Flow characteristic analysis-based distributed intrusion detection method
An intrusion detection, distributed technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of low detection accuracy and detection efficiency, and achieve high-efficiency detection capabilities, timely and accurate detection effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
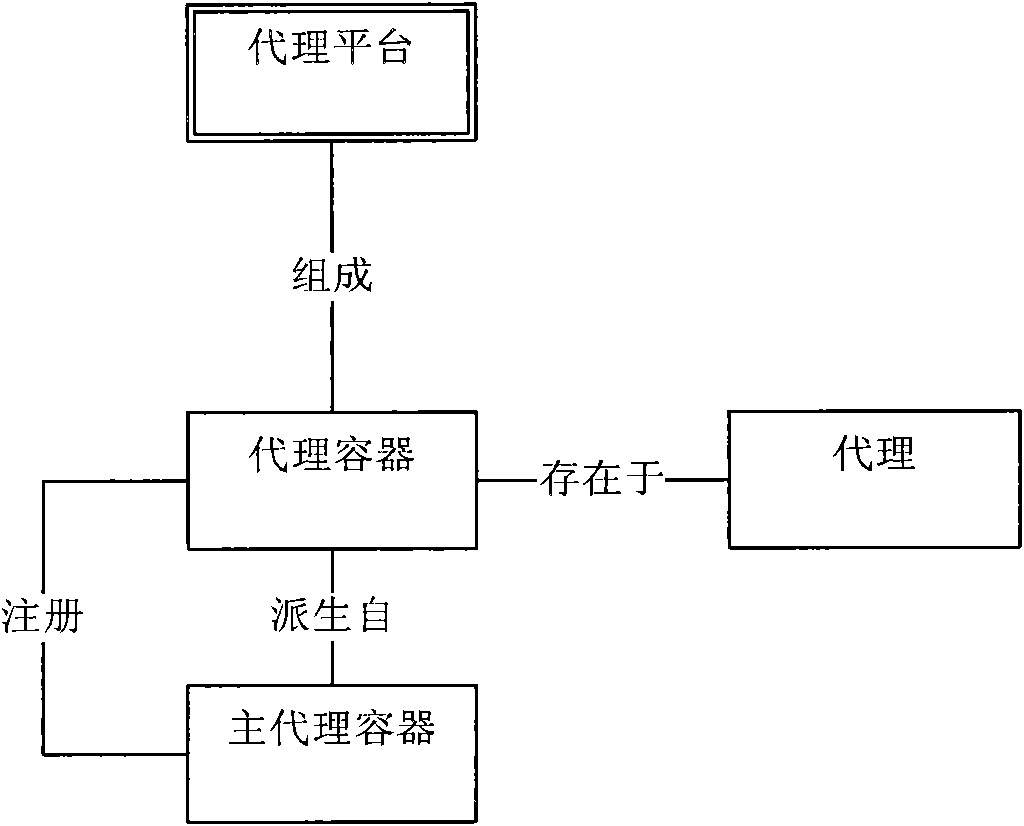
[0038] The implementation of methods such as the intrusion detection architecture and traffic characteristic algorithm proposed by the present invention is implemented through an actual intrusion detection system, and the deployment structure of the intrusion detection system is as follows Figure 4 shown.
[0039] Figure 4 In , the intrusion detection system includes two types of nodes:
