Dynamic password card and dynamic password generating method
A dynamic password token and dynamic password technology, applied in the electronic field, can solve the security problems of dynamic passwords and other problems, and achieve the effect of preventing improper use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
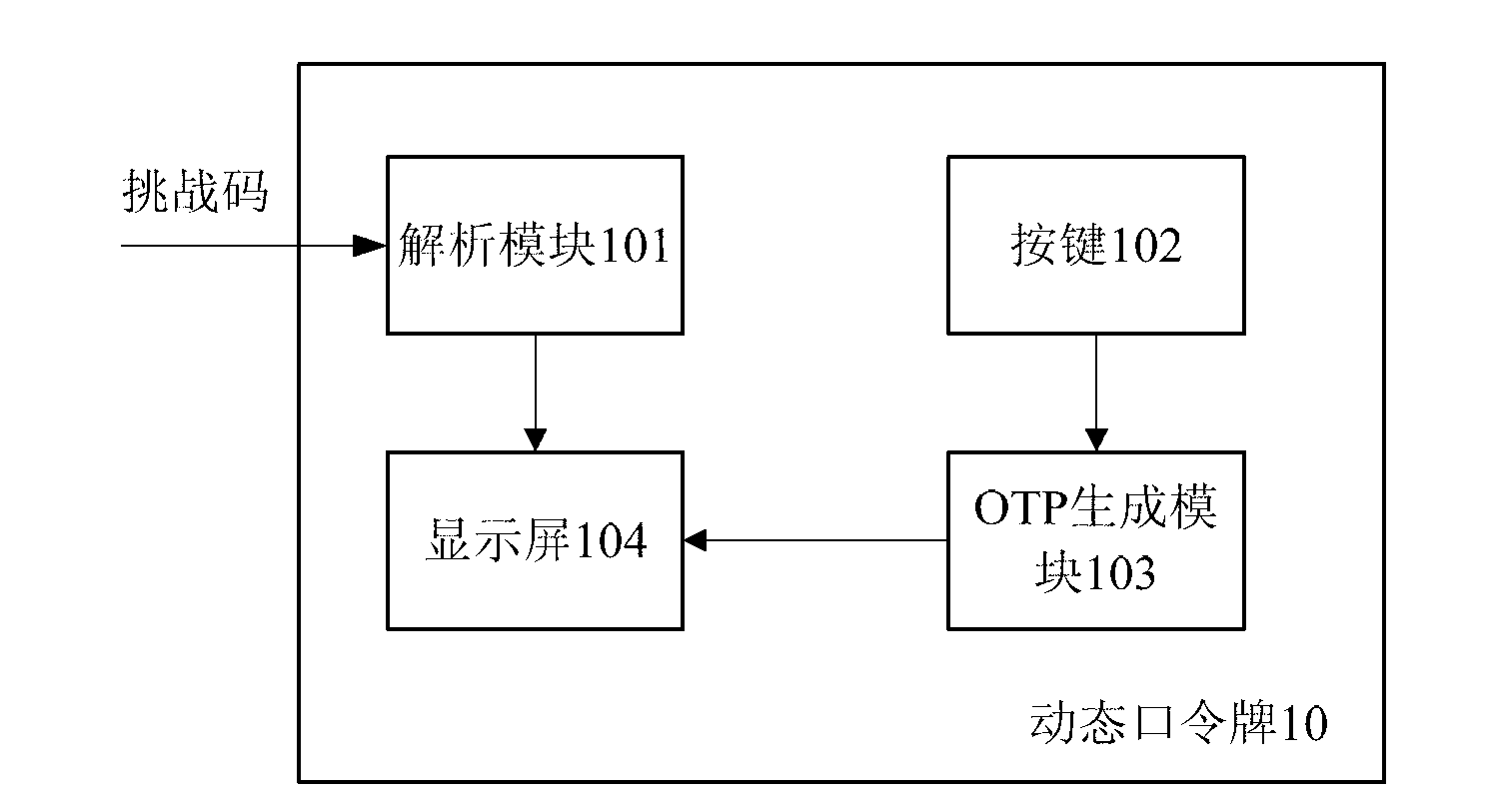
[0034] On the one hand, this embodiment provides an OTP token 10, such as figure 1 As shown, the OTP token 10 includes: an analysis module 101 , a button 102 , an OTP generation module 103 , and a display screen 104 .
