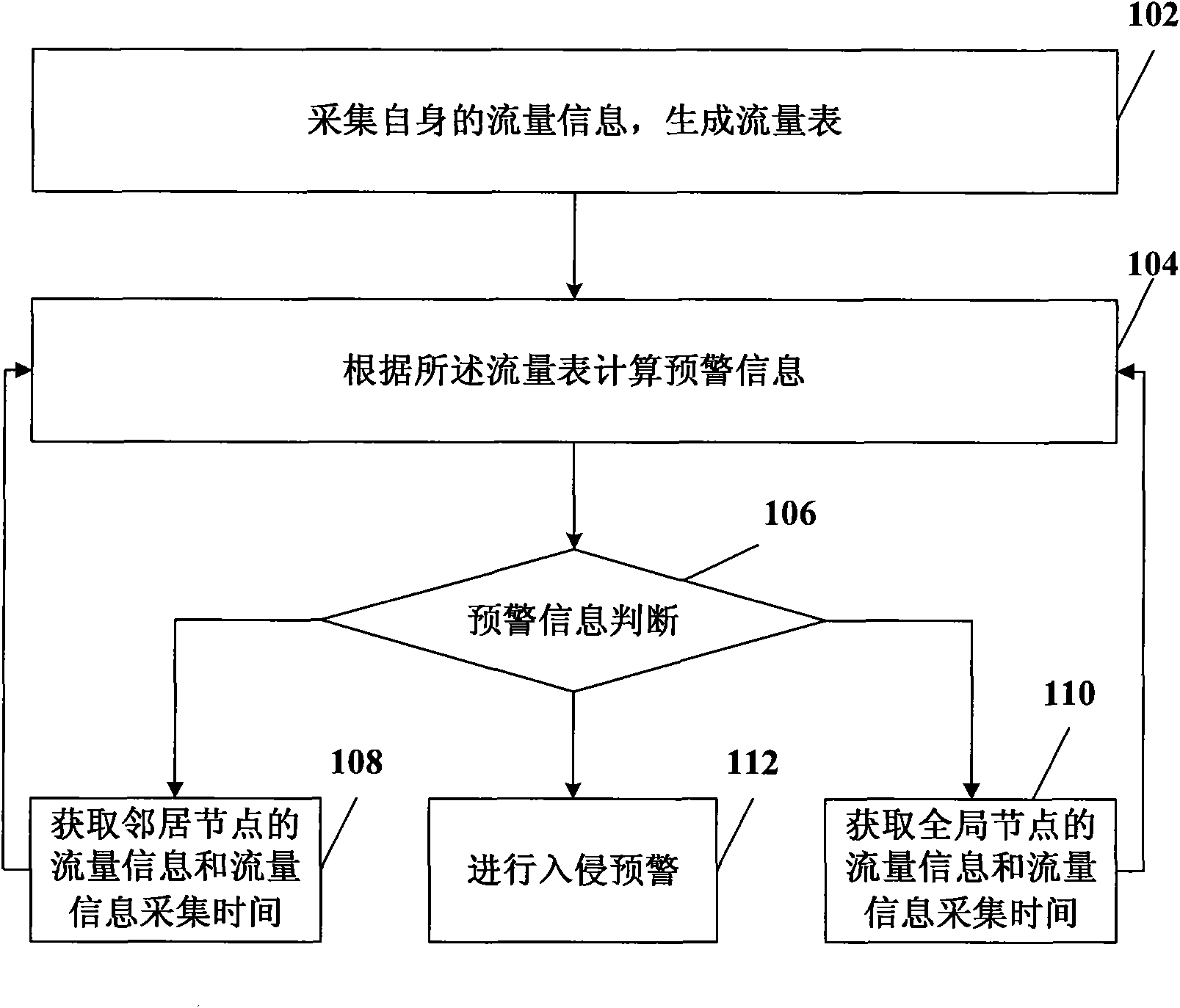
[0038] figure 1 It is a flowchart of a distributed intrusion detection method in an embodiment of the present invention. The method includes:
[0039] 102. Collect its own flow information and generate a flow table.
[0040]The network node collects its own flow information, and the flow information includes at least one of input packet rate; SYN request packet input rate and SYN confirmation packet input rate; ICMP packet rate; UDP packet input rate. These traffic information can be raw values or processed appropriately. For example, discretize the flow information. For example, all traffic information is quantified into 8 levels, that is, the finally obtained traffic information belongs to the set {0, 1, 2, 3, 4, 5, 6, 7}. The method of discretizing the original value of flow information can be to establish a fixed mapping relationship, such as fixedly mapping the original value within a certain range to a specific discretized flow information value; it is also possibl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com