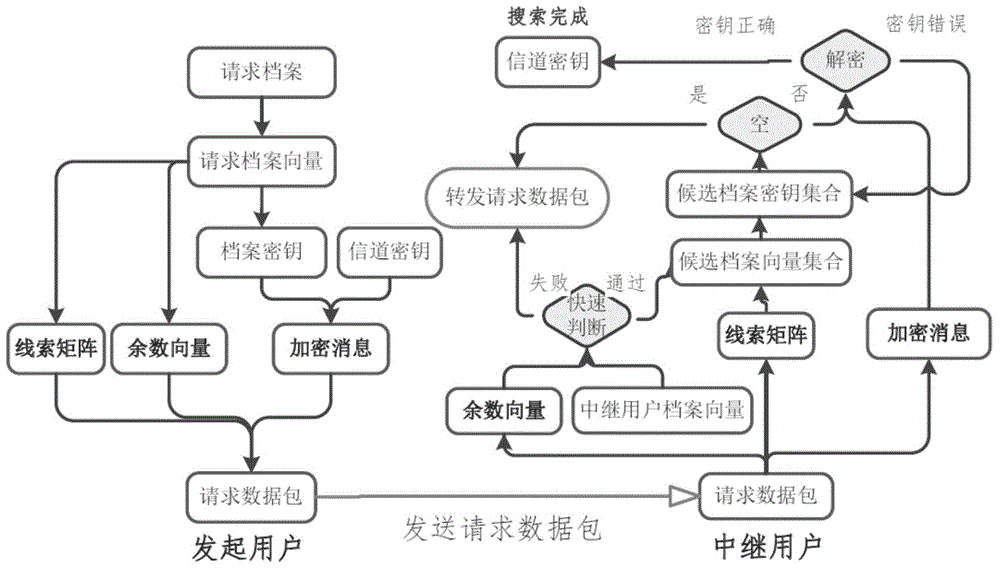
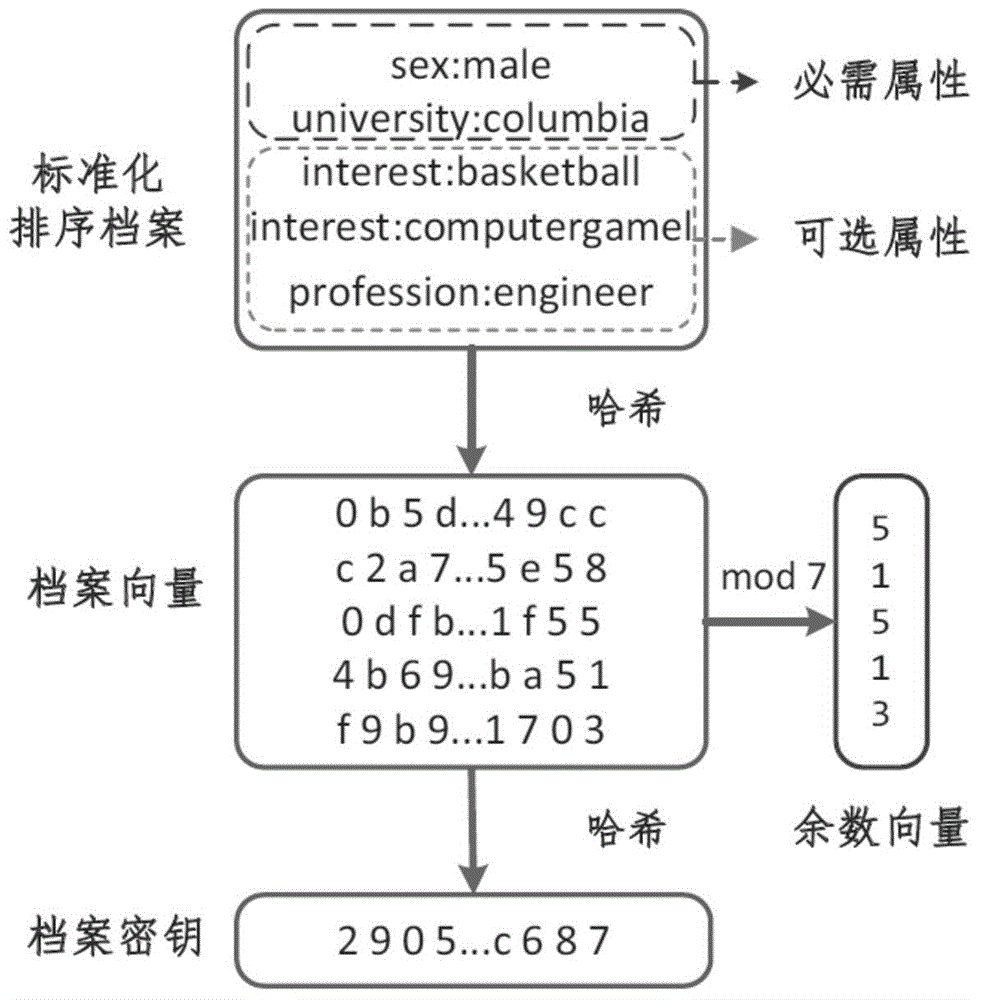
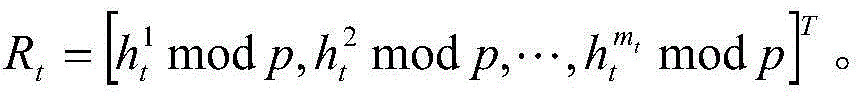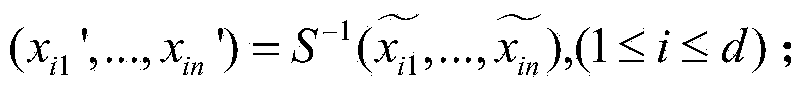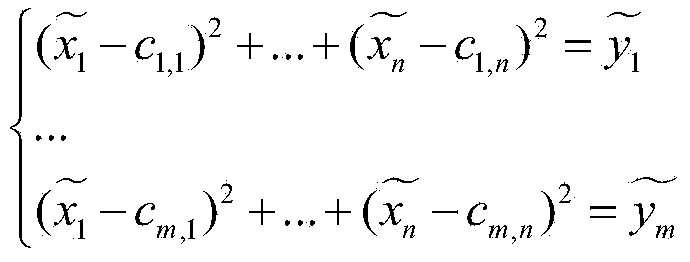Patents
Literature
85results about How to "Easy to decrypt" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
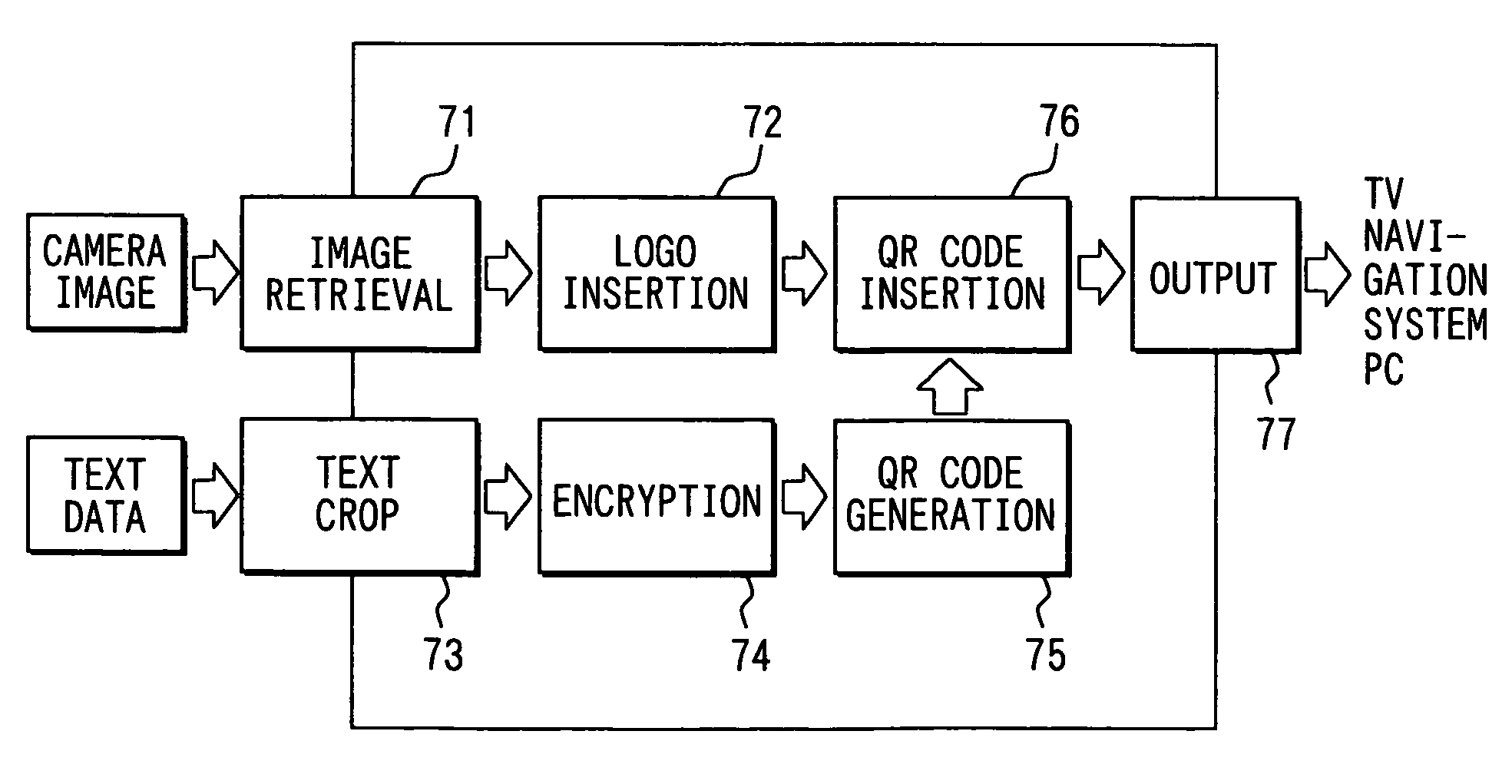
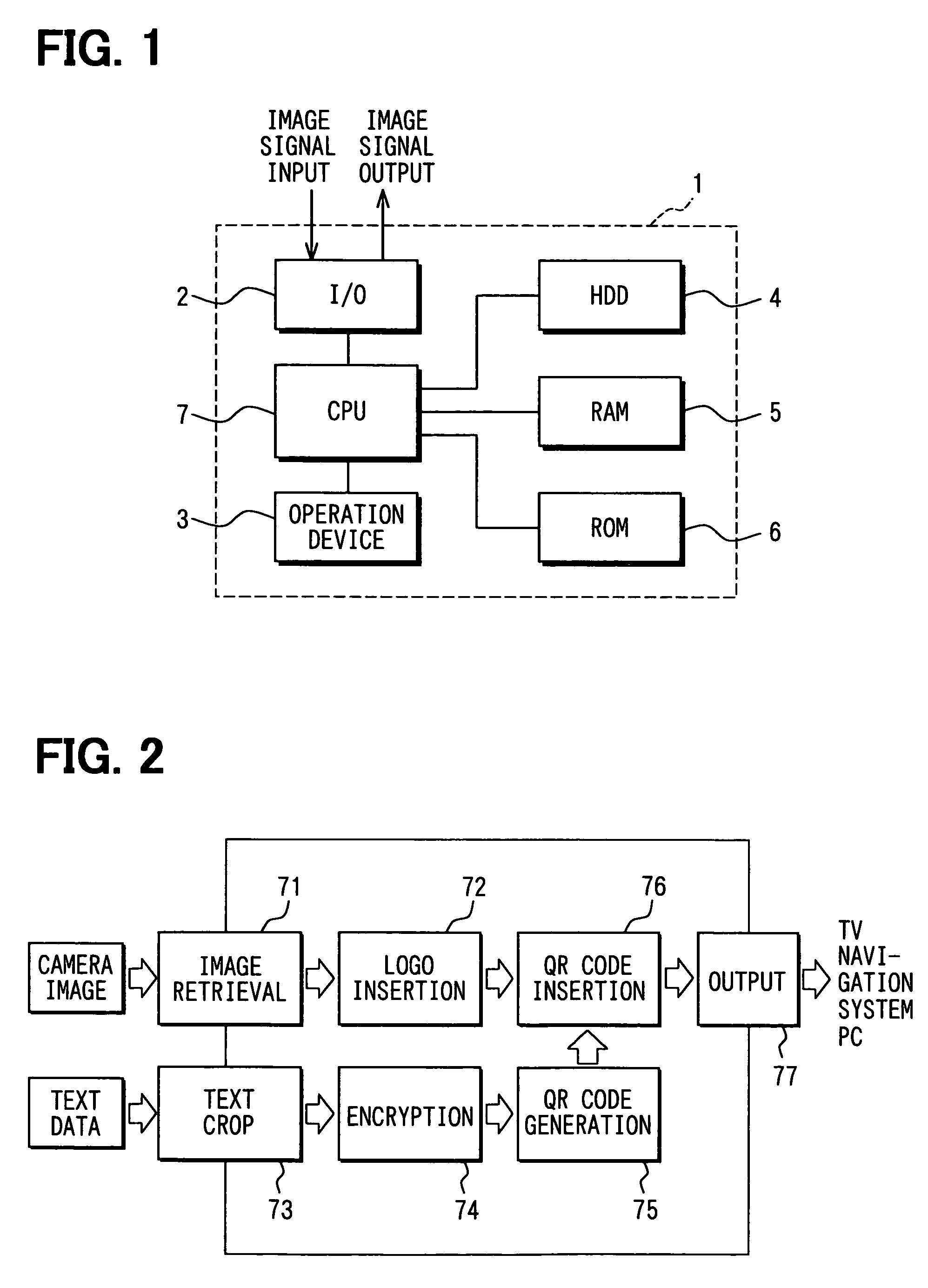
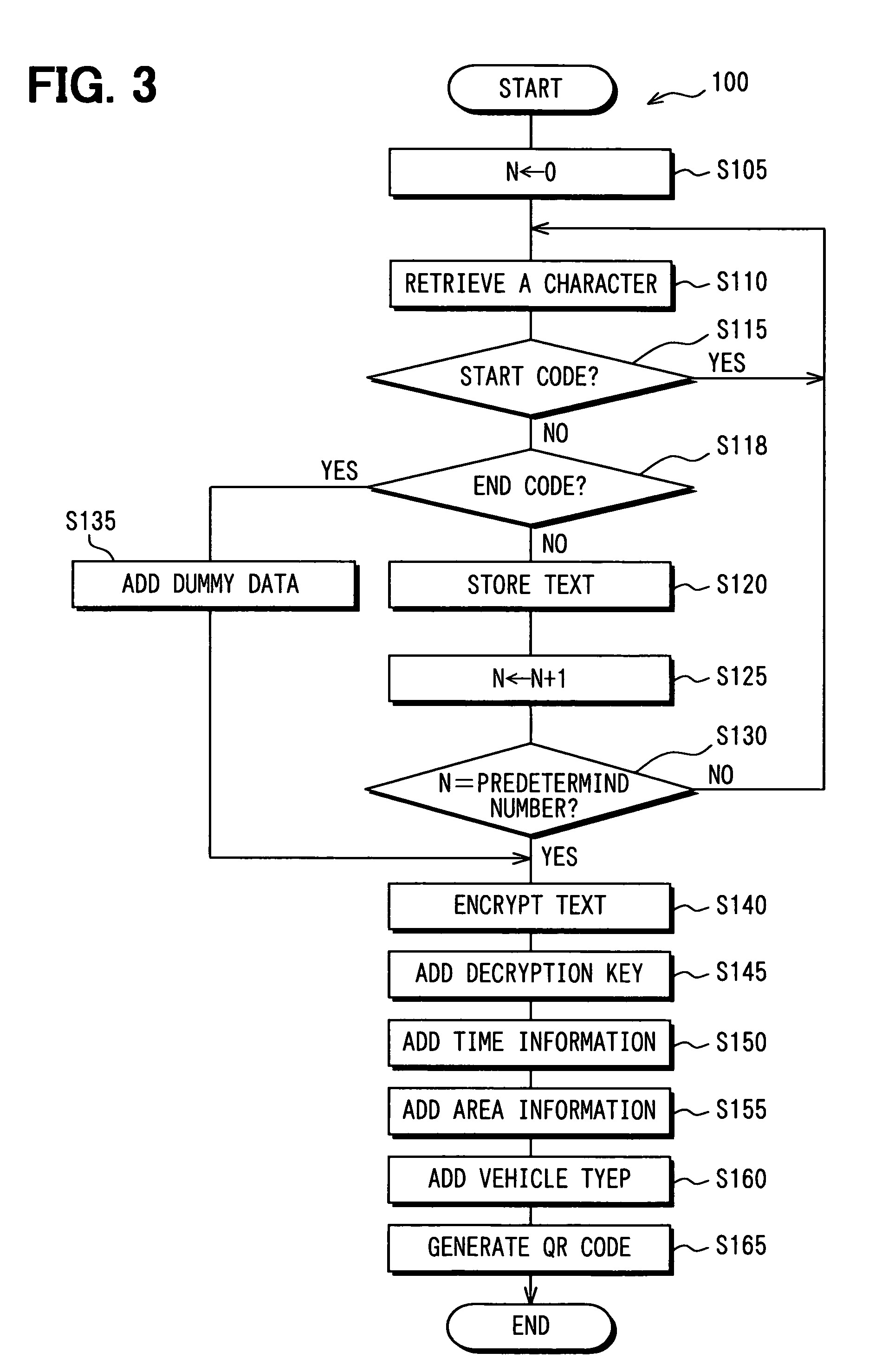
Image signal output device, coded image signal generation method, image signal output program, camera operation system, camera operation program, matrix code decoding device, and matrix code decoding program
InactiveUS20060086796A1Efficient captureEasy to decryptTelevision system detailsCharacter and pattern recognitionCoding decodingOutput device
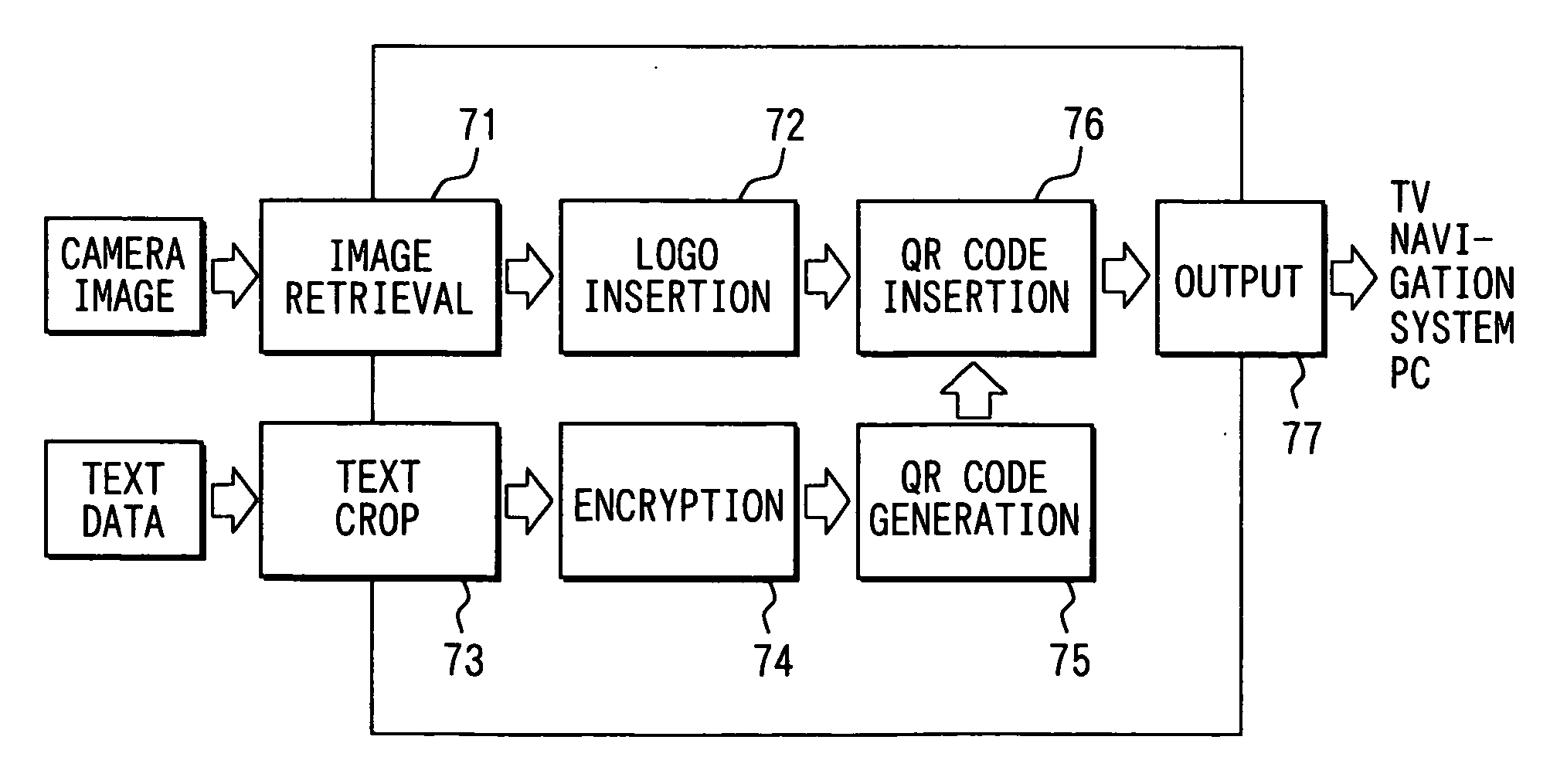
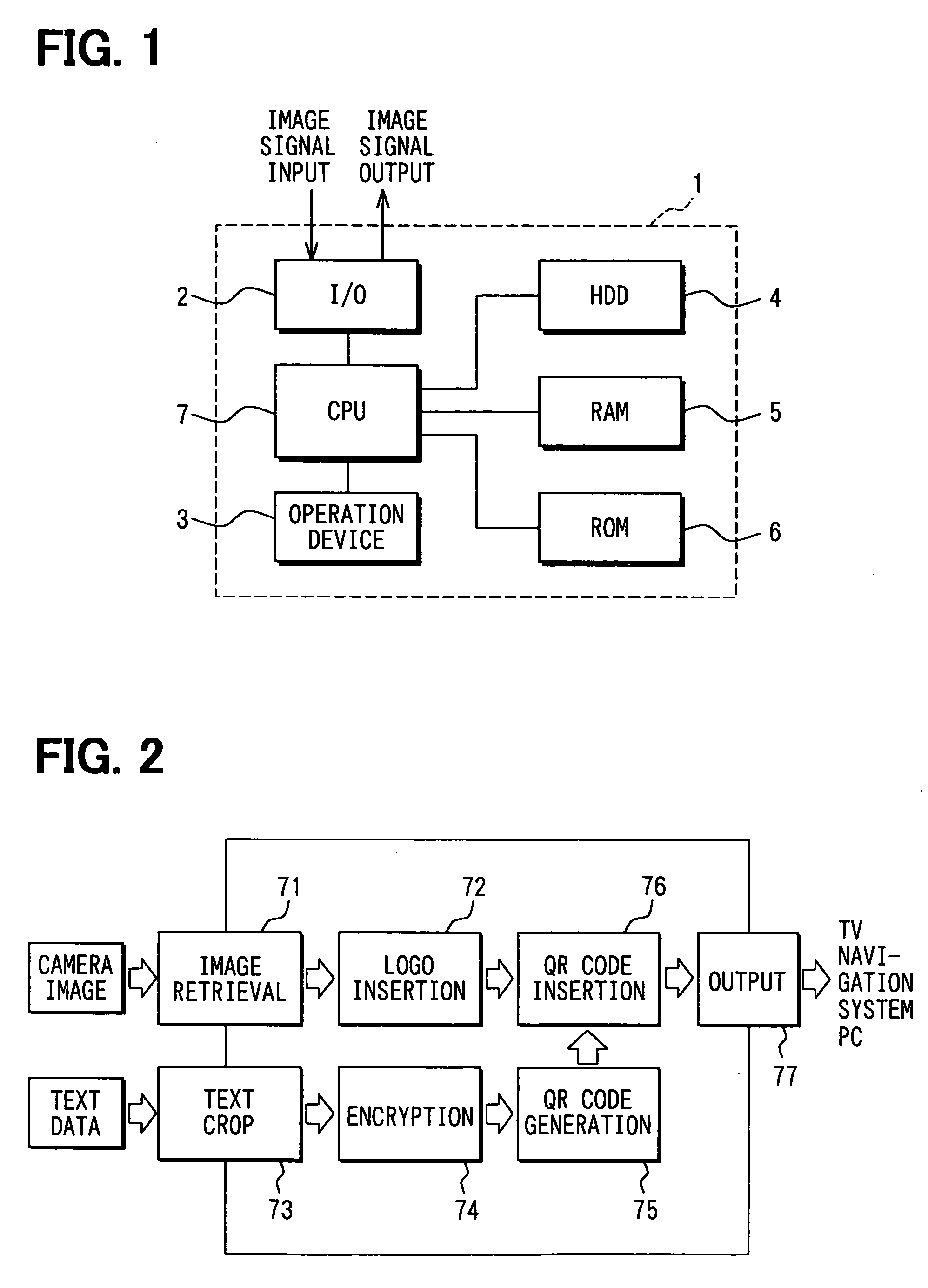
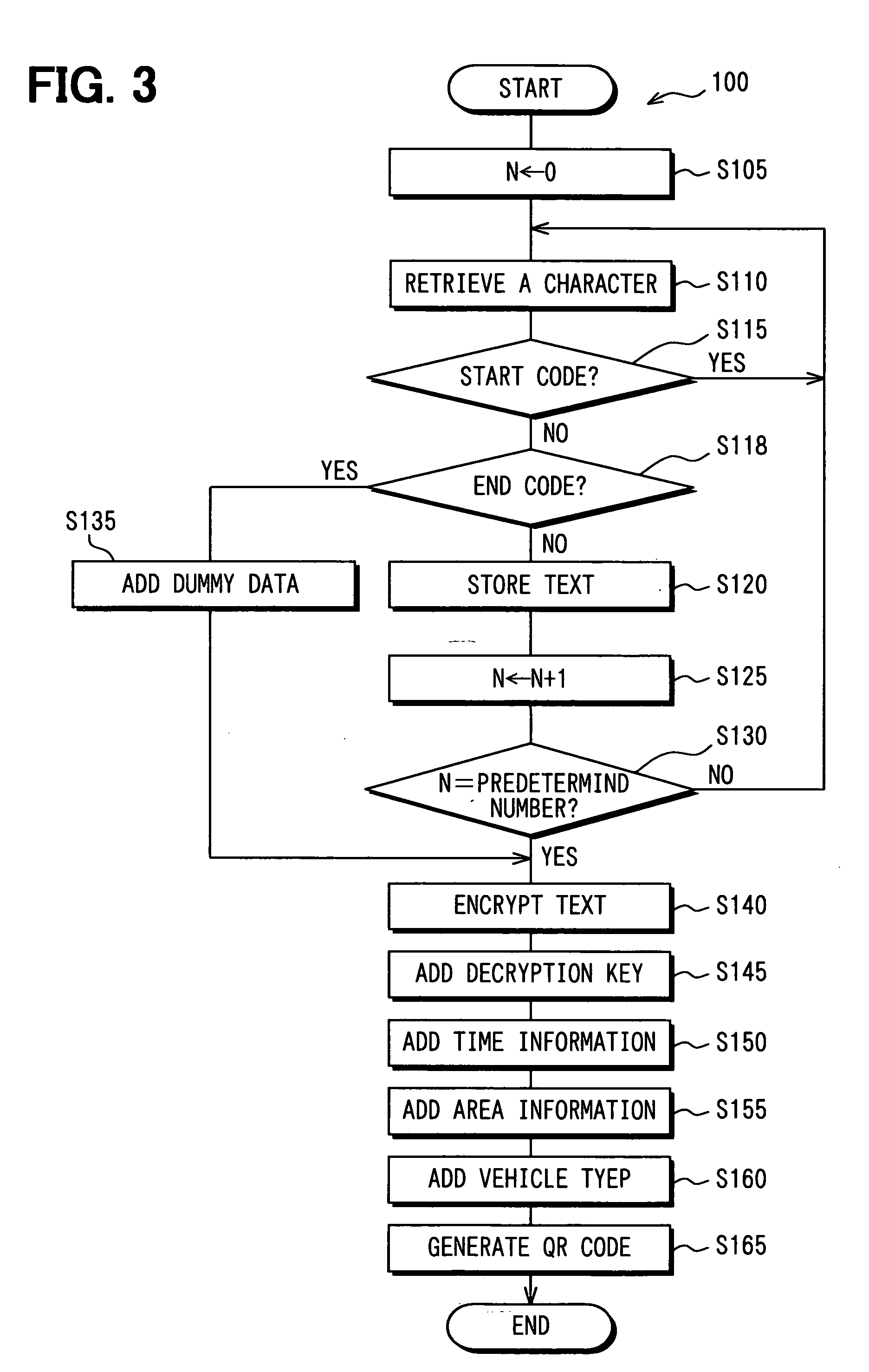
An image signal output device includes a code generating means for generating a two-dimensional geometrical code based on a source data, a obtaining means for retrieving a sequential image signal, a code inserting means for inserting the two-dimensional geometrical code in the sequential image signal and a output means for outputting the sequential image signal. The code inserting means imperceptibly inserts the two-dimensional geometrical code in the sequential image signal, and the output means outputs the sequential image signal having the two-dimensional geometrical code inserted therein. The imperceptible two-dimensional geometrical code is captured by a camera in a cell phone to be decoded and stored in a memory medium.