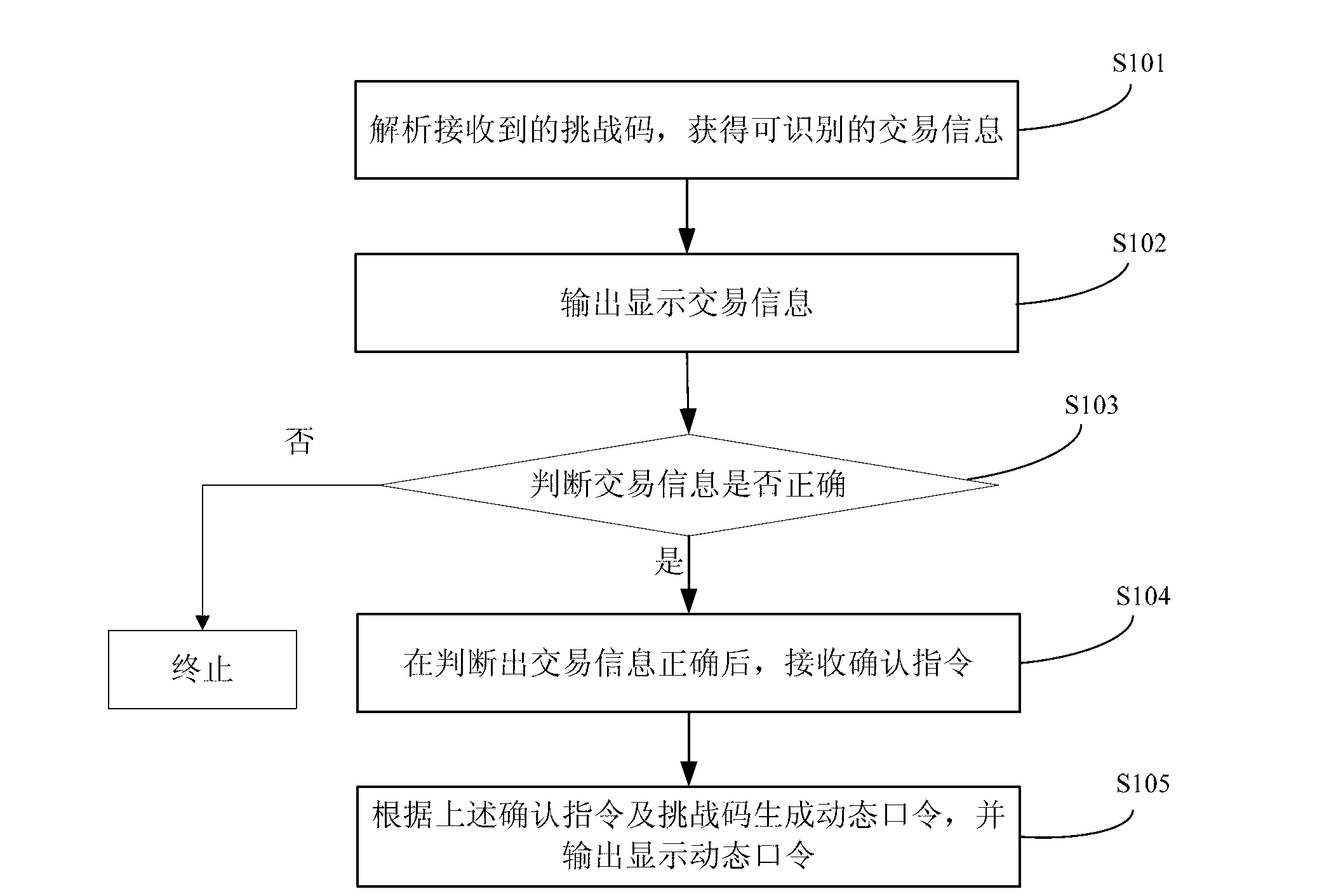
[0035] The user initiates a network transaction on the website. After receiving the transaction data, the bank server calculates the relevant data of the transaction and generates a challenge code, and informs the user of the challenge code (for example: via mobile phone SMS) or through wired / wireless communication. The method is sent from a terminal (for example: PC, mobile terminal, mobile phone, PAD, etc.) to the OTP token 10 . After receiving the challenge code manually input by the user or obtained through wired / wireless communication, the parsing module 101 uses a pre-stored parsing algorithm that matches the challenge code generation algorithm to parse the challenge code to obtain identifiable transaction information, and outputs Transaction information...
