Method and system for updating certification key
An authentication key and consistent technology, applied in the field of information security, can solve the problems of high cost, insecure authentication key, troublesome authentication key management, etc., and achieve the effect of avoiding insecurity and inconvenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
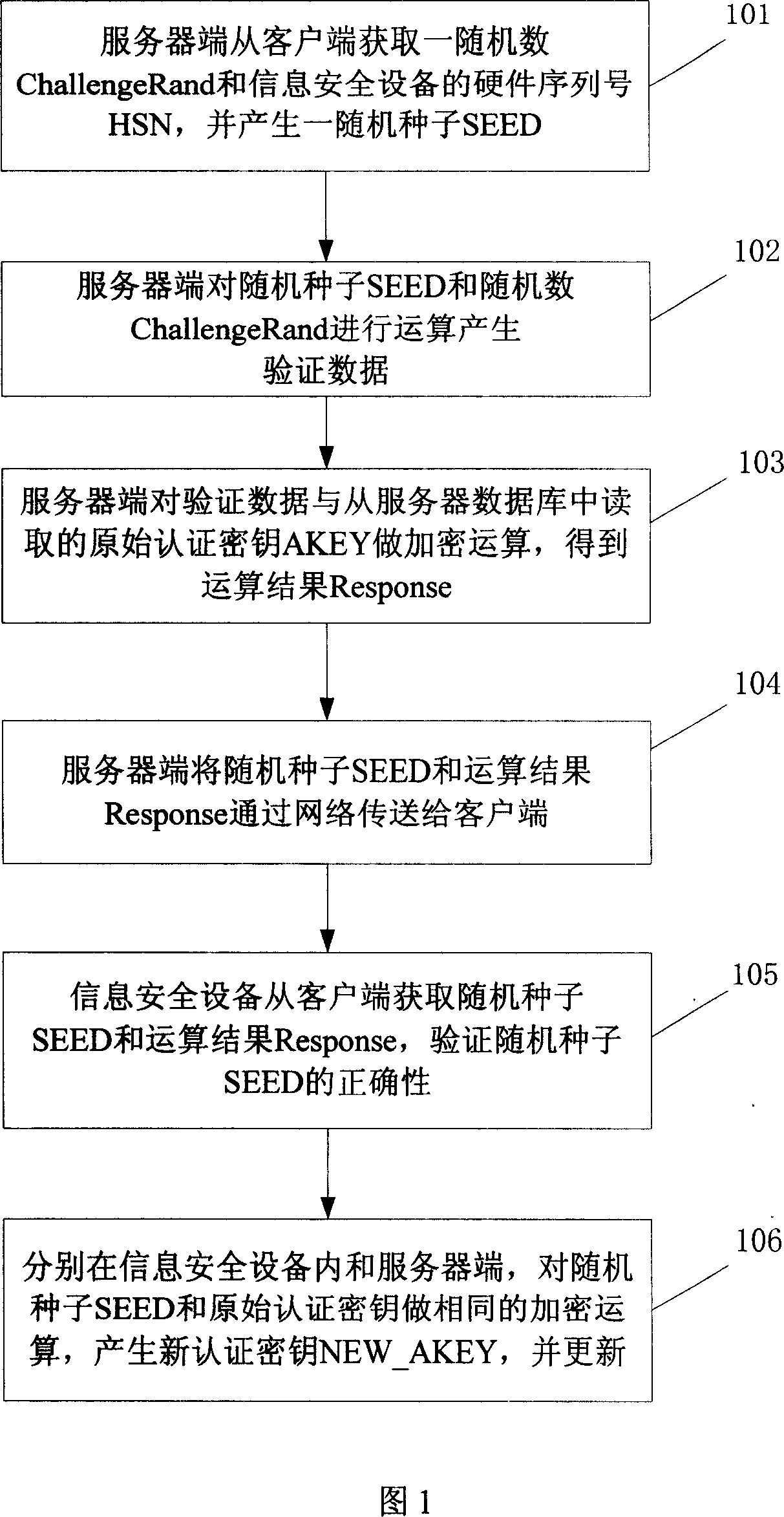
[0057] As shown in Figure 1, a method for updating an authentication key proposed by an embodiment of the present invention specifically includes the following steps:
[0058] Step 101: the server obtains a random number ChallengeRand and the hardware serial number HSN of the information security device from the client, and generates a random seed SEED.
[0059] The random number ChallengeRand is pre-generated inside the information security device connected to the client computer and stored in the information security device.
[0060] Step 102: The server side performs operations on the random seed SEED and the random number ChallengeRand to generate verification data.
[0061] Operations include combination, and, or, not, exclusive or, addition, subtraction, and multiplication.