Owner:DENSO CORP
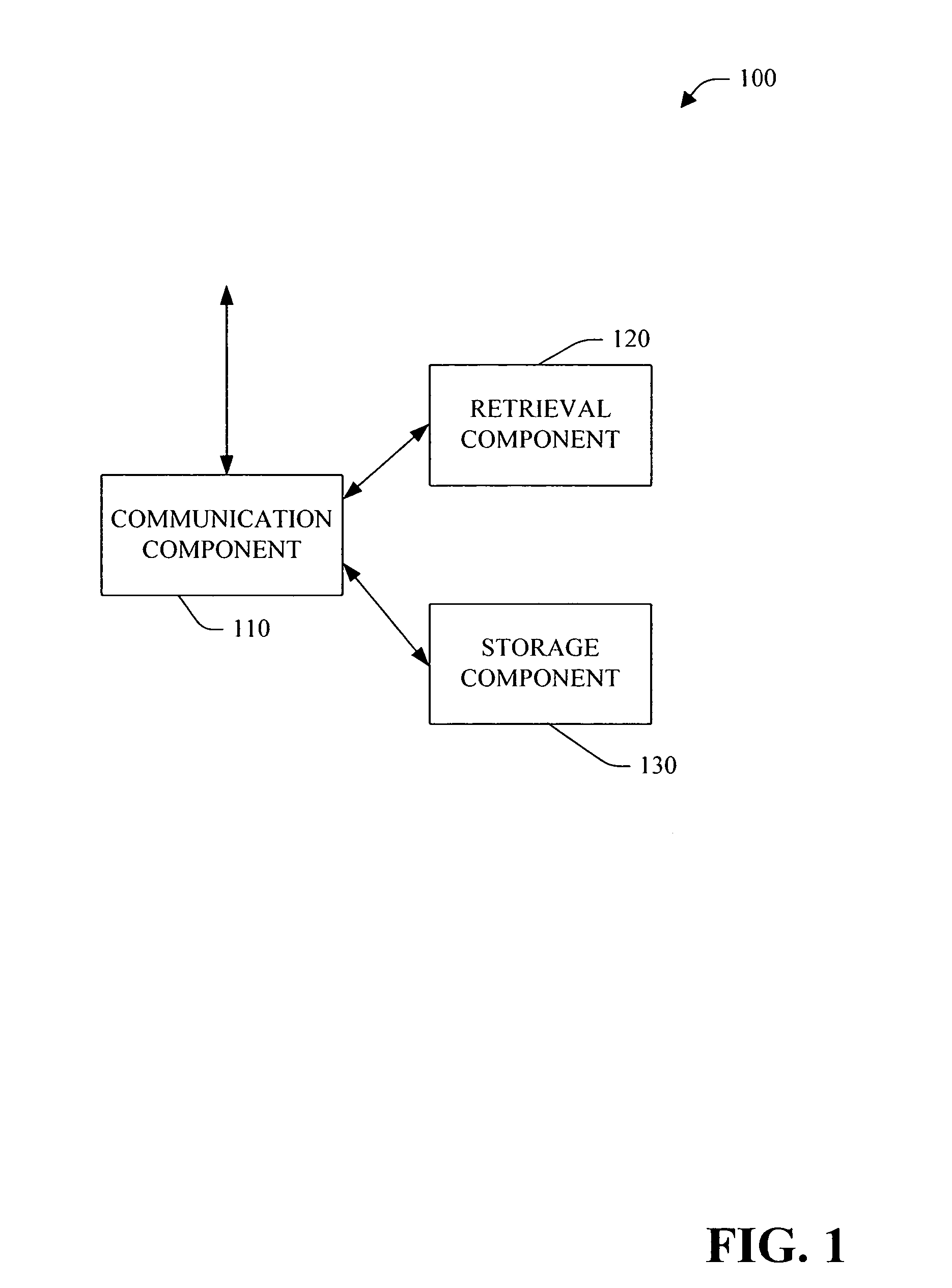
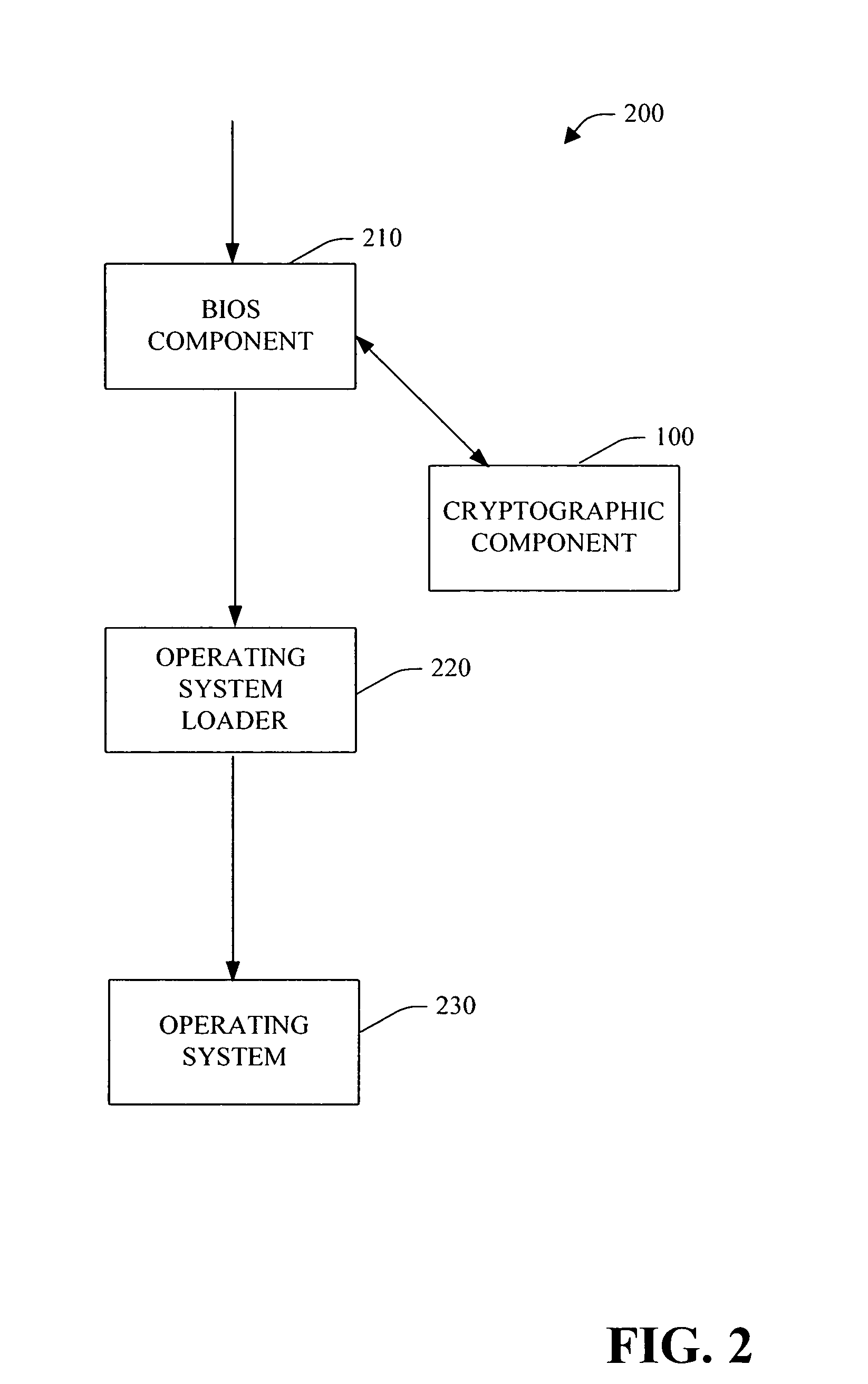
BIOS integrated encryption
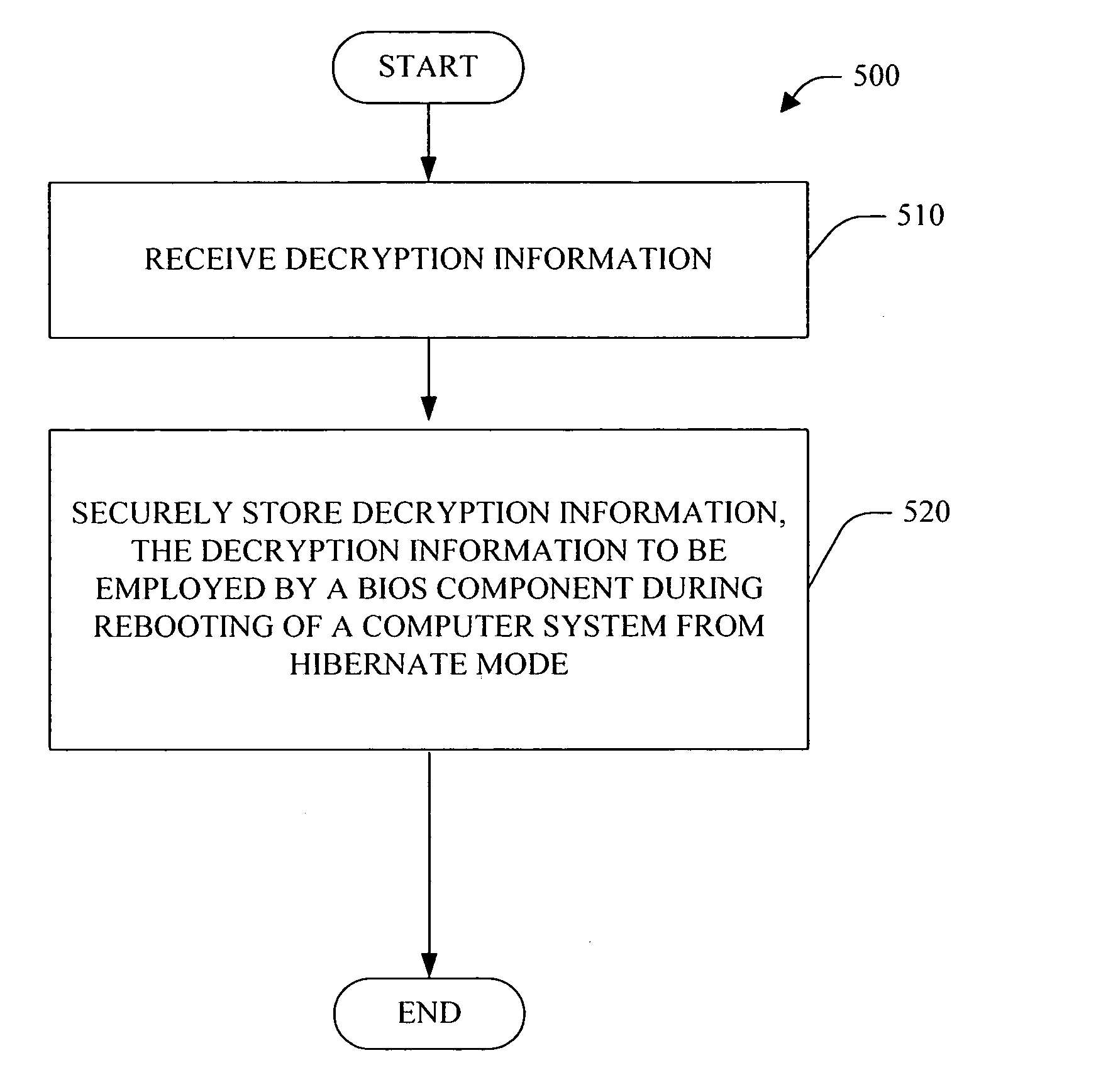
InactiveUS7376968B2Easy to decryptFacilitate secure rebooting of a computer systemDigital data processing detailsDigital computer detailsOperational systemComputerized system
A system and method for facilitating BIOS integrated encryption is provided. An interface is defined between the operating system and the BIOS. The operating system employs this interface to provide BIOS code information to facilitate decryption of data that is encrypted on the system. In the pre-operating system boot phase, the BIOS employs the decryption information provided from this interface in order to decrypt the data. The decrypted information can be employed to facilitate secure rebooting of a computer system from hibernate mode and / or secure access to device(s).
Owner:MICROSOFT TECH LICENSING LLC
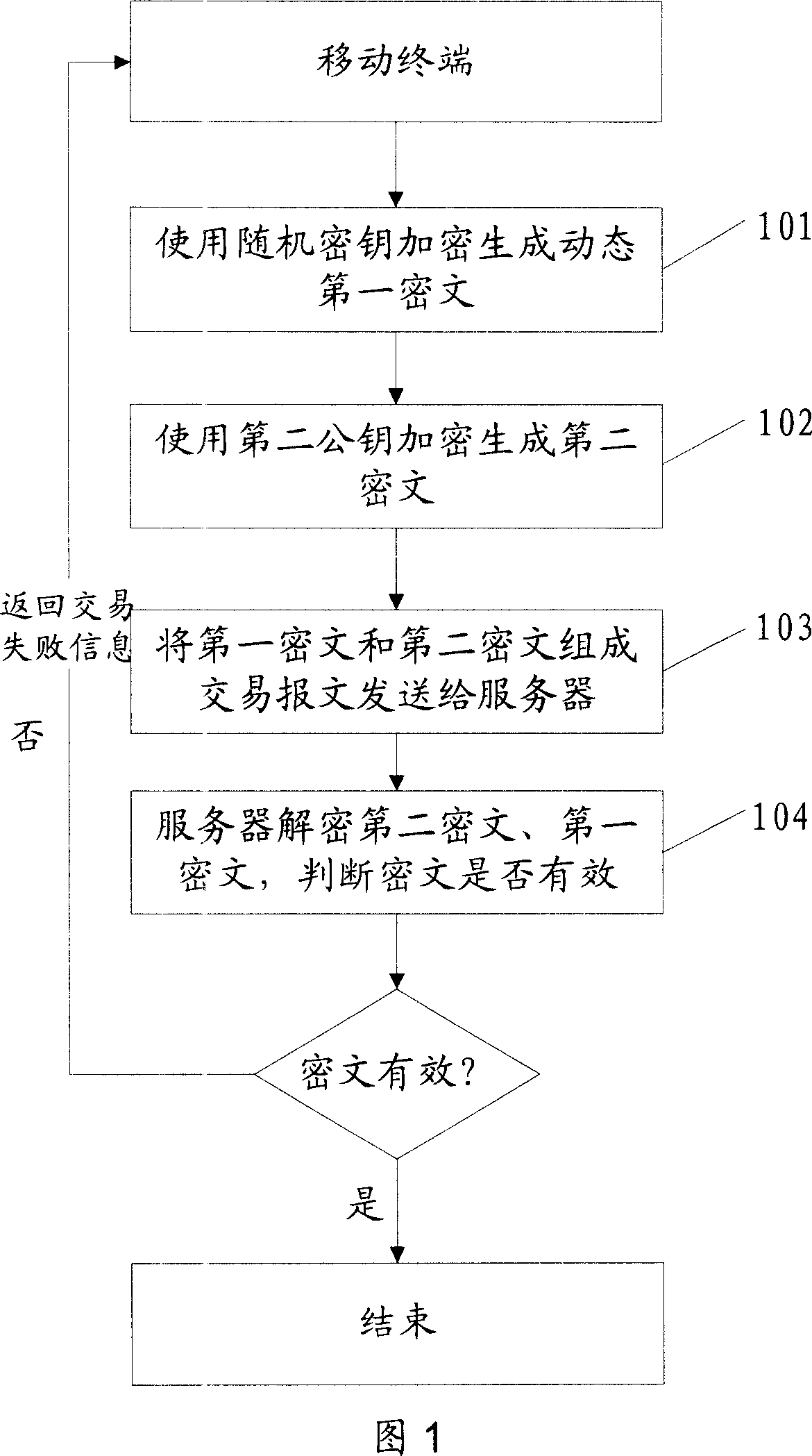
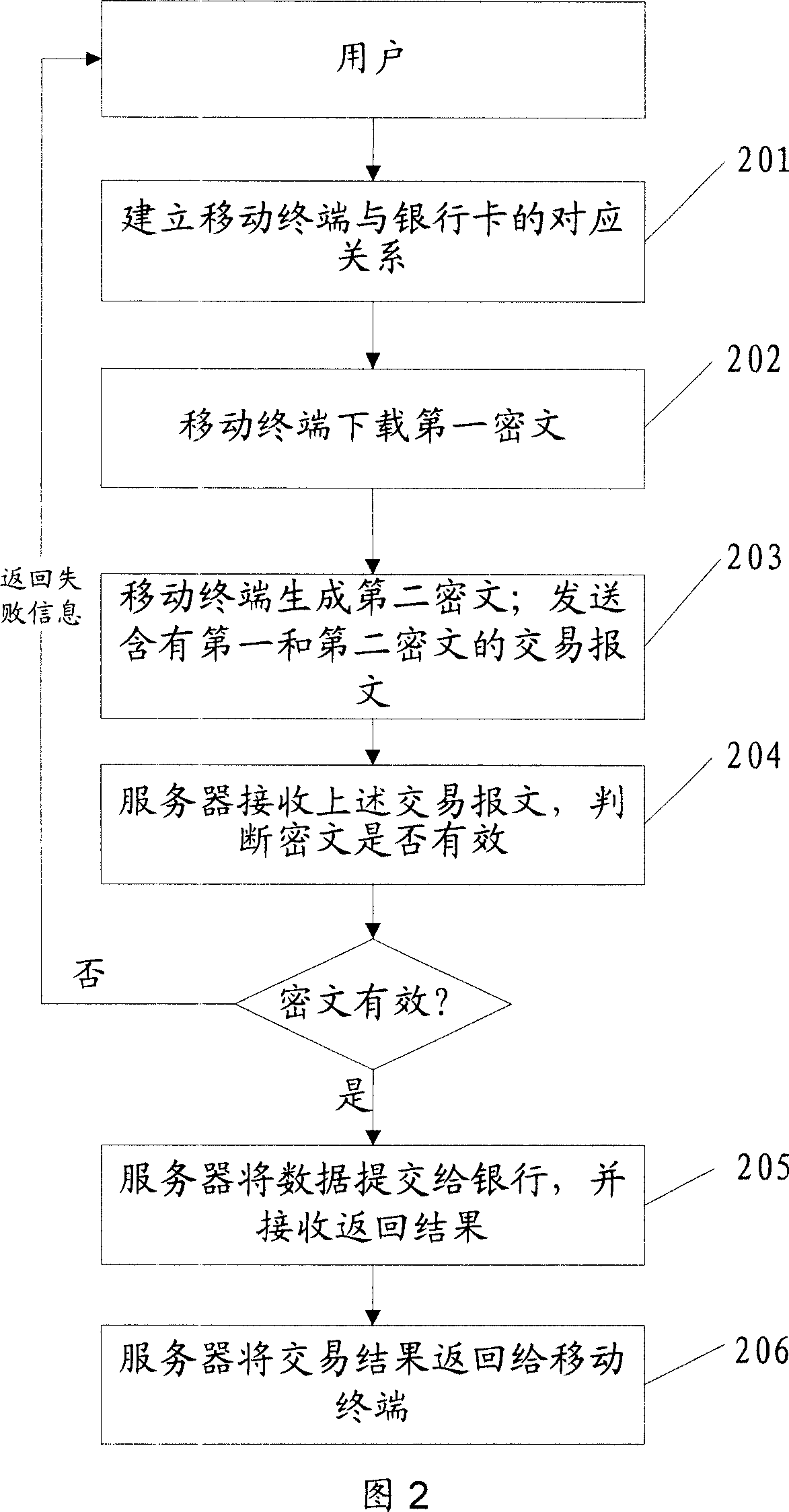
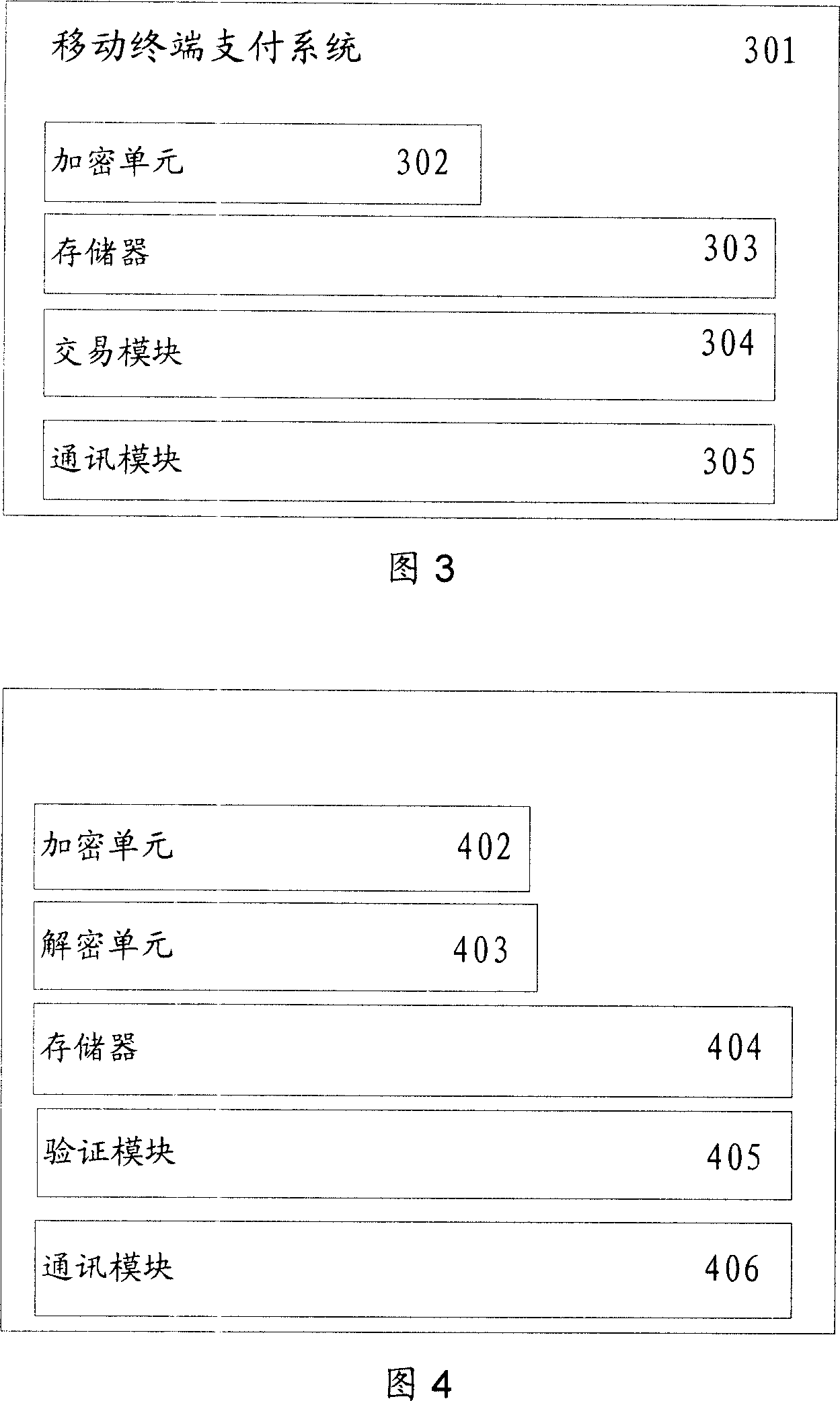
Safety data transmission method and paying method, paying terminal and paying server
ActiveCN101098225AProtection securityEnsure safetyUser identity/authority verificationPayment architectureTime markPassword
The invention discloses a safe data transmission method, comprising that a mobile terminal uses a second public key to encrypt the personal password of bank card to generate a second cryptogram, the mobile terminal combines the first and second cryptograms into a trade report to be sent to a server, while the first cryptogram contains card track information stored in the mobile terminal, the server decrypts the first and second cryptograms, for best, the mobile terminal can use random password to encrypt the first cryptogram to generate a dynamic first cryptogram, while the random password is generated by relative algorism according to dynamic factor. The invention uses asymmetry encrypt technique to encrypt the data sent by mobile terminal, and uses random password to generate dynamic cryptogram, and generates the cryptogram with living period according to time mark, therefore, the transmission safety of finance data as cark track information or the like is effectively protected via the combined encrypt methods, to realize mobile payment.
Owner:CHINA UNIONPAY
Image signal output device and a method of generating a coded image signal
InactiveUS7604172B2Easy to decryptEfficient captureTelevision system detailsCharacter and pattern recognitionOutput deviceImage signal
An image signal output device includes a code generating means for generating a two-dimensional geometrical code based on a source data, a obtaining means for retrieving a sequential image signal, a code inserting means for inserting the two-dimensional geometrical code in the sequential image signal and a output means for outputting the sequential image signal. The code inserting means imperceptibly inserts the two-dimensional geometrical code in the sequential image signal, and the output means outputs the sequential image signal having the two-dimensional geometrical code inserted therein. The imperceptible two-dimensional geometrical code is captured by a camera in a cell phone to be decoded and stored in a memory medium.
Owner:DENSO CORP
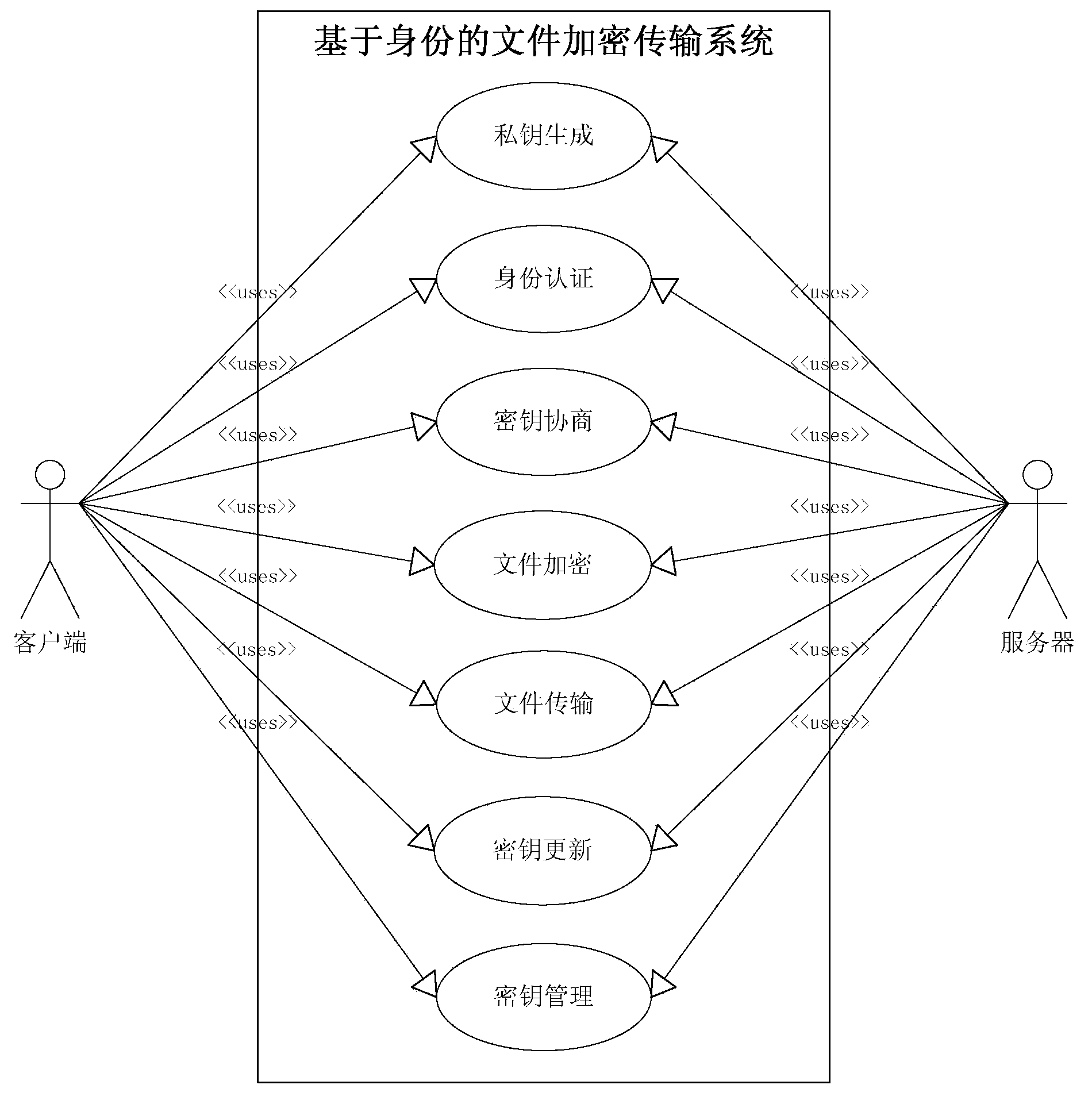
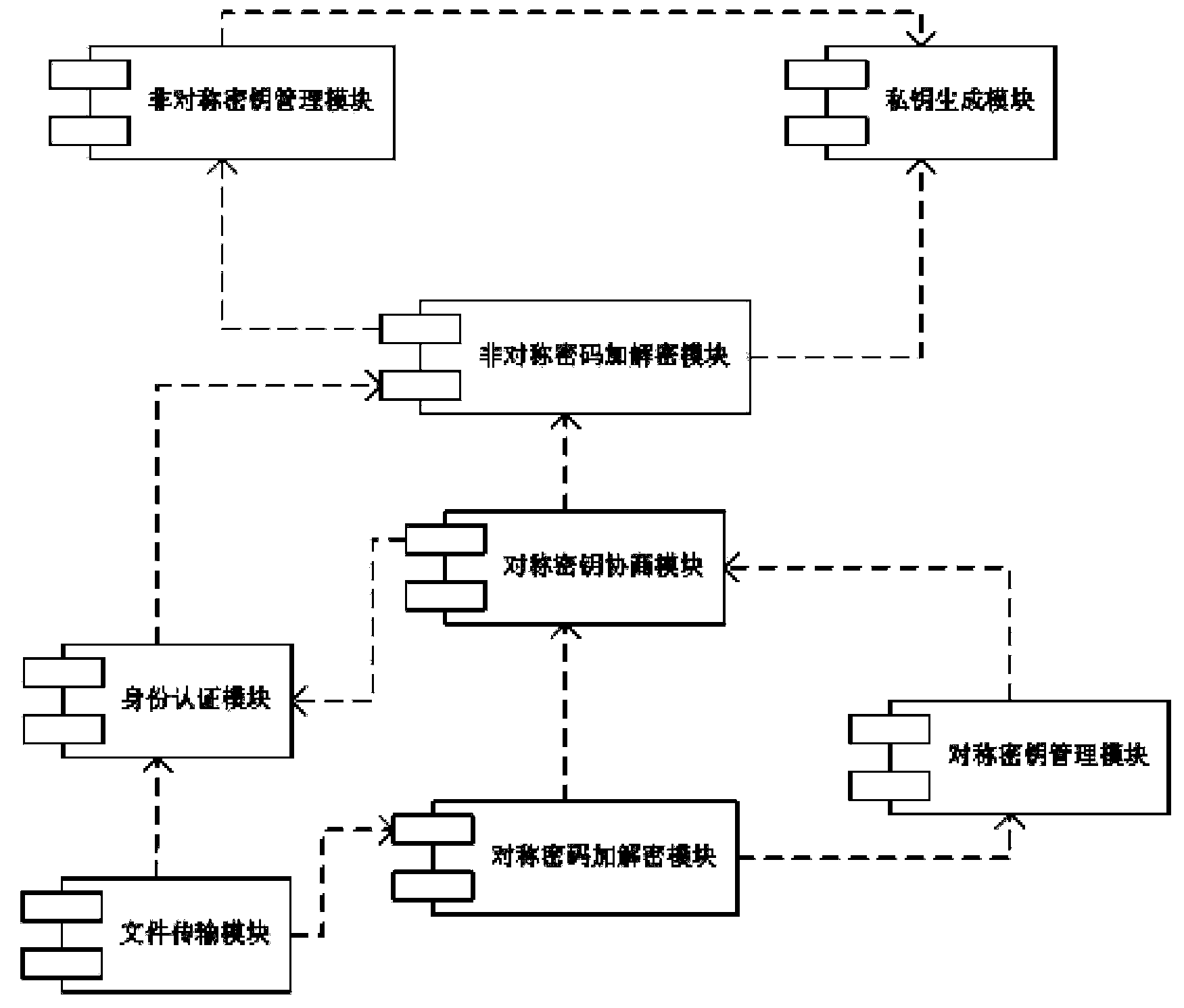
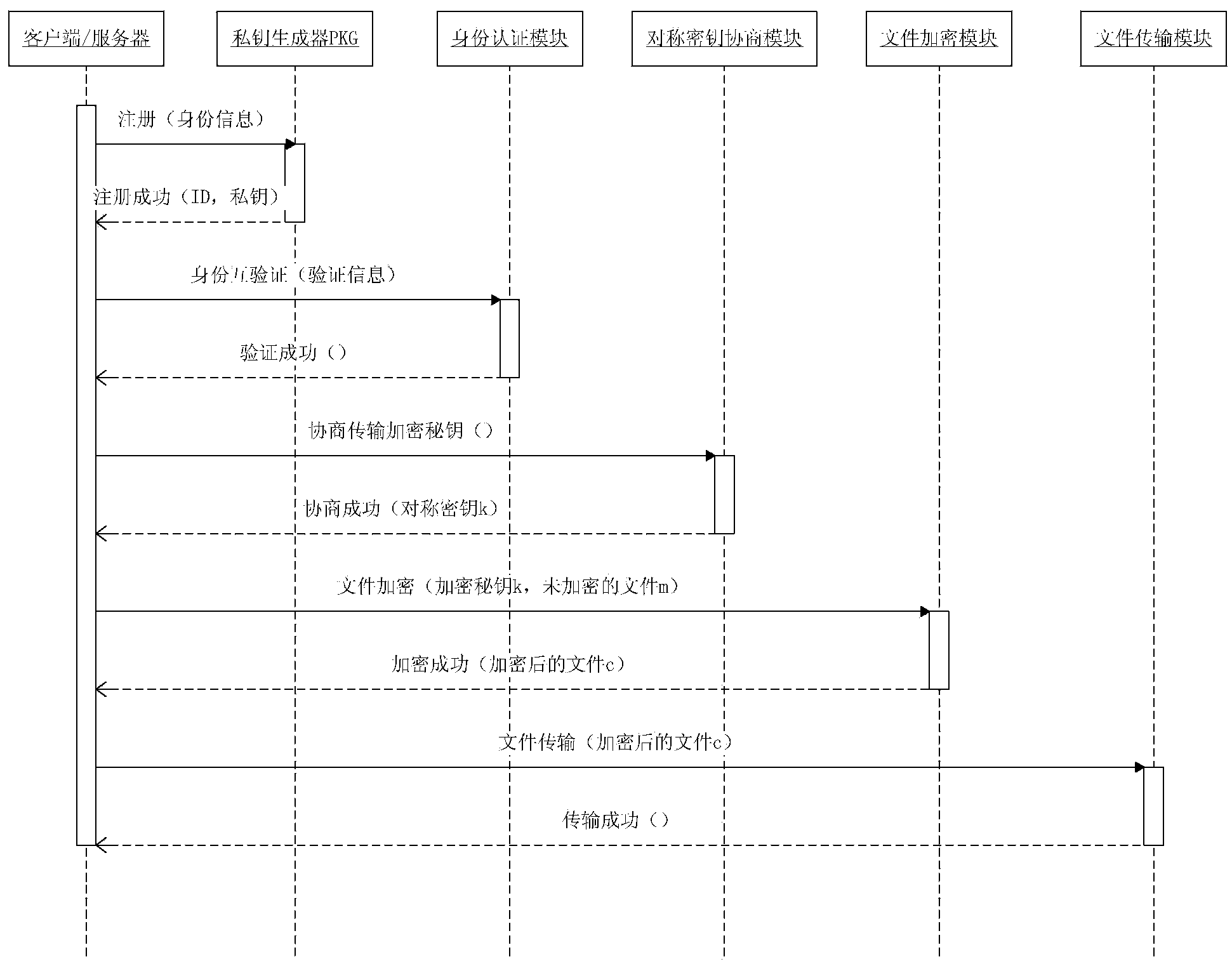
Identity-based file encryption transmission method
ActiveCN103354498AResist attackDelayed decryptionUser identity/authority verificationClient-sideEncryption
The invention discloses an identity-based file encryption transmission method which is applicable to a system of client / server architecture based on FTP. The method, based on identity based encryption algorithm, comprises the following steps: generation of public keys and private keys of a client and a server; identity authentication; negotiation of a symmetric key; transmission of encrypted files and secret key update and management. The identity based encryption (IBE) algorithm is used in the identity-based method, so that users can communicate safely and signature of each person is authenticated without exchanging the public keys and the private keys; besides, the file safety transmission method is low in cost, flexible in form, high in efficiency and good in safety.
