Task assigning mechanism for large-scale distributive invasion detecting system
An intrusion detection system and task assignment technology, applied in the field of network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
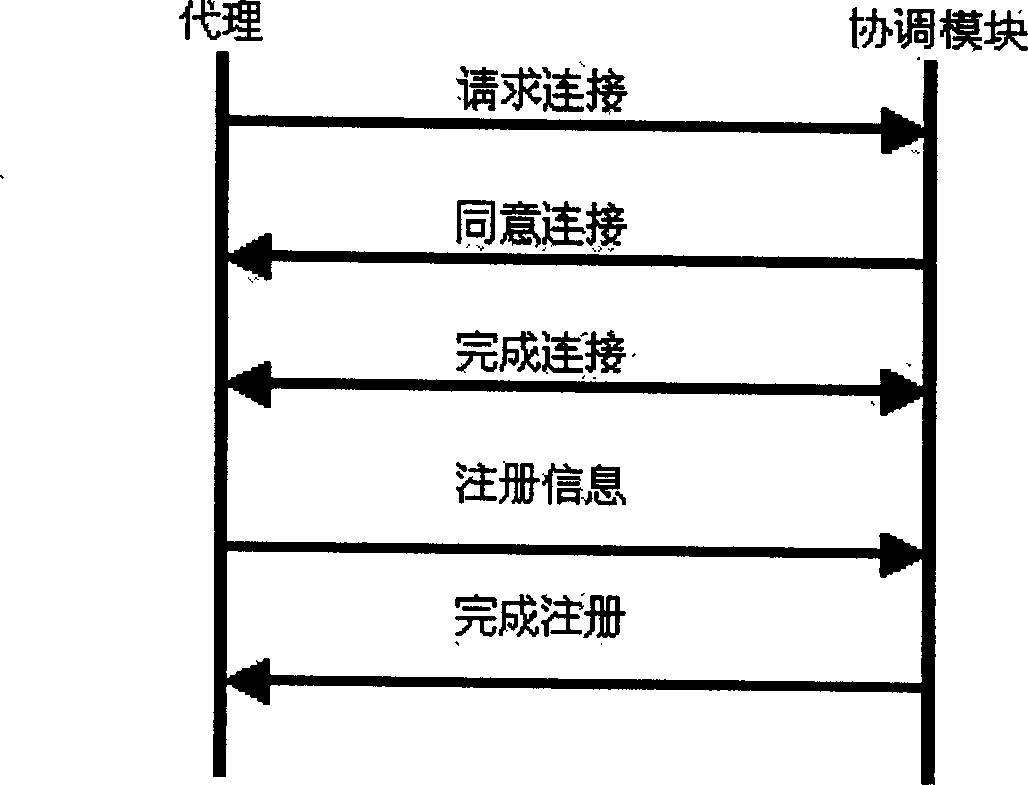
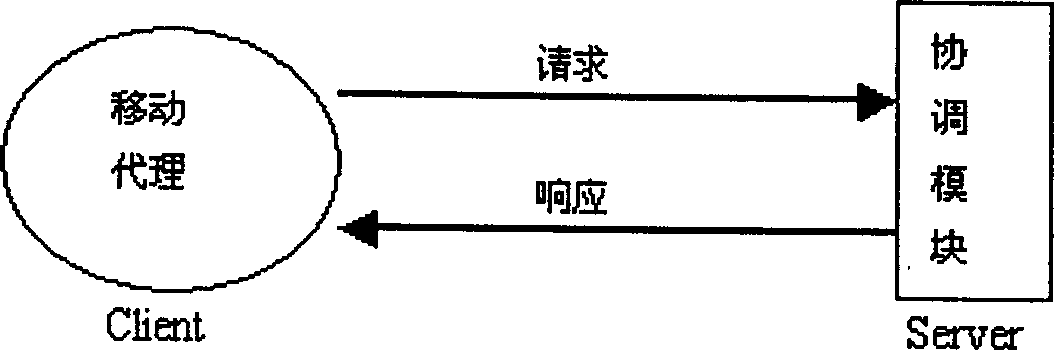
[0089] Consider a node subsystem of a large-scale distributed intrusion detection system. A specific embodiment of the present invention can be expressed as follows.
[0090] (1) Proxy naming rules
[0091] According to the functions and tasks to be completed by the agent, the static agent is divided into four categories, that is, the data collection agent, the analysis agent, the fusion agent, and the response agent. Correspondingly, according to the tasks that the mobile agent assists the static agent to complete, it can be Mobile agents are also divided into collection mobile agents, analysis mobile agents, fusion mobile agents, and response mobile agents. According to the category and function of the agent, we adopt the following naming rules.
[0092] Static generation - S (stationary)
[0093] Mobile Agent——M(mobile)
[0094] Collection agent - C (collection)
[0095] Analysis agent——A(analysis)
[0096] Fusion agent——F(fusio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com