[0062] Step 103: The server side reads the original authentication key AKEY from the server database according to the obtained hardware serial number of the information security device, and encrypt...
Embodiment 2
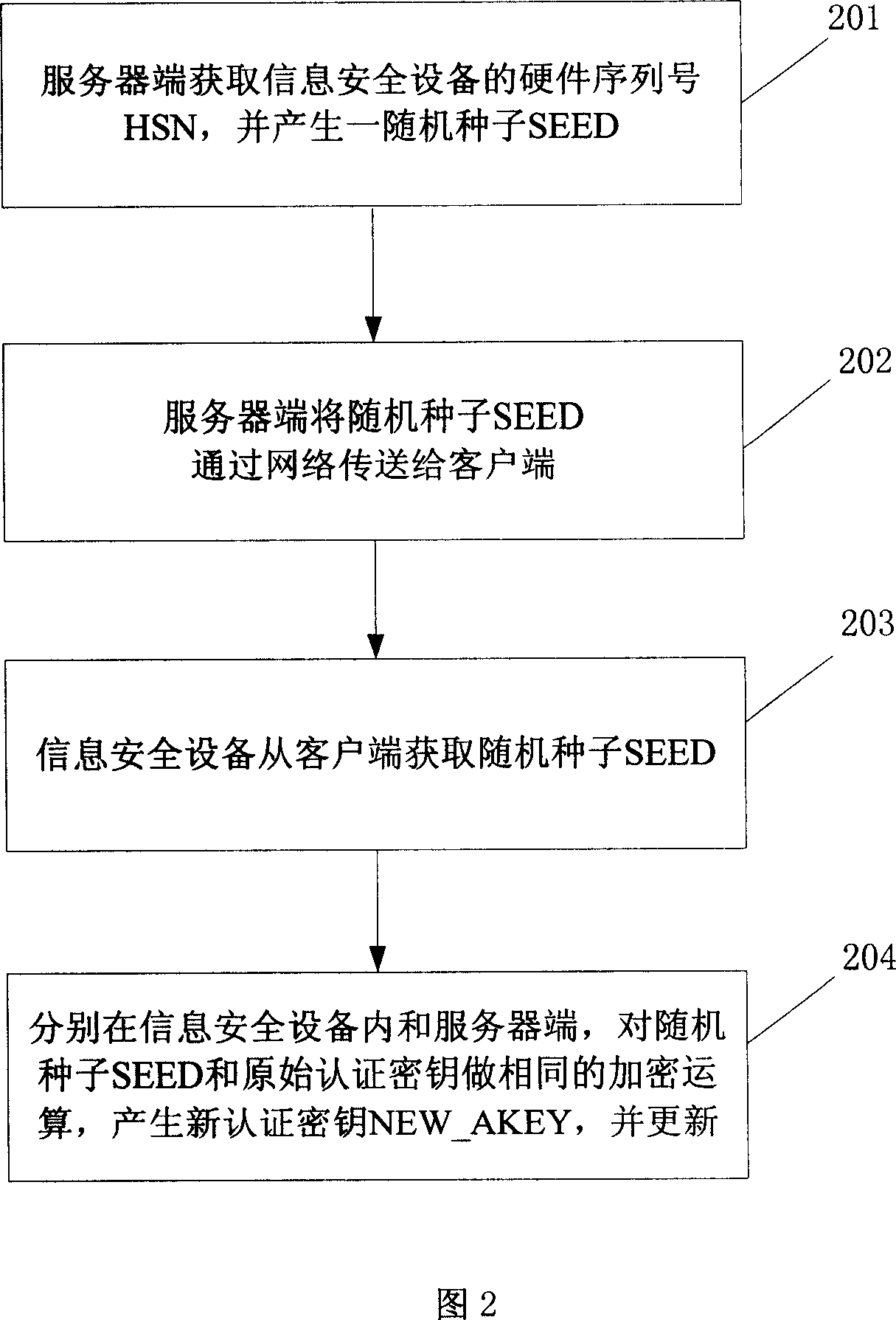
[0073] As shown in Figure 2, the embodiment of the present invention also proposes a method for updating the authentication key, which specifically includes the following steps:
[0074] Step 201: the server acquires the hardware serial number HSN of the information security device from the client, and generates a random seed SEED.
[0075] Step 202: the server transmits the random seed SEED to the client through the network.
[0076] Step 203: the information security device acquires a random seed SEED from the client.
[0077] Step 204: In the information security device and the server, perform the same encryption operation on the random seed SEED and the original authentication key to generate a new authentication key NEW_AKEY, and use the new authentication key NEW_AKEY to update the database in the information security device and the server The authentication key in .
[0078] The method of generating and updating the authentication key NEW_AKEY in the information secur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com