Owner:北京创世泰克科技股份有限公司
A data encryption, decryption system and method
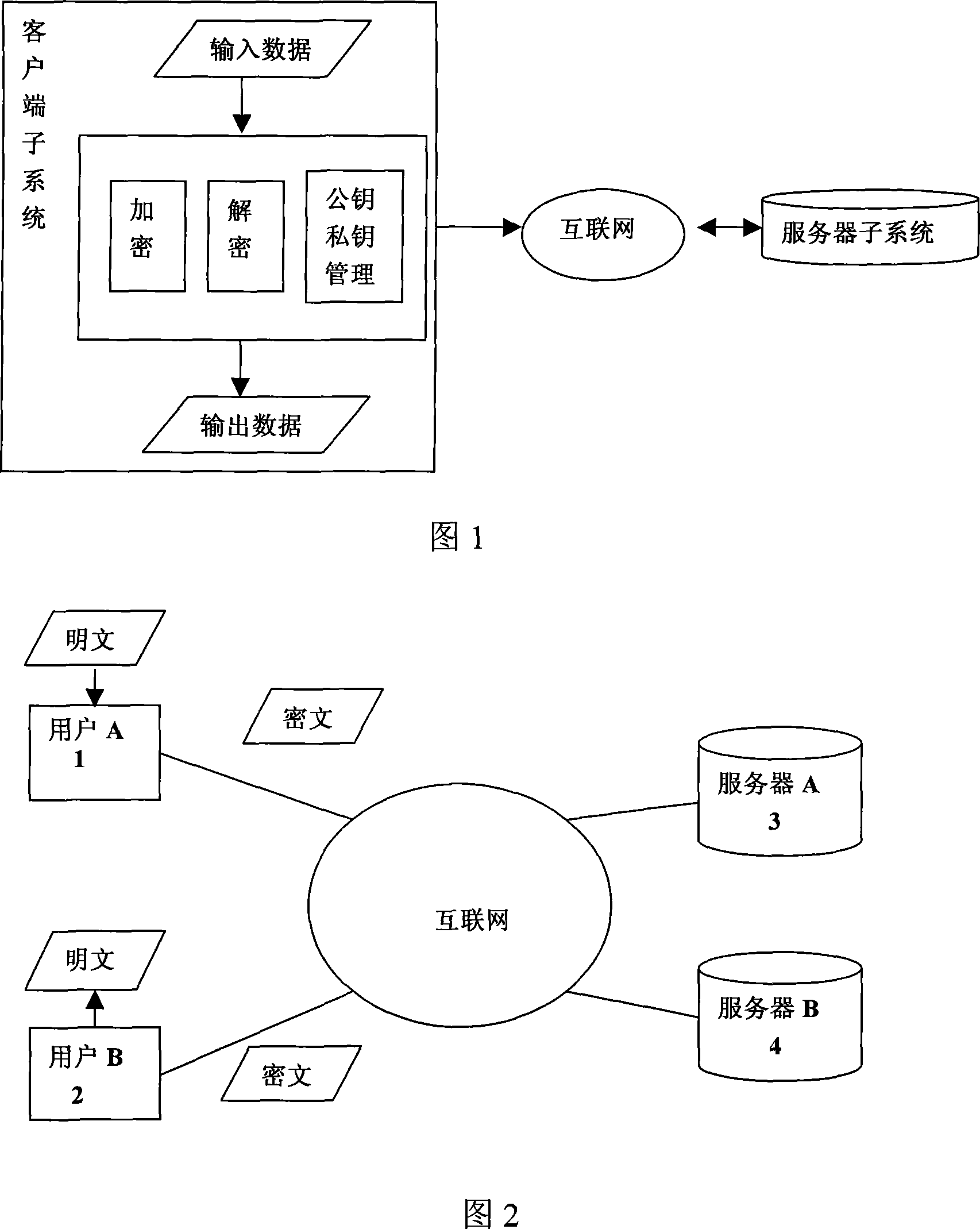
InactiveCN101123495AEasy to decryptEasy to useKey distribution for secure communicationPublic key for secure communicationPlaintextCiphertext
The present invention discloses a system and a method that can automatically complete the decryption and encryption of data files via the Internet. The system comprises a client-end subsystem, which performs decryption and encryption by receiving the instructions of client and manages public or private keys, and a server subsystem, which receives job requests from the client-end subsystem, executes jobs and returns job results. A reader first publishes a public key to the server subsystem, and a user symmetrically encrypts a file plaintext by a user-set password Keyl; then the user acquires the public key of reader via the Internet and uses the public key to symmetrically encrypt the password Keyl that is then stored in a file head; after receiving the file of user, the reader first decrypts the ciphertext of the password Keyl in the file head by the private key of reader to acquire the password Keyl, which is then used again to decrypt the cipher text of the file in order to obtain the plaintext. By combining the encryption and decryption of the file and the management of keys with the Internet, the present invention can enable users to conveniently decrypt or encrypt files anytime and anywhere.
Owner:农革
Method for undetectably impeding key strength of encryption usage for products exported outside the U.S.
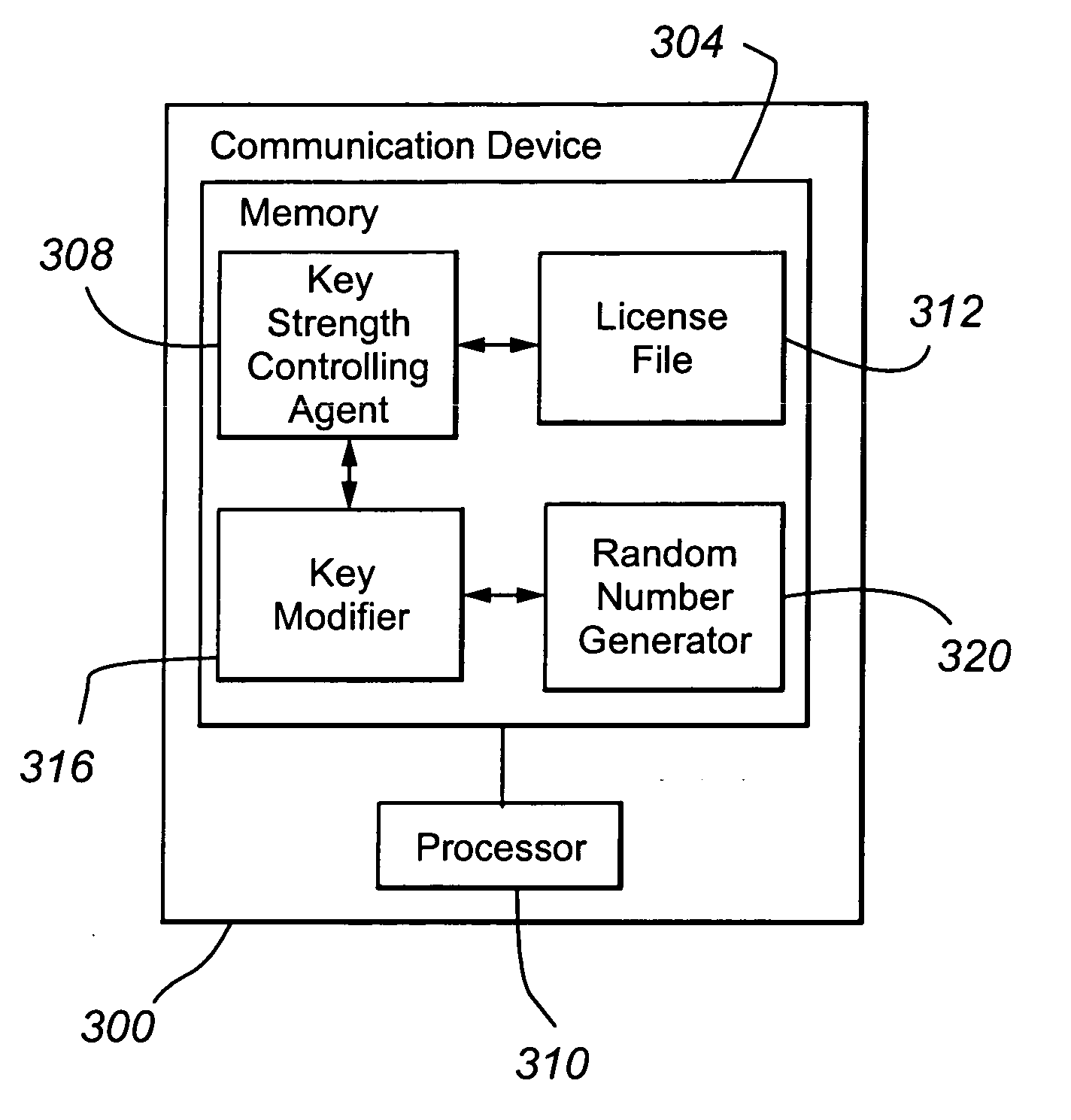
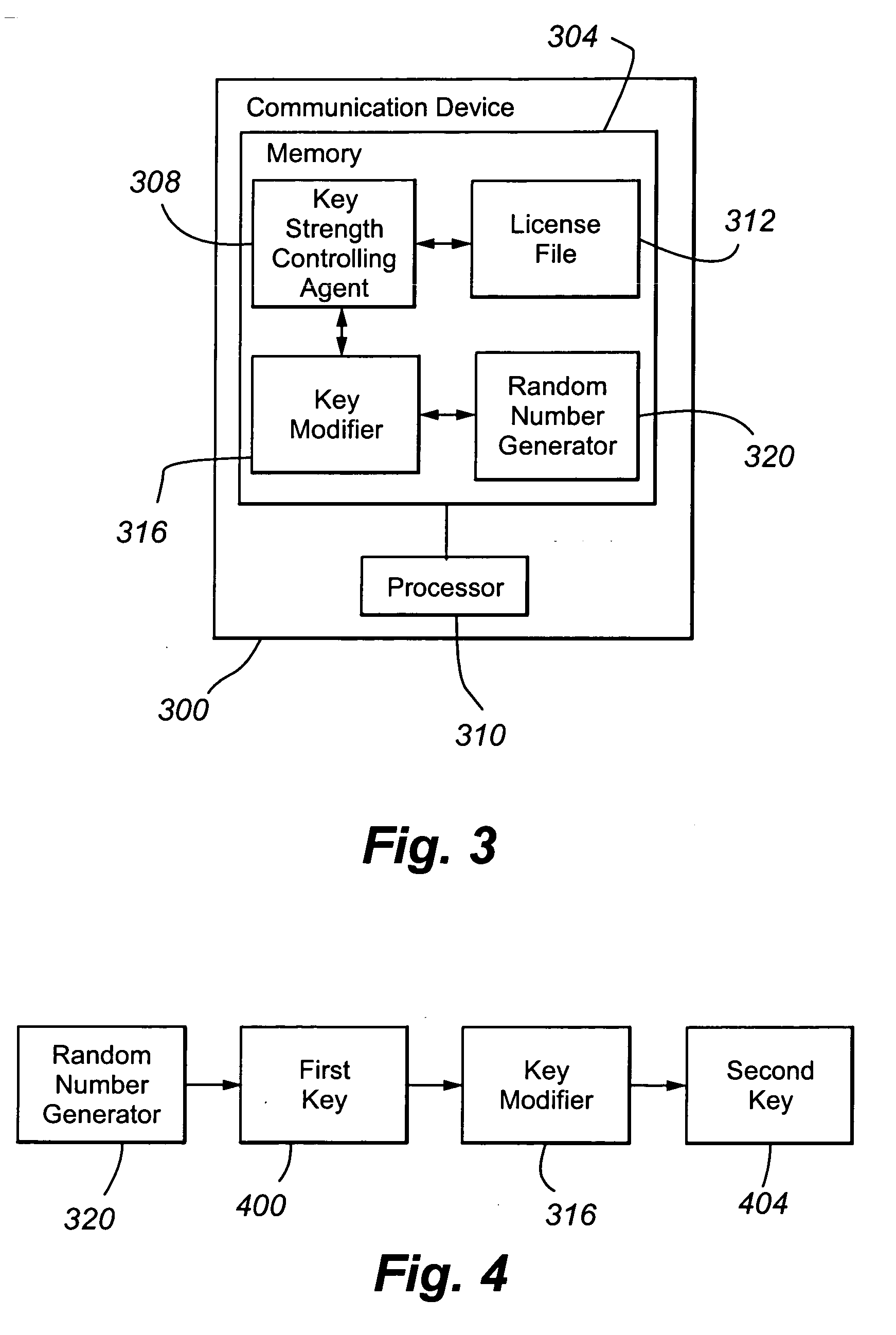
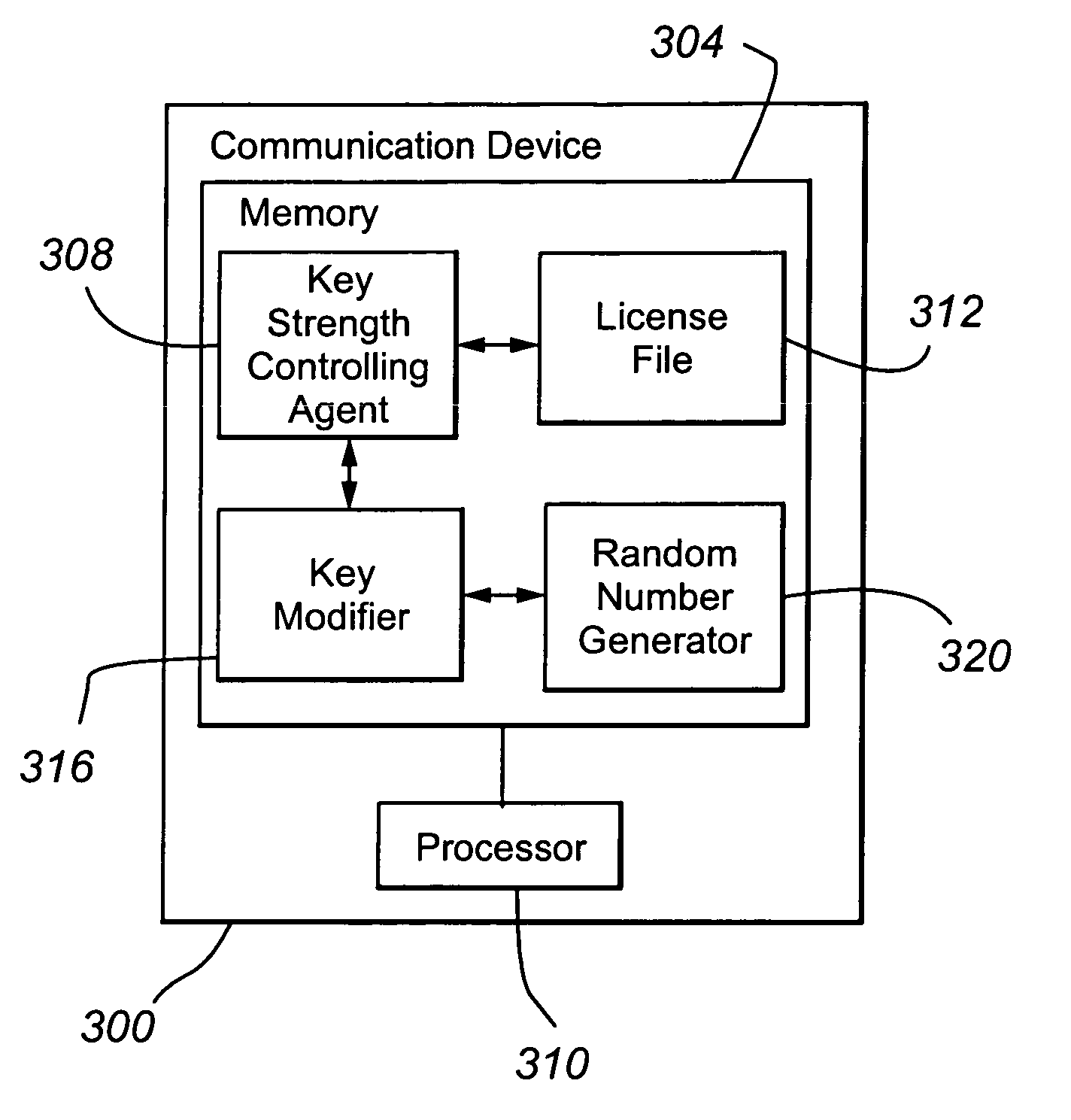
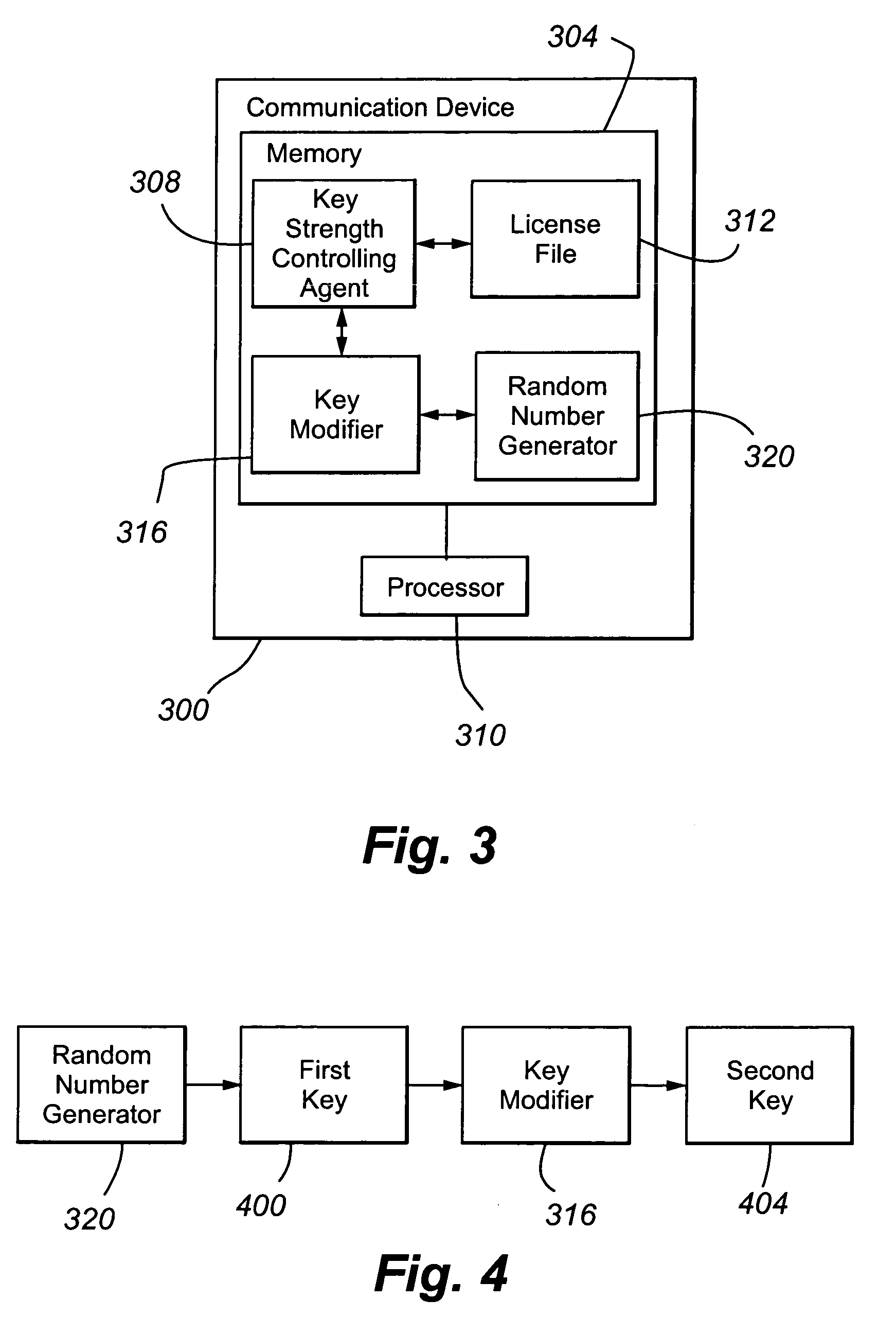
InactiveUS20070058814A1Simple and effectiveEasy to decryptKey distribution for secure communicationEncryptionCommunication device
In one embodiment, a communication device includes a key strength controlling agent 308 operable to (i) receive a request for a cryptographic key; (ii) determine, from a restriction identifier, whether the cryptographic key strength is restricted; (iii) when the cryptographic key is restricted, cause the use of a second cryptographic key having a second key strength; and (iv) when the cryptographic key is not restricted, cause the use of a first cryptographic key having a first key strength. The first and second key strengths are different.
