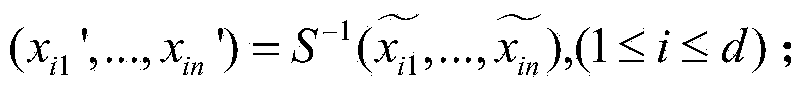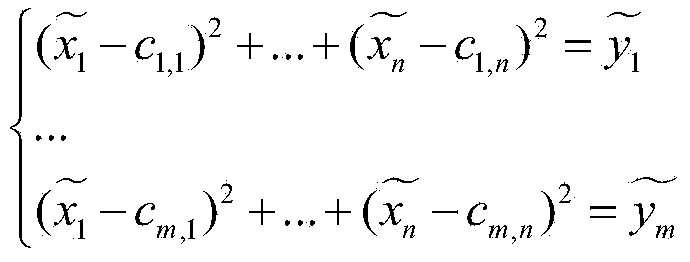Multivariable public-key encryption/decryption system and method based on hypersphere
A multi-variable public key, hypersphere technology, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
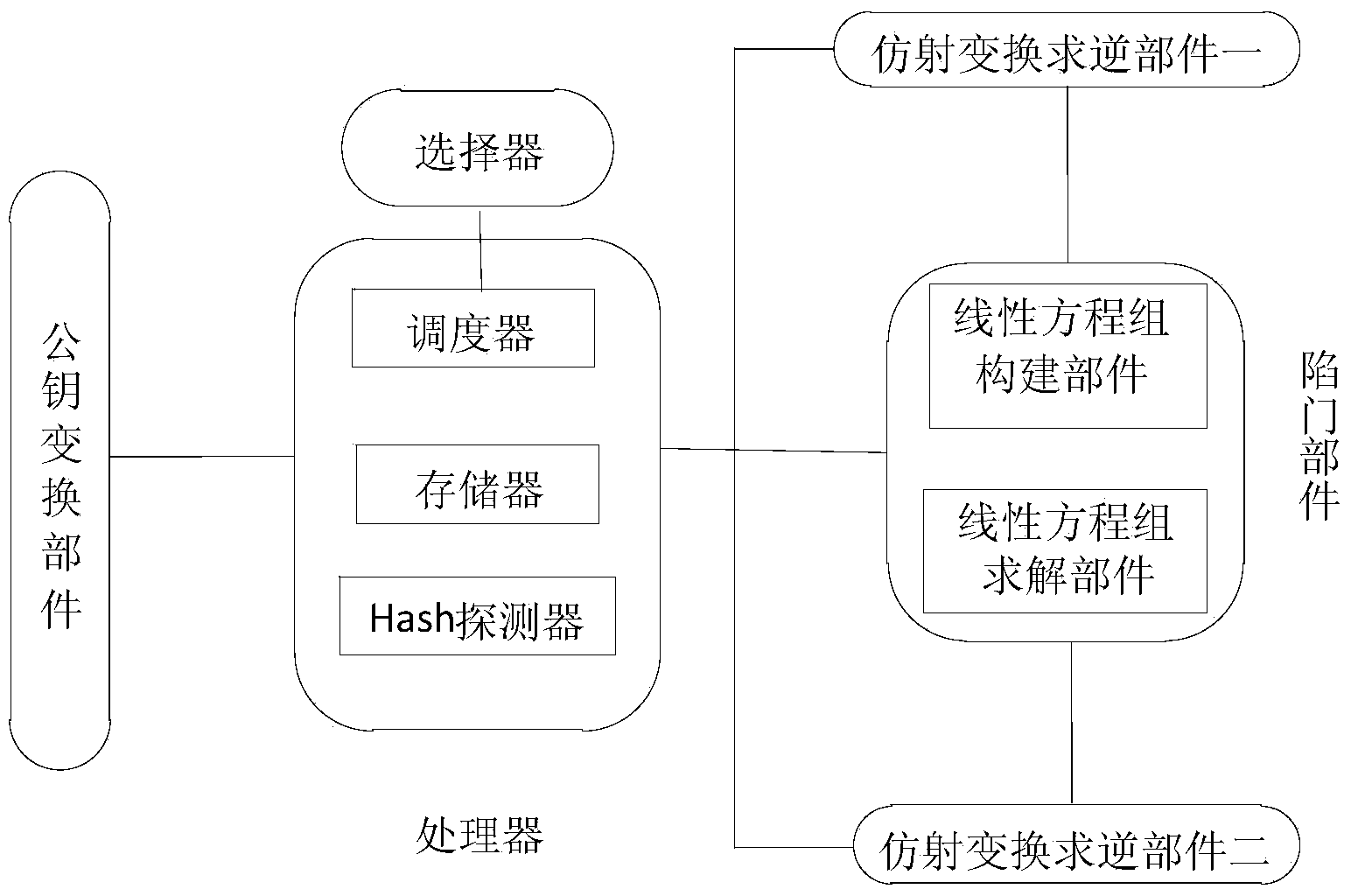
[0053] Such as figure 1 , a hypersphere-based multivariate public-key encryption / decryption system, comprising:
[0054] A, the selector, which is connected with the scheduler in the processor, when the selector is in the open state, the encryption module of the system works, and when the selector is in the closed state, the decryption module of the system works;
[0055] B, encryption module, is used for encrypting the plaintext to be encrypted, forms ciphertext, completes encryption, and it comprises processor, public key transformation part, and the plaintext to be encrypted is transmitted to processor, and wherein processor comprises scheduler, Hash Detector, memory, Hash detector calculates the hash value of the plaintext, obtains the hash redundant data of the plaintext, and stores the plaintext and its hash redundant data of the plaintext in the memory, and then transmits the plaintext data to the public key transformation component, public The key transformation compo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com