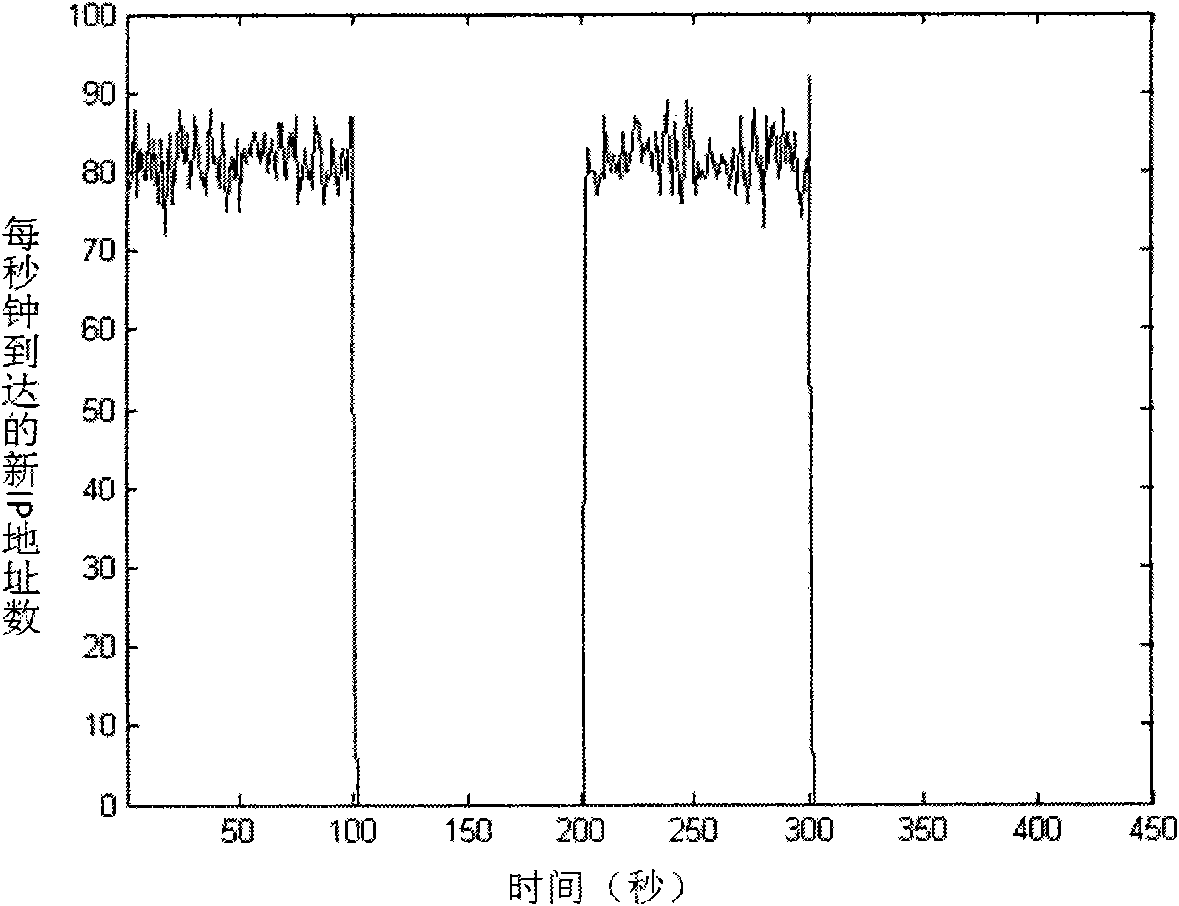
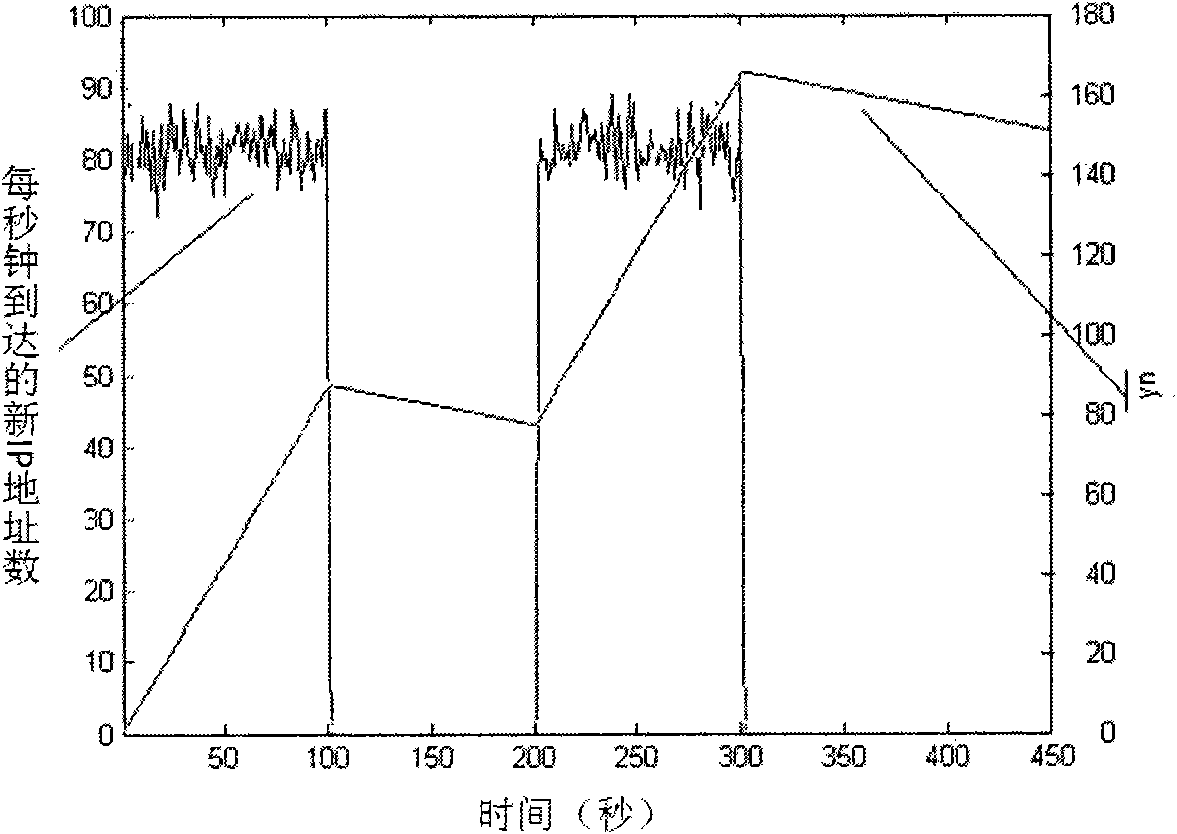
[0040] (1) Nodes deploying intelligent analysis and decision-making Agent: This type of node is set up with routing port mirroring for connecting the LAN to the external network, that is, from this type of node, the uplink or downlink network traffic of the entire network can be analyzed or captured. Deploy an intelligent analysis and decision-making agent on this node, so that the agent's network traffic analysis module can collect the traffic characteristic statistics of the entire network, and the intelligent analysis module applies the CUSUM algorithm for analysis. The interfaces at t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com