Owner:AVAYA INC
System and method for encryption and decryption based on quantum key distribution
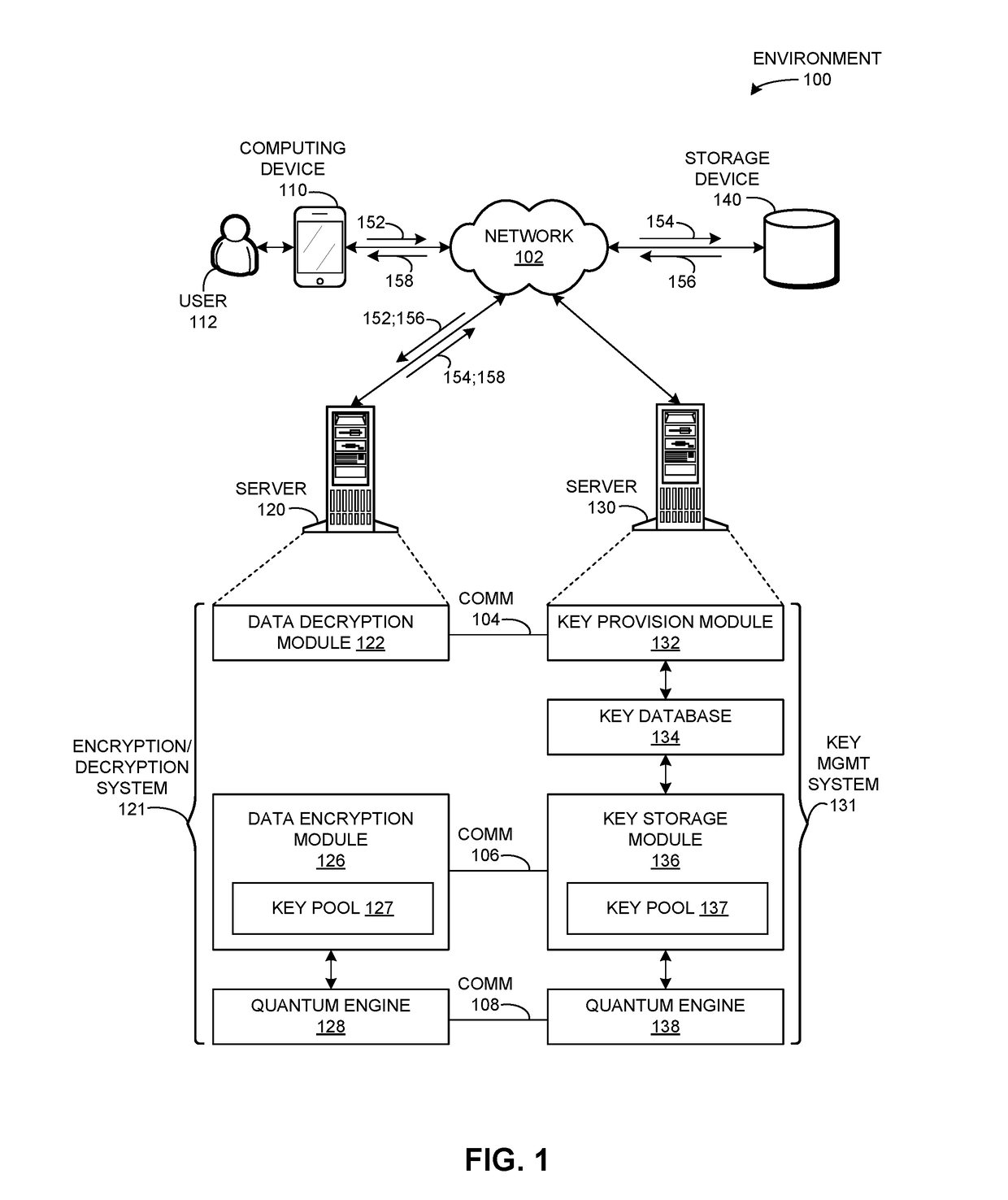
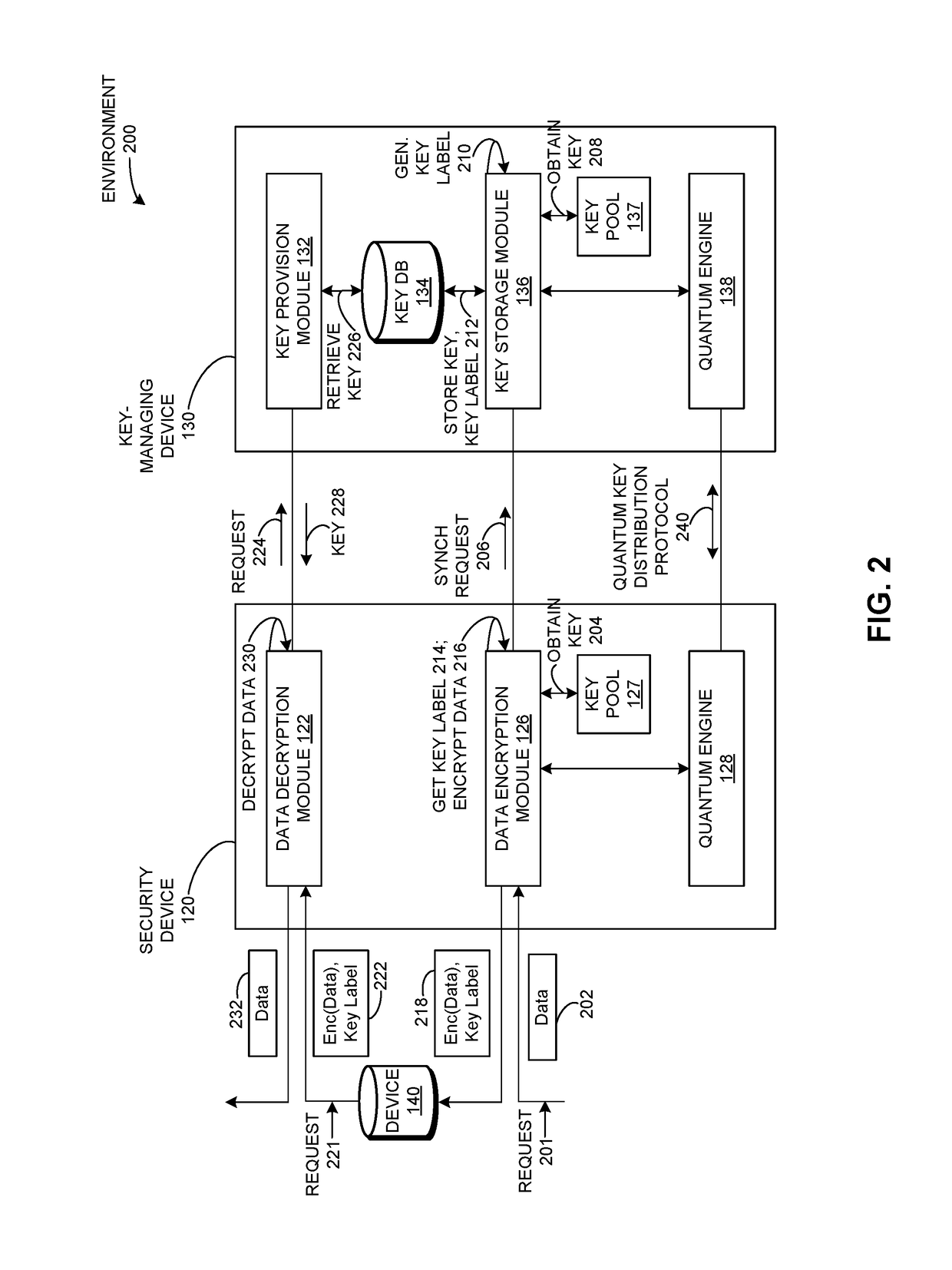
ActiveUS20170324550A1Facilitate secure encryption and decryptionFacilitating secure encryption and decryptionKey distribution for secure communicationProtocol for Carrying Authentication for Network AccessKey distribution
One embodiment of the present invention provides a system for facilitating storage encryption and decryption. During operation, the system receives a first request to encrypt data which is to be stored on a remote device, wherein the first request indicates the data. The system updates a key based on a dynamic key refreshment protocol. The system determines a key label for the updated key. The system encrypts the data based on the updated key, and transmits the encrypted data and the key label to the remote device, thereby facilitating secure encryption and decryption of data on the remote device.
Owner:ALIBABA GRP HLDG LTD
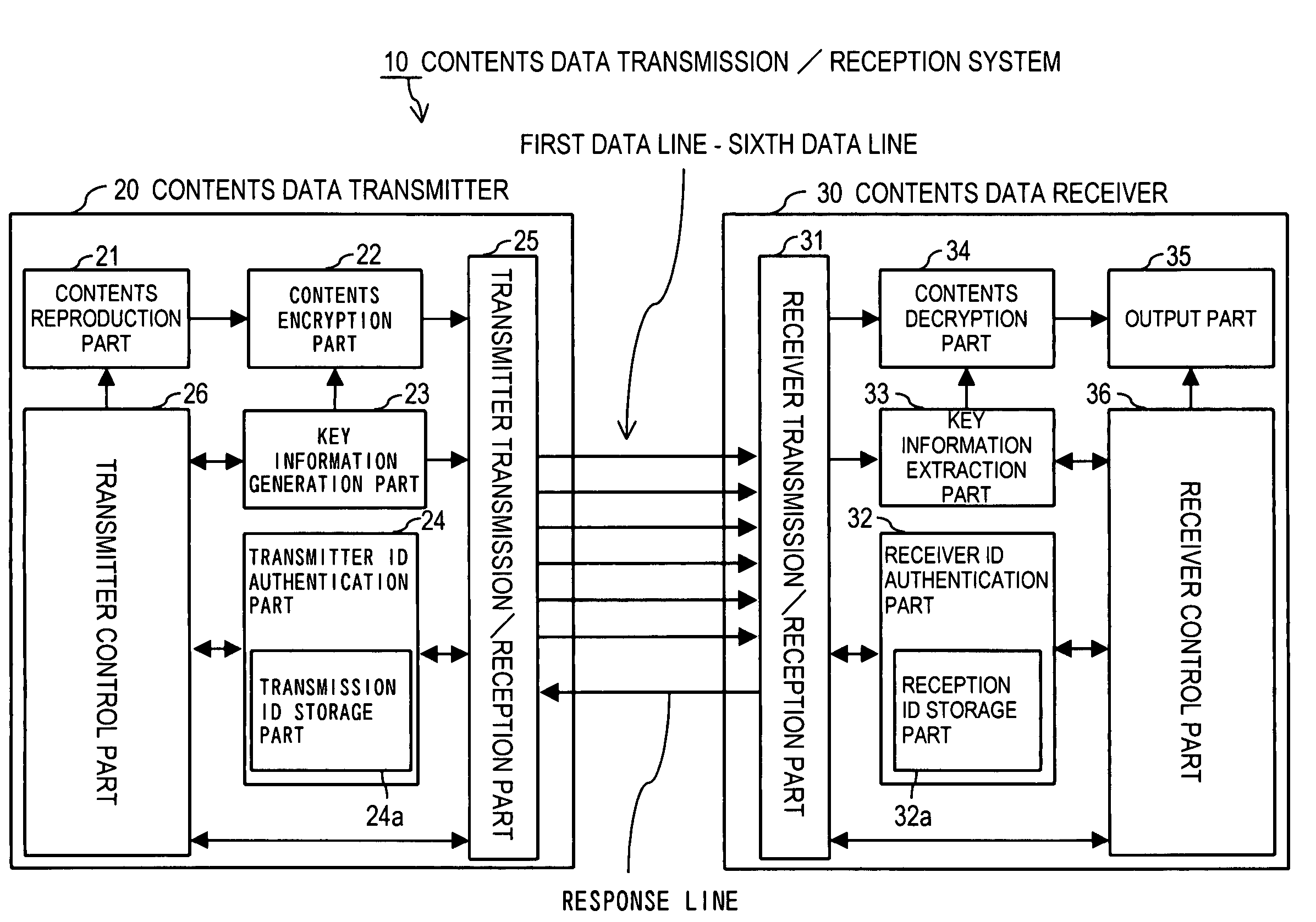
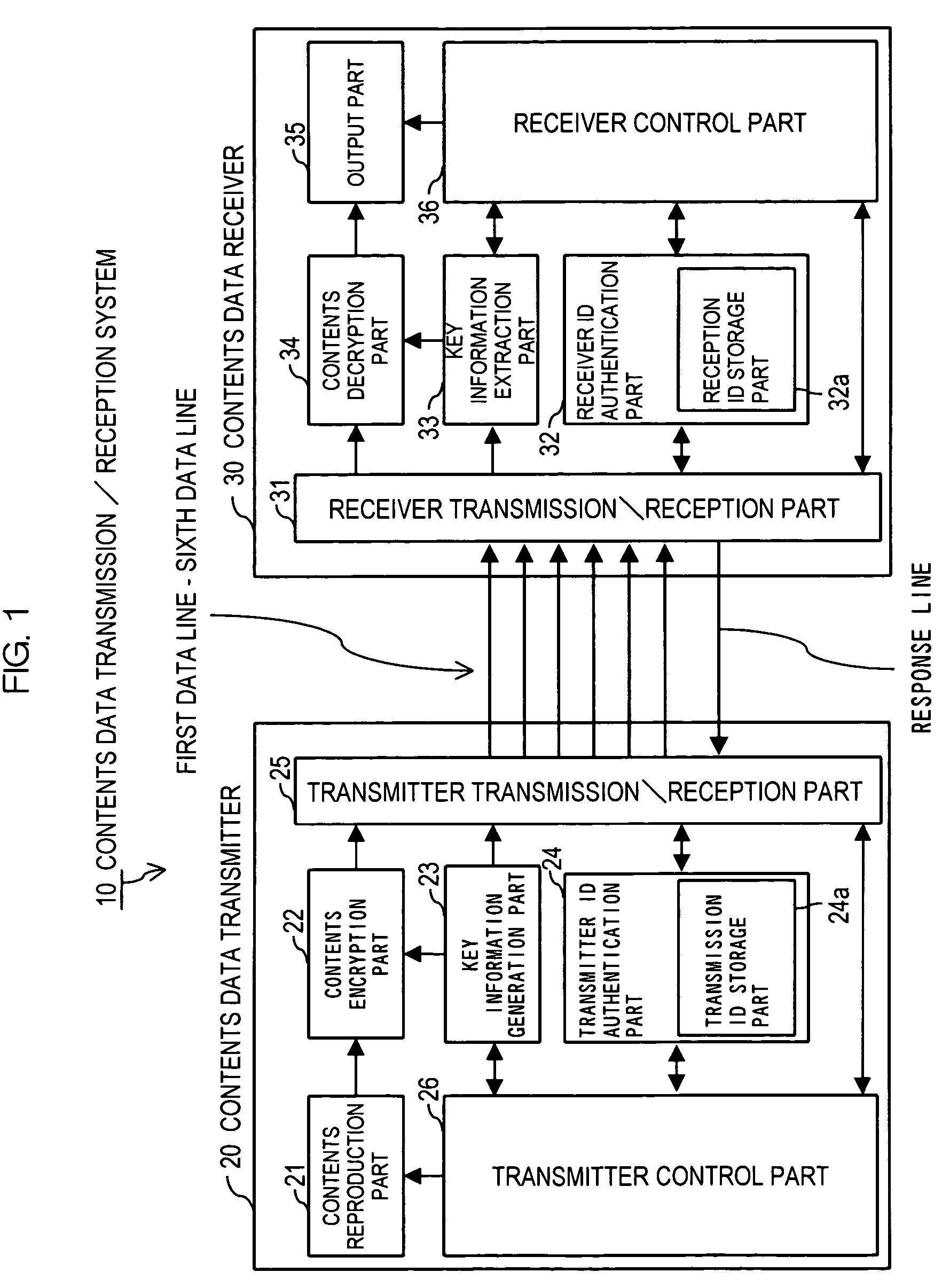
Contents data transmission/reception system, contents data transmitter, contents data receiver and contents data transmission/reception method
ActiveUS7412060B2Easy to decryptDifficult to extractUnauthorized memory use protectionRecord information storageData transmissionDatabase
In a contents data transmission / reception system, a contents data transmitter generates a plurality of key information, encrypts contents data by using one of the key information, transmits the key information through a plurality of signal routes to a contents data receiver, and then, transmits the encrypted contents data used by the key information through the signal routes to the contents data receiver. The contents data receiver receives the key information and the encrypted contents data transmitted from the contents data transmitter through the signal routes, and decrypts the encrypted contents data by using the key information.
Owner:D & M HOLDINGS INC
Cryptosystem using multivariable polynomials
InactiveUS20020001383A1Improve securityEasy to decryptPublic key for secure communicationSecret communicationCiphertextCryptosystem
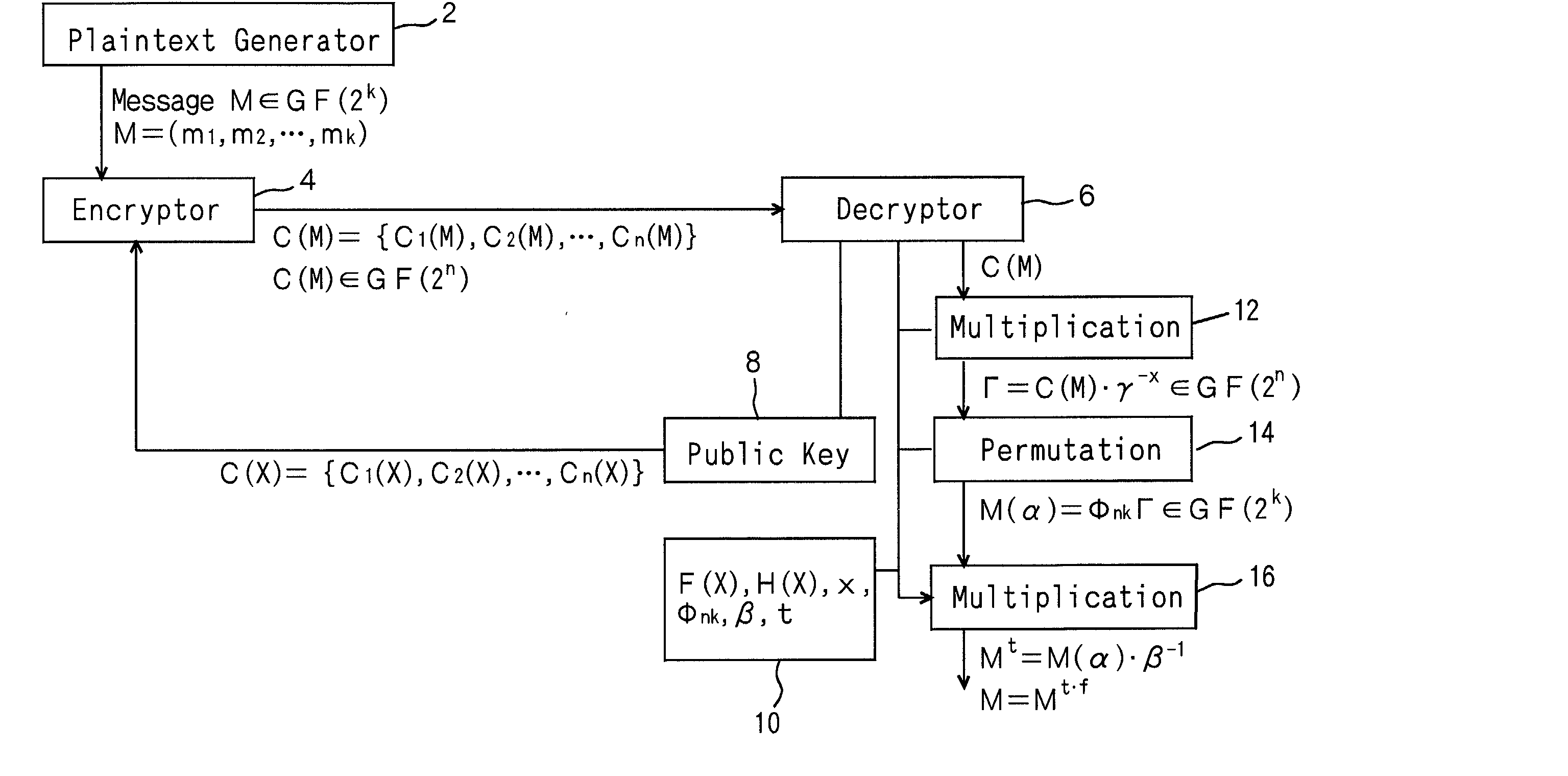
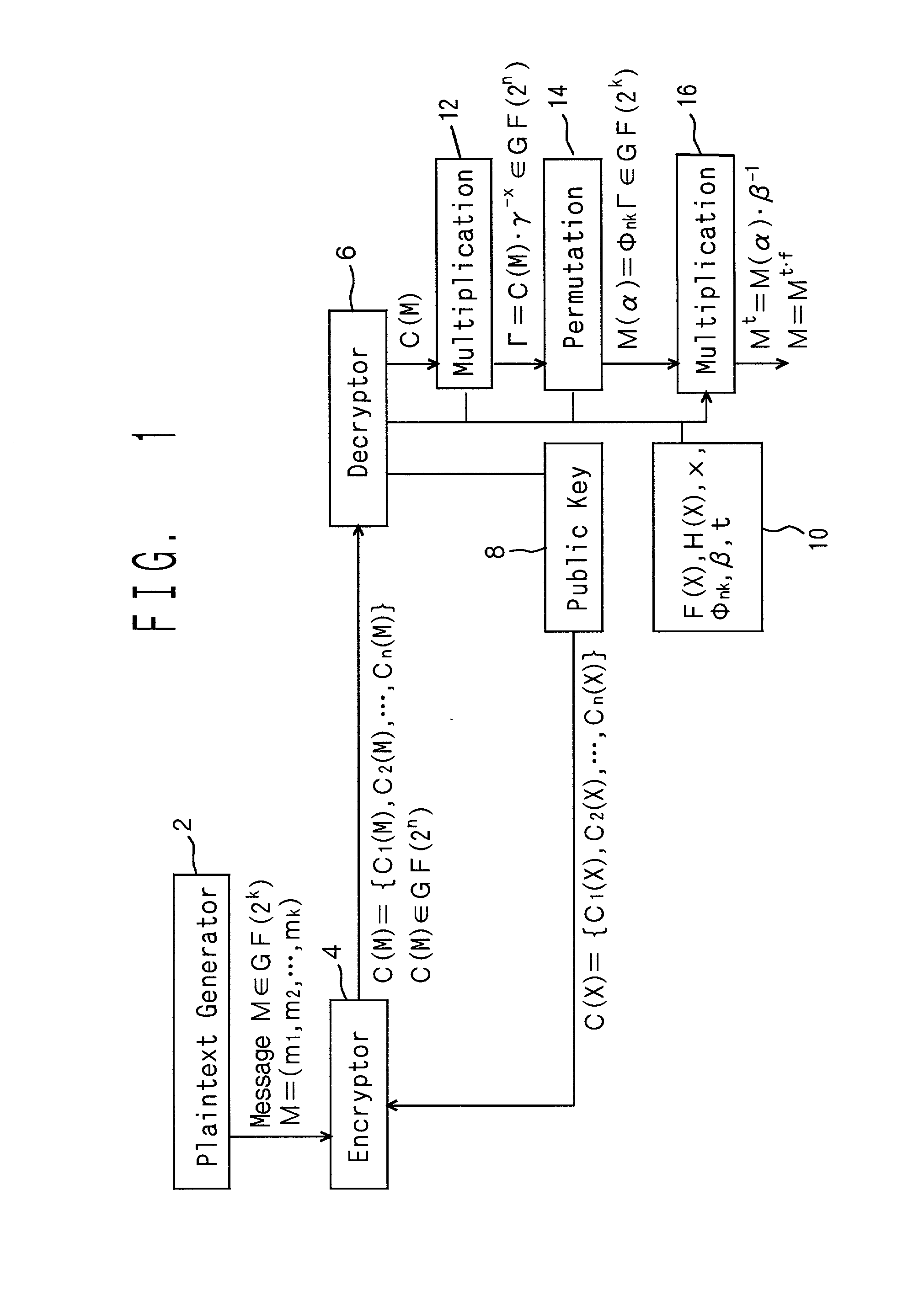
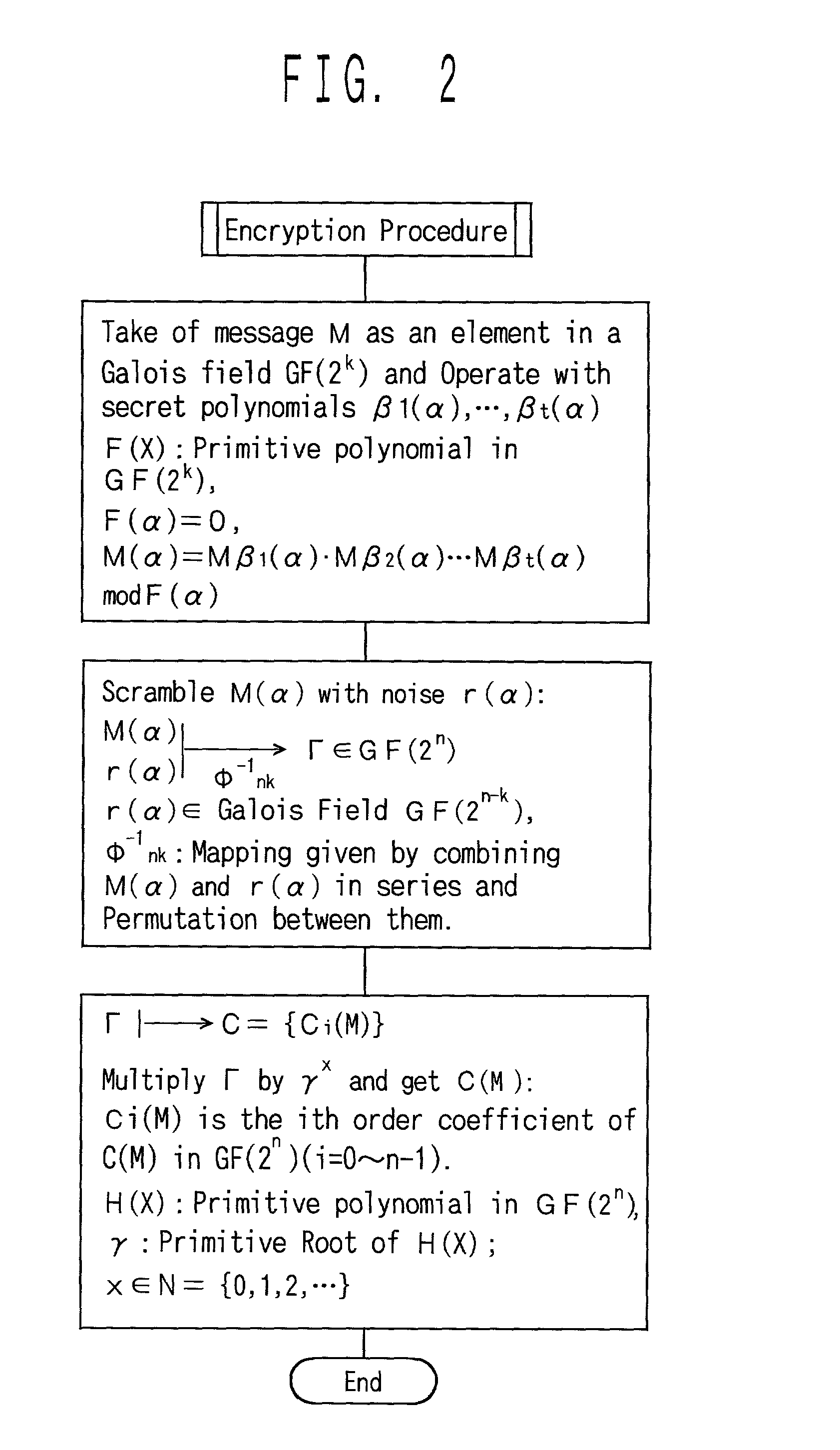
Let us consider a message M an element (m1,m2, . . . ,mk) in a Galois field GF (2k), and multiply it by a product of polynomials beta 1(alpha)-alpha t(alpha) into M(alpha).<paragraph lvl="0"><in-line-formula>M(alpha)=Mbeta1(alpha).Mbeta2(alpha) . . . Mbetat(alpha)< / in-line-formula>Combine a noise vector r(alpha) of n-k to M(alpha) in series so that the data is expanded into degree n. Next, they are transformed into Γ by permutation. Γ is multiplied by an element gammax in the Galois field GF(2n) into cyphertext C(M), where gamma is a primitive root of the multiplicative group of the Galois field GF(2n). Practically, when the message M is substituted for X in a public key C(X), the cyphertext C(M) is obtained. The cyphertext C(M) is multiplied by gamma-x, is applied to an inverse permutation, and the noise vector r(alpha) is separated. Then, the inverse element of the product of beta1(alpha)-betat(alpha) is multiplied and is raised to an adequate index. Then the decrypted message is obtained.
