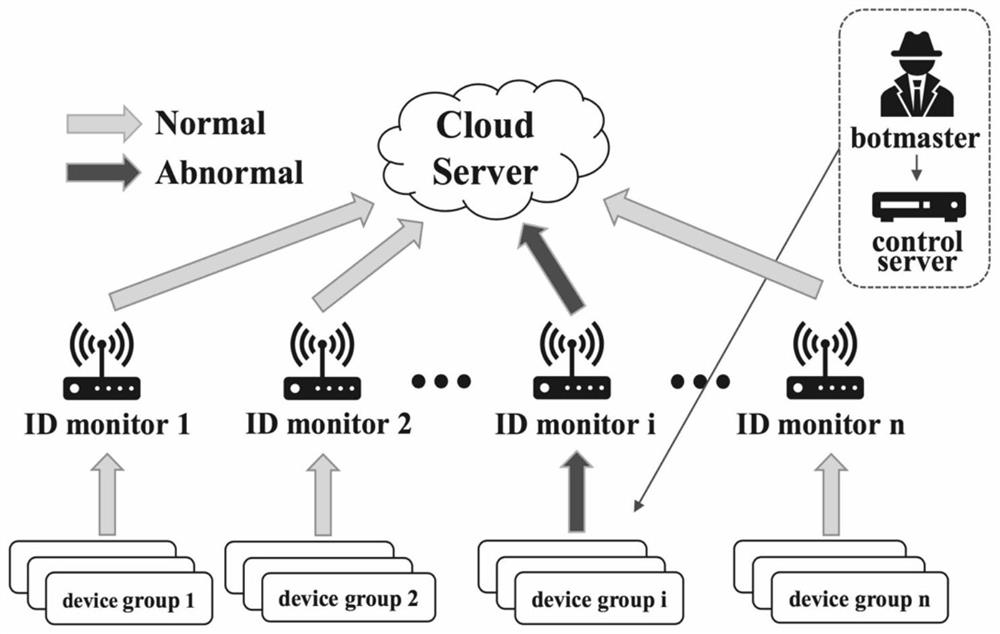
Lightweight distributed intrusion detection method
An intrusion detection and distributed technology, applied in the field of information security, can solve the problems of IDS service provider burden, system paralysis, IDS model accuracy decline, etc., and achieve the effect of fast prediction speed, less feature engineering, and low false positive rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
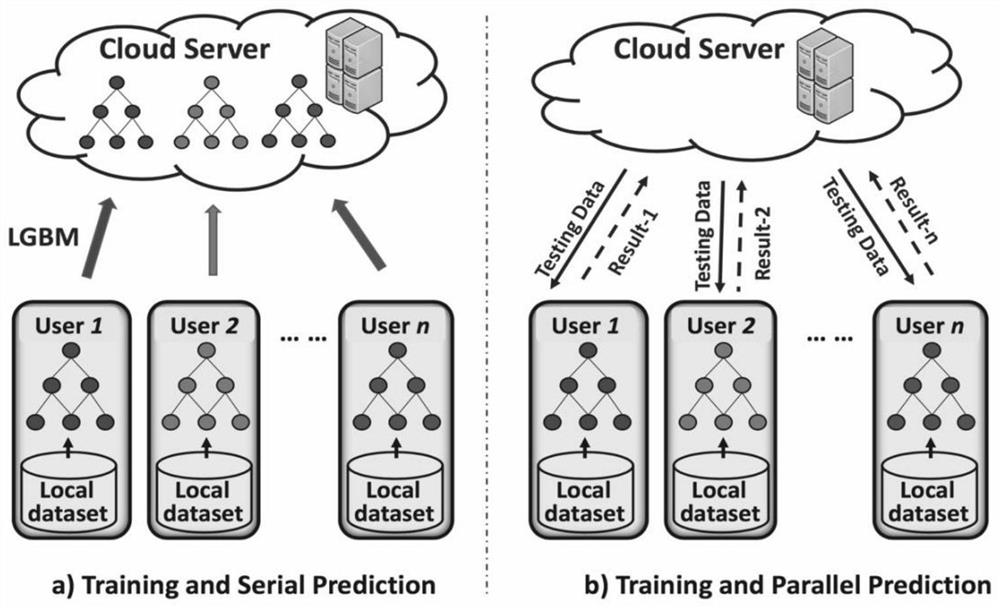
[0026] Such as figure 2 As shown, in the method of the present invention, each client uses its own private data set for training to obtain a local LGBM; the server then integrates the prediction results of each client's LGBM to obtain an intrusion detection result.
[0027] 1) Client training process
[0028] In CoLGBM, the gradient boosted decision tree GBDT variant LightGBM (LGBM) is used. LGBM discloses two new techniques: one-sided sampling GOSS and exclusive feature bundling EFB, which are used to handle a large number of data instances and a large number of features, respectively. We denote the total amount of data as T 0 , the total amount of non-zero data is denoted as T 1 , the total amount of features is denoted as S 0 , and the characteristic number is denoted as S 1 . Since it takes a lot of time to estimate the information gain of all segments by scanning all data instances, we use GOSS and EFB algorithms to reduce the complexity of histogram construction f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com