Embodiment 2
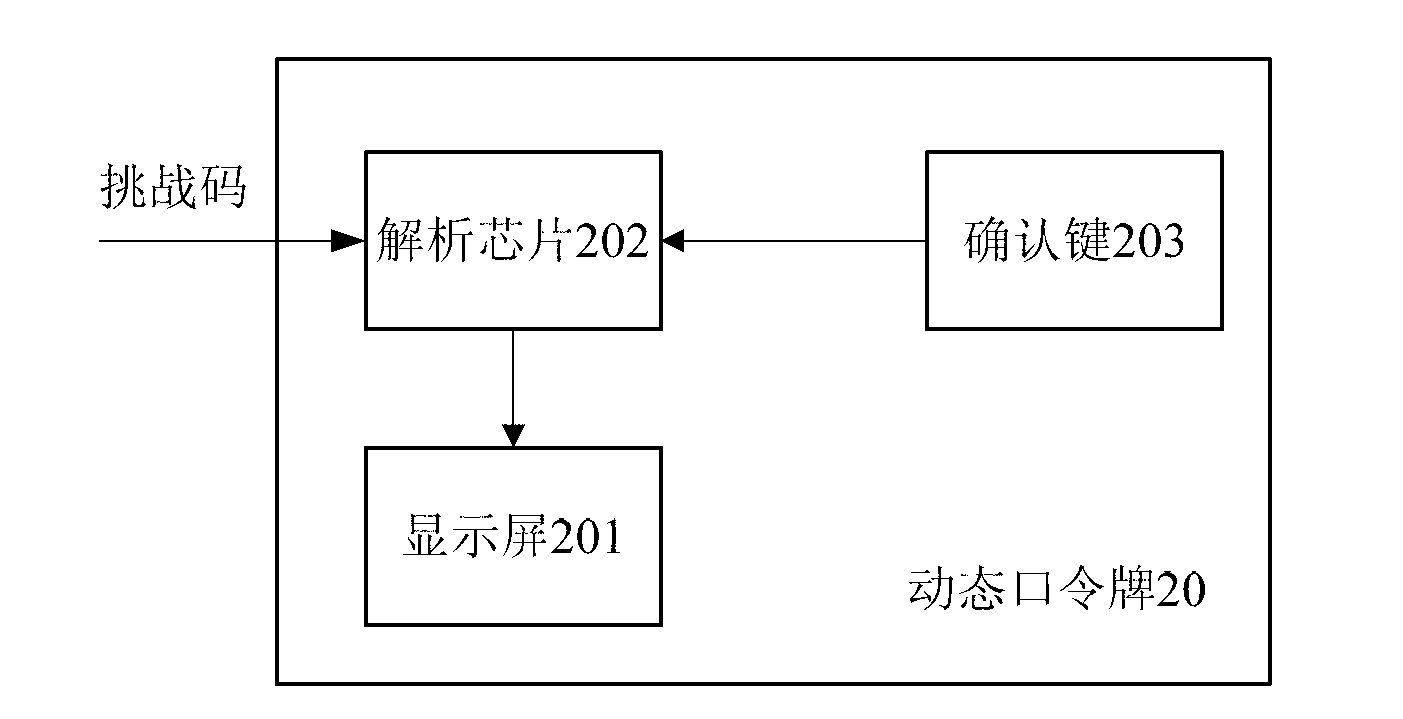
[0058] On the one hand, this embodiment provides an OTP token 30, such as Figure 4 As shown, the OTP token 30 includes: an analysis module 301 , a button 302 , an OTP generation module 303 , a display screen 304 and a receiving module 305 .
[0059] The receiving module 305 receives the challenge code input by the user and outputs it to the display screen 304 for display, so that the user can check whether the challenge code displayed on the display screen 304 is correct. If the input is correct, the user presses the button 302 to confirm, and the button 302 receives the user's first code. 2. Confirm the instruction, and output the second confirmation instruction to the receiving module 305, and the receiving module 305 outputs the challenge code to the analysis module 301 according to the second confirmation instruction.
[0060] Specifically, the receiving module 305 can use a wireless communication module such as an NFC module, a Bluetooth module or a radio frequency modul...
Embodiment 3
[0089] The difference between this embodiment and Embodiment 2 lies in the difference of the receiving module. The receiving module of this embodiment uses optical transmission to transmit information.
[0090] This embodiment provides OTP token 40, such as Image 6 As shown, the OTP token 40 includes: an analysis module 401 , a button 402 , an OTP generation module 403 , a display screen 404 and a receiving module 405 .
[0091] Preferably, Image 6The shown OTP token may further include a storage module 406 .
[0092] Image 6 The parsing module in the shown embodiment, button, OTP generation module and connection relationship and structure of display screen and Figure 4 The example shown is the same, Image 6 The storage module further included in the illustrated embodiment is the same as Figure 4 The structure and connection relationship of the storage modules further included in the illustrated embodiments are the same, and the above-mentioned identical parts will ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com