Owner:MURATA MASCH LTD +1
System for securely communicating information packets
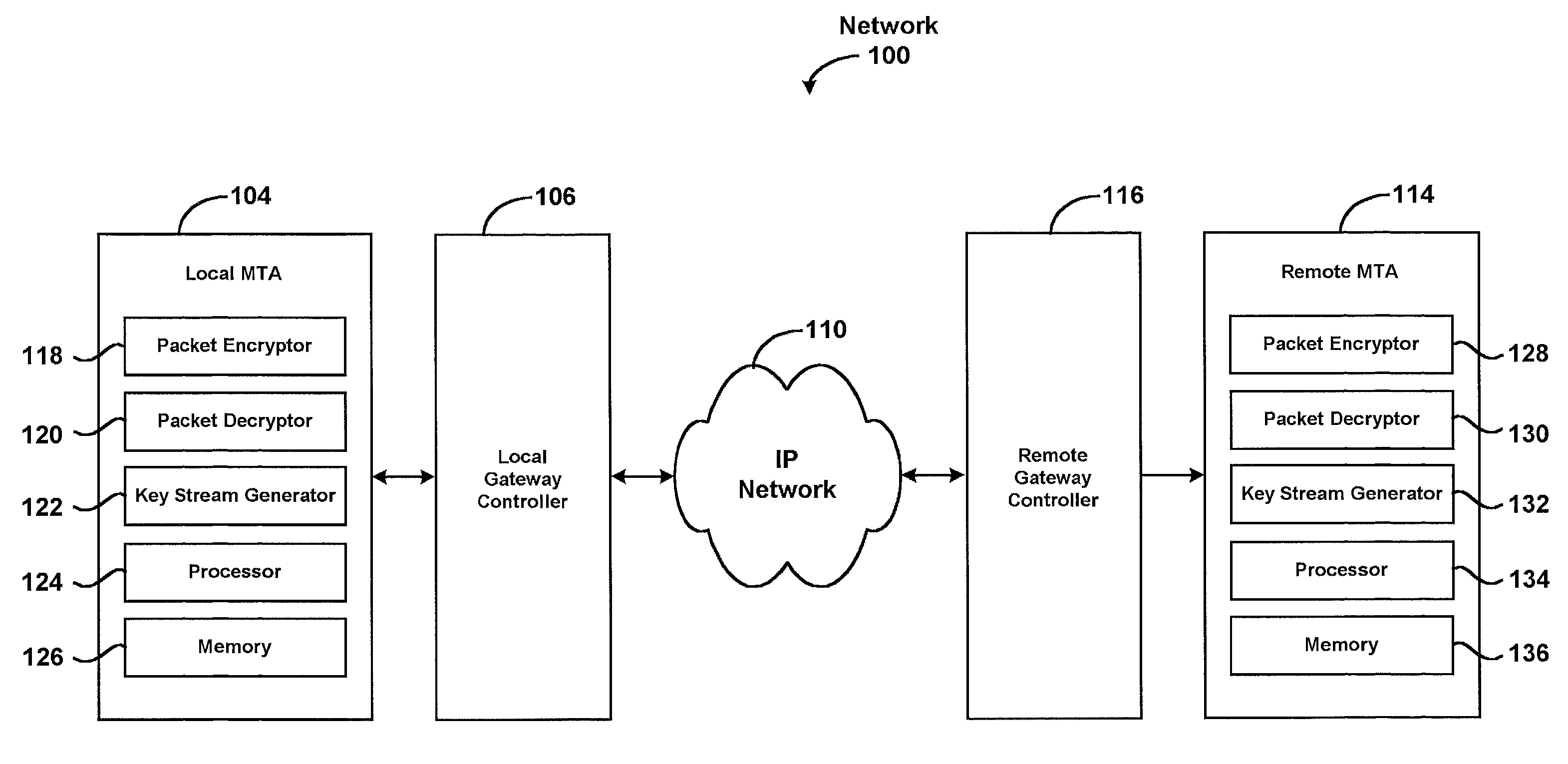
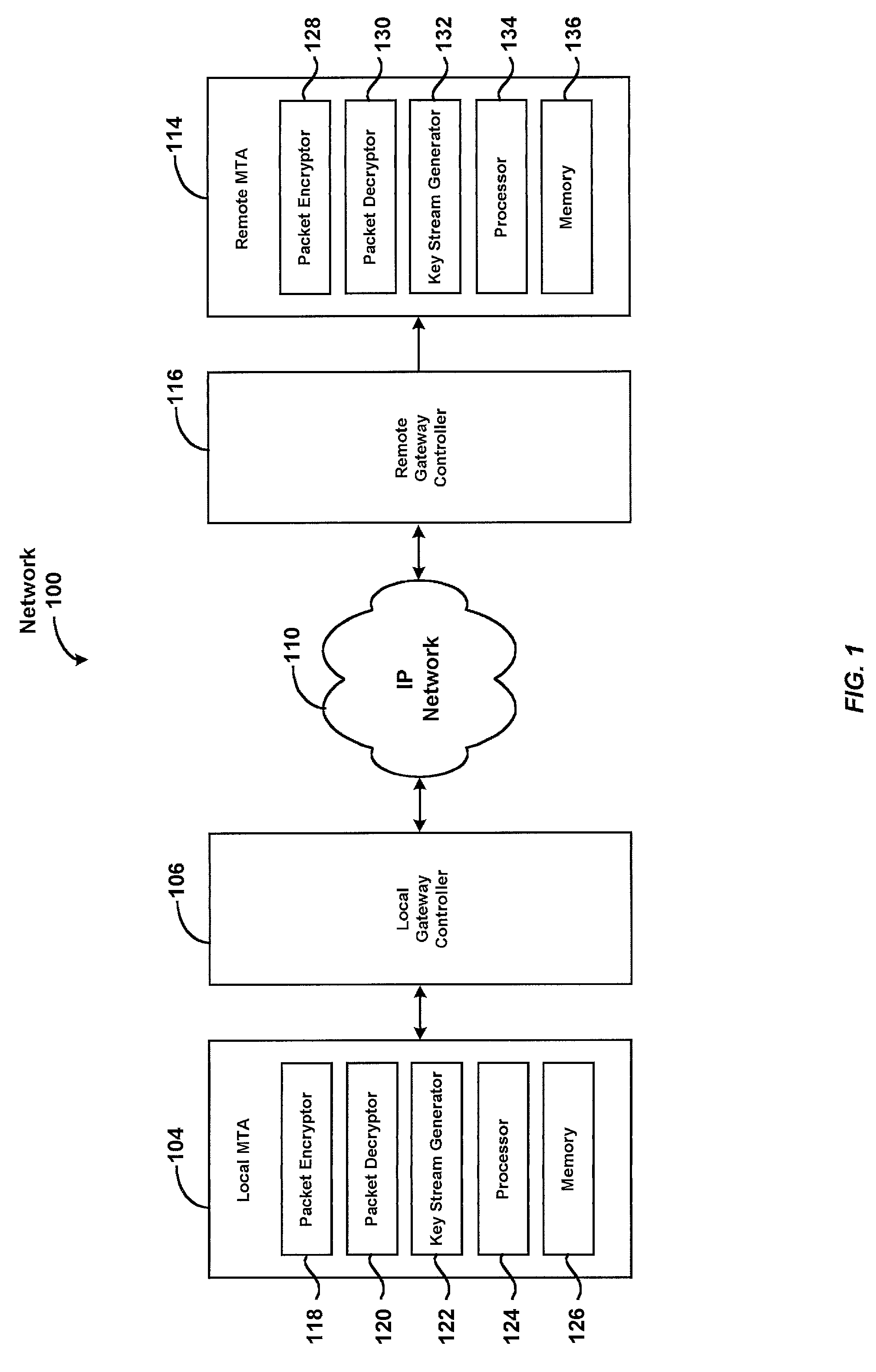
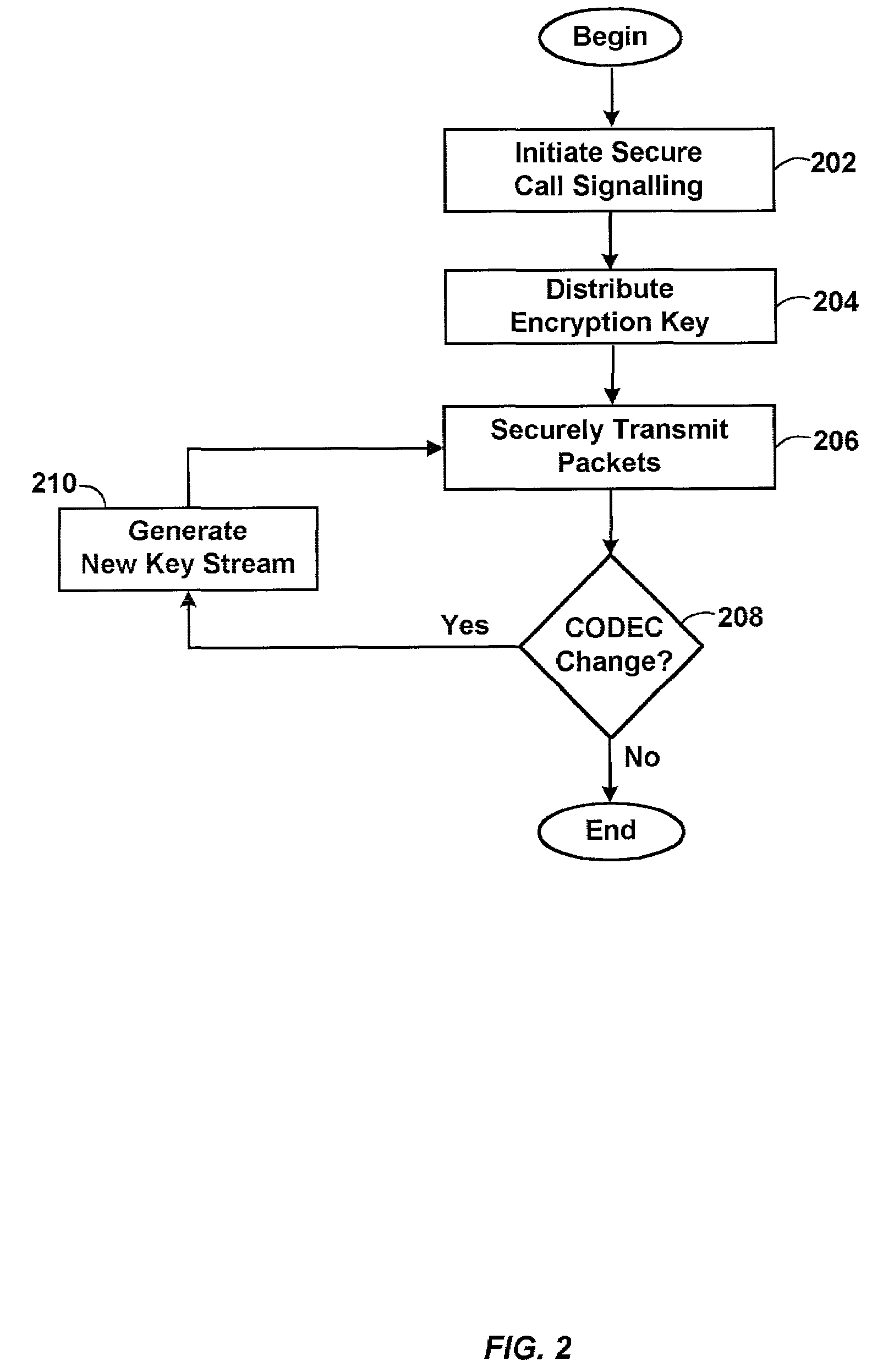
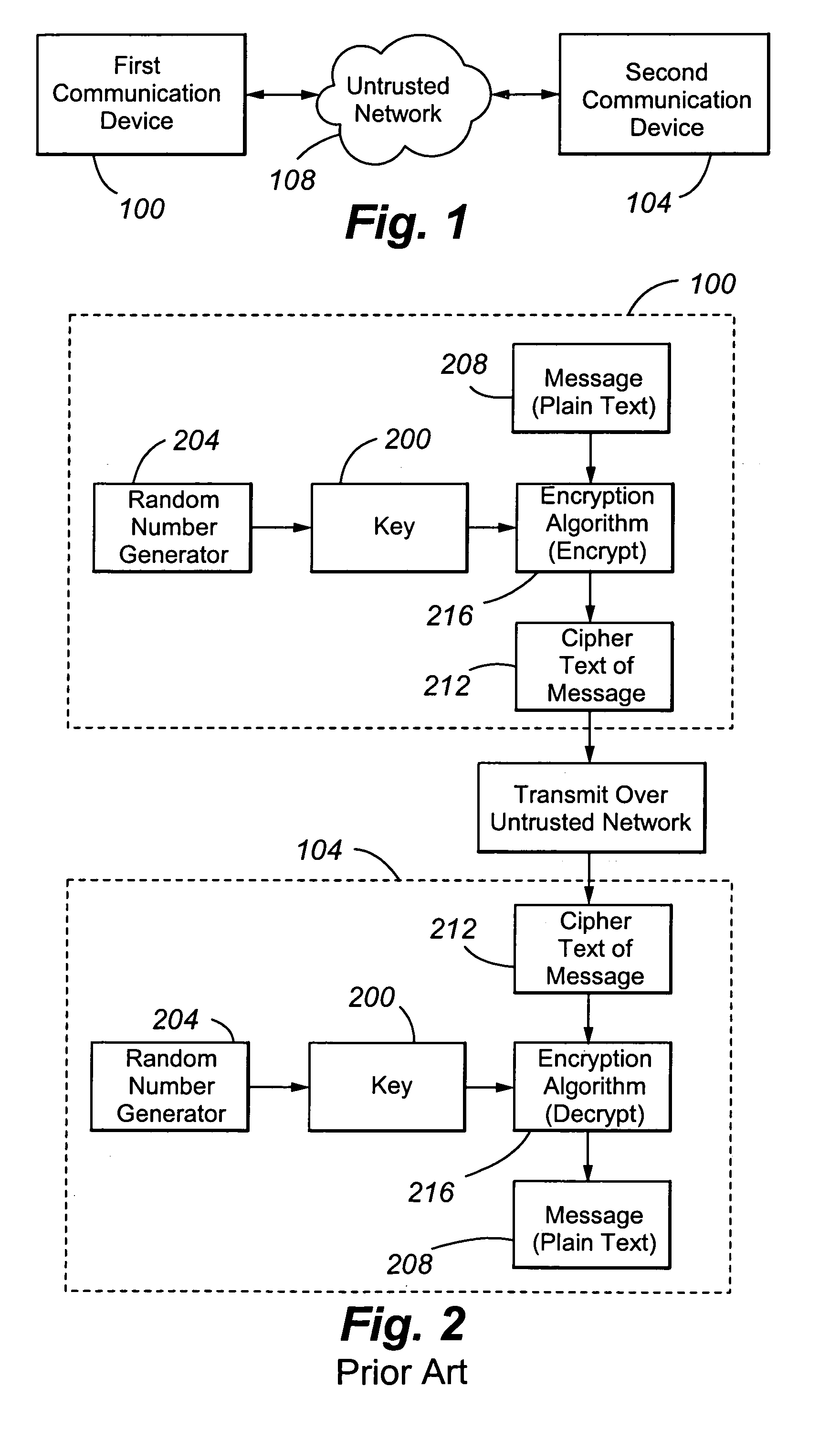
InactiveUS7684565B2Secure transmissionEasy to decryptSynchronising transmission/receiving encryption devicesData stream serial/continuous modificationComputer networkTime Protocol
A system for securely transmitting Real Time Protocol voice packets to a remote multimedia terminal adapter over an Internet protocol network. The system features an MTA (a local multimedia terminal adapter) having a key stream generator for generating a first key stream used for encrypting the voice packets. The remote multimedia terminal adapter receives and decrypts the voice packets. Also, the system includes a remote key stream generator for generating the first key stream in order to decrypt the encrypted voice packets and a packet decryptor decrypting the encrypted voice packets using the first key stream, wherein both key stream generators are capable of generating a second key stream to prevent reuse of any portion of the first key stream during the communication session.
Owner:GOOGLE TECH HLDG LLC
Method for removing visual watermark of block local encrypted digital image
InactiveCN1945623ANo damageSimple and fast operationImage data processing detailsWatermark methodResonance
The invention is a method that the digital image can be encrypted in block parts and eliminated the visible watermarks. Every pixels of 2-value watermark image will be corresponded to the pixels nub of 4 * 4 size in the vector gray image, and encryption is made to a part of pixels in the block corresponding to black pixels to get the image with translucent watermark. The embedding and the resuming sides possess the same key or key generator. The sender embeds the 2-value digital watermark image into the vector translucently on the base of key, which can be the image of scenery taken by digital camera, CT or magnetic resonance, satellite remote sensing and et al, and discloses the image with digital watermark. When getting it, the resuming side can remove the 2-value digital watermark image to renew the former one by the same key.
Owner:DANDONG DONGFANG MEASUREMENT&CONTROL TECHCO +1
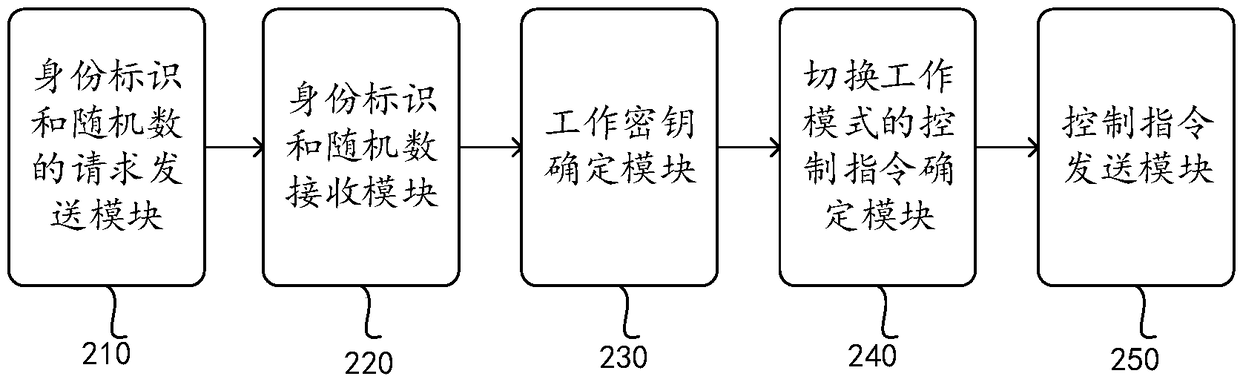
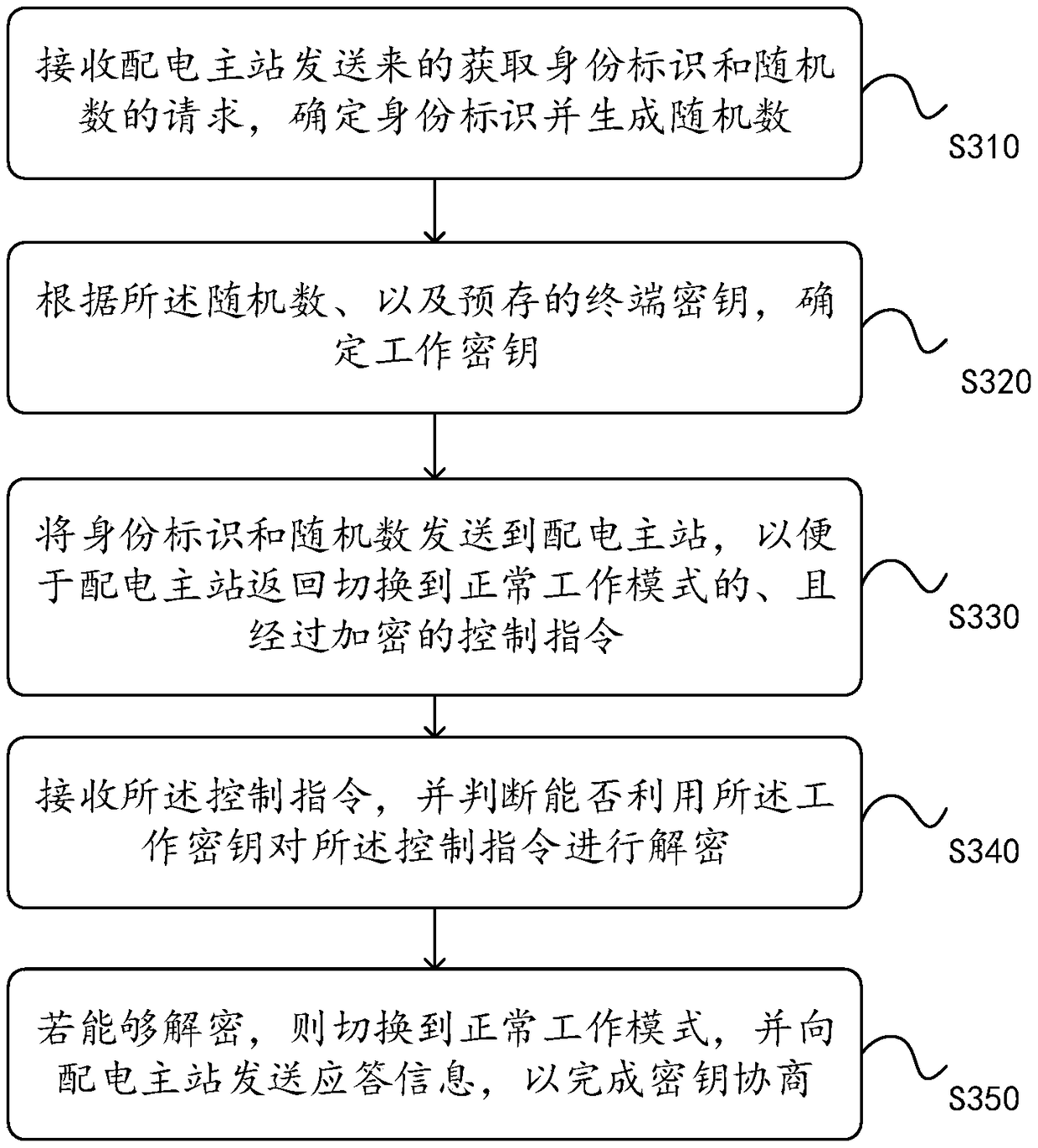
Key negotiation method and device, and power distribution automatic system
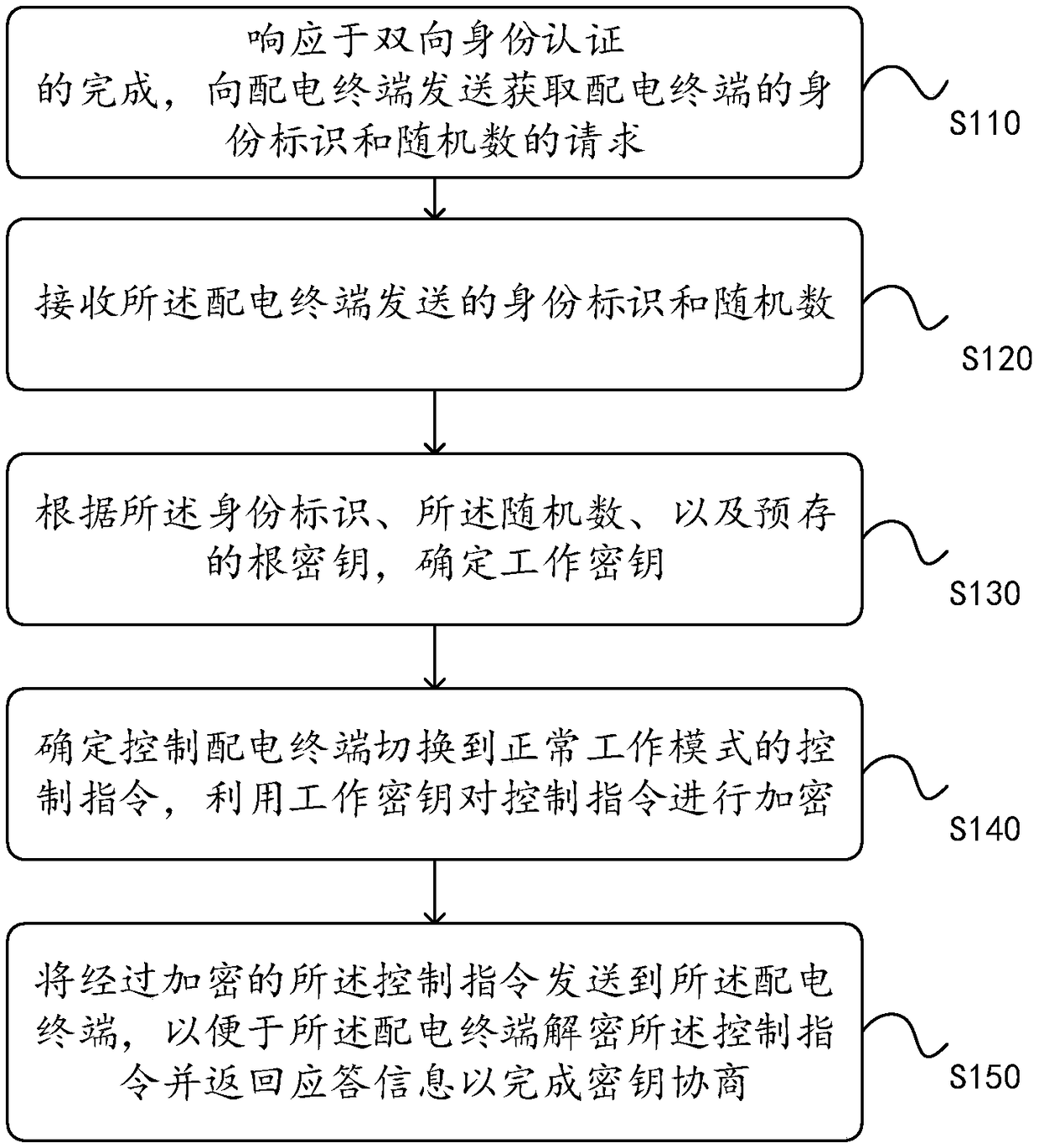
InactiveCN108809645AImprove securityEasy to decryptKey distribution for secure communicationUser identity/authority verificationPrimary stationKey generation
The invention discloses a key negotiation method applied to a power distribution main station of a distribution automatic system, which can obtain the identity label and random number of the power distribution terminal after the two-way identity authentication is completed, and generates a working key according to the identity label, the random number and the root key and sends a control instruction encrypted with the working key to the power distribution terminal, so that the power distribution terminal decrypts the control instruction and returns response information to complete key negotiation. It can be seen that the working key in the present invention is generated according to the identity label and the random number; in different session processes, the random number is different, sothe working key is also different and is not easy for the illegal personnel to crack, thereby greatly improving the safety of the distribution automatic system. Correspondingly, the present inventionalso provides a key negotiation device, a key negotiation method and device applied to the power distribution terminal, and a power distribution automatic system, the functions of which correspond tothe functions of the aforementioned method.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD
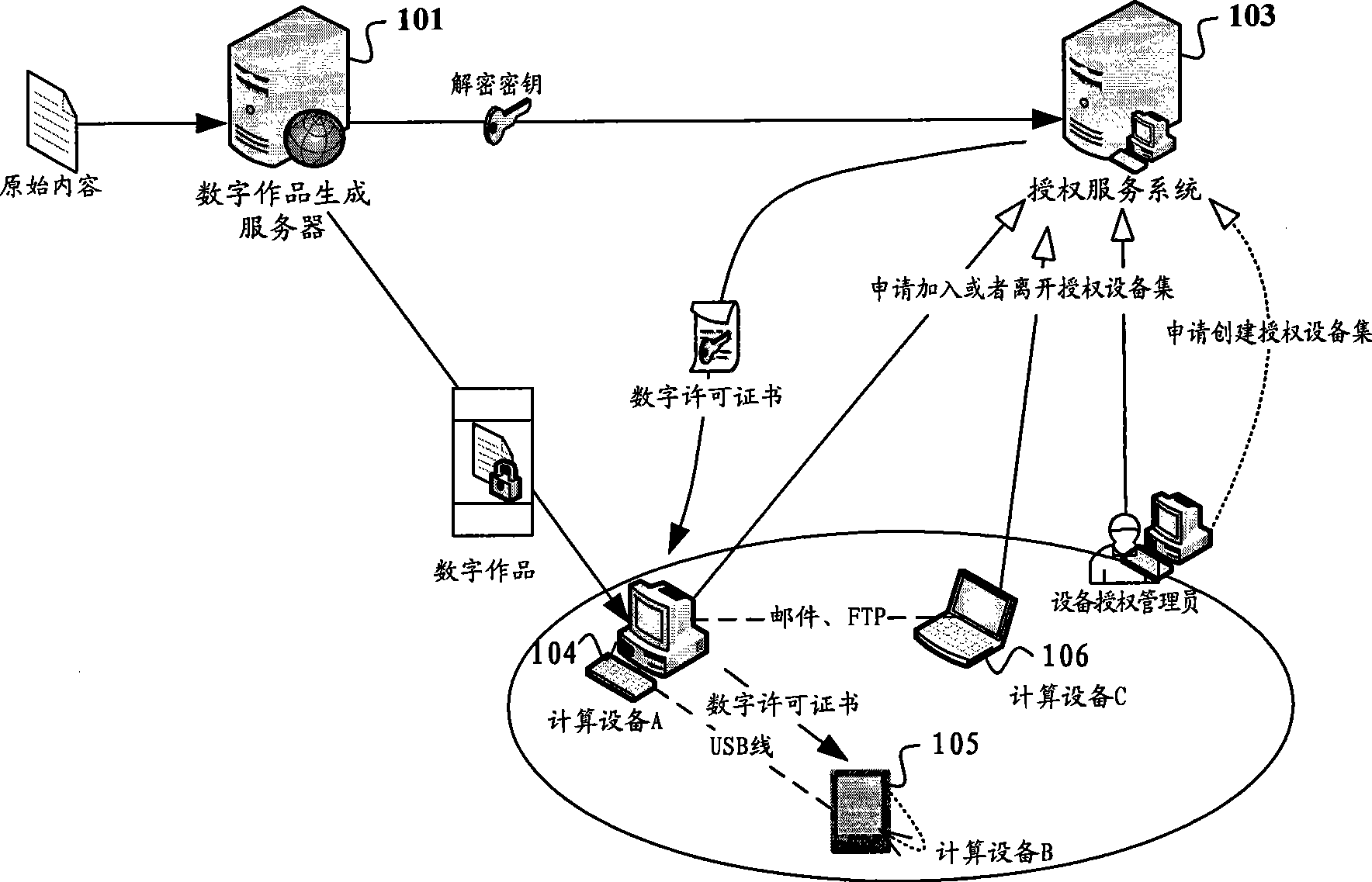
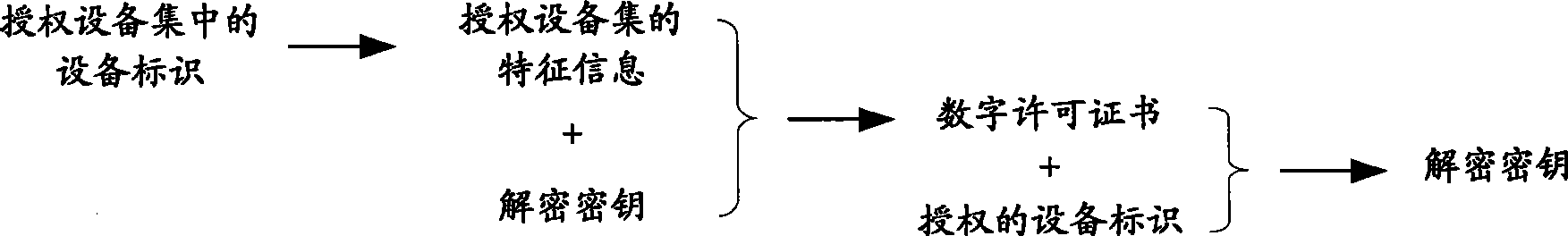
Digital exequatur sending system and digital work decipher operation method
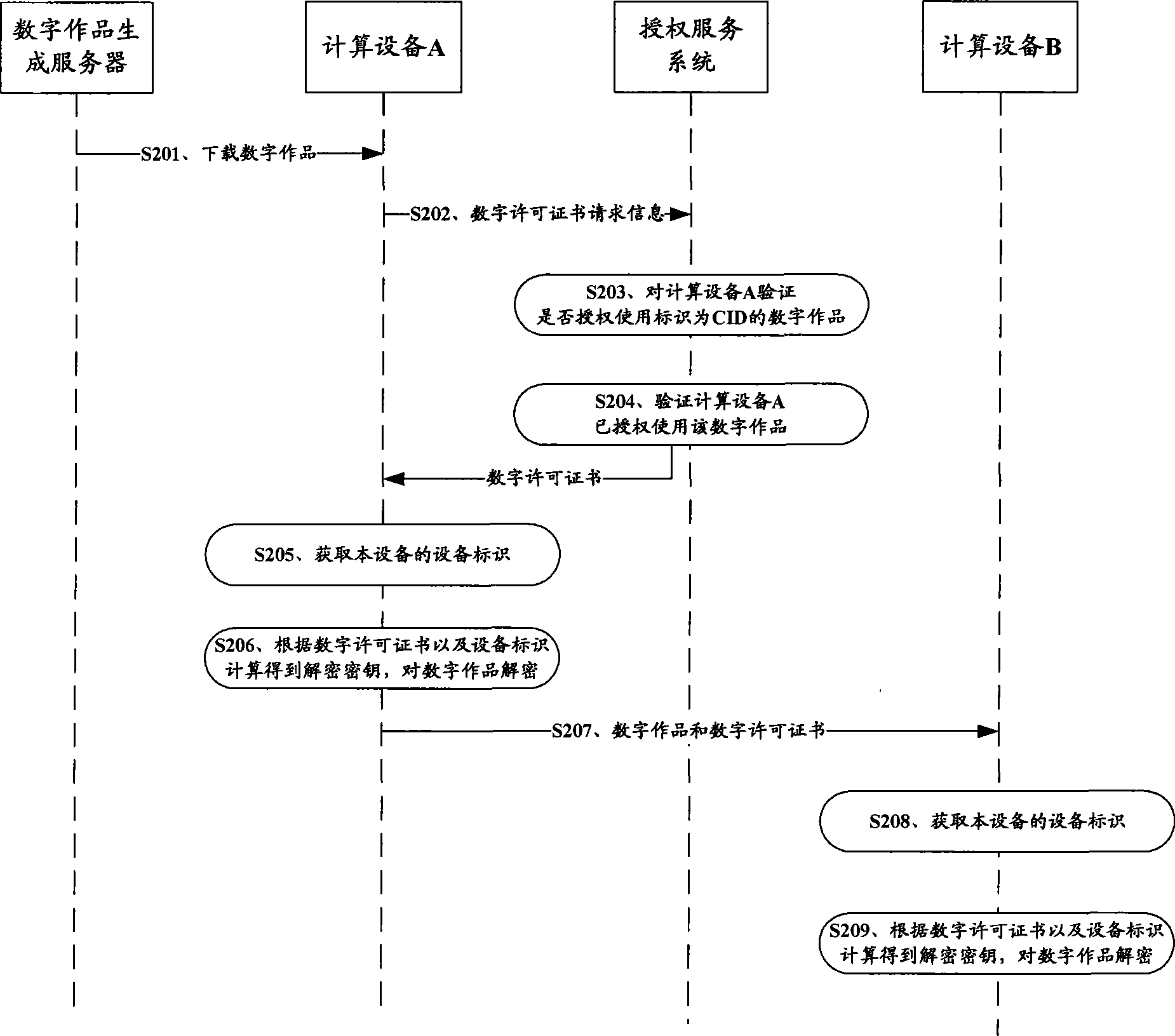
ActiveCN101425112AGood replicationEasy to getDigital data authenticationProgram/content distribution protectionDECIPHERAuthorization
The invention relates to the field of digital work copyright protection, in particular to a technique in which a multi-computing apparatus uses a digital work upon authorization, and more particular to a digital permit transmitting system, a computing apparatus and a digital work decryption operating method. The method comprises the following steps: the computing apparatus obtains a digital permit of the digital work; the digital permit is generated according to characteristic information of an authorization apparatus set and a decryption key of the digital work; and the computing apparatus obtains an apparatus identifier of the present computing apparatus, restores the decryption key according to the digital permit and the apparatus identifier of the present computing apparatus, and operates the digital work after decrypting the digital work by using the decryption key. Due to the convenient reduplication of the digital permit, the authorized computing apparatus can conveniently obtain the digital permit and conveniently utilizing the apparatus identifier of the present computing apparatus and the digital permit to obtain the decryption key so as to decrypt and operate the digital work.
