A data encryption, decryption system and method
A data encryption and subsystem technology, applied to the public key and key distribution of secure communication, which can solve problems such as inconvenience of use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The present invention will be further elaborated below in conjunction with the accompanying drawings.
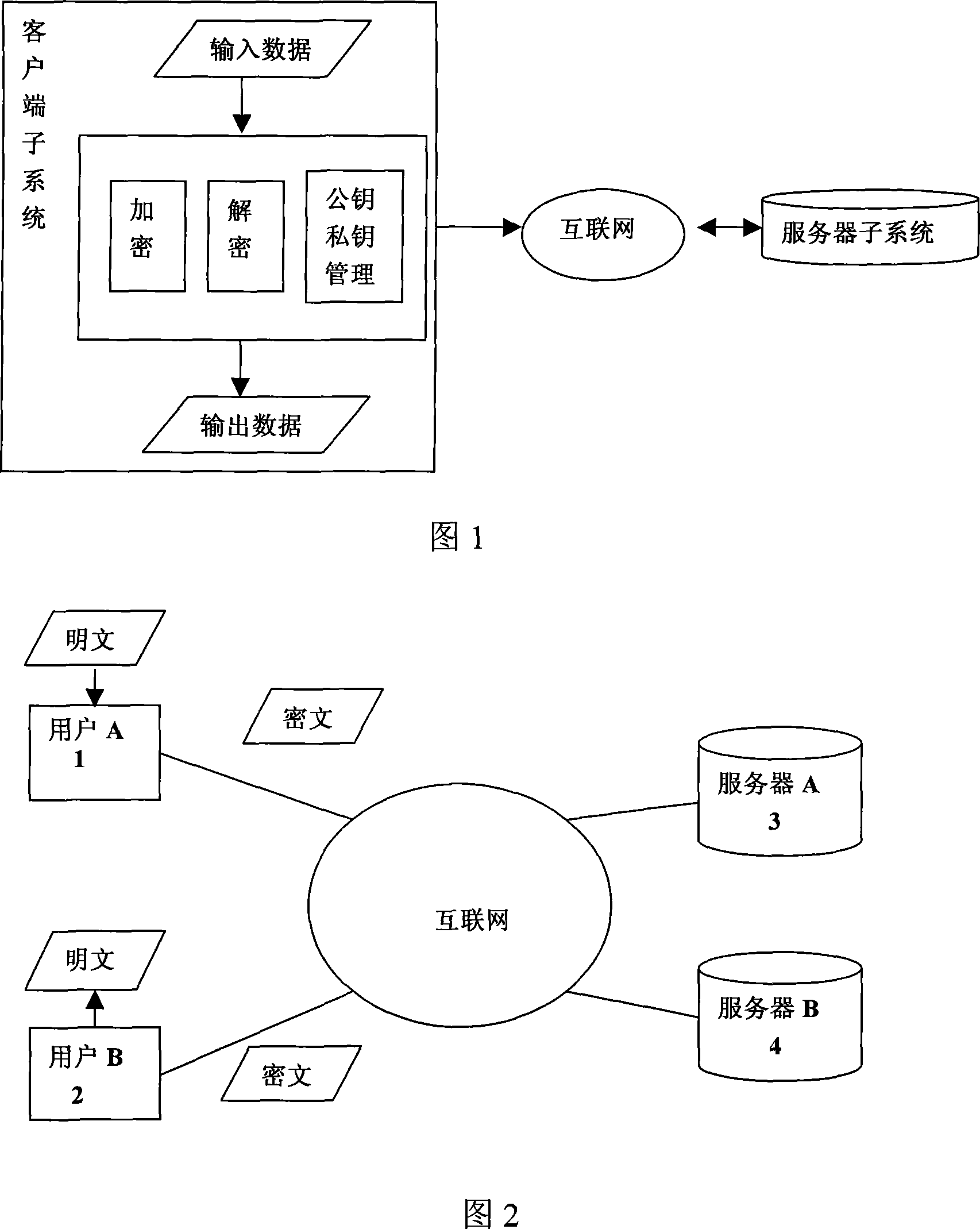
[0048] As shown in Figure 1, a data encryption and decryption system includes a client subsystem that accepts user instructions to encrypt and decrypt files, and manages public / private keys, and a client subsystem that accepts job requests, executes The server subsystem that does the job and returns the job result, the client subsystem and the server subsystem communicate data through the Internet. The jobs performed by the server subsystem include the generation, storage, release and management of public / private keys, and the review of the release information of the public key. The server can also make public and private key review requests from different users according to the user's preset settings. Authority control; encrypt the data submitted in the job according to the public key stored in the server by the user; decrypt the data submitted in the job according t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com