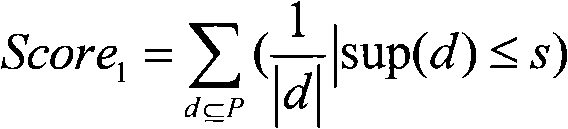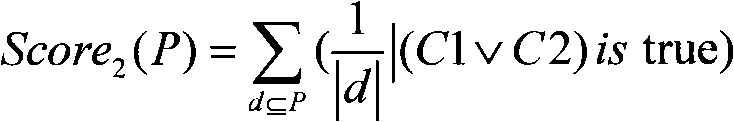Distributed intrusion detection method in wireless sensor network
A wireless sensor and intrusion detection technology, applied in data exchange networks, transmission systems, digital transmission systems, etc., can solve the problems of no intrusion detection, can not meet the requirements of wireless sensor network intrusion detection, etc., to reduce the amount of calculation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
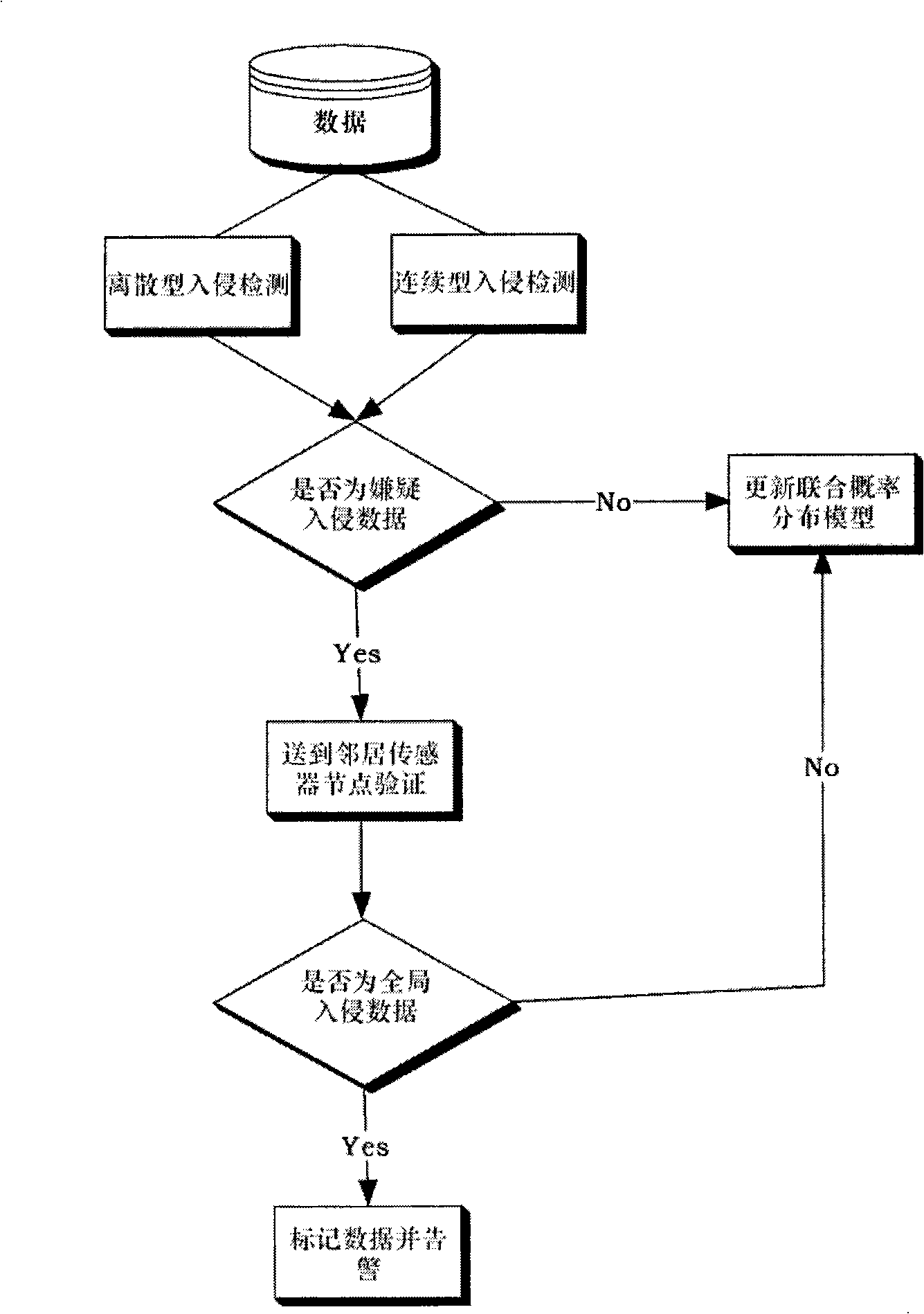
[0024] The embodiments of the present invention are described in detail below in conjunction with the accompanying drawings: this embodiment is implemented on the premise of the technical solution of the present invention, and detailed implementation methods and specific operating procedures are provided, but the protection scope of the present invention is not limited to the following the described embodiment.
[0025] In this embodiment, a Matlab program is used to simulate a wireless sensor network, and all sensor nodes are equal in status, and all participate in data collection and routing and forwarding functions. In addition to storing data and network logs, each sensor node also stores the information of neighbor nodes (one hop) and the joint distribution probability model of local network log data. In order to meet the real-time requirements, the sensor network nodes first run the apriori algorithm on the non-invasive data to obtain the frequency table of each item and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com