Owner:PEKING UNIV +2
Terminal control method, terminal and system
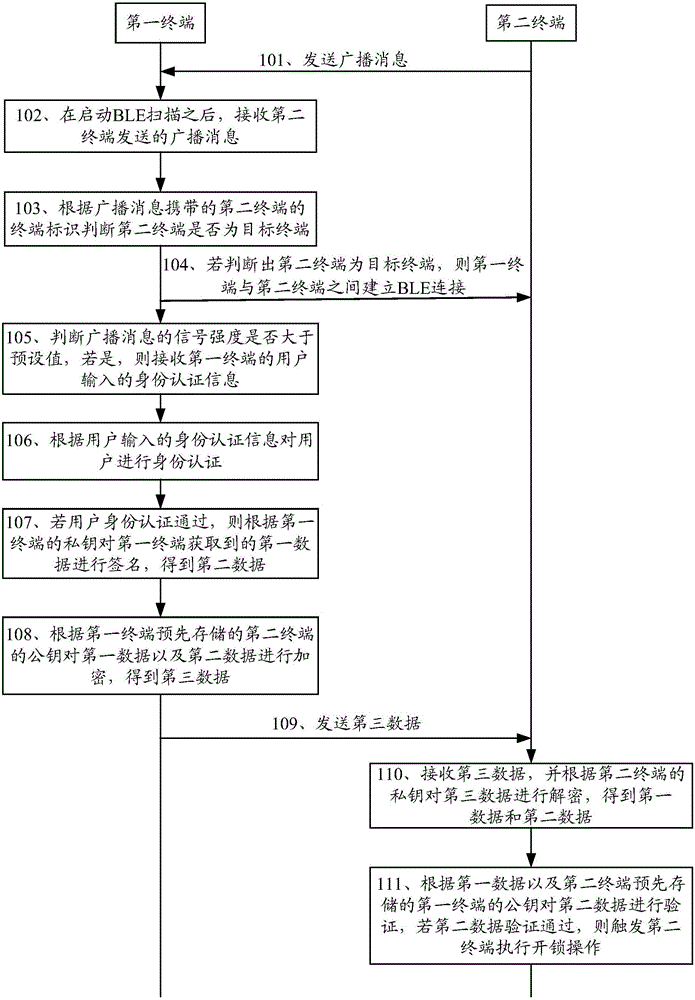
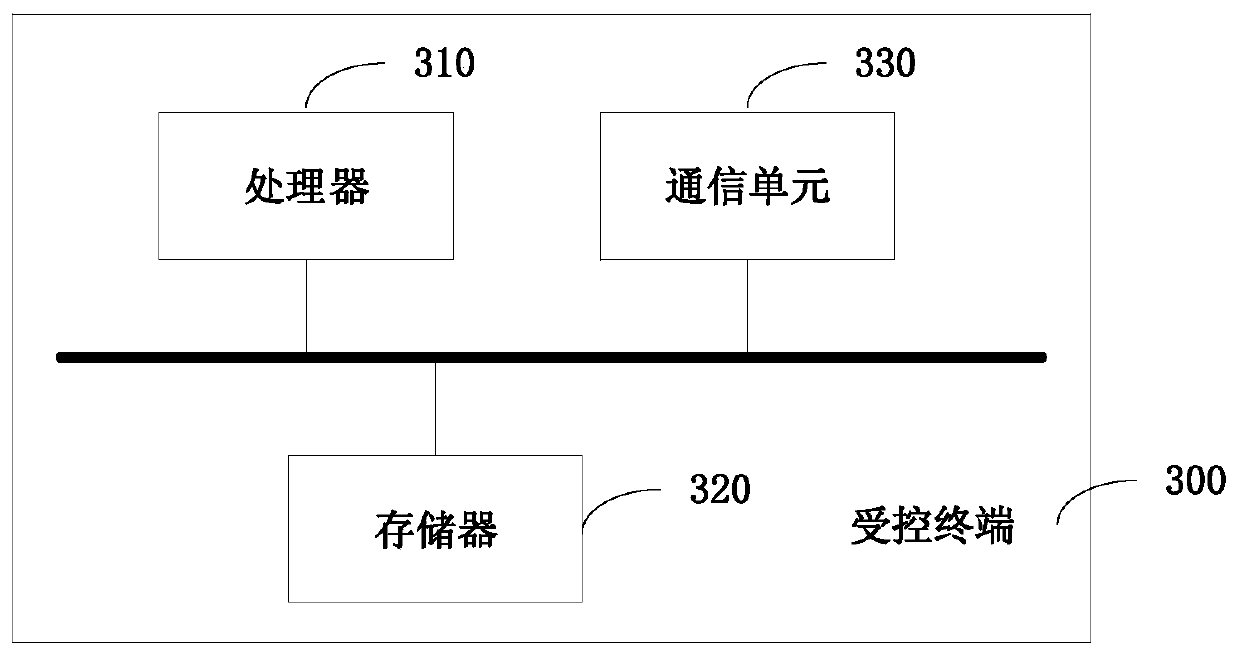
InactiveCN106850540AEasy to decryptImprove data securityUser identity/authority verificationIndividual entry/exit registersData validationComputer engineering
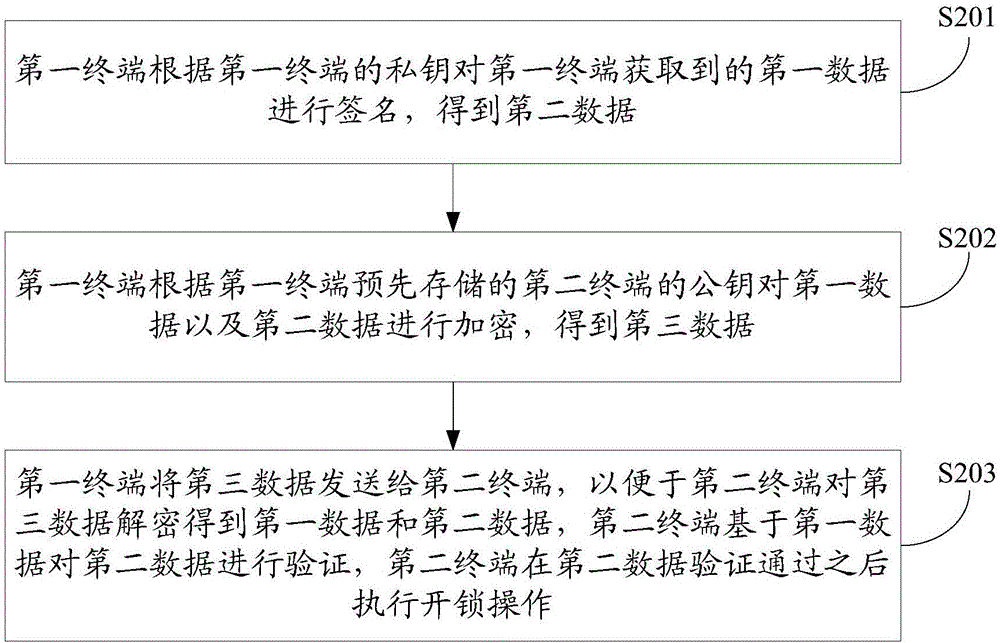
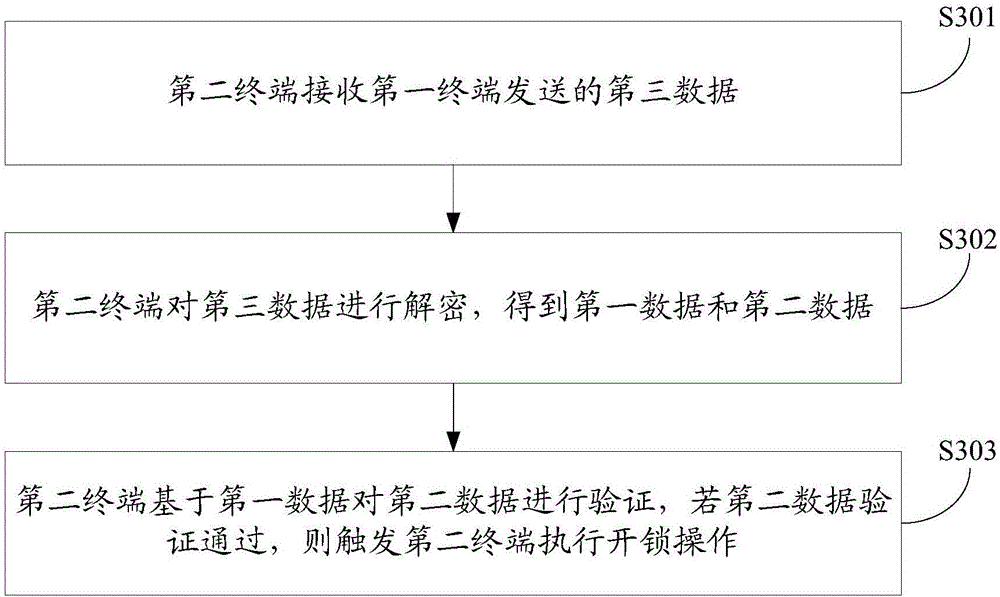
The embodiment of the present invention discloses a terminal control method, terminal and system, wherein the method includes: the first terminal signs the first data acquired by the first terminal according to the private key of the first terminal, and obtains the second data; the first terminal encrypts the first data and the second data according to the public key of the second terminal pre-stored by the first terminal to obtain third data; the first terminal encrypts the The third data is sent to the second terminal, so that the second terminal decrypts the third data to obtain the first data and the second data, and the second terminal based on the first data The second data is verified, and the second terminal performs an unlocking operation after the second data is verified. The embodiment of the present invention can effectively improve the data security in the process of keyless unlocking by adopting the public-private key cryptography technology to sign and encrypt the data.
Owner:SHENZHEN GIONEE COMM EQUIP
Privacy protection type attribute matching method based on symmetrical encryption
The invention relates to a privacy protection type attribute matching method based on symmetrical encryption. According to the method, a secret key is generated by means of common attributes naturally shared by matched users, an establish request and a secure channel secret key are connected through the secret key in an encryption mode, and only the matched users can generate the same secret key, decrypt a message conveniently and obtain a channel secret key; in this way, privacy protection type attribute matching and secure channel establishment are achieved synchronously through one round of communication, accurate and fuzzy matching / searching can be achieved, any privacy information can not be obtained by a participant with a similarity degree lower than the threshold value, an established secure channel can resist man-in-the-middle attack, and meanwhile, the attribute matching mechanism is verifiable so that matching result cheating attack can be resisted. Compared with most existing methods depending on an asymmetric encryption system and a trusted third party, the method has the advantages that calculation cost and communication cost are reduced greatly, calculated amount is small, practicality is high, flexibility is high, and the lightweight purpose is realized.
Owner:RUN TECH CO LTD
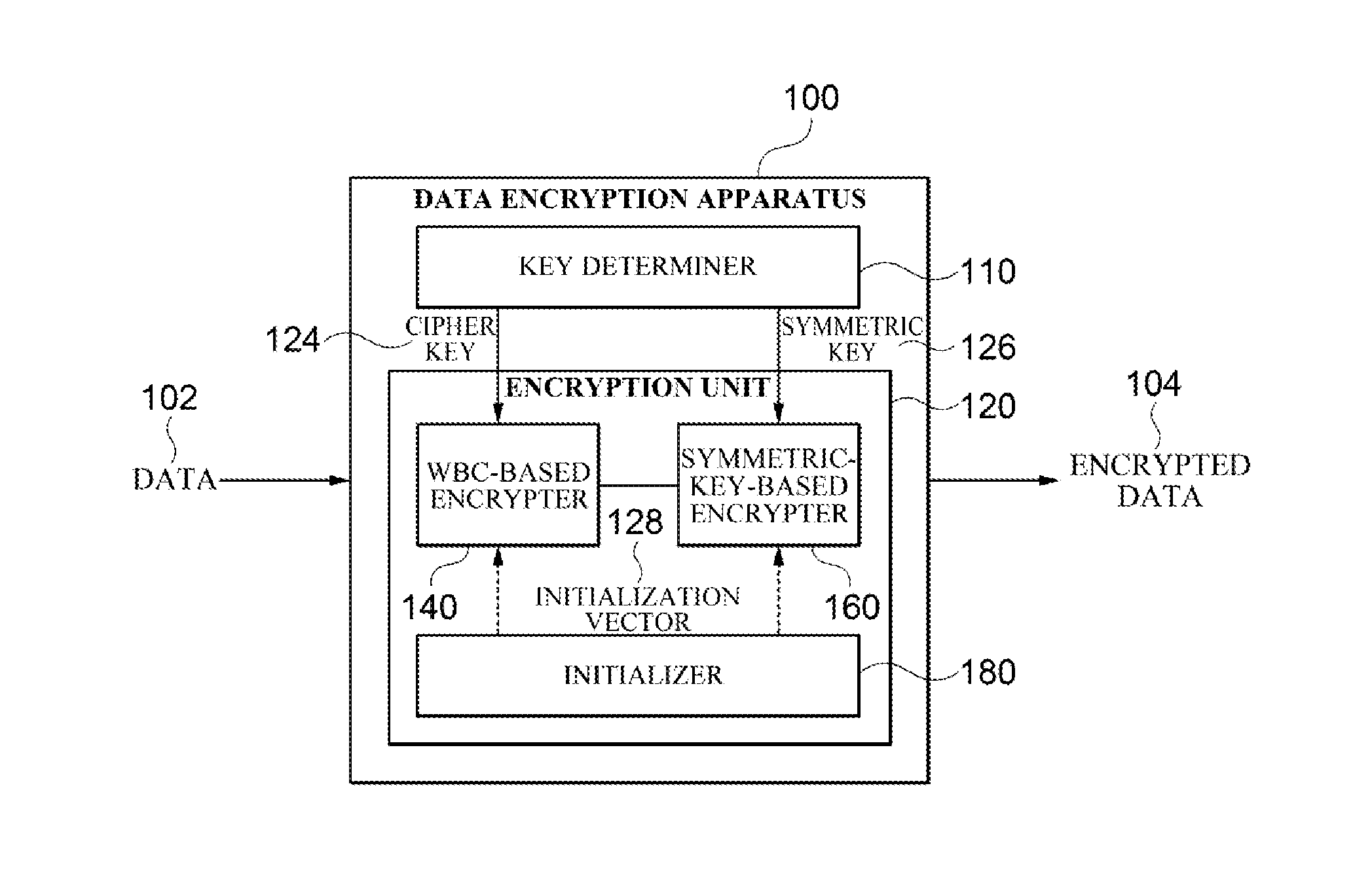
Apparatus and method for data encryption
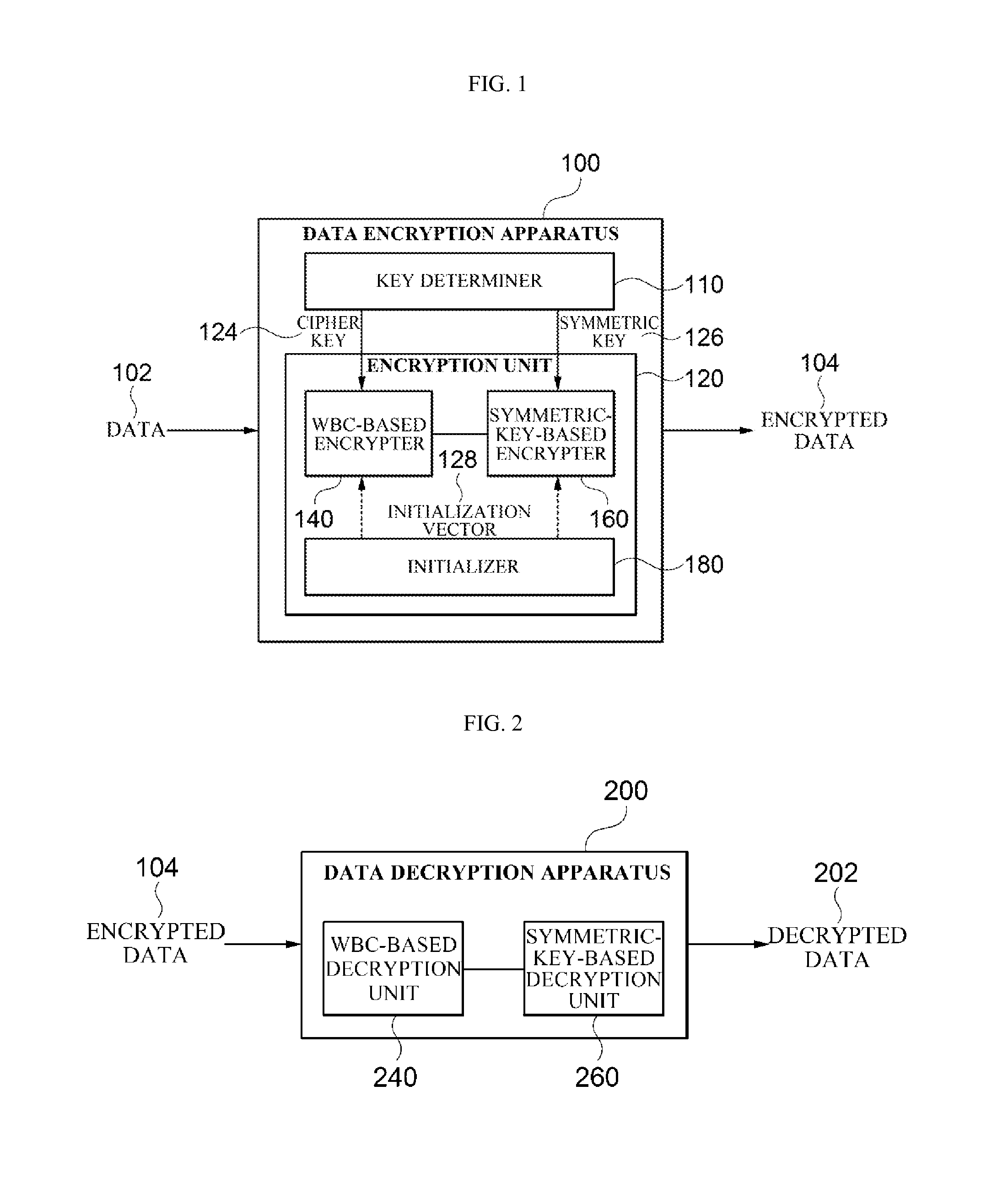
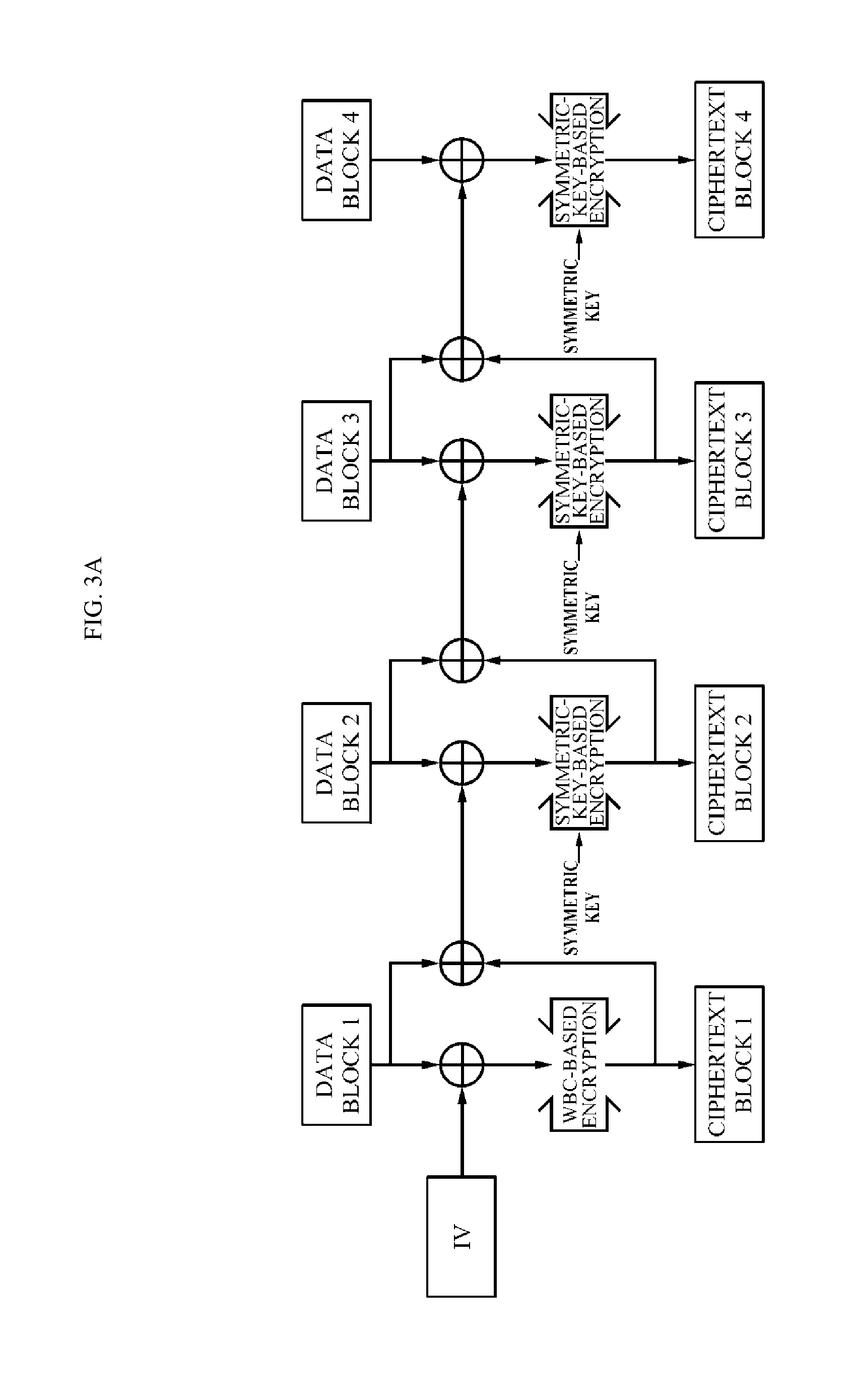
ActiveUS20160080144A1Easy accessEasy to decryptKey distribution for secure communicationCiphertextWhite box cryptography
Provided is an apparatus for encrypting data including a key determiner configured to determine a cipher key for white-box cryptography (WBC)-based encryption and a symmetric key different from the cipher key and an encrypter configured to generate a ciphertext of the data using the WBC-based encryption and symmetric-key-based encryption with the symmetric key.
Owner:SAMSUNG SDS CO LTD
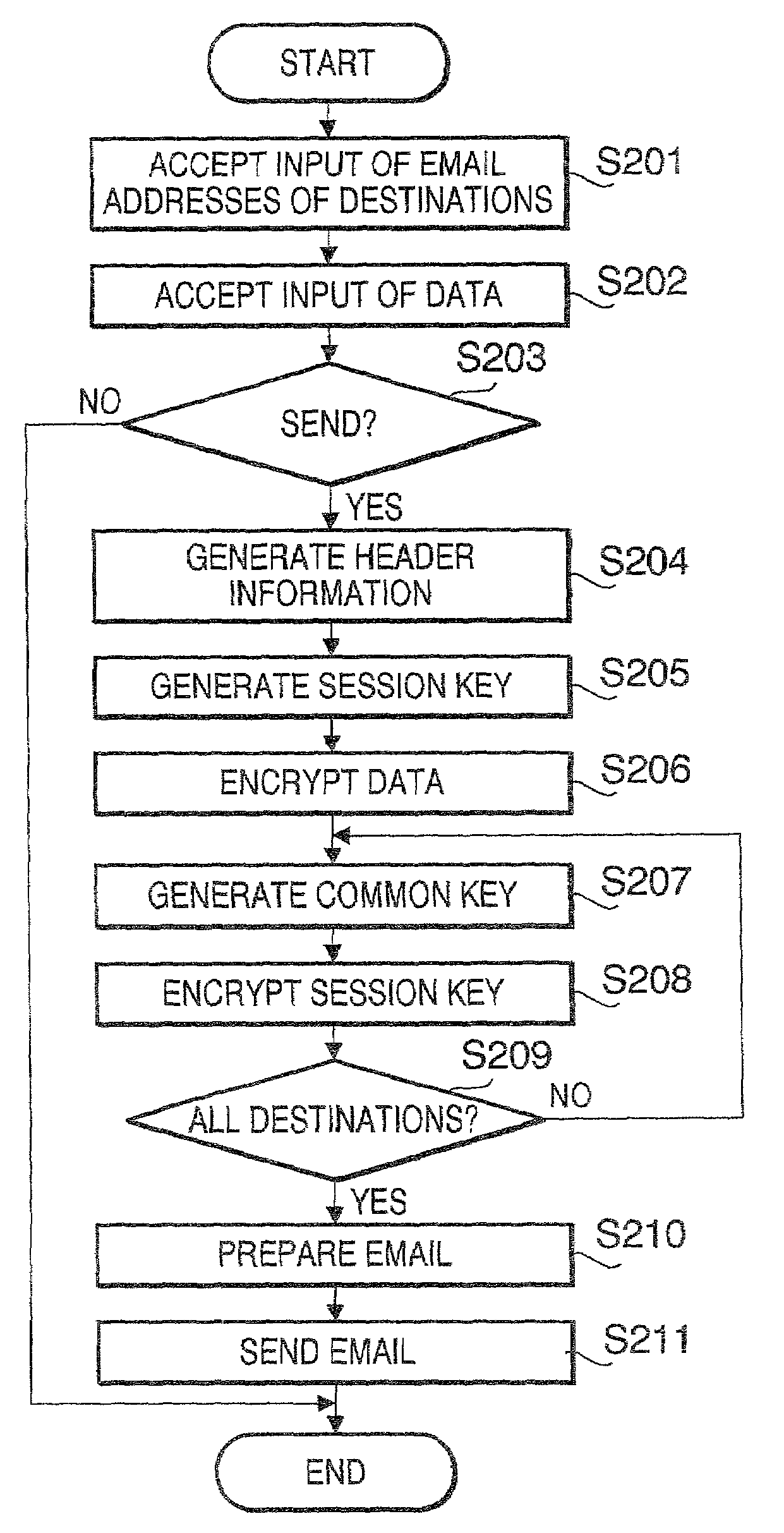
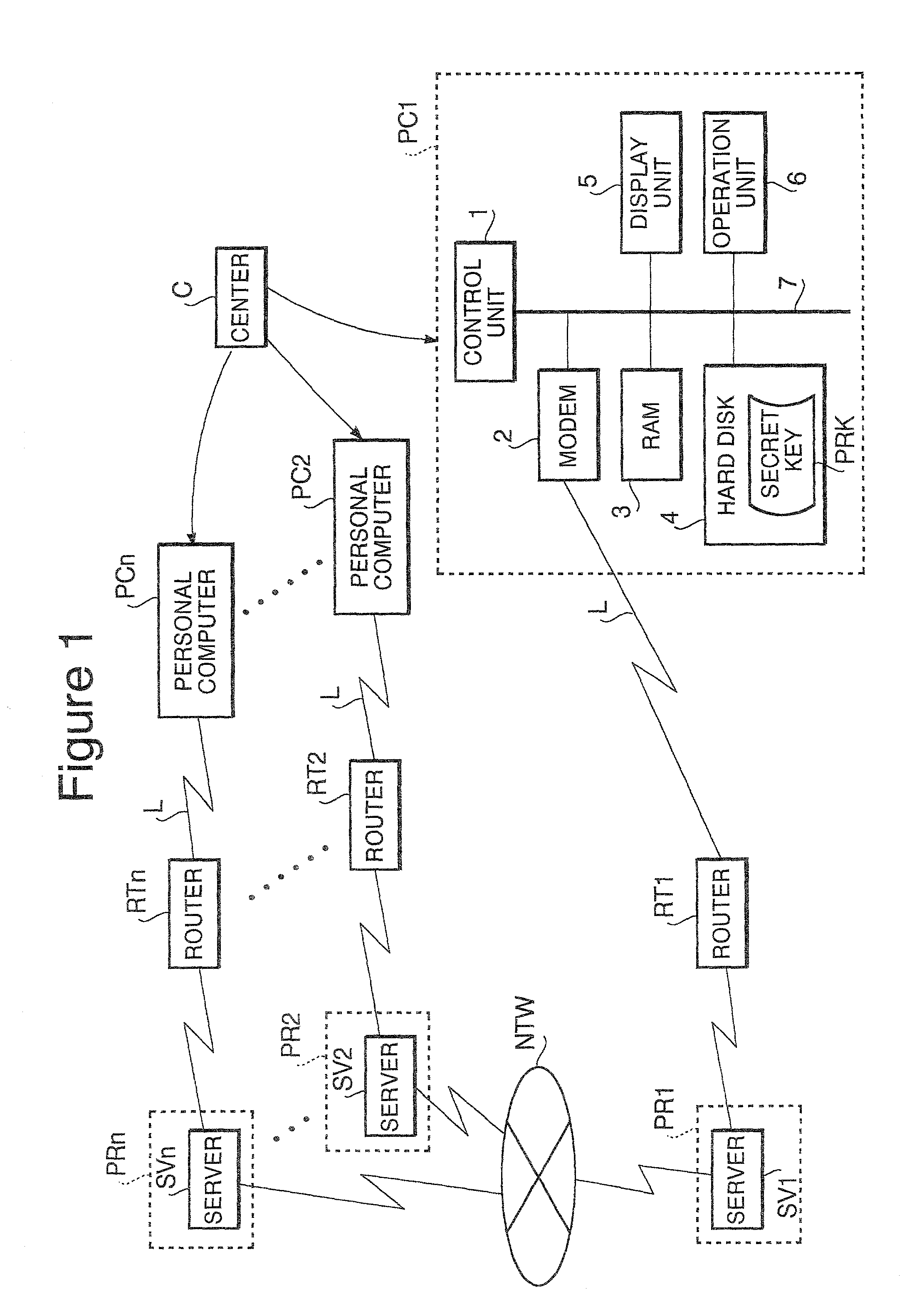
Method of transmitting email, device for implementing same method, and storing medium storing program for transmitting email
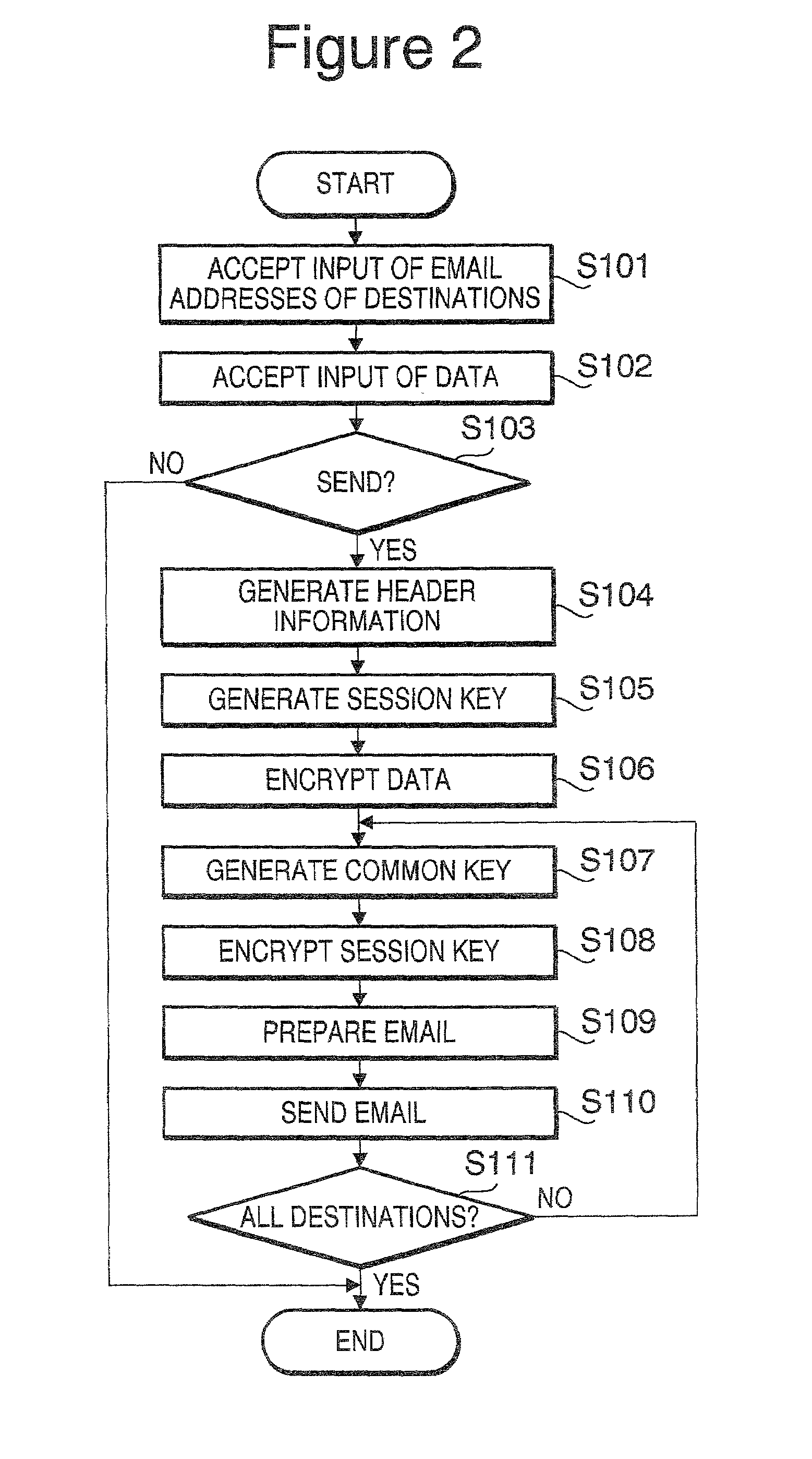
ActiveUS7167981B2Shorten the timeReduce the burden onMultiple digital computer combinationsSecret communicationEmail addressPersonal computer
A method of transmitting email and a device for transmitting email capable of broadcasting the email including encrypted data effectively. When a personal computer PC1 accepts an instruction to transmit same data to multiple destinations by email, the PC1 generates a session key (S105) and encrypts the data by utilizing the generated session key (S106). Next, the PC1 generates the common key by utilizing a public key generated based on an email address of each destination and the secret key acquired from a center in advance (S107), and encrypts the session key by utilizing the generated common key (S108). The PC1 transmits the email including the encrypted data and the encrypted session key to each destination (S110).
Owner:MURATA MASCH LTD
Method for undetectably impeding key strength of encryption usage for products exported outside the U.S
InactiveUS7873166B2Easy to decryptThe process is simple and effectiveKey distribution for secure communicationUltimate tensile strengthCommunication device
In one embodiment, a communication device includes a key strength controlling agent 308 operable to (i) receive a request for a cryptographic key; (ii) determine, from a restriction identifier, whether the cryptographic key strength is restricted; (iii) when the cryptographic key is restricted, cause the use of a second cryptographic key having a second key strength; and (iv) when the cryptographic key is not restricted, cause the use of a first cryptographic key having a first key strength. The first and second key strengths are different.
Owner:AVAYA INC
Data sending method, data receiving method, sending end and receiving end
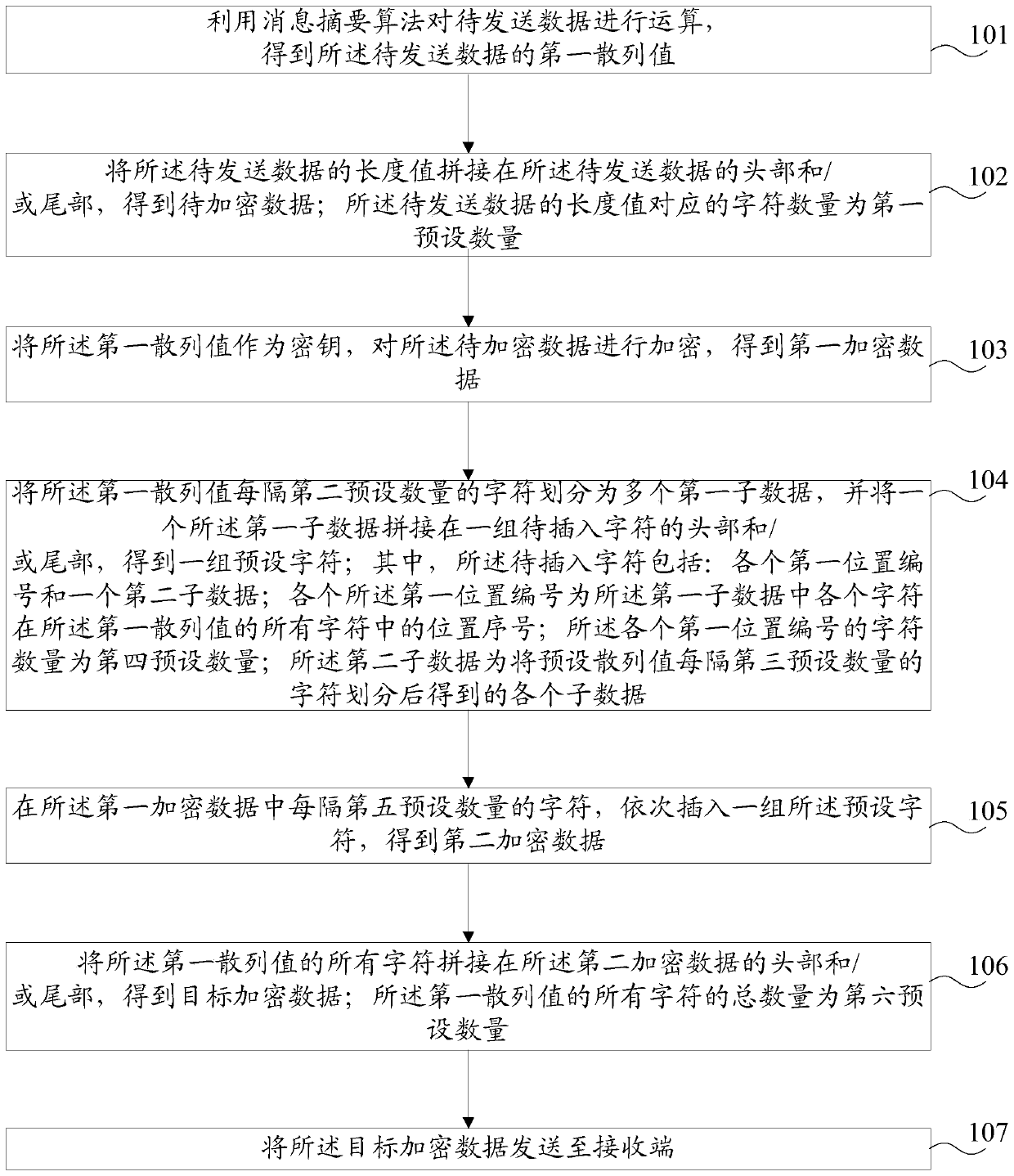
ActiveCN111211888AImprove securityEasy to decryptKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAlgorithmEngineering
The invention provides a data sending method, a data receiving method, a sending end and a receiving end, and relates to the technical field of communication. The sending method comprises the following steps: calculating to-be-sent data by utilizing a message digest algorithm to obtain a first hashed value of the to-be-sent data, splicing the length value of the to-be-sent data to the head and / orthe tail of the to-be-sent data to obtain to-be-encrypted data, encrypting the to-be-encrypted data to obtain first encrypted data, dividing the first hashed value into a plurality of pieces of firstsub-data at an interval of every a second preset number of characters, splicing one piece of first sub-data to the head and / or the tail of a group of to-be-inserted characters to obtain a group of preset characters, sequentially inserting a group of preset characters into the first encrypted data at intervals of a fifth preset number of characters to obtain second encrypted data, and splicing allcharacters of the first hashed value at the head and / or the tail of the second encrypted data to obtain target encrypted data. The data transmission security performance is high, and whether the target encrypted data is tampered or not can be conveniently verified.
Owner:新奇点智能科技集团有限公司
Safe cloud storage method and system with support of file encryption based on windows platform
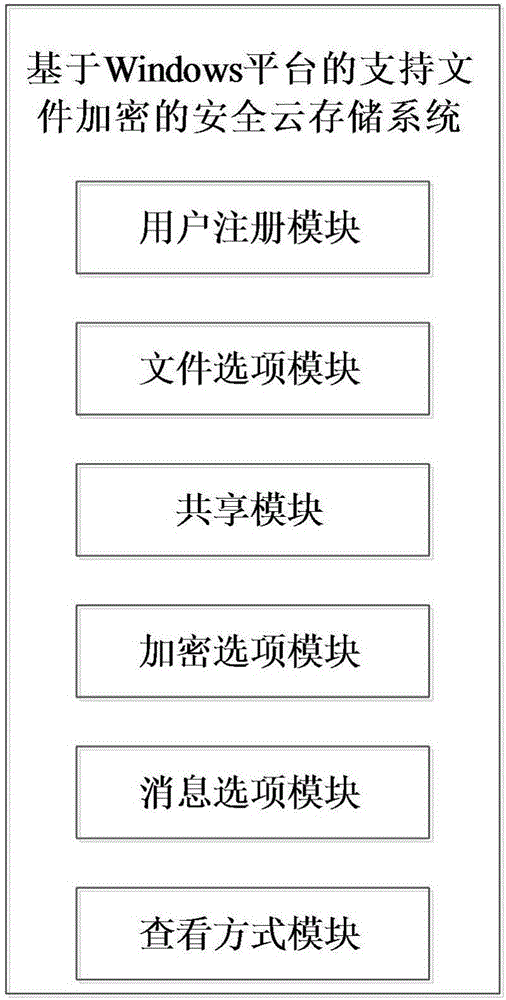
InactiveCN106302411AImprove securityImprove efficiencyDigital data protectionTransmissionJavaTerm memory
The invention discloses a safe cloud storage method and system with the support of file encryption based on a windows platform. The system comprises a user registration module, a file option module, a sharing module, an encryption option module, a message option module, a check mode module. The method and the system are based on Eclipse and the Java language development is used, the practicability is high, the cost of development is low, and the energy consumption is low; an RSA encryption algorithm is used to protect a session key, the security of the algorithm is high, and the efficiency is relatively high; a Hadoop cloud storage architecture is used by a cloud end storage architecture, the distributed storage and threshold storage are realized. The system has the advantages of a small size and low memory consumption, the storage of a private key into a mobile device is supported, and the decryption operation of an encrypted file is supported.
Owner:XIAN UNIV OF POSTS & TELECOMM
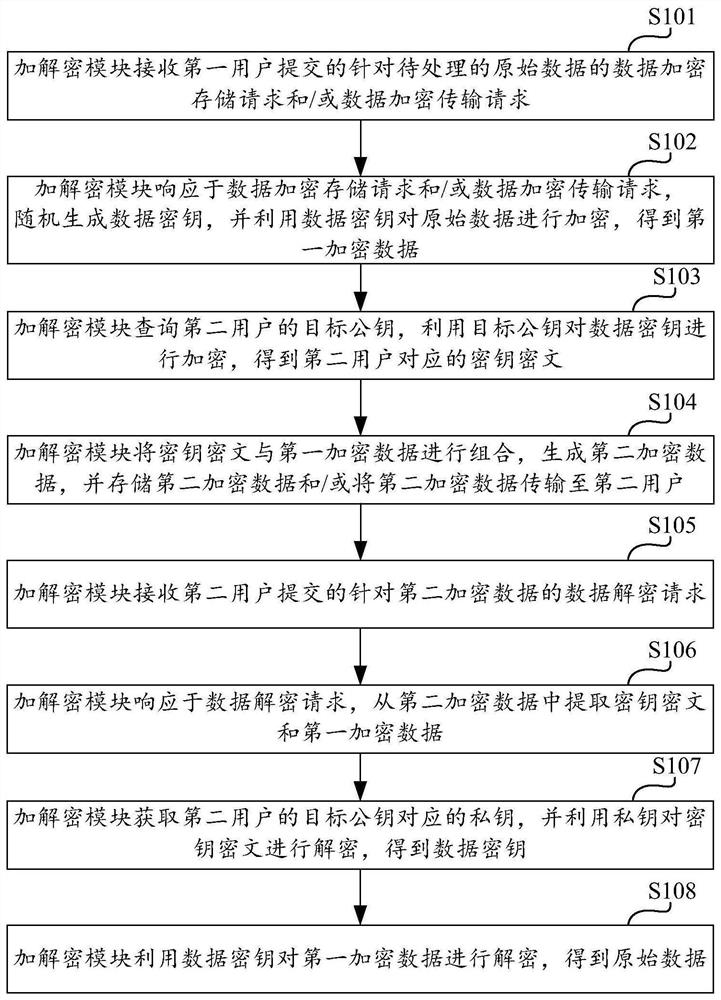
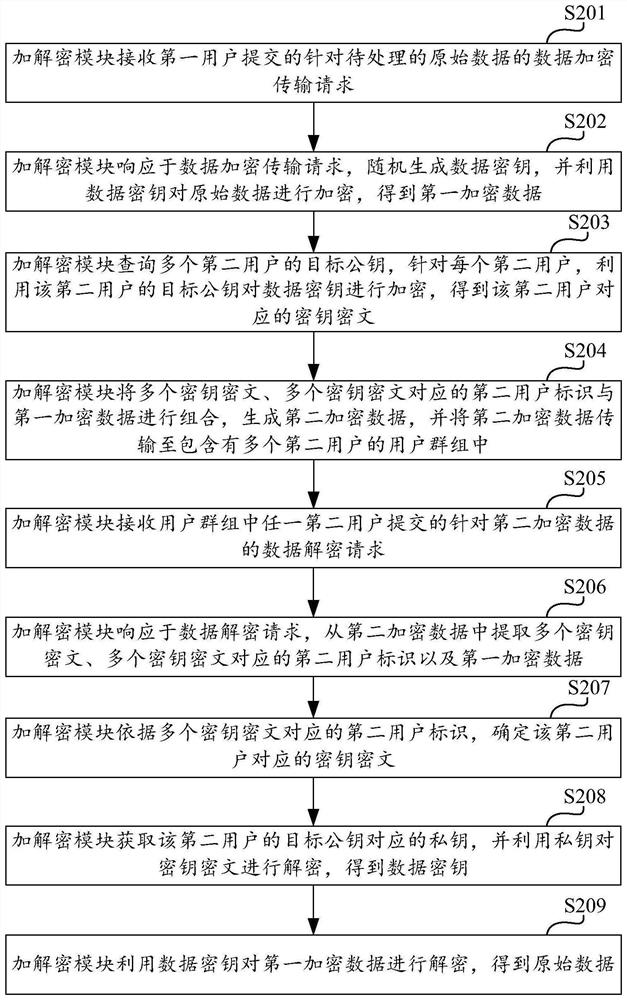
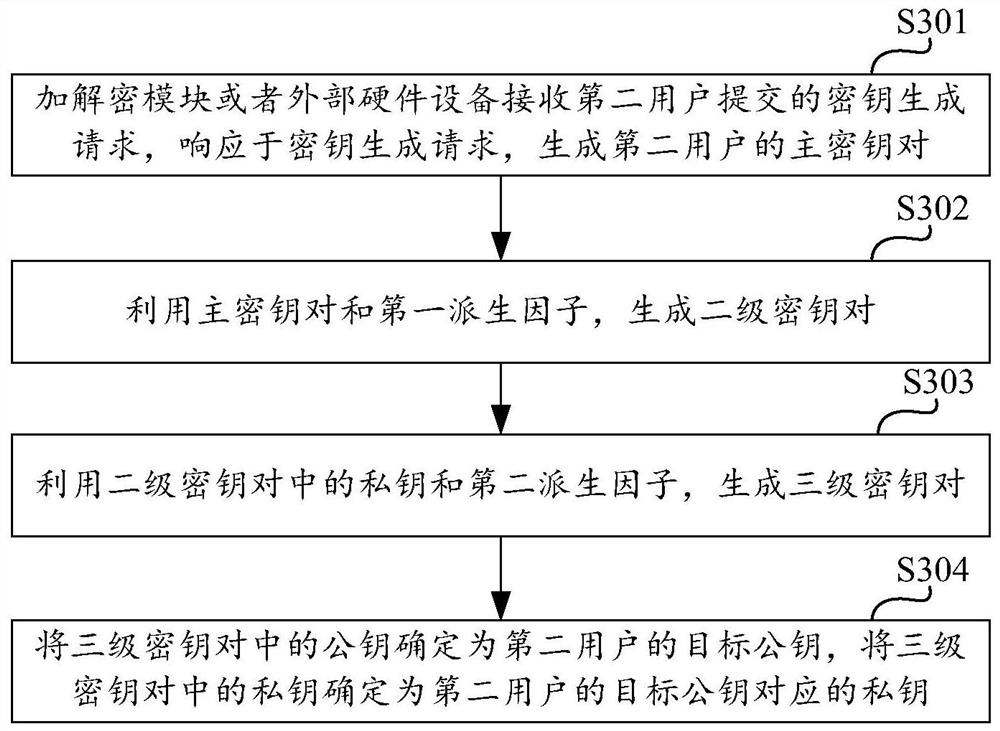
Data encryption and decryption method and device, computing equipment and storage medium
ActiveCN112235289AEnsure safetyImprove securityKey distribution for secure communicationDigital data protectionPlaintextCiphertext
The invention discloses a data encryption and decryption method and device, computing equipment and a storage medium, and the method comprises the steps: receiving a data encryption storage request and / or a data encryption transmission request, submitted by a first user, for to-be-processed original data; in response to the request, randomly generating a data key, and encrypting the original databy using the data key to obtain first encrypted data; querying a target public key of a second user, and encrypting the data key by using the target public key to obtain a key ciphertext correspondingto the second user; and combining the key ciphertext with the first encrypted data to generate second encrypted data, and storing the second encrypted data and / or transmitting the second encrypted data to a second user. According to the scheme, data storage and / or data transmission can be conveniently completed in an encryption mode, the second user can also conveniently decrypt the encrypted data, and the plaintext of the data key is not stored and / or transmitted, so that the data security is effectively improved.
Owner:GUILIN WEIWANG INTERNET INFORMATION TECH CO LTD
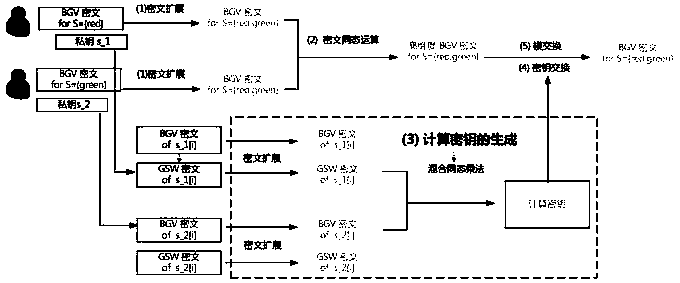
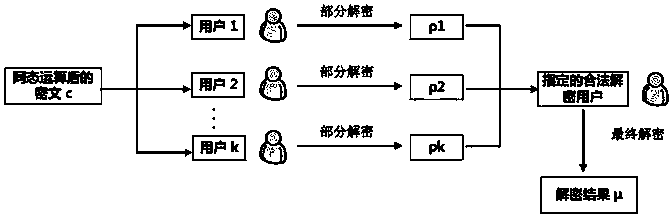
BGV type multi-key fully homomorphic encryption method with directional decryption function
PendingCN111342950AEasy to decryptReduce complexityKey distribution for secure communicationMultiple keys/algorithms usageAlgorithmCiphertext
The invention belongs to the field of information security and privacy protection, and particularly relates to a BGV type multi-key fully homomorphic encryption method with a directional decryption function, which comprises the following steps that different users use BGV type homomorphic encryption on plaintext data of themselves to obtain ciphertext corresponding to different keys; user extension is performed on the ciphertext participating in homomorphic calculation to obtain an extended ciphertext of a set (user set S) composed of all users participating in homomorphic calculation; homomorphic operation is performed on the extended ciphertext of the user set S participating in calculation to obtain a result ciphertext; the users participating in calculation carry out directional partial decryption on the result ciphertext respectively, and send partial decryption results to the users needing to be decrypted finally; and a decrypted user is appointed to carry out final decryption toobtain a plaintext result of homomorphic calculation. According to the method, the controllability of the ciphertext decryption result is enhanced, the limitation that MPC related technologies need to be used in the ciphertext broadcasting process is eliminated, and the complexity of the decryption result is reduced.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
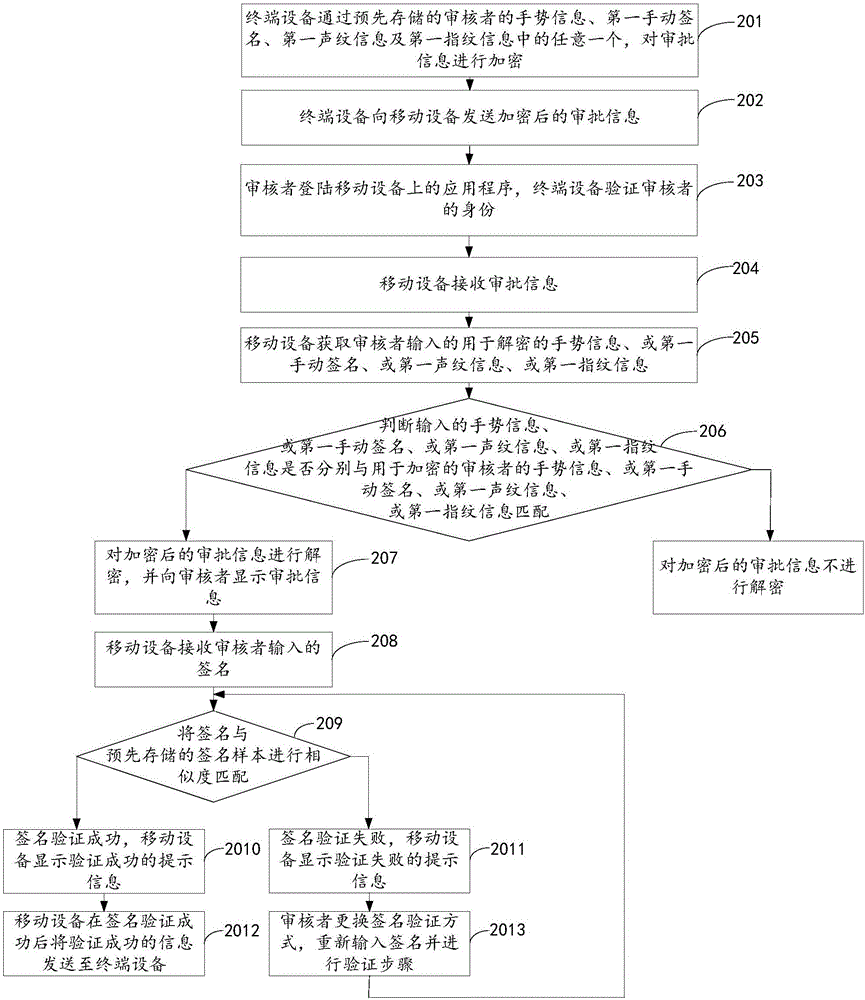
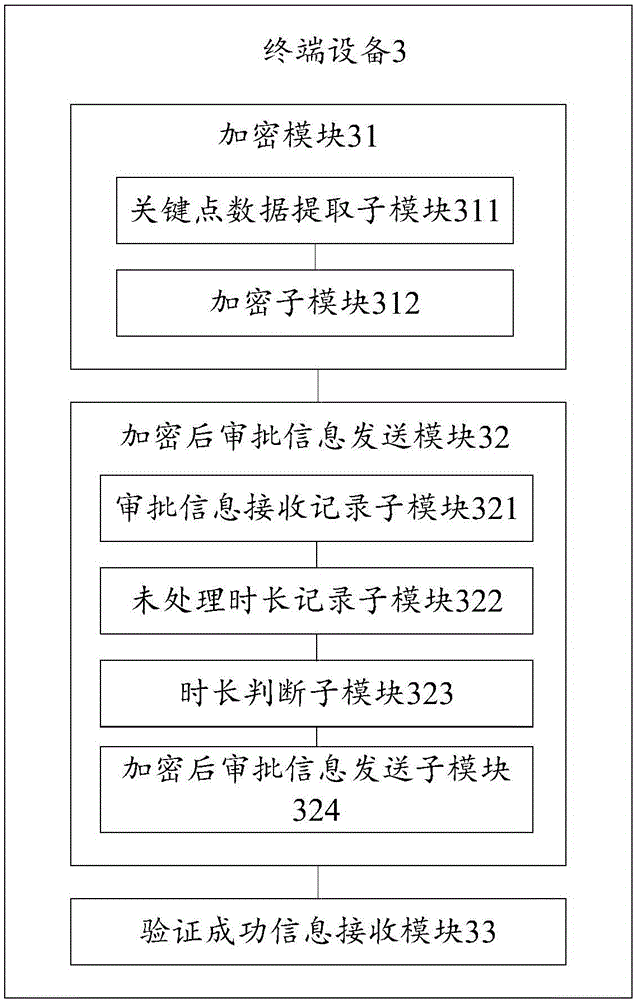
Approval signature verifying method, mobile device, terminal device and system
InactiveCN106572082AImprove securityAvoid waitingKey distribution for secure communicationUser identity/authority verificationValidation methodsTerminal equipment
The invention discloses an approval signature verifying method, a mobile device, a terminal device and a system and belongs to the technical field of communication. The method comprises the following steps: the terminal device is used for encrypting approval information via anyone of an approver gesture information, a first hand-written signature, first voiceprint information and first fingerprint information which are pre-stored; the mobile terminal obtains decryption information input via an approver, encrypted approval information is decrypted according to the decryption information, the mobile terminal obtains an approver-input signature on the approval information and verifies the signature after the approval information is successfully decrypted, and successful verification information is sent to the terminal device after the signature is successfully verified. The decryption information is obtained via the mobile device, the signature on the approval information is obtained, the approver can complete approval procedures via the mobile device, approving efficiency is improved, a problem that waiting is caused due to failure to complete the approval procedures timely when the approver is on a business trip or cannot have convenient access to the terminal device, and user experience is improved.
Owner:KMERIT SUZHOU INFORMATION SCI & TECH CO LTD
Multivariable public-key encryption/decryption system and method based on hypersphere
ActiveCN103780382AEasy to decryptReduce operational complexityPublic key for secure communicationPlaintextHypersphere
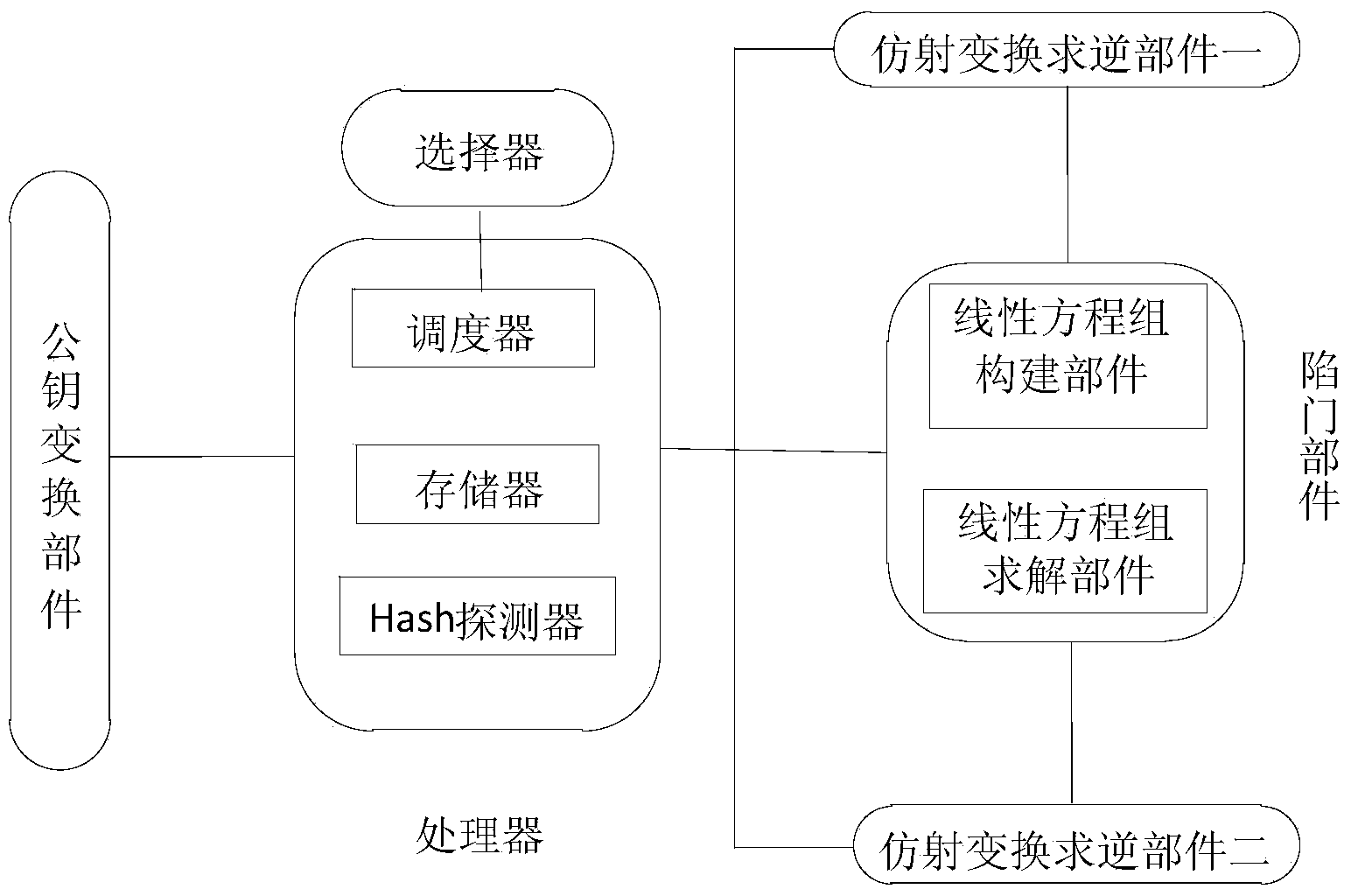
The invention discloses a multivariable public-key encryption / decryption system based on a hypersphere. The system includes an encryption module and a decryption module, wherein the encryption module includes a processor and a public-key conversion part which converting plaintext into ciphertext; and the decryption module includes a processor, an affine transformation inversion part I, a trap door part and an affine transformation inversion part II. The trap door part includes a linear equation set construction part and a linear equation set solution part and different parts execute corresponding operations. At last, a group of data is obtained and the group of data is stored and output as decrypted plaintext. If no data is generated by the decryption module, the processor outputs alarm information of decryption error to a user. The system and the method do not use a large-domain technology, and designed center mapping includes N groups of sphere centers used as private keys so as to realize center hiding and at the same time, operation speed is significantly high and a decryption process only requires solution of a linear equation set.
Owner:SOUTH CHINA UNIV OF TECH
Certificate-based end-to-end key exchange method
ActiveCN108259486ASimplify the exchange processImprove exchange efficiencyKey distribution for secure communicationUser identity/authority verificationKey exchangeMan-in-the-middle attack
The invention discloses a certificate-based end-to-end key exchange method. The method comprises the following steps: first step, a terminal I obtains a public key of a terminal II, wherein the specific process is as follows: A1, the terminal I encrypts the public key and submits the same to a server; A2, the server decrypts the public key encrypted by the terminal I, a digital certificate authentication center creates a user certificate of the terminal I, and the server stores the user certificate of the terminal I; A3, the terminal I generates a request message for key exchange with the terminal II; A4, the server sends the user certificate of the terminal I to the terminal II, and after the terminal II agrees to the key exchange request, the server sends the user certificate of the terminal II to the terminal I; A5, the terminal I parses the public key of the terminal II from the user certificate of the terminal I and stores and the same. Similarly, the terminal II acquires the public key of terminal 1. By adoption of the certificate-based end-to-end key exchange method, the key exchange process is simplified, the man-in-the-middle attacks and replay attacks in the registrationprocess are prevented, and the security of the public key is improved.
Owner:河南芯盾网安科技发展有限公司
Multi-signature implementation method and device, equipment and storage medium
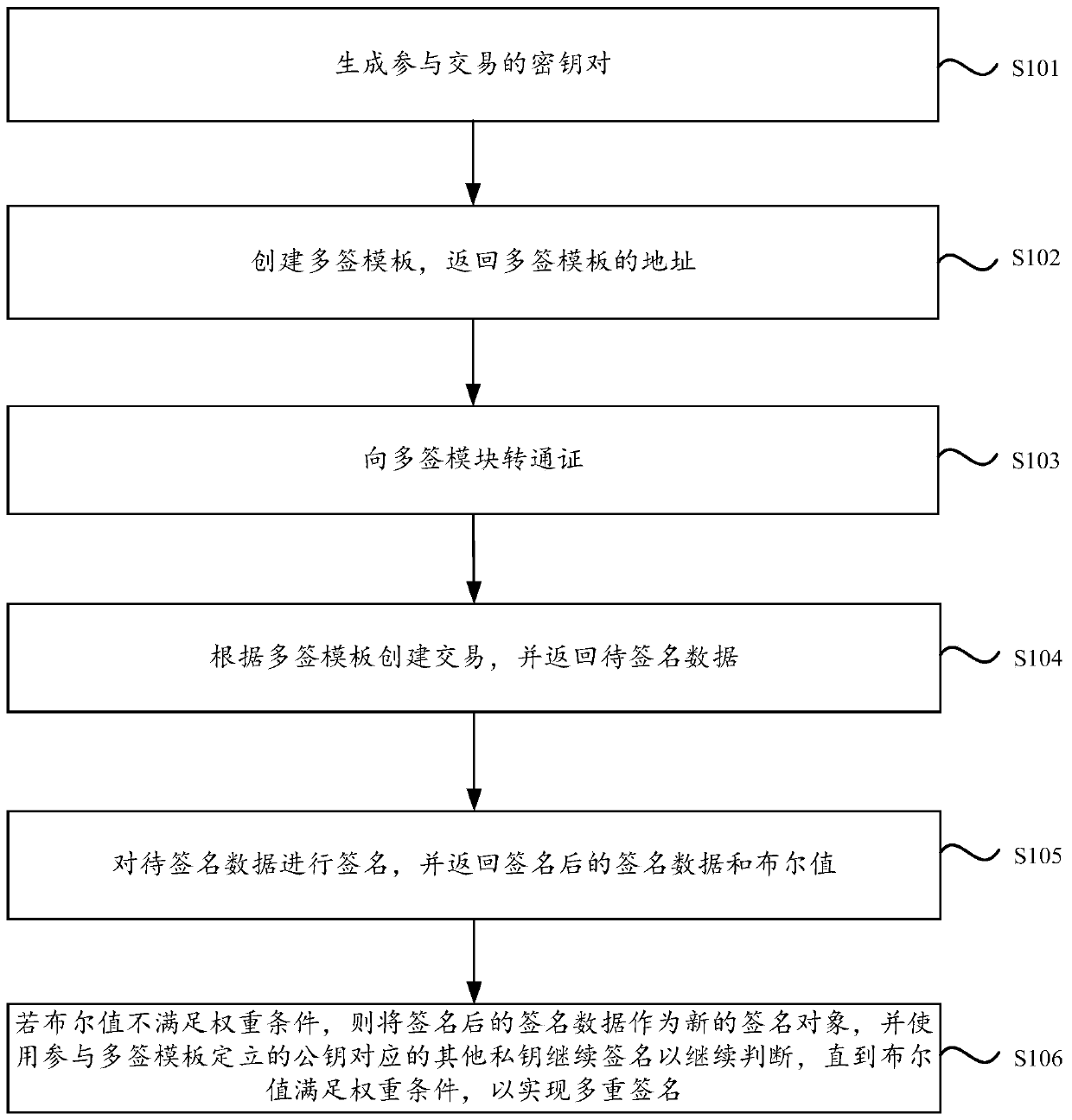
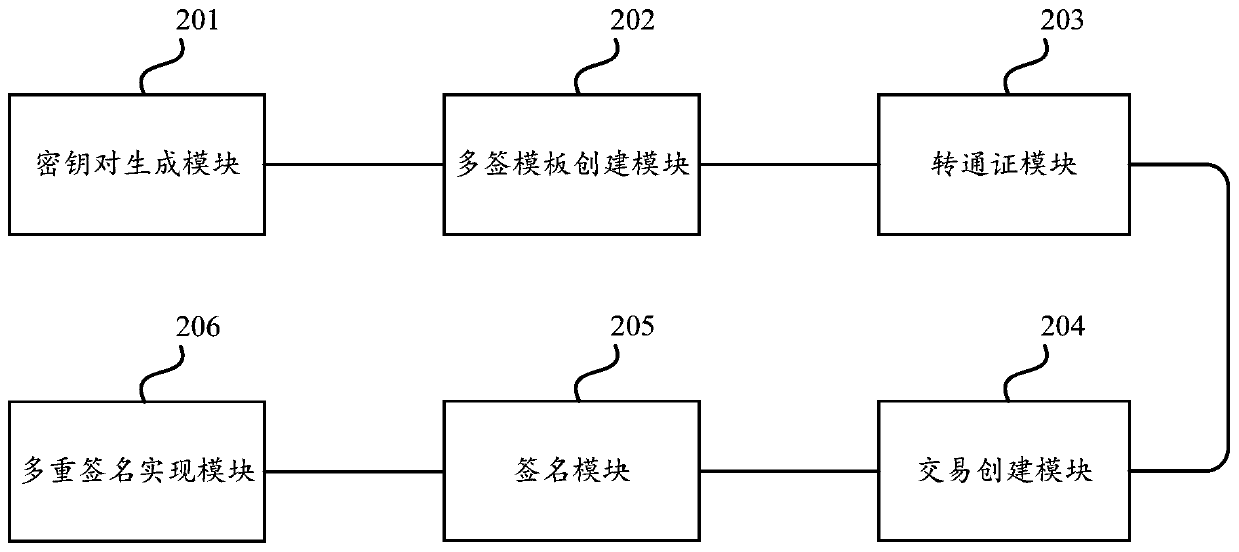
PendingCN111523889AEasy to operateGood encryptionKey distribution for secure communicationMultiple keys/algorithms usageEngineeringMultisignature
The invention relates to a multi-signature implementation method and device, equipment, and a storage medium. The method comprises the steps of generating a key pair participating in a transaction; creating a multi-label template, and returning the address of the multi-label template; transferring a pass certificate to the multi-signature module; creating a transaction according to the multi-signature template, and returning to-be-signed data; signing the to-be-signed data, and returning signed signature data and a Boolean value; and if the Boolean value does not meet the weight condition, taking the signed signature data as a new signature object, and continuing to sign by using other private keys corresponding to a public key participating in multi-signature template establishment so asto continue to judge until the Boolean value meets the weight condition, thereby realizing multi-signature. The multi-signature scheme has the characteristics of simplicity and safety in operation andhigh running speed.
Owner:KUNMING DABANGKE SCI & TECH CO LTD
Data encryption method, security chip, and computer readable storage medium
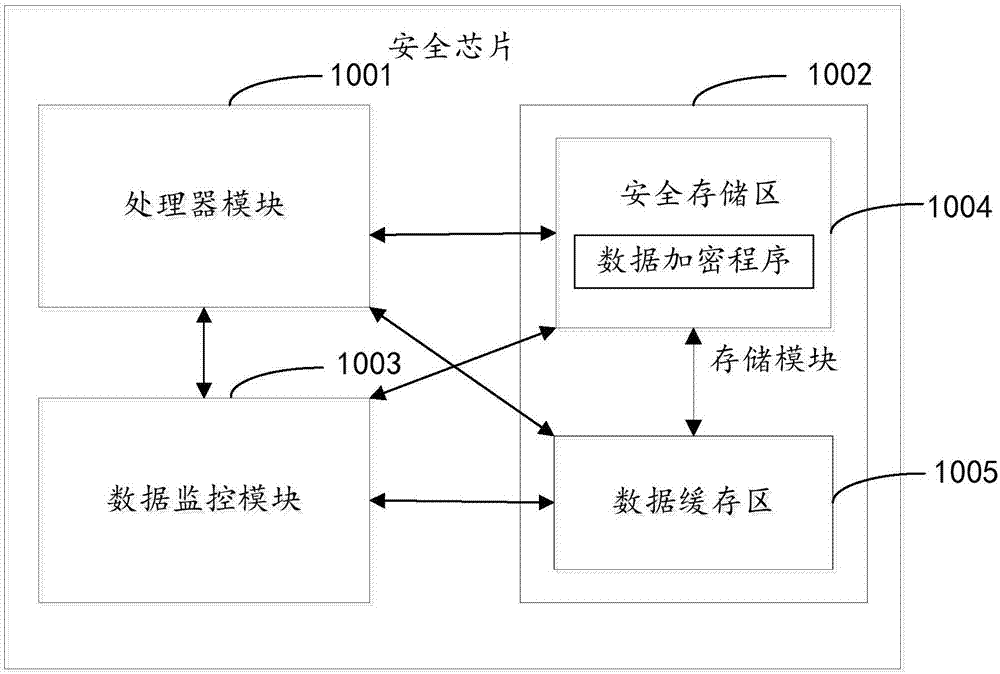
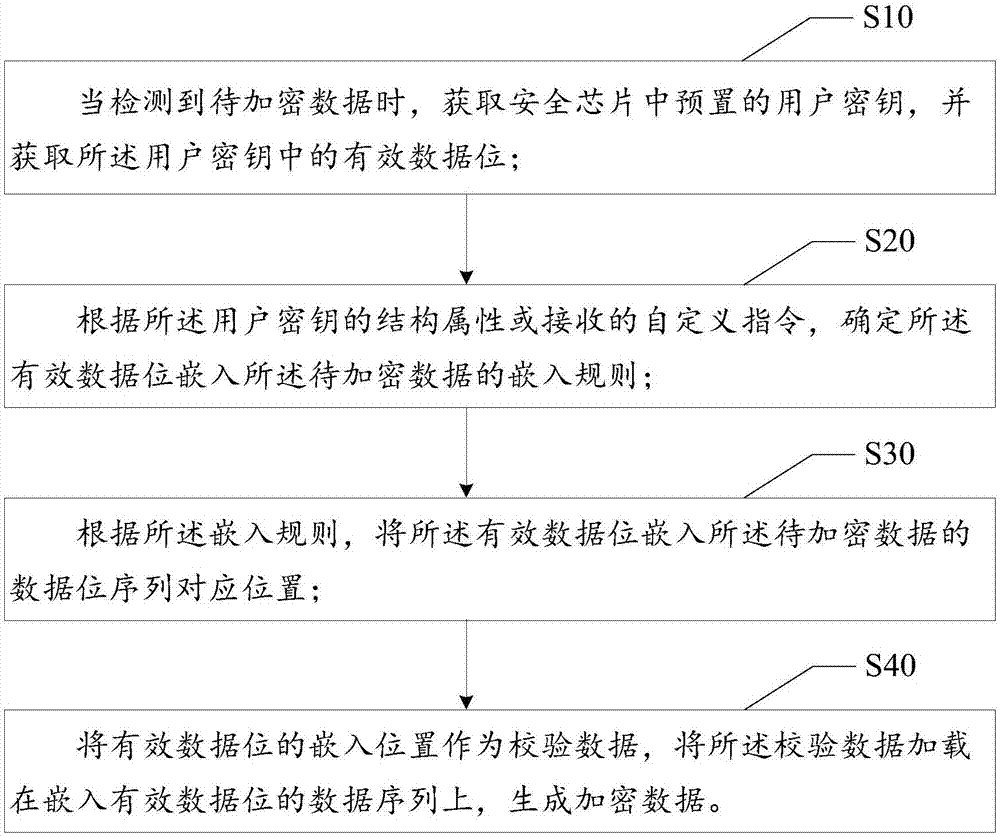
InactiveCN107359989AEnsure safetyIncrease the difficulty of crackingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareData sequences
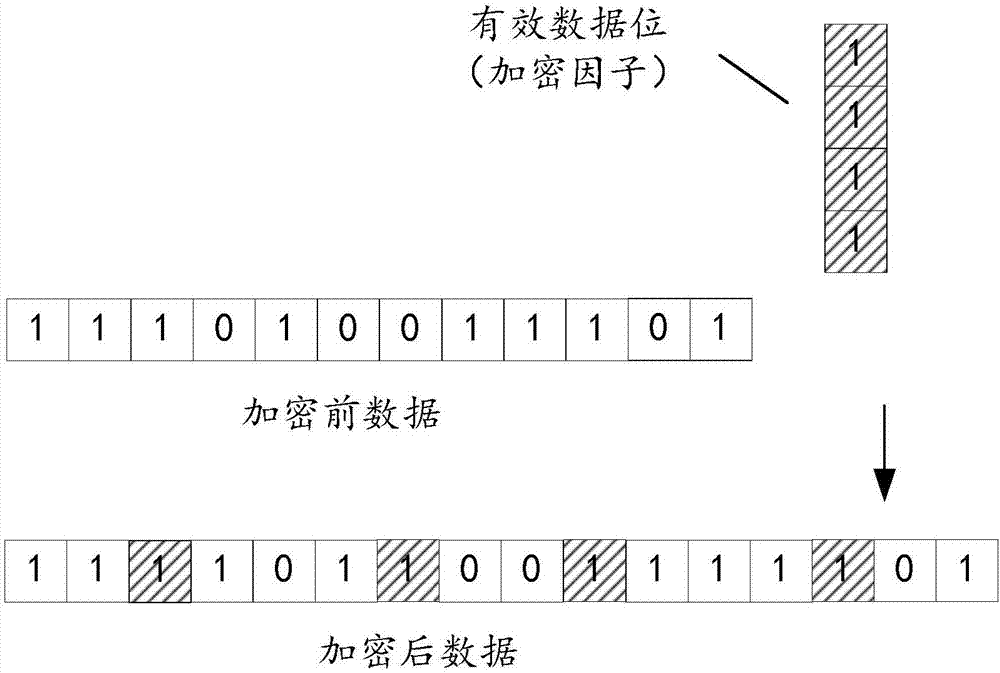
The invention discloses a data encryption method. The method includes steps of acquiring a user key preset in a security chip and valid data bits in the user key when to-be-encrypted data is detected; determining an embedding rule for embedding the valid data bits in the to-be-encrypted data according to the structure attribute of the user key or a received customized instruction; embedding the valid data bits in corresponding positions of a data bit sequence of the to-be-encrypted data according to the embedding rule; using the embedded positions of the valid data bits as check data, and loading the check data onto the data sequence in which the valid data bits are embedded in order to generate encrypted data. The invention also discloses a security chip and a computer readable storage medium. The data encryption method can increase the cracking difficulty of encrypted data.
Owner:GD MIDEA AIR-CONDITIONING EQUIP CO LTD
Embedded device firmware security upgrading method and system, terminal and storage medium
PendingCN111596938AEnsure safetyEnsure stabilityDigital data protectionSoftware deploymentEncryptionTemporary file
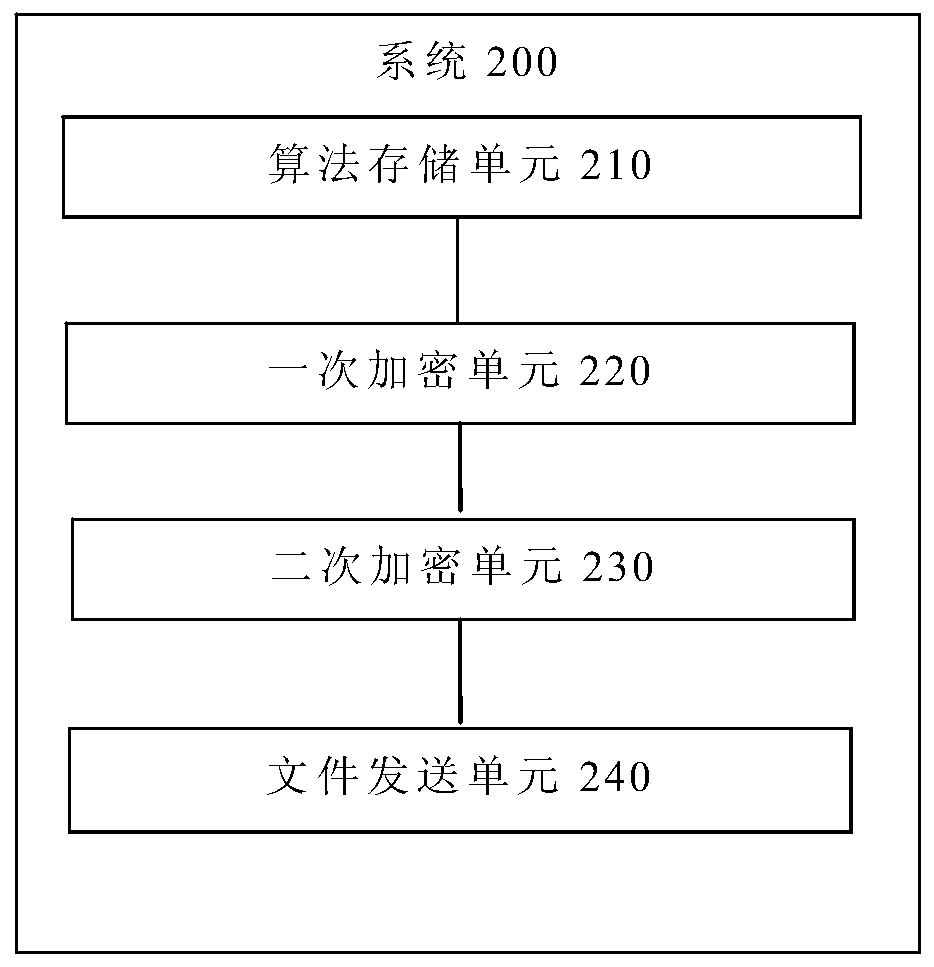
The invention provides an embedded device firmware security upgrading method and system, a terminal and a storage medium, and the embedded device firmware security upgrading method comprises the steps: setting an encryption algorithm library, and storing a plurality of encryption algorithms in the encryption algorithm library; randomly selecting an encryption algorithm from the encryption algorithm library as a primary encryption algorithm to perform primary encryption on an upgrade file, and encoding and packaging the primary encryption file and the primary encryption algorithm into a temporary file; randomly selecting an encryption algorithm from the encryption algorithm library as a secondary encryption algorithm to encrypt the temporary file, and encoding and packaging the encrypted file and the secondary encryption algorithm into an encrypted upgrade file; and sending the encrypted upgrading file to a terminal to which embedded equipment to be upgraded belongs, wherein the encrypted upgrading file is decrypted and decompressed by the terminal and then burnt to the embedded equipment to be upgraded. According to the embedded device firmware security upgrading method and system,the security of the firmware upgrading file can be improved, so that the security upgrading of the firmware of the embedded equipment is realized.
Owner:青岛海米飞驰智能科技有限公司
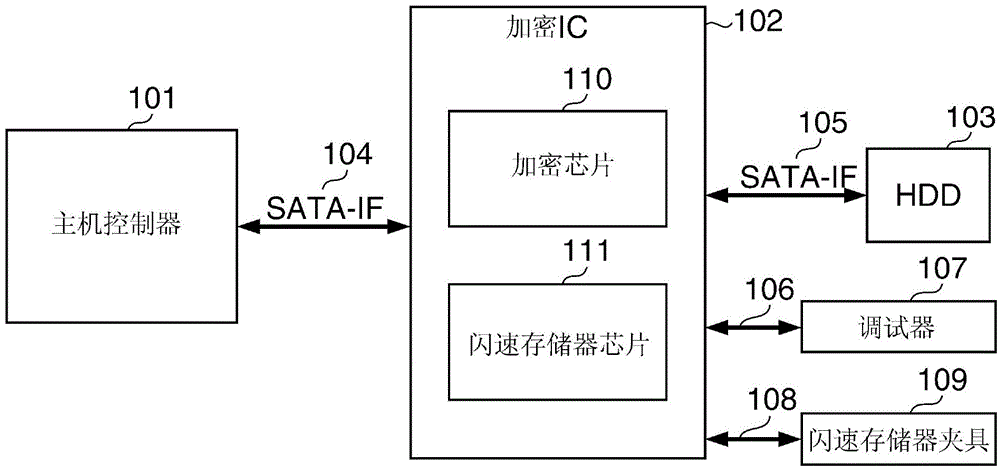
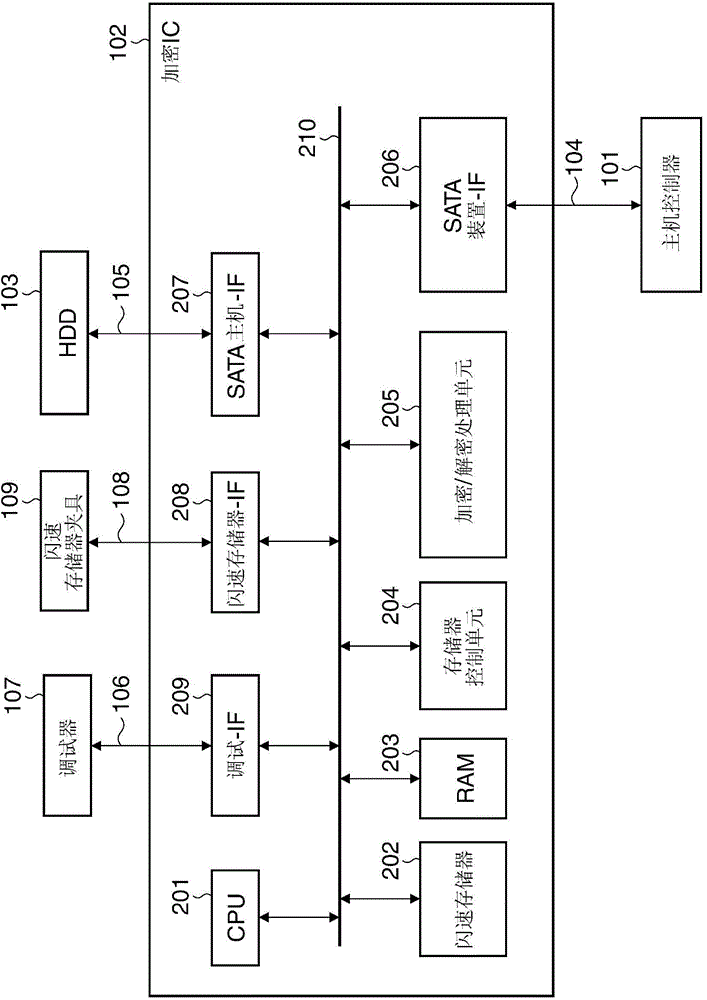
ENCRYPTION/DECRYPTION SYSTEM and its control method
ActiveCN104902138AEasy to decryptInternal/peripheral component protectionSecuring communicationComputer hardwareEncryption
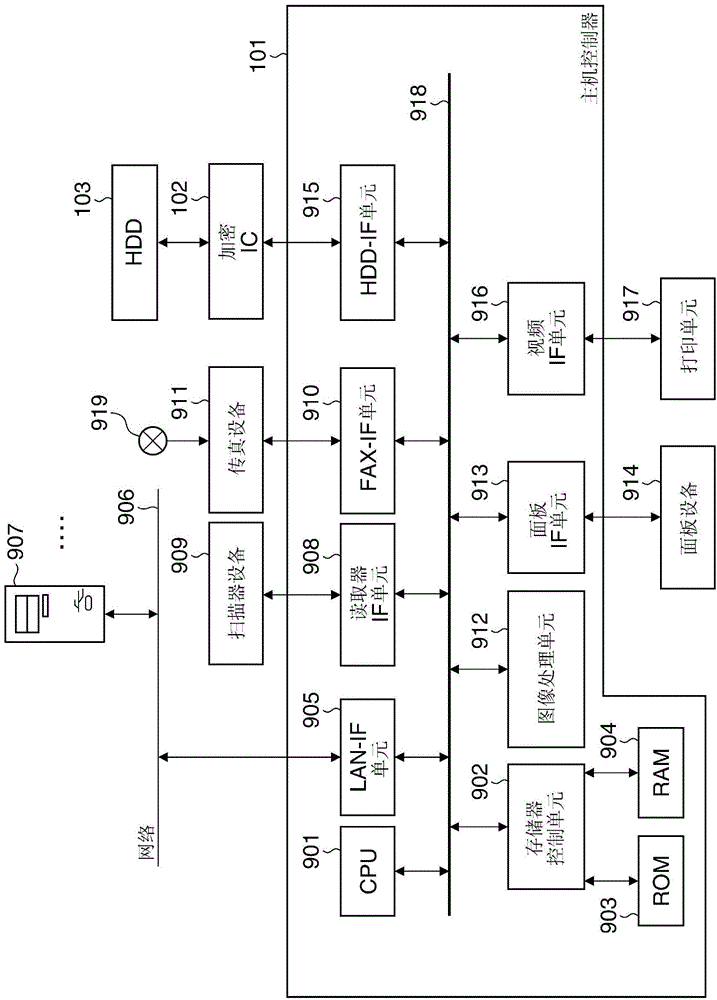
An encryption / decryption system which is capable of preventing encrypted data from being easily decrypted. A program for carrying out an encryption process or a decryption process on data sent and received to and from a host apparatus is stored in encrypted form. A key for decrypting the stored program is generated in response to startup of the encryption / decryption system. The stored program is decrypted using the generated key, and the decrypted program is executed.
Owner:CANON KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com